Automatic monitoring method and system for open source component vulnerabilities
An automatic monitoring and vulnerability technology, applied in the direction of instruments, electrical digital data processing, platform integrity maintenance, etc., can solve the problems of inability to respond to vulnerabilities in a timely manner, low analysis efficiency, inconsistent timing of vulnerability explosion and repair, etc., to improve security and vulnerability response timeliness, improve security response timeliness, and save huge workload
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
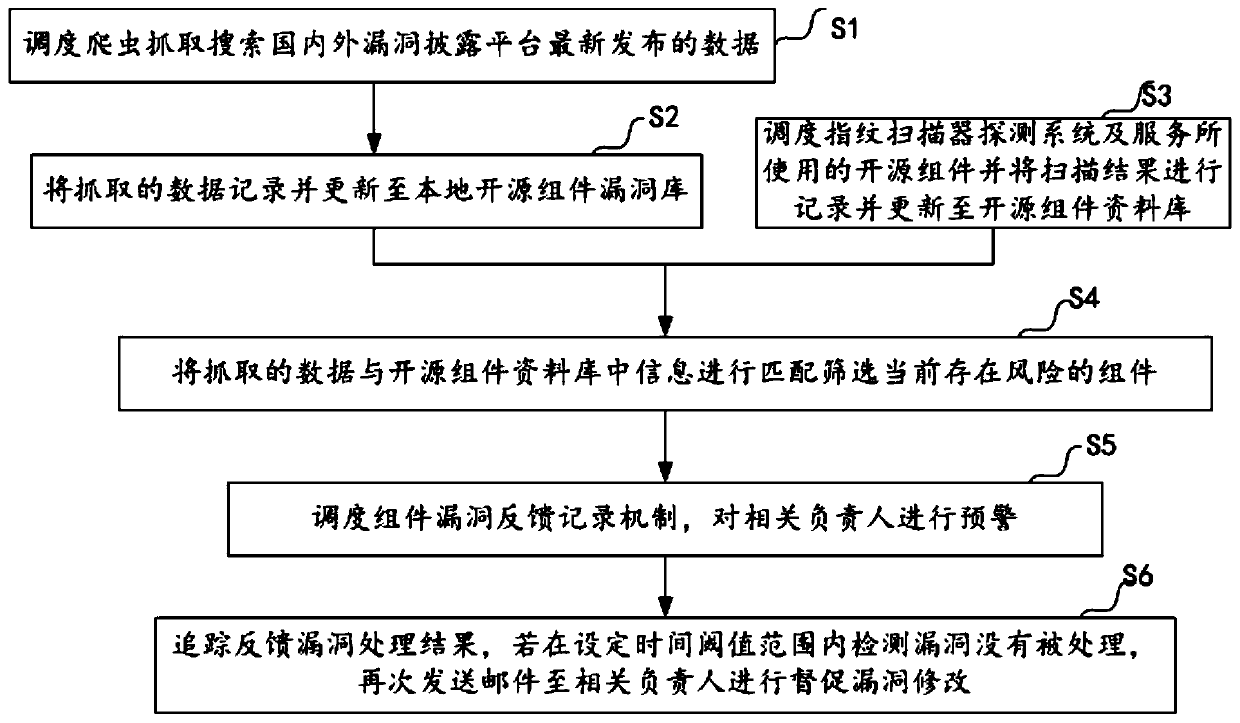
[0052] Such asfigure 1 As shown, the embodiment of the present invention provides a method for automatic monitoring of open source component vulnerabilities, including the following steps:
[0053] S1: Schedule crawlers to crawl and search for the latest data released by domestic and foreign vulnerability disclosure platforms;
[0054] What needs to be explained is that in this step, the crawler is set to be automatically dispatched at zero o'clock every day to capture data from domestic and foreign vulnerability disclosure platforms such as CVE, cnnvd, and cnvd;
[0055] S2: Record and update the captured data to the local open source component vulnerability library;
[0056] Extract effective key information from the captured data, integrate and filter the captured data, and save it to the local vulnerability database in a standard format; effective key information includes CVE-ID, vulnerability name, vulnerability details, vulnerable components, affected component versions,...
Embodiment 2
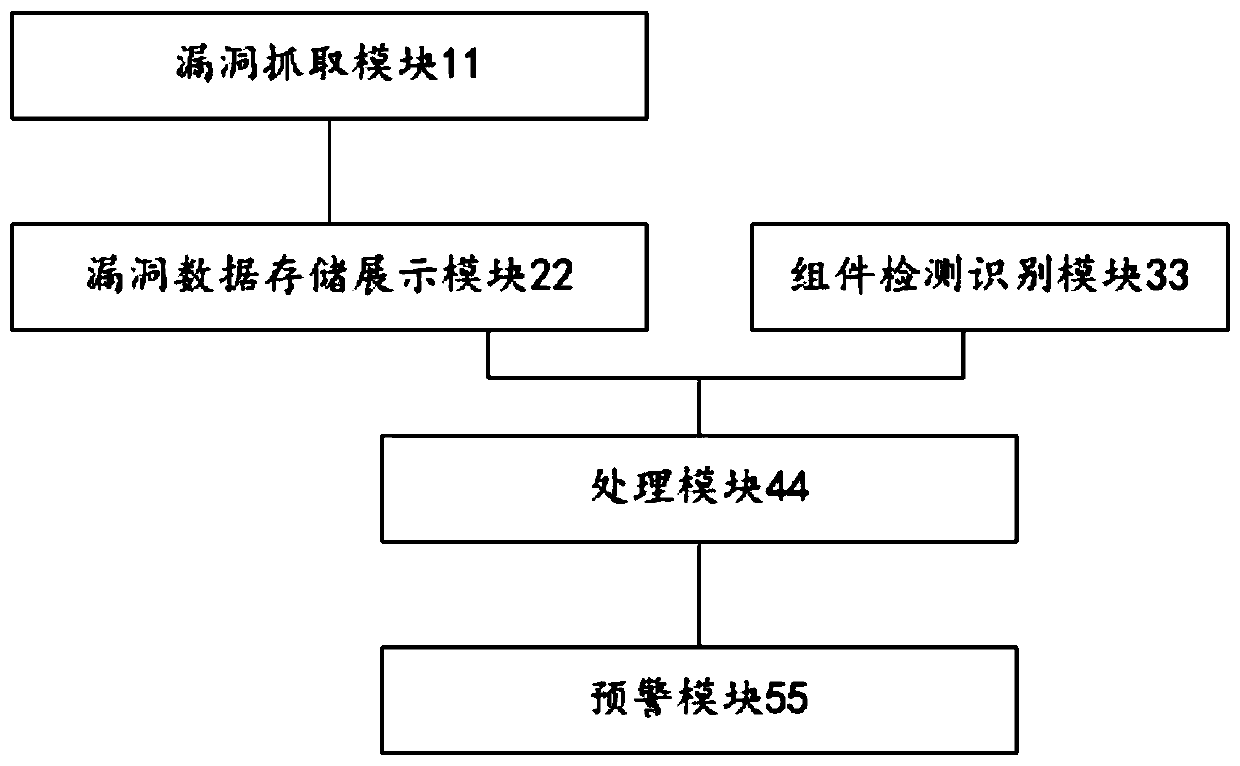
[0063] Such as figure 2 As shown, the embodiment of the present invention provides an automatic monitoring system for open source component vulnerabilities, including a vulnerability capture module 11, a vulnerability data storage display module 22, a component detection and identification module 33, a processing module 44, and an early warning module 55;
[0064] The vulnerability capture module 11 is used to schedule crawlers to capture and search the latest data released by domestic and foreign vulnerability disclosure platforms;
[0065] The vulnerability data storage and display module 22 is used to record and update the captured data to the local open source component vulnerability library and provide a quick display query function;
[0066] The vulnerability data storage display module 22 includes a key information extraction unit and a processing storage unit;
[0067] The key information extraction unit is used to extract effective key information from the captured ...
Embodiment 3
[0078] An embodiment of the present invention provides an automatic monitoring system for open source component vulnerabilities, including a vulnerability capture module 11, a vulnerability data storage and display module 22, a component detection and identification module 33, a processing module 44, and an early warning module 55;
[0079] The vulnerability capture module 11 is used to schedule crawlers to capture and search the latest data released by domestic and foreign vulnerability disclosure platforms;
[0080] The vulnerability data storage and display module 22 is used to record and update the captured data to the local open source component vulnerability library and provide a quick display query function;
[0081] The vulnerability data storage display module 22 includes a key information extraction unit and a processing storage unit;
[0082] The key information extraction unit is used to extract effective key information from the captured data; effective key inform...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com