Network worm detection and characteristic automatic extraction method and system
A worm and network technology, applied in the field of network security, can solve problems such as loss of effectiveness, and achieve the effect of preventing the spread of worms and preventing large-scale economic losses
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0036] Concrete implementation method of the present invention is:
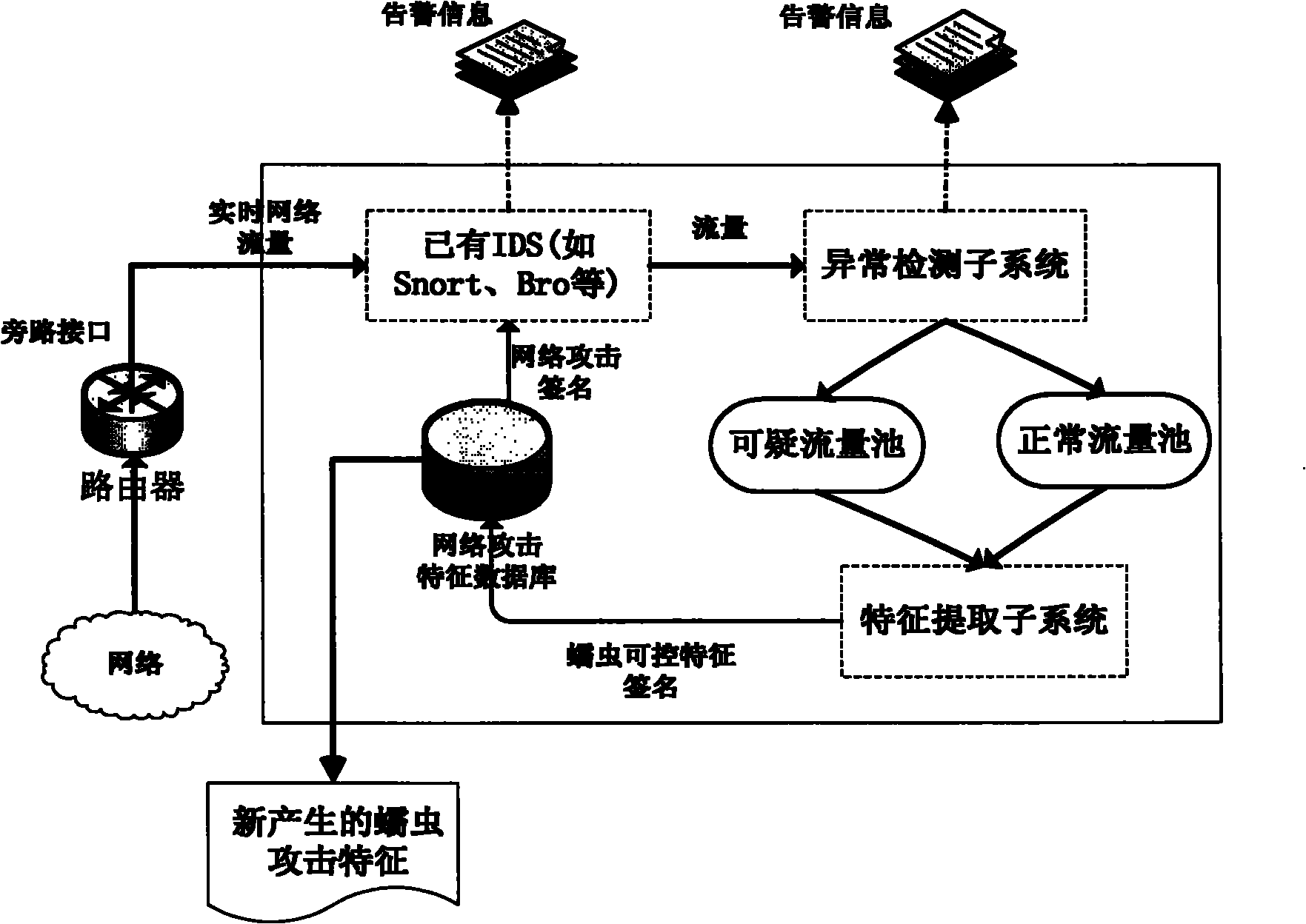
[0037] Step 1: Capture network packets at the gateway by way of bypass listening.
[0038] Step 2: The data packets pass through the existing IDS, and are matched against the network attack signature database to detect known worm attacks.
[0039] Step 3: The anomaly detection subsystem will analyze and detect the captured data packets. The anomaly detection is divided into two stages: threshold training and online detection.
[0040] (I) Threshold training stage
[0041] Four anomaly detection strategies are performed on the traffic to calculate the thresholds of the four parameters of the number of initiated connections, the number of failed connections, divergence and packet similarity. During the training phase, normal network traffic captured by the system was used.
[0042] Below we will introduce the calculation methods of the observed values of these four parameters one by one.
[0043] (I-1) Appl...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com