Method for detecting WEB service abnormality
A web service and anomaly detection technology, applied in the field of network security, can solve problems such as lag
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0020] At first, explain the thought of the present invention:
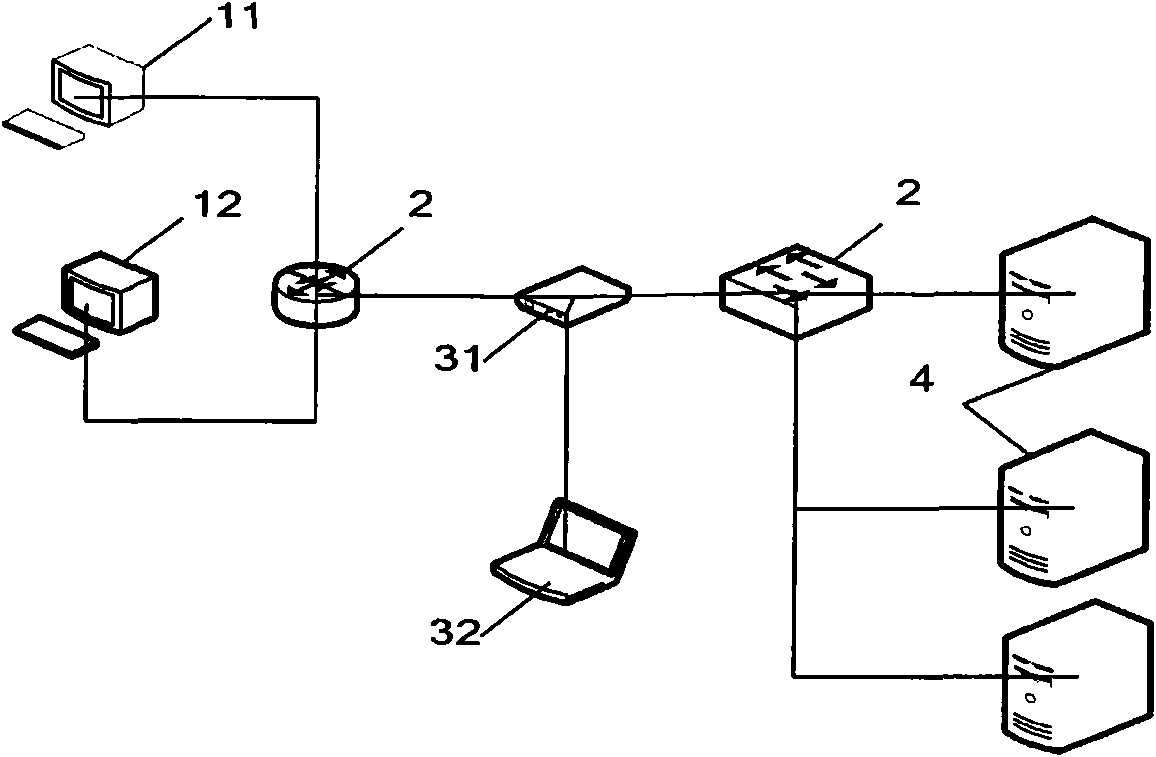
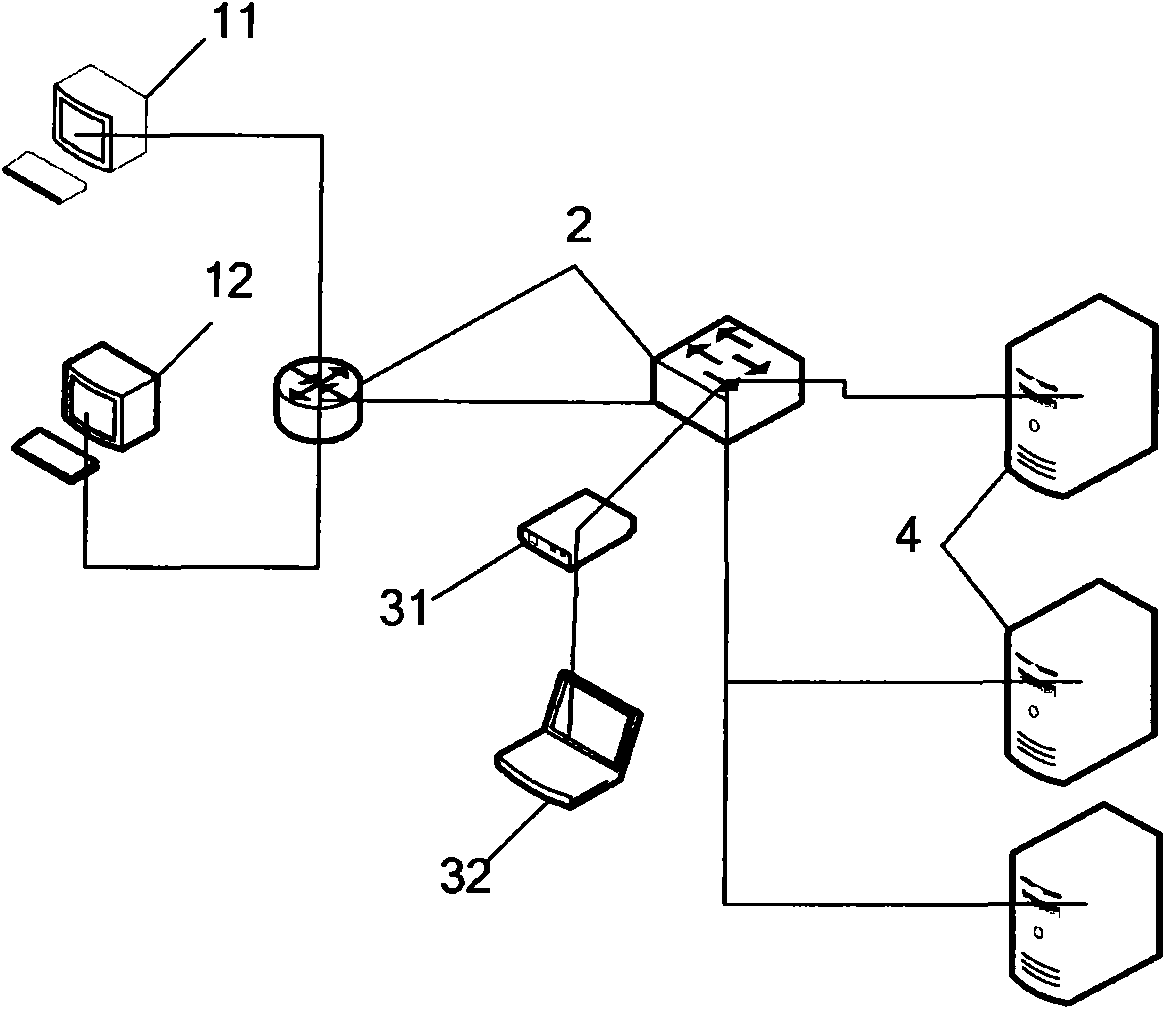
[0021] Through the analysis and research of the TCP / IP and HTTP protocol communication messages between the client and the Web server in various states, the normal state of the Web server, the abnormal state of the attack, and the communication report are established. By analyzing the behavior patterns of network communication packets, we can discover the status changes of the Web server, thereby detecting unknown denial-of-service attacks. The request data part is extracted and recorded, so that the attack detection device using the transparent series access mode can further detect and block the same attack in the future; the attack detection device using the bypass mode can promptly report to the police when the attack occurs and log and provide attack signatures to administrators.
[0022] Second step, explain basic principle of the present invention:
[0023] Correspondence Model between Web Server State an...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com