Patents
Literature
65 results about "Interdiction" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Interdiction is a military term for the act of delaying, disrupting, or destroying enemy forces or supplies en route to the battle area. A distinction is often made between strategic and tactical interdiction. The former refers to operations whose effects are broad and long-term; tactical operations are designed to affect events rapidly and in a localized area.
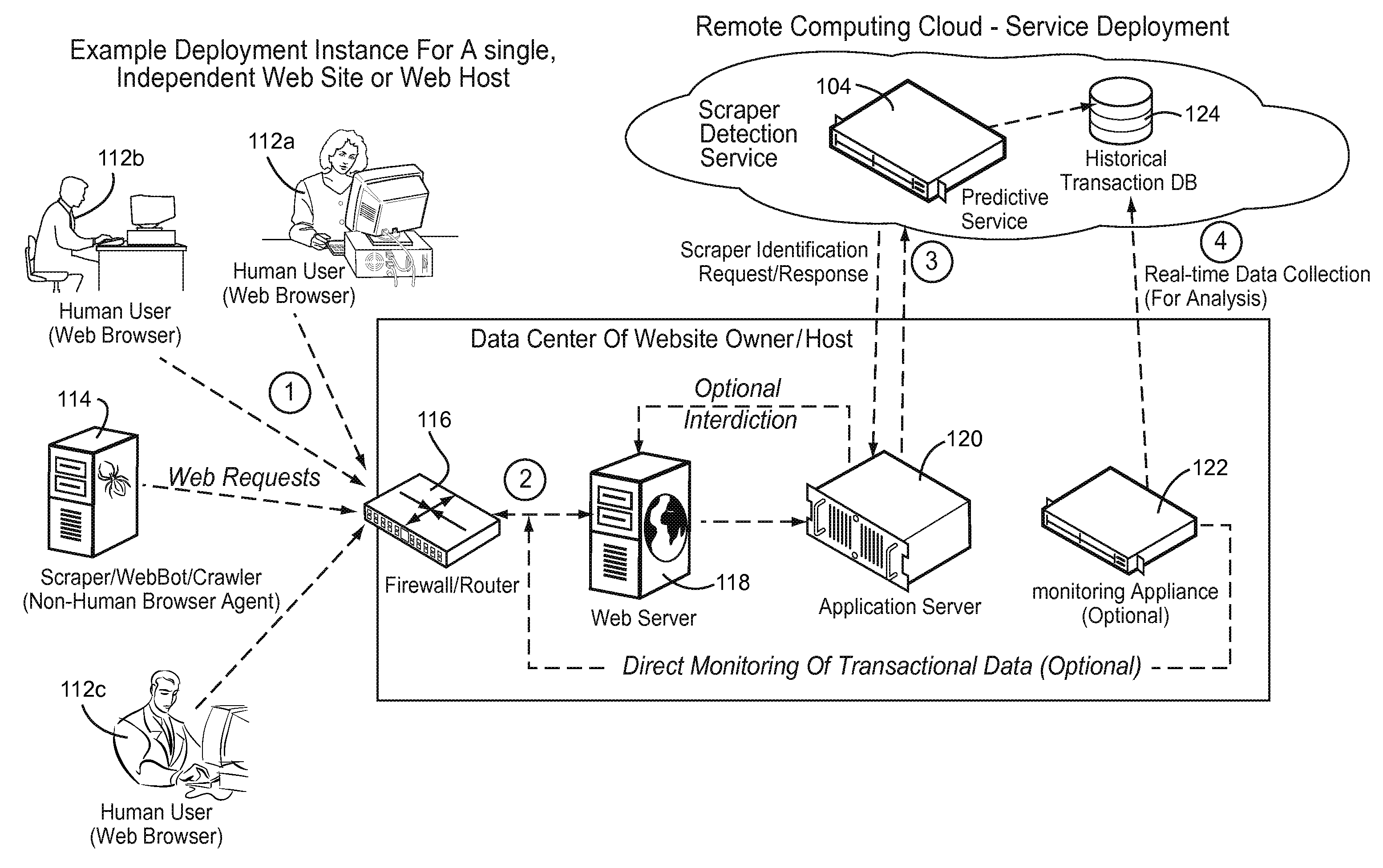
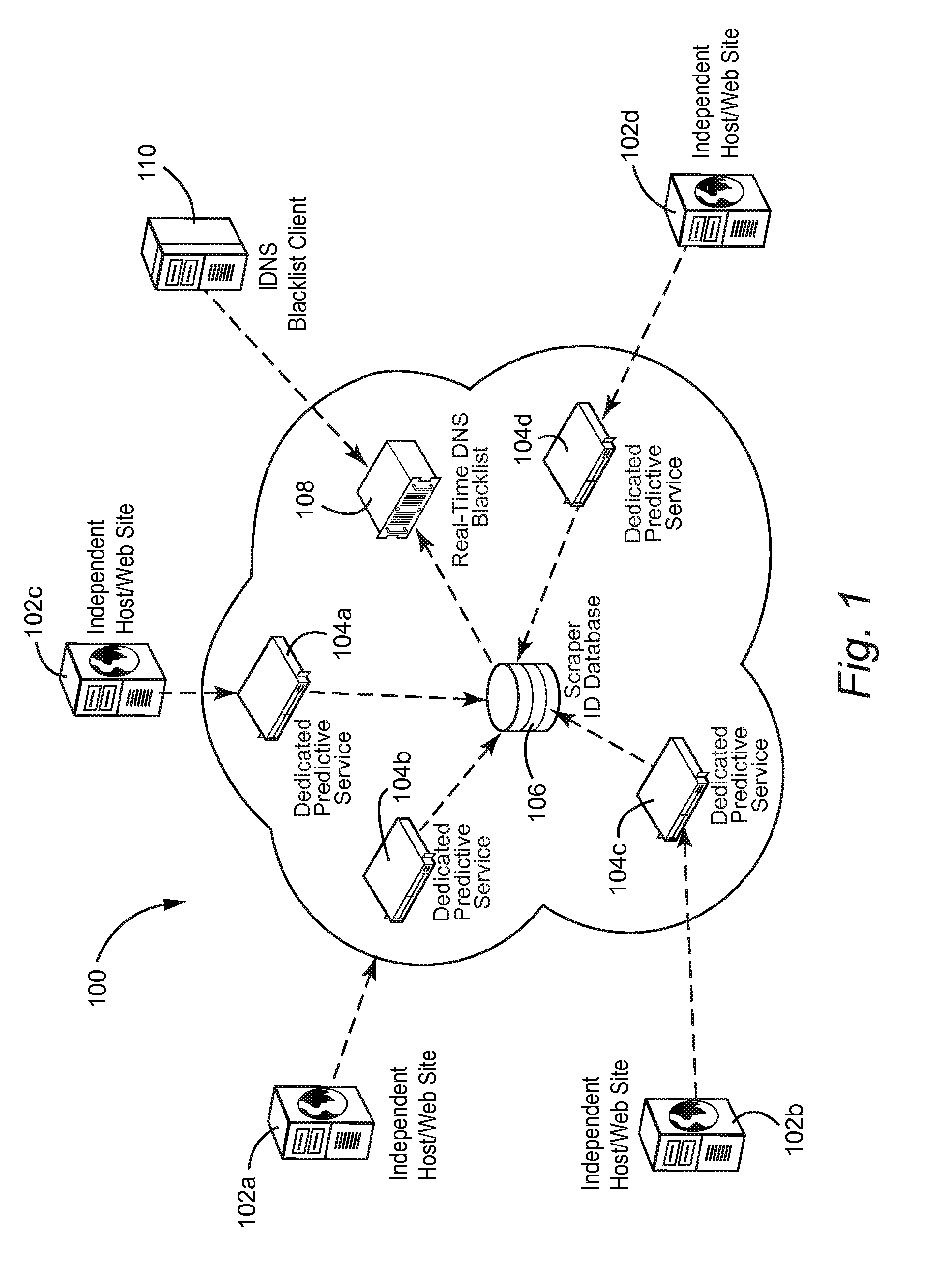
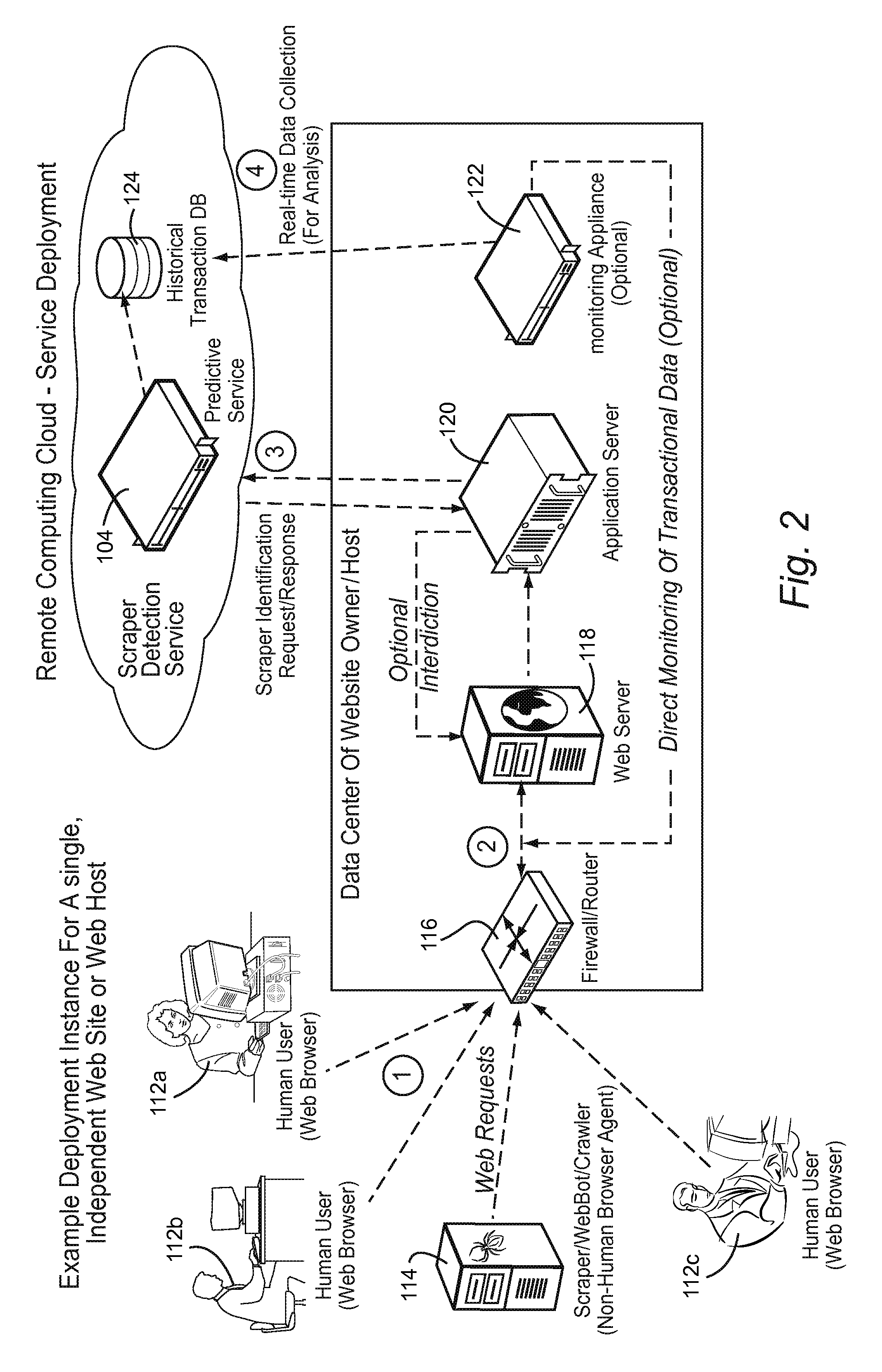
Trained predictive services to interdict undesired website accesses
Webcrawlers and scraper bots are detrimental because they place a significant processing burden on web servers, corrupt traffic metrics, use excessive bandwidth, excessively load web servers, create spam, cause ad click fraud, encourage unauthorized linking, deprive the original collector / poster of the information of exclusive rights to analysis and summarize information posted on their own site, and enable anyone to create low-cost Internet advertising network products for ultimate sellers. A scaleable predictive service distributed in the cloud can be used to detect scraper activity in real time and take appropriate interdictive access up to and including denial of service based on the likelihood that non-human agents are responsible for accesses. Information gathered from a number of servers can be aggregated to provide real time interdiction protecting a number of disparate servers in a network.
Owner:AUTOTRADER COM
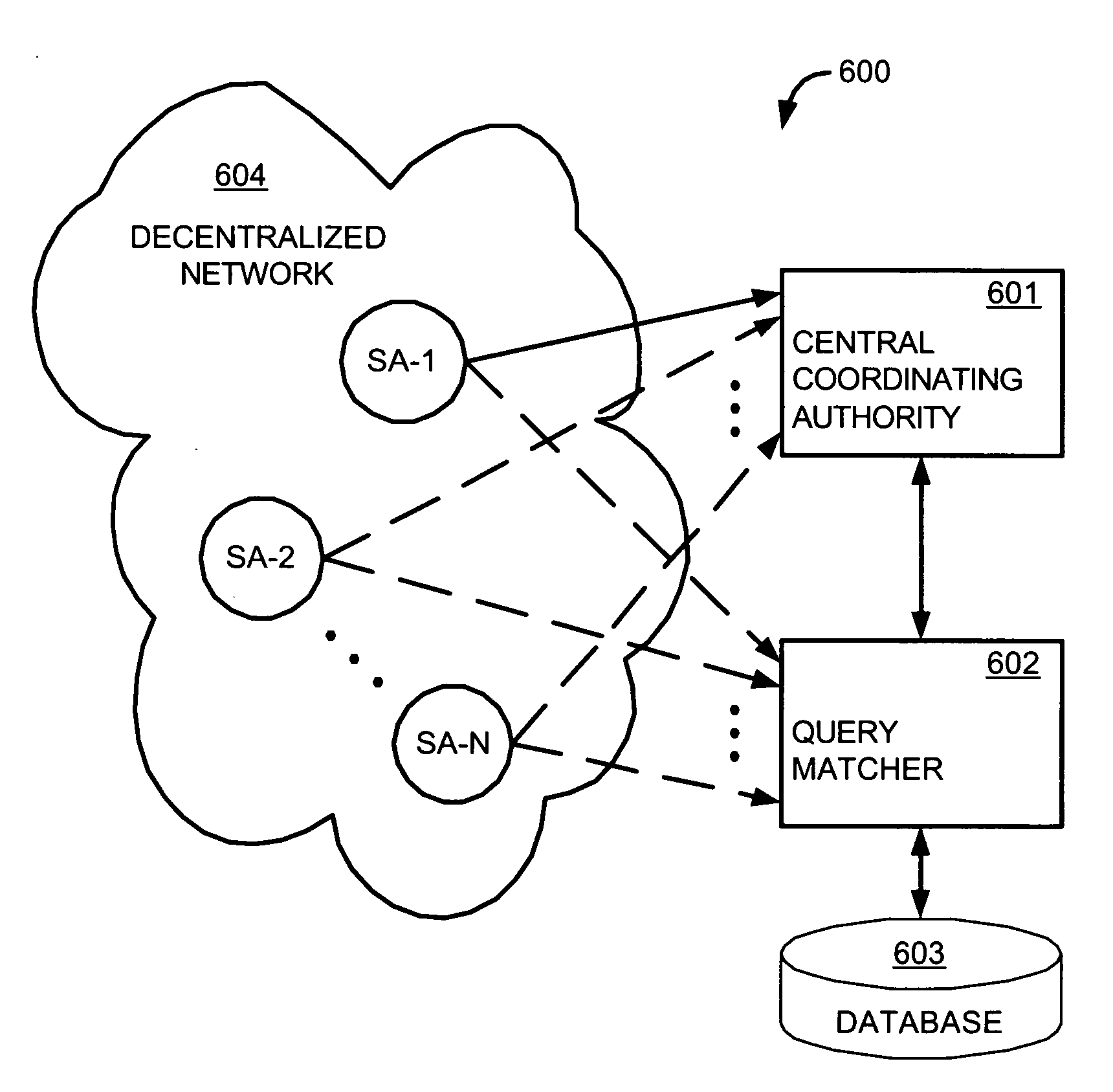
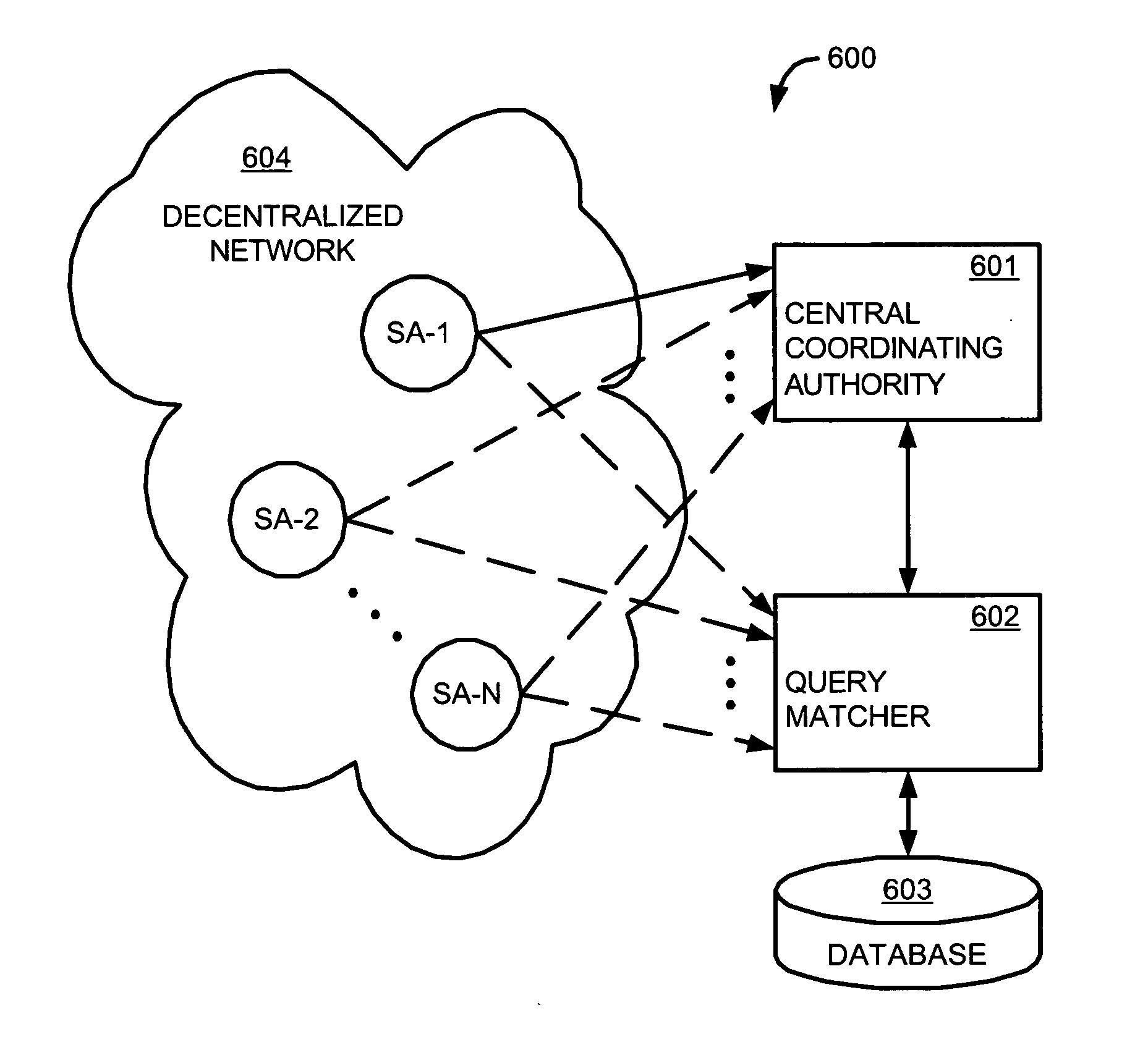
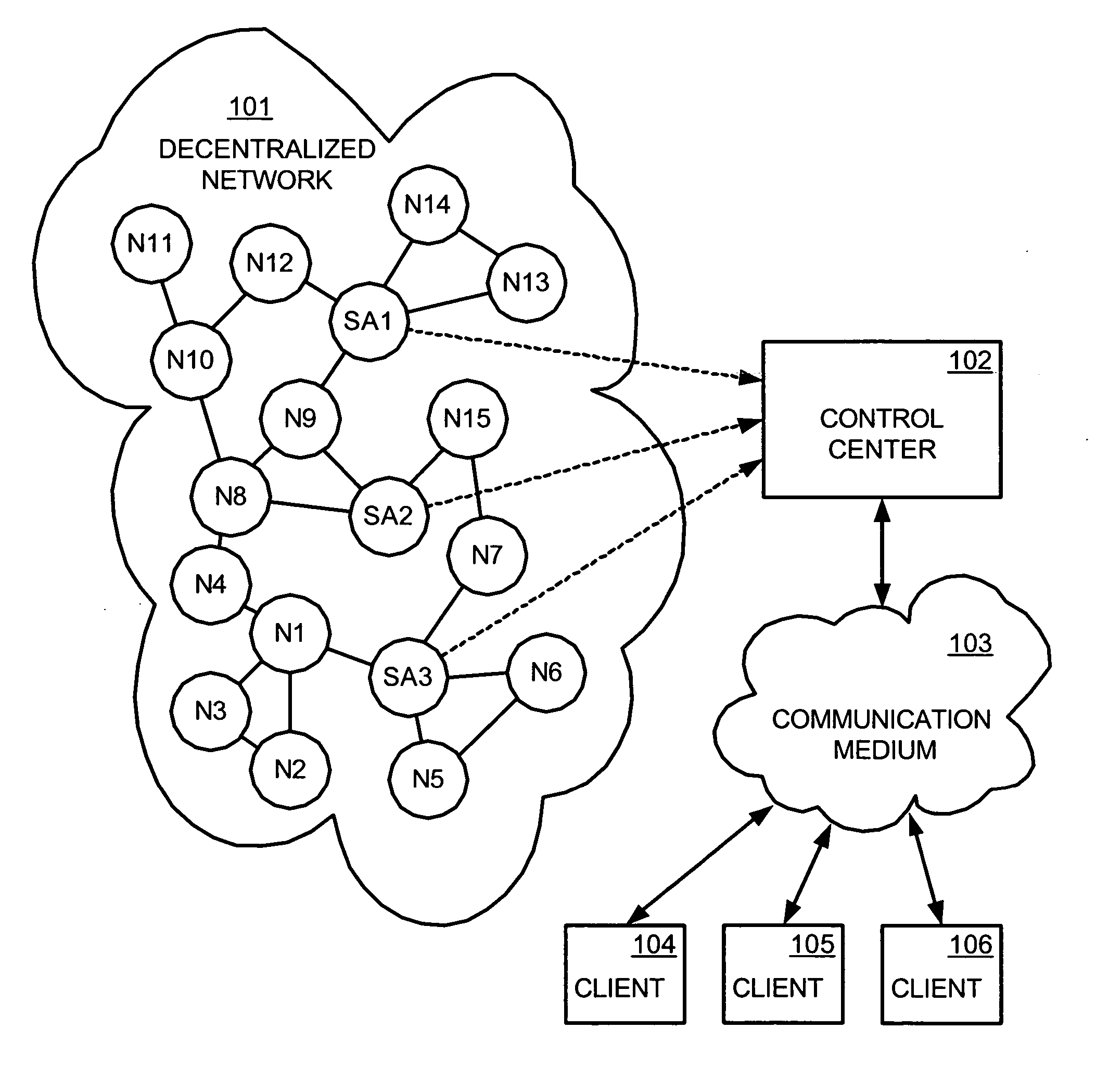
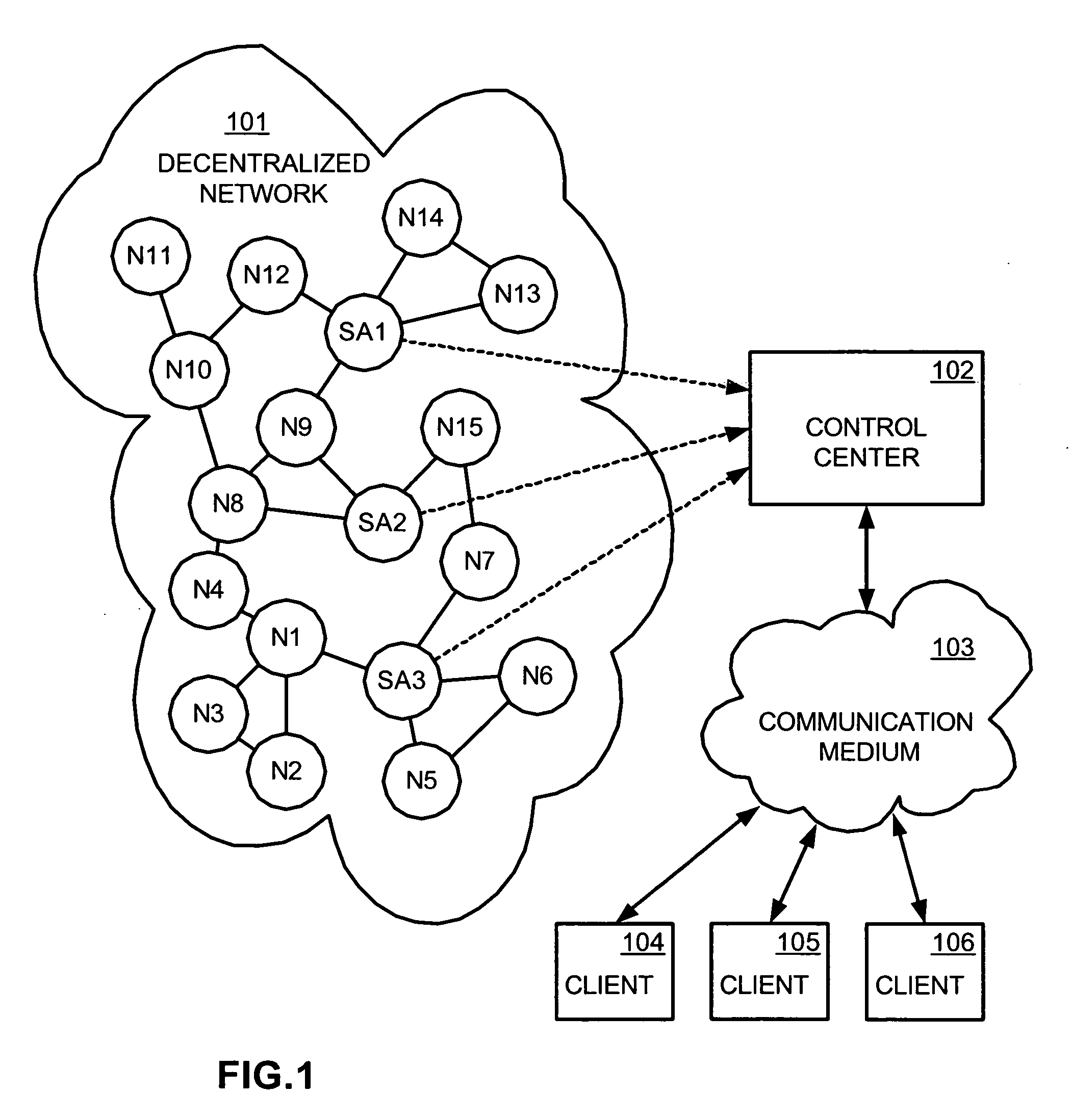
Interdiction of unauthorized copying in a decentralized network
An interdiction system includes software agents masquerading as nodes in a decentralized network, a query matcher that receives search results captured by the software agents and reports matches with protected files back to the software agents, and a central coordinating authority that coordinates activities of the software agents by sending instructions to the software agents specifying actions to be taken. Possible activities and related interdicting methods include manipulating search results before forwarding them on in the network, quarantining selected nodes in the network, performing file impersonations such as transferring synthesized decoys, performing file transfer attenuation, and hash spoofing.
Owner:MACROVISION CORP
Deterent for unmanned aerial systems
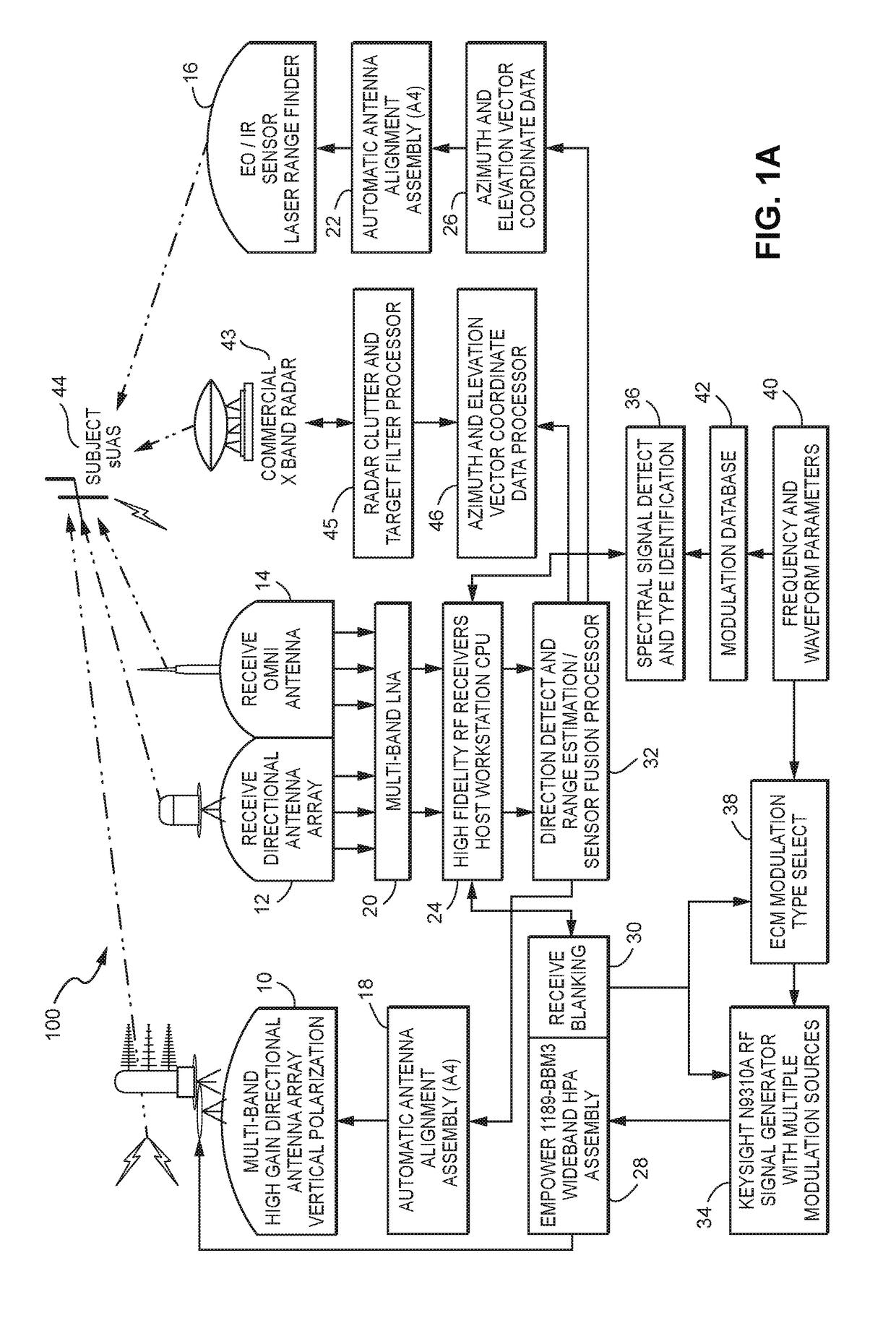
ActiveUS20170192089A1Defence devicesDirection/deviation determining electromagnetic systemsNon destructiveAutomated algorithm
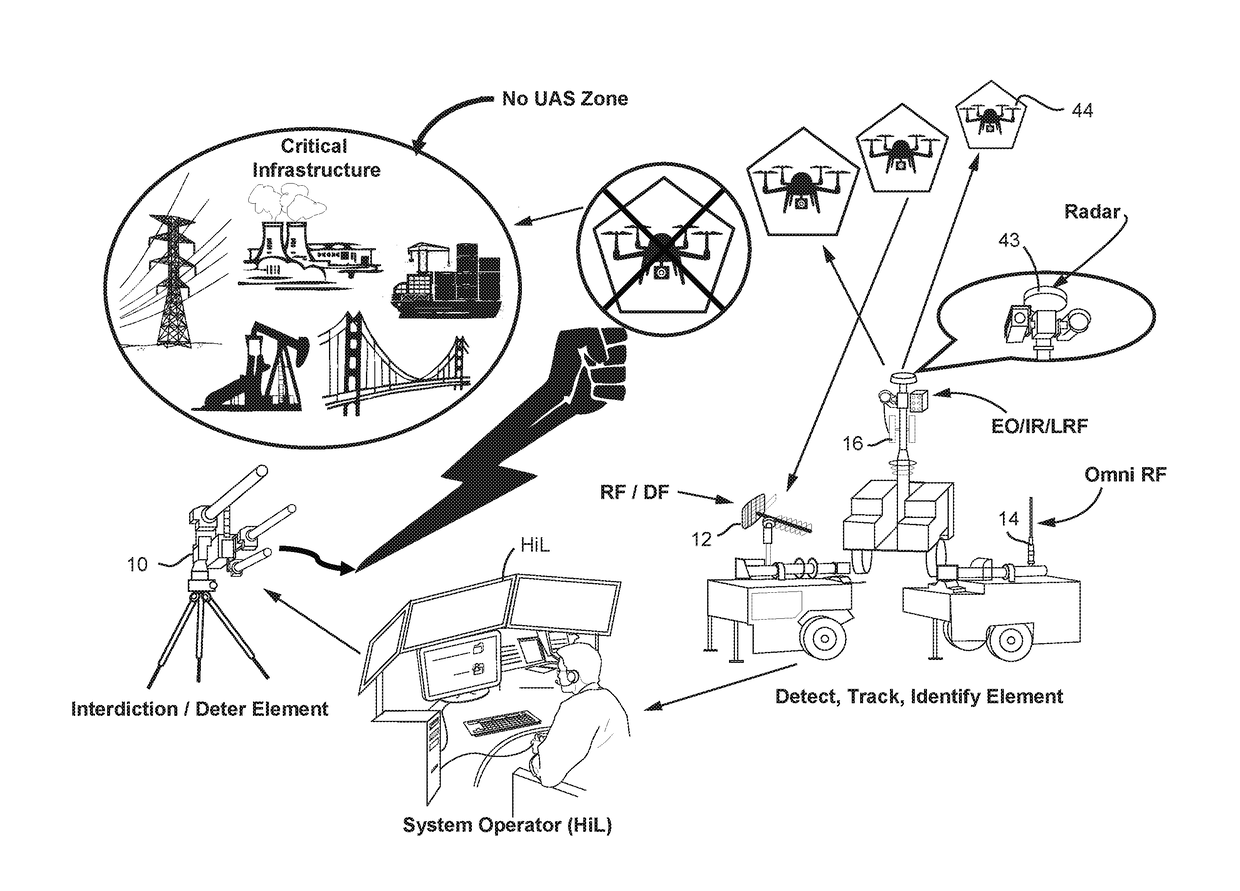
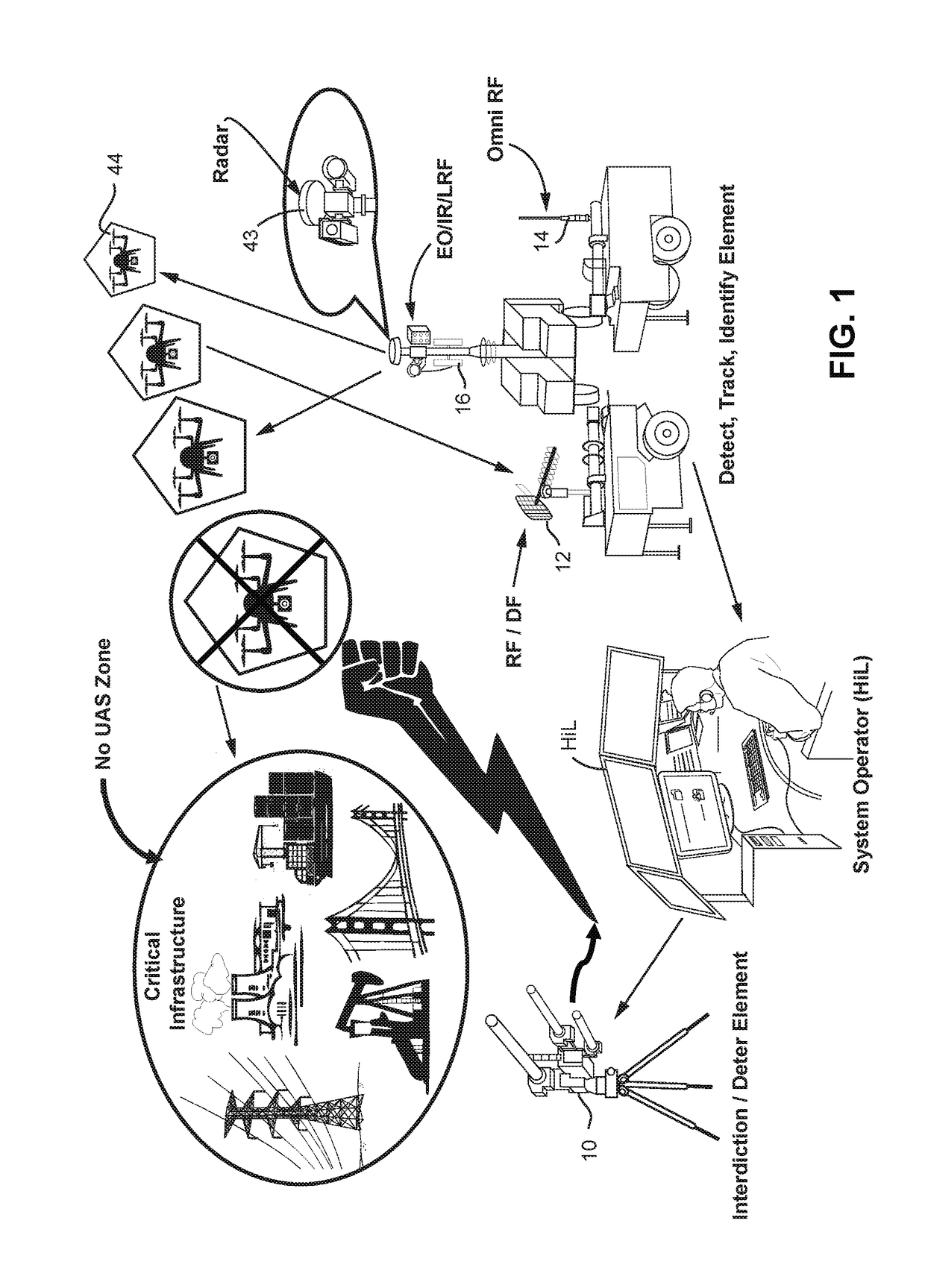
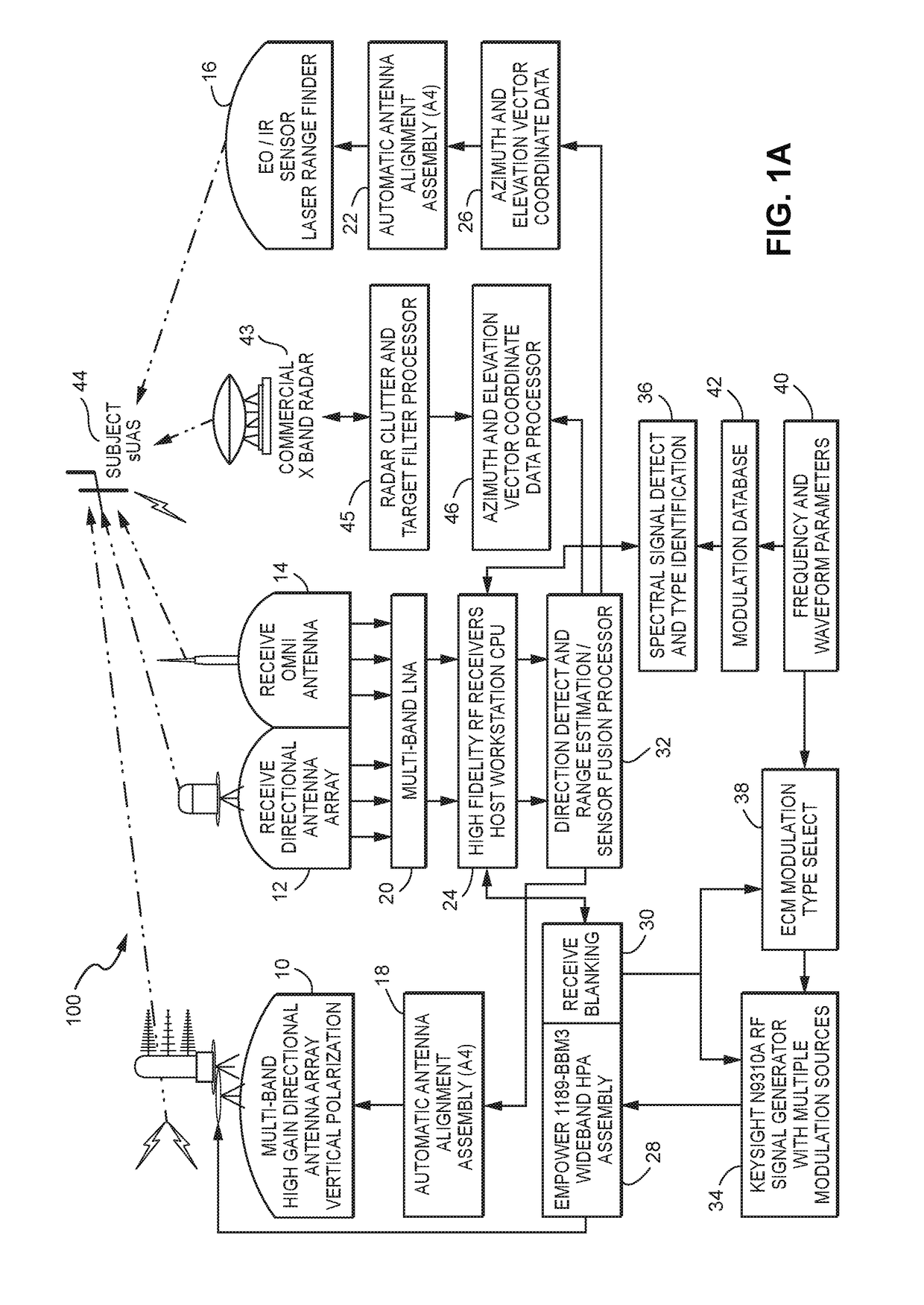
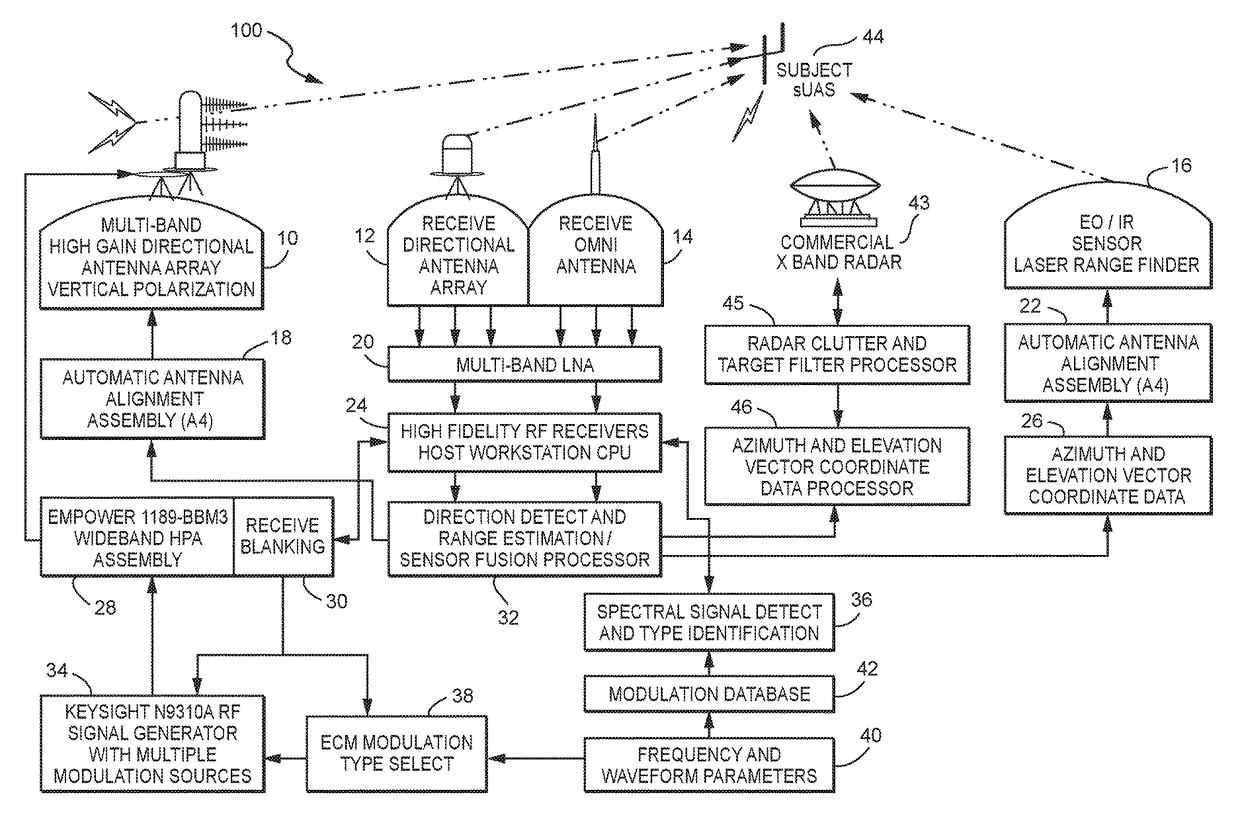
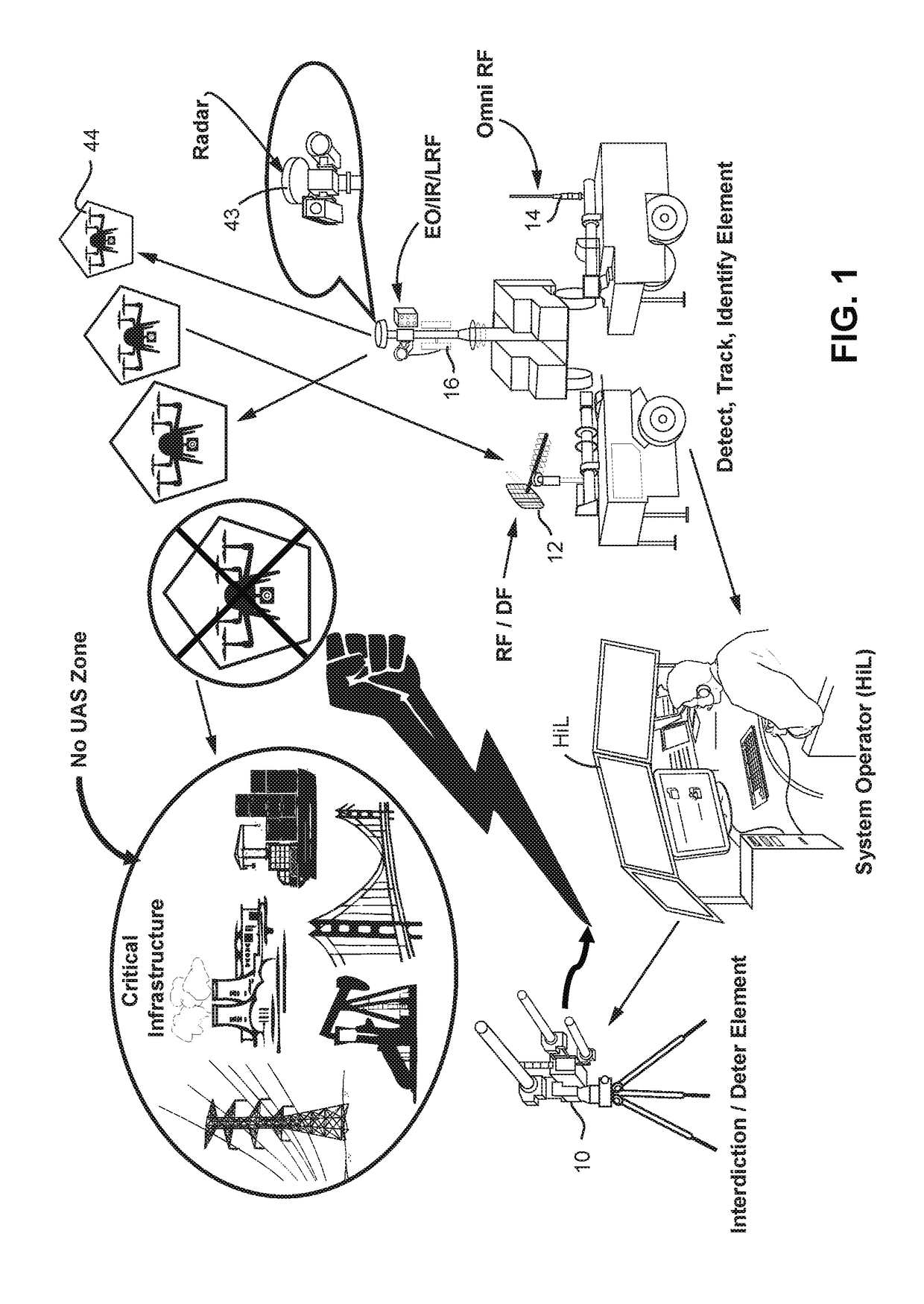
A system (100) for providing an integrated multi-sensor detection and countermeasure against commercial unmanned aerial systems / vehicles (44) and includes a detecting element (103, 104, 105), a tracking element (103,104, 105) an identification element (103, 104, 105) and an interdiction element (102). The detecting element detects an unmanned aerial vehicle in flight in the region of, or approaching, a property, place, event or very important person. The tracking element determines the exact location of the unmanned aerial vehicle. The identification / classification element utilizing data from the other elements generates the identification and threat assessment of the UAS. The interdiction element, based on automated algorithms can either direct the unmanned aerial vehicle away from the property, place, event or very important person in a non-destructive manner, or can disable the unmanned aerial vehicle in a destructive manner. The interdiction process may be over ridden by intervention by a System Operator / HiL.
Owner:XIDRONE SYST INC
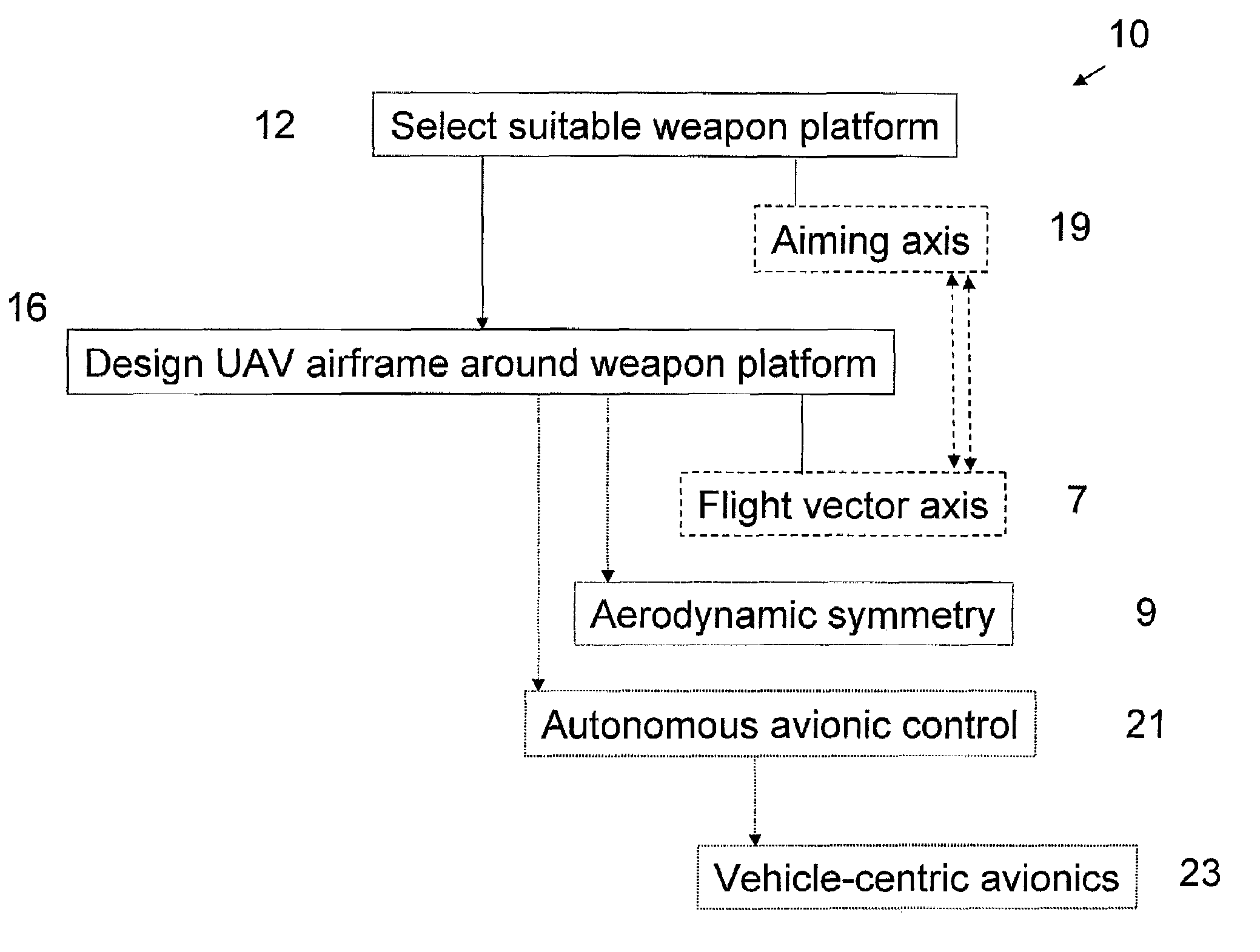
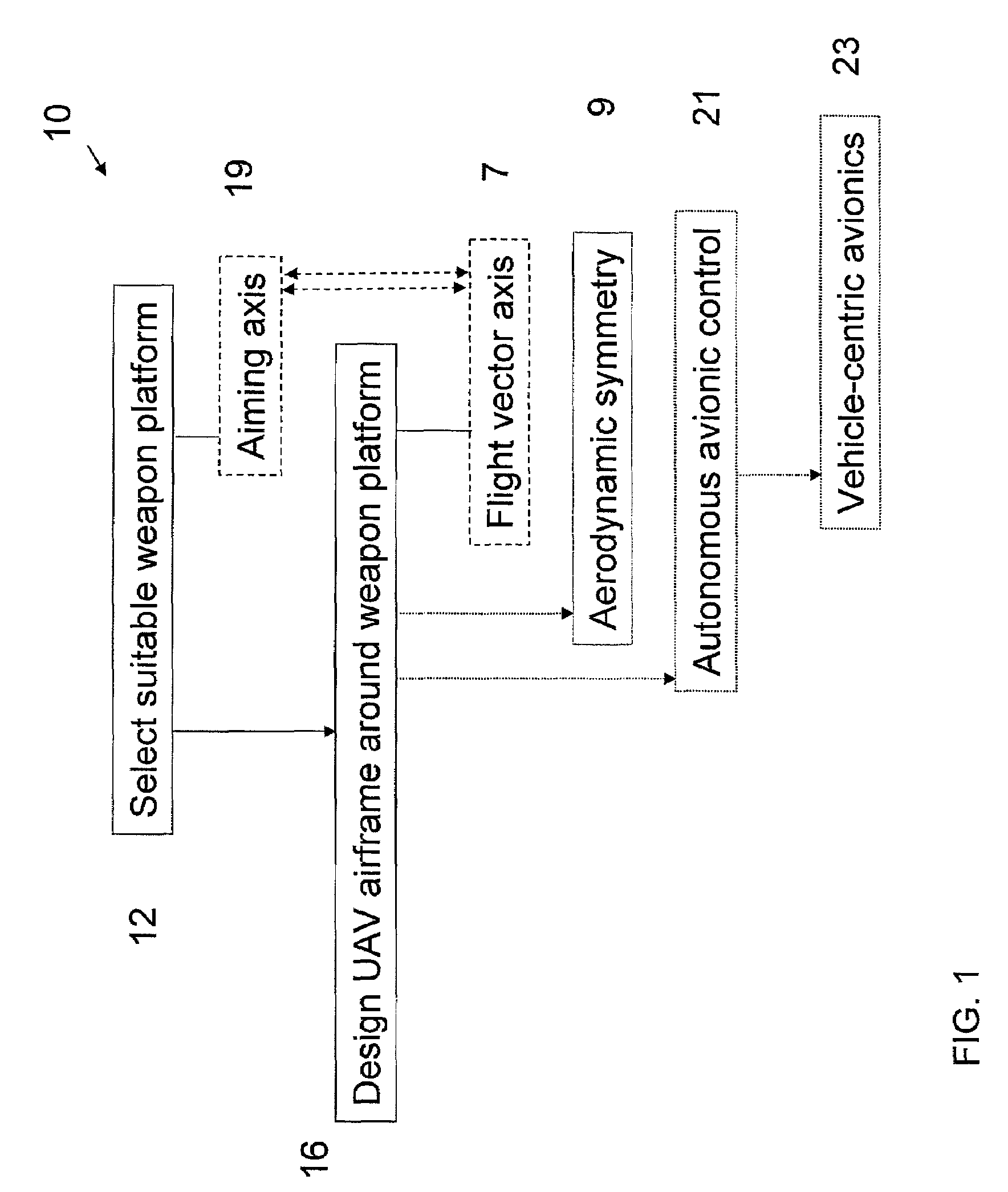
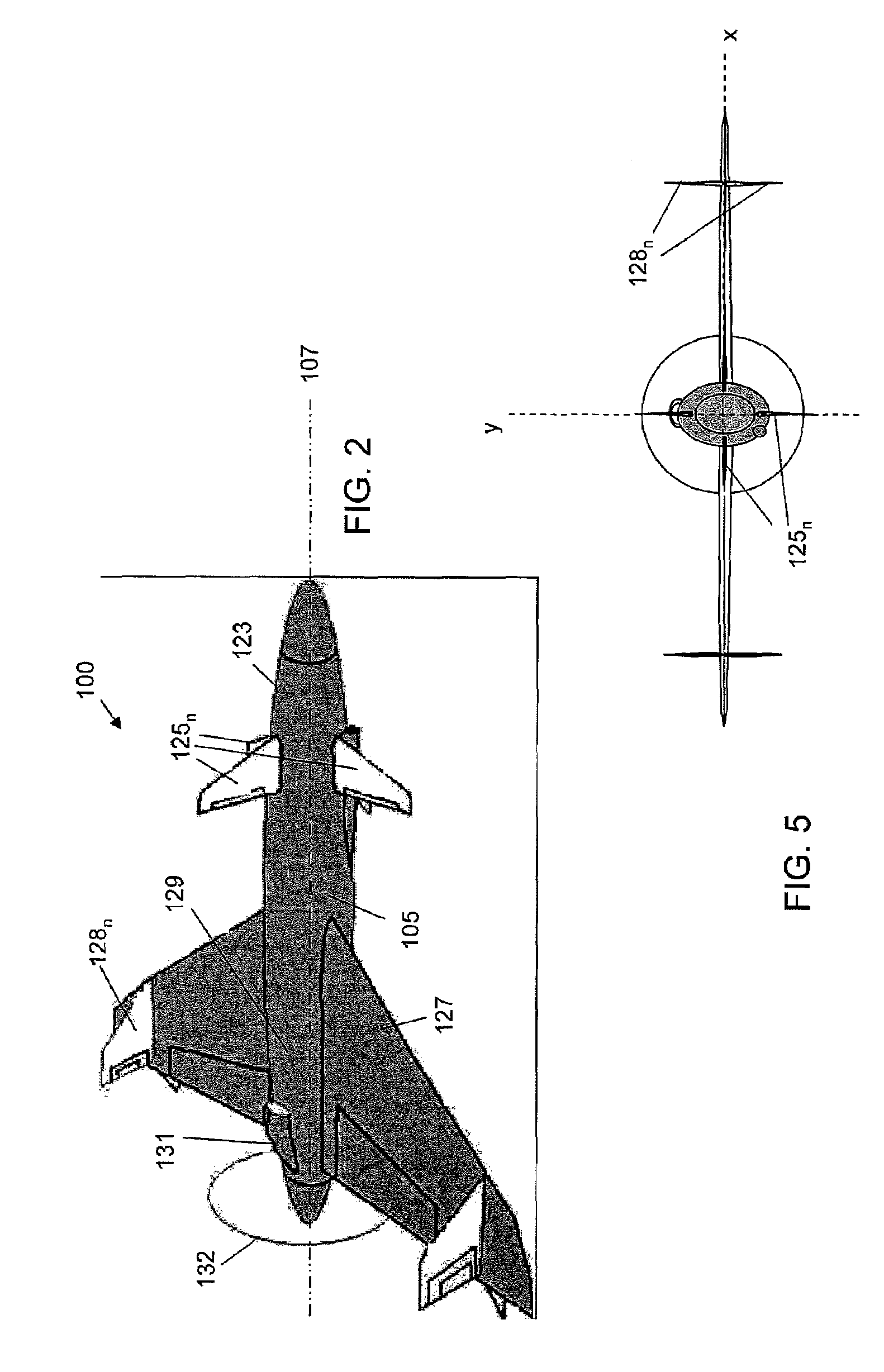
Unmanned air vehicle, integrated weapon platform, avionics system and control method
InactiveUS20070023582A1Forgiving of small errorMaximize probabilityUnmanned aerial vehiclesDigital data processing detailsAviationControl system
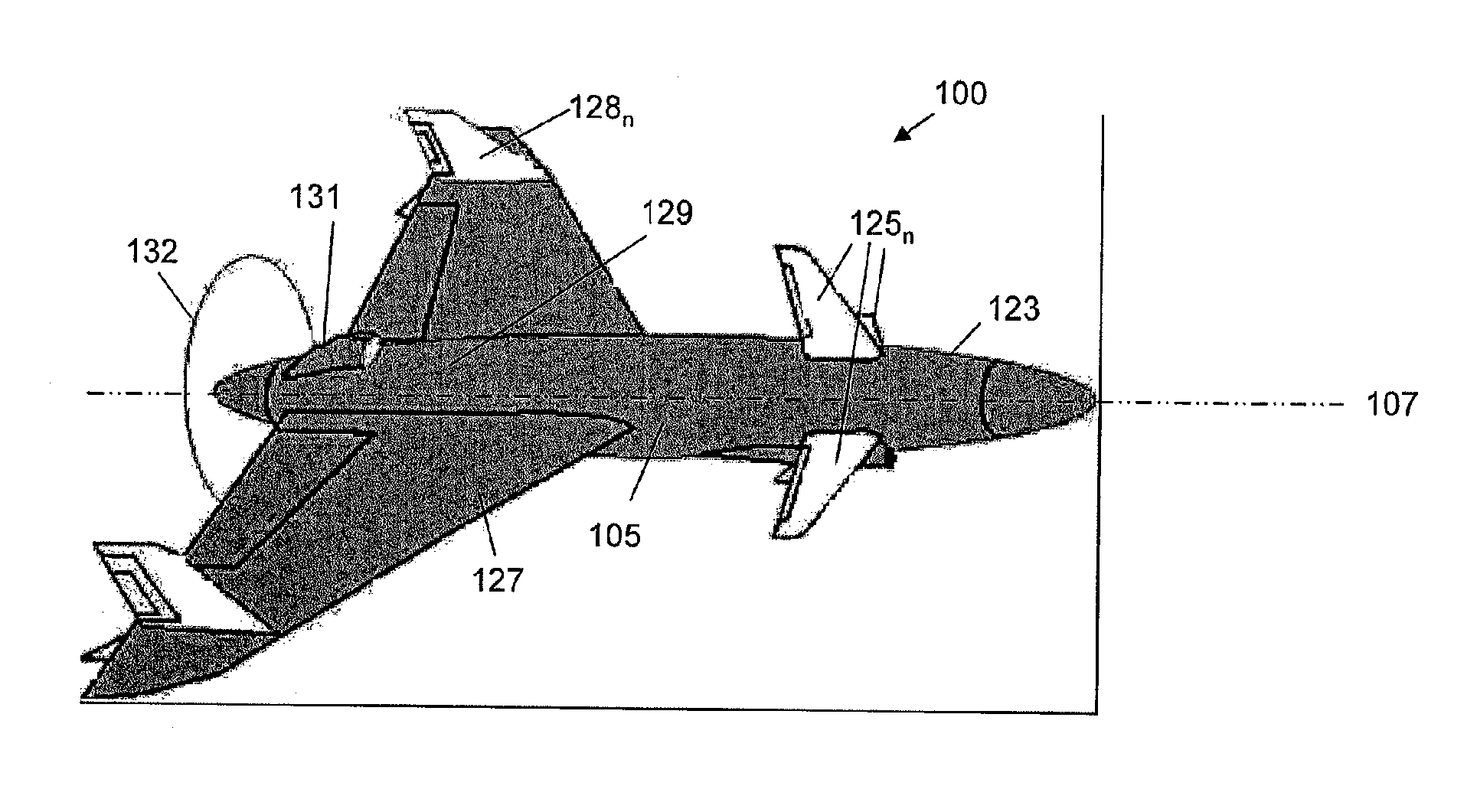
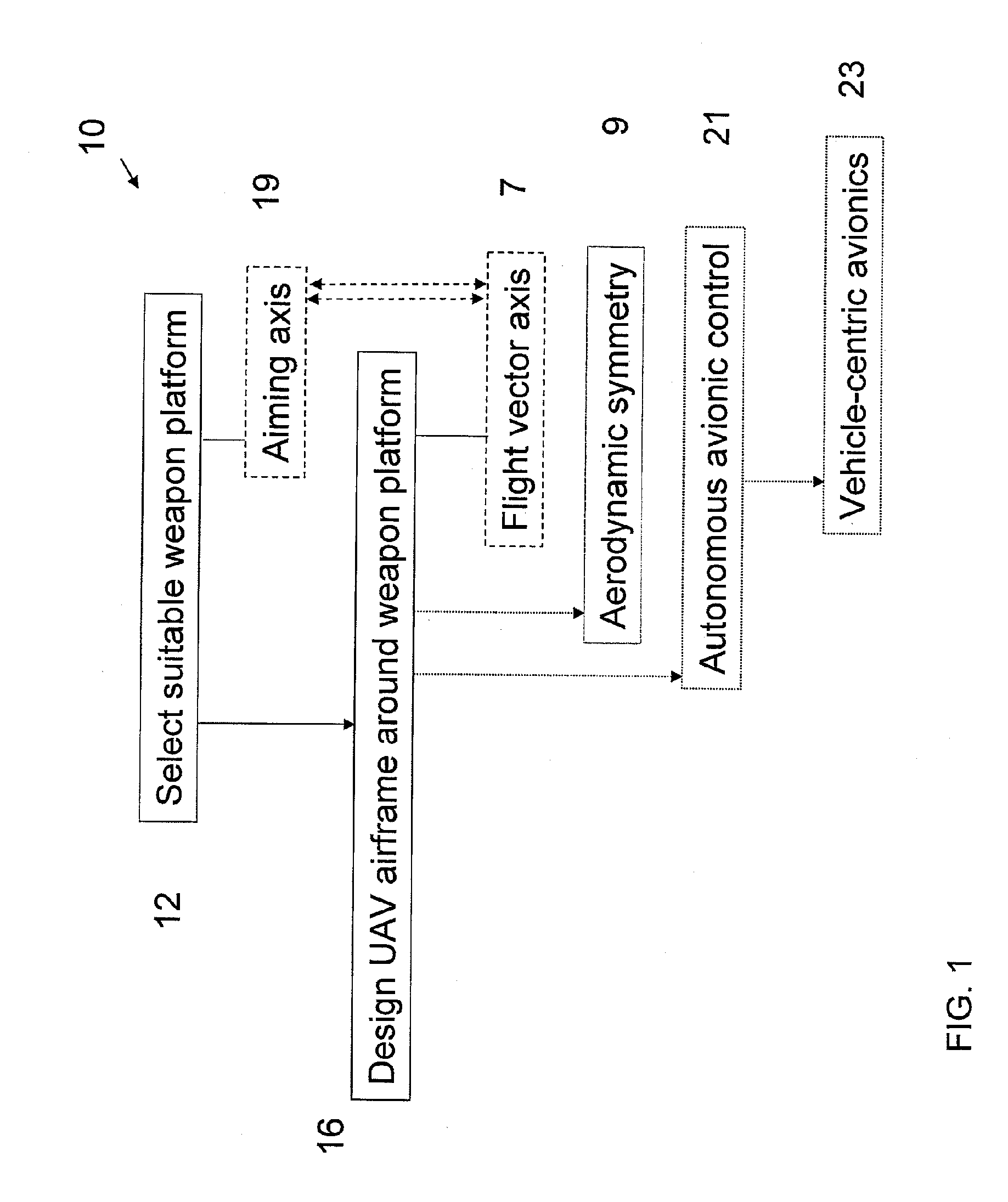
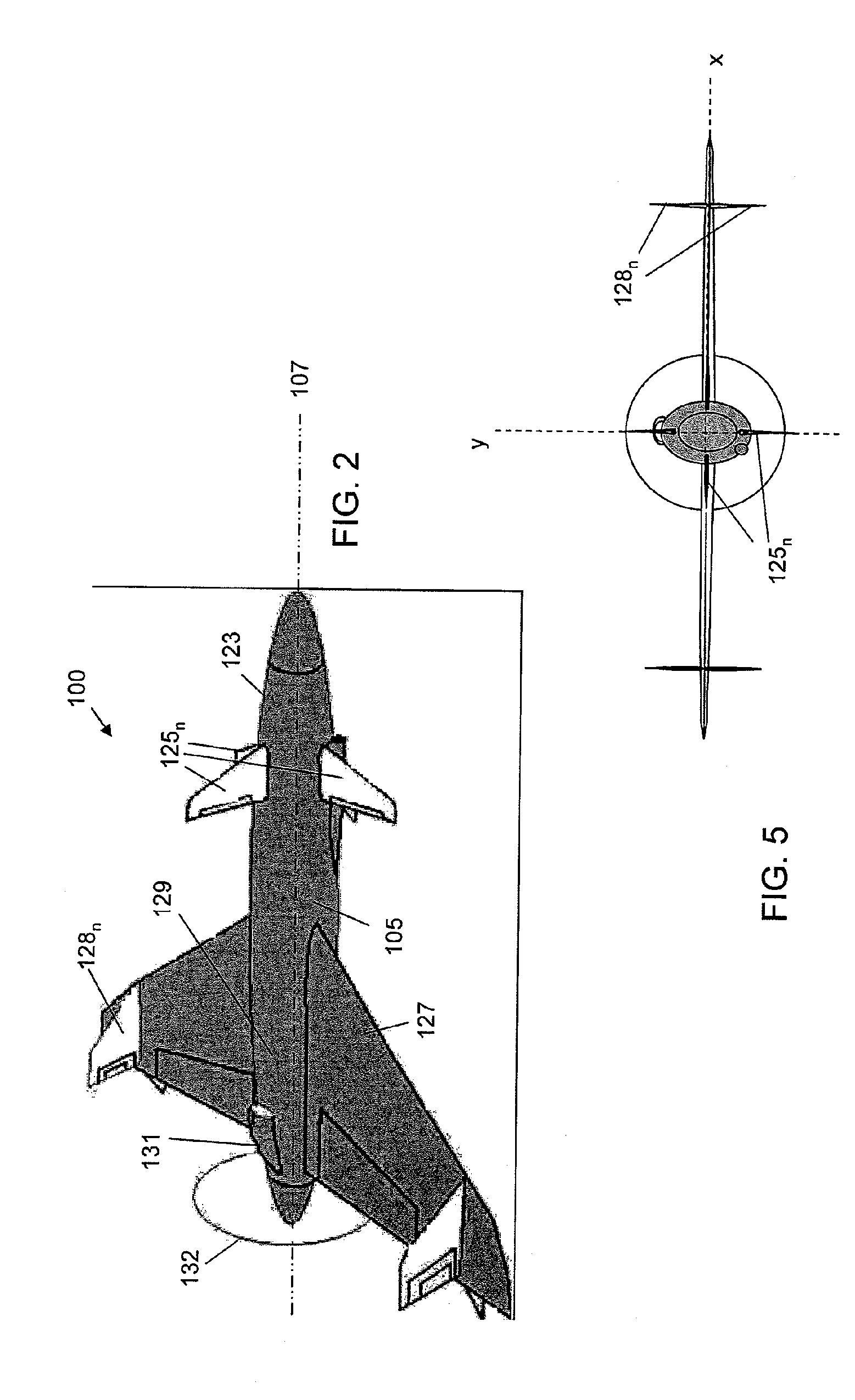
A small, reusable interceptor unmanned air vehicle (UAV), an avionics control system for the UAV, a design method for the UAV and a method for controlling the UAV, for interdiction of small scale air, water and ground threats. The UAV includes a high performance airframe with integrated weapon and avionics platforms. Design of the UAV first involves the selection of a suitable weapon, then the design of the interceptor airframe to achieve weapon aiming via airframe maneuvering. The UAV utilizes an avionics control system that is vehicle-centric and, as such, provides for a high degree of autonomous control of the UAV. A situational awareness processor has access to a suite of disparate sensors that provide data for intelligently (autonomously) carrying out various mission scenarios. A flight control processor operationally integrated with the situational awareness processor includes a pilot controller and an autopilot controller for flying and maneuvering the UAV.
Owner:LOCKHEED MARTIN CORP
Demand based method for interdiction of unauthorized copying in a decentralized network
InactiveUS20050114709A1Digital data processing detailsUnauthorized memory use protectionDecoyNetwork communication
A multi-level and / or demand based method and apparatus for interdicting unauthorized copying in a decentralized network are described. In their preferred embodiments, the method and apparatus start out by performing search result manipulation to interdict unauthorized copying of protected files. If a trigger event is detected in network communications, however, such as a threshold number of requests being exceeded for a protected file by a network node, then the method floods that node with decoys of the protected file to enhance interdiction efforts.
Owner:MACROVISION CORP
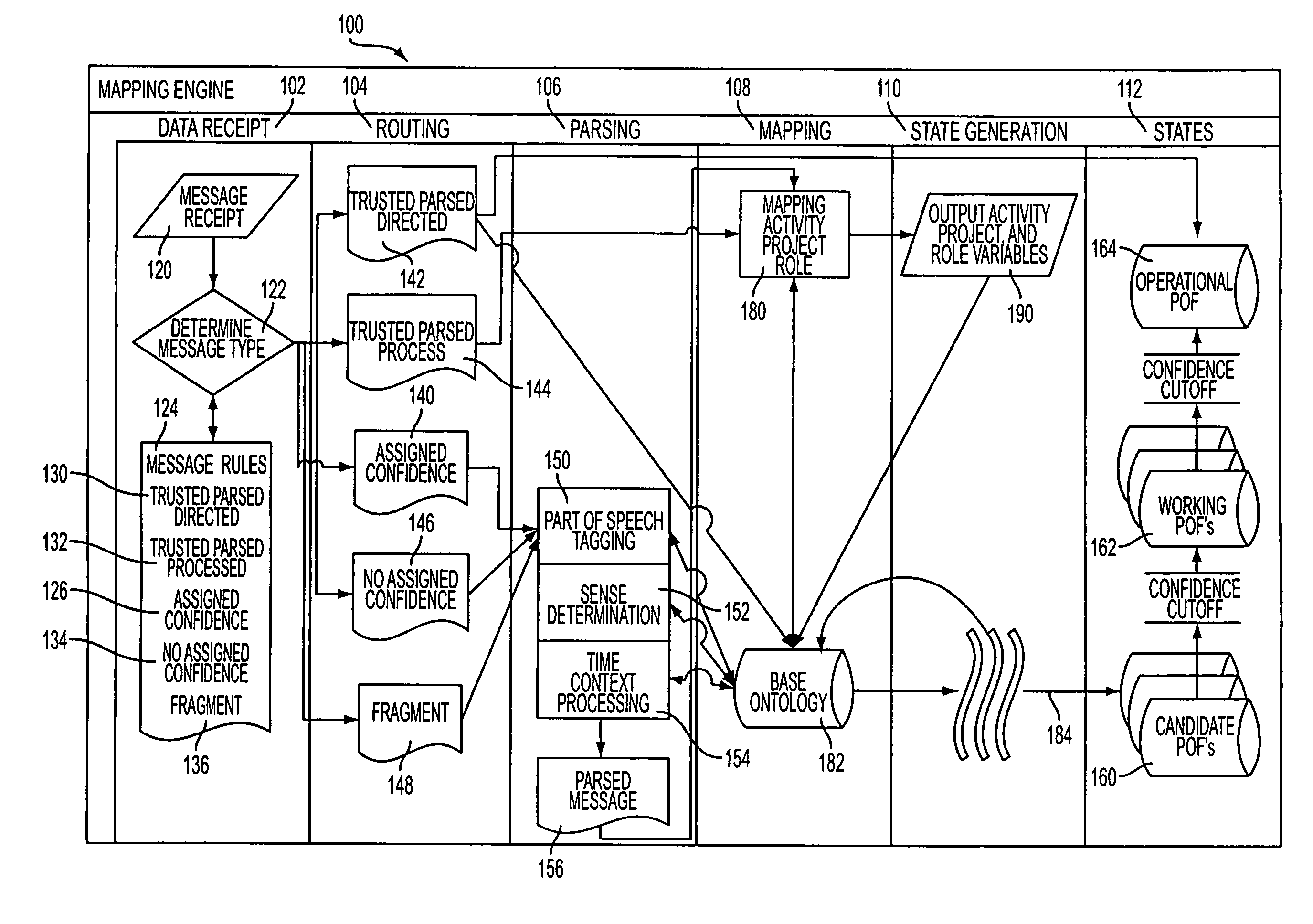
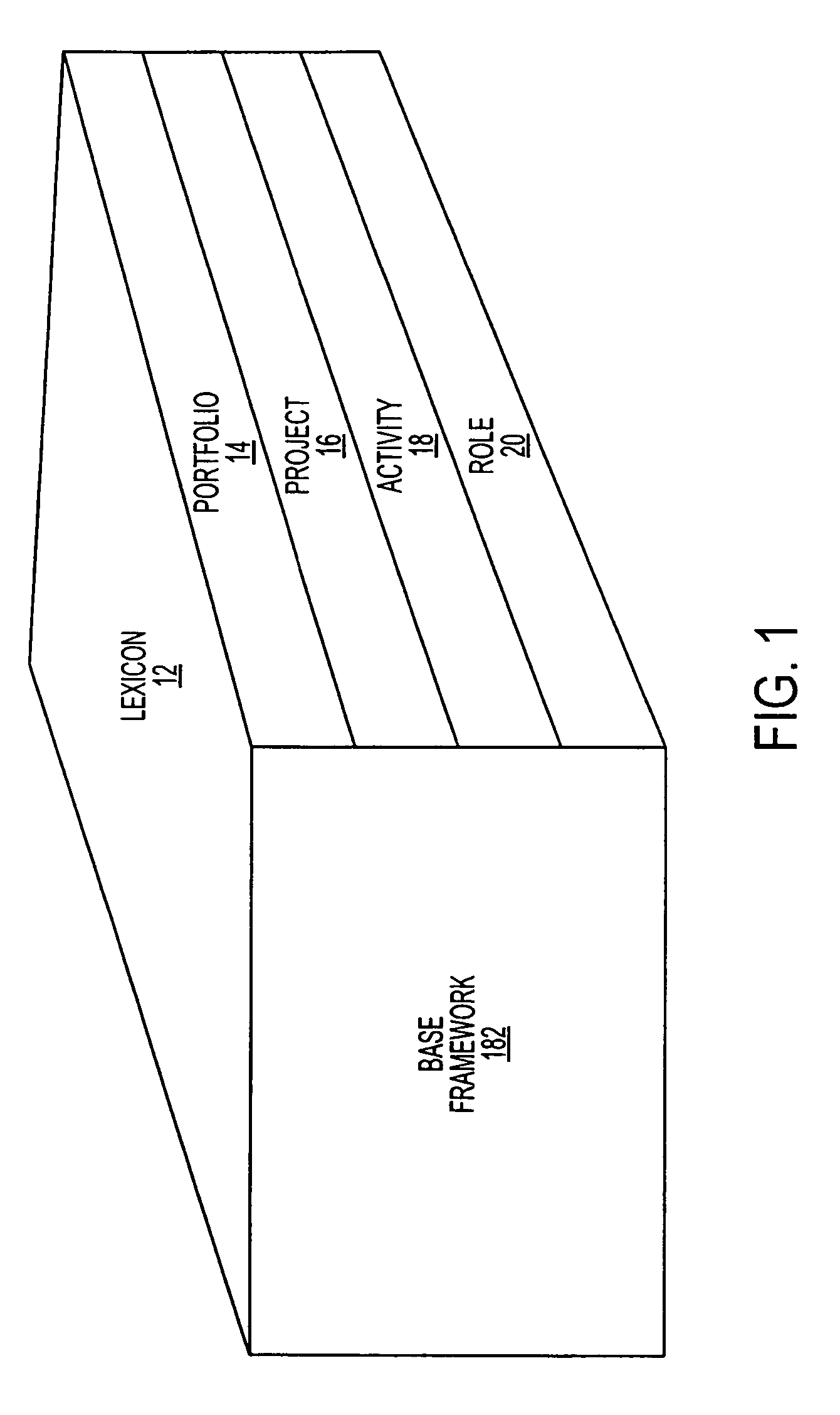
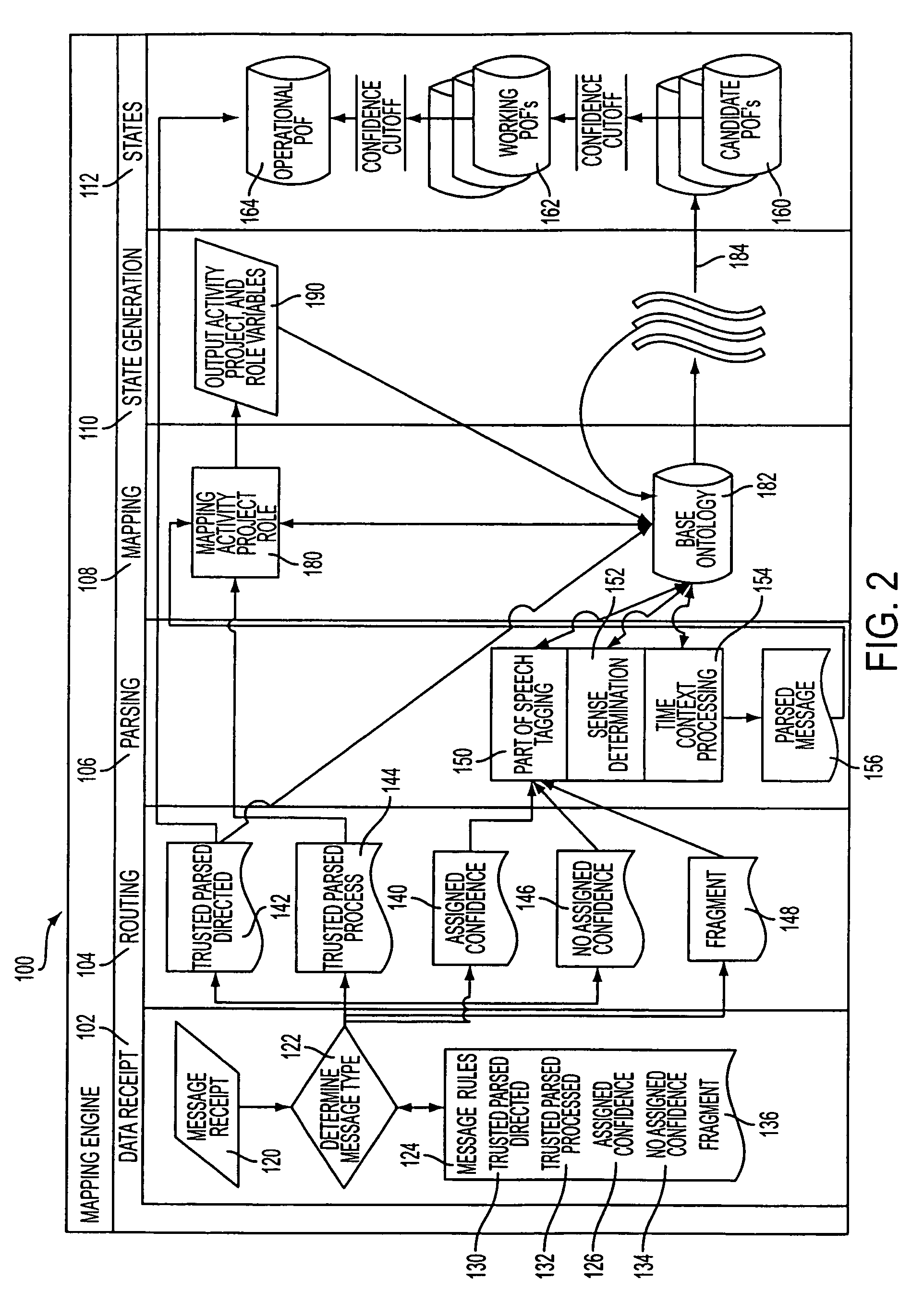
Predictive analytic method and apparatus
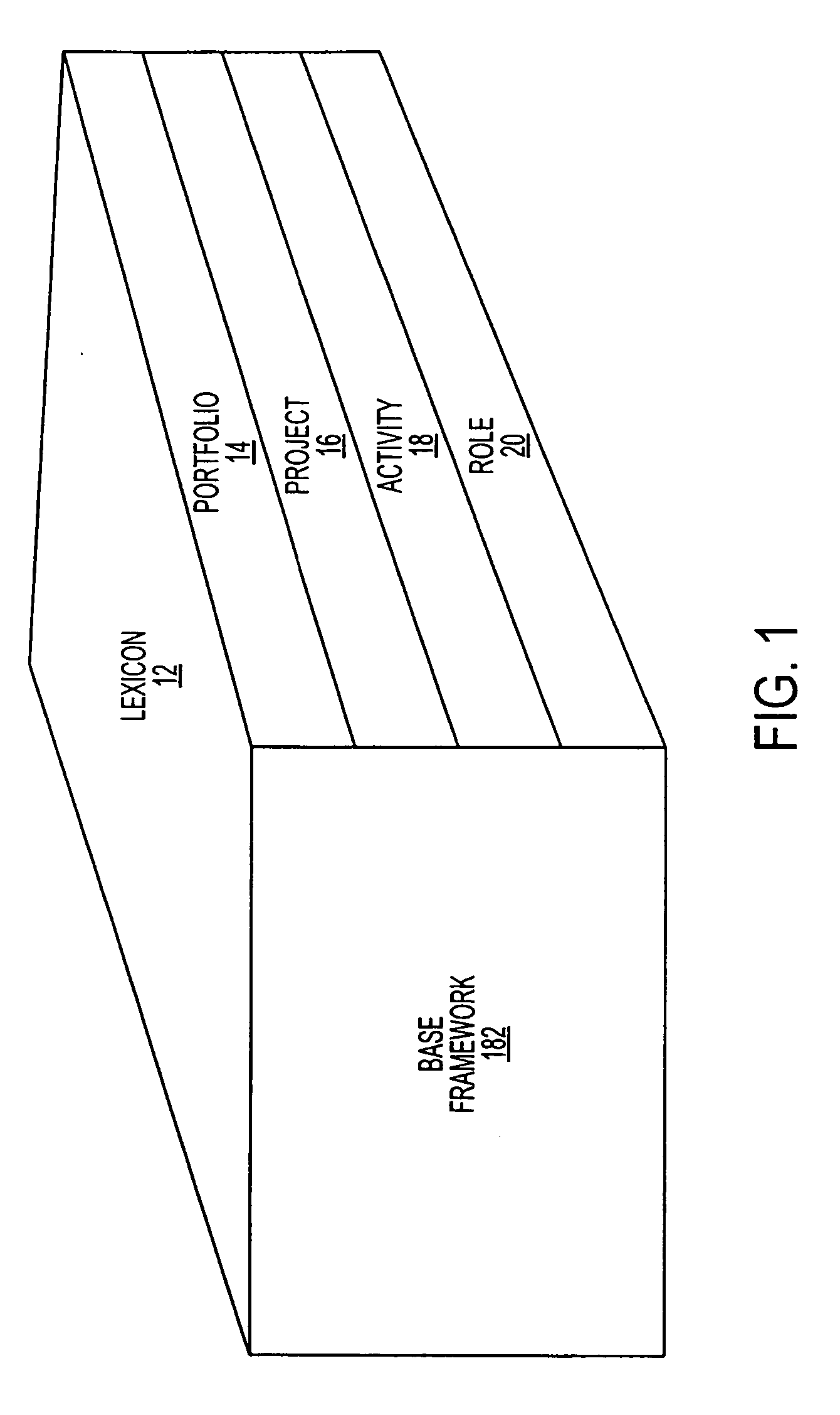
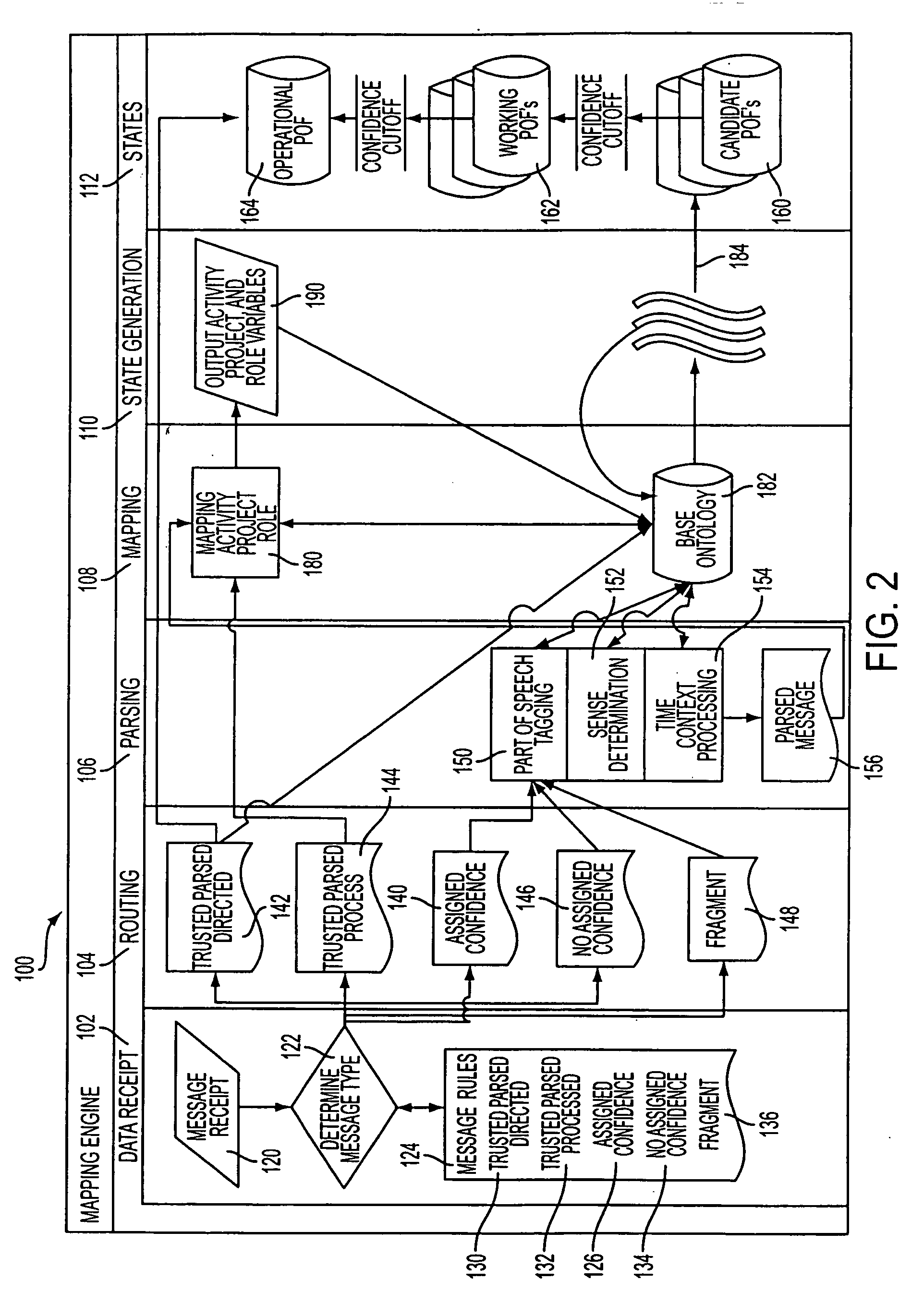
InactiveUS20060184483A1Digital data processing detailsKnowledge representationProject managementRelational view
A computerized project management analytical system and method that develops and manages an ontology that links objects and is capable of being mined. The ontology is comprised of a project ontology framework, a matching engine and a project status matrix that illustrates a multi-relational view of the project status, of confidence levels, or interdiction points and / or positions on project timelines.
Owner:METIER
Deterent for unmanned aerial systems
ActiveUS9715009B1Defence devicesDirection/deviation determining electromagnetic systemsNon destructiveCountermeasure
Owner:XIDRONE SYST INC
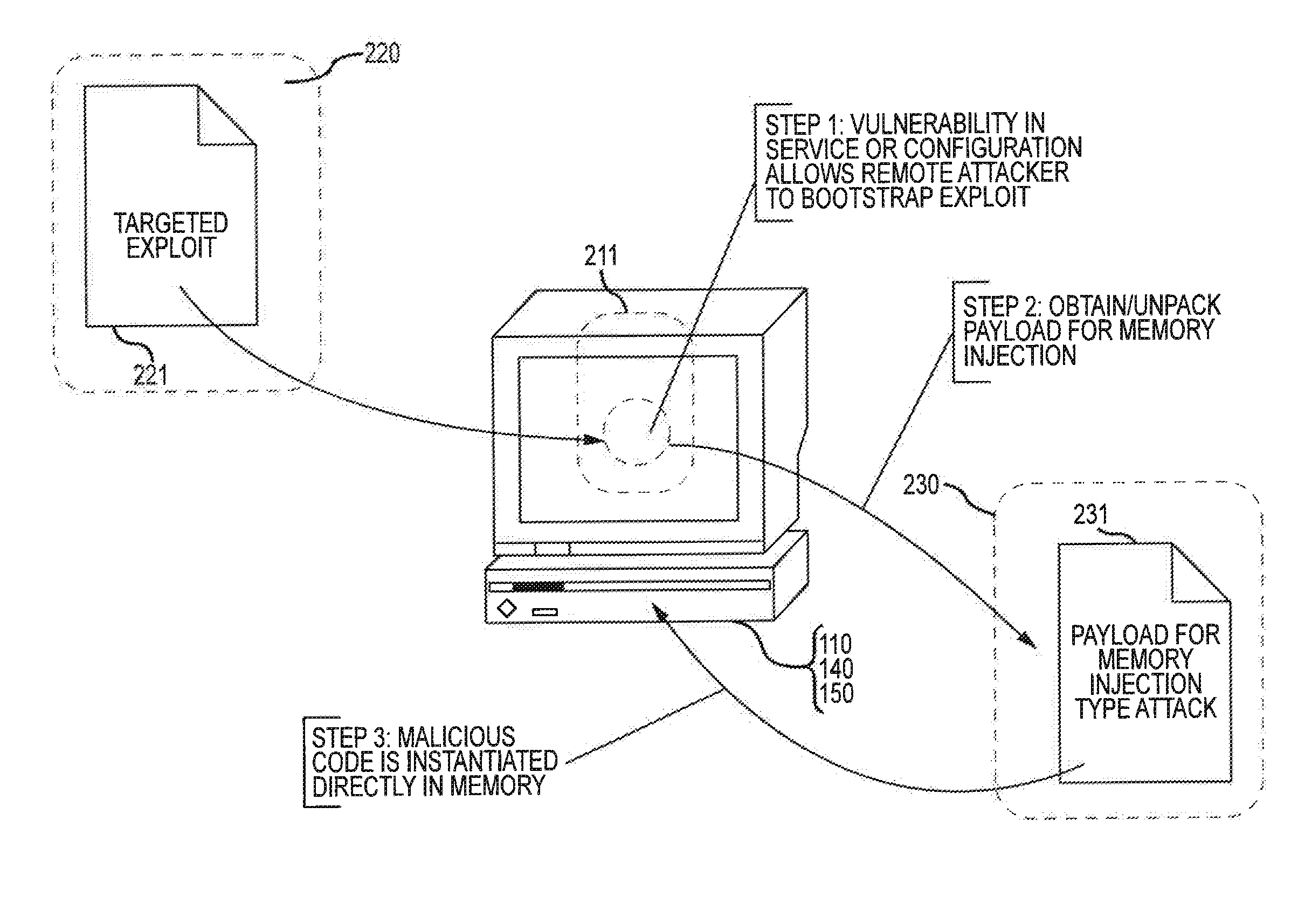
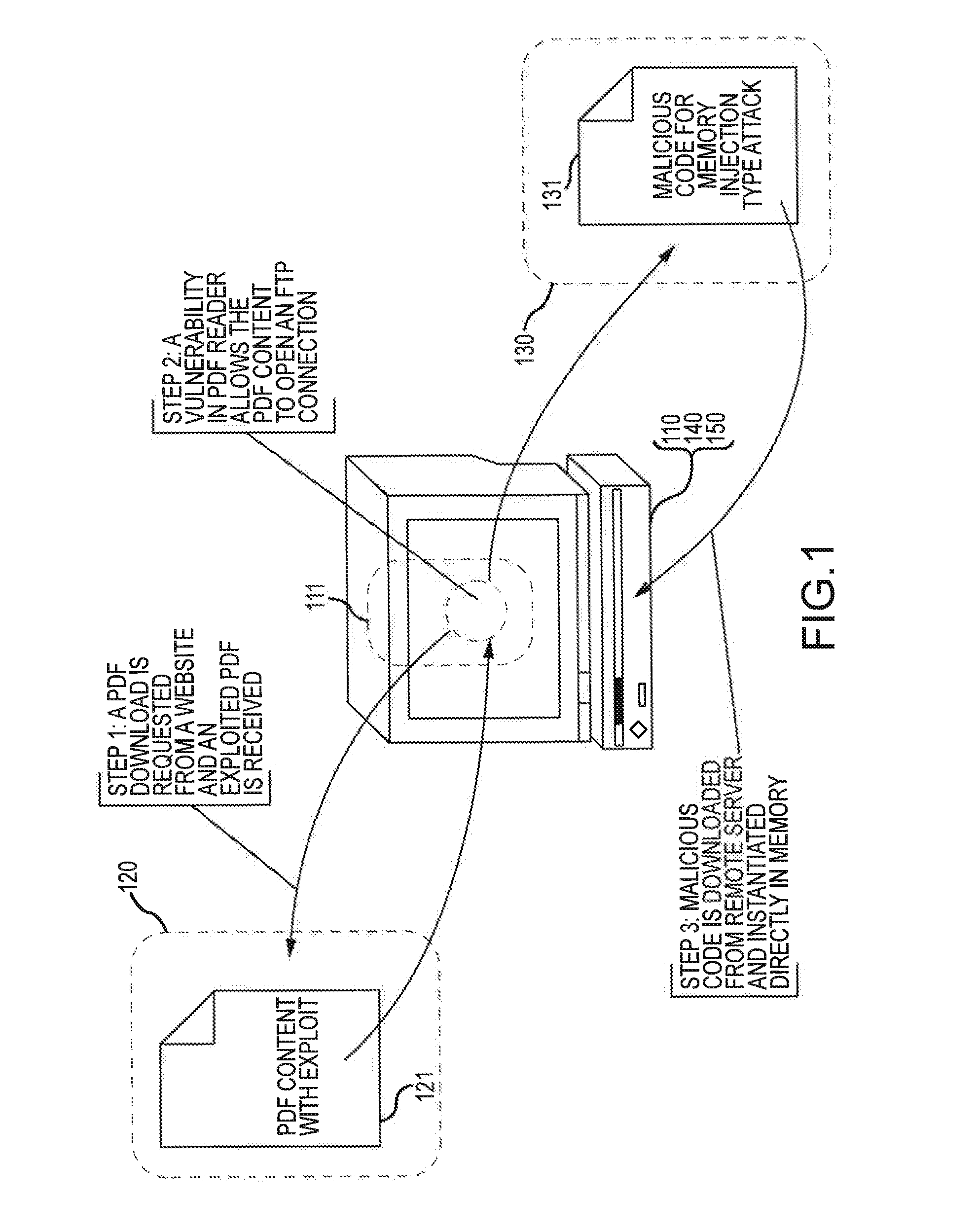
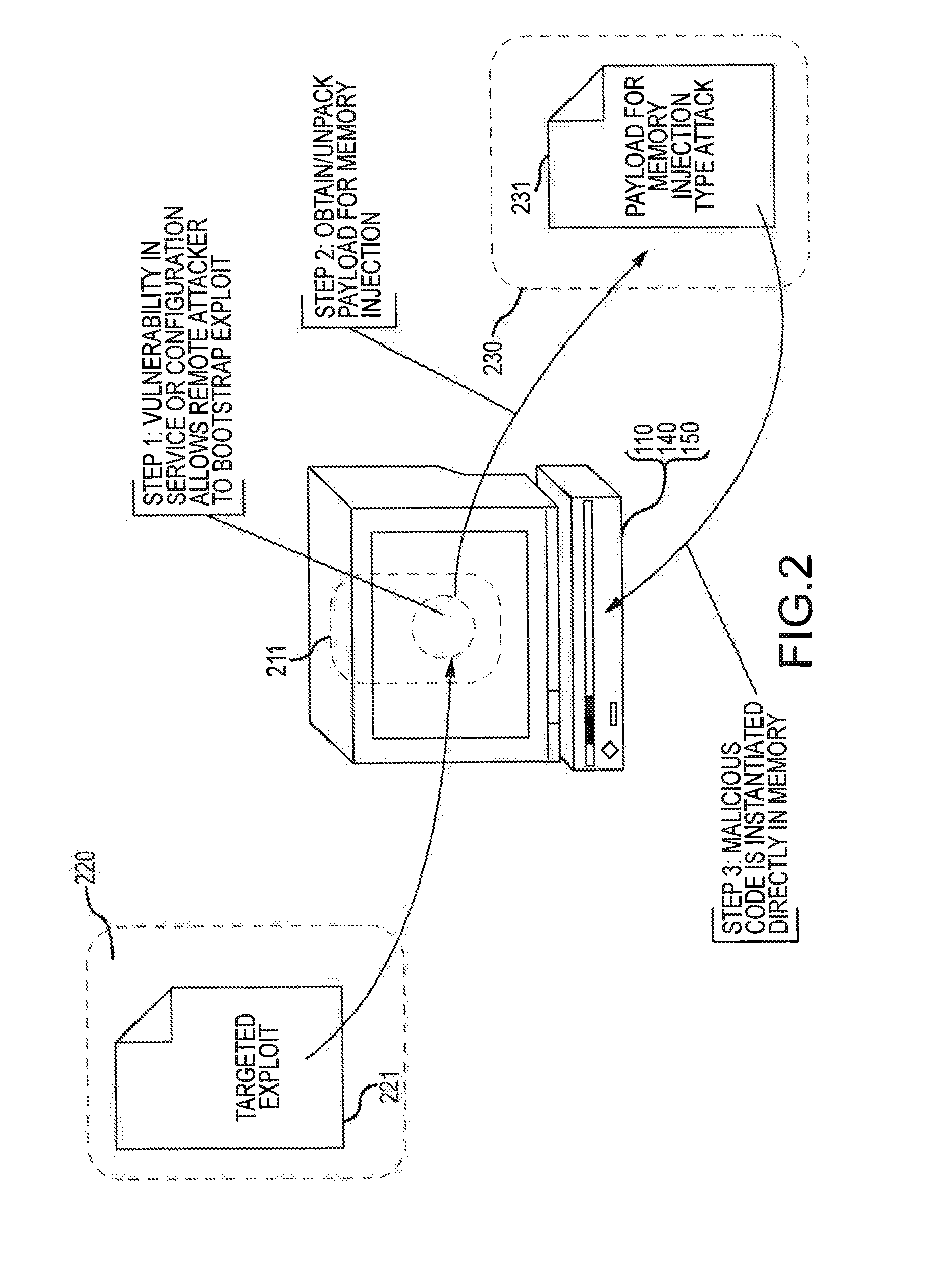
Information security techniques including detection, interdiction and/or mitigation of memory injection attacks
ActiveUS20130290662A1Easy to processUnauthorized memory use protectionPlatform integrity maintainanceComputerized systemInformation security
Methods of detecting malicious code injected into memory of a computer system are disclosed. The memory injection detection methods may include enumerating memory regions of an address space in memory of computer system to create memory region address information. The memory region address information may be compared to loaded module address information to facilitate detection of malicious code memory injection.
Owner:IVANTI INC
Unmanned air vehicle, integrated weapon platform, avionics system and control method
InactiveUS7542828B2Forgiving of small errorMaximize probabilityUnmanned aerial vehiclesDigital data processing detailsAviationControl system
A small, reusable interceptor unmanned air vehicle (UAV), an avionics control system for the UAV, a design method for the UAV and a method for controlling the UAV, for interdiction of small scale air, water and ground threats. The UAV includes a high performance airframe with integrated weapon and avionics platforms. Design of the UAV first involves the selection of a suitable weapon, then the design of the interceptor airframe to achieve weapon aiming via airframe maneuvering. The UAV utilizes an avionics control system that is vehicle-centric and, as such, provides for a high degree of autonomous control of the UAV. A situational awareness processor has access to a suite of disparate sensors that provide data for intelligently (autonomously) carrying out various mission scenarios. A flight control processor operationally integrated with the situational awareness processor includes a pilot controller and an autopilot controller for flying and maneuvering the UAV.
Owner:LOCKHEED MARTIN CORP
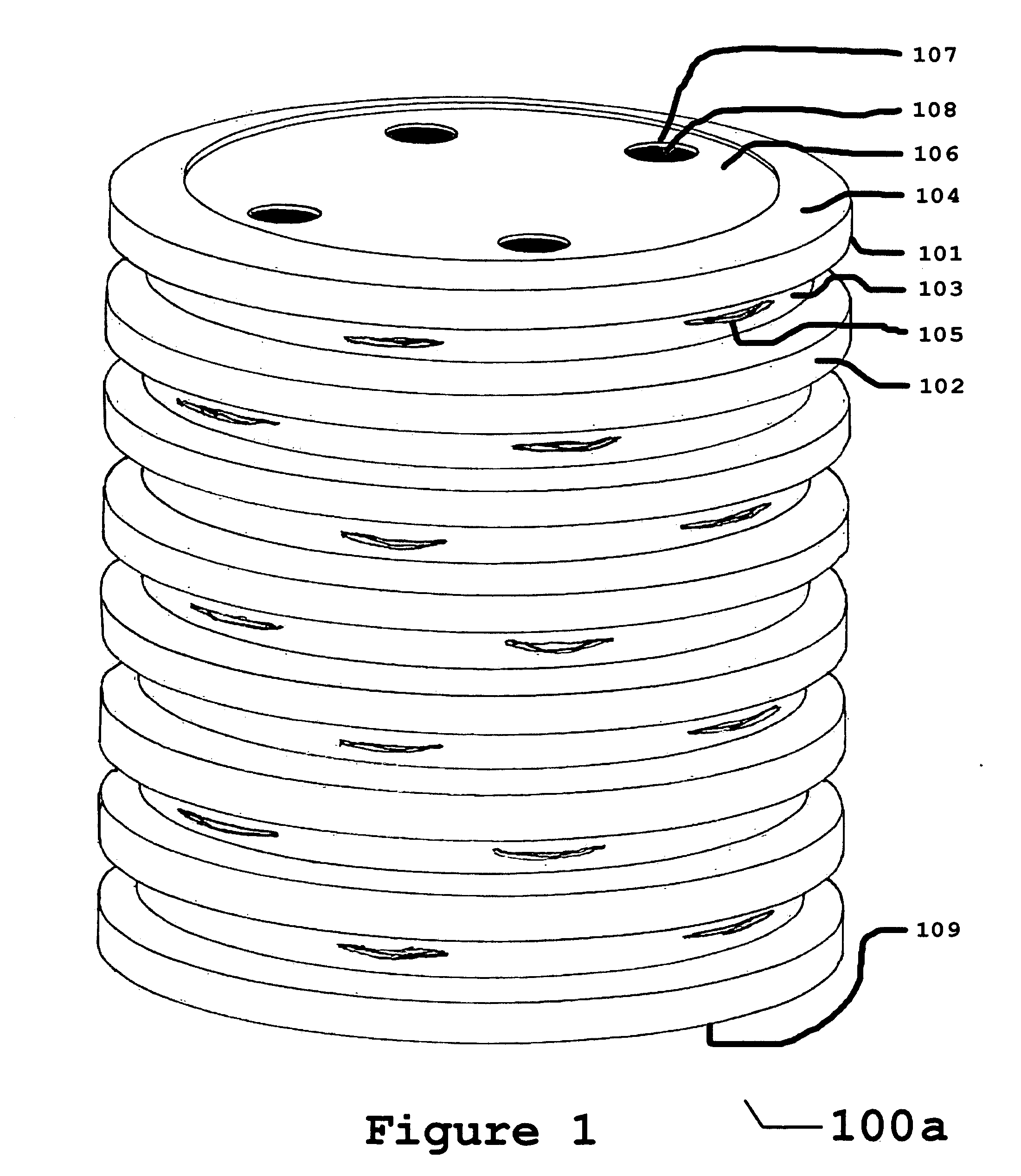
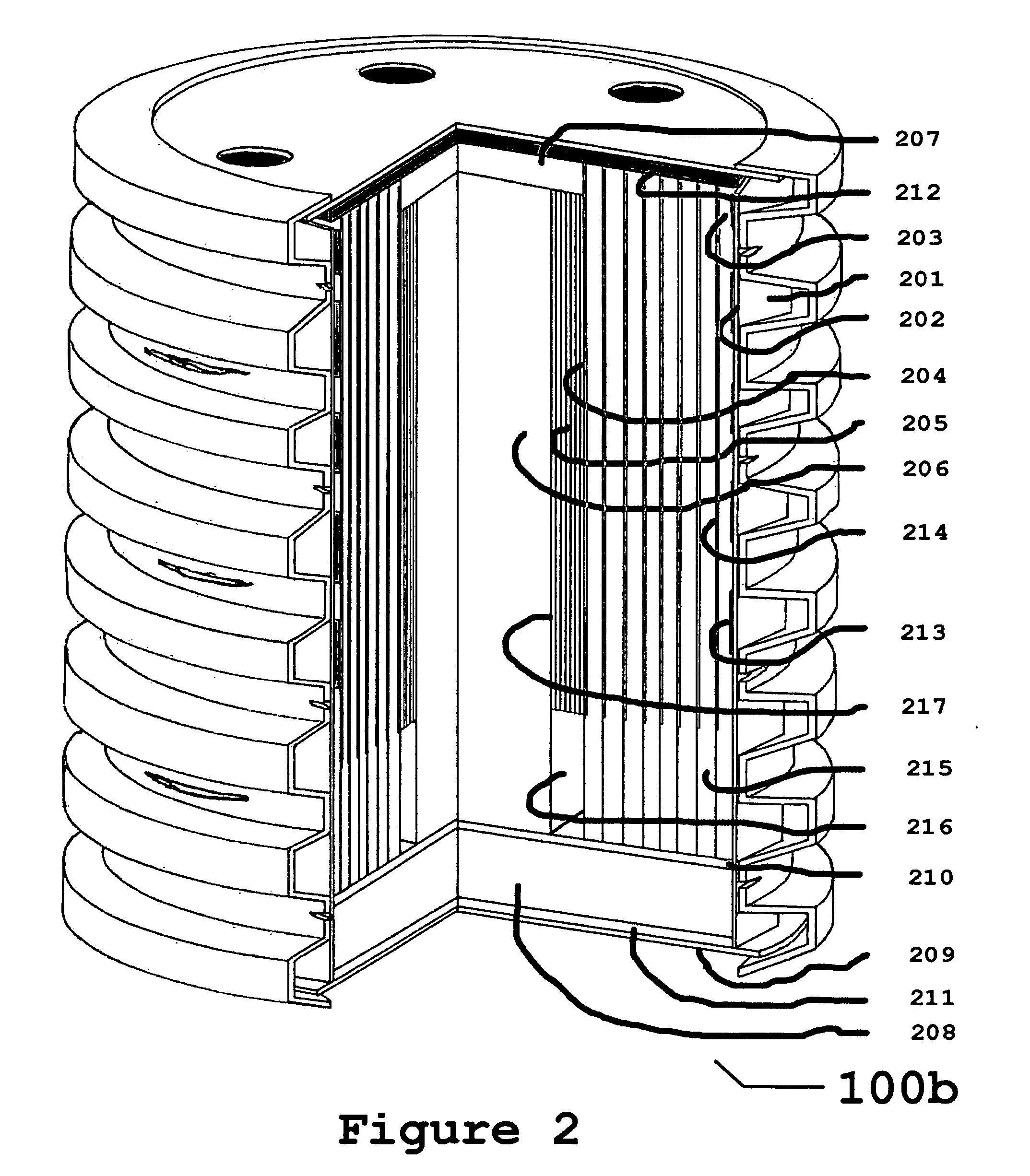
Apparatus and method to intercept and interdict subterranean termites using miscible tasks
InactiveUS20070256350A1Easy to useWell mixedInsect catchers and killersPoisonBiological bodyVisual inspection
Herein is disclosed an apparatus for intercepting and interdicting target organisms such as subterranean termites, which apparatus is comprised of an outer shell fitted with a port for organism ingress and egress and a dorsal cover fitted with a signal port for visual inspections. Inside are materials suitable as food for the organisms targeted by the device, so arranged and comprised as to aid and encourage the habitation, propagation, and retention of biological pesticides, including entomopathogenic nematodes. The subject invention teaches a method of gradually deploying its apparatus to intercept the presence, measure the strength and vigor, and interdict aggregations, of said target organisms. The method permits minimal, systematic deployments that undergo progressive evolutions as information from each deployed device accumulates. Reliance on simple, accurate, visual signals, to determine servicing and supplementation requirements, reduces the user's inspection and servicing time, minimizes the use of interdiction agents, and speeds the interdiction of the targeted organism at the site.
Owner:CATES JERRY
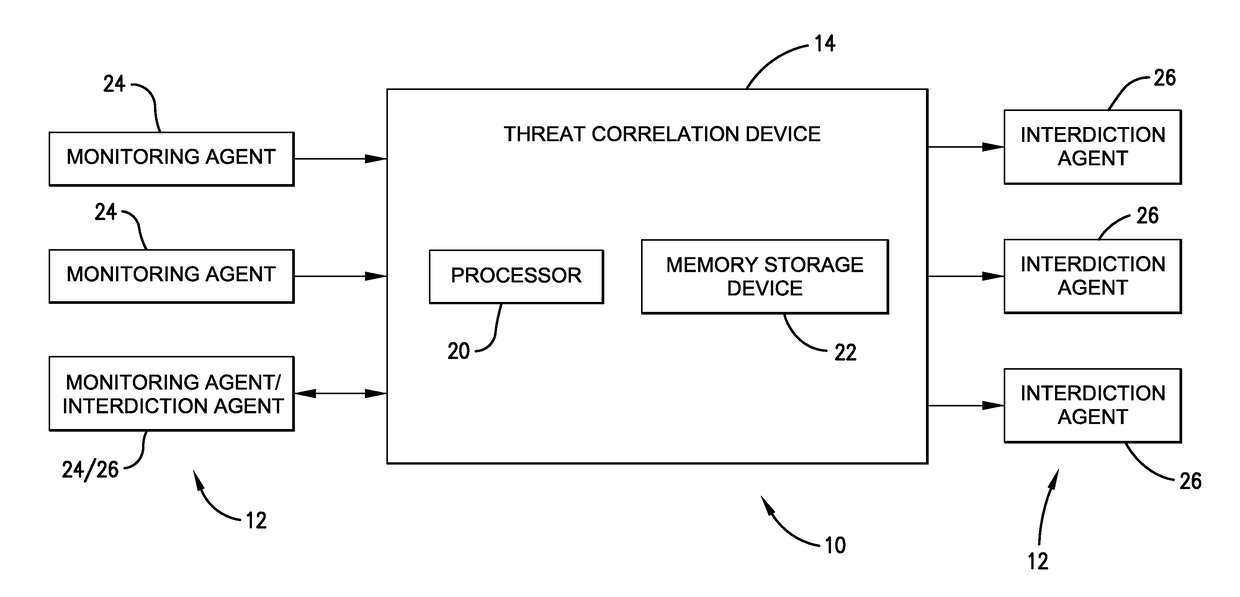
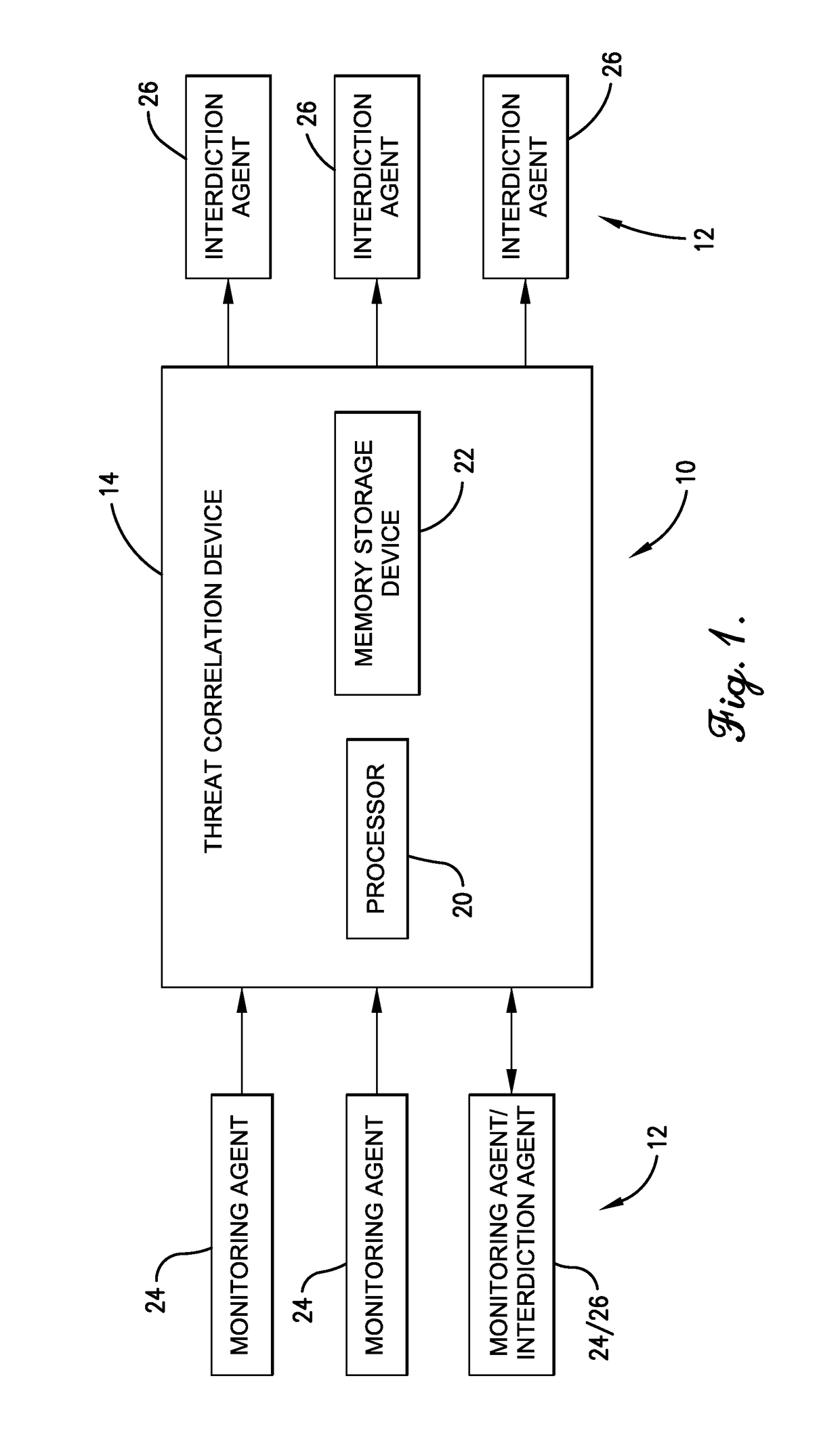
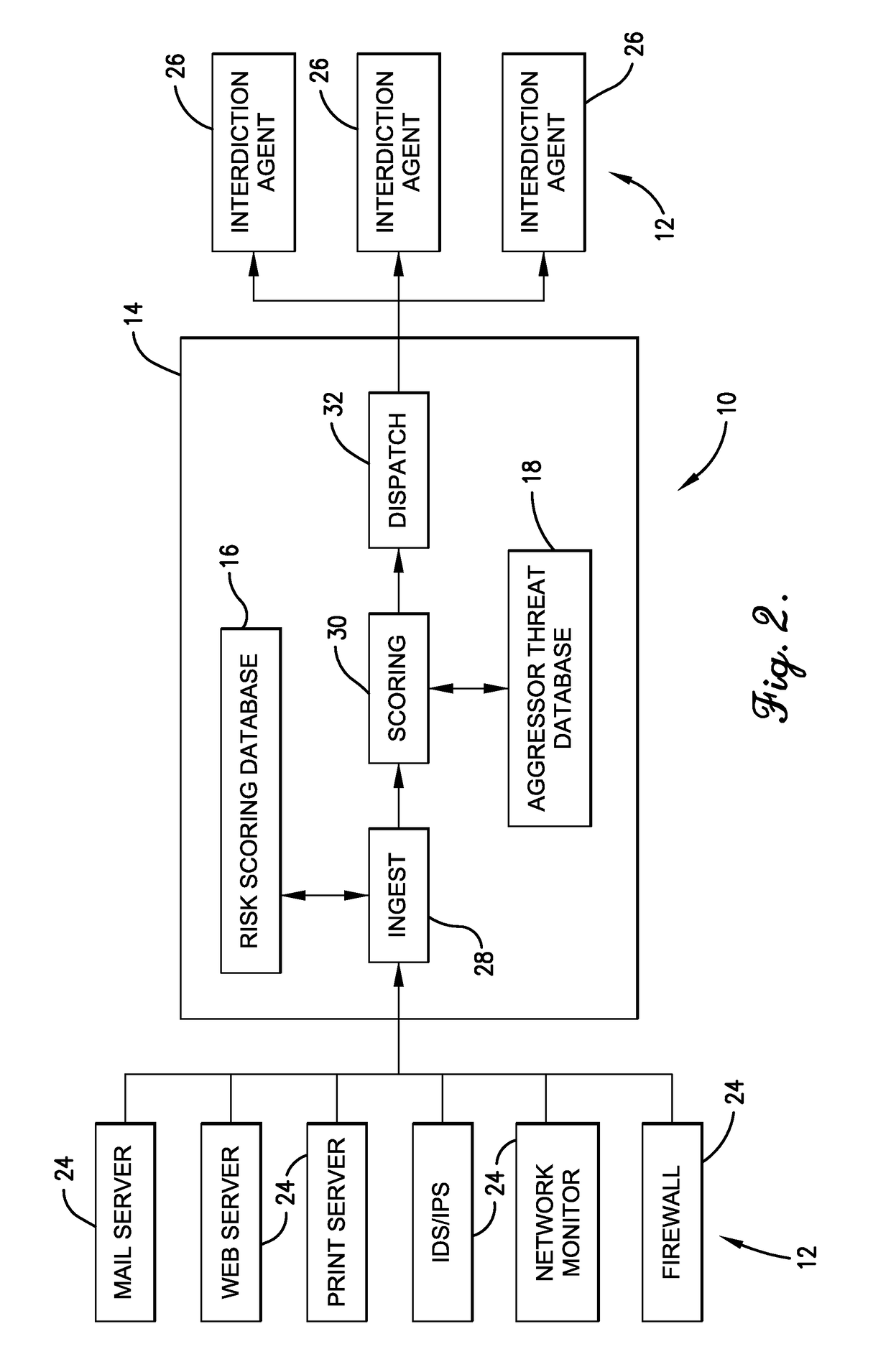
Network protection system and threat correlation engine
A network protection system and method for processing of network traffic between one or more networked devices. The network protection system may include the networked devices and a threat correlation device. The networked devices may operate as a monitoring agent and / or an interdiction agent. The threat correlation device may execute computer code for receiving information from the monitoring agent regarding an event recognized by the monitoring agent, retrieving an event score for the event from a risk scoring database based on an event type, a destination of the event, and a number of occurrences of the event, and updating a risk score by adding the event score to the risk score. When the risk score reaches a critical threshold, the threat correlation device may send instructions to the interdiction agent to take protective or defensive action against data traffic of that event type and from that aggressor.
Owner:INSCYT LLC
Societal-scale graph-based interdiction for virus propagation slowdown in telecommunications networks
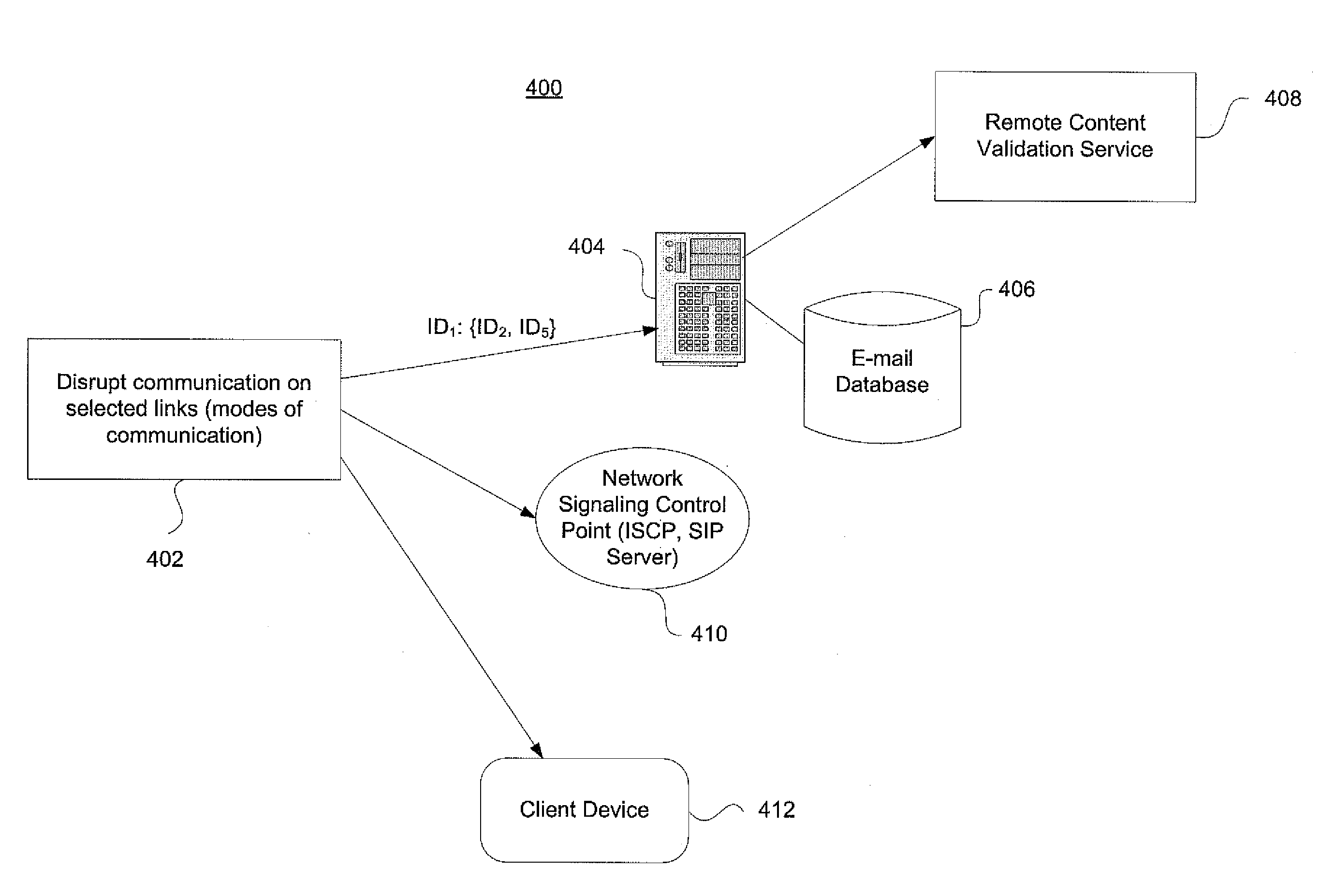
InactiveUS20110295982A1Disrupting spreadExtended durationMemory loss protectionError detection/correctionCyber-attackTelecommunications network
Embodiments of the invention enable very rapid intervention on detection of computer network attacks by viruses or other malicious code. Targeted disruption of links between selected nodes in the network is used to hinder the spread of such malicious code. This applies to e-mail and other modes of communication. For instance, identification of and response to an attack may occur within 5-10 minutes instead of the hours or days timescale associated with known signature-based virus protection techniques. Aspects of the invention directly adapt to observed patterns of social contacts and exchanges to provide a substantial increase, e.g., on the order of a 10-fold increase, in the time until a virus affects 70-80% of network users. This provides anti-virus inoculation mechanisms significant time, for instance on the order of 1-2 additional days, before an attack disrupts worldwide communication networks.
Owner:TT GOVERNMENT SOLUTIONS
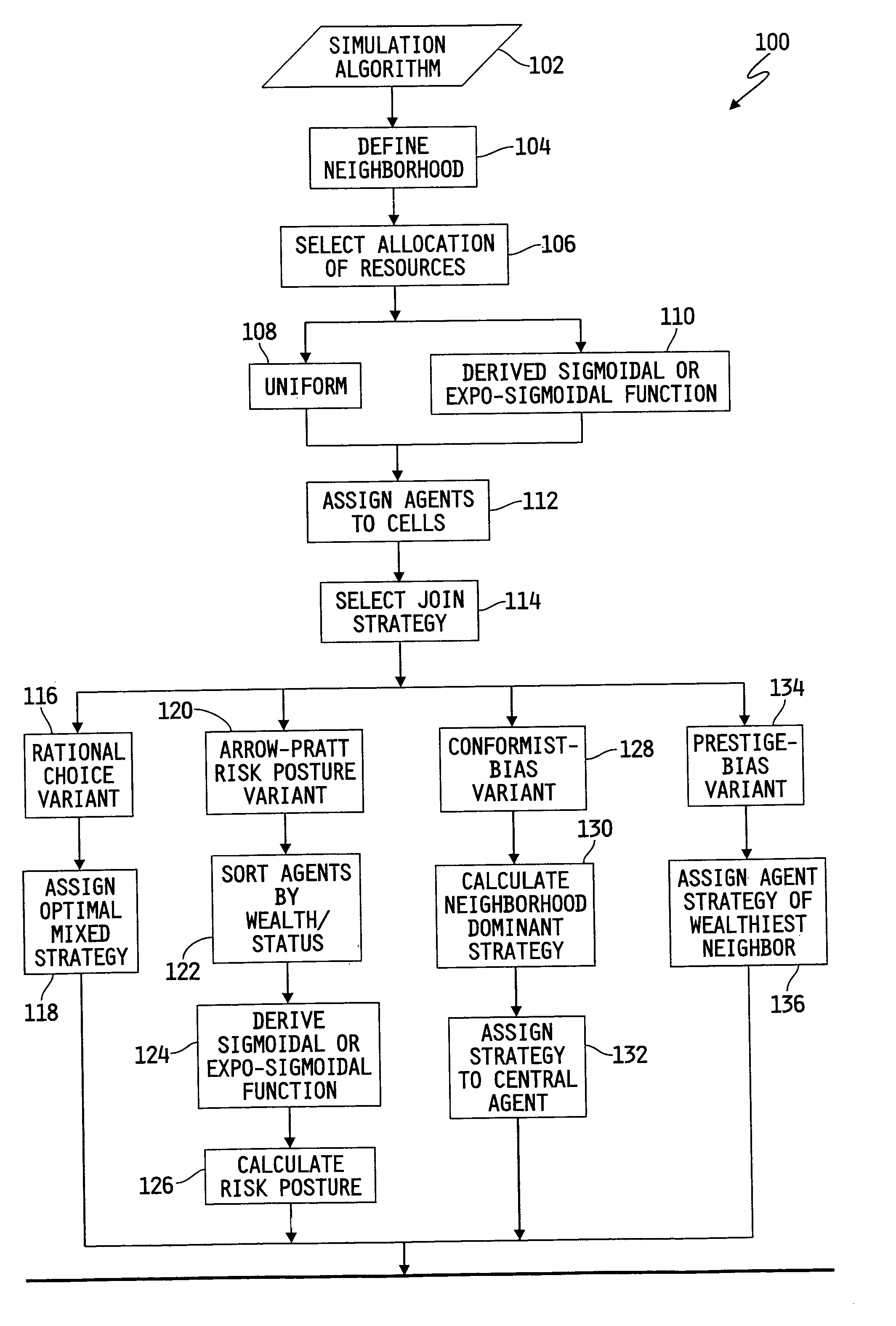
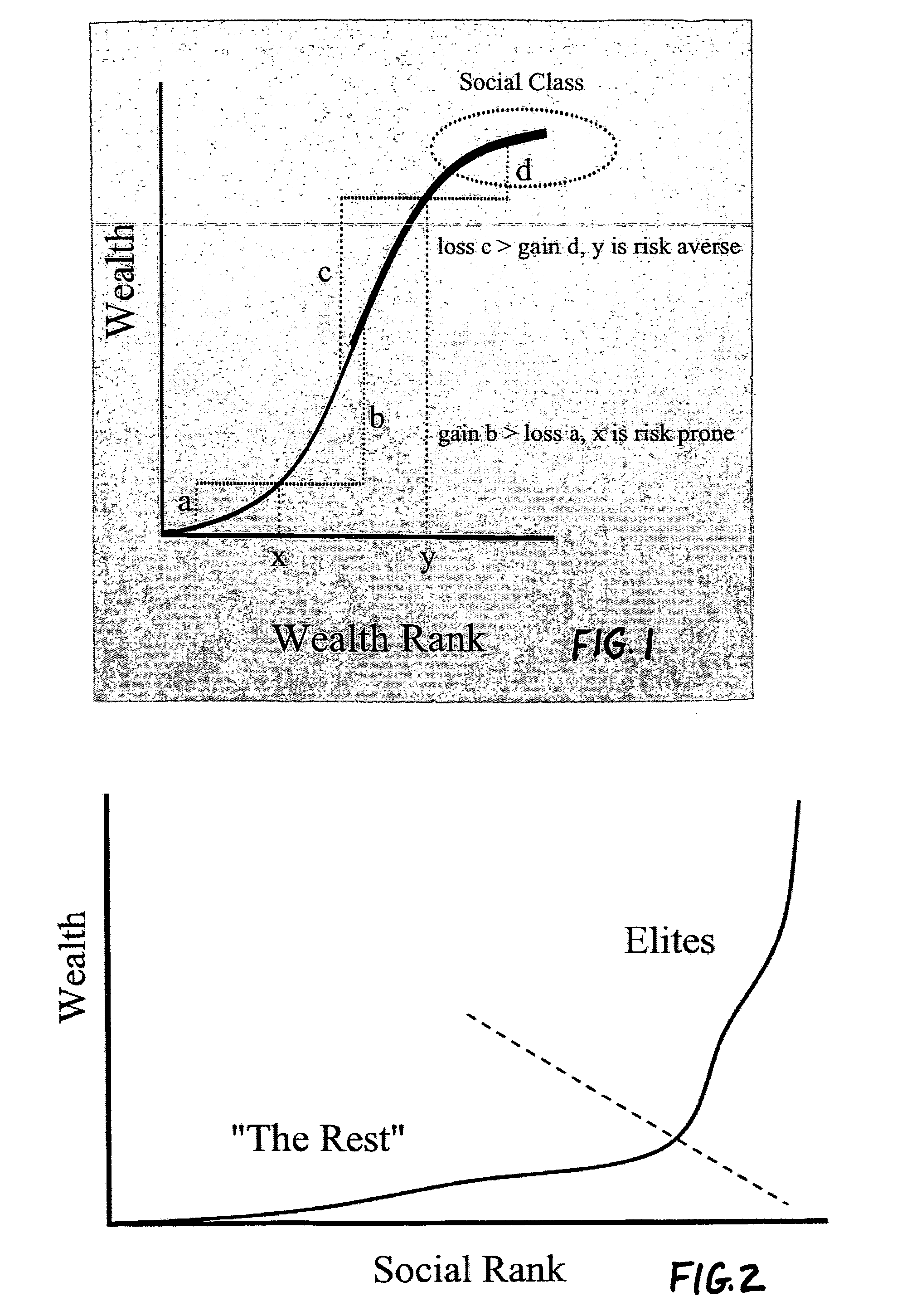
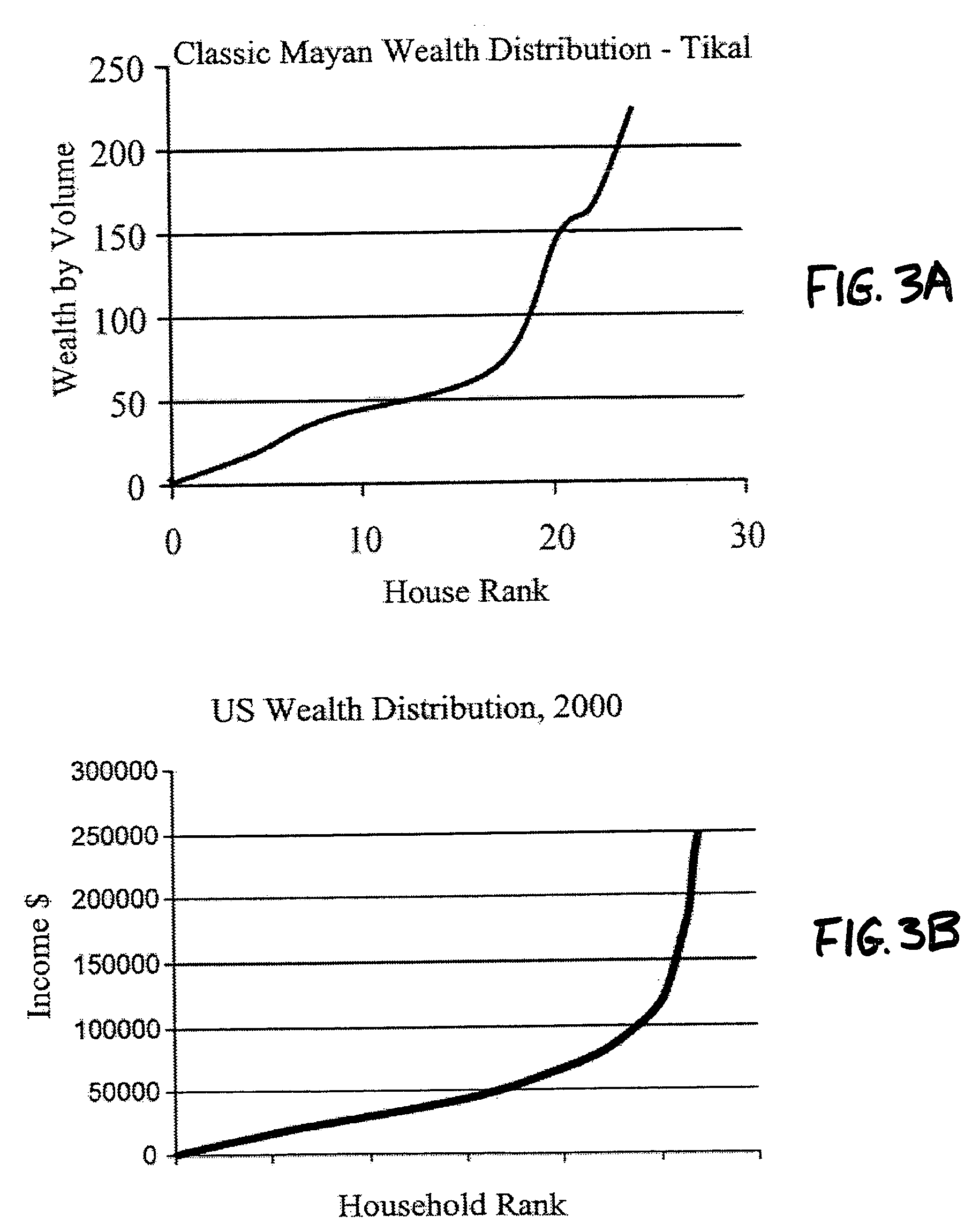
Agent based modeling of risk sensitivity and decision making on coalitions
An agent based model system provides simulation of the influence of environmental variables and tendencies in individual and social decision making relating to the formation of coalitions and ethnic groups. The system is based on improved understandings of human decision making under risk, and incorporates recent theoretical developments and computational tools. The system gives analysts the ability to predict the development of coalitions and ethnic groups, as well as the ability to manage the behavior of individuals in such groups. The model results provide confidence intervals for various possible scenarios in a mix of agents' decision rules and distribution of environmental resources. Applications include management of ethnic groups and violent conditions in unstable nations, the tracking of terrorist organizations, development of coalitions and oligopolies in business, and the modeling and interdiction of criminal organizations.
Owner:PURDUE RES FOUND INC
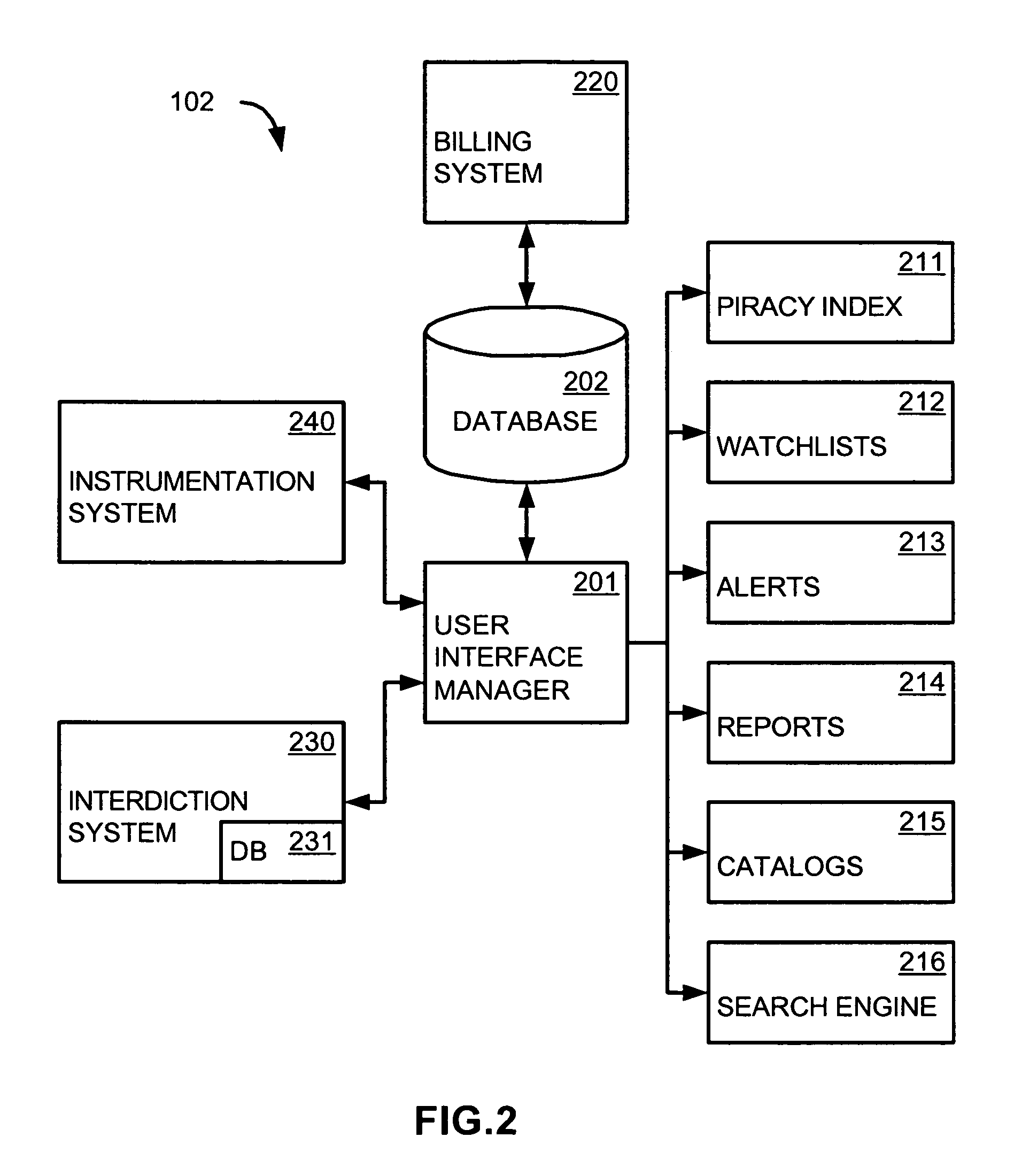
System, method and client user interface for a copy protection service
ActiveUS20050198535A1Easily interfaceDigital data processing detailsUnauthorized memory use protectionClient-sideCopy protection
A system, method and client user interface for a copy protection service employs software agents masquerading as nodes in decentralized networks for monitoring and interdicting file sharing activities of protected files in the networks. A control center communicates with the software agents and subscriber client computers through user interfaces, so as to provide monitoring information to users of the client computers and control the monitoring and interdiction of protected files according to instructions received from the client computers. A one-click method for requesting protection of a file, providing the terms of such protection, and updating billing information for the user is implemented through the user interface to simplify user interaction with the copy protection service.
Owner:ROVI SOLUTIONS CORP
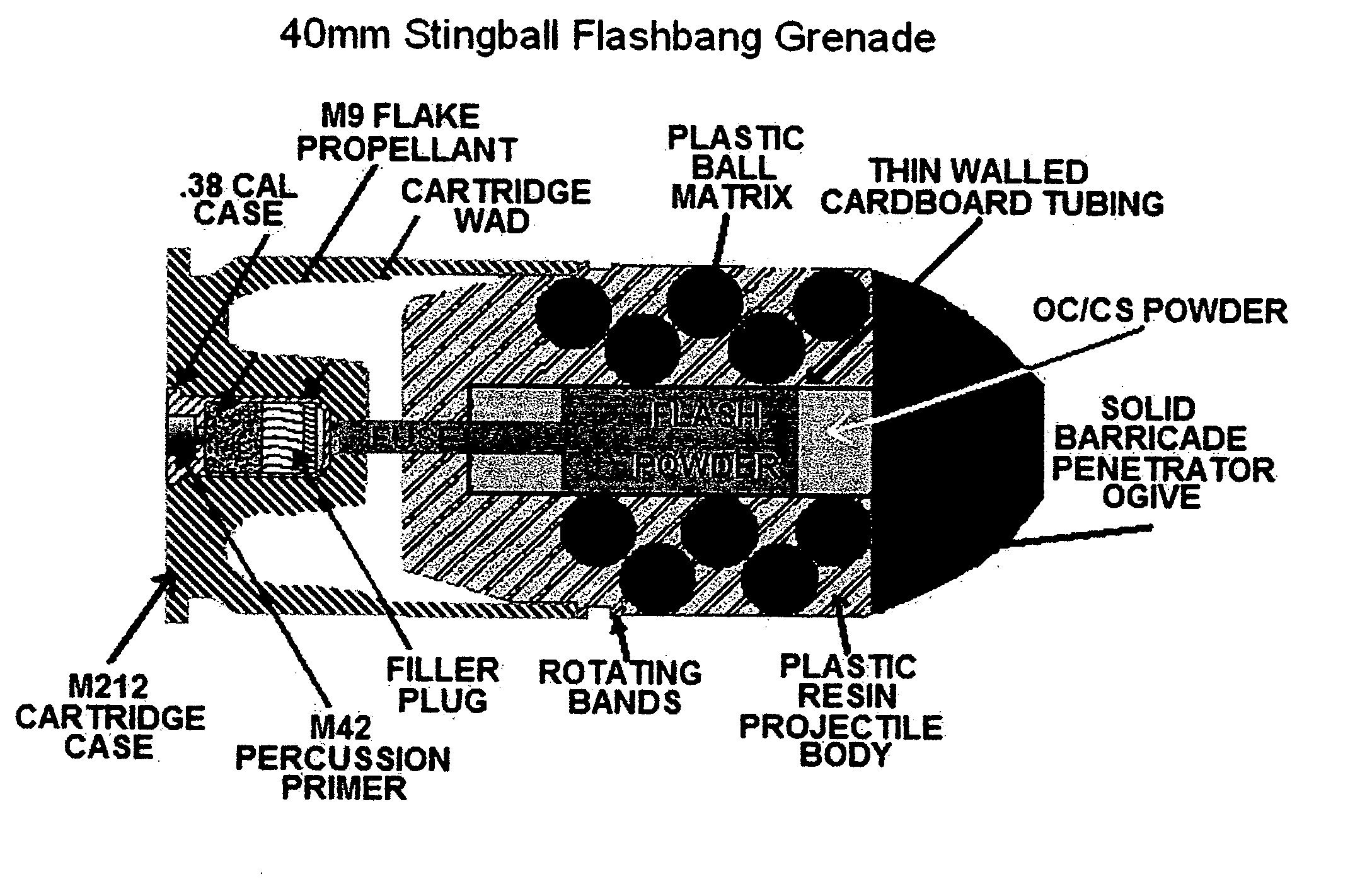
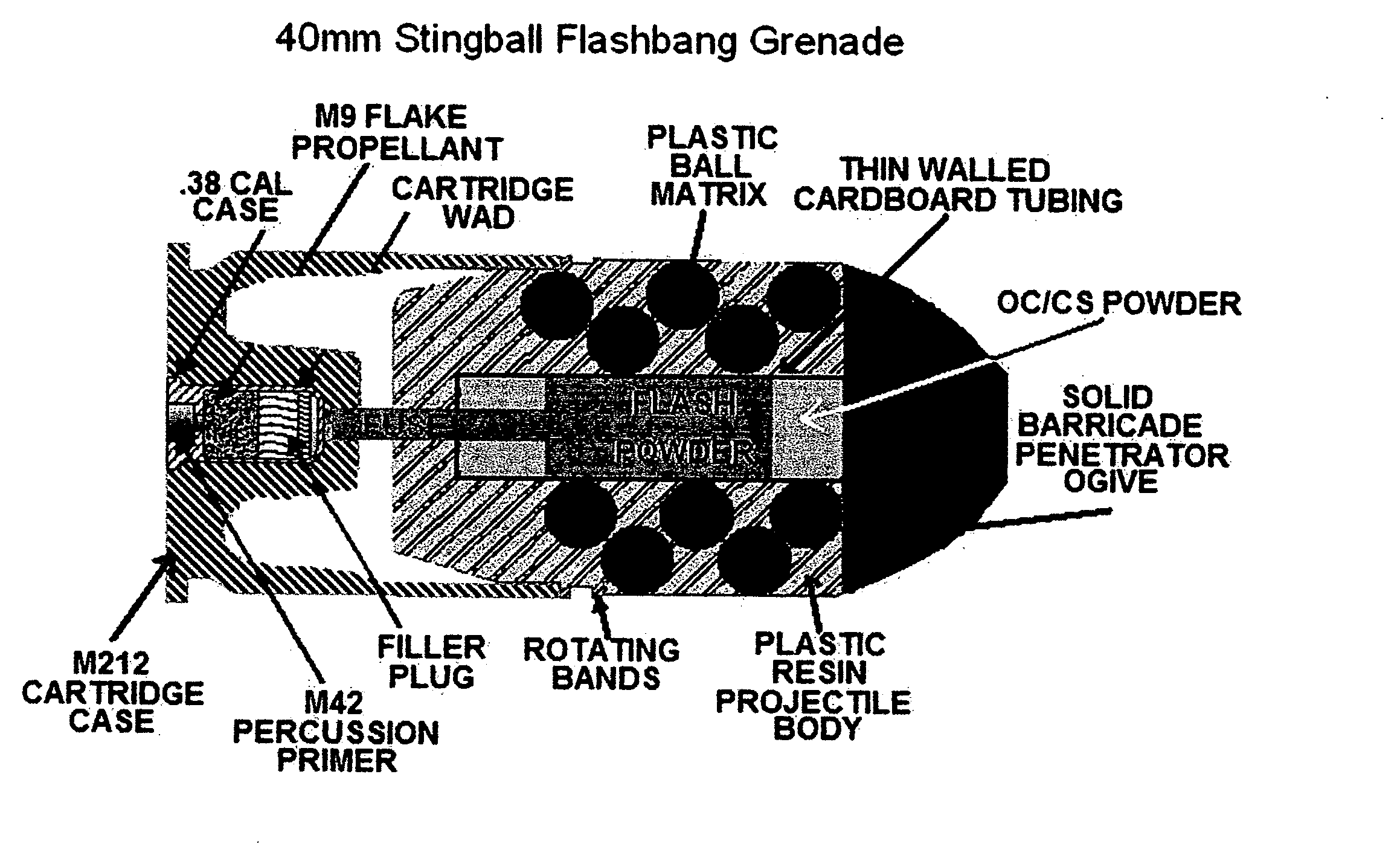
XM-5866 Stingball flashbang grenade
The grenade is a multi-purpose munition which can be used as a distraction device, like a flash bang grenade, and can be equipped with chemical agent powder for added capabilities. The grenade is also a sting ball grenade and is a less-lethal form of weapon, designed to reduce fatalities in civilians located in conflict areas. The munition is constructed to be low lethality, and capable of being launched from military and law enforcement 37 mm and 40 mm grenade launchers presently in use today. It is designed to be used in multiple roles when lethal projectiles are not a viable or preferred option, such as hostage situations, riots, room and building clearing operations, narcotics interdictions, distraction and diversionary purposes, and as a method of introducing a chemical agent into a small area from a distance. The grenade can be employed from distances over 400 yards, extending the range of the present art, which is 30 yards.
Owner:MR GEORGE LEROY CONFER
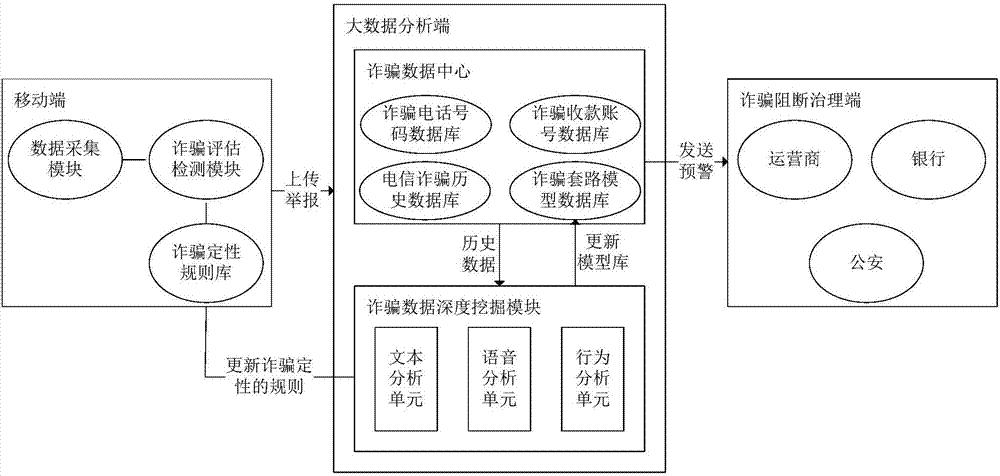
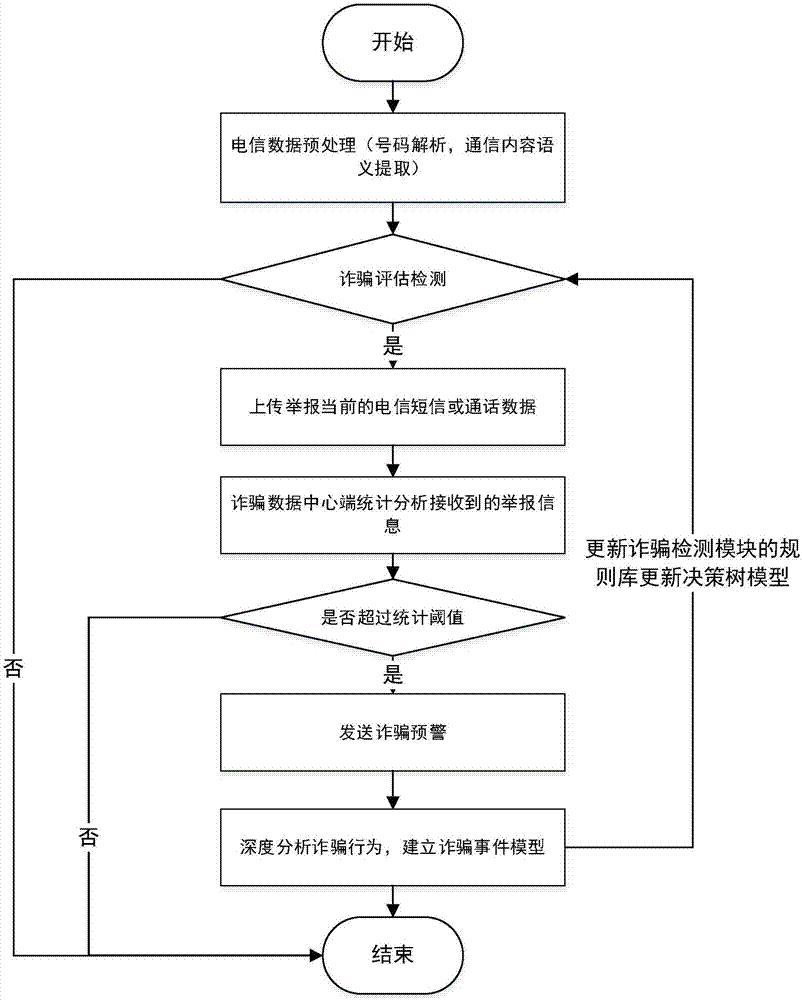
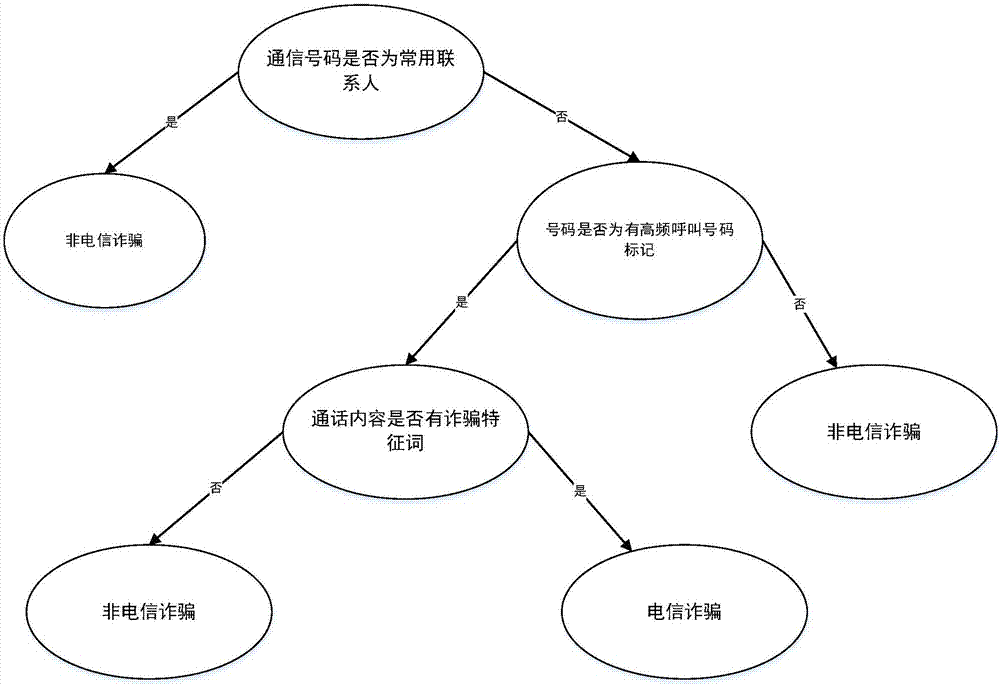
Telecommunication fraud prevention system and method based on big data and machine learning
InactiveCN106970911APrevent fraudulent incidentsCombating Telecom FraudSemantic analysisSubstation equipmentData informationMobile end
Owner:INST OF SOFTWARE APPL TECH GUANGZHOU & CHINESE ACAD OF SCI
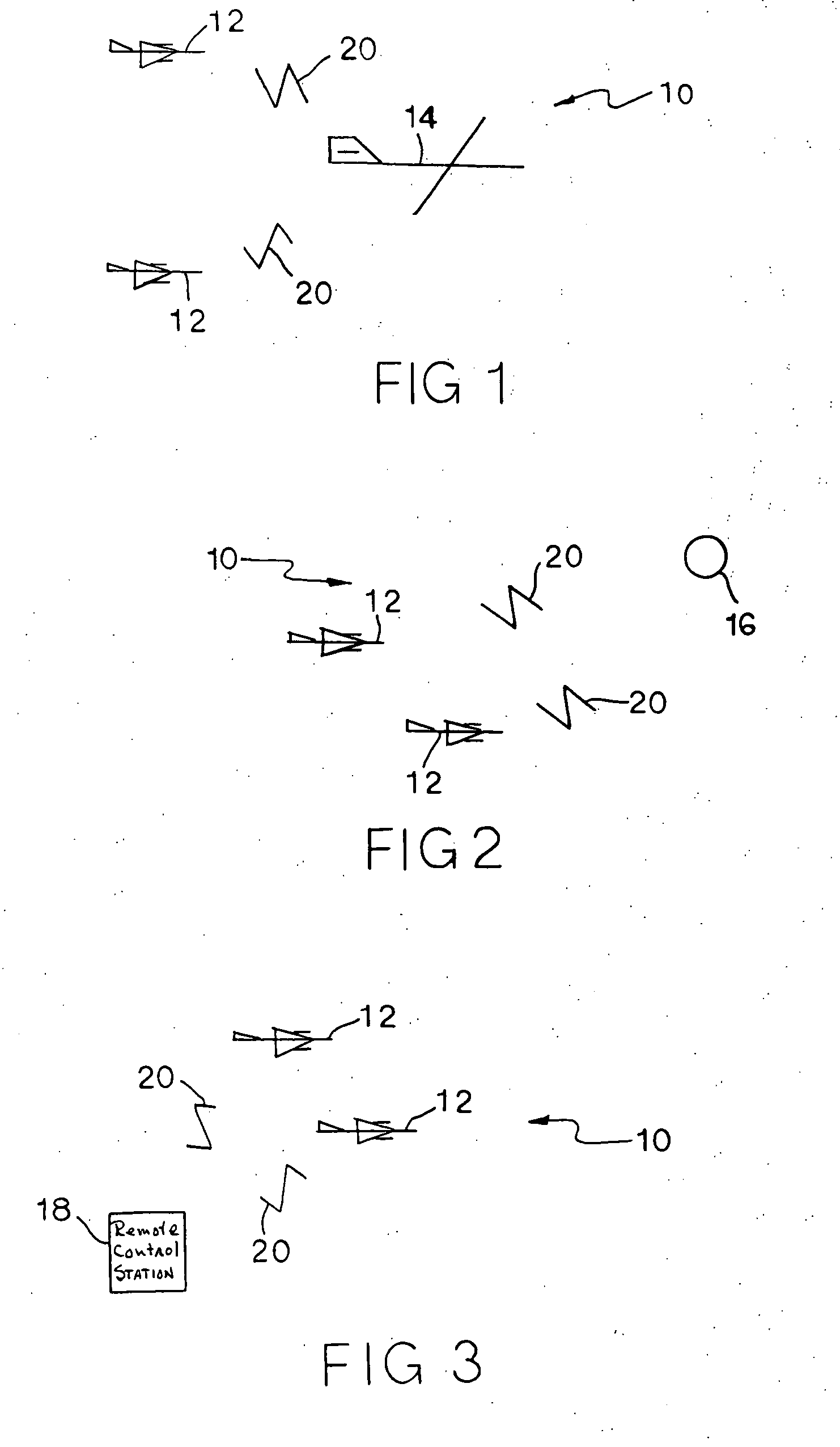
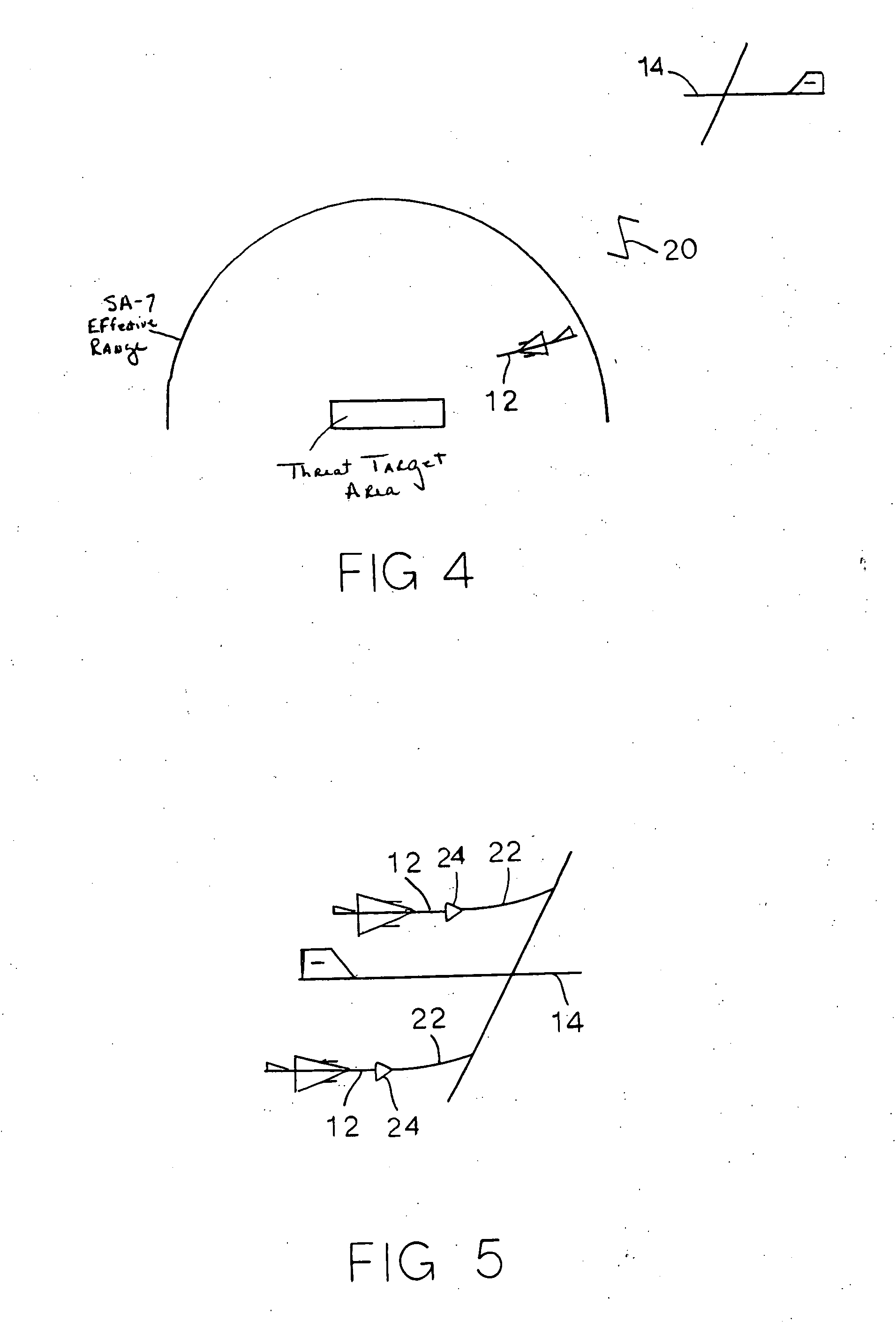
System and method for remote control of interdiction aircraft
InactiveUS20070023570A1Rule out the possibilityOvercome limitationsUnmanned aerial vehiclesActuated automaticallyFlight vehicleInterdiction
An aircraft attack interdiction system using an unmanned interdiction aircraft piloted using a remote control system. In-flight refueling system, weapons launcher systems and intelligence gathering equipment are mounted on the interdiction aircraft. A remote flight control operator to remotely fly the interdiction aircraft can be based on a remote flight control commander aircraft that can be flown at safe distances from targets that are attacked by the interdiction aircraft.
Owner:BERNARD CHARLES W
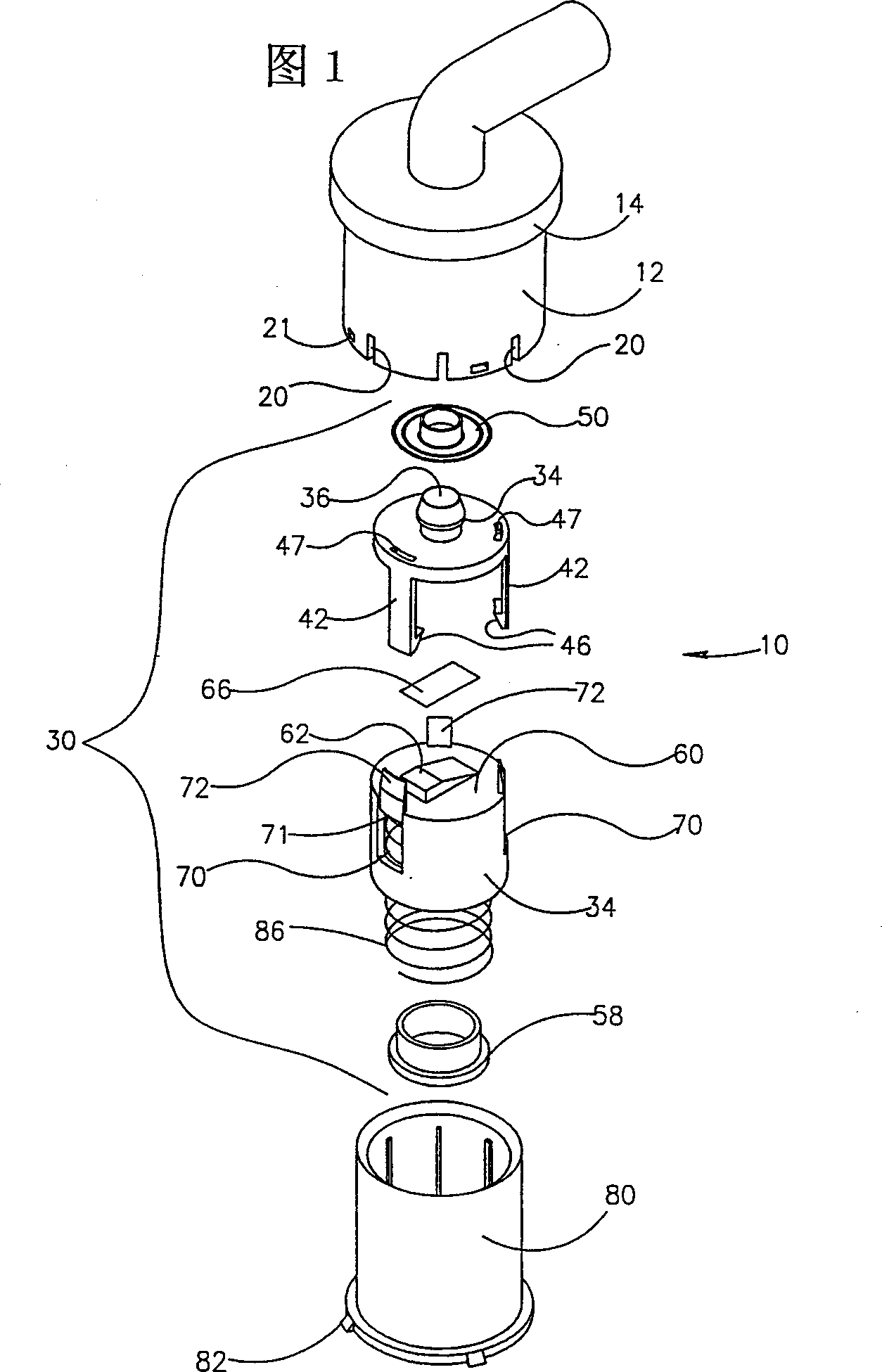
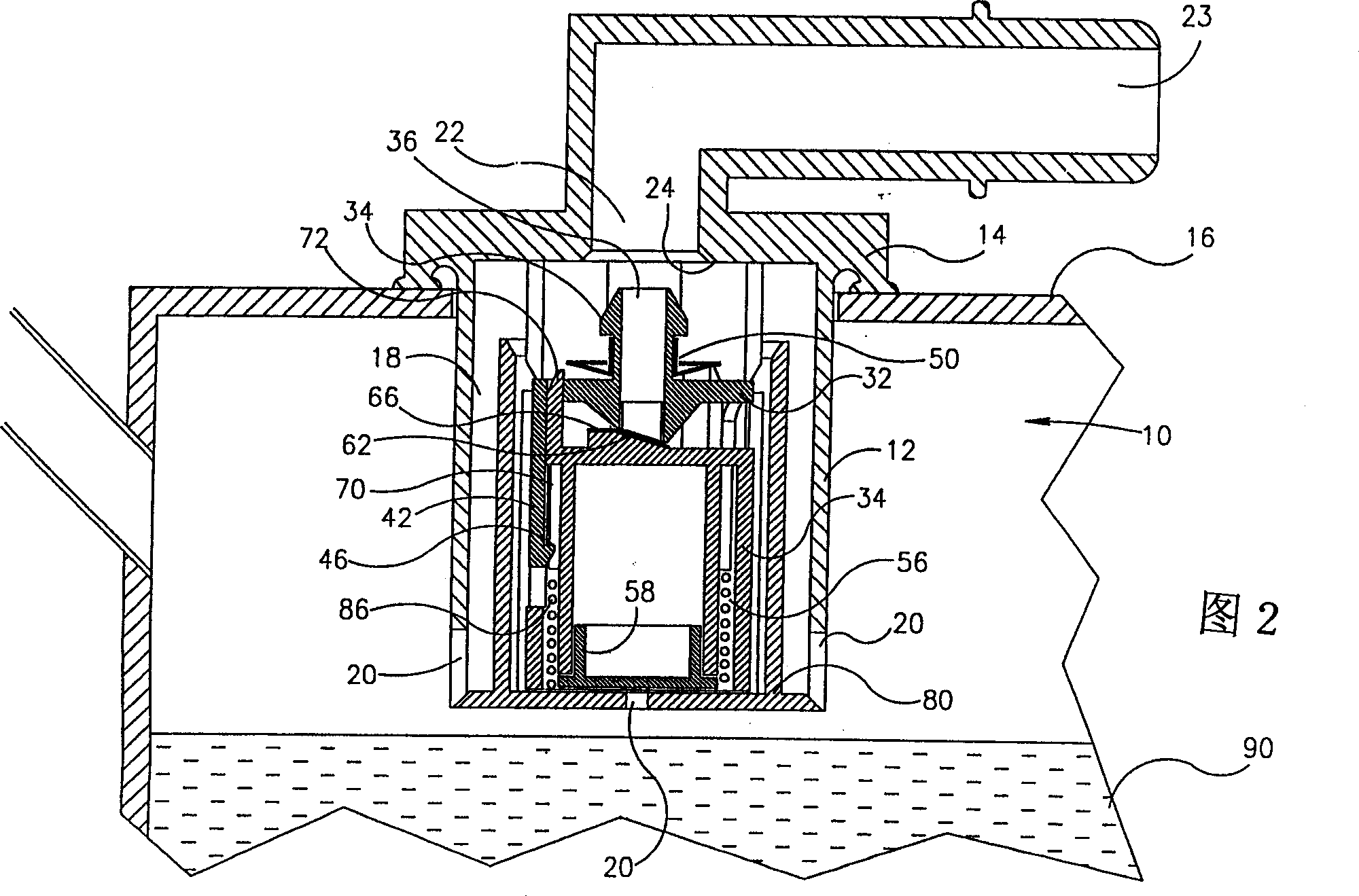
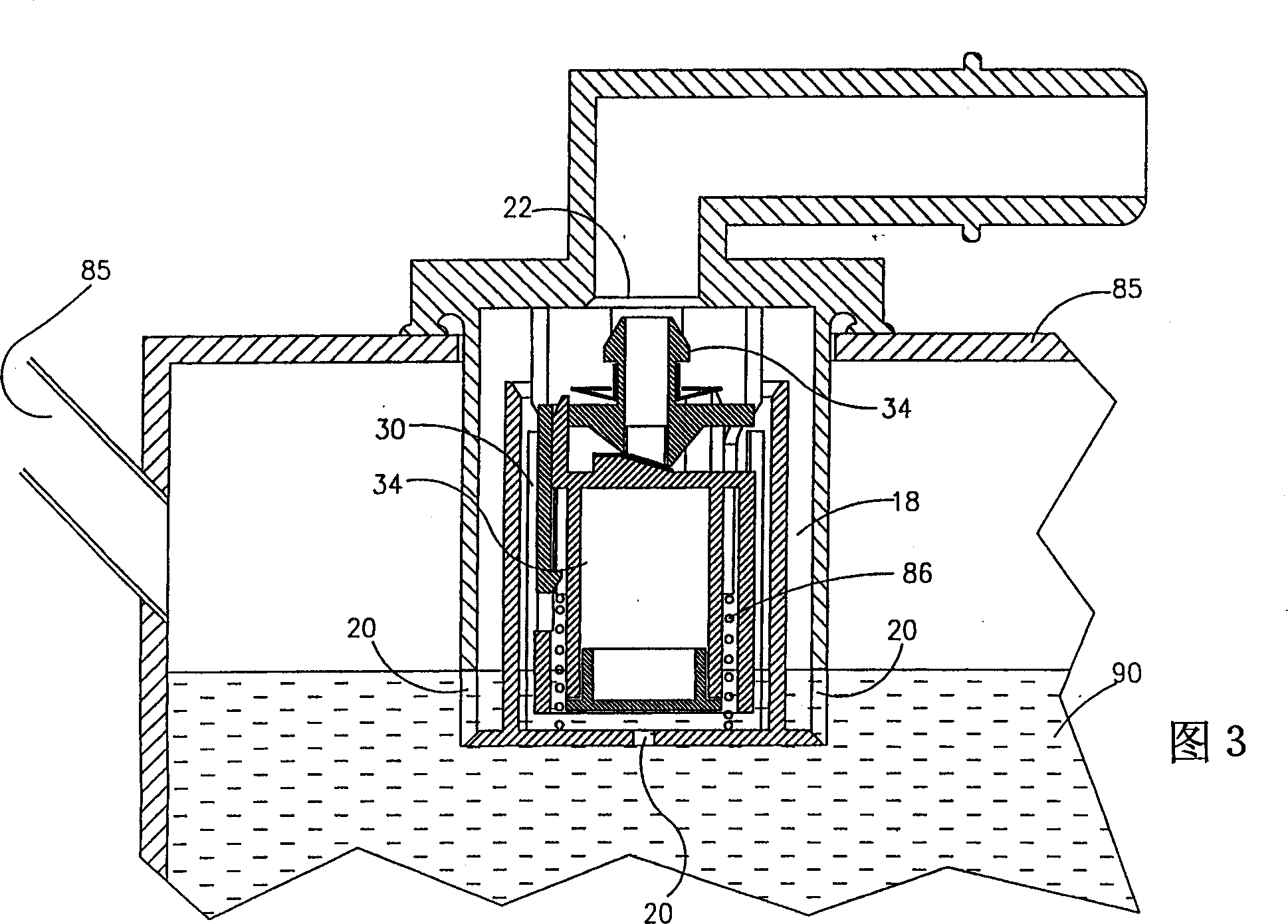
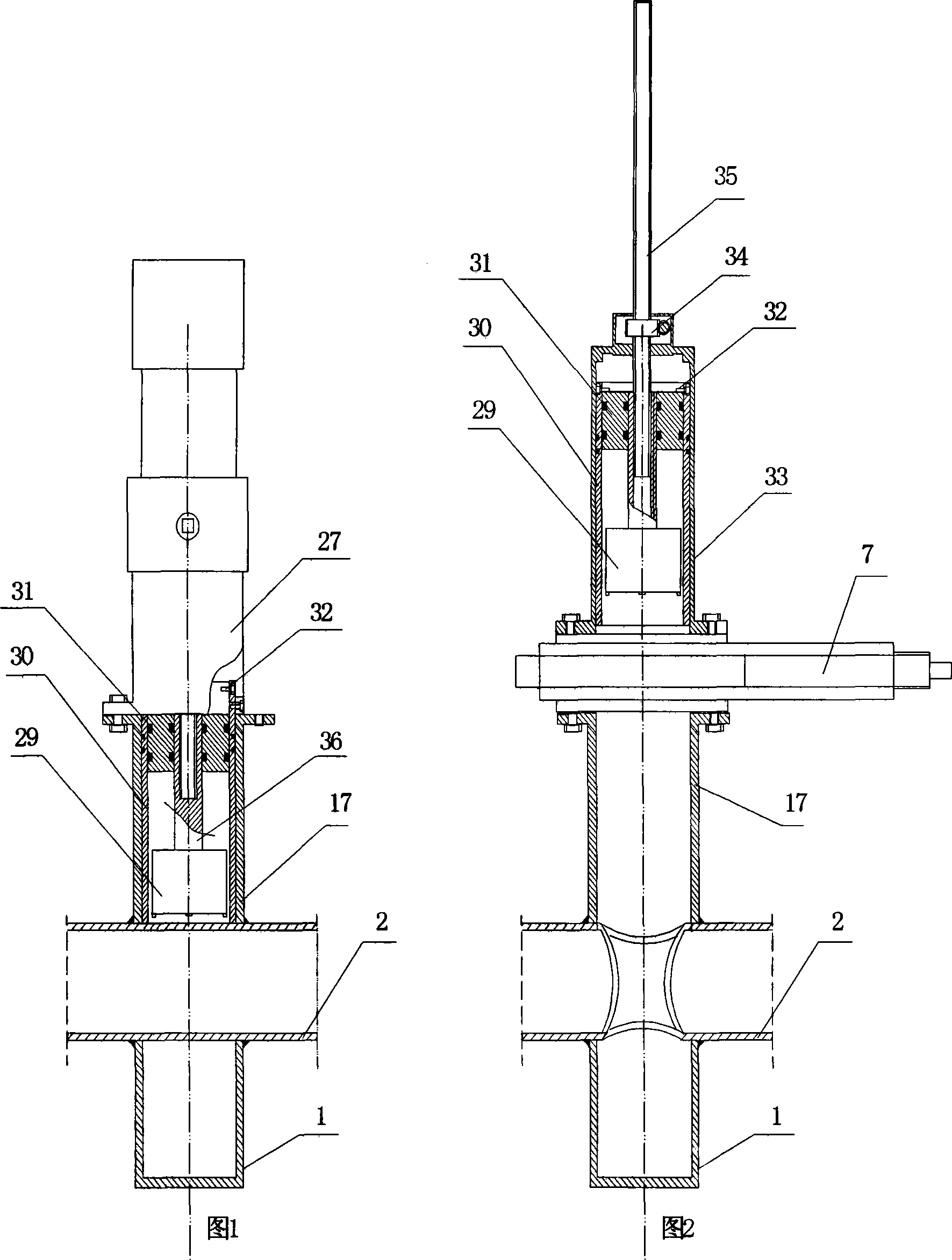
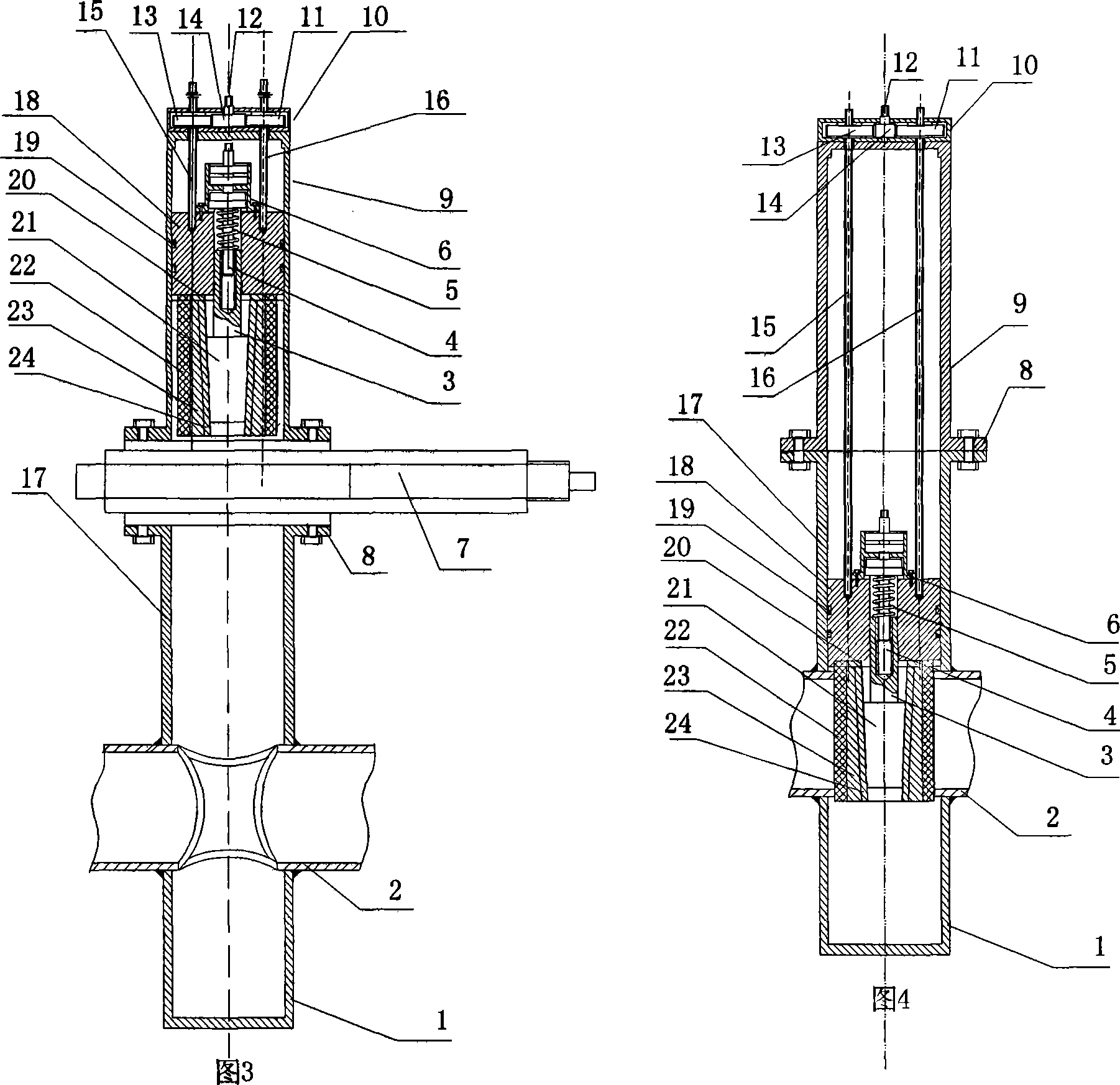
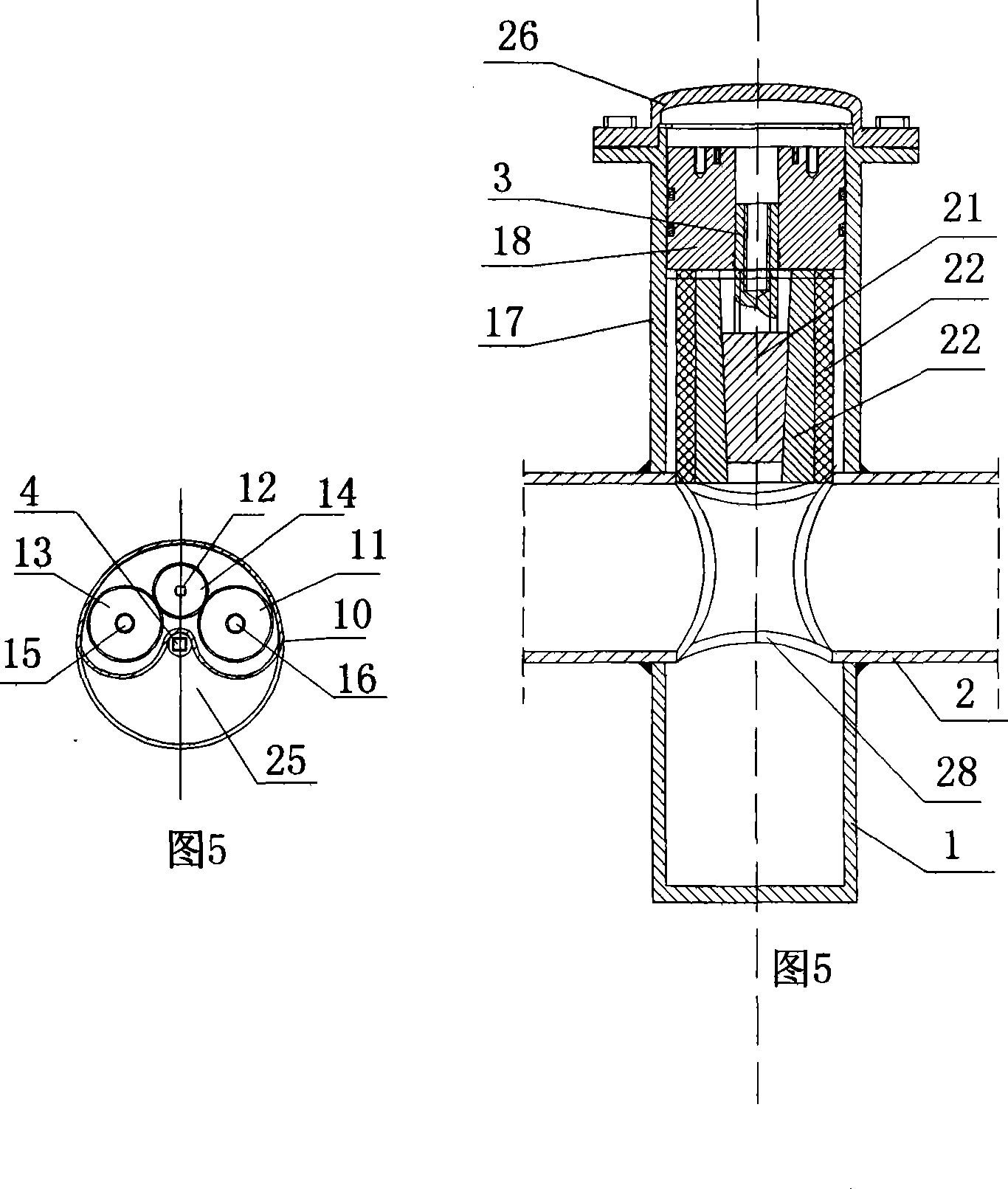
Over filling interdiction, vent and roll over valve
InactiveCN1349598AReduce the effective cross-sectional areaSoft closeElectric propulsion mountingEqualizing valvesInterdictionConfined space
An over filling interdiction and roll over valve (10) comprising a housing (12) defining a confined space (18) formed with fluid inlets (20), a fluid outlet port (22) at a top end of the confined space (18), and a valve seating (24) bounding the outlet port (22). A valve assembly is located within the confined space and comprises a first stage member (32) and a second stage member (34), both being substantially coaxially displaceable within the housing. The first stage member has at a bottom end thereof a substantially elongated slit-like inlet aperture (36), and at a top end thereof an outlet aperture being in flow communication with the inlet aperture. The first stage member is axially displaceable between a first position in which the outlet aperture progressively sealingly engages the outlet port of the housing, and a second position in which it is disengaged therefrom. The second stage member is a float fitted with a flexible closure membrane strip (66) anchored at one end thereof to a top wall (62) of the float member. The closure membrane faces the inlet aperture of the first stage member, and the second stage member is displaceable between a first position in which the closure membrane sealingly engages the inlet aperture, and a second position in which it is progressively disengaged therefrom. At least one anchoring member (42) extending between the first stage member (32) and the second stage member (34).
Owner:拉瓦尔农业合作社有限公司
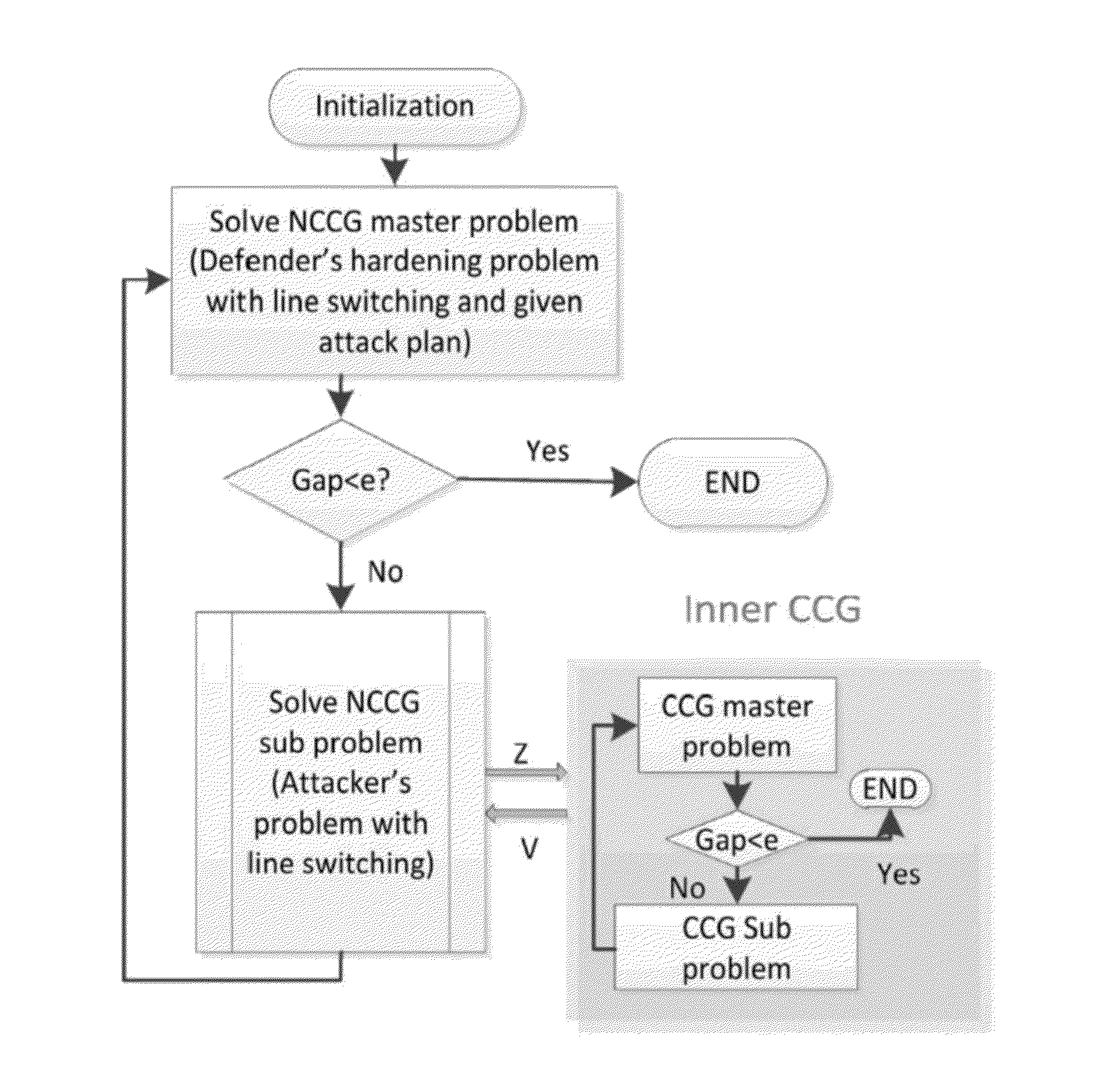
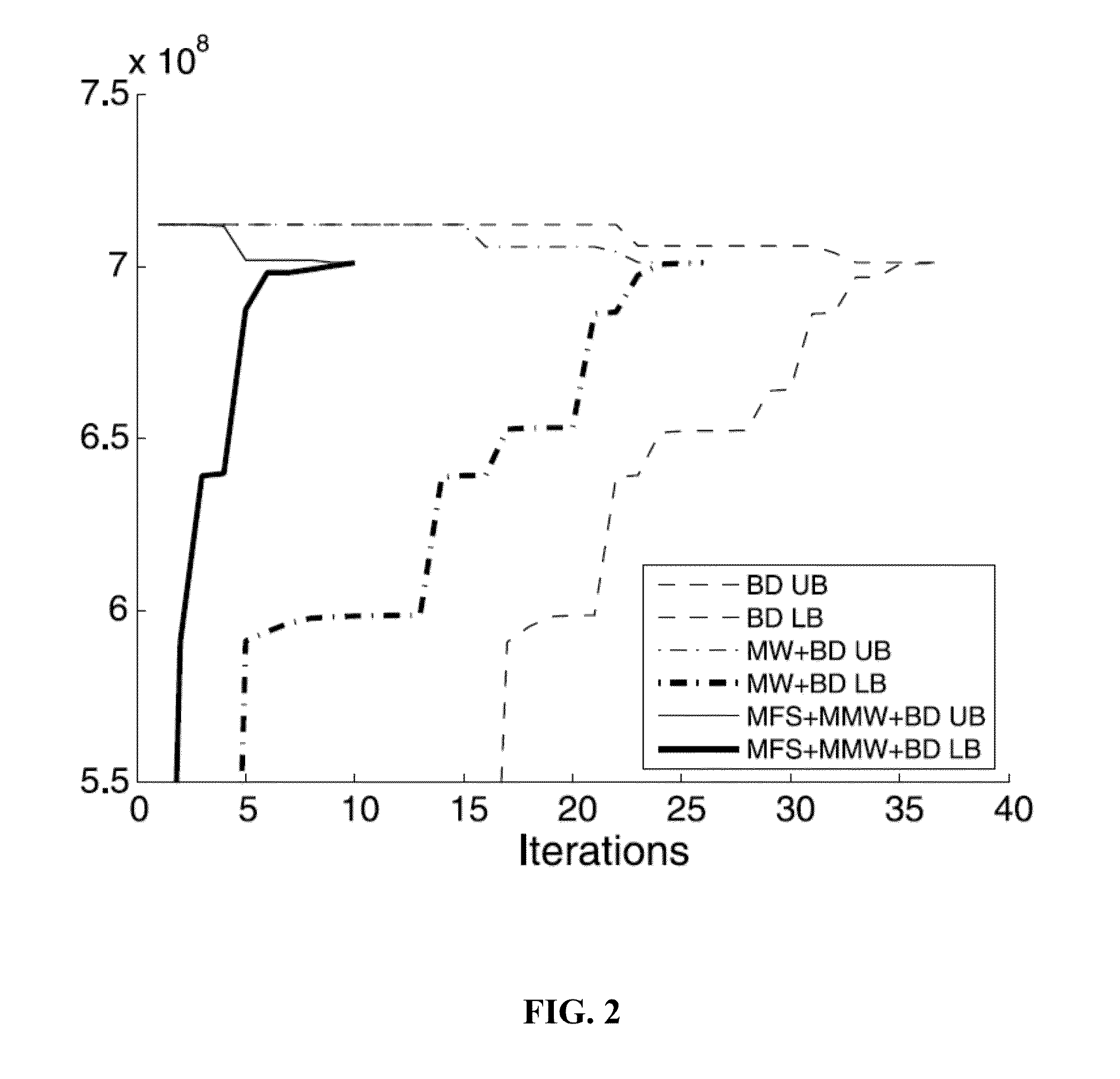
Methods and systems for computation of bilevel mixed integer programming problems
InactiveUS20160335223A1Improve computing efficiencyImprove processing capability and performanceComplex mathematical operationsDecompositionProgram planning
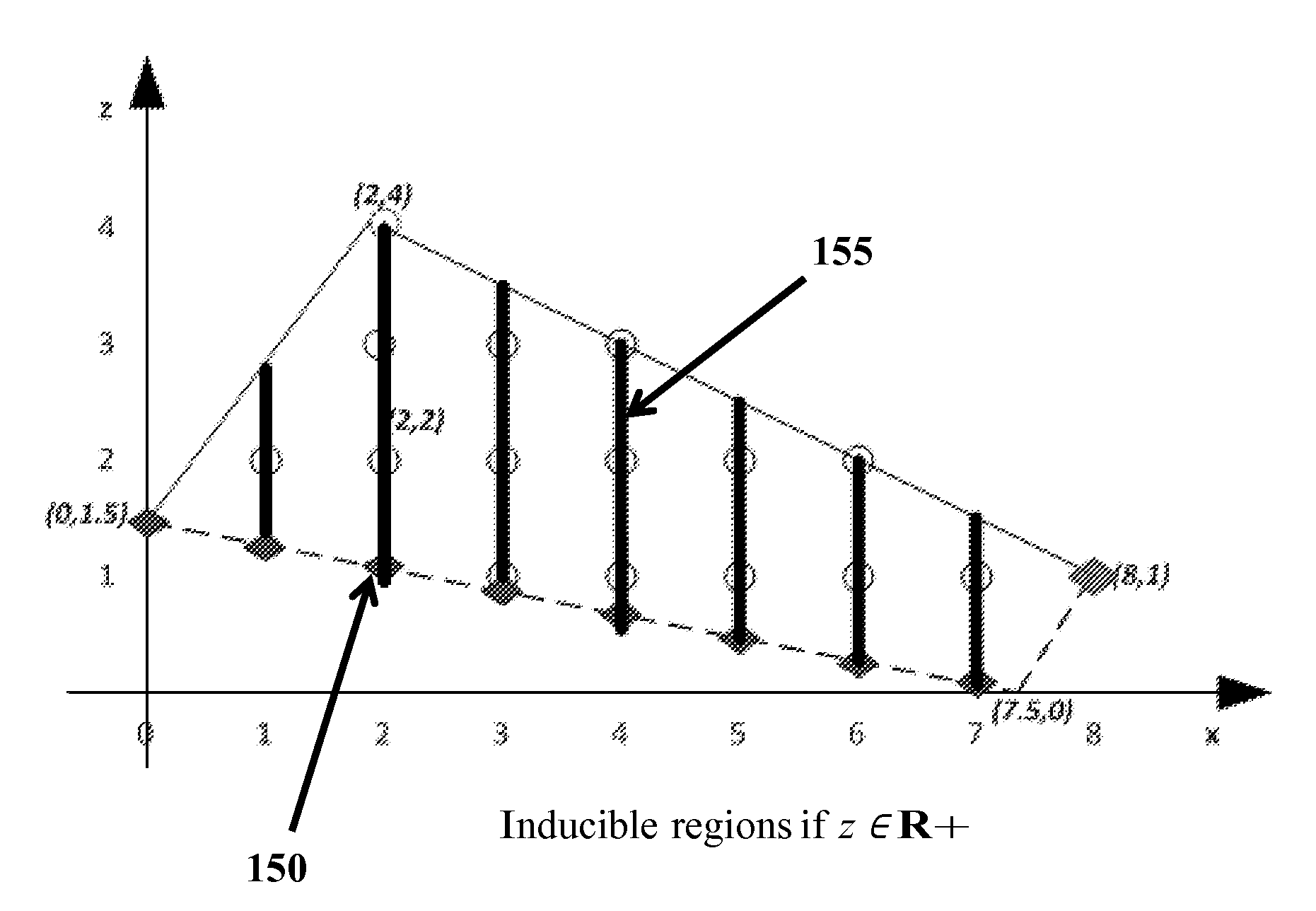
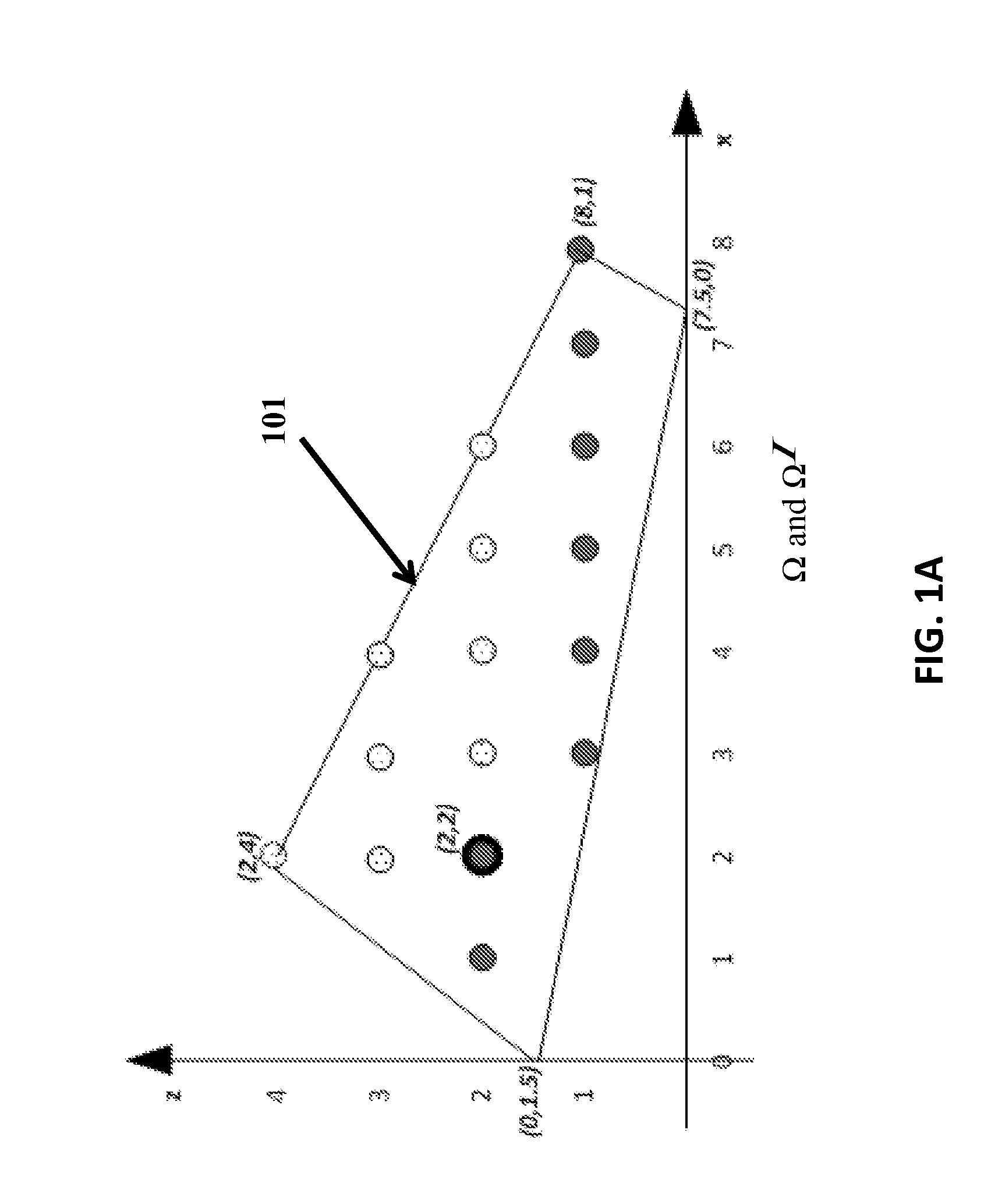
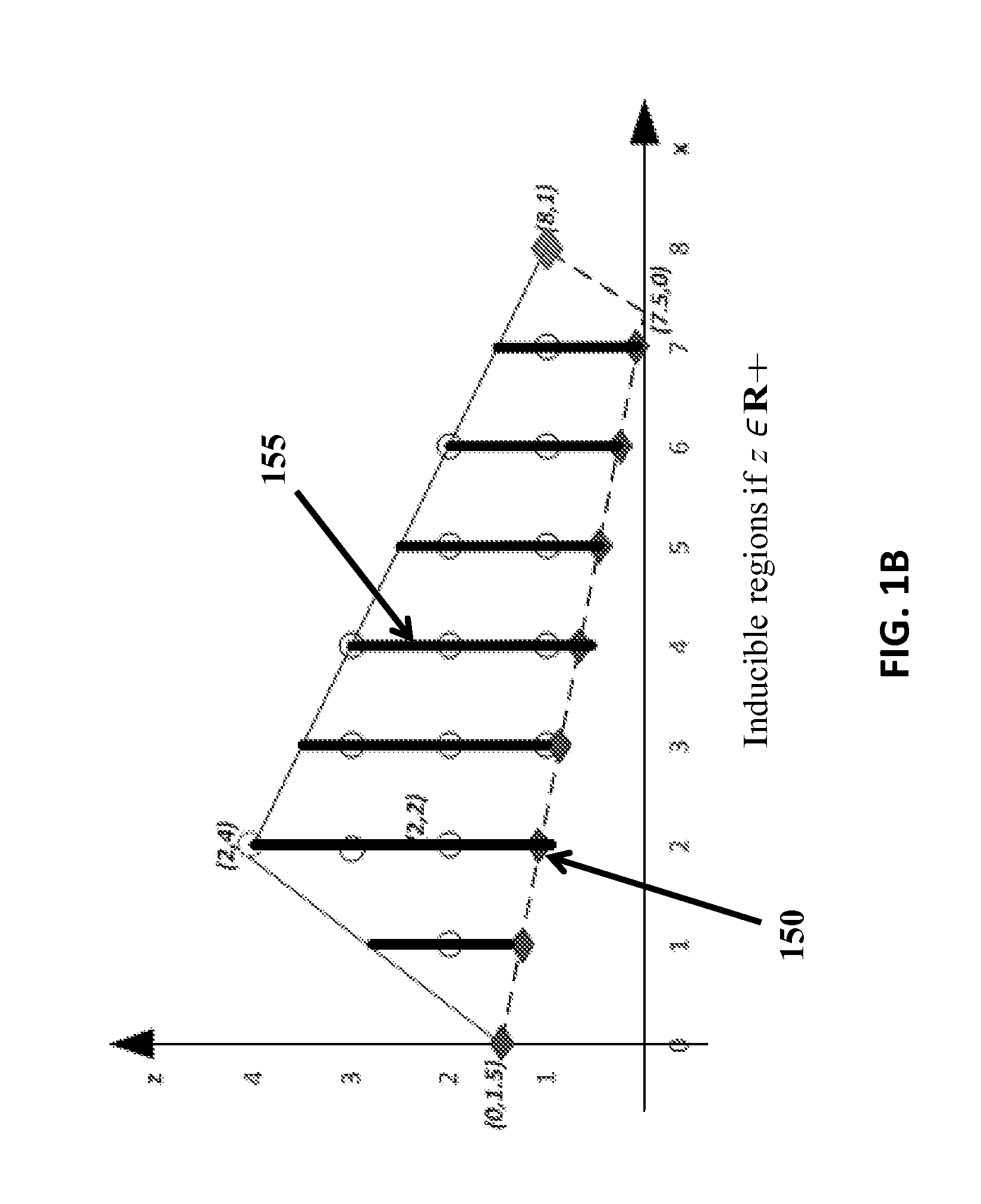
Techniques and systems are disclosed for improving the computation and solution of bilevel MIP problems. Various single-level reformulation techniques can be used to transform a bilevel MIP problem into soluble form. Decomposition techniques can be applied to the single-level reformulations to iteratively converge on an optimal or near-optimal solution. Some techniques described herein are operative within software applications for solving mathematical problems or MIP problems, and some are operable within an application programming interface or MIP solution service that other software components can access. In some cases, the techniques may be operative within domain-specific modeling software that solves, models, plans, or suggests actions in particular scenarios, for example power grid interdiction analysis and defense tools.
Owner:UNIV OF SOUTH FLORIDA
Column and constraint generation method for optimal strategies
InactiveUS20140258356A1Easy to solveStable supportComplex mathematical operationsComputation using denominational number representationPower gridParallel computing
Optimization processes, which are parameter driven for solving interdiction problems, for example, power grid interdiction problems, are provided. An algorithm of the subject invention can include column-and-constraint generation and can be used to solve a set of system interdiction, vulnerability analysis, and reliability based design problems, including a power grid vulnerability analysis problem and an edge-interdiction minimum dominating set problem. An algorithm can be provided on a computer-readable medium, a computer, a portable computing device, or other machine.
Owner:UNIV OF SOUTH FLORIDA
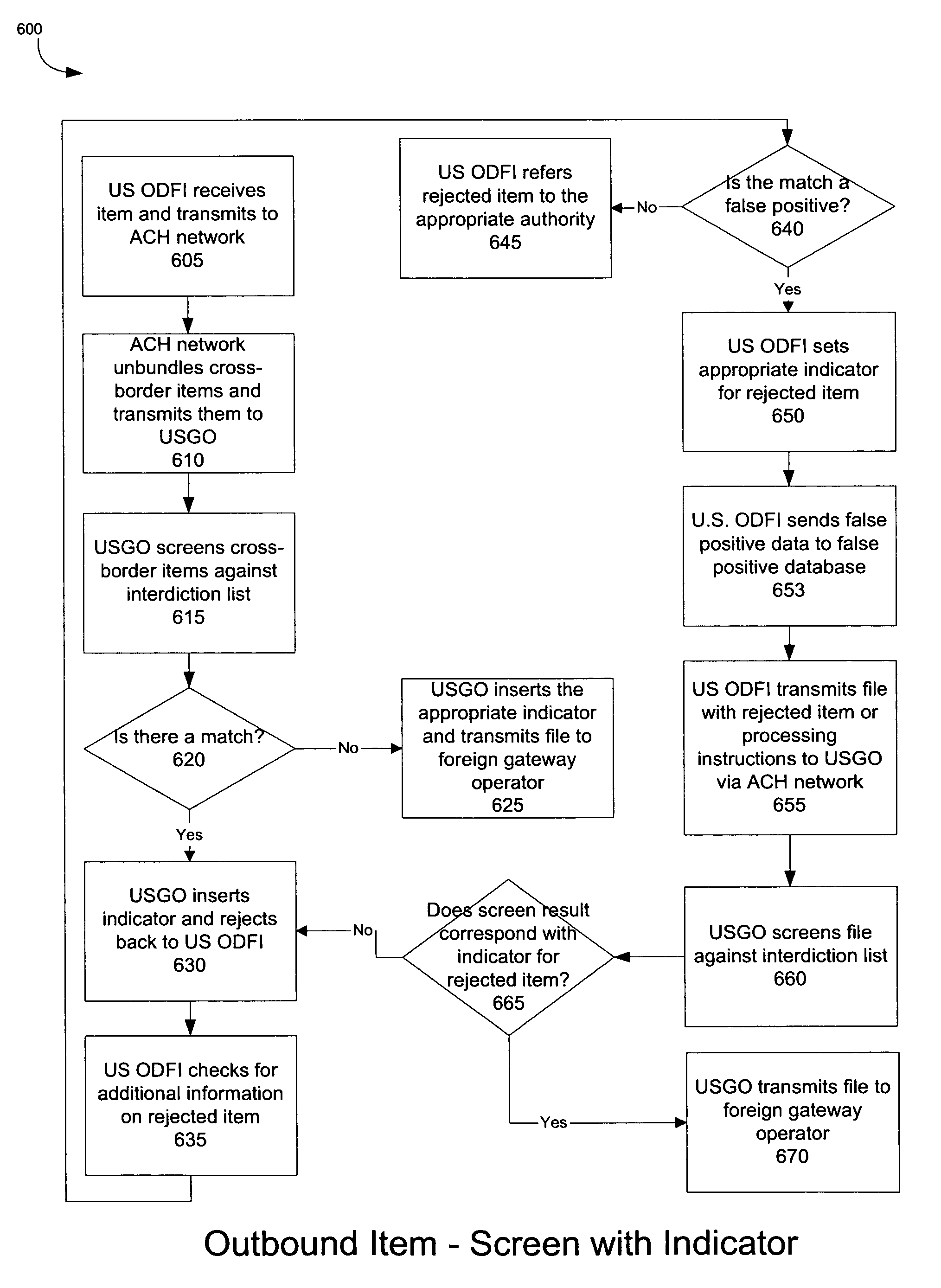
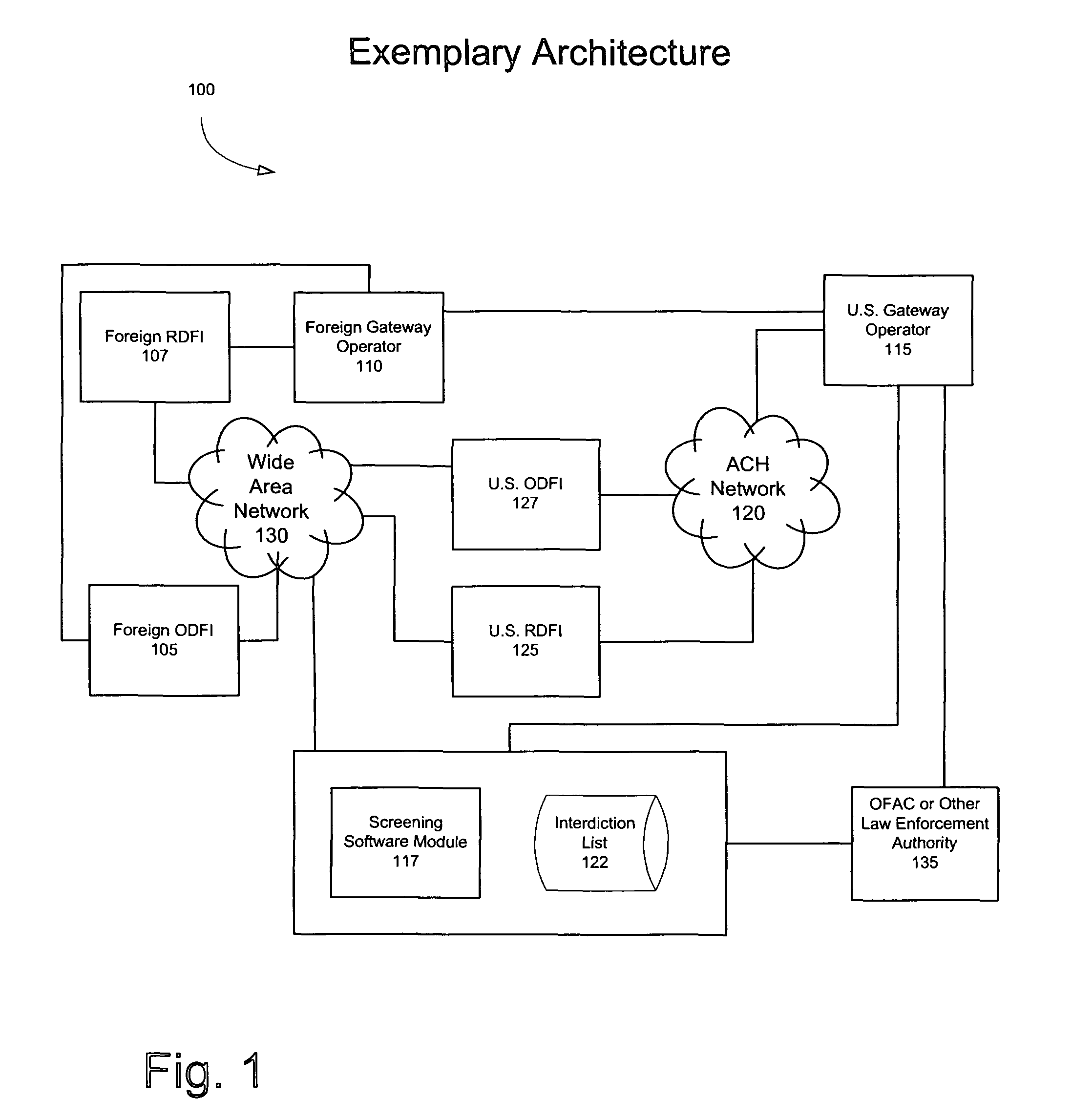
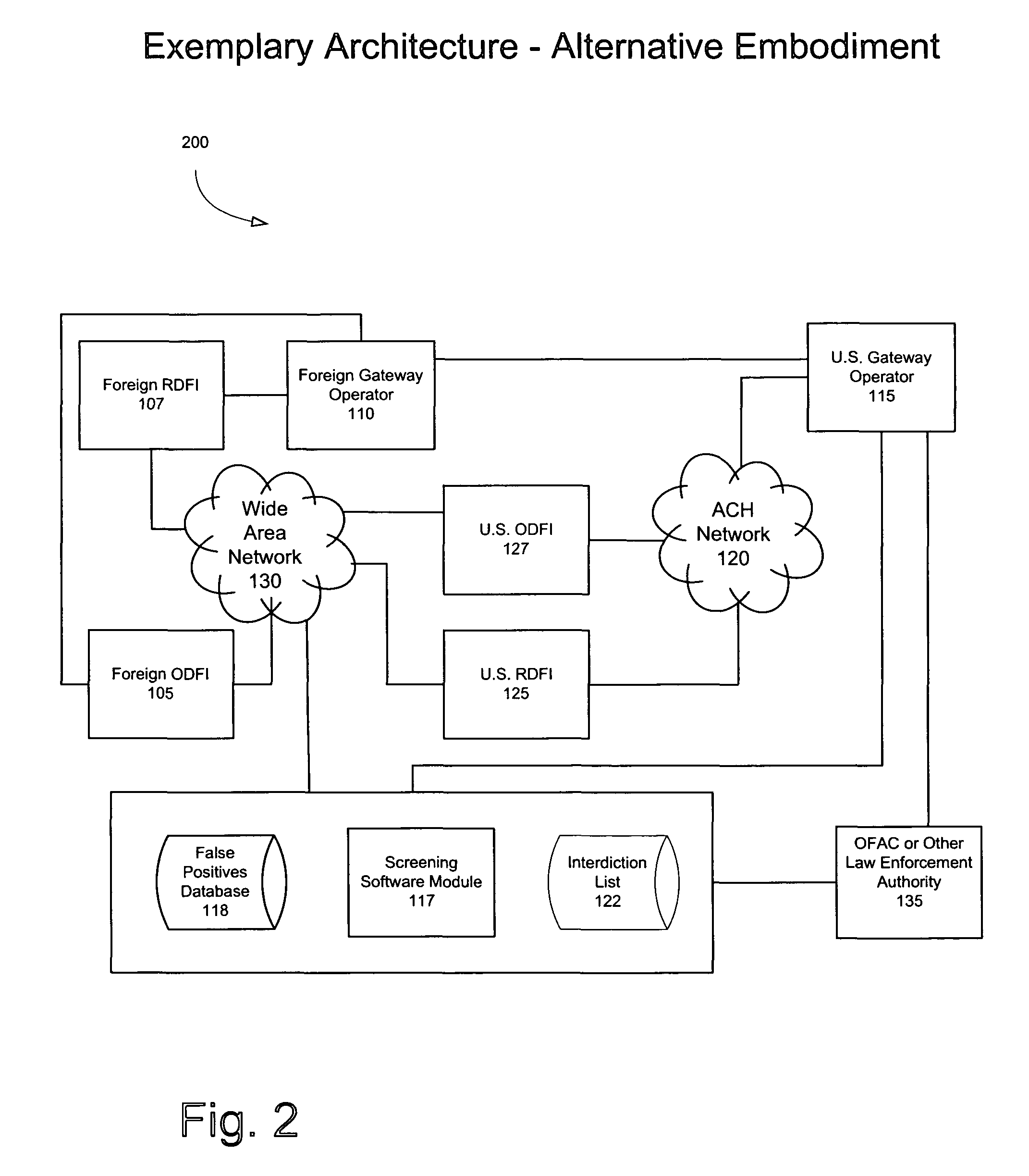
Method and system for screening financial transactions
ActiveUS7881996B1Efficient screeningMinimize screening errorFinanceProtocol authorisationFinancial transactionData mining
Efficiently screening ACH items and providing an indicator of the screening result. Electronic files, which can be in the NACHA file format, comprise ACH items. A gateway operator or an originating financial institution can screen each ACH item using a screening software module. For each ACH item, an indicator associated with the screening can be inserted into the ACH file before the ACH item is forwarded to a receiving financial institution. The indicator can identify whether the screening produced a match against an interdiction list and / or whether the screening produced a false positive. If the screening produced a match, processing of the ACH item can be suspended, and the ACH item can be returned to the originating financial institution. Notification of the match can be transmitted to the originating financial institution, the receiving financial institution, and / or law enforcement authorities.
Owner:US FEDERAL RESERVE BANK OF ATLANTA
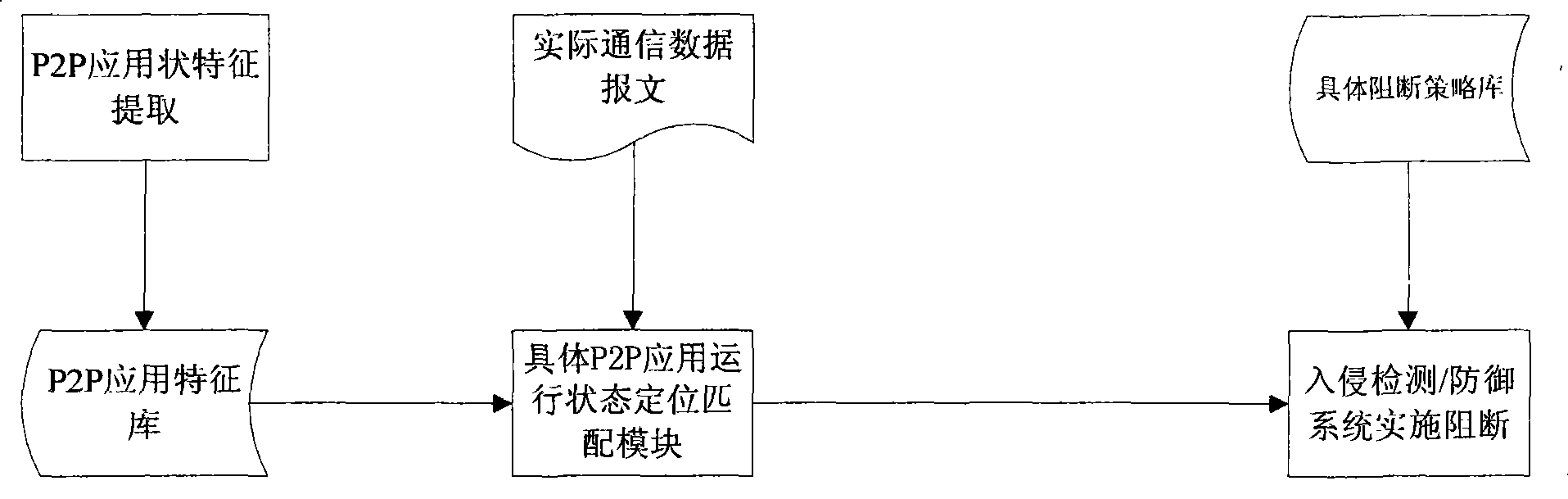
Method and system for monitoring P2P software
InactiveCN101442519AResolve accuracyImprove accuracyData switching networksNetworking protocolPattern matching
The invention relates to a P2P software monitoring method and a P2P software monitoring system capable of being used in network products. The method and the system can extract various protocol features during network protocol communication according to information carried by actually captured messages, so as to realize monitoring of P2P application, and can implement interdiction of different strategies according to actual demands and aiming at different running states. The method and the system comprise three stages of establishment of a protocol feature model, application stage identification and positioning, and implementation of corresponding interdiction strategies, wherein a module for establishing the protocol feature model works out matching features of specific states of detailed P2P application; an application stage identification and positioning module realizes positioning of application states and protocol states affiliated to detailed data messages in the multi-pattern matching mode; and a corresponding interdiction strategy module realizes establishment and correlation of related strategies and corresponding monitoring function.
Owner:BEIJING VENUS INFORMATION TECH
Predictive analytic method and apparatus
InactiveUS7822747B2Digital data processing detailsKnowledge representationProject managementRelational view
A computerized project management analytical system and method that develops and manages an ontology that links objects and is capable of being mined. The ontology is comprised of a project ontology framework, a matching engine and a project status matrix that illustrates a multi-relational view of the project status, of confidence levels, or interdiction points and / or positions on project timelines.
Owner:METIER
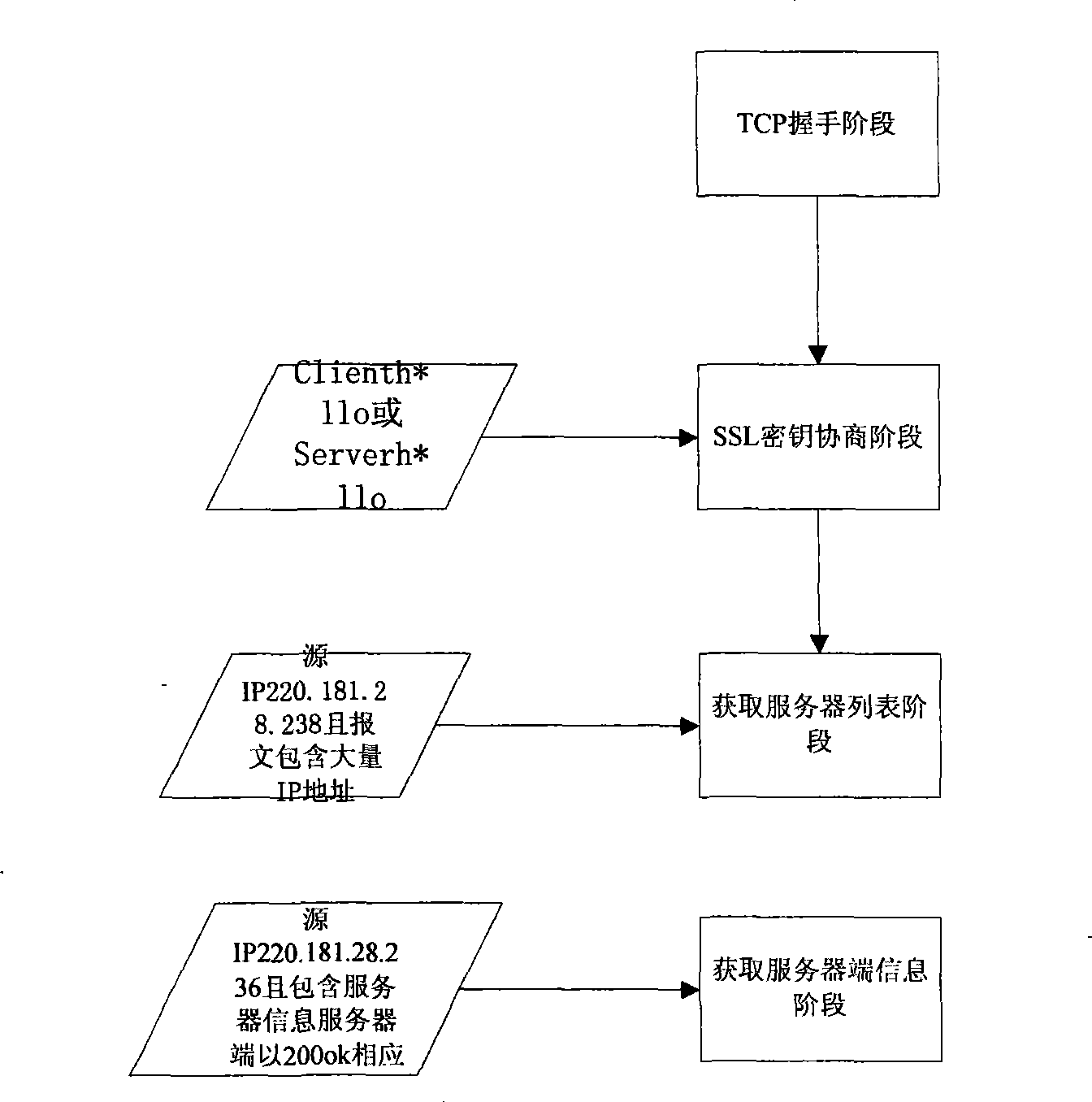
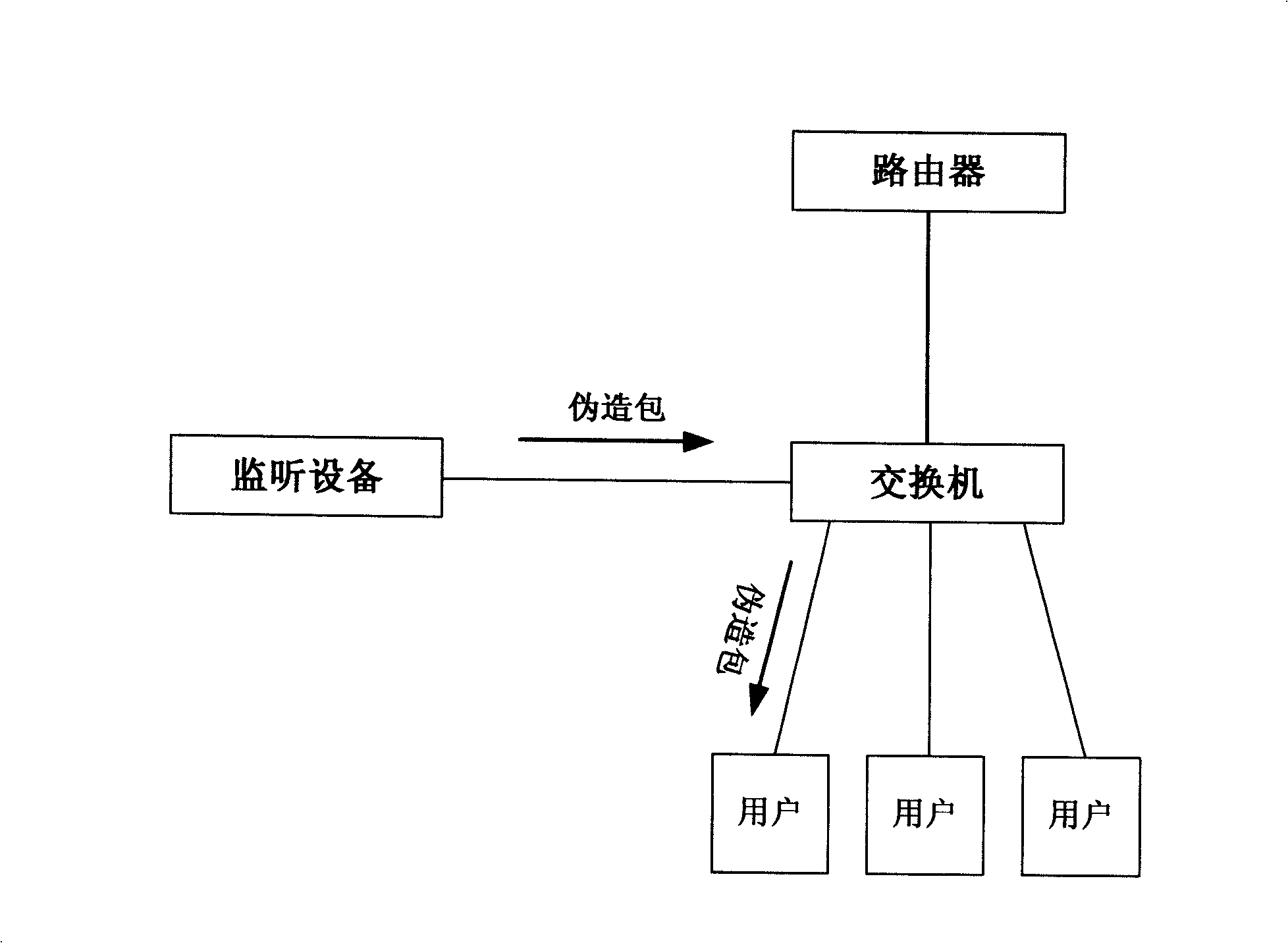
By-path interdiction TCP connection
The present invention provides a method, which is used for blocking TCP connection of a network in the bypass way. The method can be used in the fields of network security, network management, network access control, and so on. A monitoring device is arranged in a local area network, which is used for monitoring for the network through a hub or the mirror port of an exchanger. When the connection of a TCP needs blocking, an imitative TCP data packet with a RST sign is assembled according to the monitored information of TCP connection; the data packet is then directly transmitted to a link layer. The machine which has the connection to be blocked receives the imitative TCP data packet, and considers that the other end of the connection has transmitted the information of resetting the connection. According to standard protocols, the operating system can automatically disconnect the TCP. Thus the application program with the connection can be disconnected, which achieves the purpose of blocking the illegal network visit.
Owner:莱克斯科技(北京)有限公司
Interdiction method and device with press pipe
The invention provides an interdiction method and device for a pressurized pipeline. The device consists of a slag collecting tube, a process tube, a reblading device, a pipeline pressurized tapping machine and a pipeline blocker. The pressurized pipeline consists of an upper welding process tube, a lower welding process tube and the slag collecting tube. The process tubes are arranged above the slag collecting tube. The upper end of the process tube is provided with a flange and is connected with flanges at the lower ends of the tapping machine, the reblading device and the pressurized pipeline blocker through the flange. Compared with the prior art, the welding type pressurized pipeline blocker has excellent effects of realizing the pressurized connection of branch pipes and the pressurized connection of bypasses, the pressurized replacement of valves, the pressurized replacement of pipelines, as well as the maintenance and replacement of the pressurized pipelines, with no need of depressurizing pipelines or stopping production and no effect on the normal medium transmission of the pipelines. The invention is convenient, portable and has the advantages of low cost and high security, solving the unsolved world difficulty of the pipeline maintenance and pressurized construction, thus having excellent popularization and using values.
Owner:济南市公明新技术开发有限公司 +1
Environmental risk management system and method
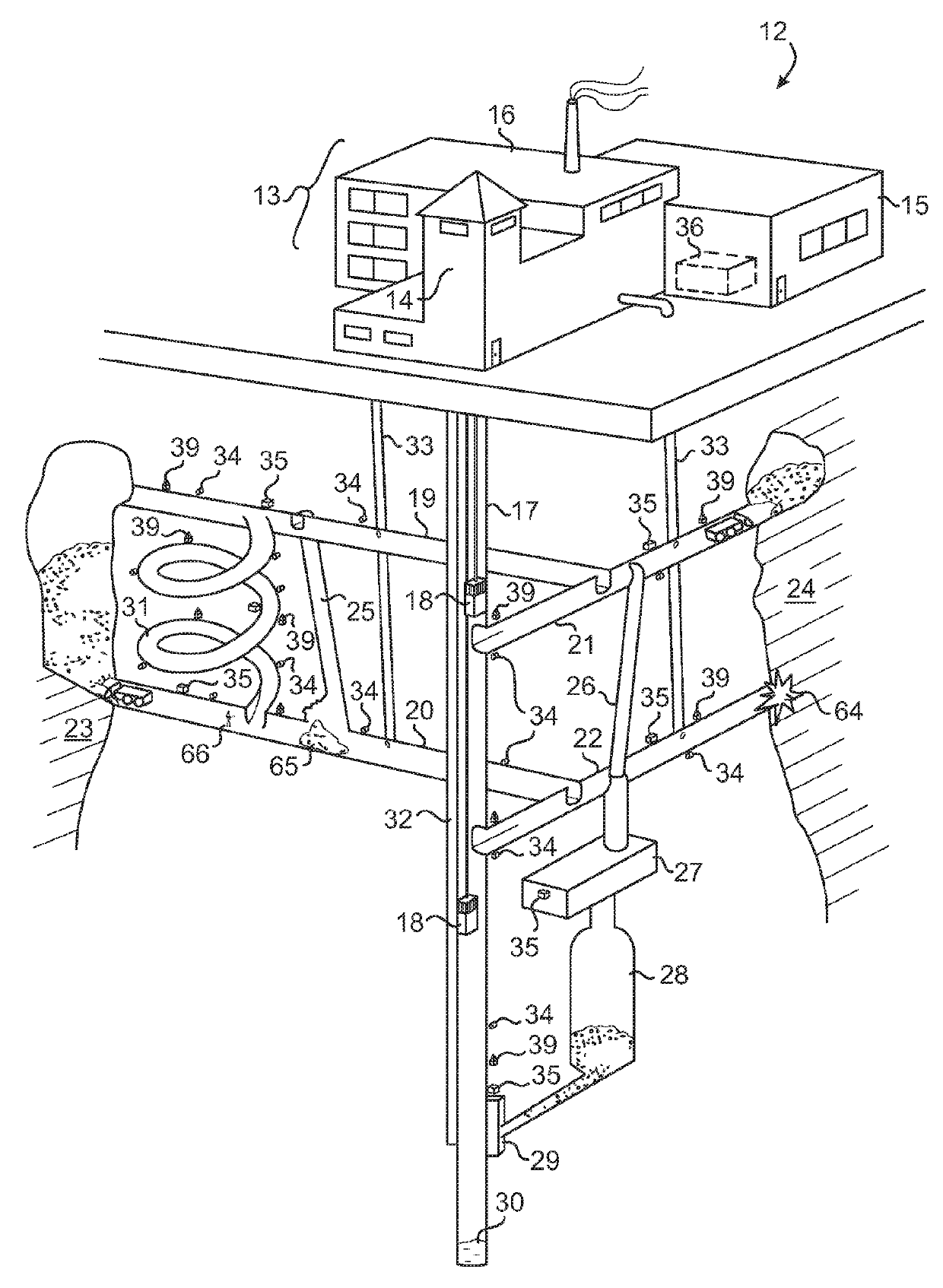
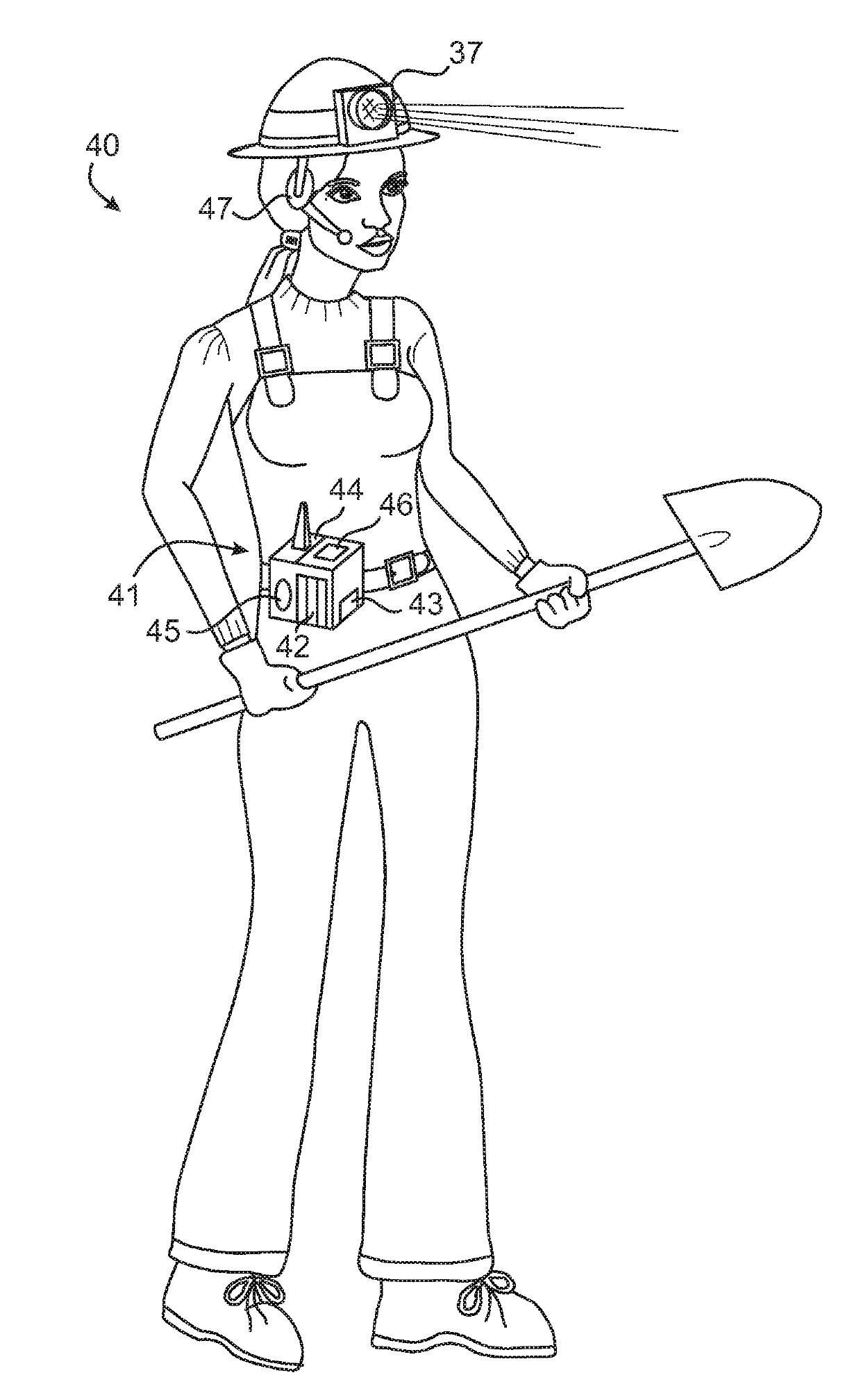
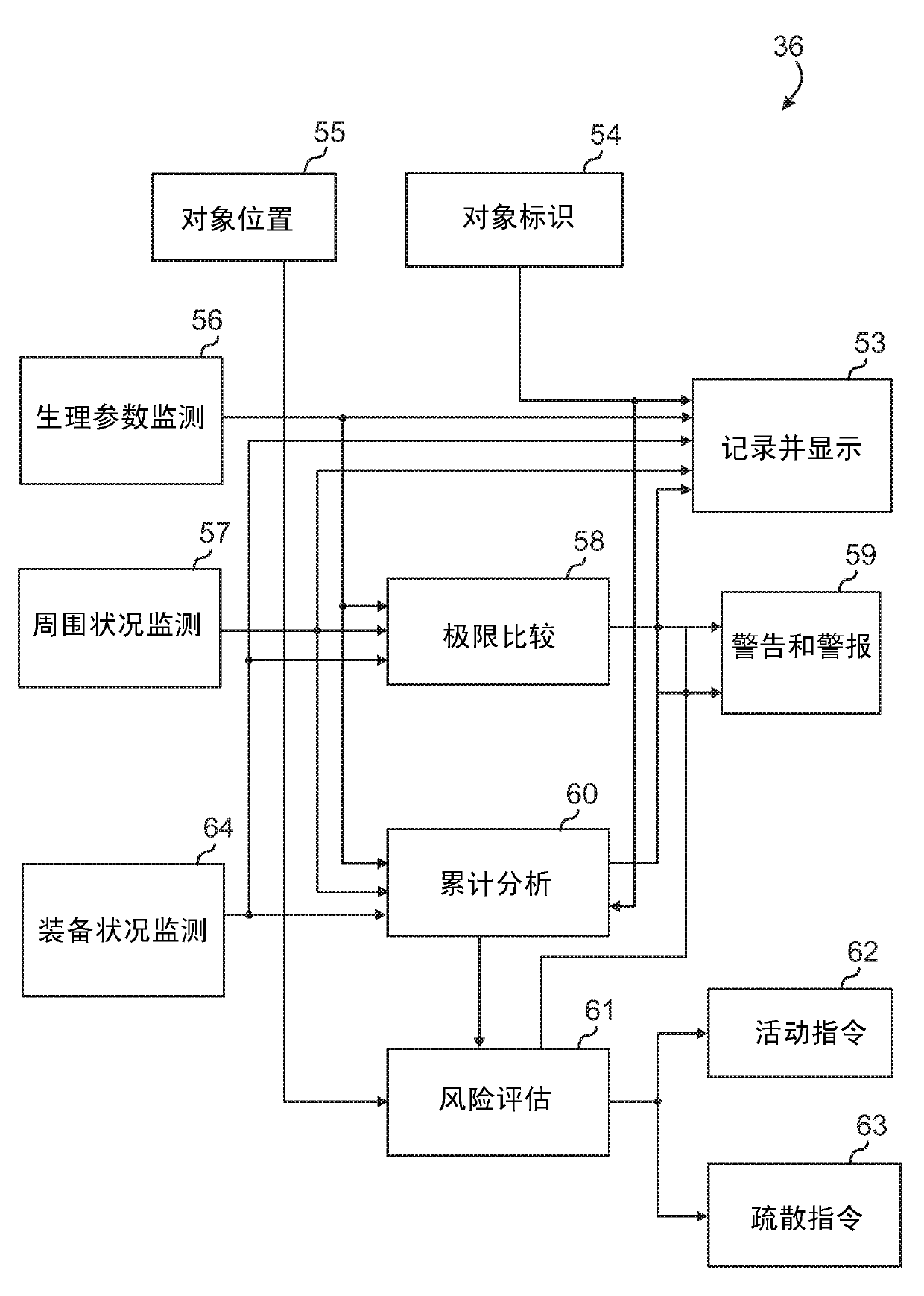
A system and method for directing and monitoring the whereabouts of persons within an environmentally hazardous area includes equipping each person with devices for monitoring personal physiological conditions (56), equipment conditions (64), topographical locations (34), environmental conditions (57) and other pertinent data. The data are individually encoded and uploaded to a processing center (36) where they are analyzed (58,60,61) in order to ensure compliance with health or environmental norms and safety regulations, generate hot-spot mapping (53) and to issue real-time risk avoidance behavior directives (62), worker, mechanism and material traffic directions, warnings (59), permissions or interdictions.
Owner:HONEYWELL INT INC
Electromagnetic personnel interdiction control method and system
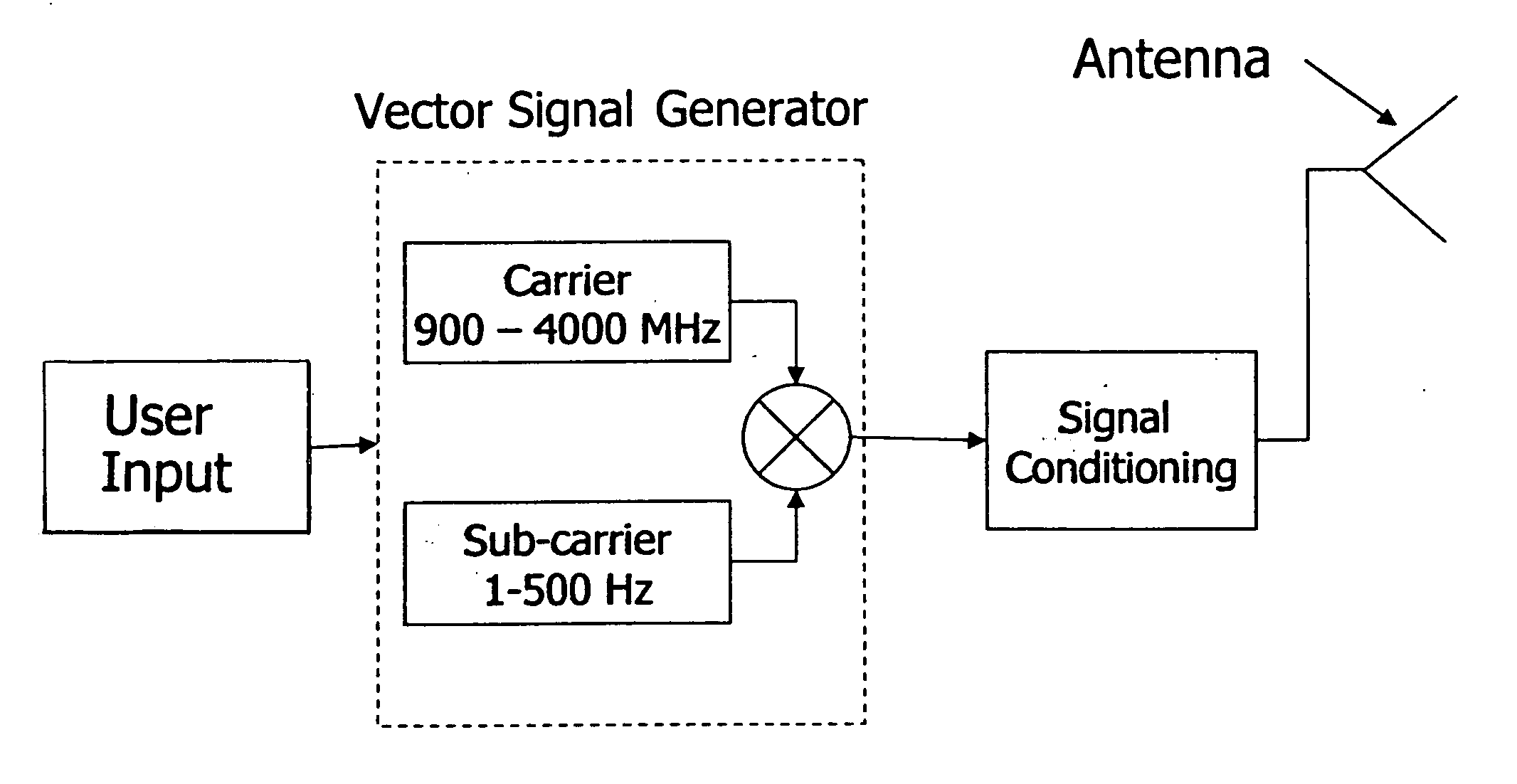
An electromagnetic personnel interdiction control (EPIC) non-destructive stun type weapon system and method utilizes beamed RF energy (Lorentz Force) to disrupt the normal mechanical transduction process and / or the chemical engine by which sound, position and other sensory input are converted to messages by nerve cells and processed by the brain to produce complete disorientation, confusion, and temporary incapacitation sufficient to temporarily and remotely render a human powerless to resist arrest or subjugation. Removal of the RF electromagnetic energy will leave the nerve cells and surrounding tissues with no damage and the second order effects of severe motion sickness and the psychological effects of “helplessness” remains until the body chemistry returns to normal.
Owner:INVOCON
Non-volatile semiconductor storage device
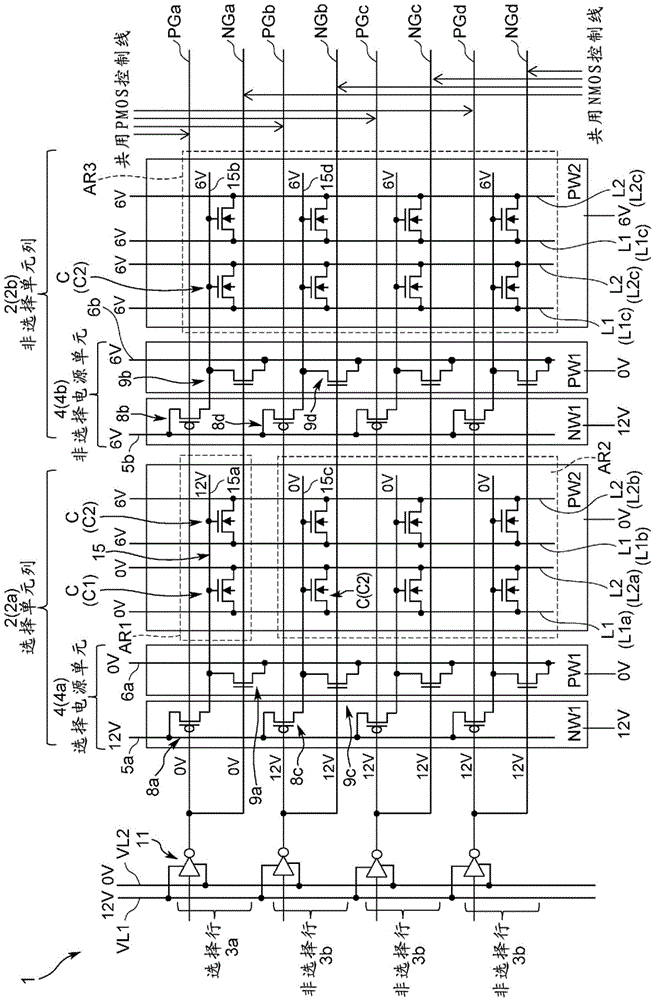
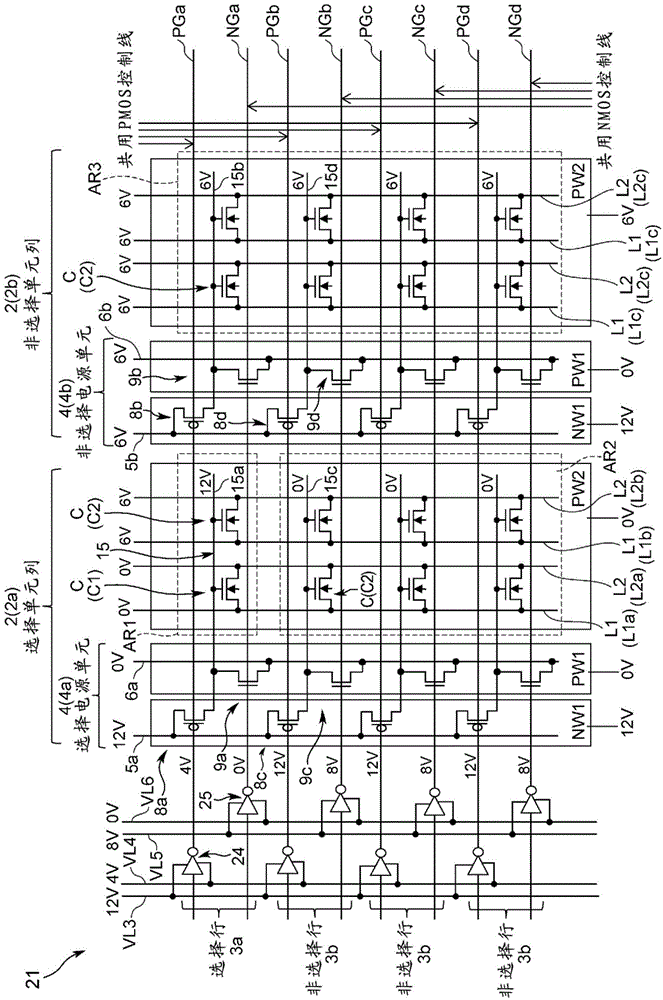
ActiveCN104380387AInhibition voltage valueMiniaturizationRead-only memoriesAddress decoderControl line
Proposed is a non-volatile semiconductor storage device with which, while effecting miniaturization, it is possible to suppress a disturb occurrence better than before. In a non-volatile semiconductor storage device, forming a plurality of words in a matrix, disposing a power source unit for each word line column (memory well), imparting a different unit voltage to each power source unit corresponding to whether a selected memory well is present in a given word line column, switching on a word line unit basis a switch mechanism of each power source unit according to a control line voltage value, and individually imparting to each word line either a charge storage gate voltage or a charge storage interdiction gate voltage, it is possible to freely set for each word line column a charge storage interdiction gate voltage value or a bit line voltage value which is capable of suppressing a disturb occurrence. A plurality of power source units are connected to a common control line in the row direction, obviating the need for a separate address decoder for each word column line, and allowing effecting miniaturization.
Owner:FLOADIA
Agent based modeling of risk sensitivity and decision making on coalitions
An agent based model system provides simulation of the influence of environmental variables and tendencies in individual and social decision making relating to the formation of coalitions and ethnic groups. The system is based on improved understandings of human decision making under risk, and incorporates recent theoretical developments and computational tools. The system gives analysts the ability to predict the development of coalitions and ethnic groups, as well as the ability to manage the behavior of individuals in such groups. The model results provide confidence intervals for various possible scenarios in a mix of agents' decision rules and distribution of environmental resources. Applications include management of ethnic groups and violent conditions in unstable nations, the tracking of terrorist organizations, development of coalitions and oligopolies in business, and the modeling and interdiction of criminal organizations.
Owner:PURDUE RES FOUND INC
Processing method for redundancy checking of ring network
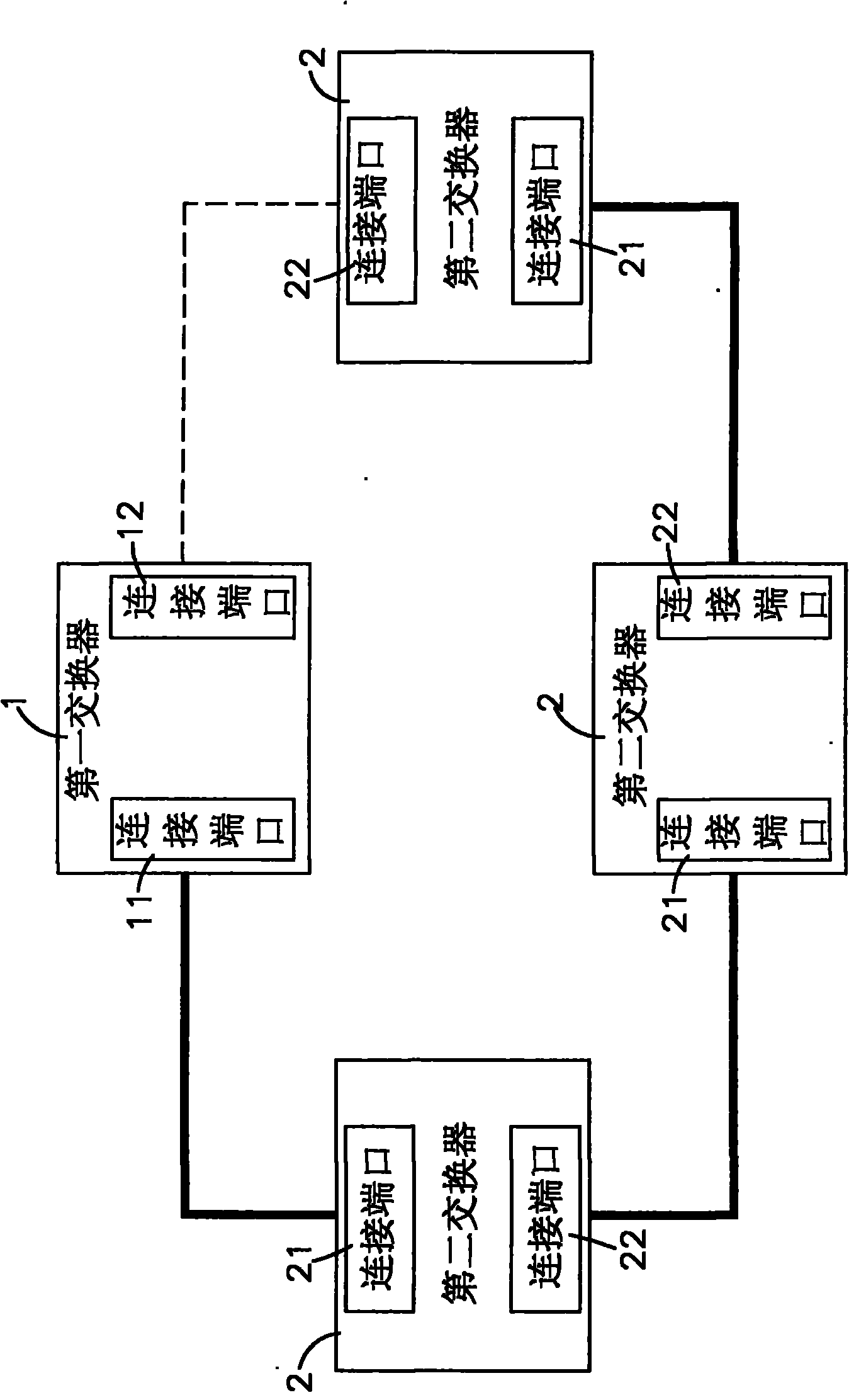
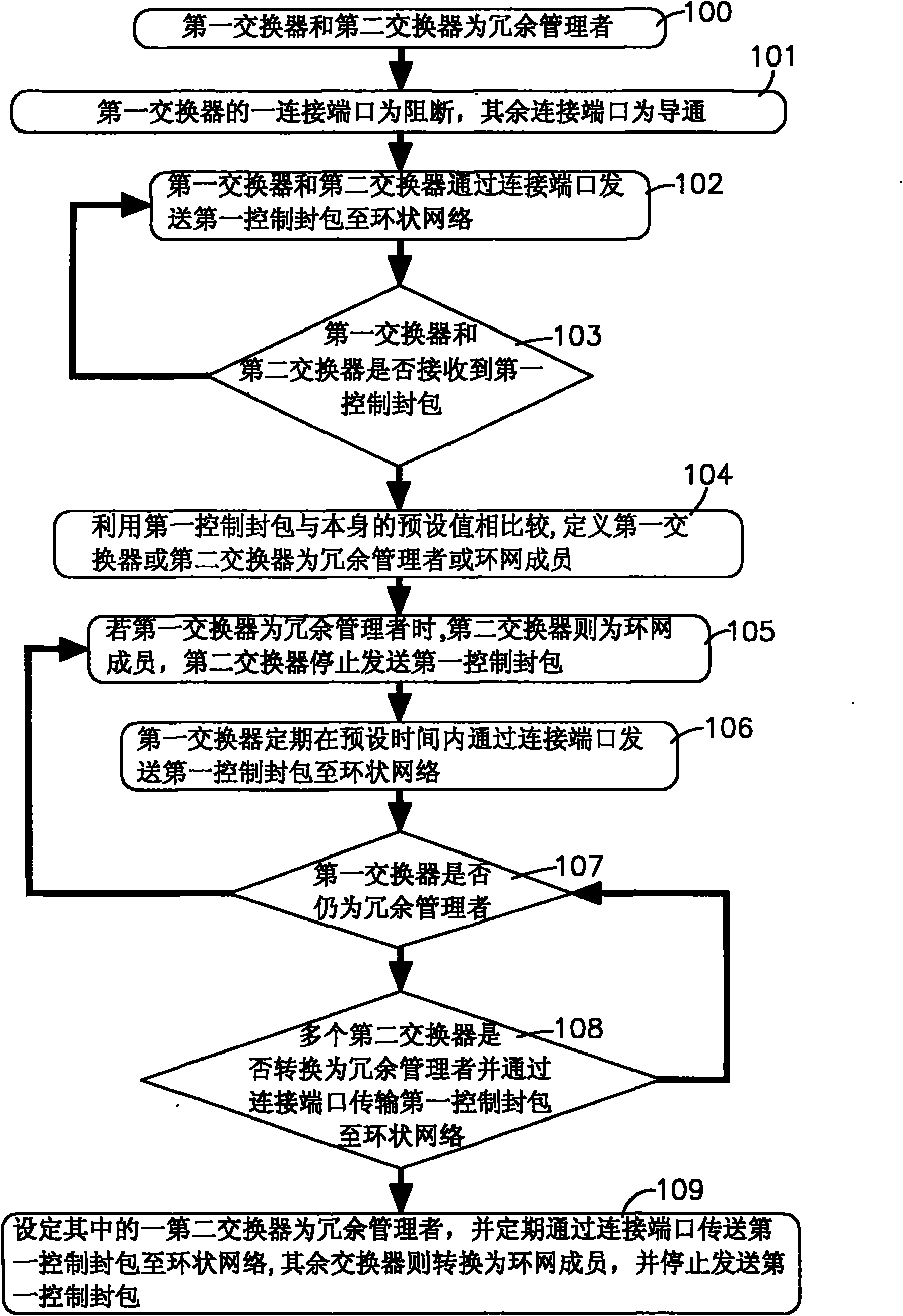
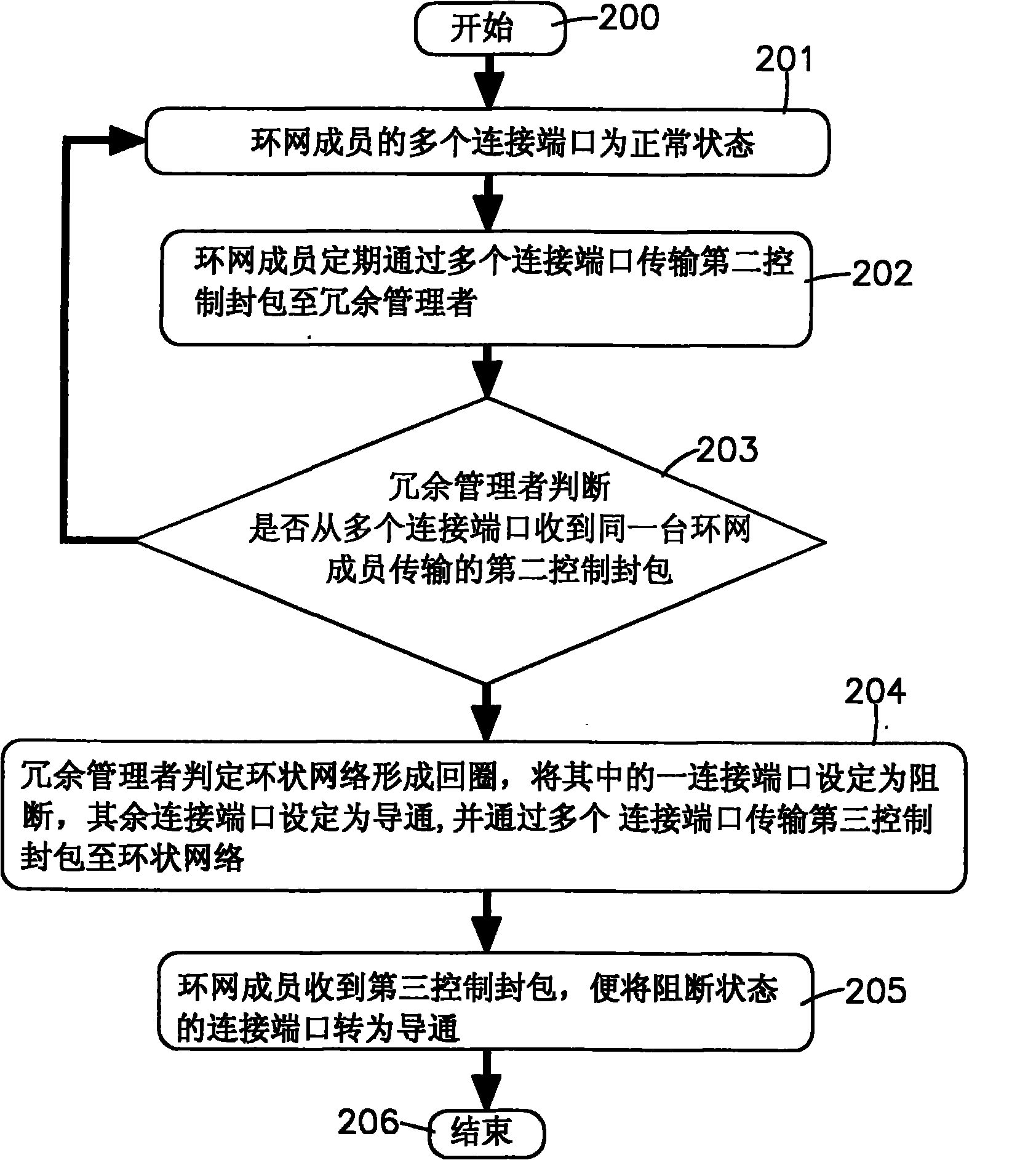
InactiveCN101771580AImprove reliabilityQuick return to normal operationsError preventionLoop networksRing networkNetwork redundancy
The invention relates to a processing method for redundancy checking of a ring network, which comprises a first exchanger and a plurality of second exchangers. When the first exchanger is set as a redundancy manager, the second exchangers are used as ring network members; in addition, one connecting port is set into an interdiction state and other connecting ports are set into a conducting state by the first exchanger; the second exchangers can periodically detect whether the connecting states of a plurality of connecting ports are abnormal or not; and when the abnormality occurs, the second exchangers can transmit a fifth control packet to the first exchanger which can convert the connecting ports into the conducting state at the time and transmit a fourth control packet to the second exchangers, thus a network entity address table of the ring network can be updated. By using a mode of transmitting the control packets through a plurality of ring network members, the invention can reduce the situations that the control packets are lost caused by the full load of network flow and excessive single equipment, thereby improving the reliability of the ring network during redundancy checking.
Owner:MOXA INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com