By-path interdiction TCP connection
A bypass, network technology, applied in the direction of data exchange, digital transmission system, electrical components, etc. through path configuration, can solve the problem of TCP connection cannot be blocked
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
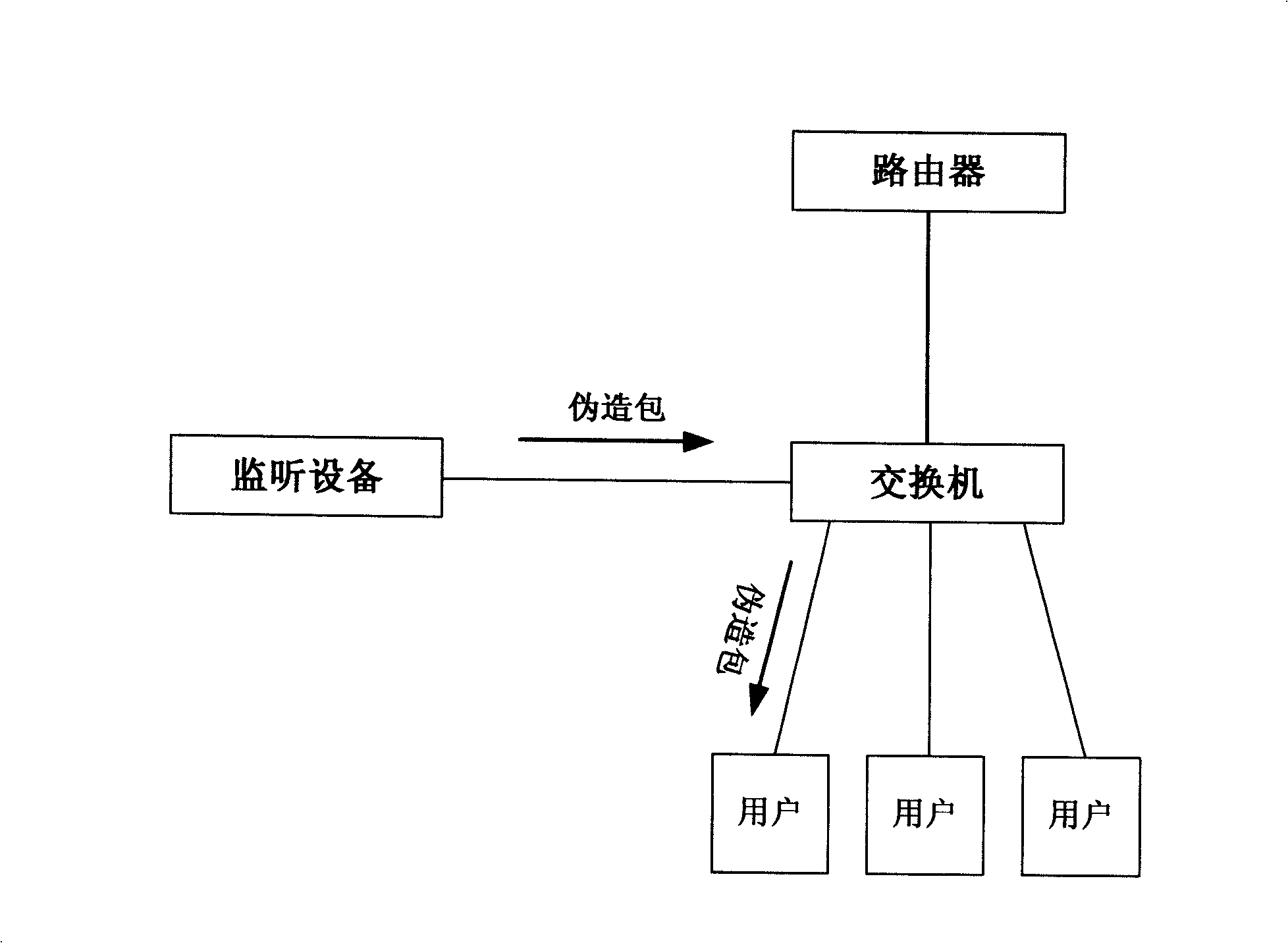
[0033] System implementation figure 1 .
[0034] 1. Connect the monitoring device to the mirror port of the hub or switch for monitoring.
[0035] 2. Identify the TCP connection that needs to be blocked in the monitored data packets.
[0036] 3. Construct a forged RST packet according to the information of the TCP connection that needs to be blocked.
[0037] 4. Send the forged data packet to the link layer with raw socket. Thus blocking specific TCP connections.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com