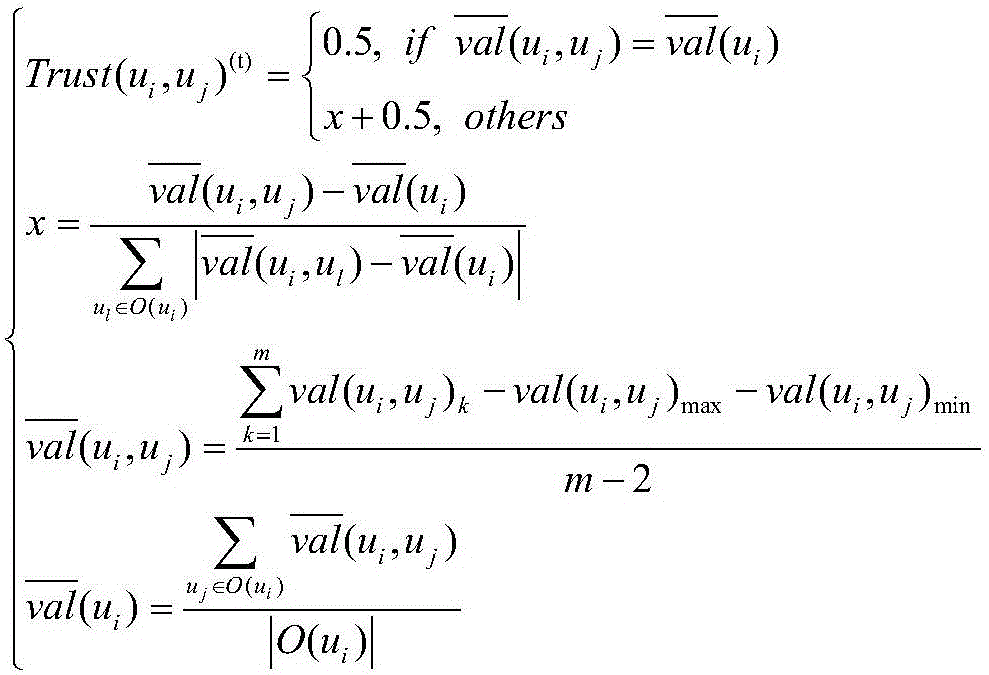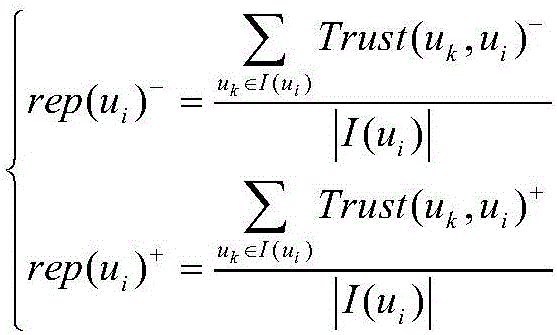Reputation system-oriented collusion attack fuzzy detection method in social network
A technology of social network and collusion attack, applied in the field of social network, can solve problems such as ignorance
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0069] The present invention will be described in detail below with reference to the drawings and specific embodiments. This embodiment is implemented on the premise of the technical solution of the present invention, and a detailed implementation mode and specific operation process are given, but the protection scope of the present invention is not limited to the following embodiments.
[0070] This application first defines social networks:
[0071] Definition 1
[0072] Social network: The social network is formalized as a bipartite graph, SG=, U={u 1 ,u 2 ,...} represents the set of users in the social network, E={e 1 ,e 2 ,...} A collection used to describe the relationship between users.
[0073] User u i It is called a node in the social network model, and the subscript i represents the i-th user; if two different users u i And user u j Between u i Reach u j The directed edge e(u i ,u j ), it indicates that there is a user u i To user u j Social relations, user u i Called the i...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com