Database protection system and method
A protection system and database technology, applied in the database field, can solve the problem of inability to scan out vulnerability threat intelligence information in real time, achieve fast and accurate vulnerability scanning, and improve security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
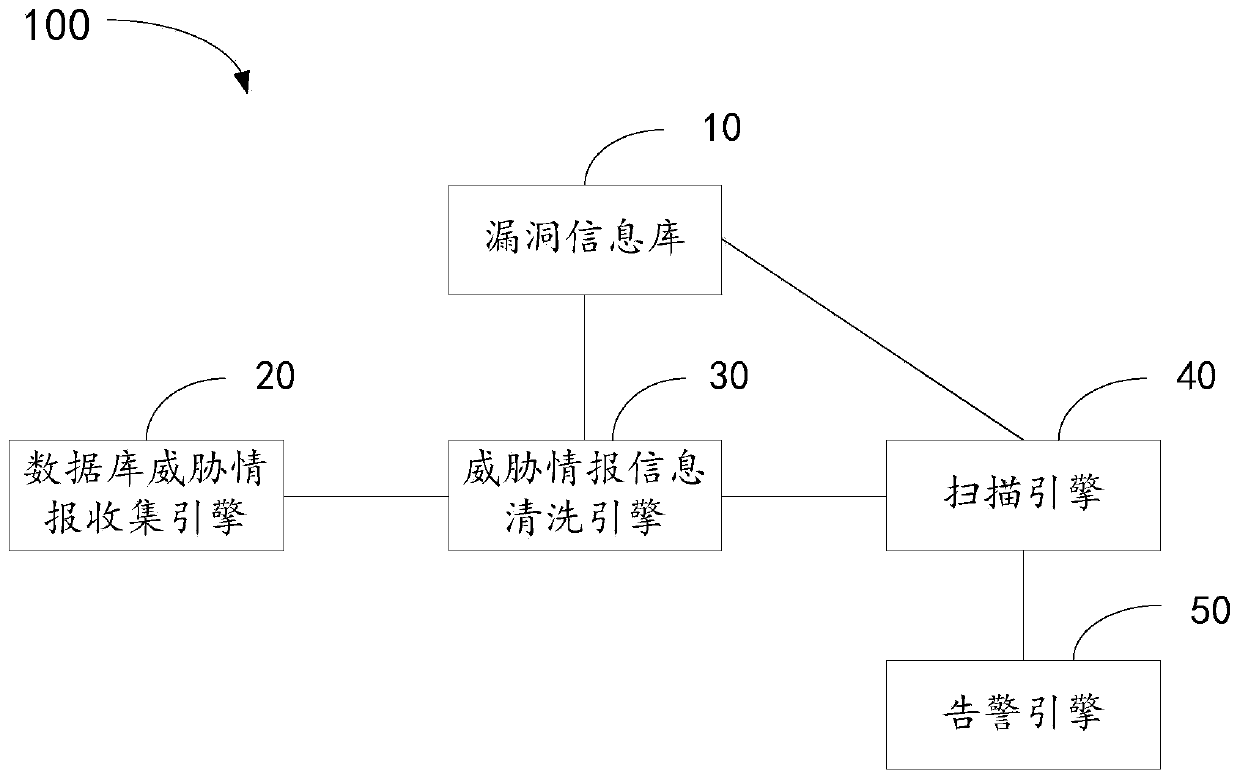
[0046] see figure 1 , figure 1 It is a schematic structural diagram of a database protection system provided by an embodiment of the present invention; figure 1 As shown, the database protection system 100 includes: a vulnerability information base 10, a database threat intelligence collection engine 20, a threat intelligence information cleaning engine 30, a scanning engine 40, and an alarm engine 50, wherein the database threat intelligence collection engine 20 is connected to The threat intelligence information cleaning engine 30 , the threat intelligence information cleaning engine 30 is connected to the scanning engine 40 , the scanning engine 40 is connected to the alarm engine 50 , and the scanning engine 40 is also connected to the vulnerability information database 10 .
[0047] Specifically, the vulnerability information database 10 is used to save database product information and corresponding threat intelligence information, wherein the database product informatio...
Embodiment 2
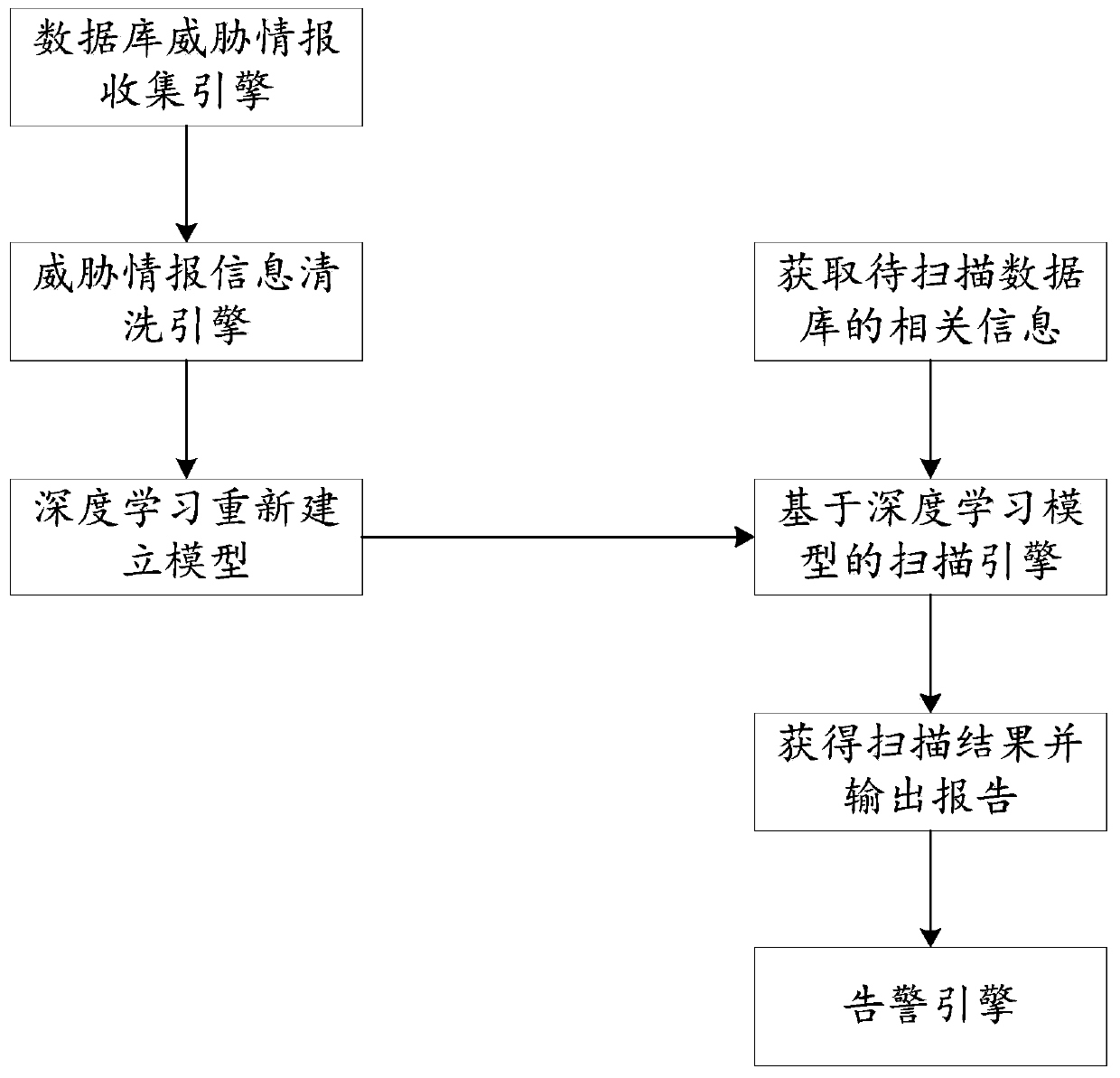
[0063] see figure 2 , figure 2 It is a work flow diagram of a database protection system provided by an embodiment of the present invention;
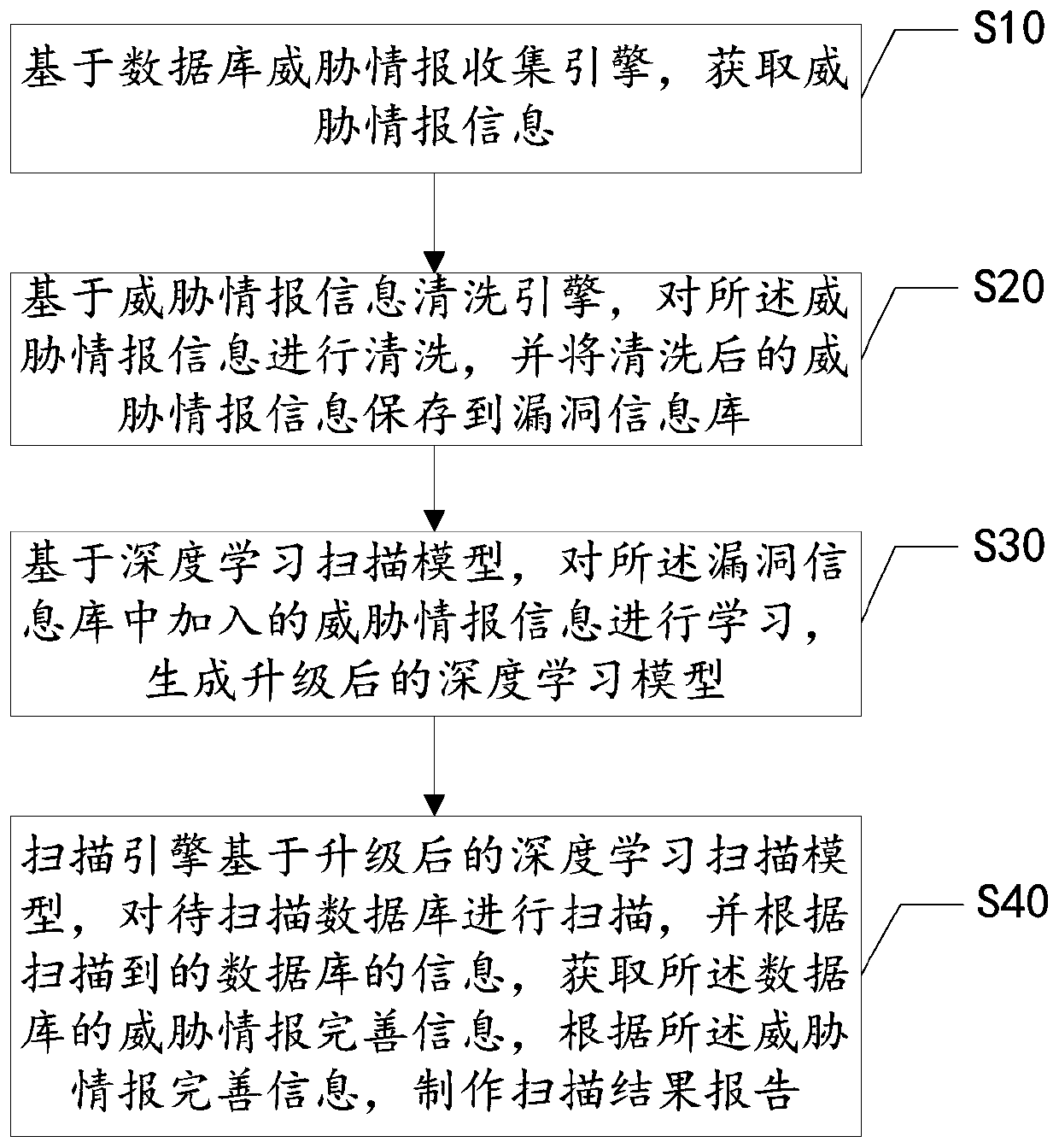
[0064] Among them, the database protection system includes: a vulnerability information database, which is used to store database product information and corresponding threat intelligence information; a database threat intelligence collection engine, which is used to obtain threat intelligence information;
[0065] A threat intelligence information cleaning engine, connected to the vulnerability information database and the database threat intelligence collection engine, used to clean the threat intelligence information, and save the cleaned threat intelligence information to the vulnerability information database;
[0066] The deep learning scanning model is used to learn the threat intelligence information added in the vulnerability information base to generate an upgraded deep learning scanning model;
[0067] The scanning engine...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com