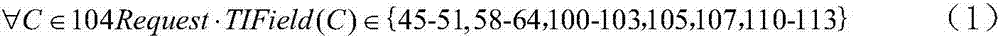IEC60870-5-104 Protocol-based SCADA (supervisory control and data acquisition) network intrusion detection method and system
A network intrusion detection and intrusion detection technology, which is applied in transmission systems, digital transmission systems, data exchange networks, etc., can solve the problems of SCADA systems lacking network security intrusion detection systems, lack of security considerations, failures, etc., to improve network security Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0040] The technical solution of the present invention will be further introduced below in conjunction with the accompanying drawings and specific implementation methods.
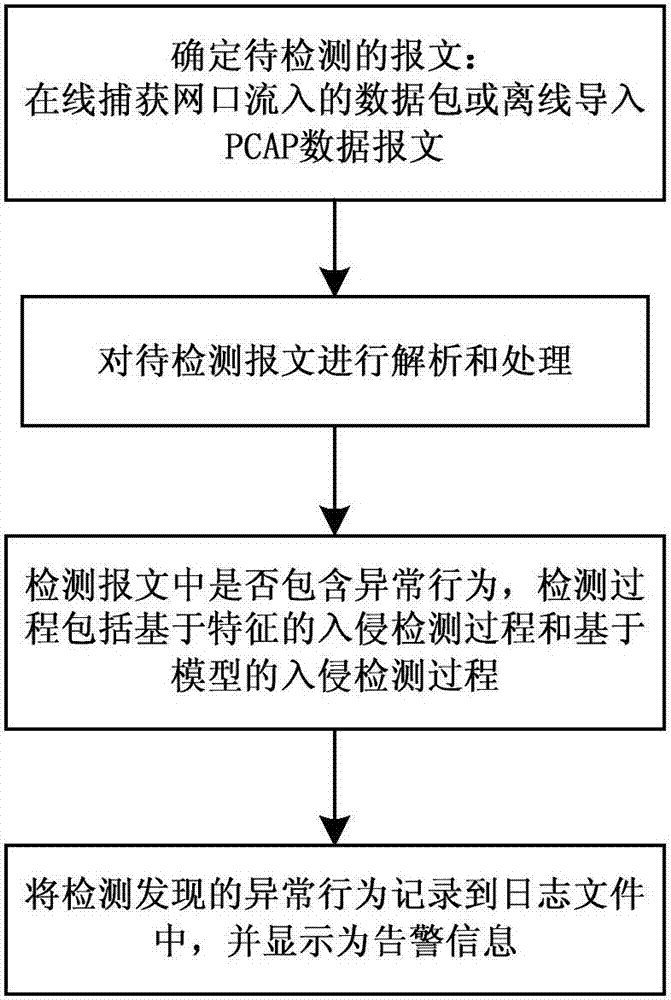
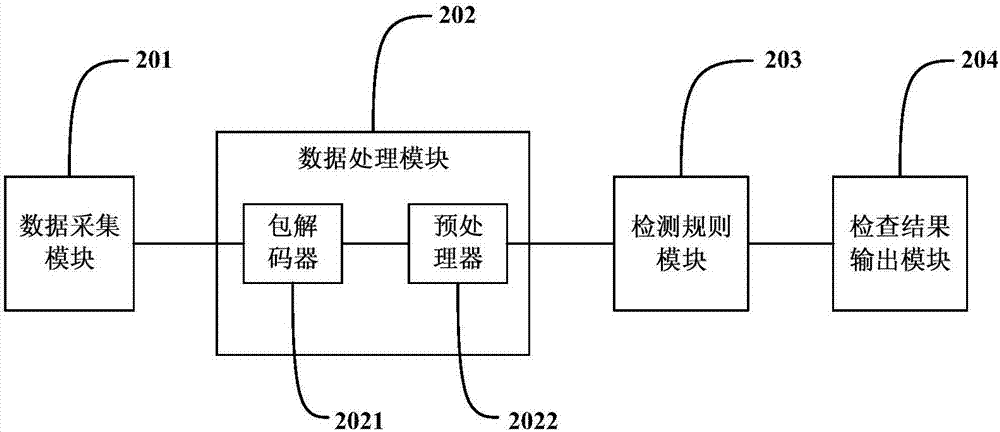
[0041] This specific embodiment discloses a kind of SCADA network intrusion detection method based on IEC60870-5-104 agreement, such as figure 1 As shown, the method includes the following steps:
[0042] Determine the message to be detected;
[0043] Detect whether there are abnormal behaviors in the message. The detection process includes a feature-based intrusion detection process and a model-based intrusion detection process. The feature-based intrusion detection process is: match the message to be detected with the rule database of attack characteristics , if they match, a corresponding alarm will be generated; the model-based intrusion detection process is: to establish a model that characterizes the expected behavior of a specific protocol, and if the detected message violates these models, a corres...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com