A blacklist real time management method and device
A blacklist and management module technology, applied in the field of data communication, can solve the problems of low real-time performance and reduced communication system security, and achieve the effects of high real-time performance, reduced communication complexity, and stable performance
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0032] The technical solutions of the present invention will be further described in more detail in conjunction with the accompanying drawings and specific embodiments.
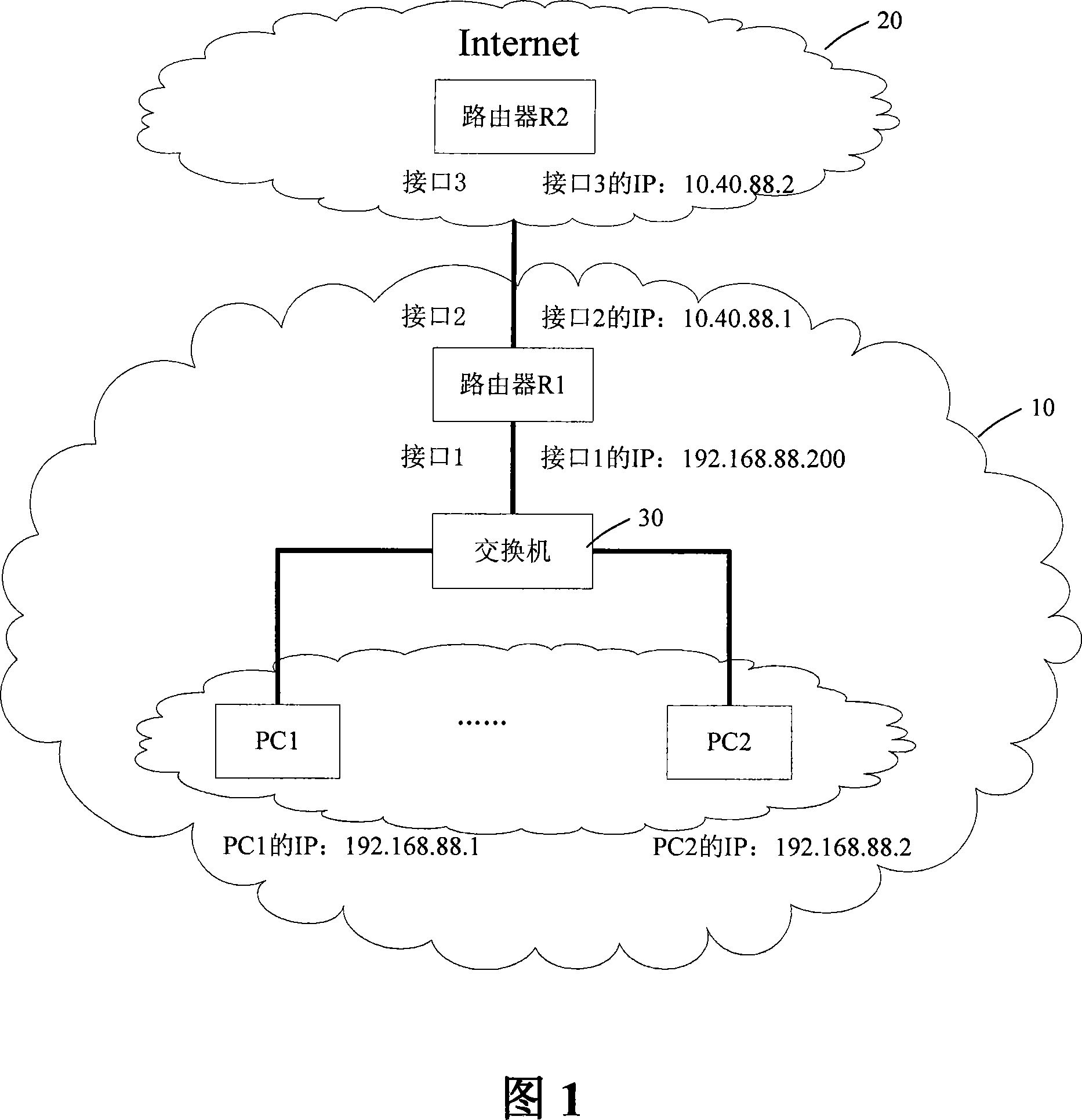
[0033] As shown in Figure 1, it is a schematic diagram of a network where intranet users access the Internet through a router with a firewall function. The hardware part in the networking relationship in the figure includes more than one host, a hub or switch, a router with firewall function, more than one ordinary router, 100 / 1000M interface boards and several twisted-pair cables. Wait.
[0034] In FIG. 1 , the intranet 10 includes but not limited to the following devices: host PC1, PC2, switch 30 and router R1 with firewall function.
[0035] The hosts PC1 and PC2 are connected to the interface 1 of the router R1 through the switch 30, and are connected to the external network 20 from the interface 2 of the router R1. The external network 20 is an external network, which may be the Internet.
[0036] The ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com