Software vulnerability discovery system and method based on attribute extraction
A software vulnerability and attribute extraction technology, applied in the field of computer security, can solve the problems of high requirements for analysts, difficult to find analysis points, and large test result sets.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0039] A non-limiting embodiment is given below in conjunction with the accompanying drawings to further illustrate the present invention. It should be understood, however, that these descriptions are exemplary only, and are not intended to limit the scope of the invention. Also, in the following description, descriptions of well-known structures and techniques are omitted to avoid unnecessarily obscuring the concept of the present invention.
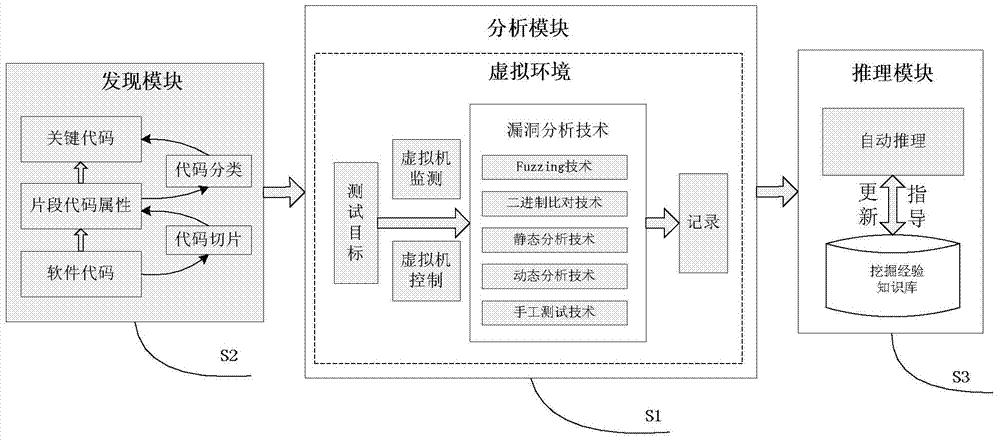
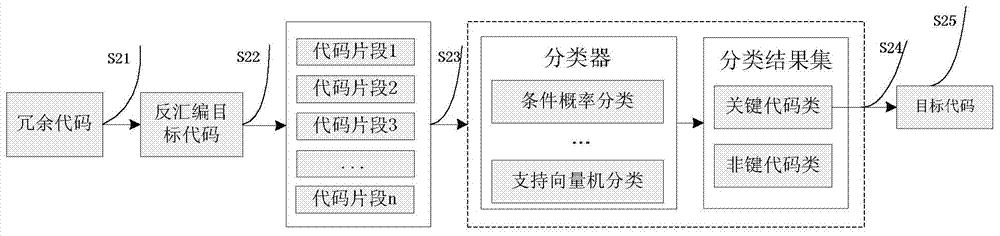
[0040] Such as figure 1 Shown is a schematic diagram of the implementation structure of the present invention, including a discovery module, an analysis module, and a reasoning module. Specifically illustrate the detailed implementation process of the present invention, comprise following 3 steps:
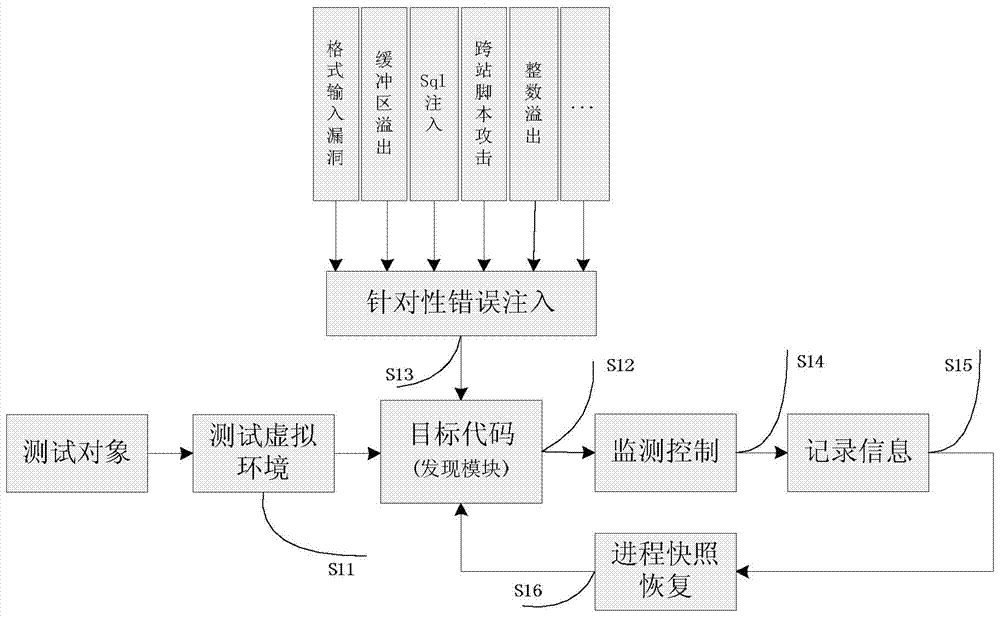
[0041] S1: The test object completes the test analysis in the virtualized test environment, and combines multiple vulnerability analysis techniques for parallel analysis. The behavior of the test object is monitored by the virtual machine...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com