Method for SQL injection vulnerability discovery based on simulated attack extension
A technology for simulating attacks and exploiting vulnerabilities, applied in electrical components, transmission systems, etc., can solve problems such as insecure web sites, insecure web server programs, and web application programs that contain vulnerabilities, achieving high detection rates, Good stability, to achieve the effect of coverage
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
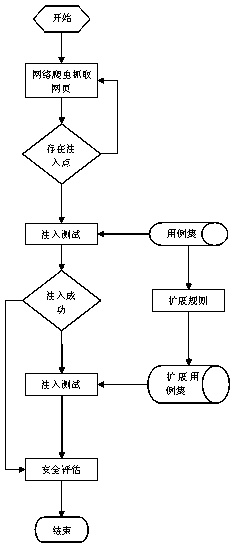
[0019] The invention provides a more comprehensive solution for scanning vulnerabilities of server codes based on simulation attack extension. This scheme maintains an initial simulated attack case set during the SQL injection vulnerability scanning process, each element in the set is a SQL injection attack case, and the set can contain a SQL injection subset and the injection use cases in the subset. When performing a vulnerability scan on a webpage with an injection point, the injection test is performed based on the injection point traversal simulation attack case set of the webpage. If the injection is successful, it means that the server has a SQL injection vulnerability and no security verification mechanism is deployed. If the injection fails, the The automatic expansion rules expand the original simulated attack cases, and then perform injection tests. If the injection of the extended use cases is successful, it means that there are vulnerabilities in the server, and th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com