Patents
Literature
38 results about "Intelligence gathering" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
This is a list of intelligence gathering disciplines. HUMINT. Human intelligence (HUMINT) are gathered from a person in the location in question. Sources can include the following: Advisors or foreign internal defense (FID) personnel working with host nation (HN) forces or populations; Diplomatic ...
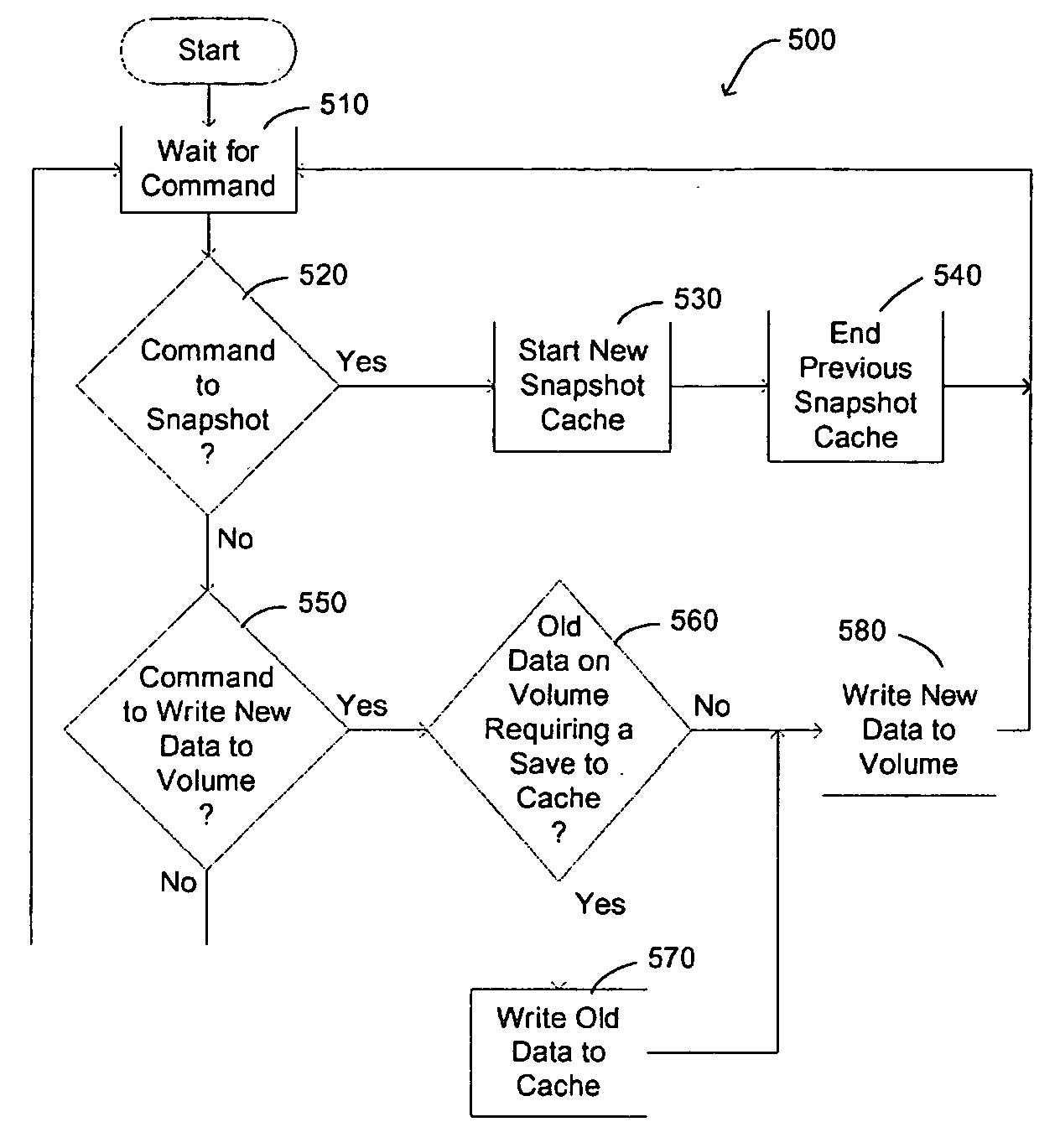
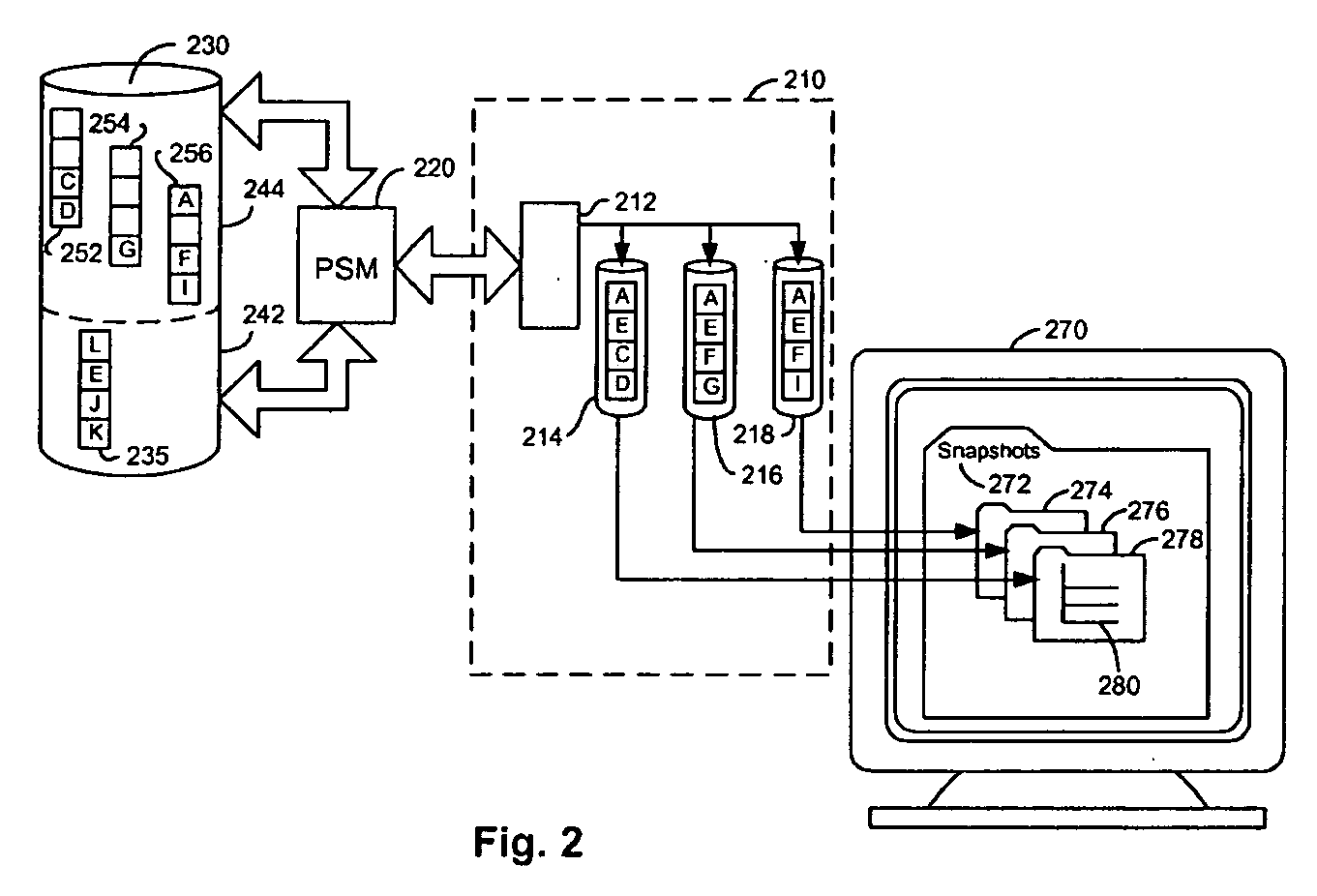
Persistent snapshot methods
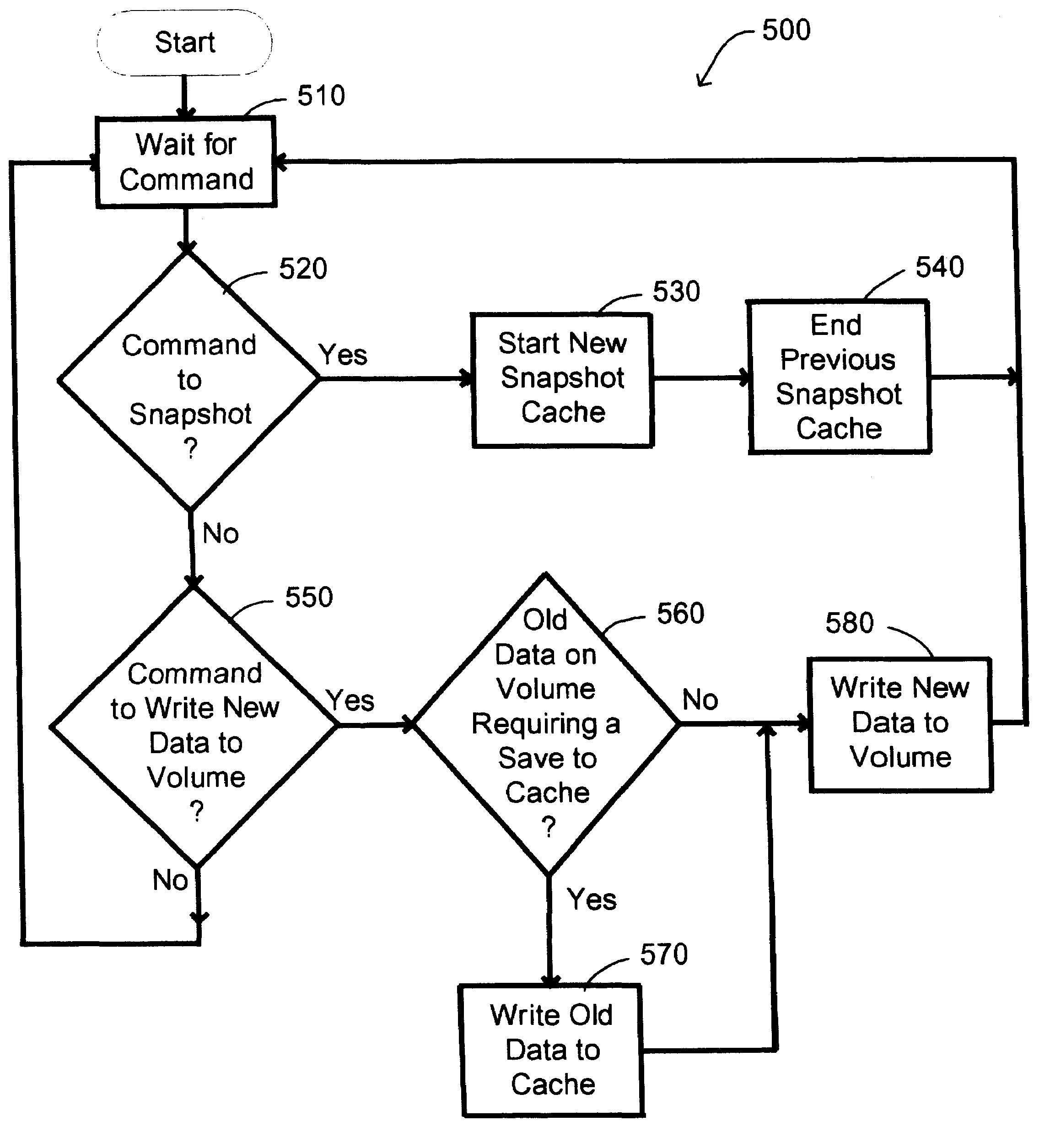
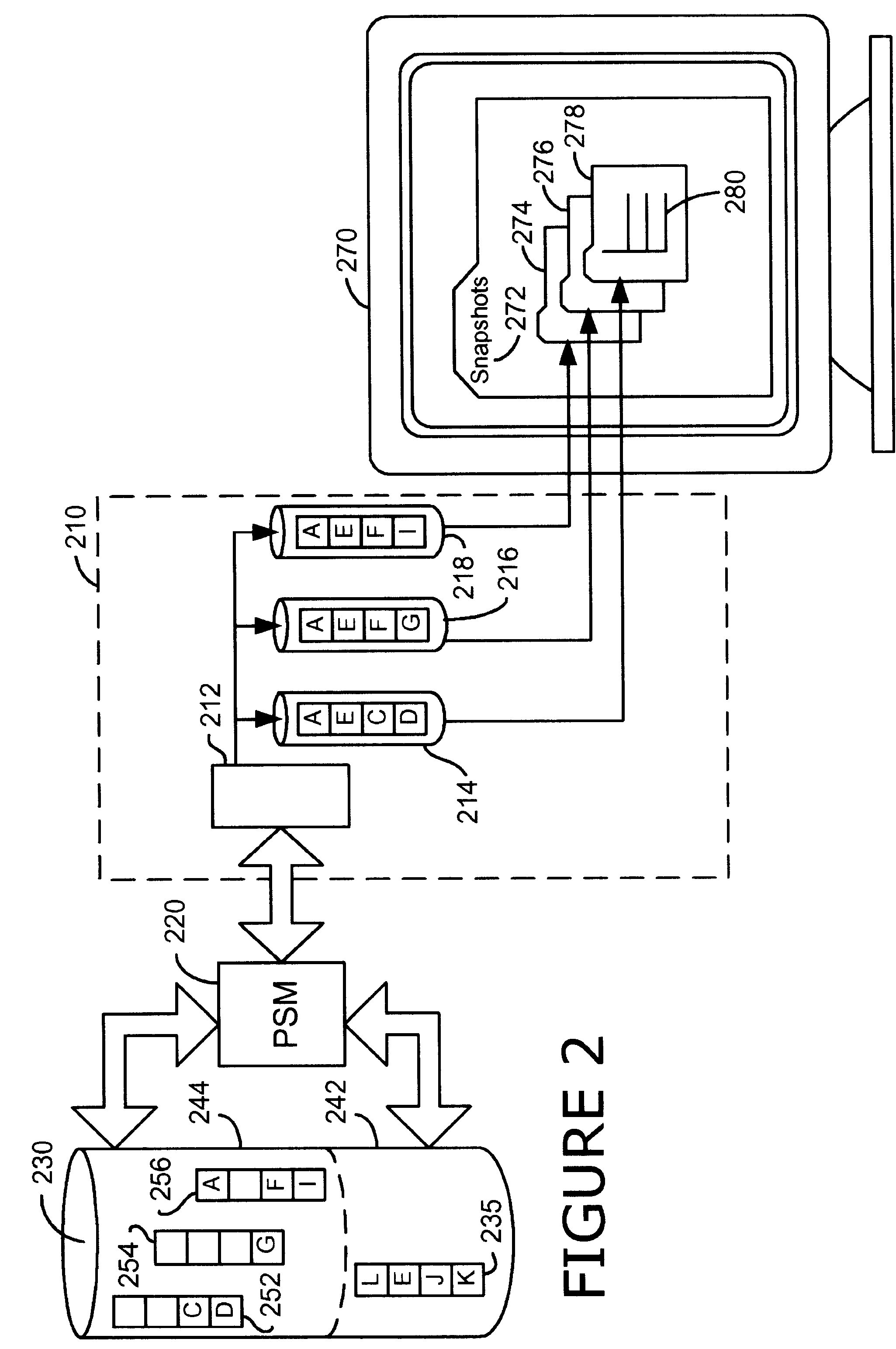
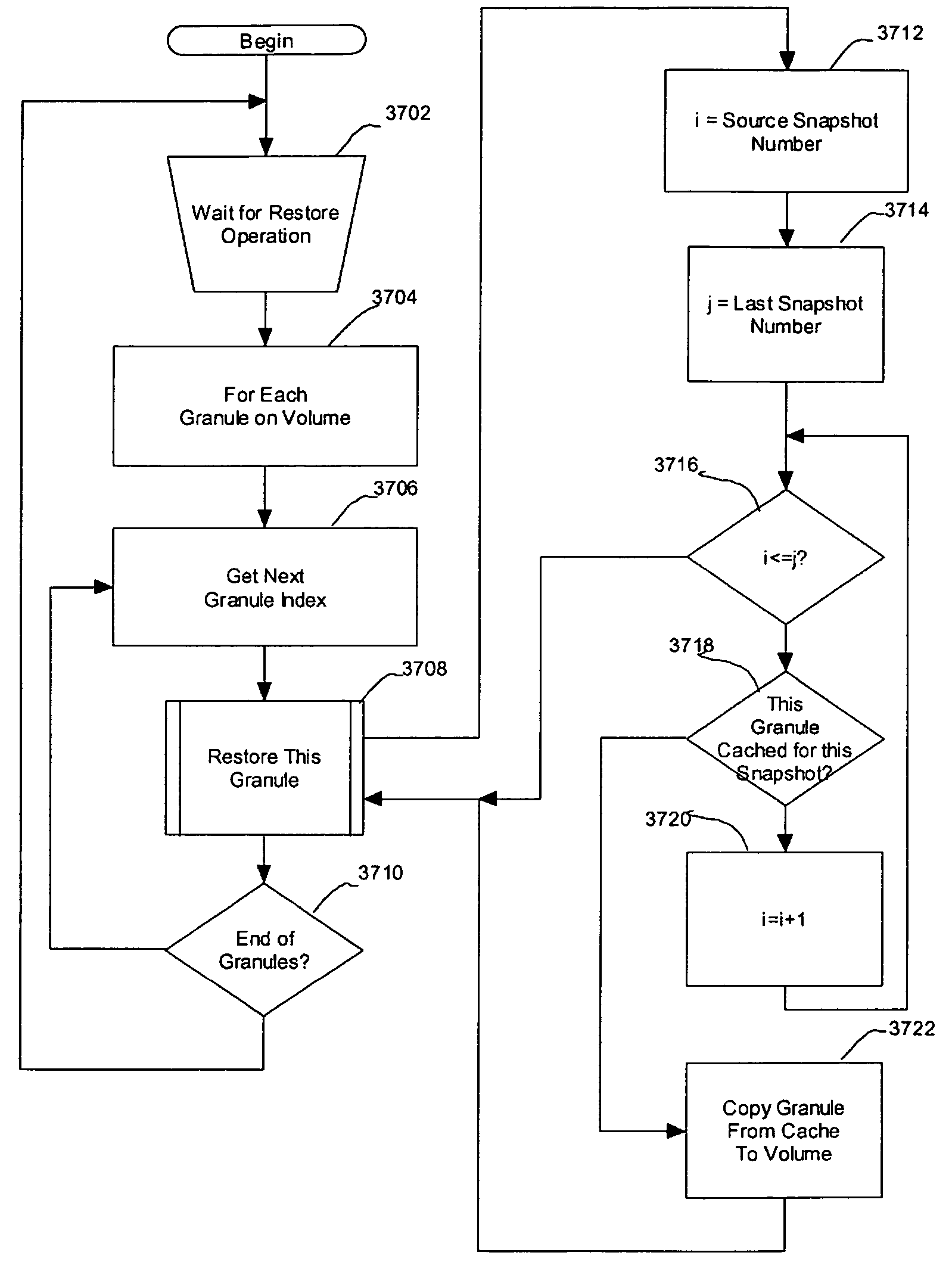
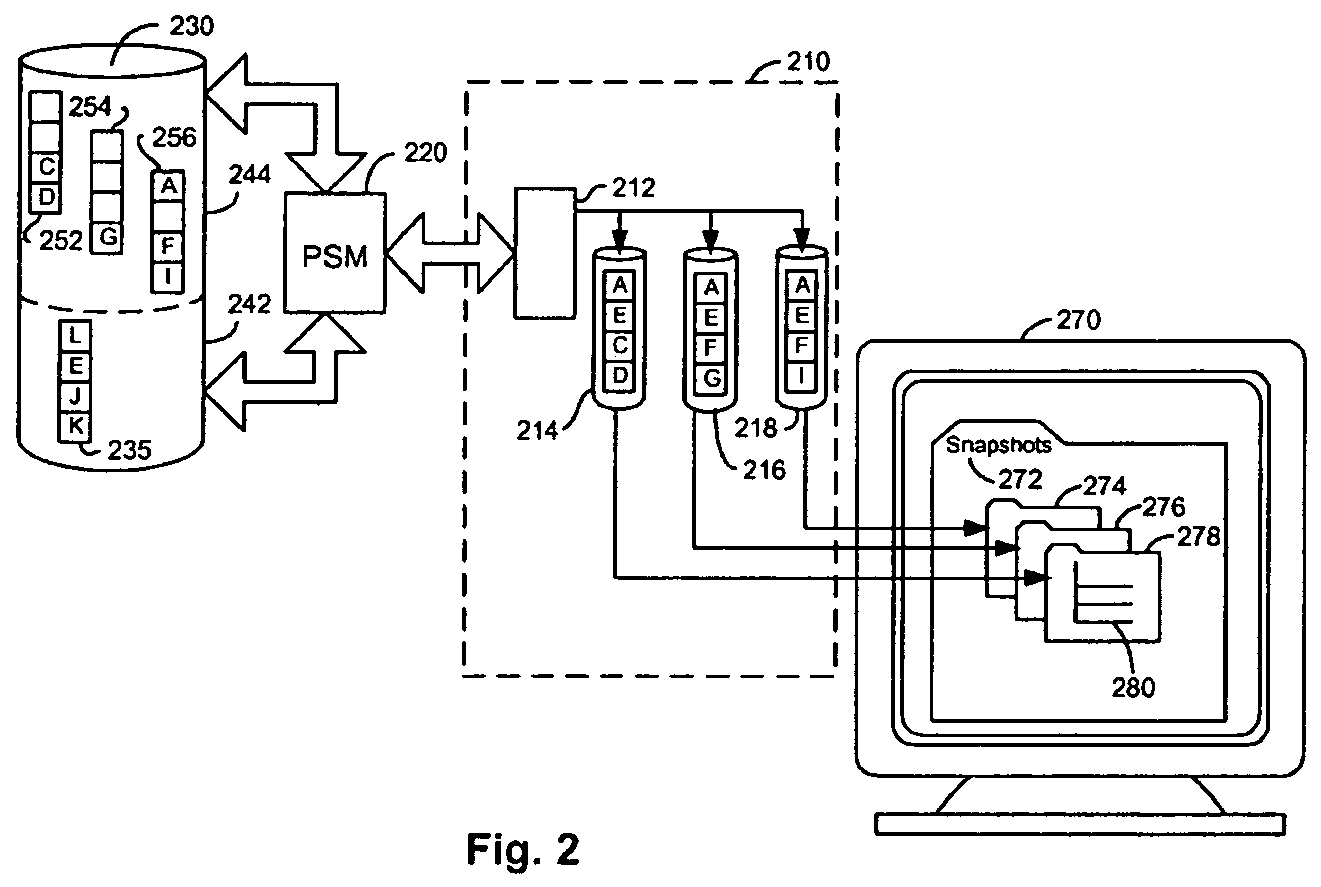
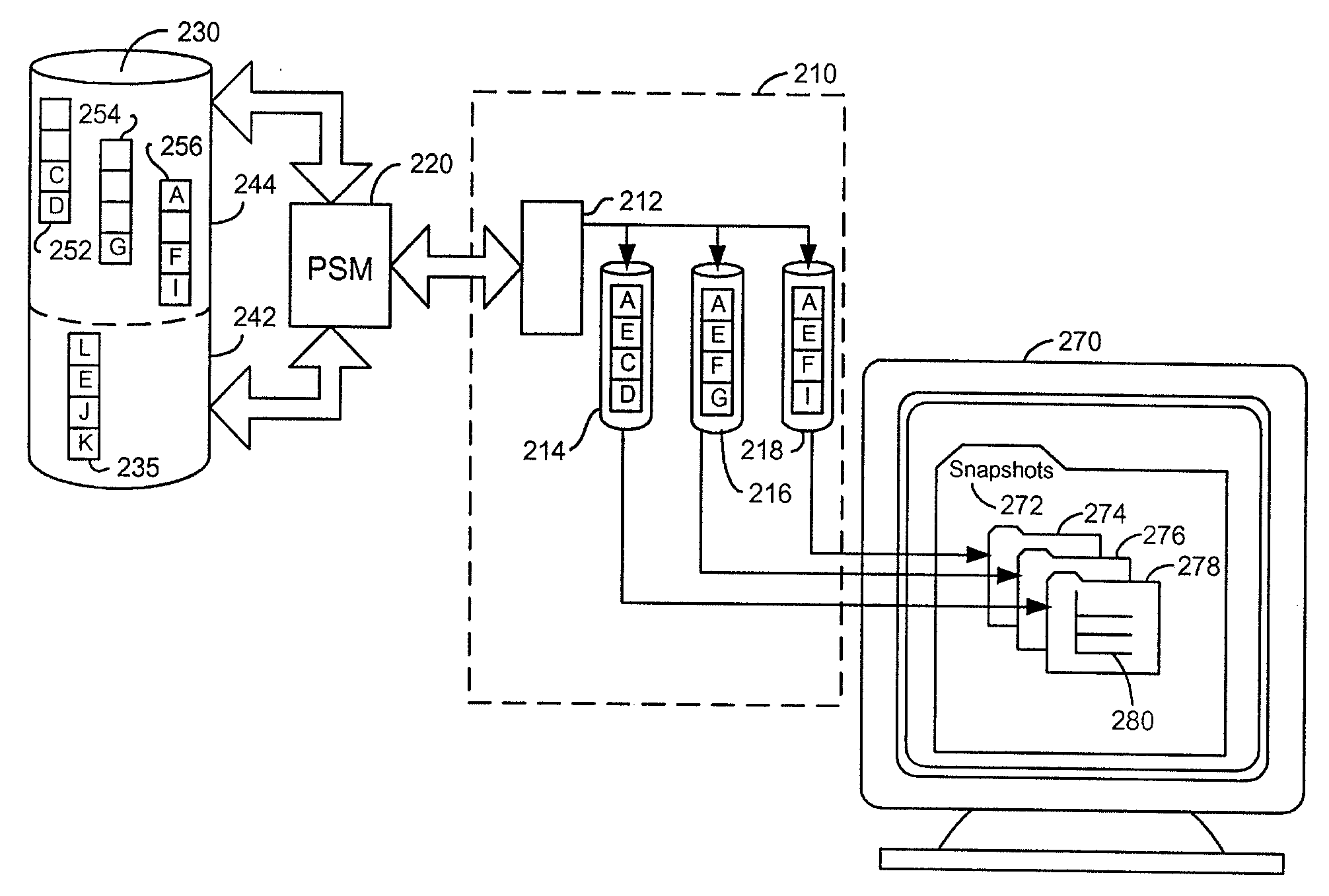
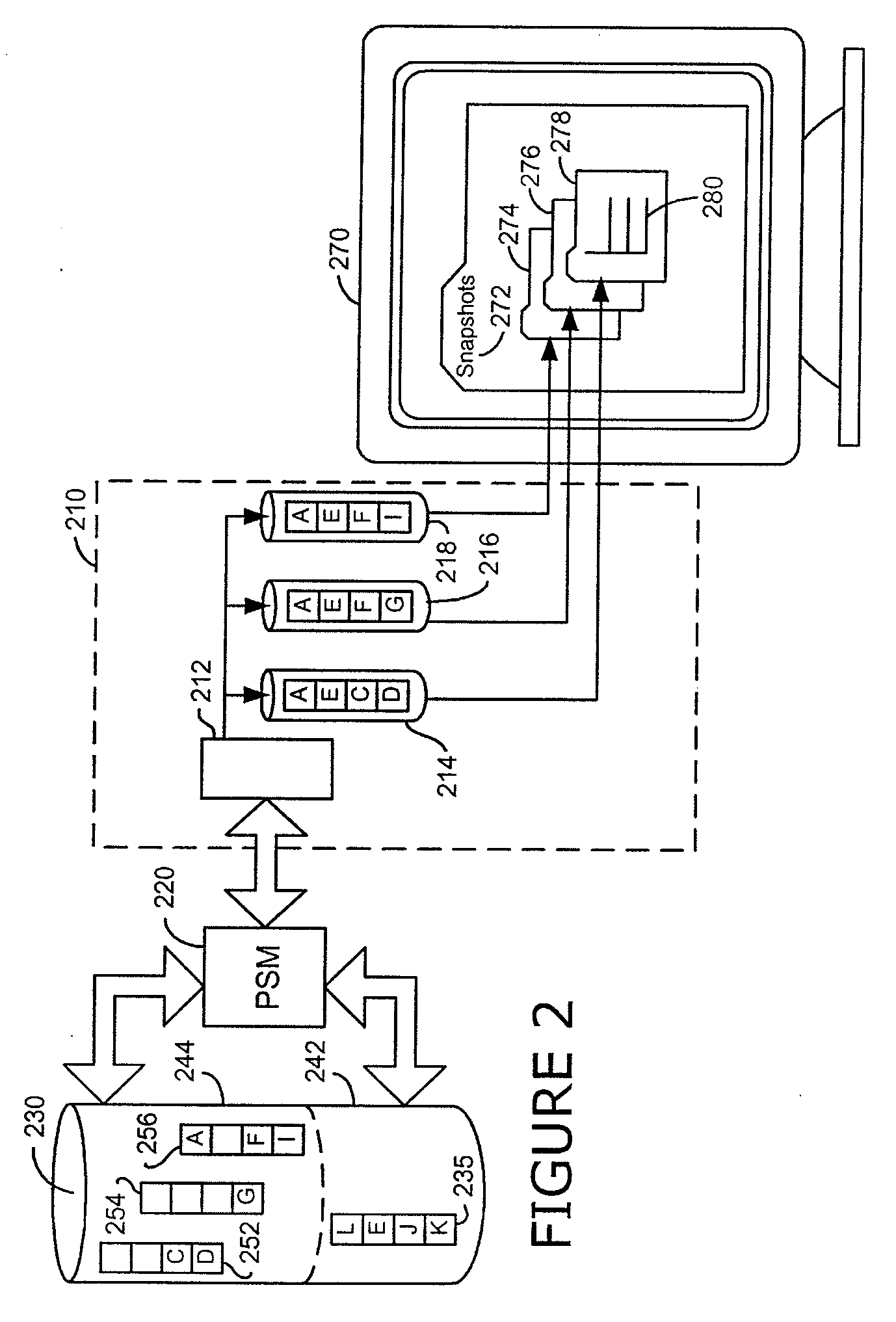
A persistent snapshot is taken and maintained in accordance with a novel method and system for extended periods of time using only a portion of a computer readable medium of which the snapshot is taken. Multiple snapshots can be taken in succession at periodic intervals and maintained practically indefinitely. The snapshots are maintained even after powering down and rebooting of the computer system. The state of the object of the snapshot for each snapshot preferably is accessible via a folder on volume of the snapshot. A restore of a file or folder may be accomplished by merely copying that file or folder from the snapshot folder to a current directory of the volume. Alternatively, the entire computer system may be restored to a previous snapshot state thereof. Snapshots that occurred after the state to which the computer is restored are not lost in the restore operation. Different rule sets and scenarios can be applied to each snapshot. Furthermore, each snapshot can be written to within the context of the snapshot and later restored to its pristine condition. Software for implementing the systems and methods of snapshots in accordance with the present invention may comprise firmware of a hard disk drive controller or a disk controller board or within the HDD casing itself. The present invention further comprises novel systems and methods in which the systems and methods of taking and maintaining snapshots are utilized in creating and managing temporal data stores, including temporal database management systems. The implications for data mining and exploration, data analysis, intelligence gathering, and artificial intelligence (just to name a few areas) are profound.
Owner:COLUMBIA DATA PRODUCTS
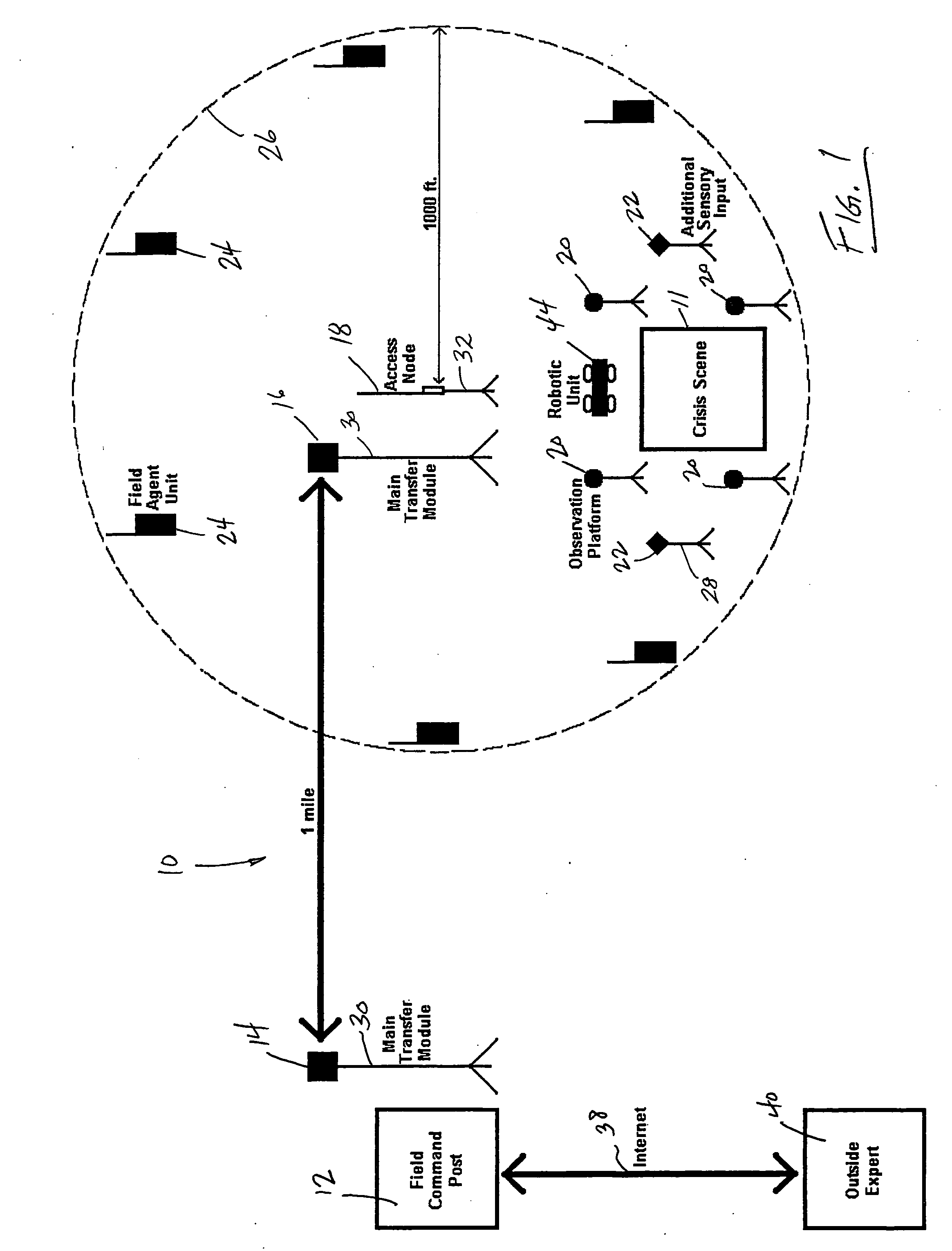
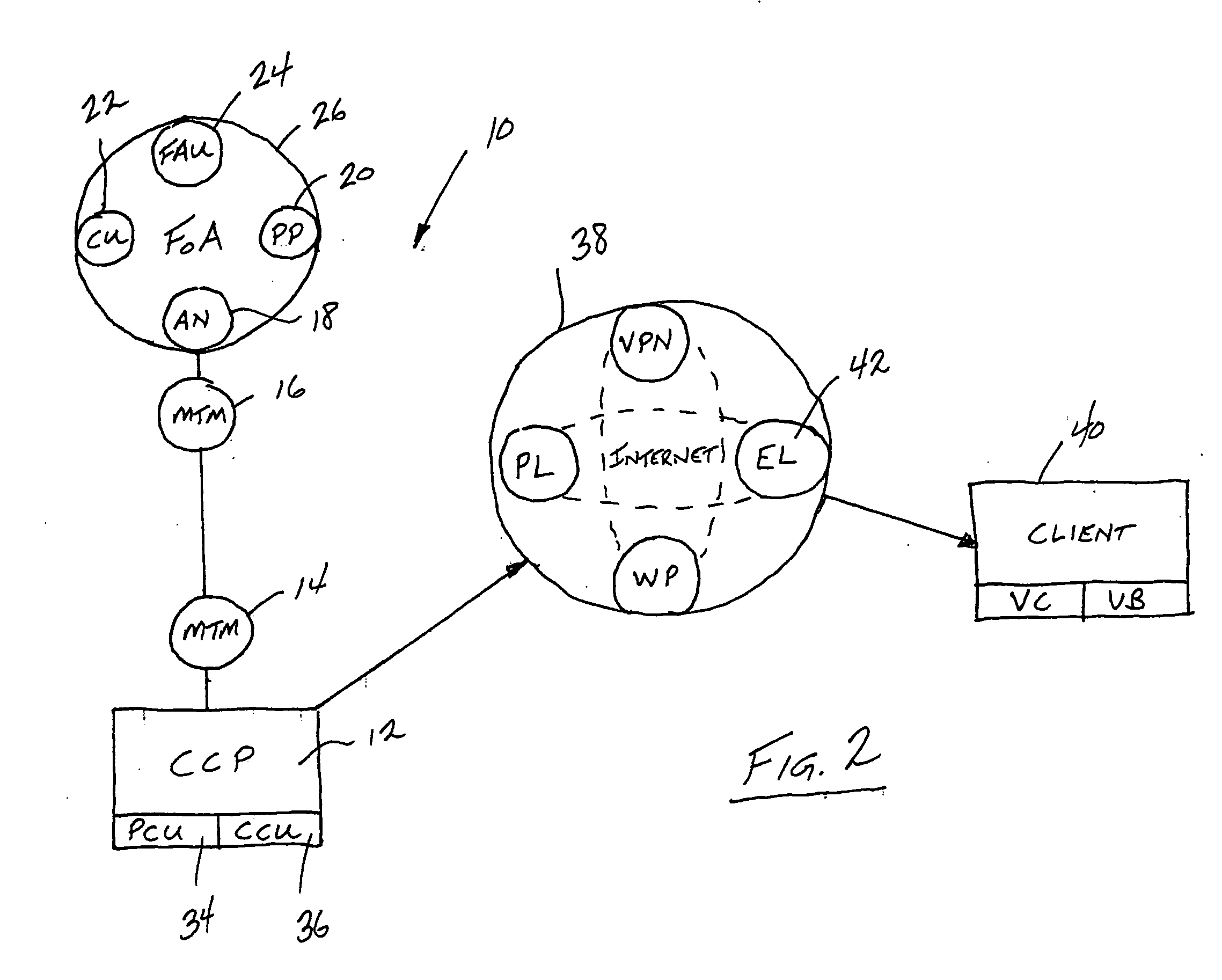
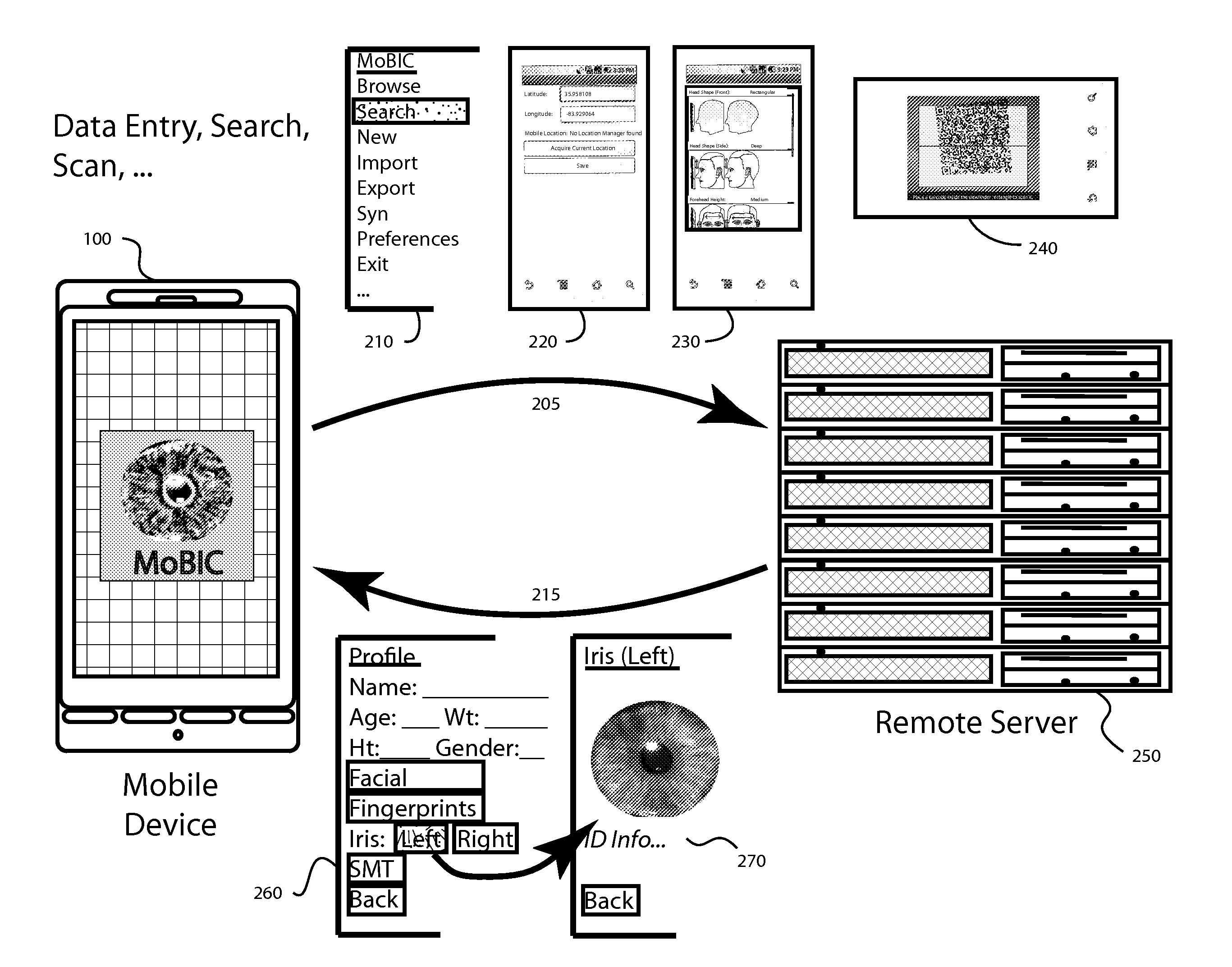
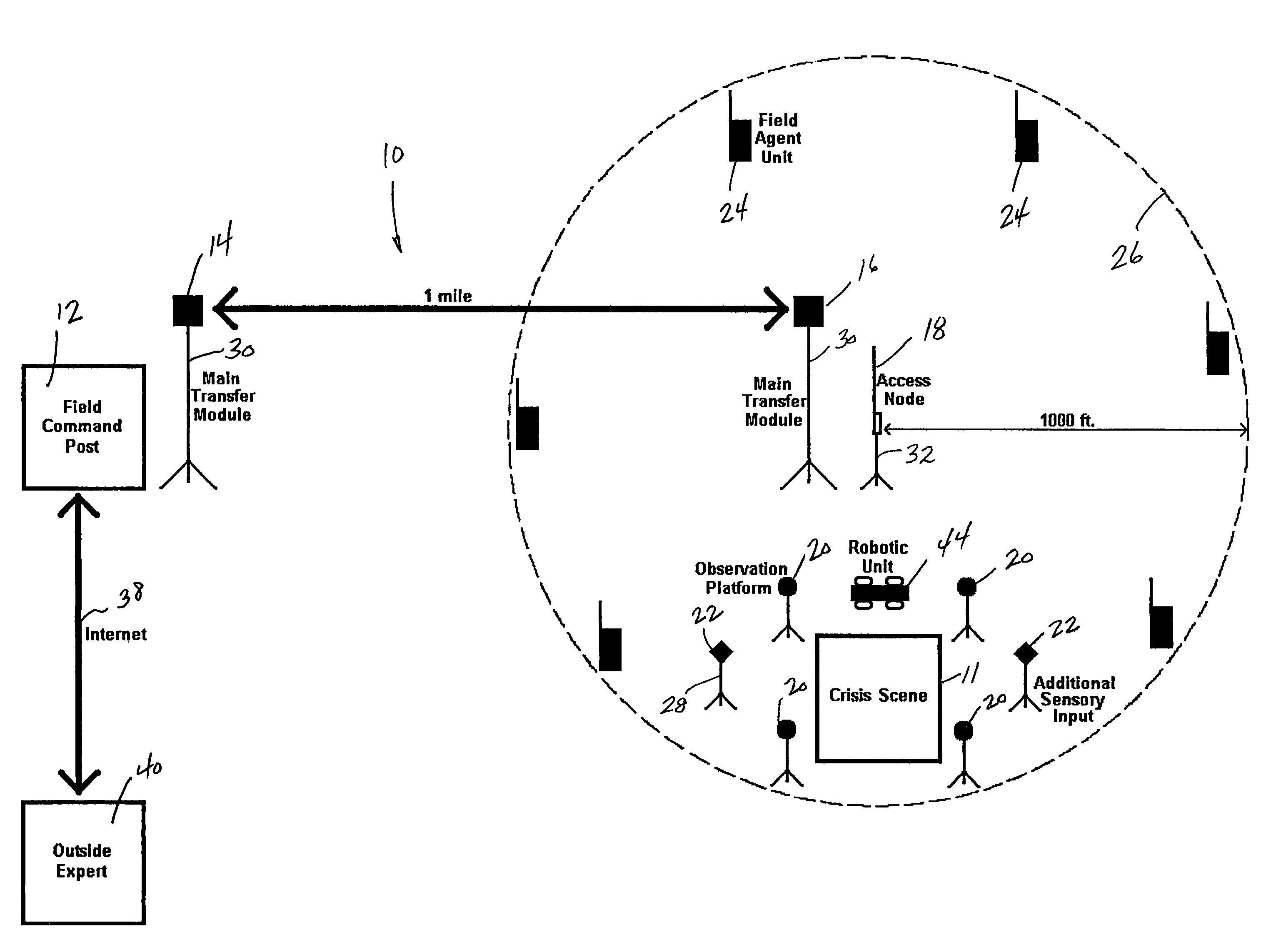
Remote field command post
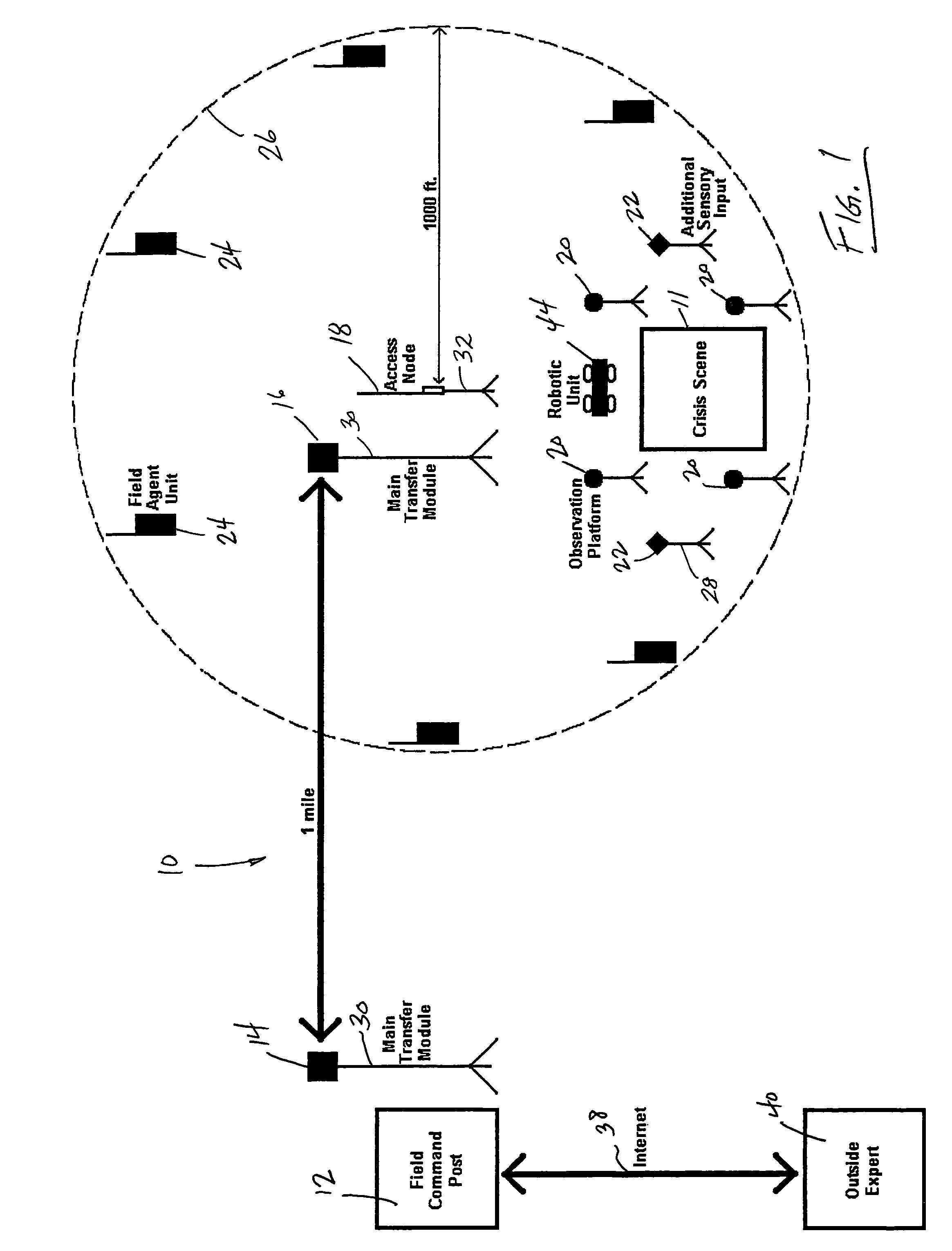
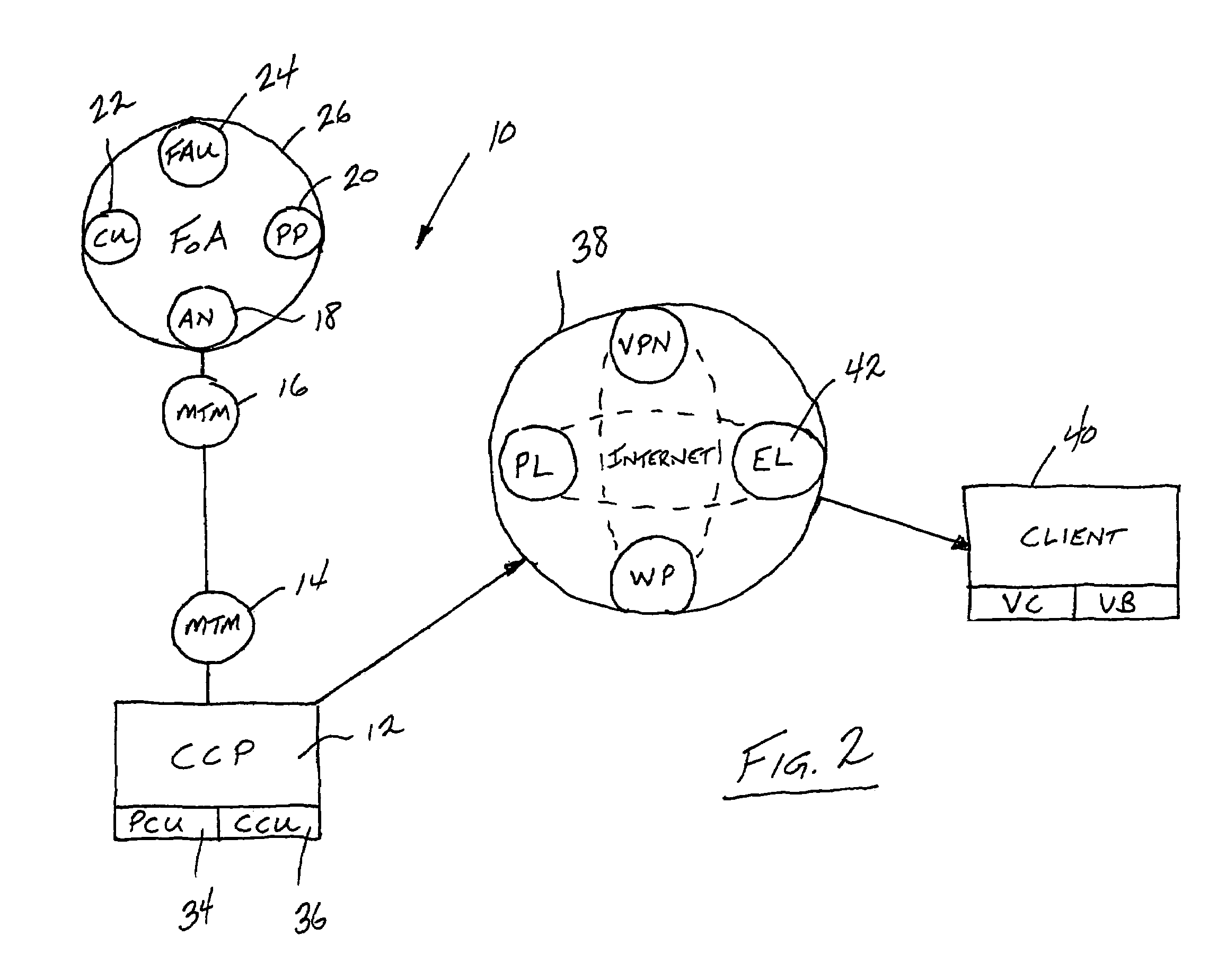
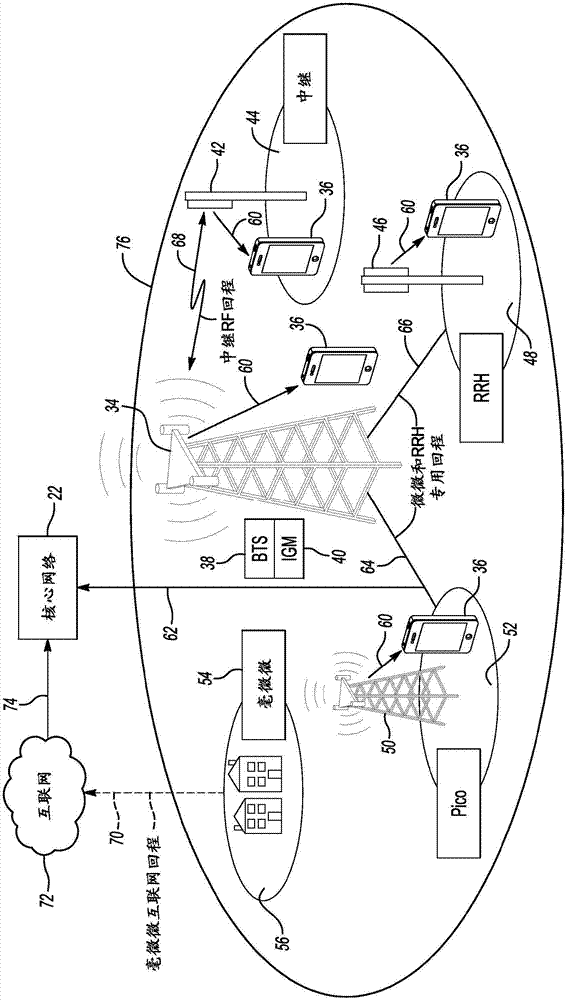
ActiveUS20060071775A1Improve developmentEnhances audio interoperabilityFrequency-division multiplex detailsTime-division multiplexRelevant informationHand held
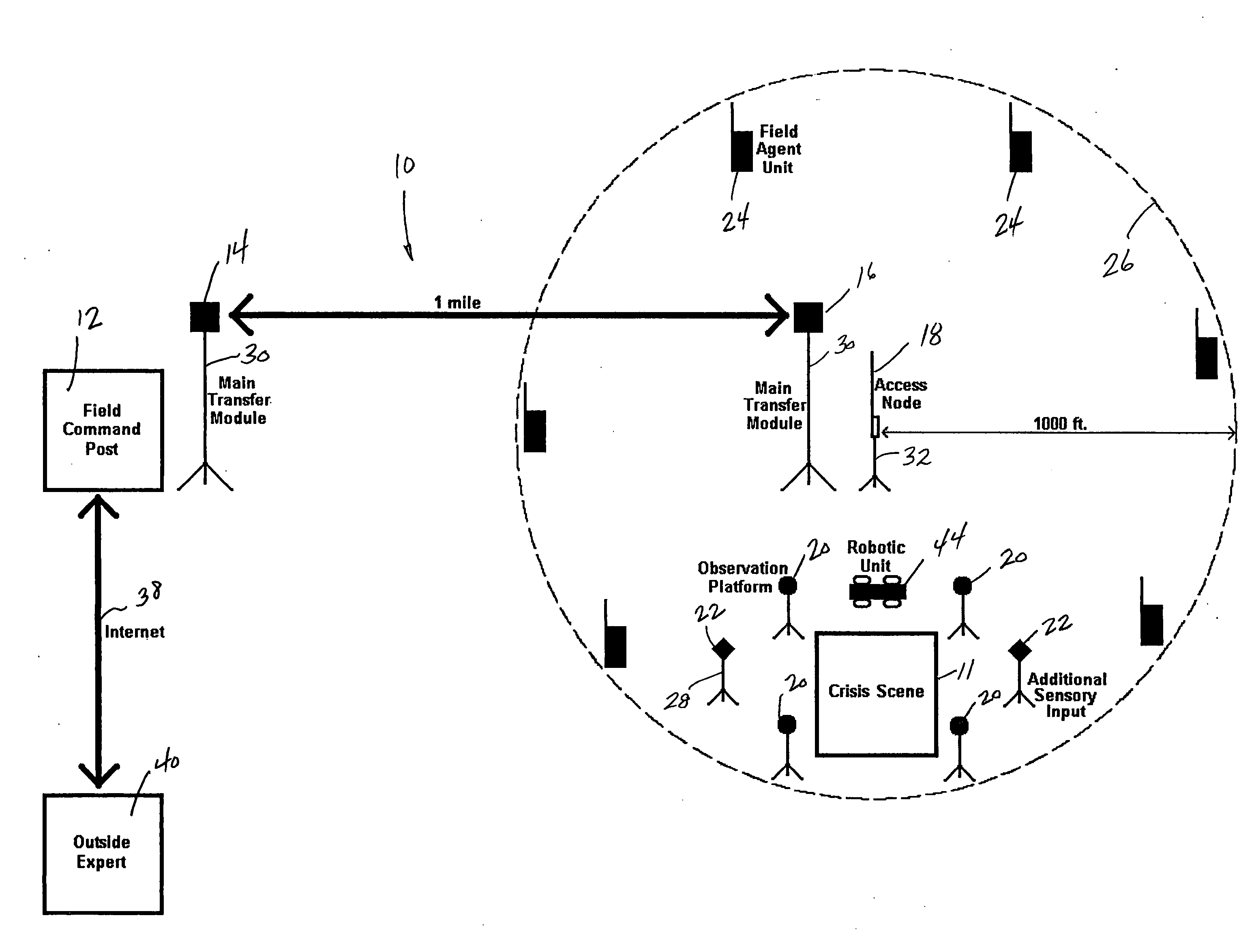
A communication and intelligence gathering system and method for monitoring a crisis scene from a remote command post. The system includes an access node positioned within communication range of multiple observation platforms that each provide information relating to the crisis scene, such as a video feed. The access node communicates with a main transfer module that relays the audio / video / data from the crisis scene to a main transfer module remotely positioned. A second main transfer module communicates with a field command post such that personnel at the field command post can monitor, react to and manage the crisis situation from the remote location. The access node position near the crisis scene also communications video and relevant information to field agents such that the field agents can monitor the video and information from a hand held / portable device.
Owner:OTTO KEVIN L +2
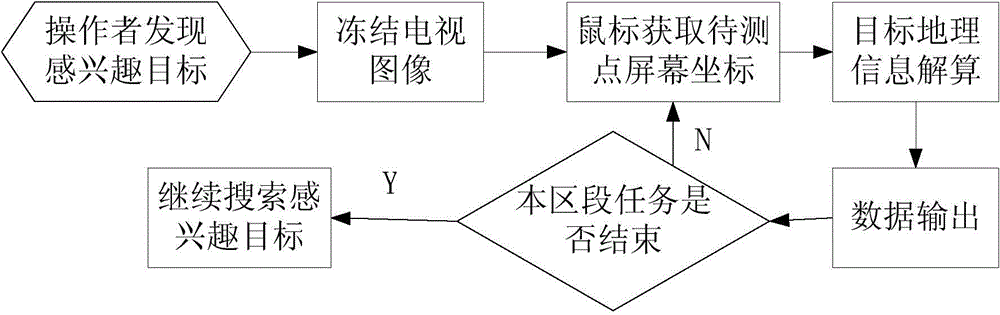
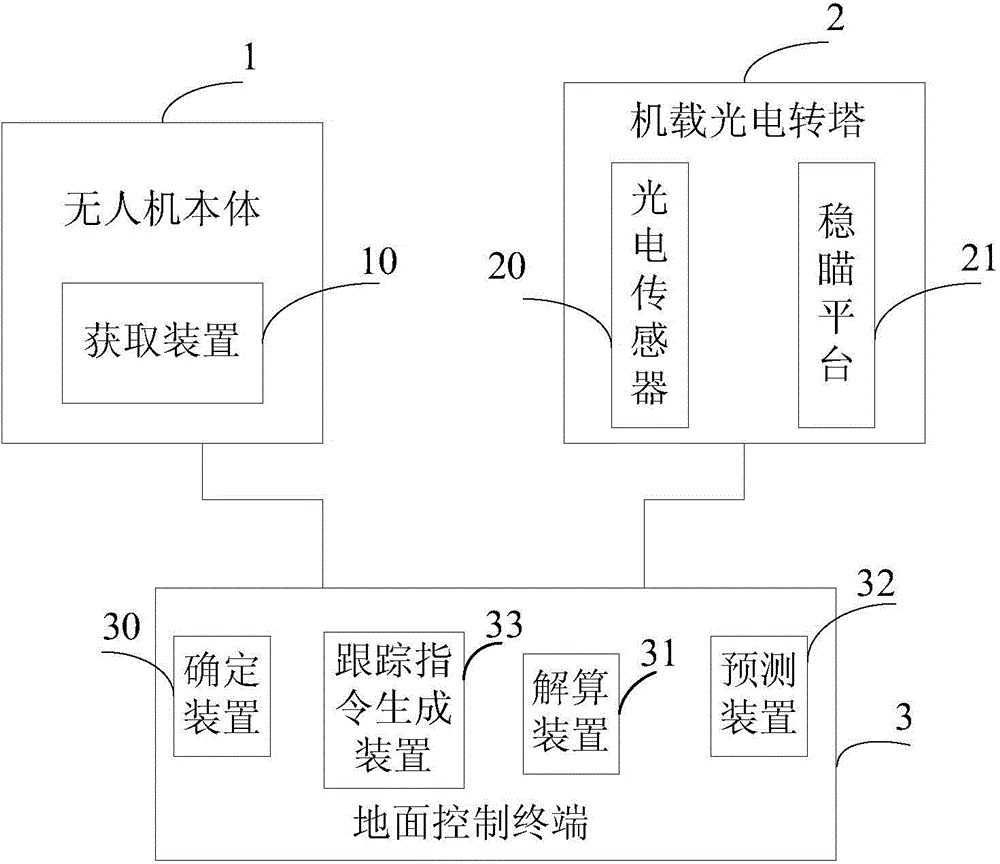
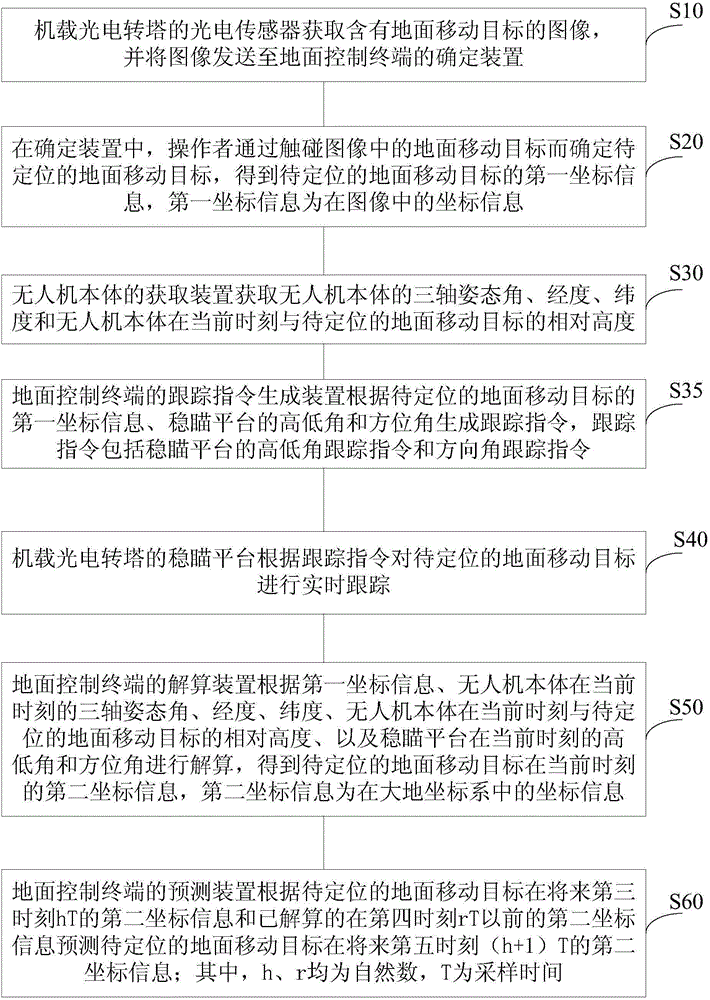
Unmanned aerial vehicle system and method for dynamically positioning ground moving target
ActiveCN103604427AMeet initial alignment requirementsHigh positioning accuracyNavigation instrumentsTarget-seeking controlLongitudeUncrewed vehicle
The invention discloses an unmanned aerial vehicle system and a method for dynamically positioning a ground moving target, belonging to the fields of unmanned aerial vehicle system application and the like. The unmanned aerial vehicle system comprises an unmanned aerial vehicle body, a vehicle-mounted photoelectric rotating tower and a ground control terminal, wherein the unmanned aerial vehicle body comprises an acquisition device, the vehicle-mounted photoelectric rotating tower comprises a photoelectric sensor and a sight-stabilizing platform, and the ground control terminal comprises a determining device, a trace command generating device, a resolving device and a predicting device. According to the technical scheme provided by the invention, geographical coordinate information including latitude, longitude and the like of a tracked ground moving target can be output in real time, the original geographical coordinate information can be accurately and quickly fitted, the moving trend of the ground moving target can be predicted and evaluated, and the original geographical coordinate information can be screened to realize display and prediction of the track of the moving target; the positioning accuracy acquired by the unmanned aerial vehicle system and the method approaches that of static positioning and can meet requirements for initial alignment of weapons including artilleries and the like, and the probability of fusion processing of an unmanned aerial vehicle intelligence system and an entire-army intelligence gathering network is provided.
Owner:CHINA ACAD OF AEROSPACE AERODYNAMICS
Persistent snapshot management system
InactiveUS20060107006A1Memory loss protectionDigital data processing detailsHard disc drivePrimitive state
A persistent snapshot is taken and maintained in accordance with a novel method and system for extended periods of time using only a portion of a computer readable medium of which the snapshot is taken. Multiple snapshots can be taken in succession at periodic intervals and maintained practically indefinitely. The snapshots are maintained even after powering down and rebooting of the computer system. The state of the object of the snapshot for each snapshot preferably is accessible via a folder on volume of the snapshot. A restore of a file or folder may be accomplished by merely copy that file or folder from the snapshot folder to a current directory of the volume. Alternatively, the entire computer system may be restored to a previous snapshot state thereof. Snapshots that occurred after the state to which the computer is restored are not lost in the restore operation. Different rule sets and scenarios can be applied to each snapshot. Furthermore, each snapshot can be written to within the context of the snapshot and later restored to its pristine condition. Software for implementing the systems and methods of snapshots in accordance with the present invention may comprise firmware of a hard disk drive controller or a disk controller board or within the HDD casing itself. The present invention further comprises novel systems and methods in which the systems and methods of taking and maintaining snapshots are utilized in creating and managing temporal data stores, including temporal database management systems. The implications for data mining and exploration, data analysis, intelligence gathering, and artificial intelligence (just to name a few areas) are profound.
Owner:COLUMBIA DATA PRODUCTS
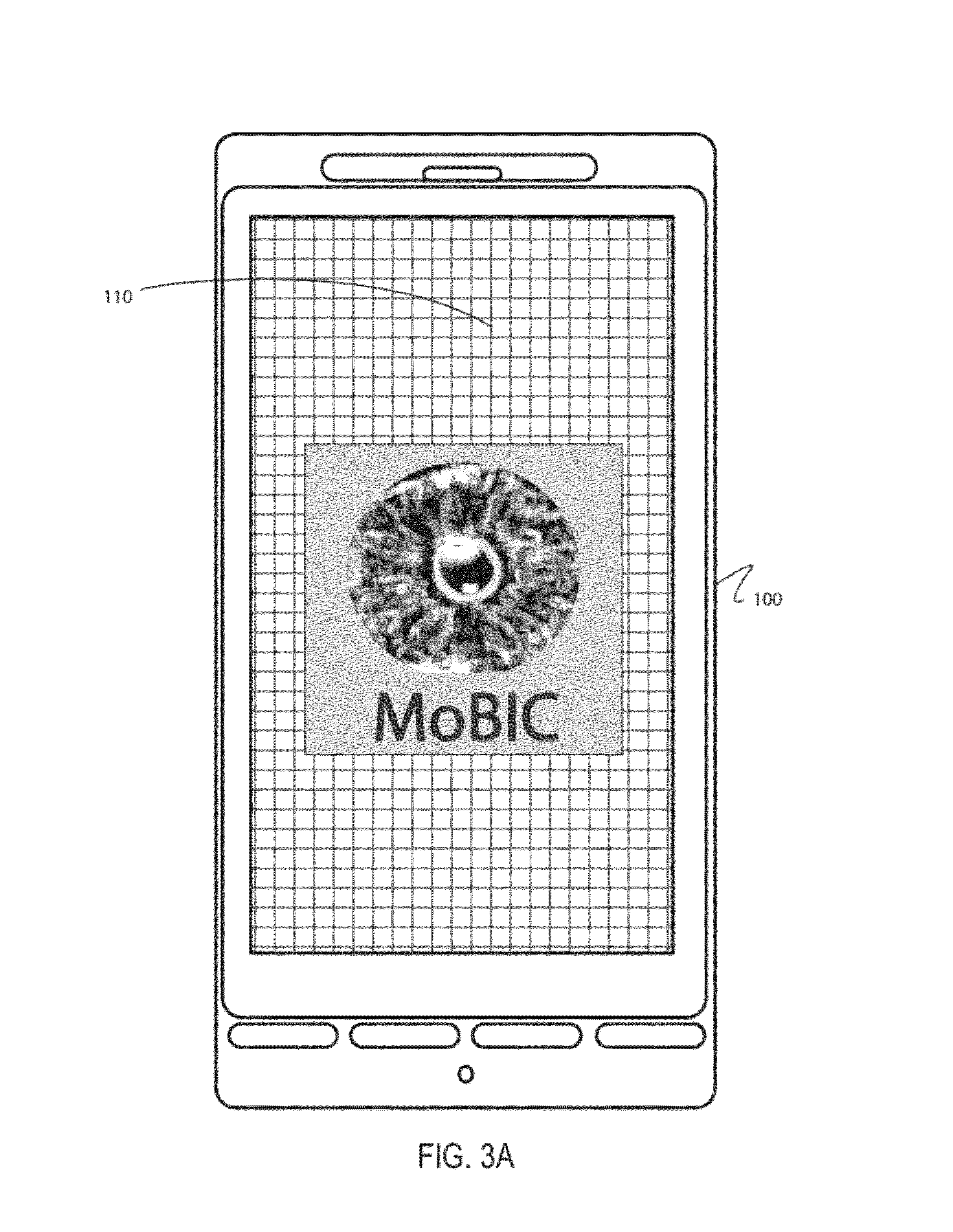
Mobile Biometrics Information Collection and Identification
ActiveUS20120148115A1Minimal costCosts of hardware modifications and associated software requirementsDigital data authenticationProteomicsHuman bodyPattern recognition
A biometric mobile device is capable of interacting with existing cellular, wireless, and wired telecommunication and other communication networks to support intelligence gathering, human body identification, special operations and other applications. A method of collecting biometric data at an accident or crime scene may comprise, for example, utilizing a camera to photograph the accident scene, collecting key entered data that may not be otherwise obtainable, using a fingerprint scanner to collect, digitize and store fingerprint data, using a lab-on-a-chip DNA profile device for collecting and analyzing a DNA specimen and generating identification and DNA profile data for bar code entry and other means for collecting any known form of biometric data including, but not limited to, vascular facial structure, dental structure, cornea, iris or other data which may be unique or limiting for identification purposes.
Owner:BIRDWELL J DOUGLAS +2
Remote field command post
ActiveUS7397368B2Easy to adjustEnhanced Situational AwarenessFrequency-division multiplex detailsTime-division multiplexRelevant informationHand held
A communication and intelligence gathering system and method for monitoring a crisis scene from a remote command post. The system includes an access node positioned within communication range of multiple observation platforms that each provide information relating to the crisis scene, such as a video feed. The access node communicates with a main transfer module that relays the audio / video / data from the crisis scene to a main transfer module remotely positioned. A second main transfer module communicates with a field command post such that personnel at the field command post can monitor, react to and manage the crisis situation from the remote location. The access node position near the crisis scene also communications video and relevant information to field agents such that the field agents can monitor the video and information from a hand held / portable device.
Owner:OTTO KEVIN L +2
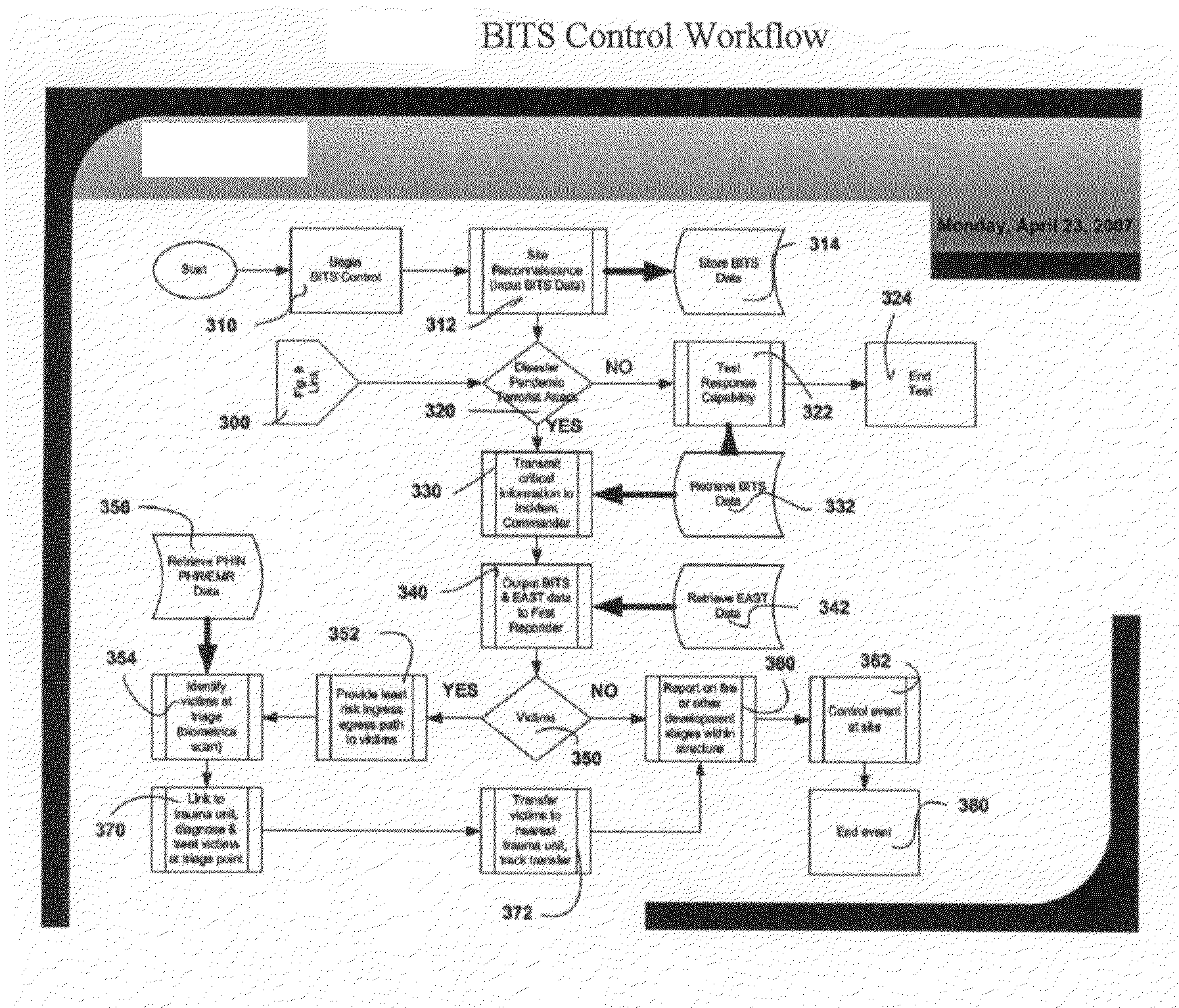
1st responder guidance and decision-support system enabling victim tracking and extraction
The invention uses processes, algorithms and programs to support emergency personnel decisions. It consists of several automated and semi-automated software components, hardware components, and processes, which are integrated into a single system that streamlines building intelligence gathering and victim extraction processes, and provides emergency personnel decision support.
Owner:MONATESTI SABATINI +1
System, method and computer program application for transforming unstructured text
InactiveUS20050120009A1Digital data processing detailsSemi-structured data mapping/conversionRelevant informationSystems approaches
A system, method and computer program application for finding relevant information from a plurality of sources including unstructured sources, mining the relevant information and generating output based upon the relevant information. The system, method and computer program application may be effectively utilized to more efficiently accomplish a variety of different business related tasks. A business that takes advantage of the system, method and computer program application receives a number of advantages, including (i) universal searching, (ii) efficient business event intelligence gathering; (iii) effective business event analyzing; and (iv) automated and streamlined up-to-date reporting.
Owner:ACUITY SOFTWARE
Persistent snapshot management system
InactiveUS7237080B2Digital data processing detailsMemory adressing/allocation/relocationHard disc drivePrimitive state
Owner:COLUMBIA DATA PRODUCTS
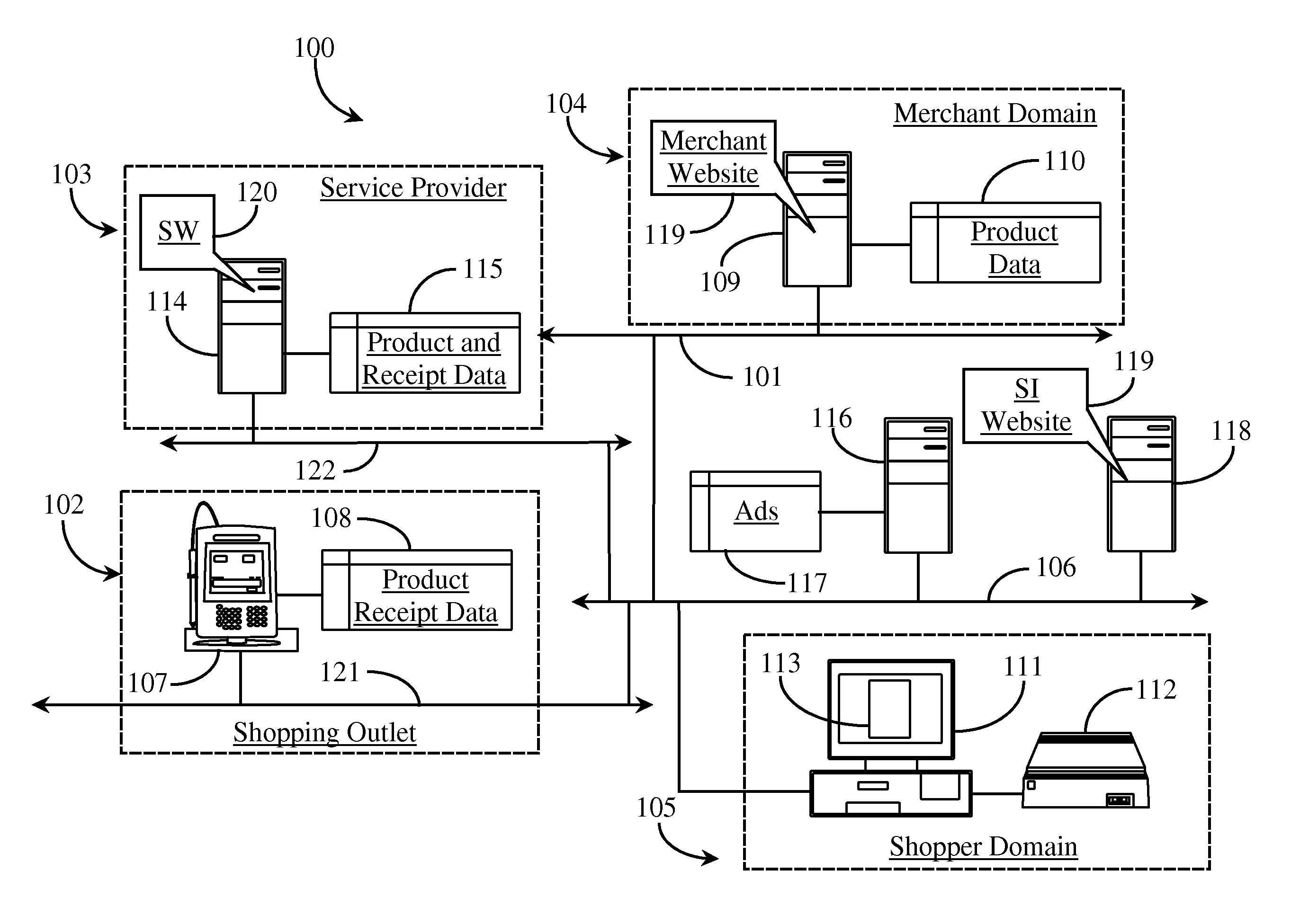
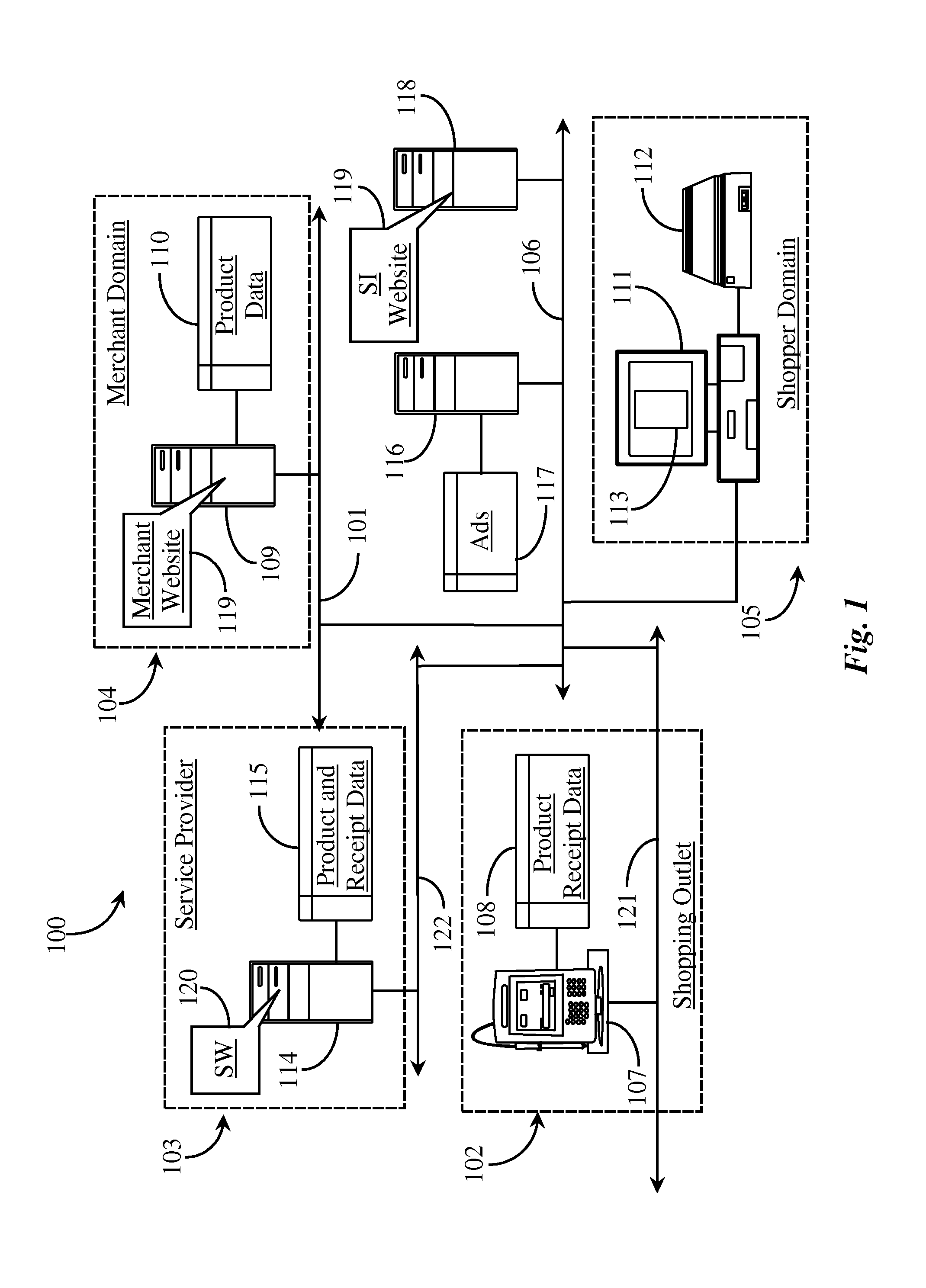
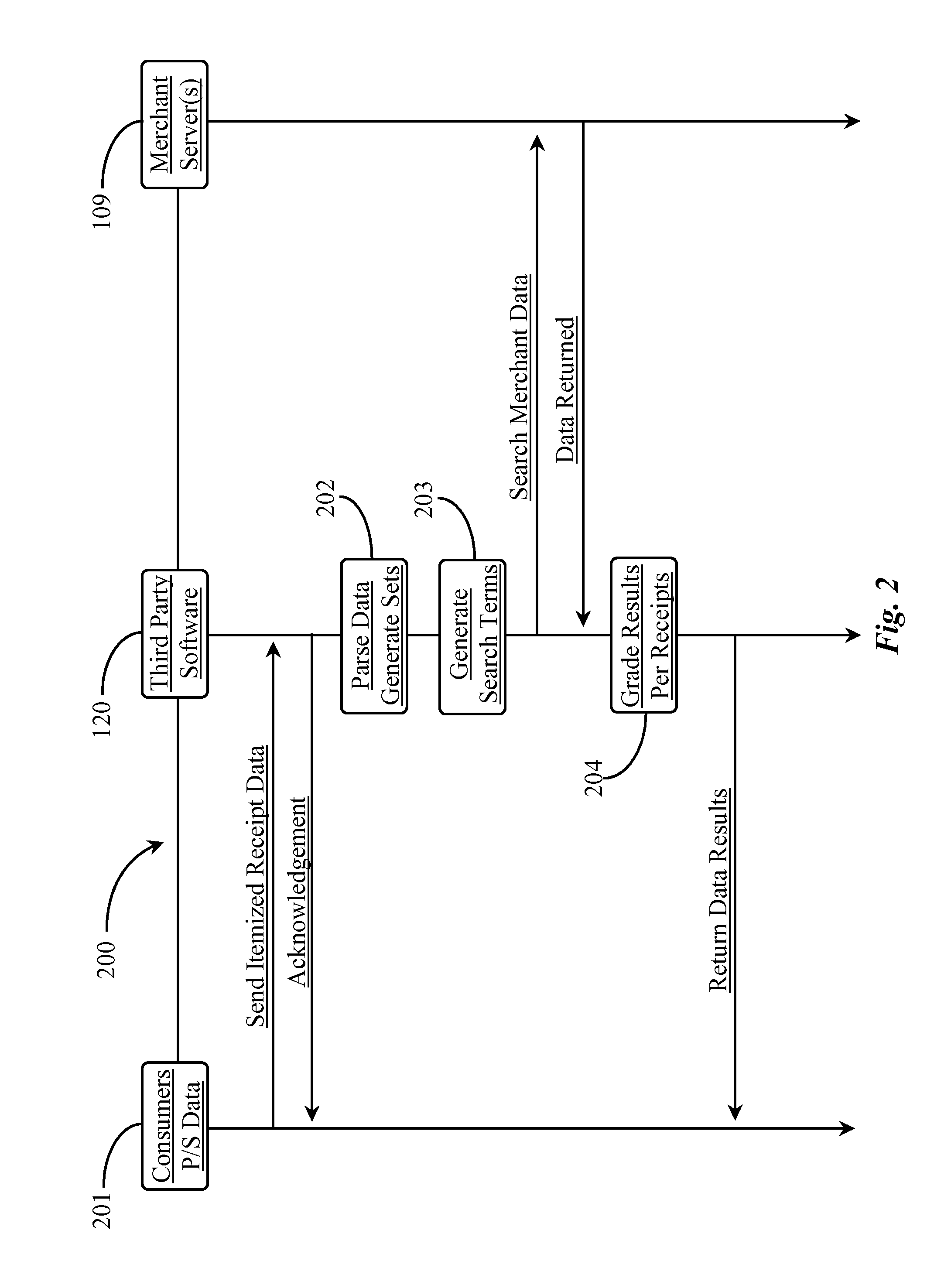
Methods and Apparatus for Gathering Intelligence from Itemized Receipts
An intelligence-gathering system operates on a network-connected server having at least one processor and at least one coupled data repository, with software executing on the at least one processor from a non-transitory medium. The software provides a first function obtaining data from itemized receipts, a second function obtaining related data from one or more merchant sites, and a third function matching data sets obtained from the itemized receipts to data sets obtained from the one or more merchant sites.
Owner:PROXIMIANT
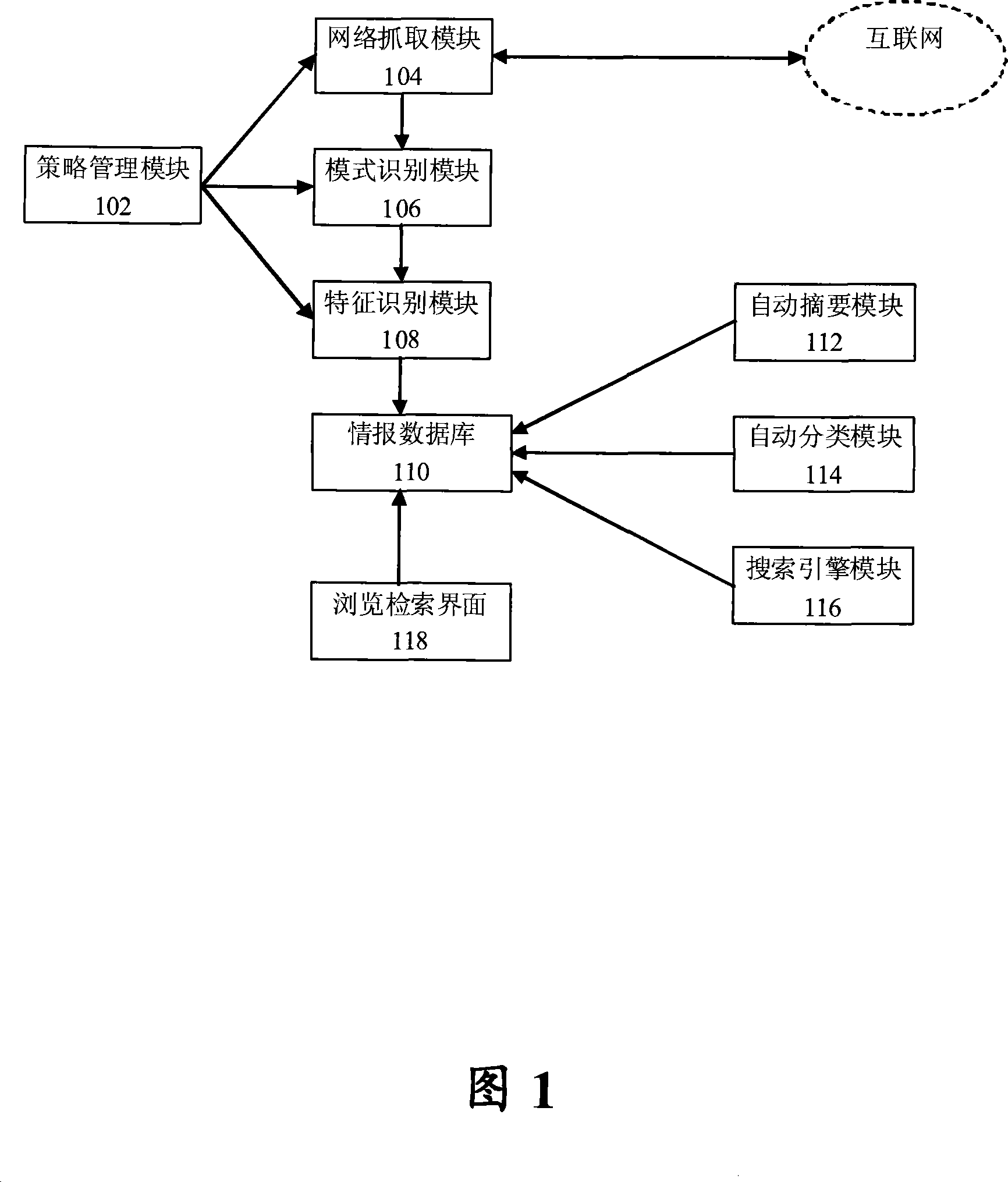
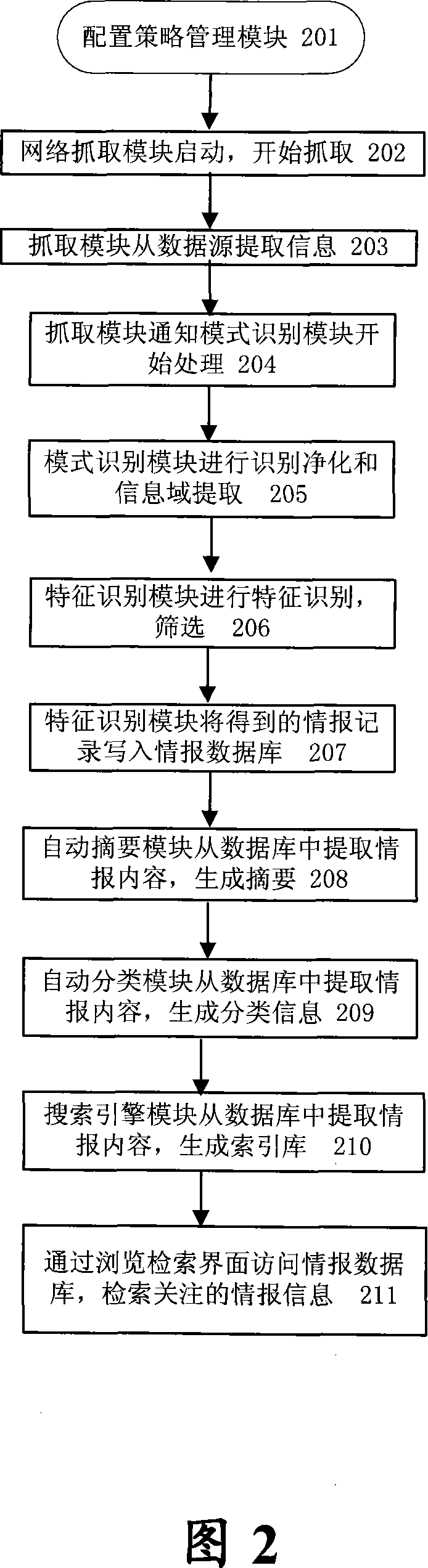
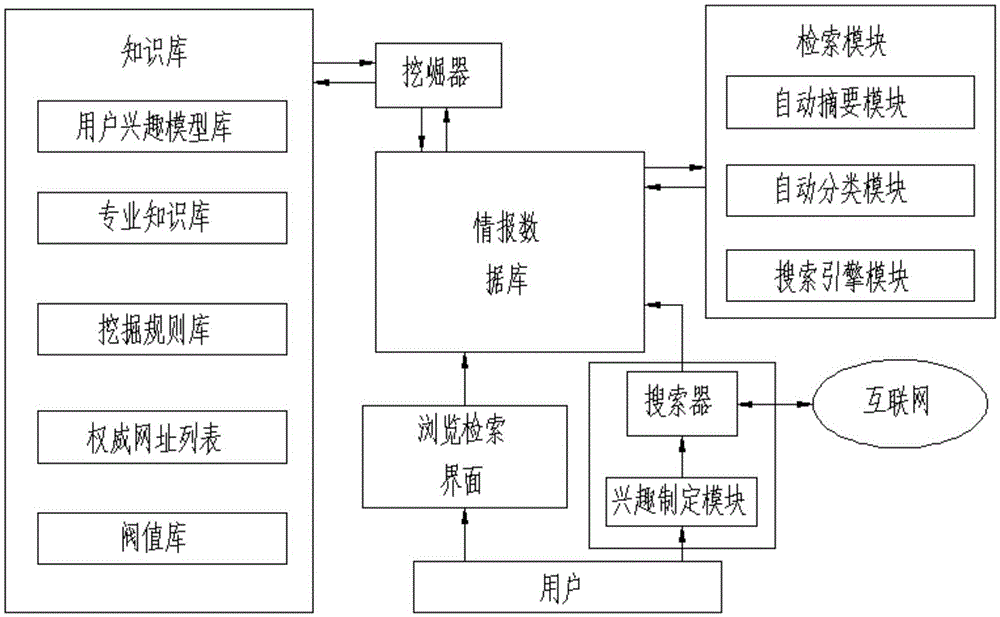
Information acquisition processing and retrieval system
InactiveCN101158963AGet it for freeFree accessSpecial data processing applicationsData miningDatabase preservation
The invention discloses a system for information collection processing and retrieving, which comprises a strategy managing module which allocates and manages the grasp strategy and the mode setting of a data mining processing module; the data mining processing module which searches according to the internet resources, saves the grasped data, extracts the valid information after identification to sieve, and writes the kept information into an information database for saving; a retrieving model which processes the information in the information database, generates the abstract information, classifies the information and constructs an index base; the information database which stors the information delivered by the data mining processing module and the returned information written by the retrieval module, and provides to a browsing and retrieving interface for retrieval; the browsing and retrieving interface which receives user query requests and retrieves via the information database. The system is able to collect information comprehensively and timely, implement automatically the subsequent processing treatment of the information, and retrieve and browse centrally.
Owner:ZTE CORP
Persistent Snapshot Methods
InactiveUS20070250663A1Memory loss protectionError detection/correctionHard disc drivePrimitive state
A persistent snapshot is taken and maintained in accordance with a novel method and system for extended periods of time using only a portion of a computer readable medium of which the snapshot is taken. Multiple snapshots can be taken in succession at periodic intervals and maintained practically indefinitely. The snapshots are maintained even after powering down and rebooting of the computer system. The state of the object of the snapshot for each snapshot preferably is accessible via a folder on volume of the snapshot. A restore of a file or folder may be accomplished by merely copying that file or folder from the snapshot folder to a current directory of the volume. Alternatively, the entire computer system may be restored to a previous snapshot state thereof. Snapshots that occurred after the state to which the computer is restored are not lost in the restore operation. Different rule sets and scenarios can be applied to each snapshot. Furthermore, each snapshot can be written to within the context of the snapshot and later restored to its pristine condition. Software for implementing the systems and methods of snapshots in accordance with the present invention may comprise firmware of a hard disk drive controller or a disk controller board or within the HDD casing itself. The present invention further comprises novel systems and methods in which the systems and methods of taking and maintaining snapshots are utilized in creating and managing temporal data stores, including temporal database management systems. The implications for data mining and exploration, data analysis, intelligence gathering, and artificial intelligence (just to name a few areas) are profound.
Owner:COLUMBIA DATA PRODUCTS
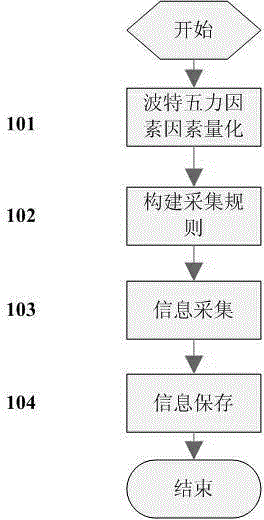
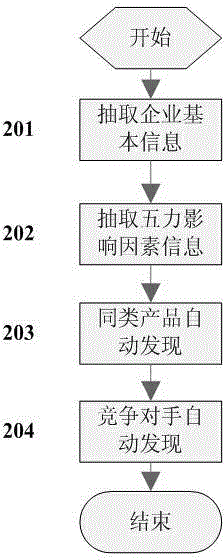
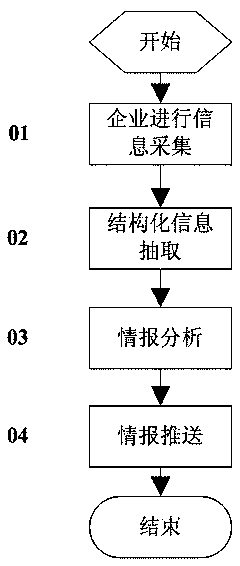
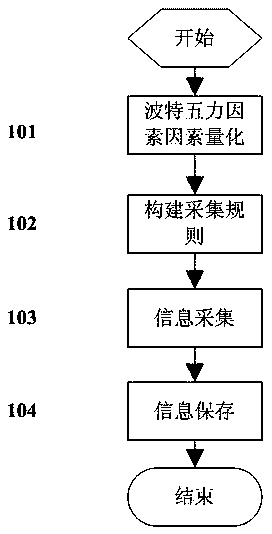
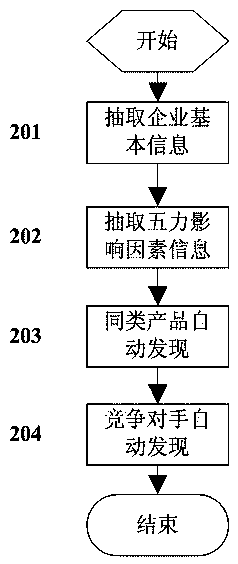
Enterprise intelligence gathering method based on Michael Porter's Five Forces Model
ActiveCN104063411AAccurate extractionResourcesSpecial data processing applicationsCompetitive intelligenceCollection methods
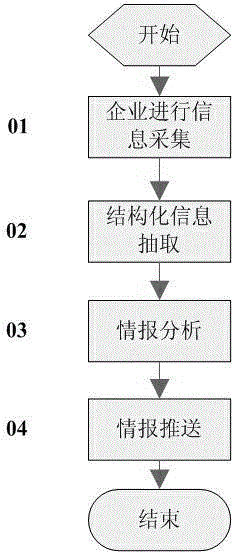
The invention discloses an enterprise intelligence gathering method based on a Michael Porter's Five Forces Model. The method comprises the steps of firstly, quantizing influence factors of potential competitors, competitors, suppliers, buyers and substitute goods in the Michael Porter's Five Forces Model, gathering an information set I according to gathering rules established by quantized factors; secondly, structurally extracting Five Forces influence factors in the set I and a structured information set S of an enterprise; thirdly, analyzing the structured information set S again, intelligently analyzing enterprise competitive intelligence, automatically finding out enterprise like products and competitors, analyzing the development trend of hot events, and finally pushing the competitive intelligence to users. The method realizes enterprise competitive intelligence gathering and confluence analysis.
Owner:JIANGSU JINGE NETWORK TECH
Mobile biometrics information collection and identification
ActiveUS9235733B2Costs of hardware modifications and associated software requirementsMinimal costDigital data authenticationProteomicsHuman bodyPattern recognition
A biometric mobile device is capable of interacting with existing cellular, wireless, and wired telecommunication and other communication networks to support intelligence gathering, human body identification, special operations and other applications. A method of collecting biometric data at an accident or crime scene may comprise, for example, utilizing a camera to photograph the accident scene, collecting key entered data that may not be otherwise obtainable, using a fingerprint scanner to collect, digitize and store fingerprint data, using a lab-on-a-chip DNA profile device for collecting and analyzing a DNA specimen and generating identification and DNA profile data for bar code entry and other means for collecting any known form of biometric data including, but not limited to, vascular facial structure, dental structure, cornea, iris or other data which may be unique or limiting for identification purposes.
Owner:BIRDWELL J DOUGLAS +2
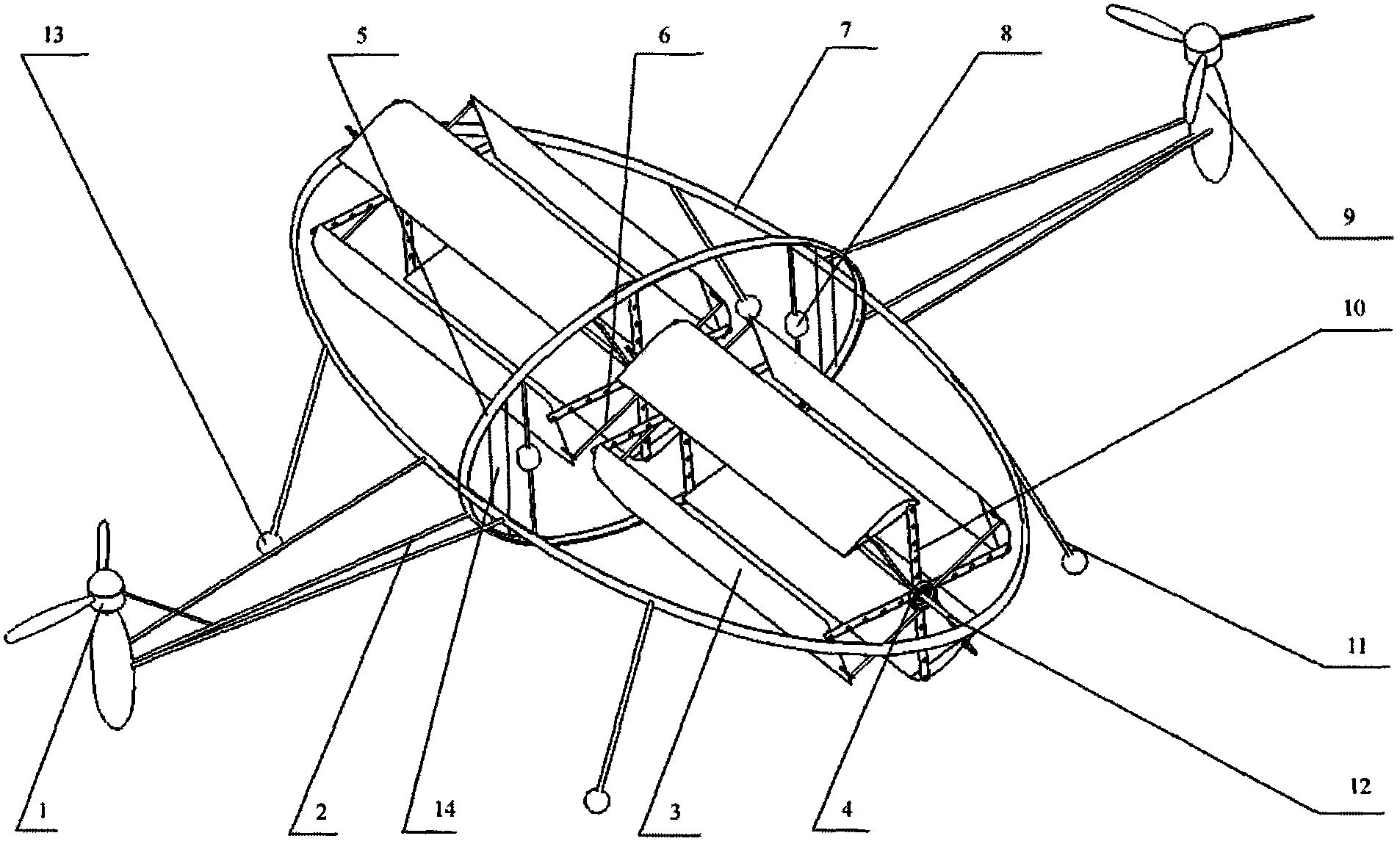
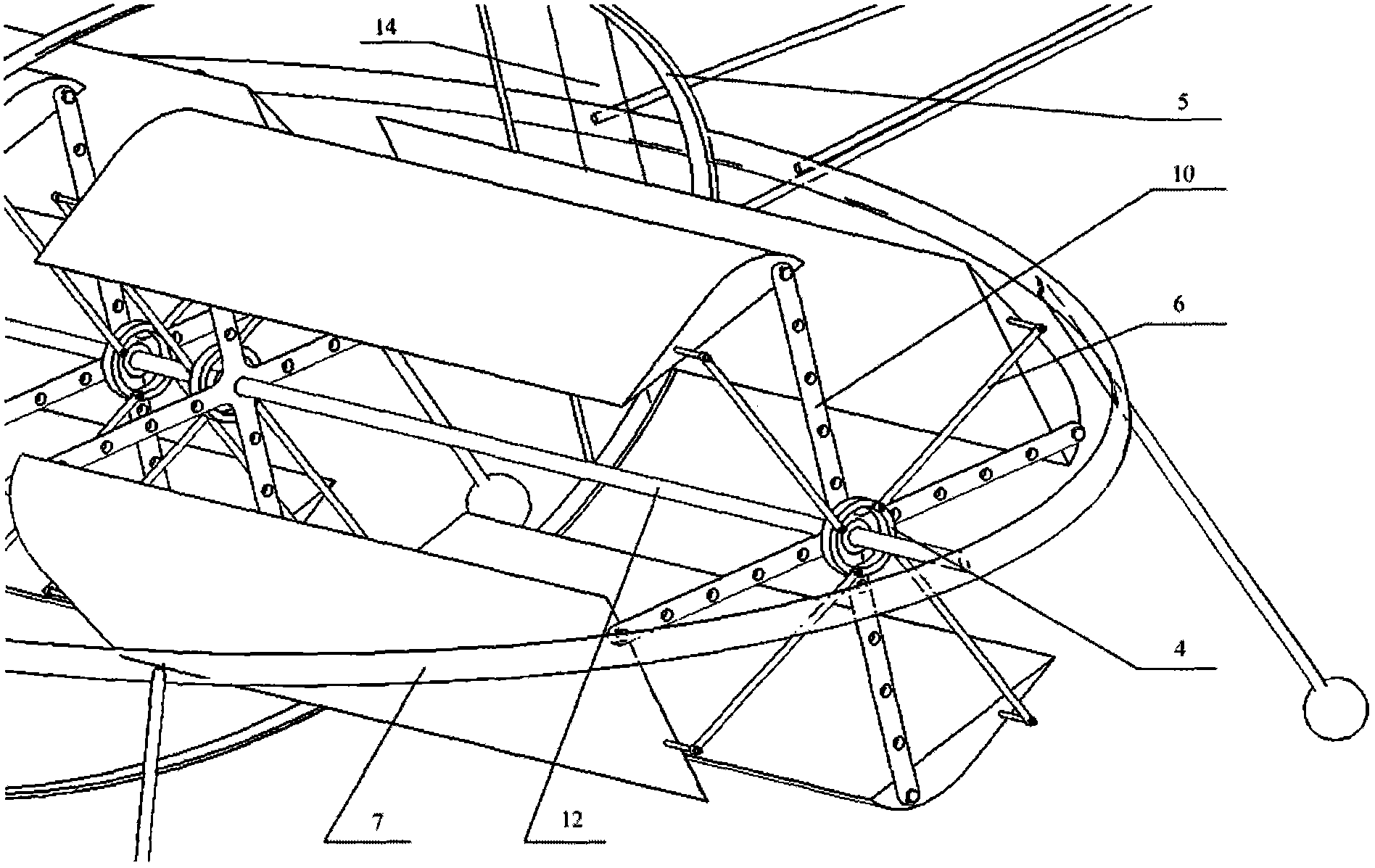
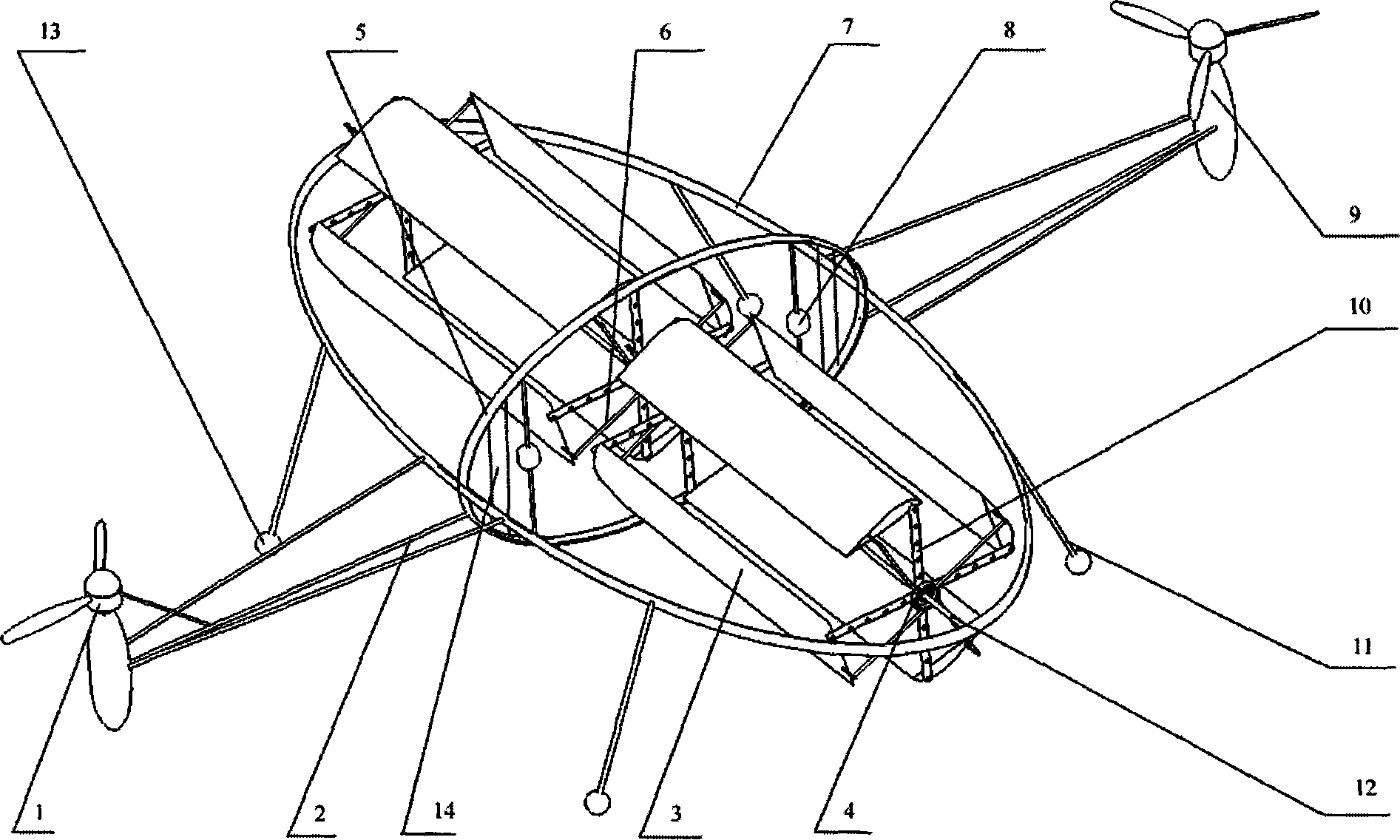
Novel aircraft
The invention relates to a novel aircraft, in particular to a cycloidal propeller aircraft. The novel aircraft is mainly characterized in that higher thrust level is provided by providing power with the aid of the combination of a cycloidal propeller and a screw propeller. The aircraft comprises a machine body, a power device, an energy source system, a control system and a bracket, wherein the machine body consists of a large elliptic frame and a small elliptic frame which are vertical two each other. The power device consists of two cycloidal propeller structures and two screw propeller structures, which interact so as to reach the purpose of maximum power; the energy source system consists of hydrogen cells so that the aircraft is green and environment friendly; and the bracket consists of a light metal rod and an elastic rubber ball, so that the aircraft has certain damping function. With the adoption of the aircraft, the low-altitude flying and parking are realized so as to execute tasks of reconnaissance, monitoring, and intelligence gathering, so that the aircraft has great practical value.
Owner:张明明 +1
Database protection system and method
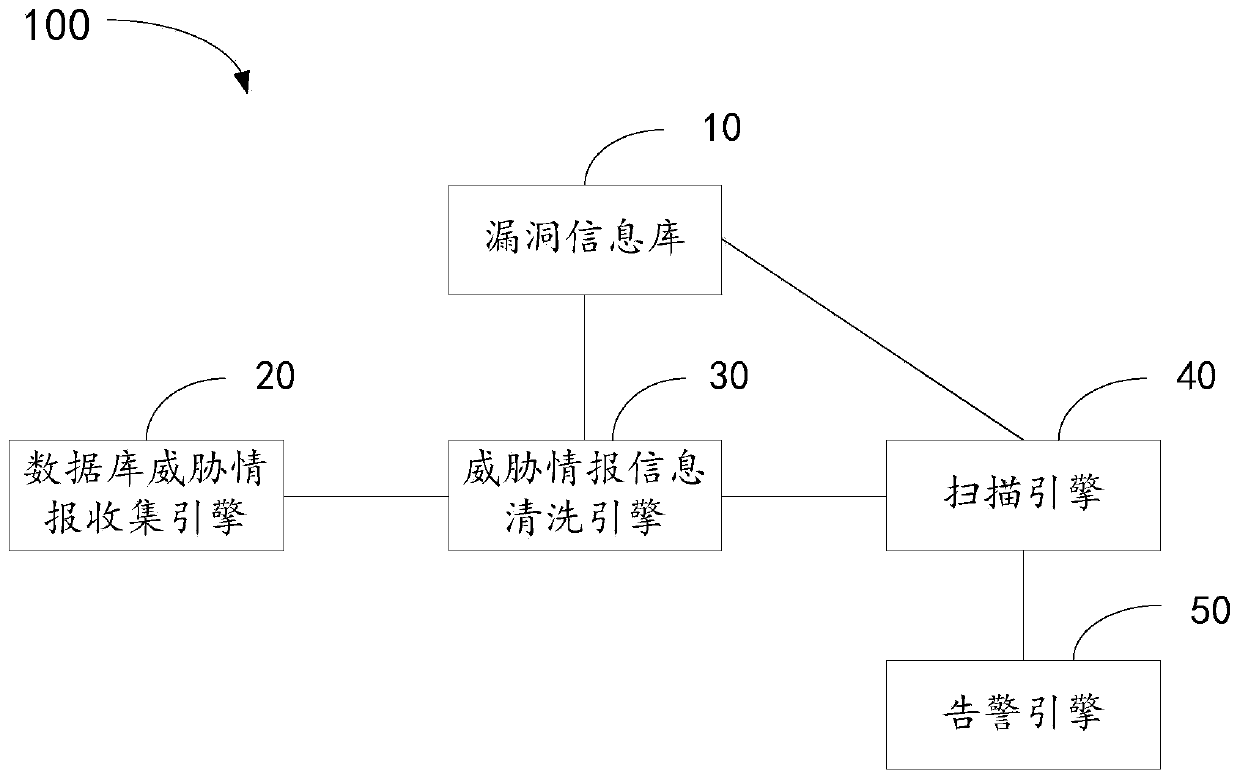
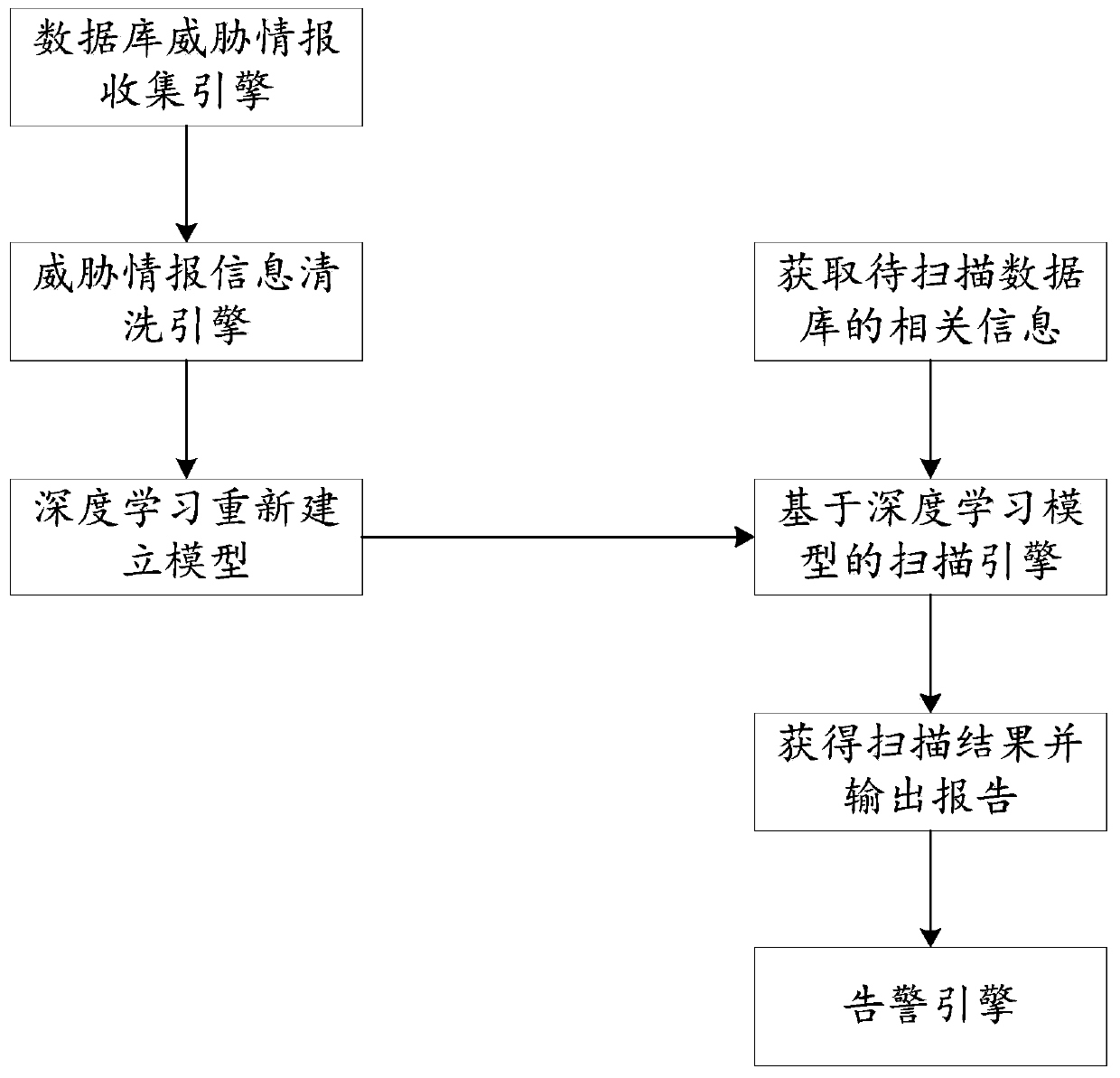
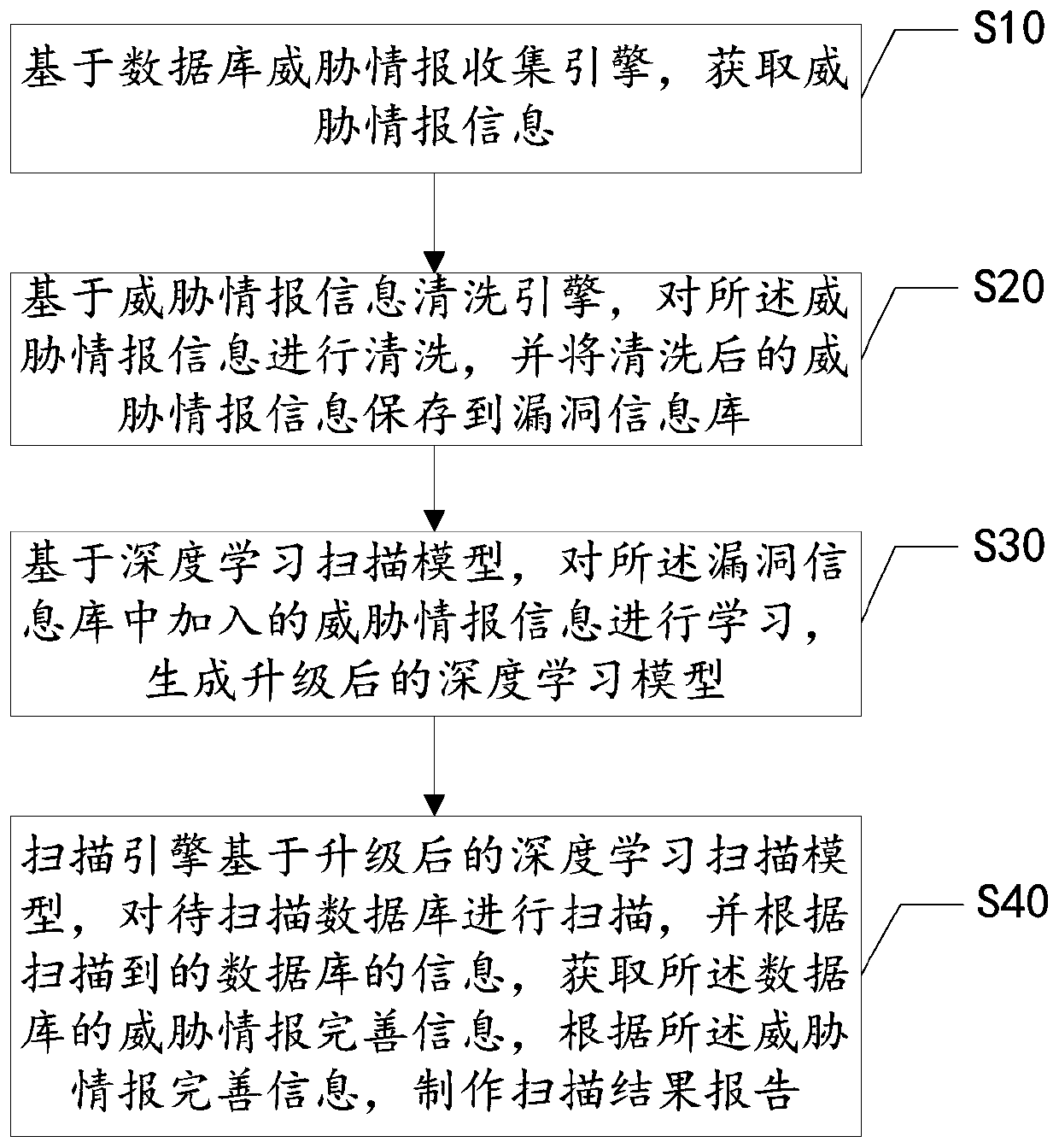
ActiveCN109871683AImprove securityScan real timePlatform integrity maintainanceMachine learningInformation repositoryProtection system
The embodiment of the invention relates to the technical field of databases, and discloses a database protection system and method, and the system comprises a vulnerability information library which is used for storing threat intelligence information; The database threat intelligence collection engine is used for acquiring threat intelligence information; The threat intelligence information cleaning engine is used for cleaning the threat intelligence information and storing the cleaned threat intelligence information into the vulnerability information base; The deep learning scanning model isused for learning the threat information added into the vulnerability information base and generating an upgraded deep learning scanning model; And the scanning engine is used for carrying out vulnerability scanning on the to-be-scanned database based on the upgraded deep learning model, obtaining threat information perfection information and making a scanning result report. Through the mode, thetechnical problem that the latest vulnerability threat information cannot be scanned in real time at present is solved, vulnerability scanning is faster and more accurate, and the security of a database is improved.
Owner:SHENZHEN ANTECH TECH
Online reputation monitoring and intelligence gathering
A system and method is provided for an automated online reputation monitoring and intelligence gathering solution that also provides services that manage a reputation once content damaging to the reputation has been identified. Functions and services of the automated online reputation monitoring and intelligence gathering solution include the aggregation of information from non-proprietary websites and social networks, the ability to contact support for assistance with reputation management, the ability to submit requests to fix online reputation, and the delivery of alerts directly to a user device.
Owner:BIZHIVE LLC
On-line monitoring device and method for vibration and noise in metro
PendingCN110031084AFully reflect the stabilityGuaranteed stabilitySubsonic/sonic/ultrasonic wave measurementUsing electrical meansVibration accelerationData acquisition
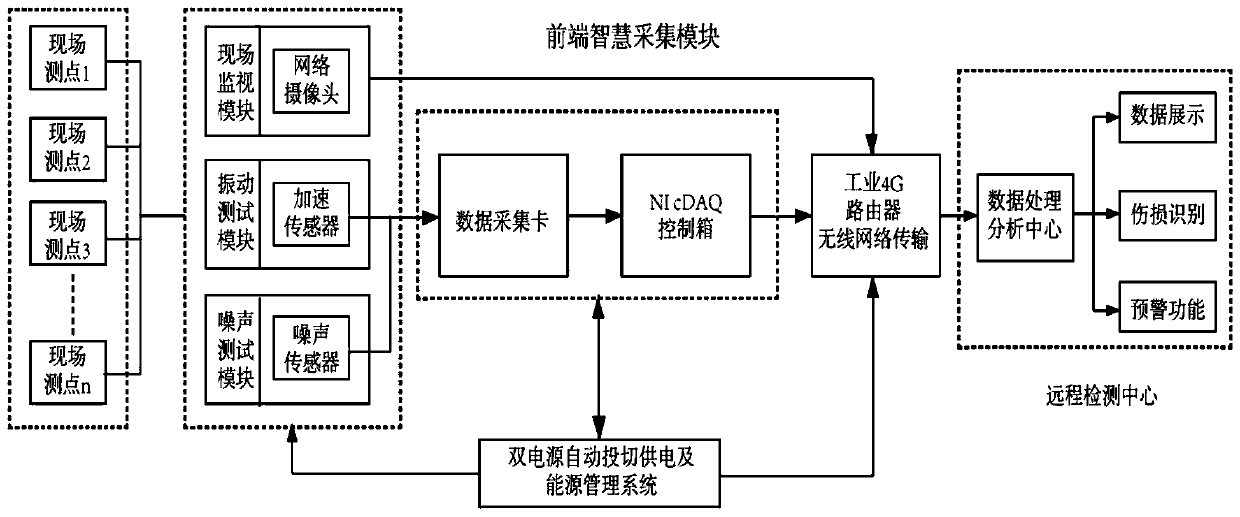
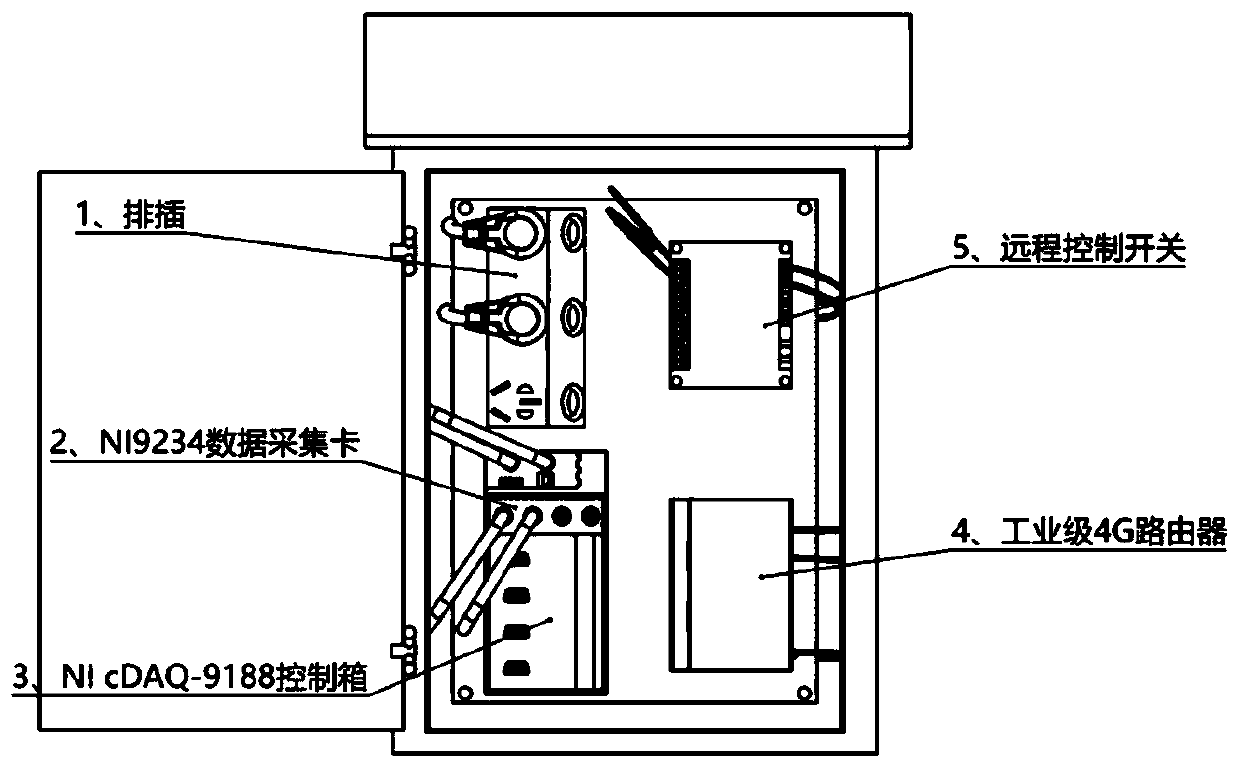
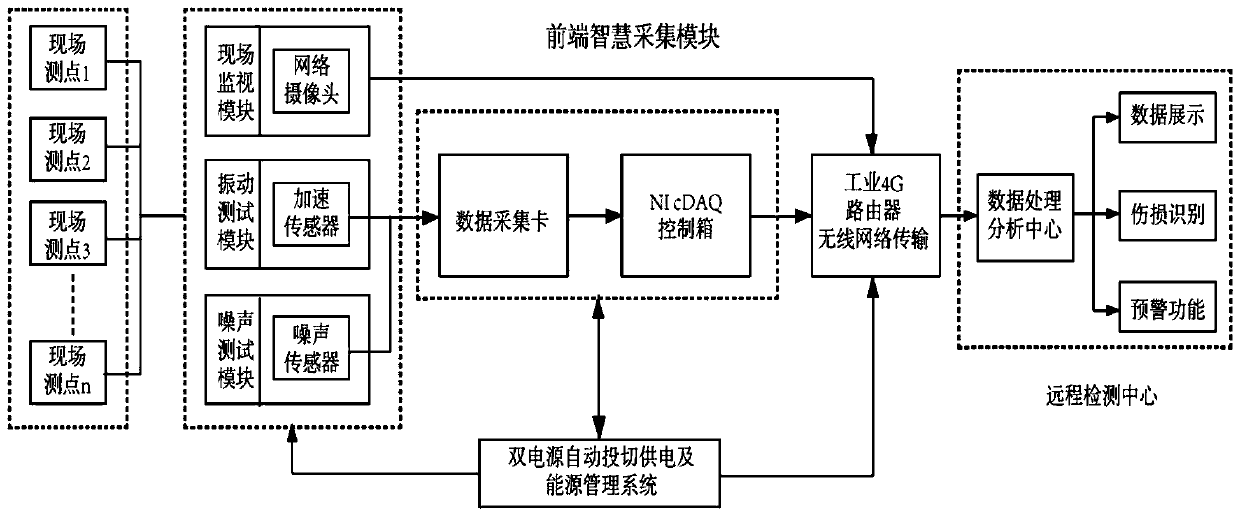
The invention relates to an on-line monitoring device and method for vibration and noise in a metro. The on-line monitoring device wirelessly communicates with a remote monitoring center, and comprises front-end intelligence gathering modules correspondingly arranged at multiple site measuring points, the front-end intelligence gathering modules comprise sound pressure sensors, vibration acceleration sensors, outdoor cameras, NI Ethernet computer cases and industrial grade 4G routers, the NI Ethernet computer cases are correspondingly connected with the sound pressure sensors, the vibration acceleration sensors and the outdoor cameras through data acquisition cards, and wirelessly communicate with the remote monitoring center through the industrial grade 4G routers, the sound pressure sensors are arranged at a horizontal distance of 700 mm away from an outer side steel rail, and the vibration acceleration sensors are arranged at the side wall of a ballast bed 50 mm below the ballast bed surface. Compared with the prior art, the on-line monitoring device has the advantages of high acquisition accuracy, being applicable to noise and vibration sensitive areas, ensuring the stability and safety of the rail and the like.
Owner:SHANGHAI UNIV OF ENG SCI
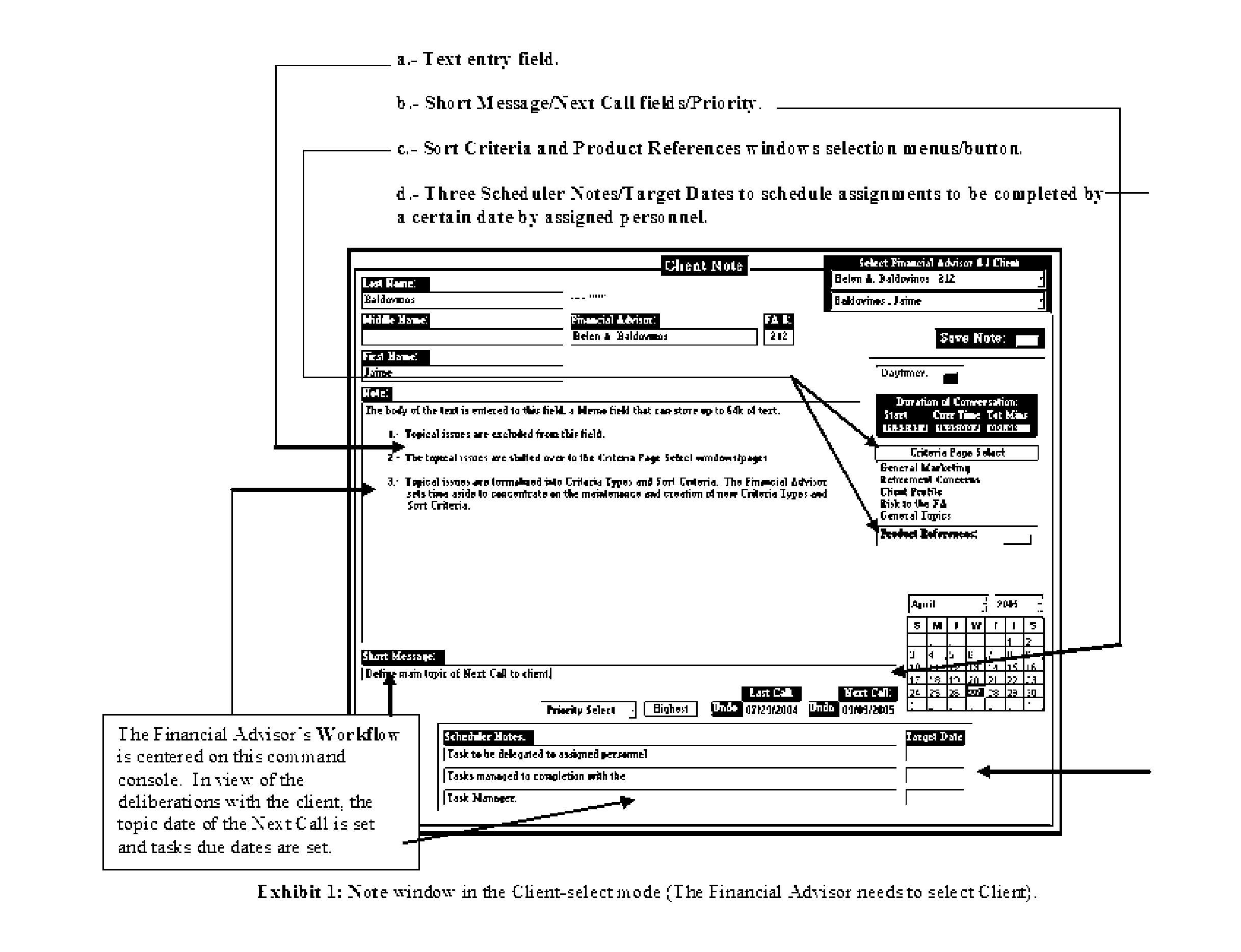
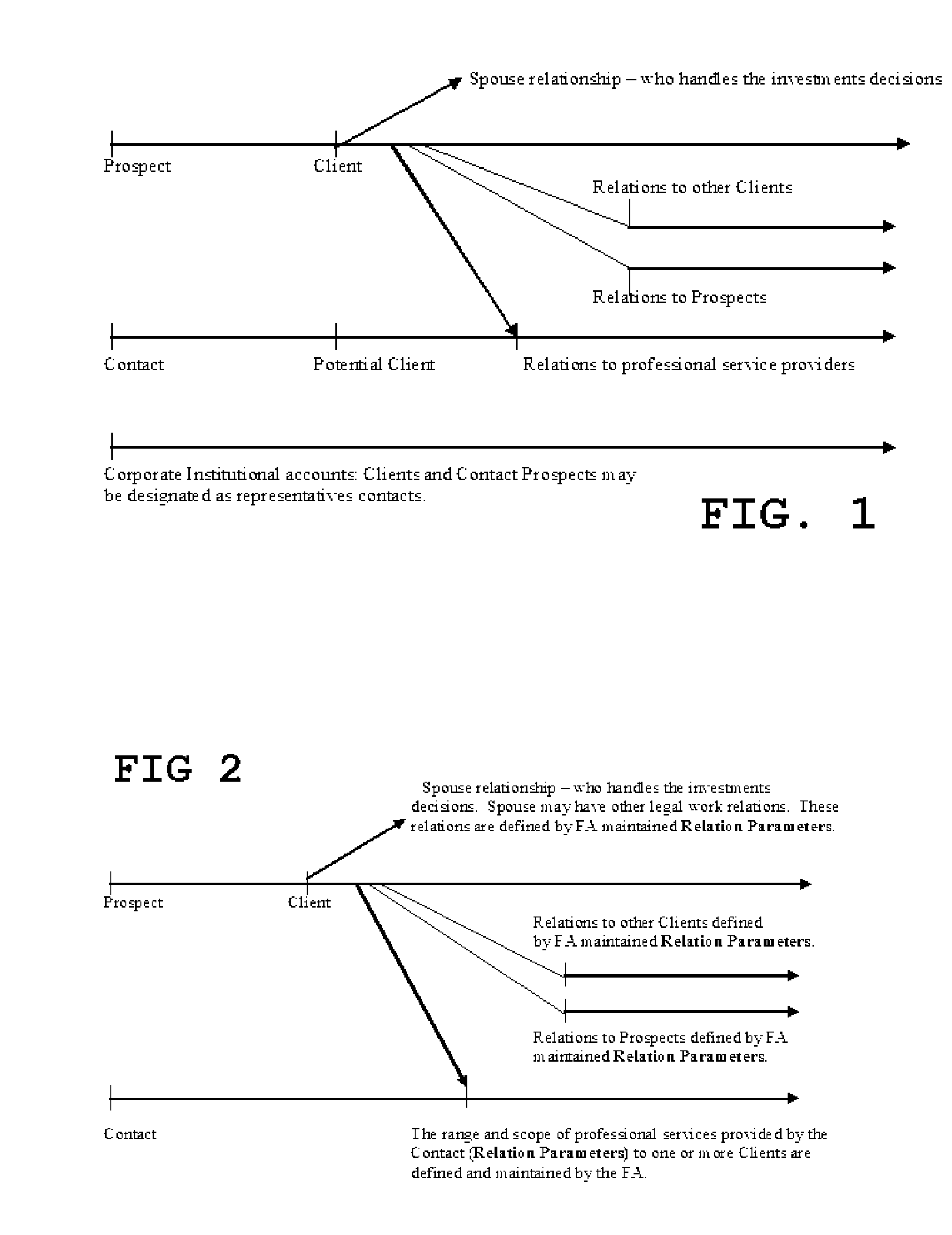
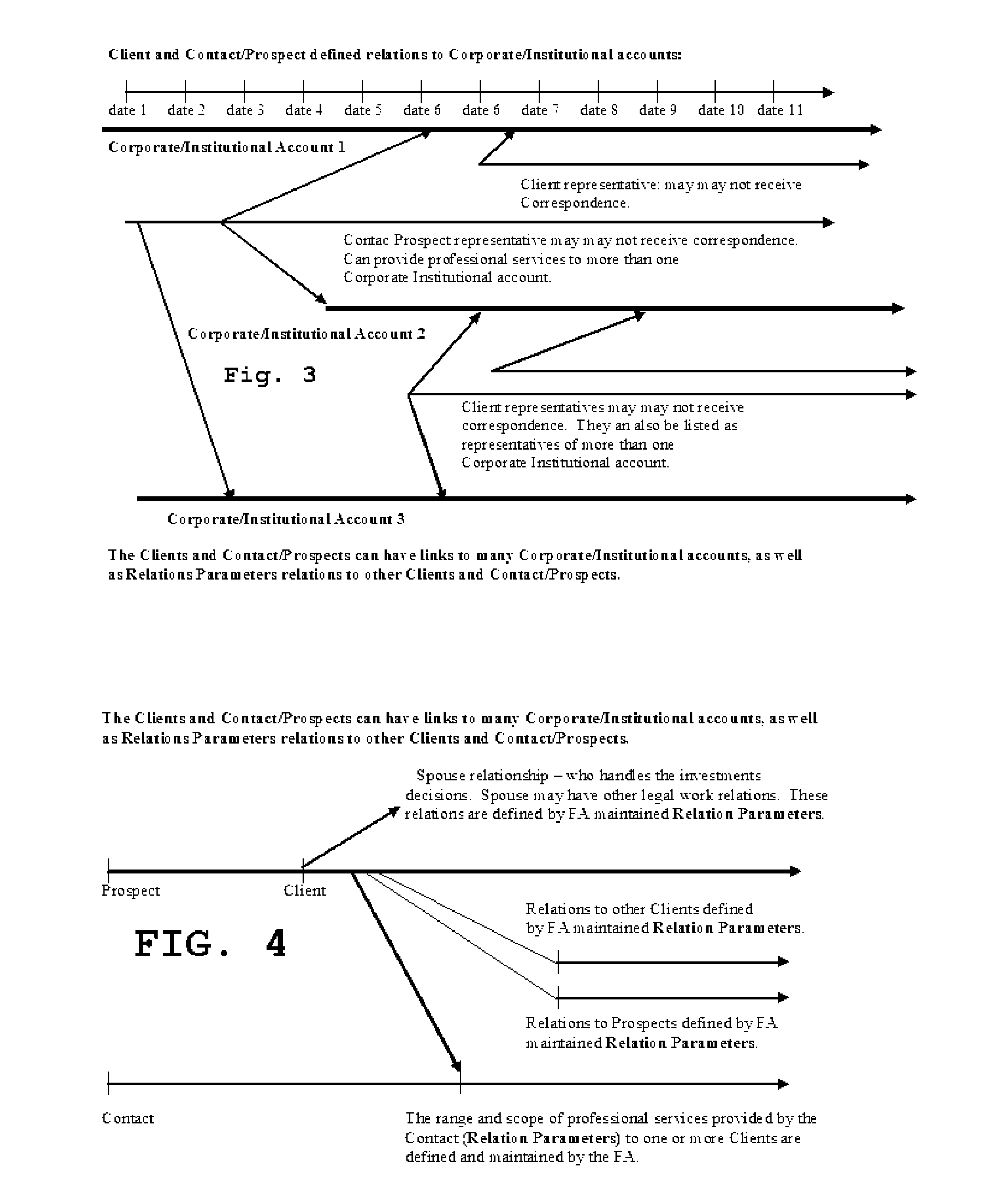
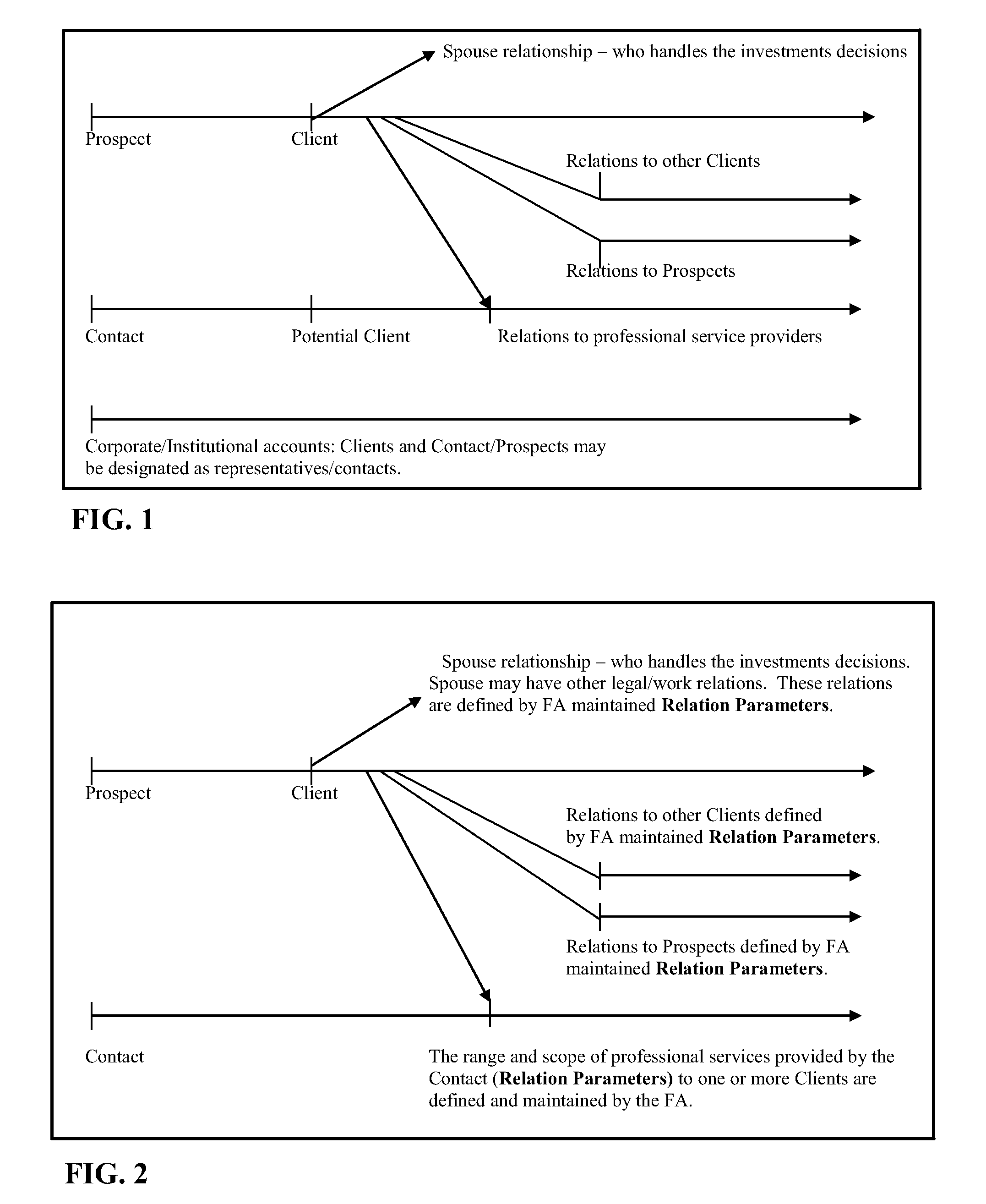
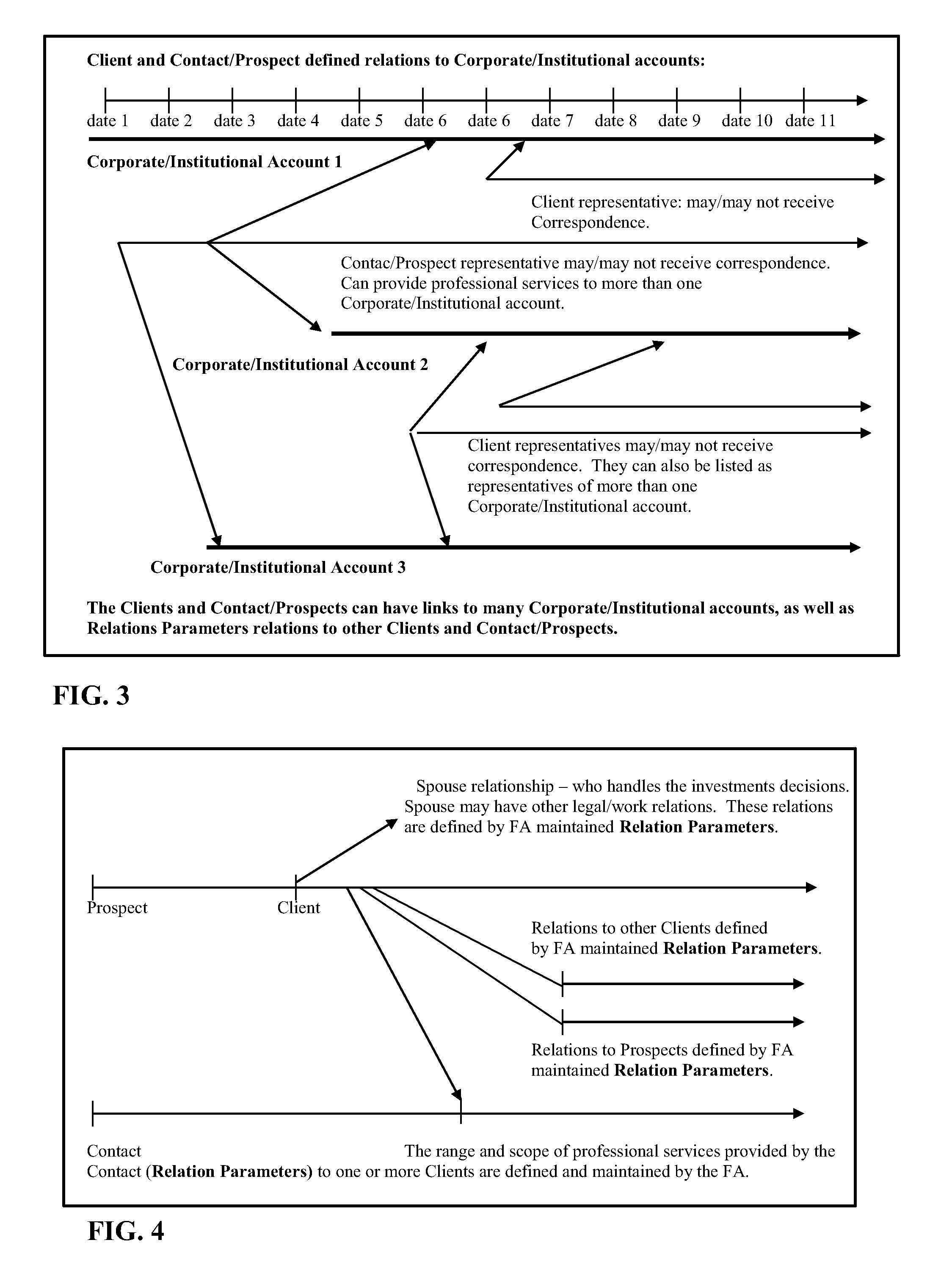
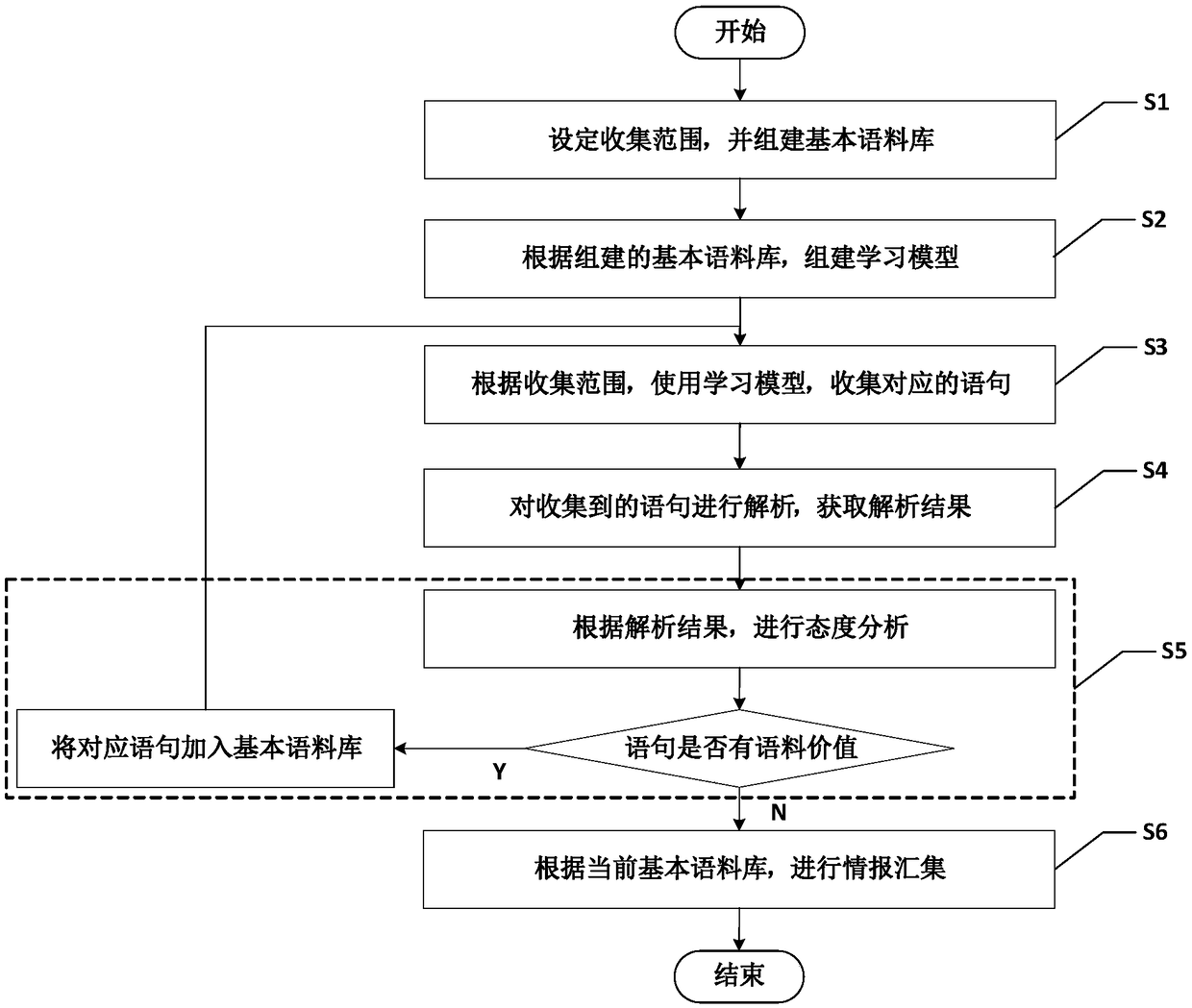
IntelligentAdvisor TM , a contact, calendar, workflow, business method, and intelligence gathering application
InactiveUS20070041574A1Overcomes many short fallsFacilitates a user's associative intellectFinanceDigital data processing detailsSubjective dataMarket place
The invention is a contact, calendar, workflow, and intelligence gathering application that allows a user, such as a financial advisor to collect, codify and analyze objective and subjective data regarding clients, corporate / institutional accounts, contacts / prospects, financial products and market trends. The invention assists a financial advisor in batch calling, scheduling work, delegating tasks and facilitating associative intellect, allowing a user to test hunches or “wispy thoughts” to discovery client and market trends.
Owner:BALDOVINOS JAIME
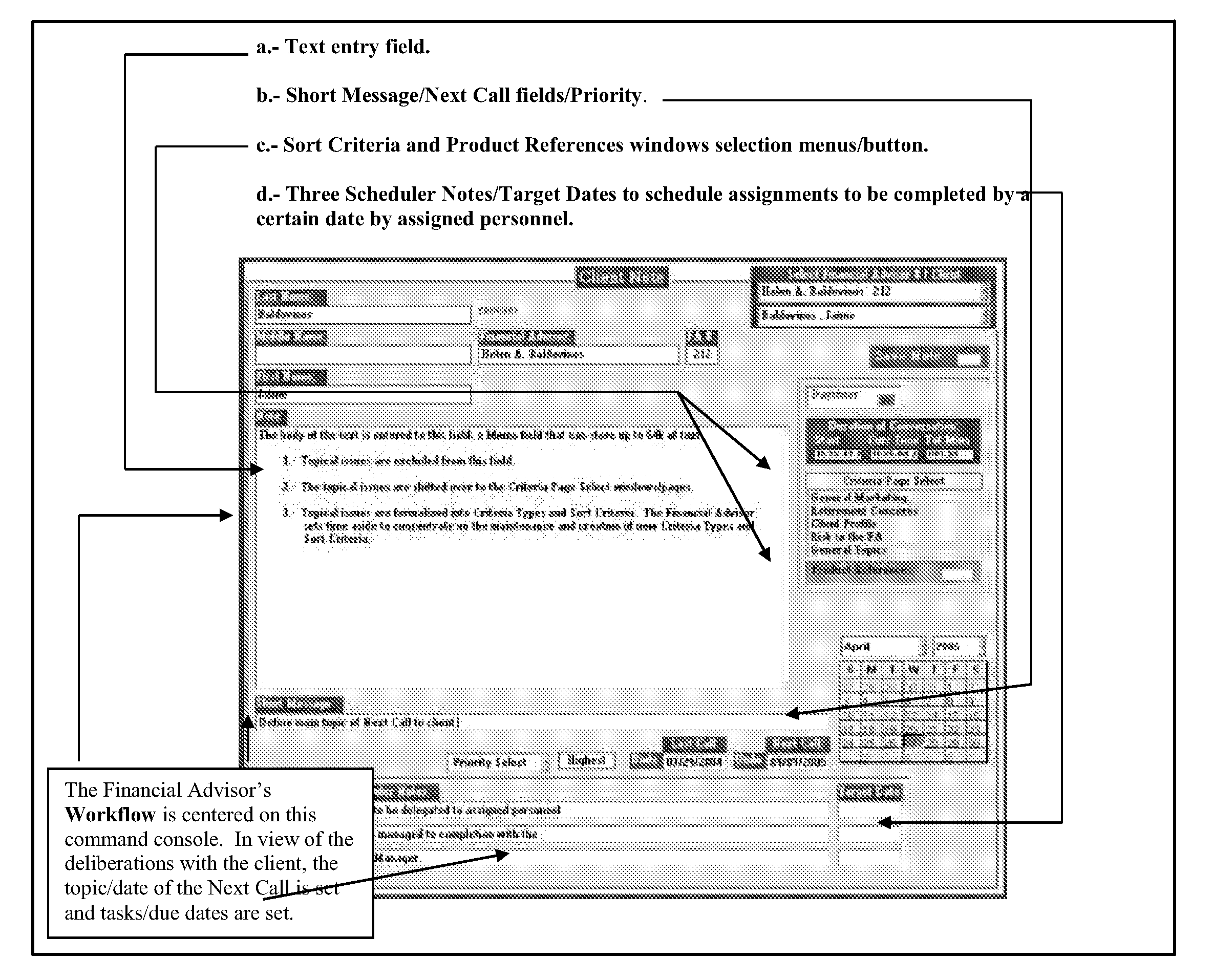
IntelligentAdvisor.TM., a contact, calendar, workflow, business method, and intelligence gathering application
InactiveUS7895200B2Overcomes many short fallsFacilitates a user's associative intellectFinanceDigital data processing detailsSubjective dataApplication software
The invention is a contact, calendar, workflow, and intelligence gathering application that allows a user, such as a financial advisor to collect, codify and analyze objective and subjective data regarding clients, corporate / institutional accounts, contacts / prospects, financial products and market trends. The invention assists a financial advisor in batch calling, scheduling work, delegating tasks and facilitating associative intellect, allowing a user to test hunches or “wispy thoughts” to discovery client and market trends.
Owner:BALDOVINOS JAIME
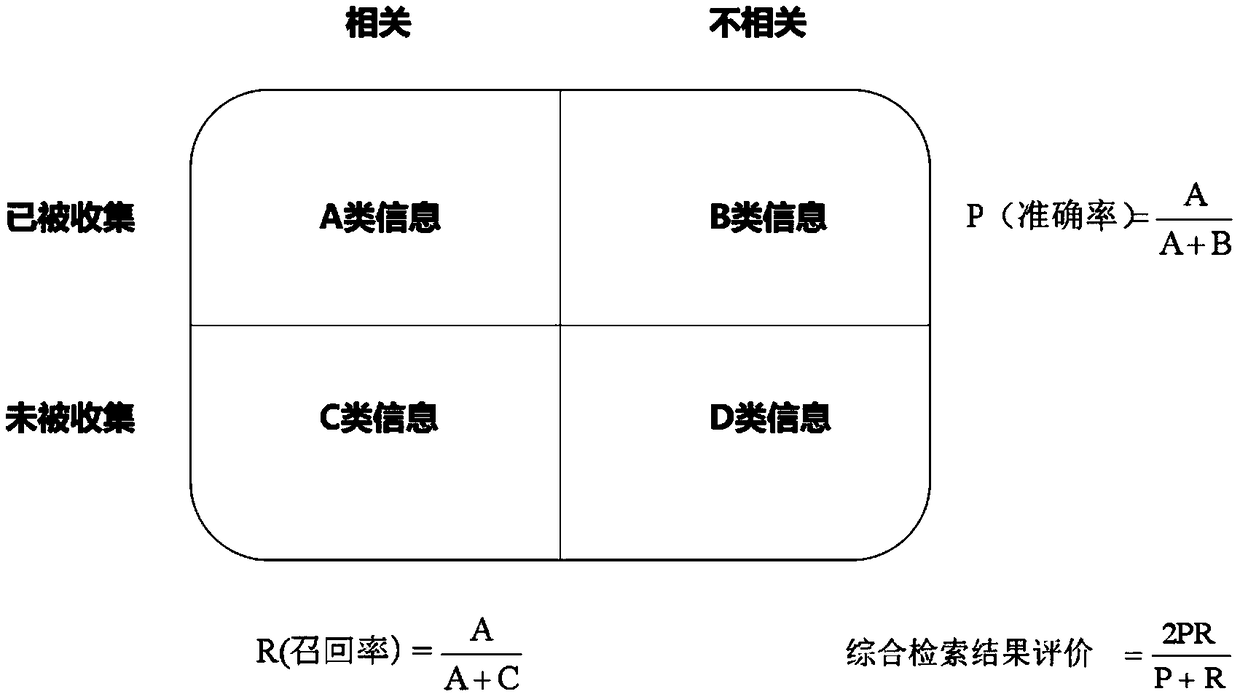
A business intelligence gathering method based on natural language processing
InactiveCN109299248AImprove accuracyImprove domain adaptabilityNatural language data processingSpecial data processing applicationsBusiness intelligenceCollection methods
The invention belongs to the field of data processing, and discloses a business information collection method based on natural language processing, comprising the following steps: S1, setting a collection range and establishing a basic corpus; S2: Constructing the learning model according to the basic corpus; S3, according to the collection scope, using the learning model to collect the corresponding statements; S4, parsing the collected statements to obtain the parsing result; 5, perform attitude analysis according to that analyze result, judging whether the sentence has corpus value, if yes,adding the correspond sentence into the basic corpus, and returning to the step S3, otherwise directly entering the step S6; 6, collect information according to that current basic corpus; The invention solves the problems of the prior art that the timeliness, the safety, the accuracy and the continuity of the service can not be guaranteed.
Owner:成都航天科工大数据研究院有限公司
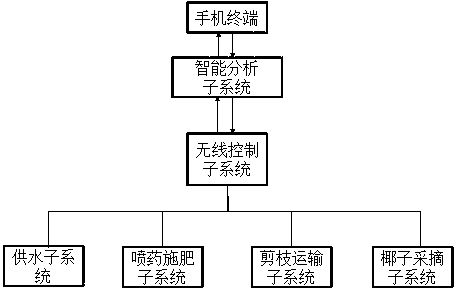
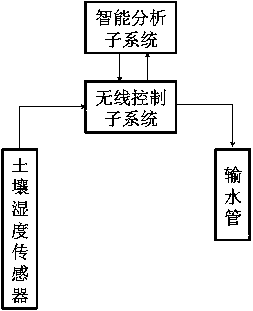
Intelligent detecting and processing system for agricultural condition information of coconut groves
InactiveCN107765670AStay in touchInnovative design ideasComputer controlSimulator controlTreatment optionsComputer science
The present invention relates to an intelligent detection and processing system of coconut grove agricultural situation information, which consists of a mobile phone terminal, an intelligent analysis subsystem, a wireless control subsystem, a water supply subsystem, a pesticide spraying and fertilization subsystem, a pruning and transportation subsystem, and a coconut picking subsystem. The composition belongs to the field of intelligent agricultural equipment technology. The intelligent detection and processing system of the coconut grove agricultural information provided by the present invention can collect the agricultural information of the coconut planting process in real time and make a quick processing plan, which can greatly improve the efficiency of the coconut grove water supply, fertilization, spraying, pruning, and picking. , can promote the intelligent development of the coconut planting industry of Hainan coconut.
Owner:HAINAN UNIVERSITY
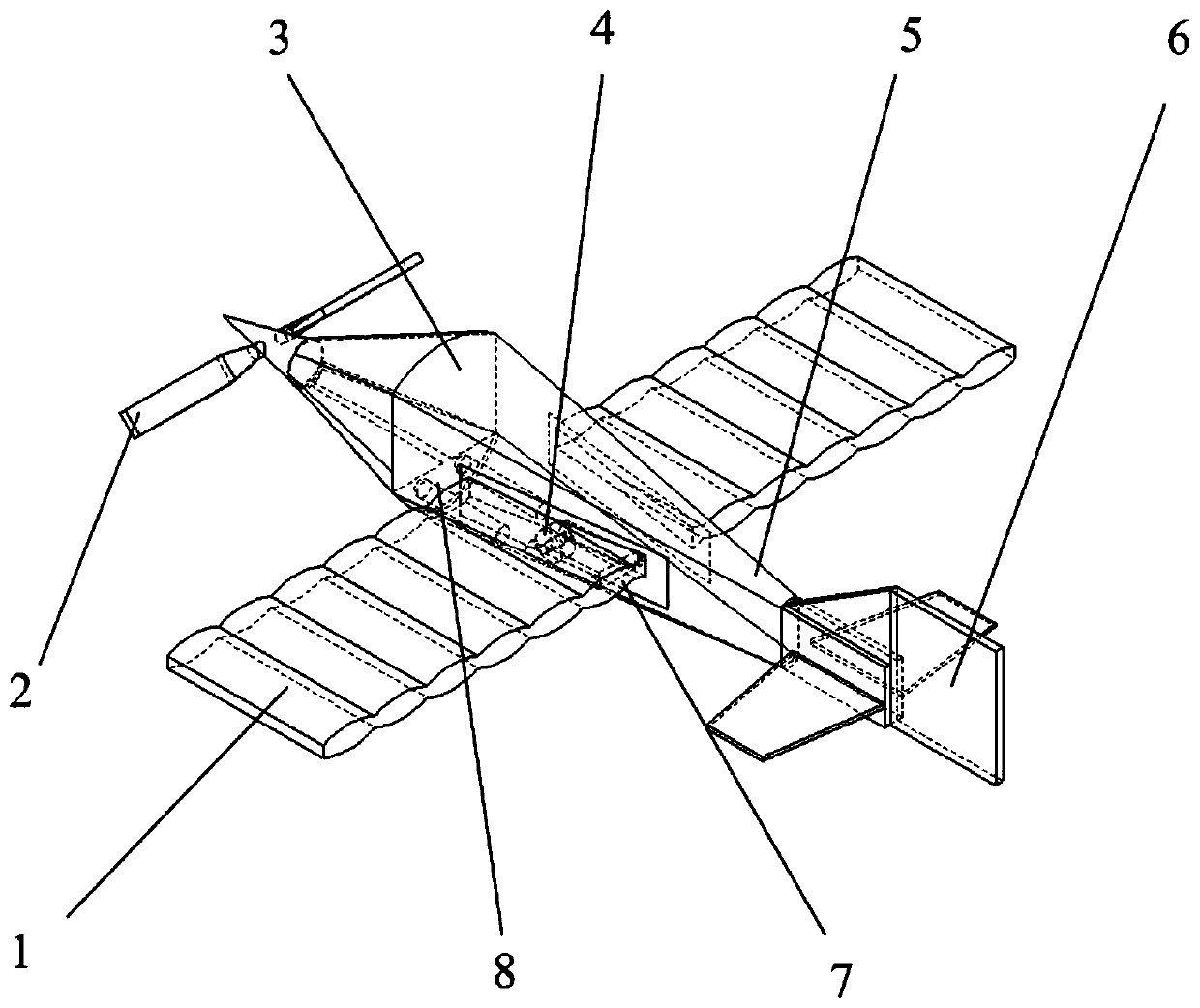
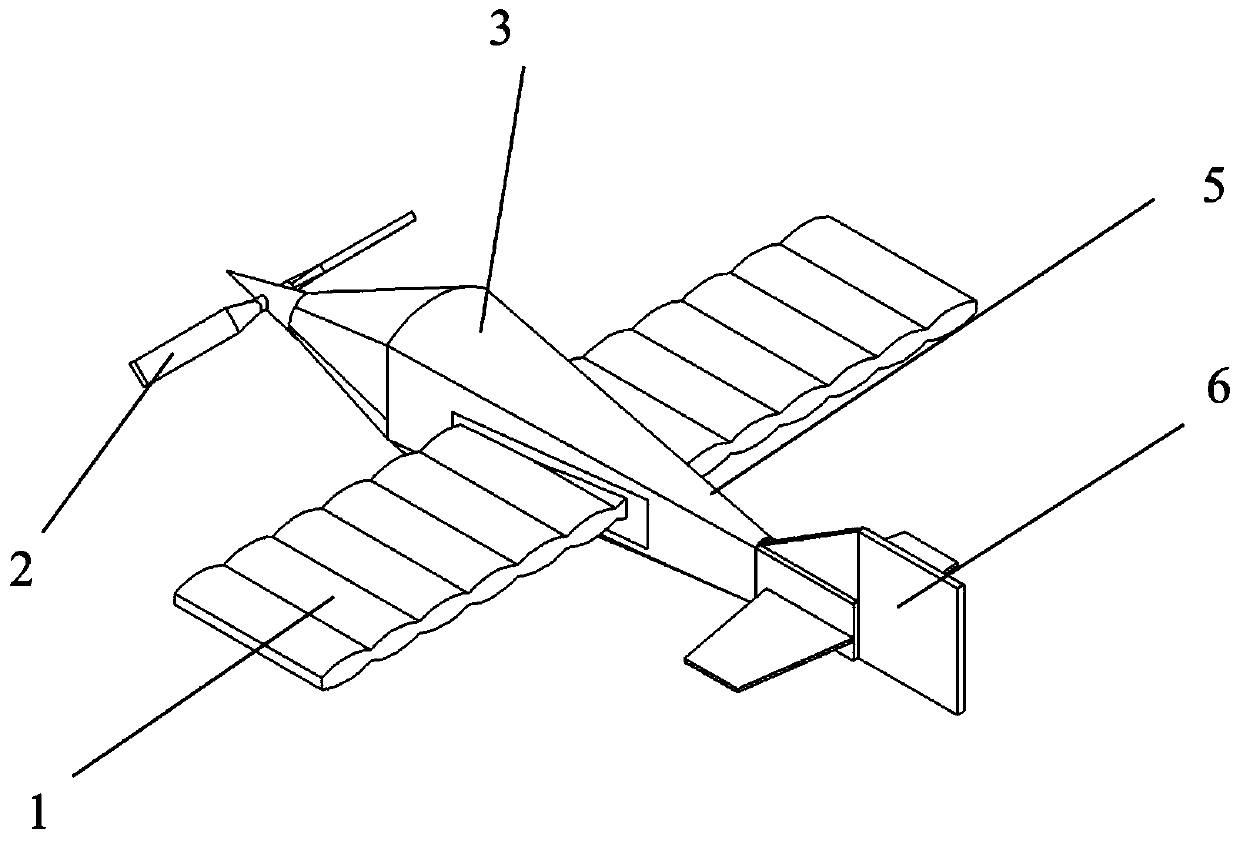
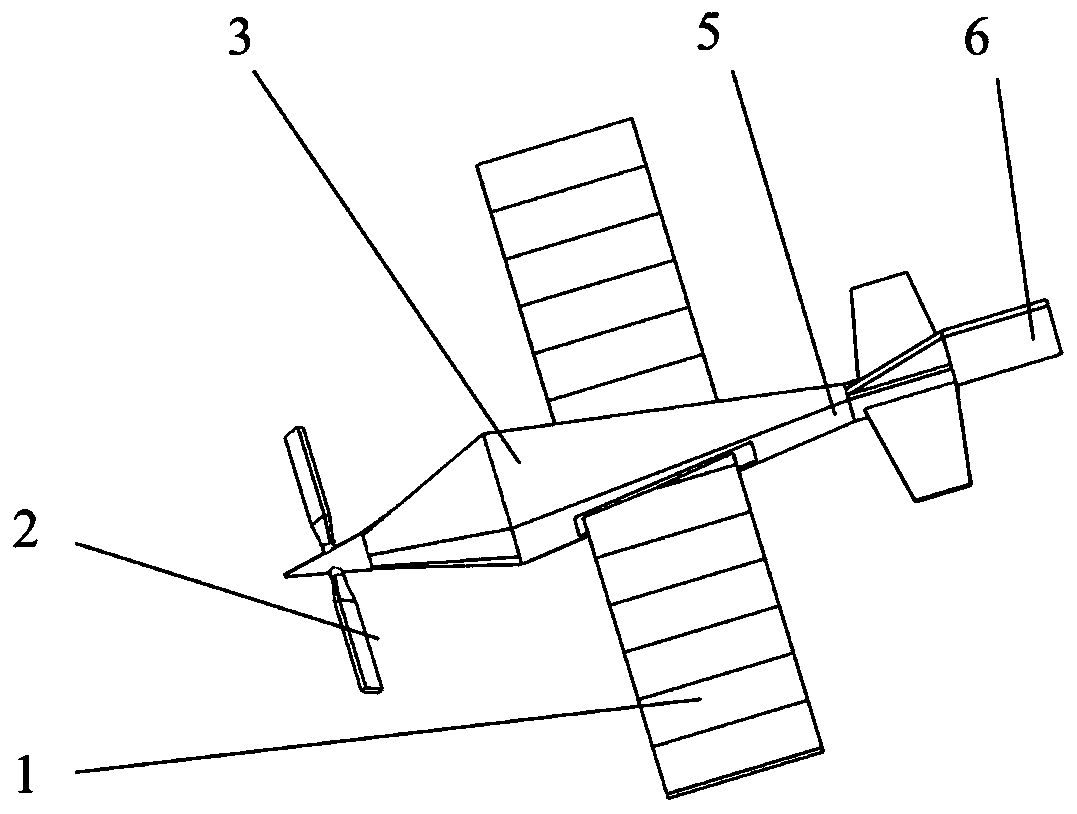
Intelligent flexible inflatable wing unmanned aerial vehicle structure
ActiveCN110371283AMake up for deficienciesImprove playbackWing adjustmentsFuselagesGas cylinderUsability
The invention provides an intelligent flexible inflatable wing unmanned aerial vehicle structure, which comprises intelligent flexible inflatable wings, a propeller, a body, a landing gear, a protective cover, an empennage, a high-pressure gas storage bottle, a missile weapon, other universal parts (9) and the like. The intelligent flexible inflatable wing unmanned aerial vehicle structure can befoldable and is small in size, light in weight, simple in structure, low in energy consumption, long in cruising time and higher in rapid maneuverability and anti-interference characteristic; the flexible inflatable wings can be quickly unfolded under a high-pressure inflation condition; the defects of a fixed-wing unmanned aerial vehicle are greatly made up under a condition that the requirementsfor the usability of the unmanned aerial vehicle are met, and the performance of the intelligent unmanned aerial vehicle is well exerted; the minimization of unmanned aerial vehicle is realized, thestorage, carrying and transportation are facilitated, and various functional advantages such as rapid reconnaissance, observation, emergency communication, disaster situation monitoring, rescue, intelligence gathering, fast enemy response and fight and the like of the unmanned aerial vehicle on a target area can be realized.
Owner:NAT UNIV OF DEFENSE TECH
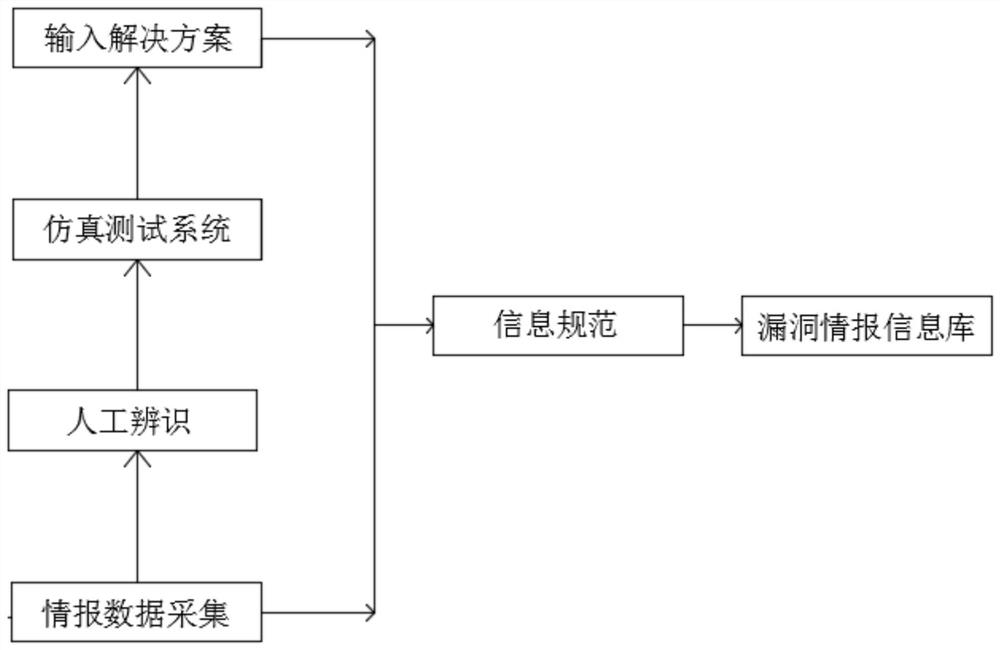
Information network unified vulnerability multi-dimensional security intelligence collection, analysis and management system
PendingCN112615812AImprove safety management levelData switching networksInformation repositoryInformation networks
The invention discloses an information network unified vulnerability multi-dimensional security intelligence collection, analysis and management system. The system comprises an intelligence data collection module, a manual identification module, a simulation test module, an input solution module, an input information standardization module and a vulnerability intelligence information base module. According to the information network unified vulnerability multi-dimensional security intelligence collection, analysis and management system, for collected original security intelligence, firstly, manual identification is carried out, credibility and possible harmfulness of the original security intelligence are preliminarily evaluated, then the security intelligence is submitted to the simulation test system module for test verification, and a general solution is given, so that a solution is provided for subsequent repair or reinforcement inpu. After the original security intelligence is analyzed and verified, the intelligence, the solution and other achievement information are normalized to form a vulnerability intelligence information specification required by the system, and the vulnerability intelligence information specification is stored in a vulnerability intelligence information base, so that the vulnerability intelligence information is convenient to use or manage by the system.
Owner:GUIZHOU POWER GRID CO LTD
Enterprise Intelligence Collection Method Based on Porter's Five Forces Model
ActiveCN104063411BAccurate extractionResourcesSpecial data processing applicationsCompetitive intelligenceCollection methods
Owner:JIANGSU JINGE NETWORK TECH
An information collection, processing and retrieval system
InactiveCN103530398BImprove filtering effectImplement classificationWeb data indexingKnowledge representationInformation processingThe Internet
Owner:合山市科学技术情报研究所
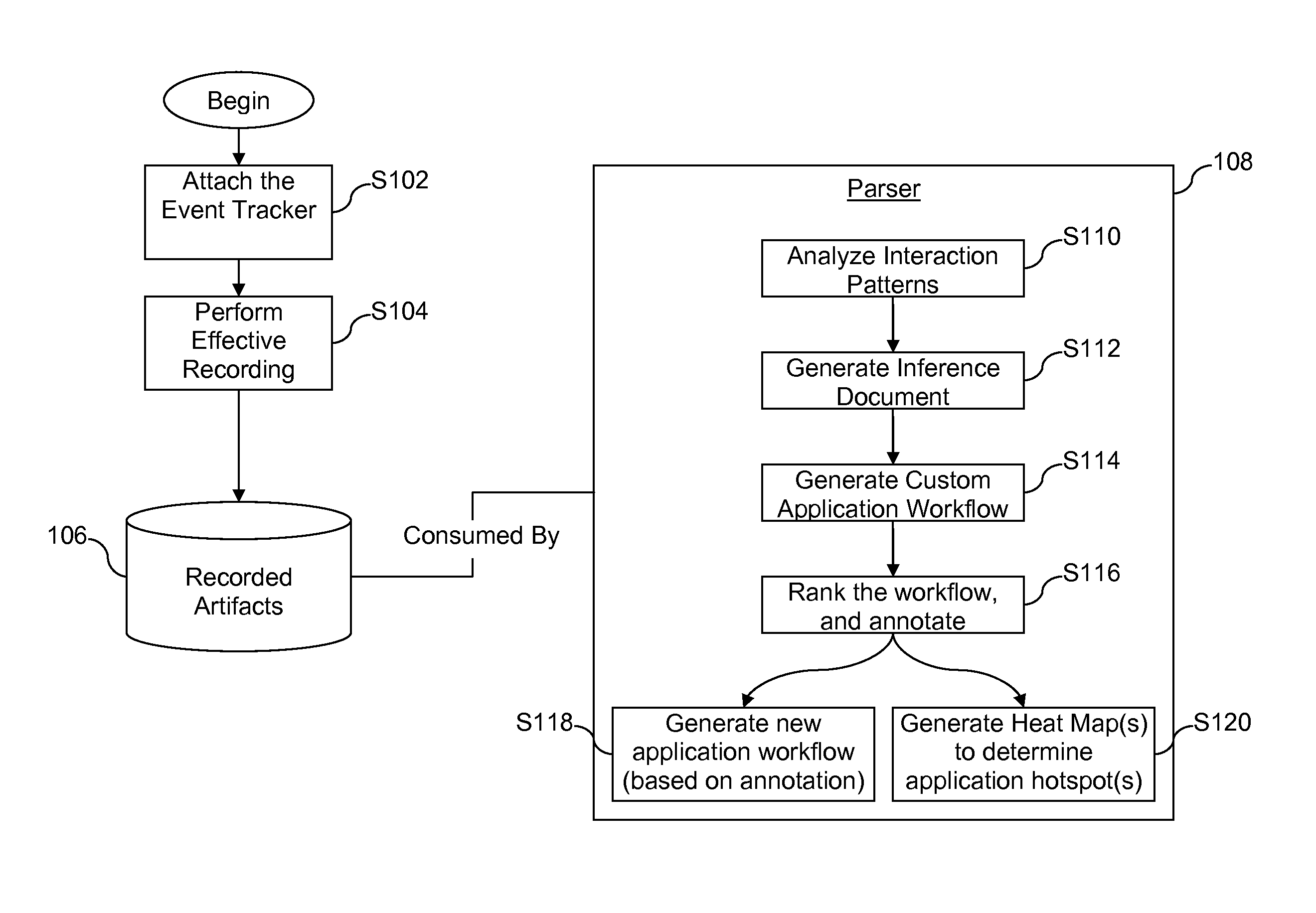
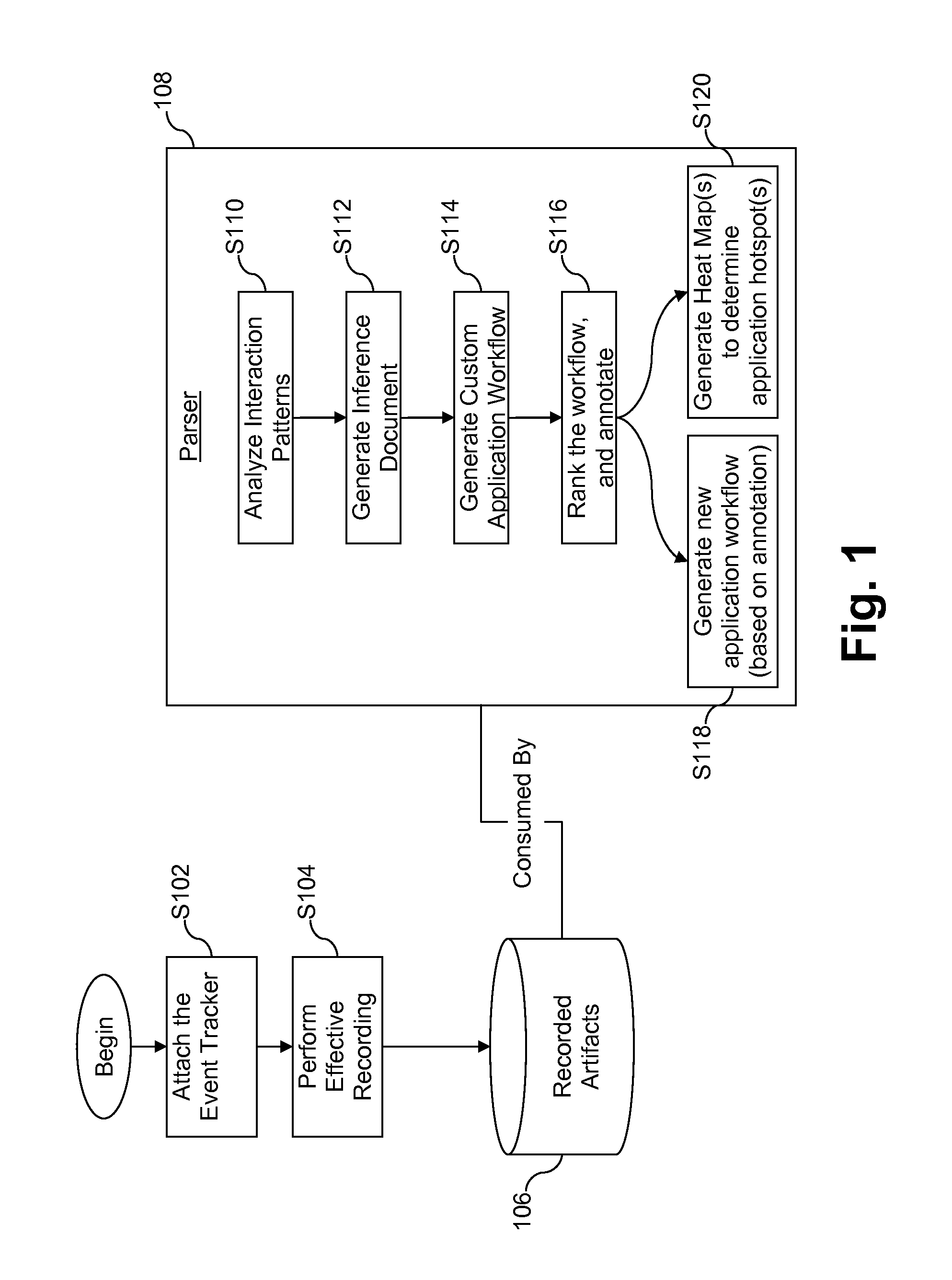
Methods for building application intelligence into event driven applications through usage learning, and systems supporting such applications
Certain example embodiments relate to application intelligence gathering systems and / or methods, e.g., in connection with Event Driven Applications and / or the like. More particularly, certain example embodiments relate to the effective recording of application evolution and usage information for usage learning and / or event auditing purposes. With respect to usage learning, certain example embodiments may help to capture data on the usage patterns and / or apply learning algorithms that work on the captured data to provide required intelligence to the application. With respect to event auditing, certain example embodiments may help to identify the “who”, “what”, “when”, “where”, “how”, and / or “why” of particular operations. Application intelligence optionally may be used in determining application “hotspots” or commonly used features that could help in areas such as application maintenance, performance tuning, and / or the like.
Owner:SOFTWARE AG
System and method including distributed intelligence among communication nodes
InactiveCN107148797ANetwork topologiesInter user/terminal allocationTelecommunications linkDistributed intelligence
An illustrative example communication system designed according to an embodiment of this invention includes a controller and a data storage accessible by the controller. The data storage includes information indicating possible communication links among communication devices within a selected region. At least one node communicates with user devices. The at least one node has an intelligence gathering module that detects at least one signal from at least one other network device capable of communicating with user devices, and processes information regarding the at least one other network device based on the at least one detected signal. The at least one node communicates the information regarding the at least one other network device to the controller and the controller includes the information regarding the at least one other network device in the stored information of the data storage.
Owner:ALCATEL LUCENT SAS
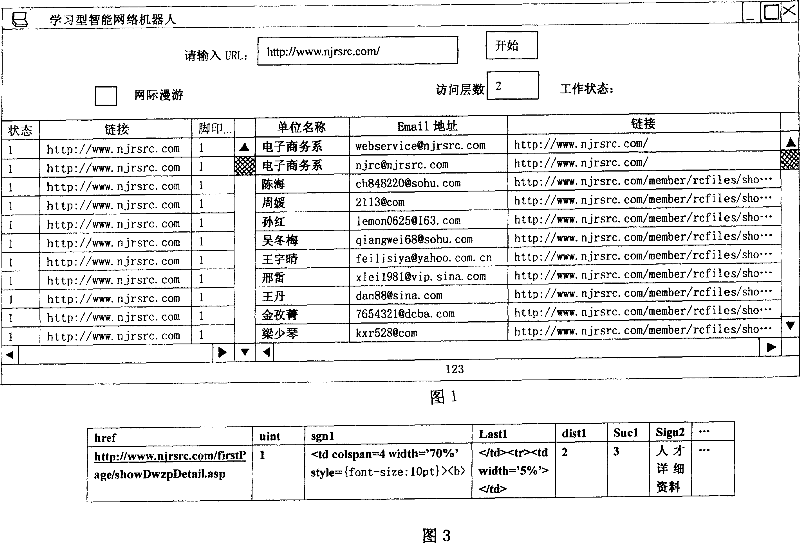
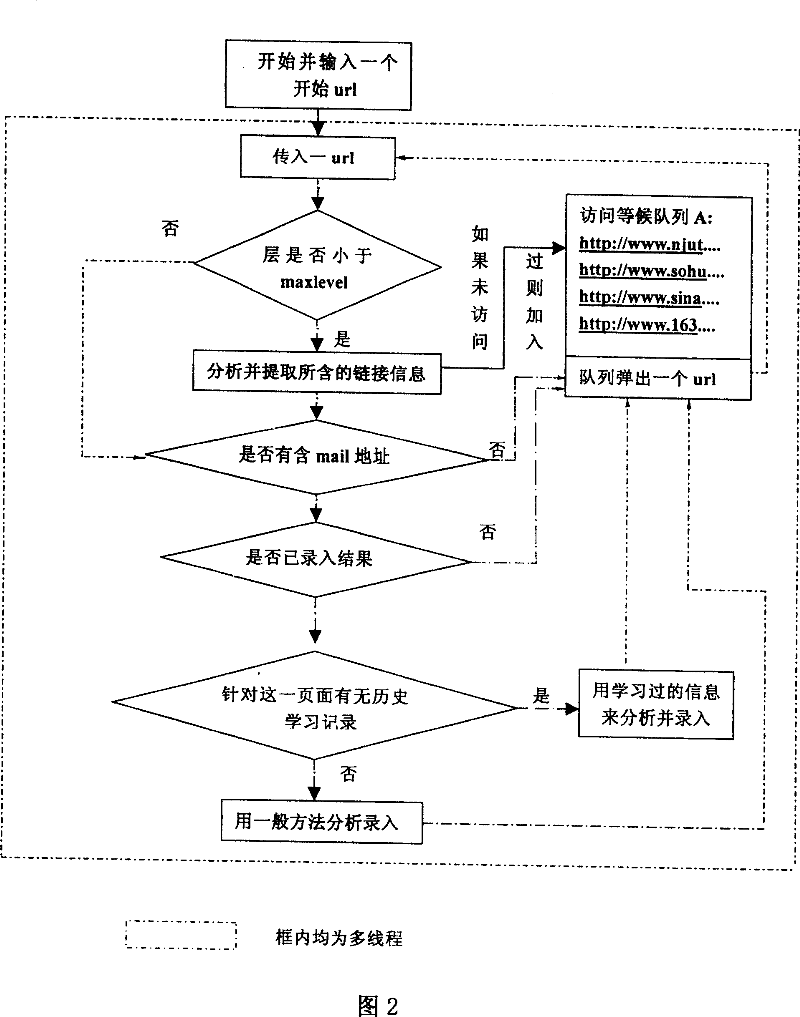
Fine-grained webpage information acquisition method
InactiveCN100354865CImprove efficiencyImprove accuracySpecial data processing applicationsWeb siteData source
Owner:NANJING TECH UNIV
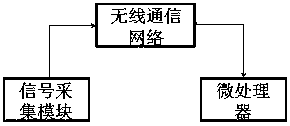
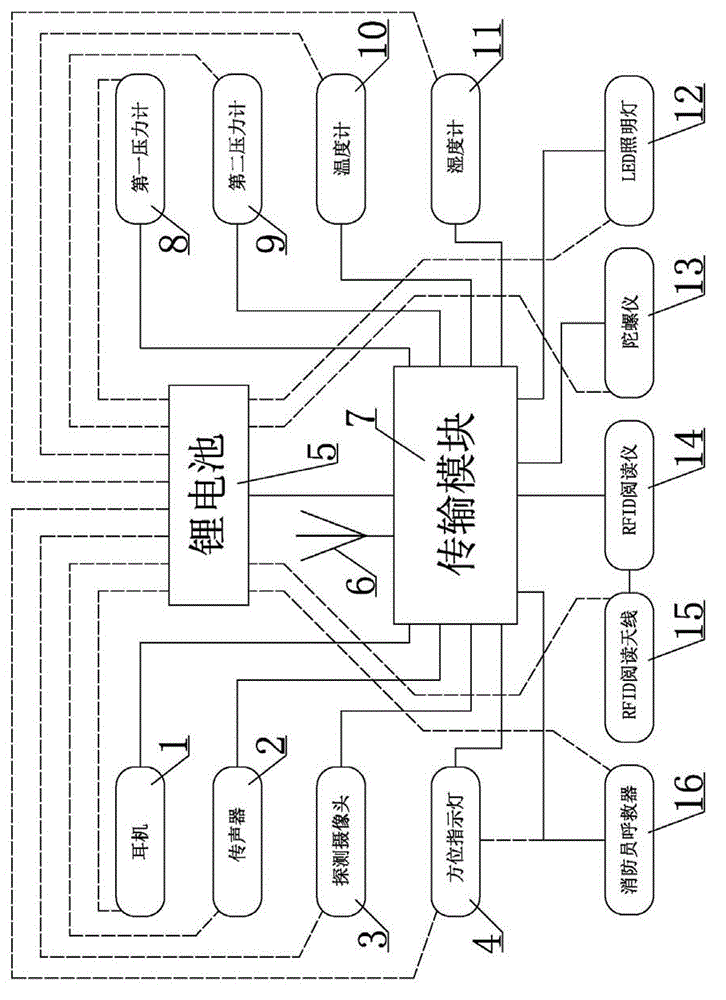
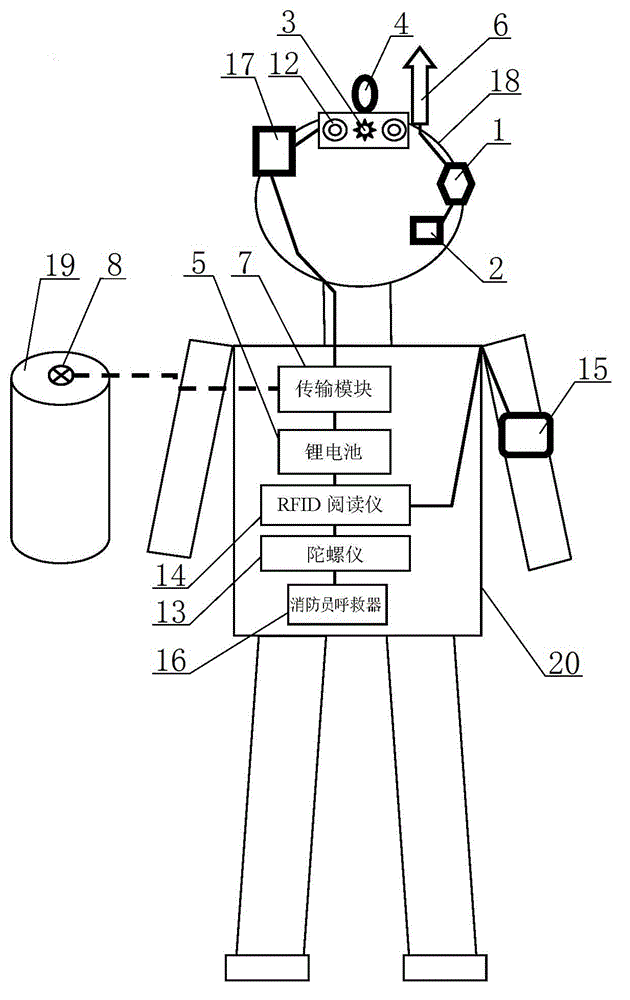
Disaster scene information intelligent collection equipment
ActiveCN103622203BDecision-making command is real and intuitiveFireproofChemical protectionHeat protectionGyroscopeFire protection
The invention discloses an intelligent information collecting device on a disaster site. A communication module, a temperature and pressure sensor, a micro sensor, an RFID reading instrument, a gyroscope, a vital sign detector and the like are designed to be additionally arranged. The several innovative functions of man positioning, telecommunication, motion state detection, air respirator pressure monitoring, external environment (temperature and pressure) detection, vital sign monitoring and the like inside a building are further achieved, and all detecting parameters can be transmitted to a field managing rescue platform in real time. The intelligent information collecting device on the disaster site is reasonable in structure, improves the fire protection and rescue efficiency, lowers the life and property loss to the minimum degree, and improves the life safety guarantee level.
Owner:新疆中睿电子科技有限公司 +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com