Sensitive subgraph based on malicious android software re-packaging detection method
A technology of repackaging and subgraphs, applied in computer security devices, instruments, electrical digital data processing, etc., can solve problems such as time-consuming, high resource occupancy, and inability to guarantee coverage, so as to reduce false negatives and avoid interference. , The effect of improving the detection success rate
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0041] The implementation of the present invention will be described in detail below in conjunction with the drawings and examples.
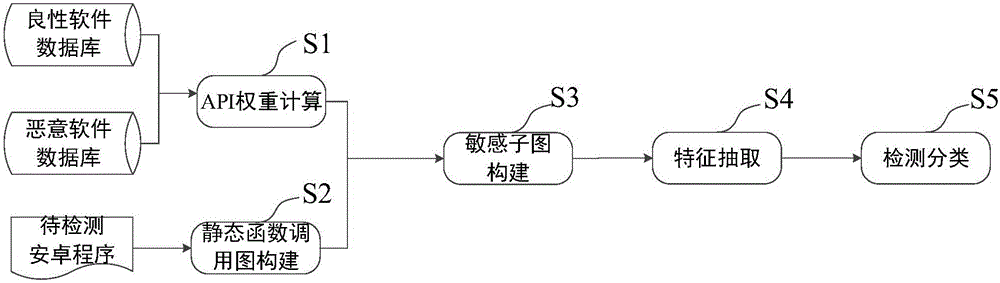
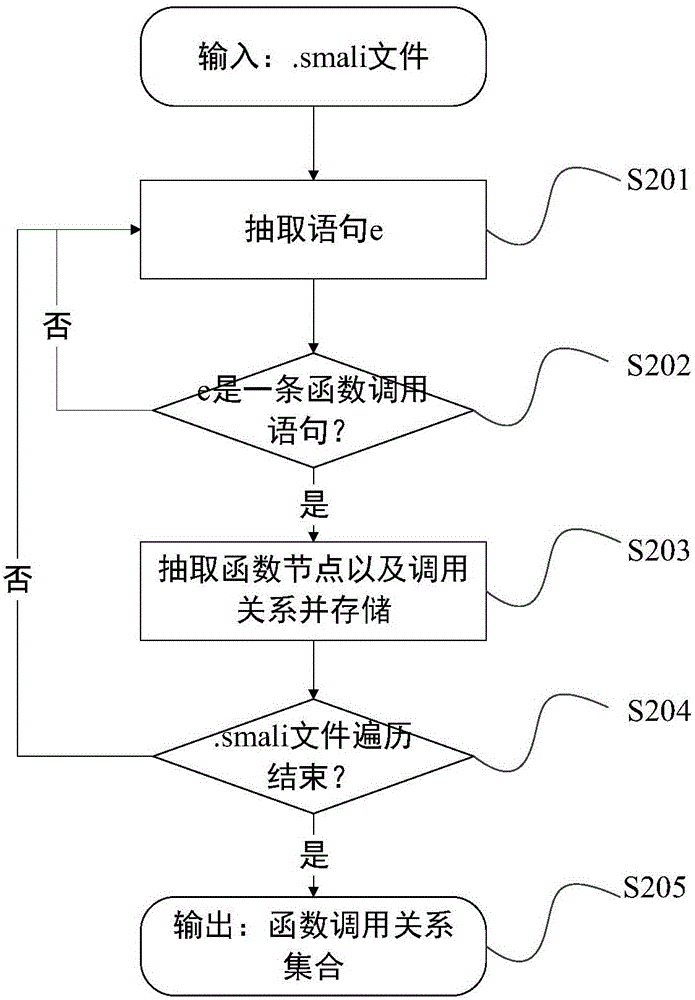
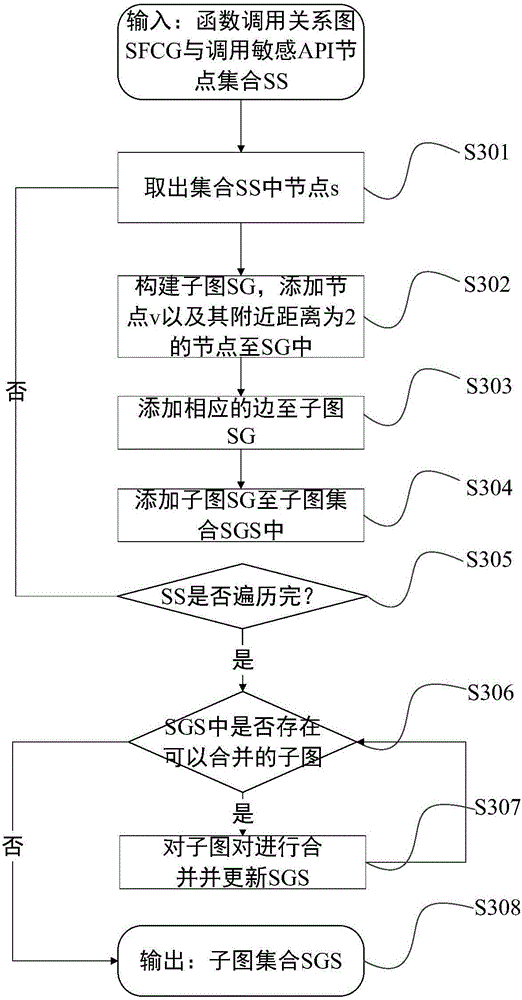
[0042] see figure 1 As shown, a kind of Android malicious repackaging program detection method based on sensitive subgraph analysis of the present invention comprises the following steps:
[0043] Step S1: Construct a sensitive function set SA={s based on the open source tool Pscout i |1≤i≤680}, where s i Indicates a sensitive function, and then obtains the category c of the Android program to be detected, such as the weather category. For sensitive functions s i , count the number of times it appears in the malicious data set M(s i ) and in the benign dataset B c The number of occurrences in b(s i , c). Calculate sensitive function s based on TF-IDF-like i With respect to the benign dataset B of category c c and the sensitivity coefficient scs(s of the malicious data set M i , c), the calculation formula is where p represents the to...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com