Patents
Literature
30results about How to "Sufficient level of security" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
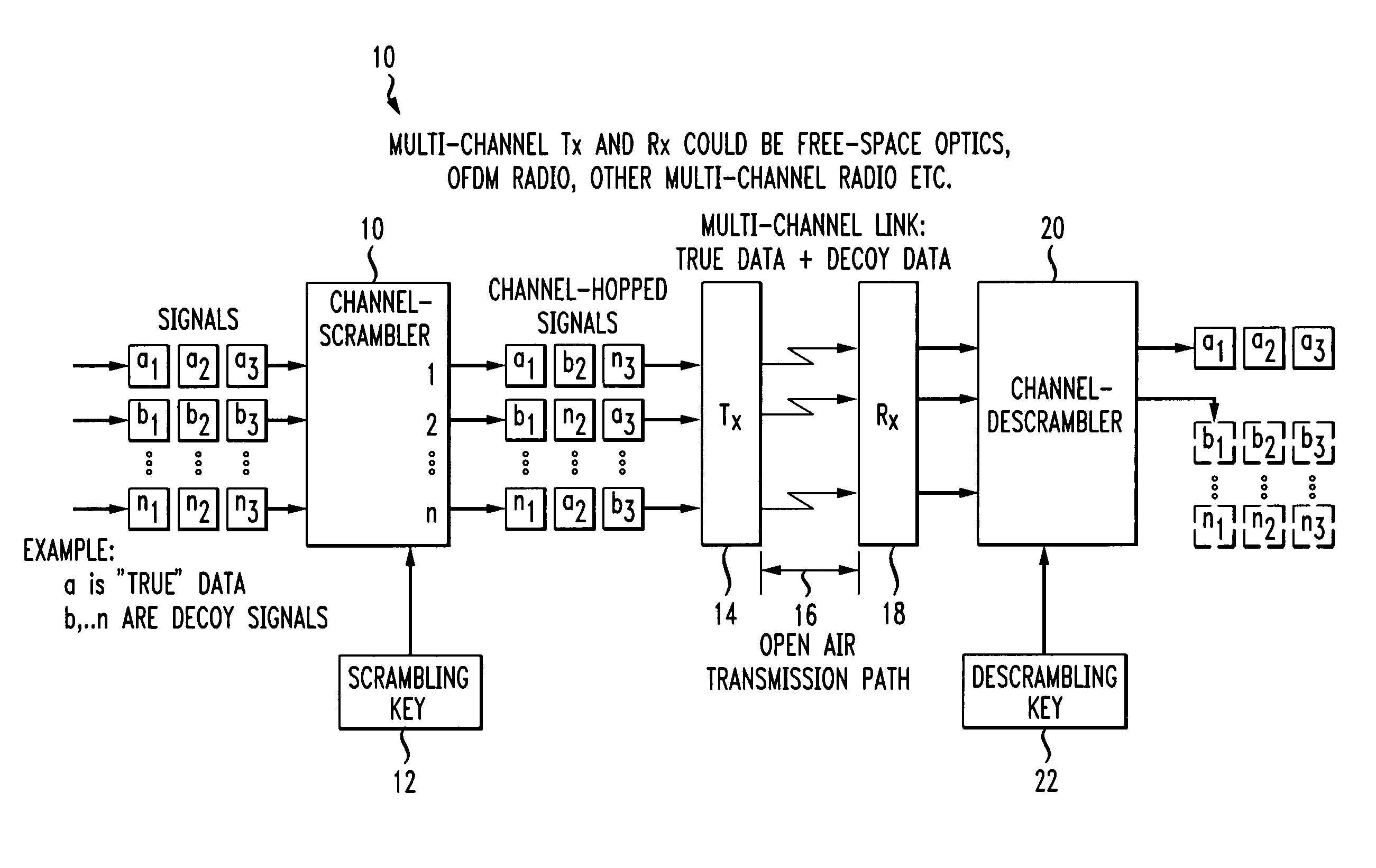
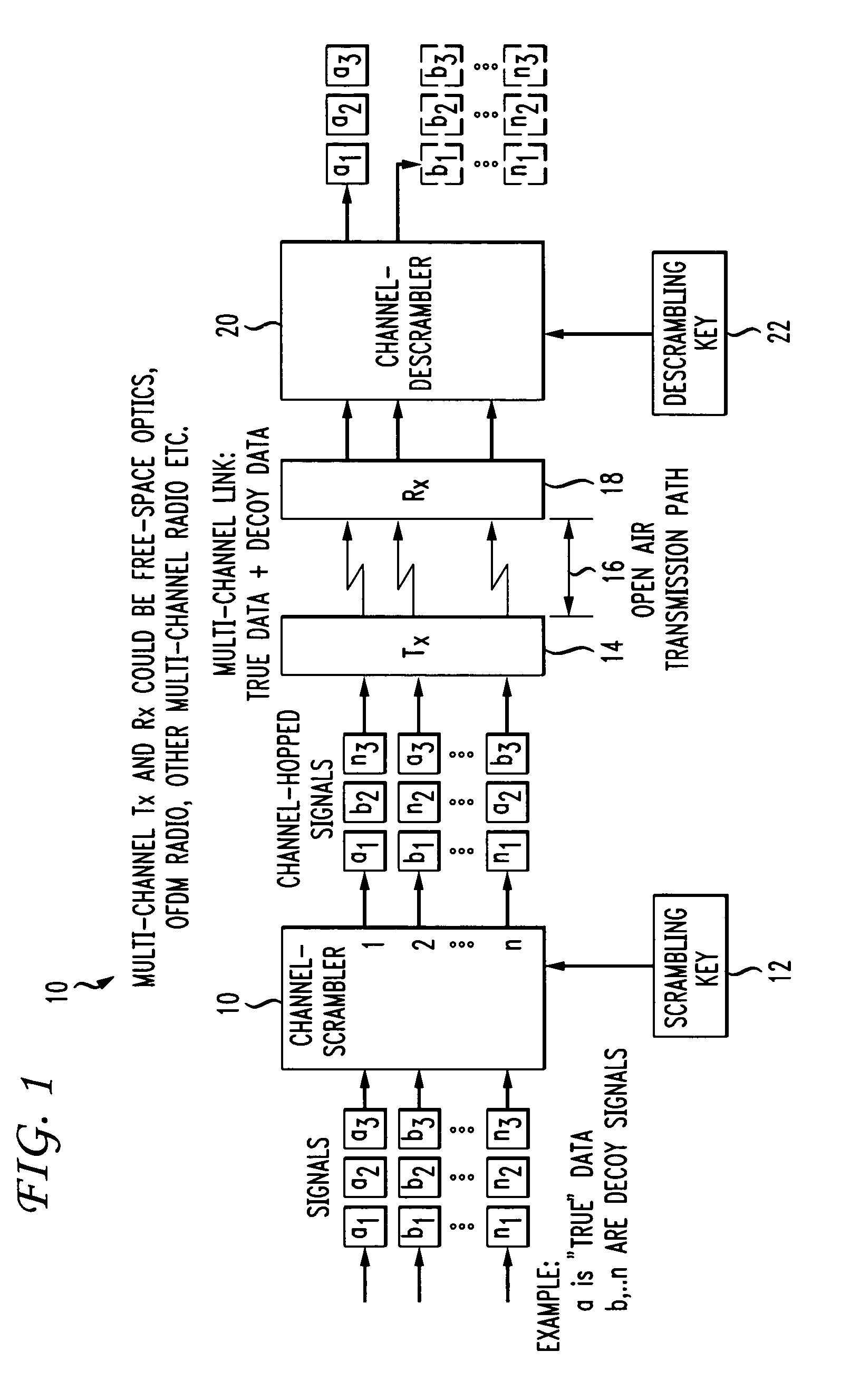
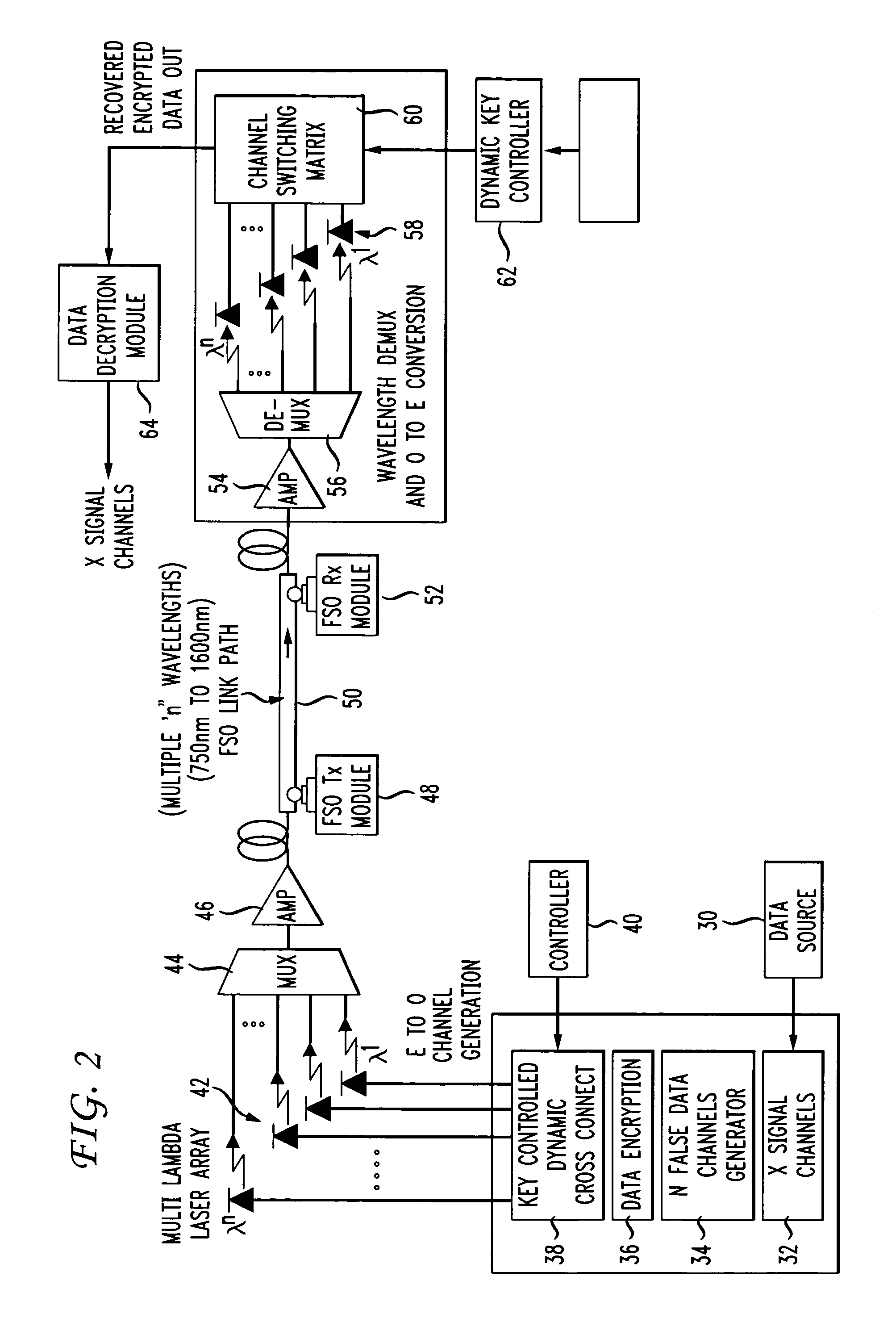
Secure open-air communication system utilizing multi-channel decoyed transmission
ActiveUS7848517B2Reduce the possibilitySufficient level of securityMultiplex system selection arrangementsSecret communicationCommunications systemDecoy
A secure, open-air communication system utilizes a plurality of “decoy” data signals to hide one or more true data signals. The true data signal(s) are channel hopped with the plurality of decoy data signals to form a multi-channel “scrambled” output signal that is thereafter transmitted in an open-air communication system. The greater the number of decoy signals, the greater the security provided to the open-air system. Further security may be provided by encrypting both the true and decoy signals prior to scrambling and / or by utilizing a spatially diverse set of transmitters and receivers. Without the knowledge of the channel assignment(s) for the true signal(s), an eavesdropper may be able to intercept (and, with time, perhaps descramble) the open-air transmitted signals, will not be able to distinguish the true data from the decoys without also knowing the channel assignment(s).
Owner:AT & T INTPROP II LP
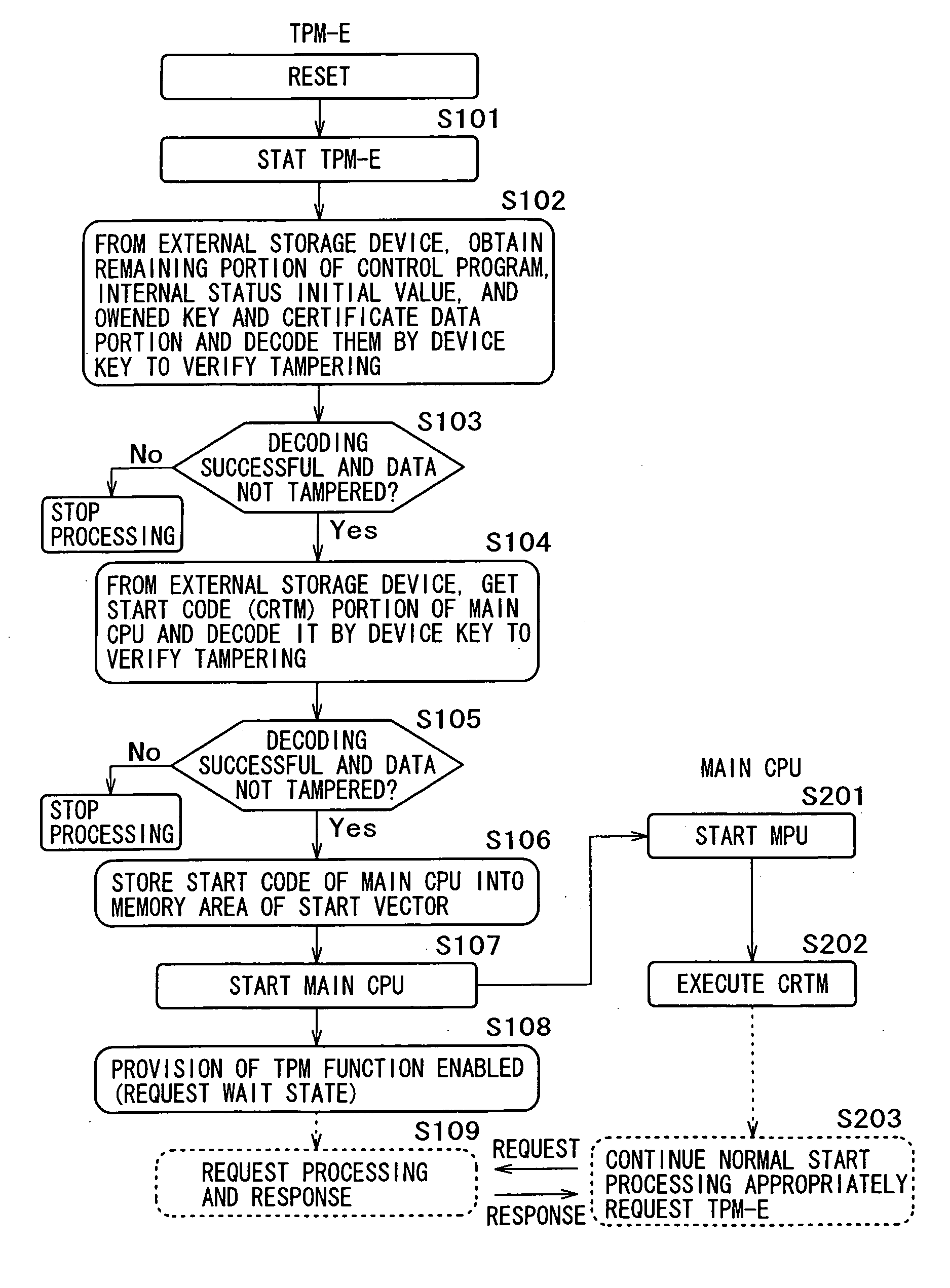
Information processing apparatus and method and computer program
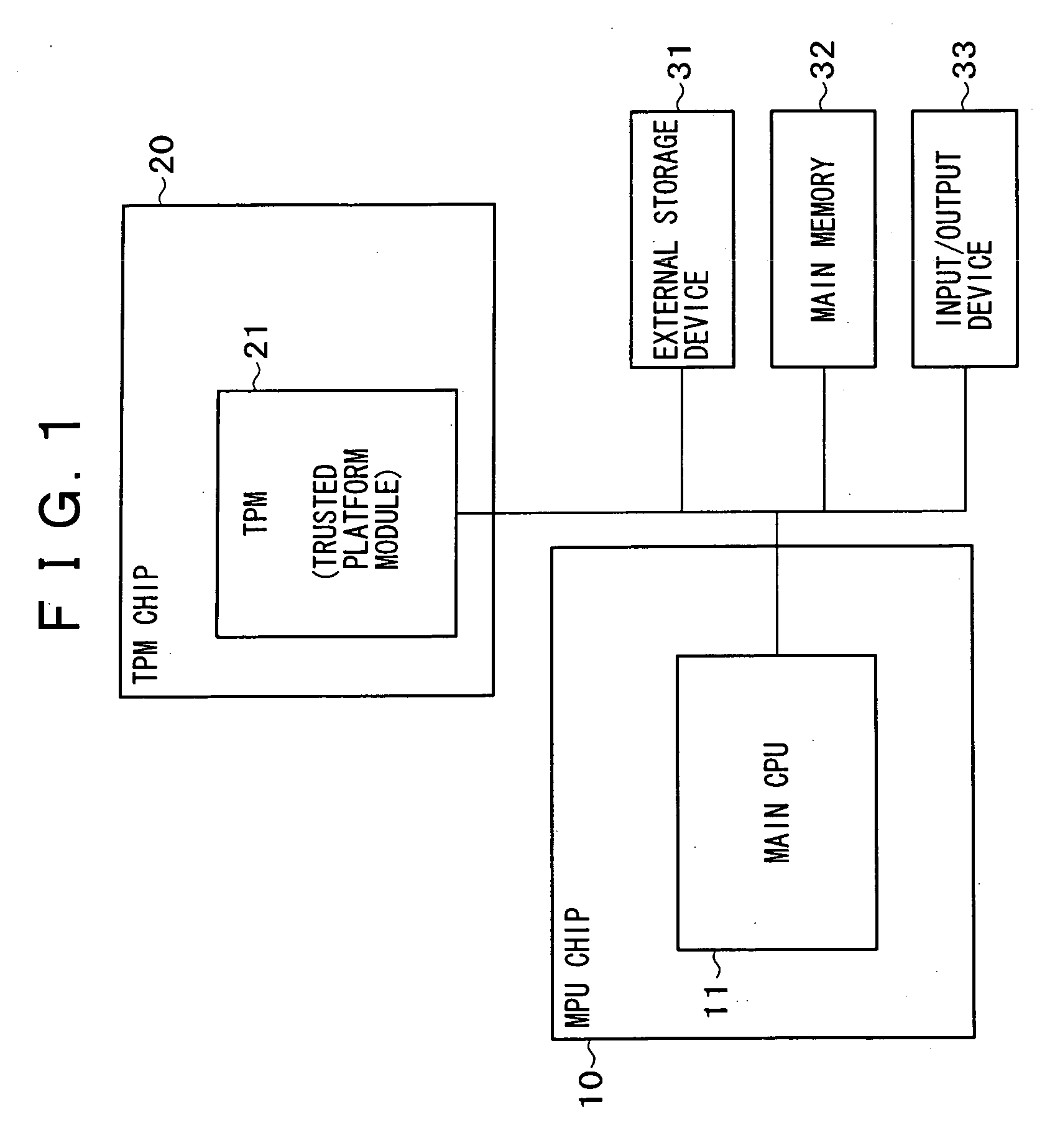
InactiveUS20050182952A1Reduced package areaReduce the amount requiredUnauthorized memory use protectionHardware monitoringInformation processingExternal storage
The present invention provides an information processing apparatus of space-saved type that can execute the processing corresponding to a security function module. A security function module storing a device key is integrally arranged in an MPU chip, the secret data including programs and data to be applied to the data processing to be executed in the security function module are encrypted with the device key or attached with a falsification verification value and the resultant programs and data are stored in an external storage section. This novel configuration can significantly reduce the amount of data to be stored in the security function module and therefore eliminate the necessity for a large-capacity flash memory. Consequently, the security function module can be integrally arranged in the MPU chip having the main CPU, thereby significantly reducing the packaging area and the production cost.
Owner:SONY CORP
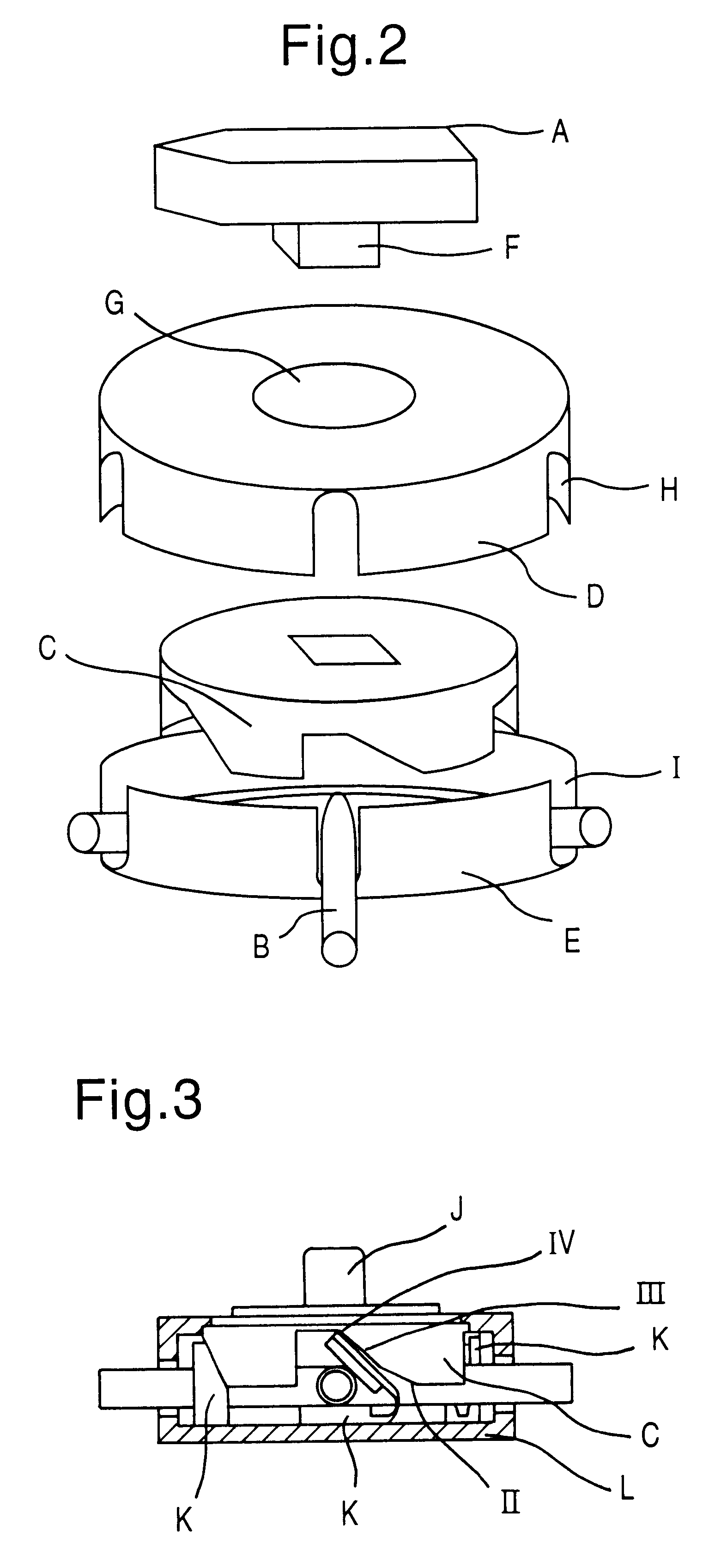
Fluid passage change-over apparatus for medical treatment
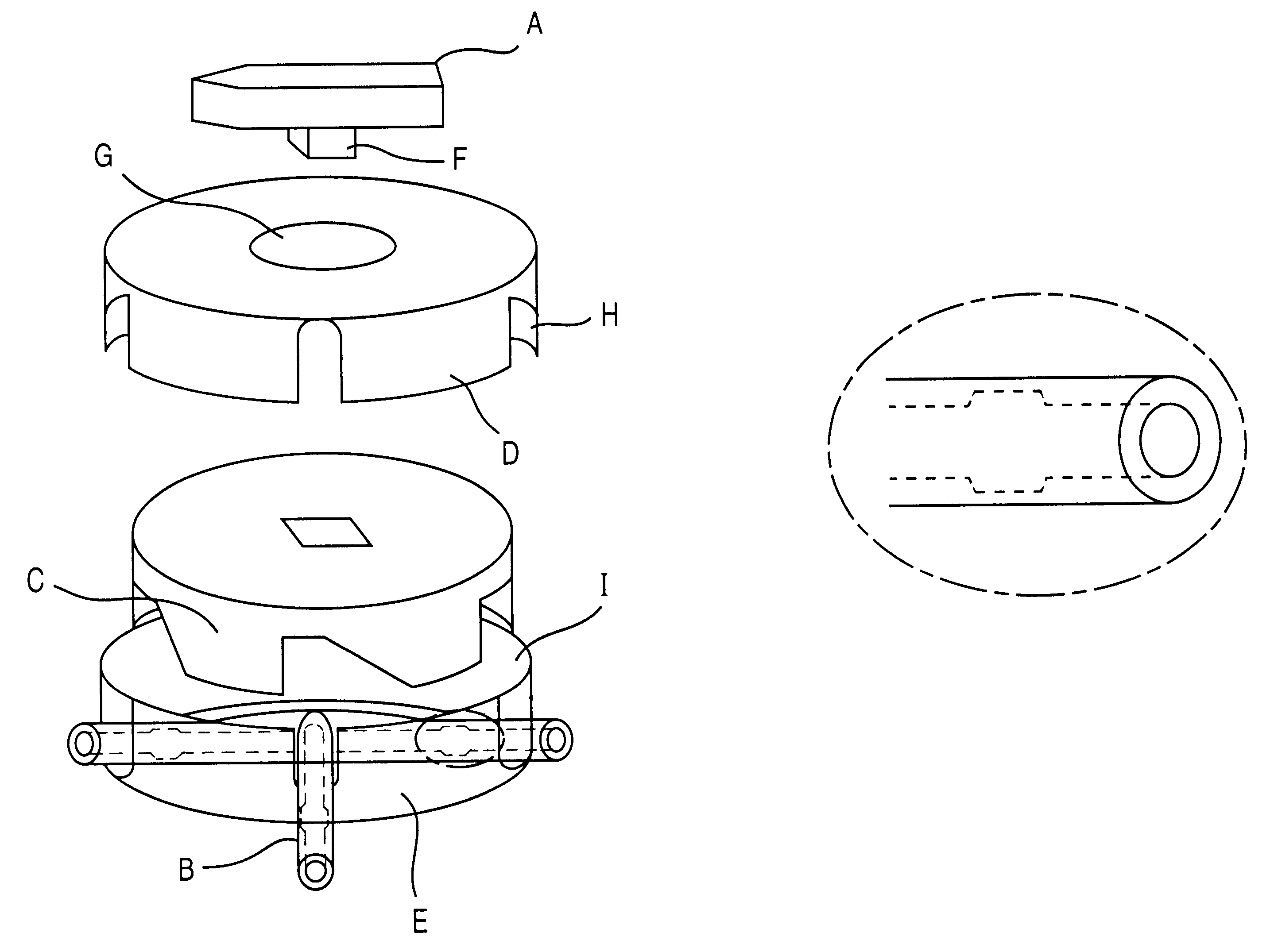
InactiveUS6589197B1Improvement of fitting structure of housingSmall sizeDiaphragm valvesEngine diaphragmsContinuous ambulatory peritoneal dialysisEngineering
A medical fluid passage switching apparatus comprising: at least, a rotatable shaft F; a cam C which is rotated in relation to the rotating movement of the shaft F to close and open divided tubes for determining a passage of a fluid; and a housing L having tube accepting holes I and so arranged to enable the holding of the cam C, is provided. More particularly, provided are such a medical fluid passage switching apparatus in a continuous ambulatory peritoneal dialysis (CAPD) system and a tube which is decreased in the diameter and / or thinned in the wall at a region where the cam or a combination of the cam and the clamp is engaged for closing and opening.
Owner:JMS CO LTD
Mask defogging system
A system for supplying and carrying air into the interior lens of a closed mask, helmet or goggle for the purpose of removing accumulated precipitation from the mask lens consisting of a battery powered air pump or aerator of any size or type which removably attaches to a person or a mask, helmet or goggle by a clip or other type of fastener which may be carried within a vest, belt pouch or on a belt pouch or on a belt or other form of carrying device or casing, or which may be build in as an integral part of a mask, helmet or goggle whereby air is carried from said pump through a single or multiple lines(s) of flexible plastic, vinyl or other type of flexible tubing or molded tubing which can be detached, or broken into two pieces, by a disconnect piece / connector (a quick disconnect piece) and whereby said tubing communicates between the pump outlet and the interior of the mask, helmet or goggle and air is directed onto the lens of the mask, helmet or goggle through some type of air inlet adapter, or air director piece, which is attached to the tubing for the purpose of directing the flow of air directly onto the interior lens of a mask, helmet or goggle for the purpose of dissipating or fully eradicating precipitation, or fog, as it is commonly called, from said lens and creating a clear view through said lens.
Owner:SALLEE MATTHEW BLAIR
Method to save computational resources by detecting encrypted payload
ActiveUS11012429B2Reduce consumptionImprove efficiencyEncryption apparatus with shift registers/memoriesNetworks interconnectionTelecommunicationsSecurity level
Described embodiments provide systems and methods for remapping connections to tunnels selected based on a security level of the communications. A first network device may be in communication with a second network device via a plurality of communication tunnels. The plurality of communication tunnels may include an encrypted communication tunnel and an unencrypted communication tunnel. The first network device may receive a packet, the packet including header information and a payload. The first network device may determine whether the received packet is encrypted to meet a threshold level of security. The first network device may, responsive to determining that the packet is to meet the threshold level of security, communicate an identifier of the payload and the header information to the second network device via the encrypted communication tunnel, and communicate the payload to the second network device via the unencrypted communication tunnel.
Owner:CITRIX SYST INC
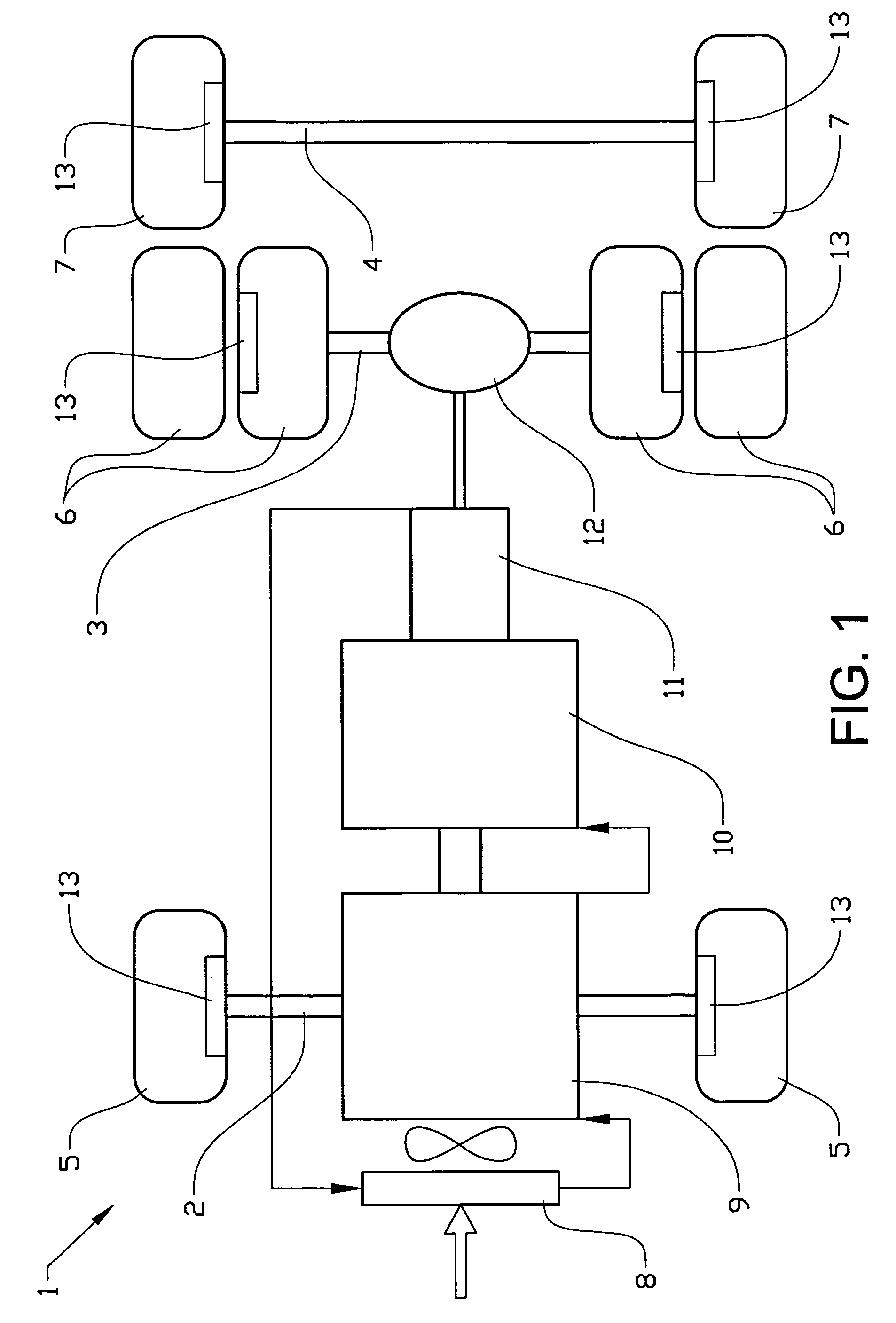
Method and apparatus for the distribution of brake torque on a vehicle
InactiveUS20060113833A1Improve vehicle performanceReduced safety marginBraking action transmissionBrake actuating mechanismsBrake torqueDrive wheel
Method and apparatus for distributing brake torque between at least a first and a second braking device on a motor vehicle having at least two wheel pairs. The first braking device is a friction brake which acts on at least one wheel pair and the second braking device acts on at least one driven wheel pair. The distribution of brake torque between the first braking device and the second braking device takes account of brake torque required and also the maximum brake torque the first braking device and the second braking device can deliver. The distribution of brake torque takes place when the vehicle is driven with a cruise control function.
Owner:VOLVO LASTVAGNAR AB
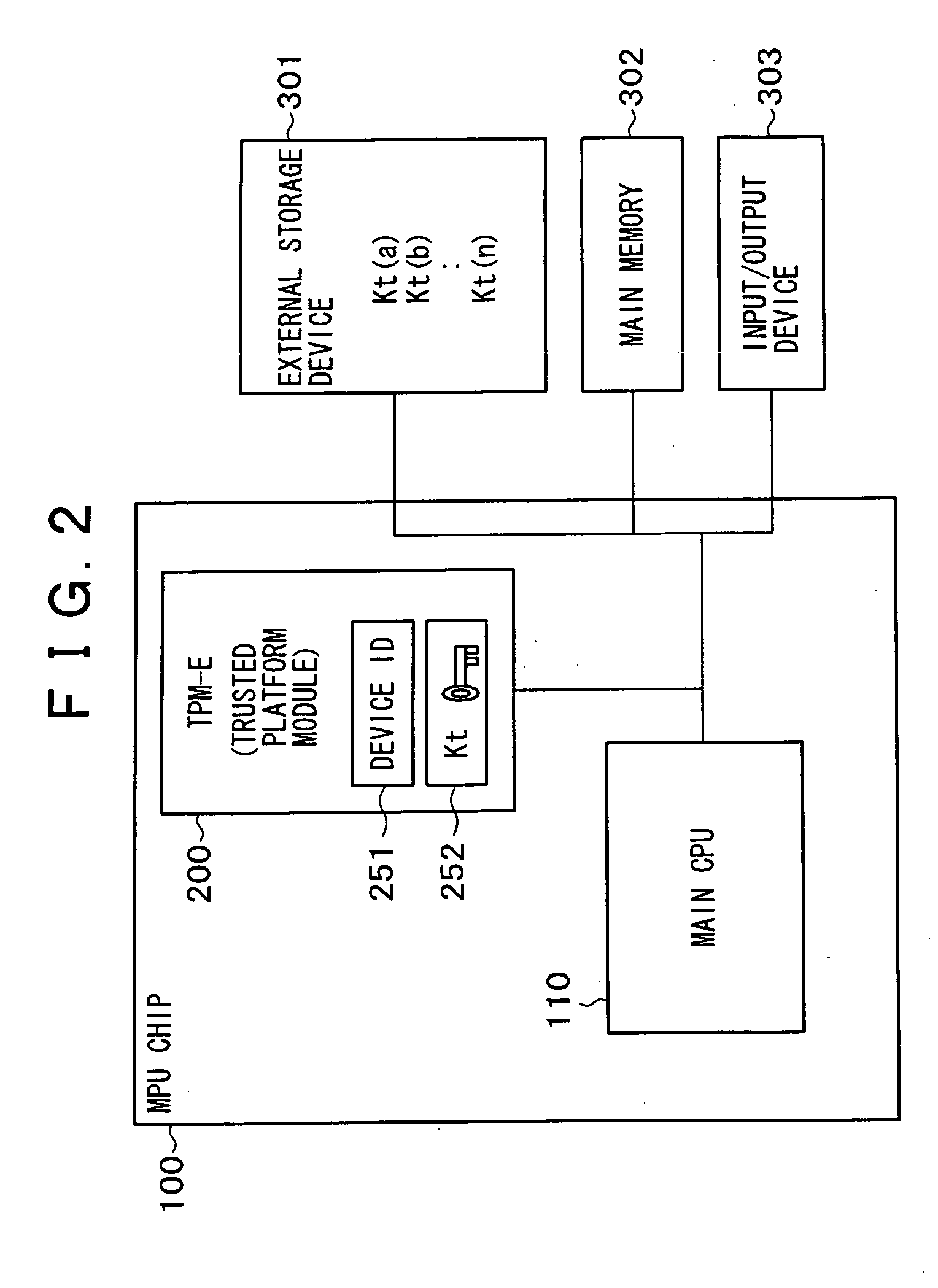
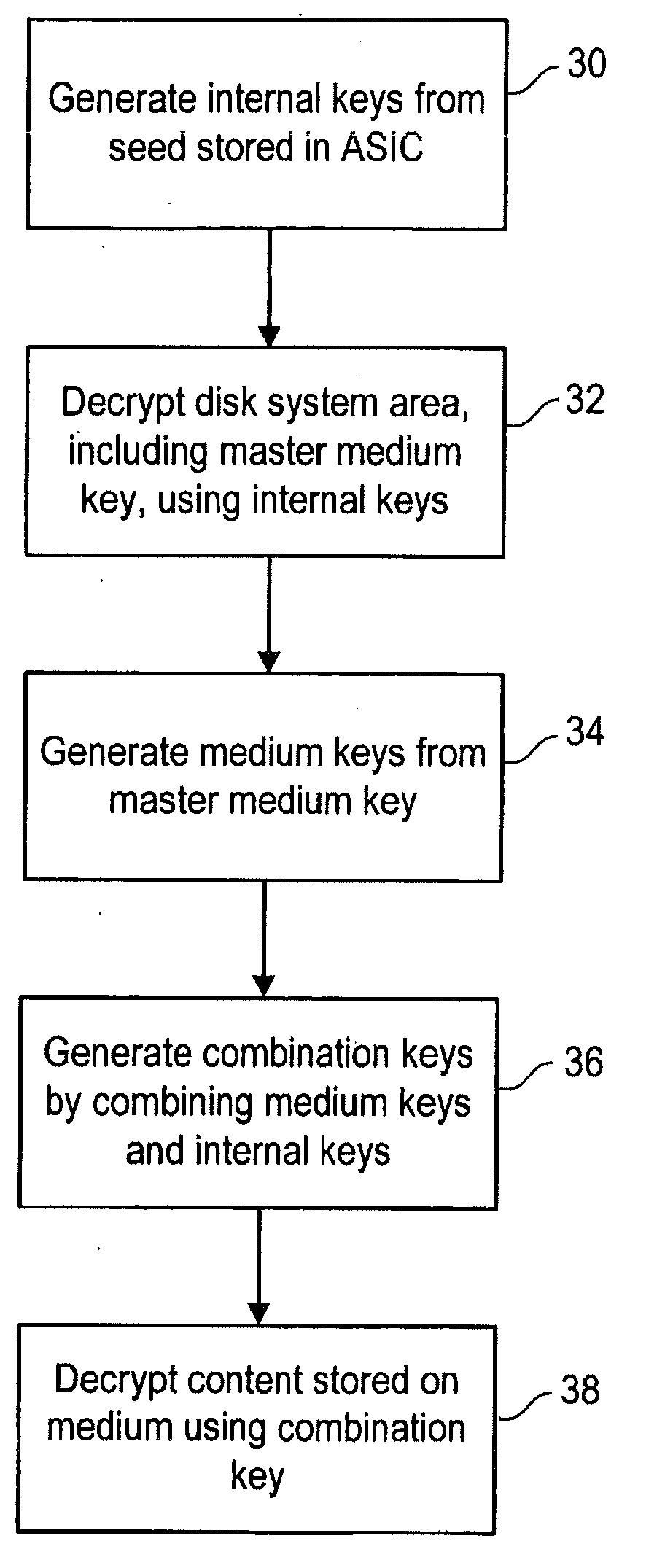
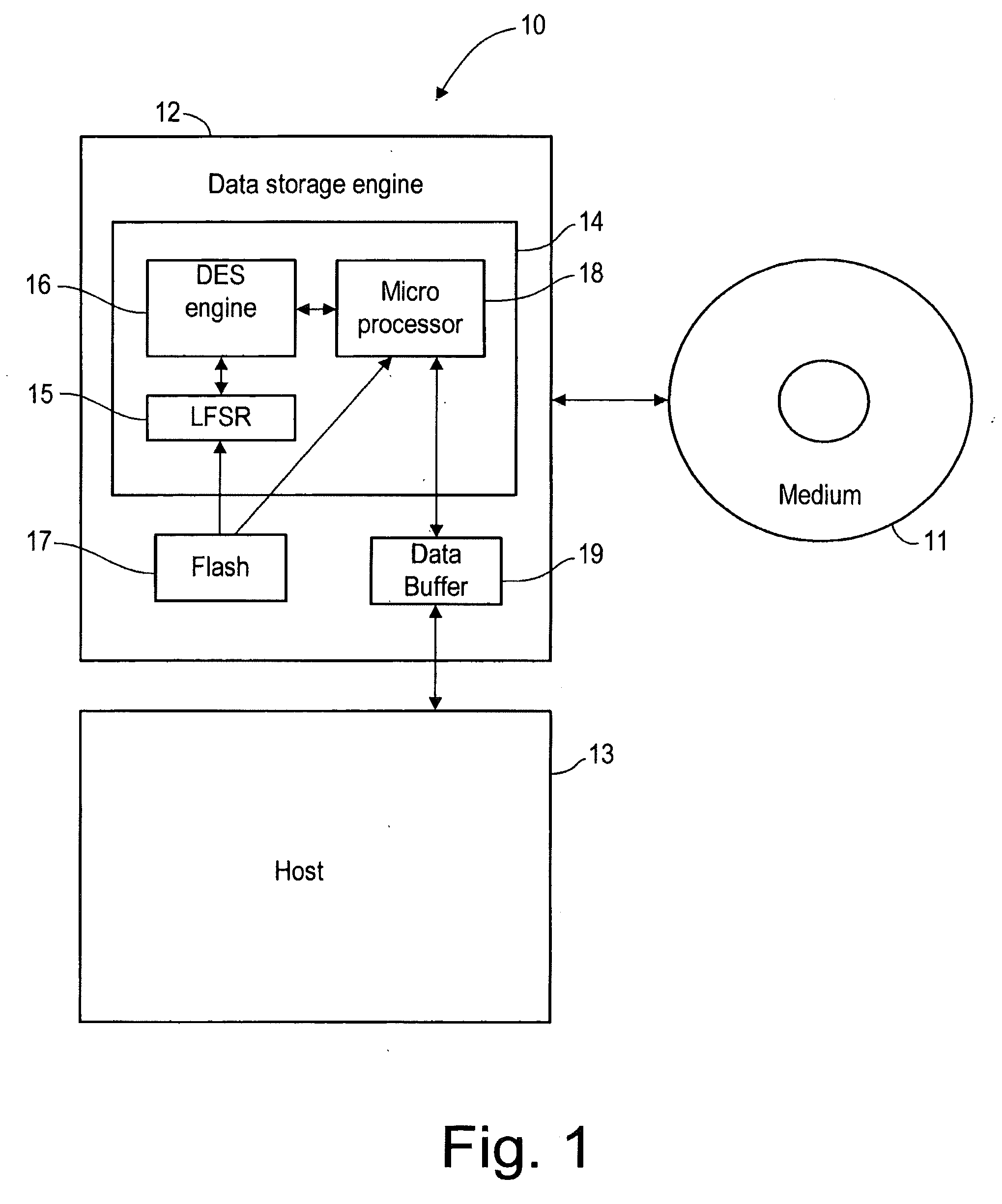
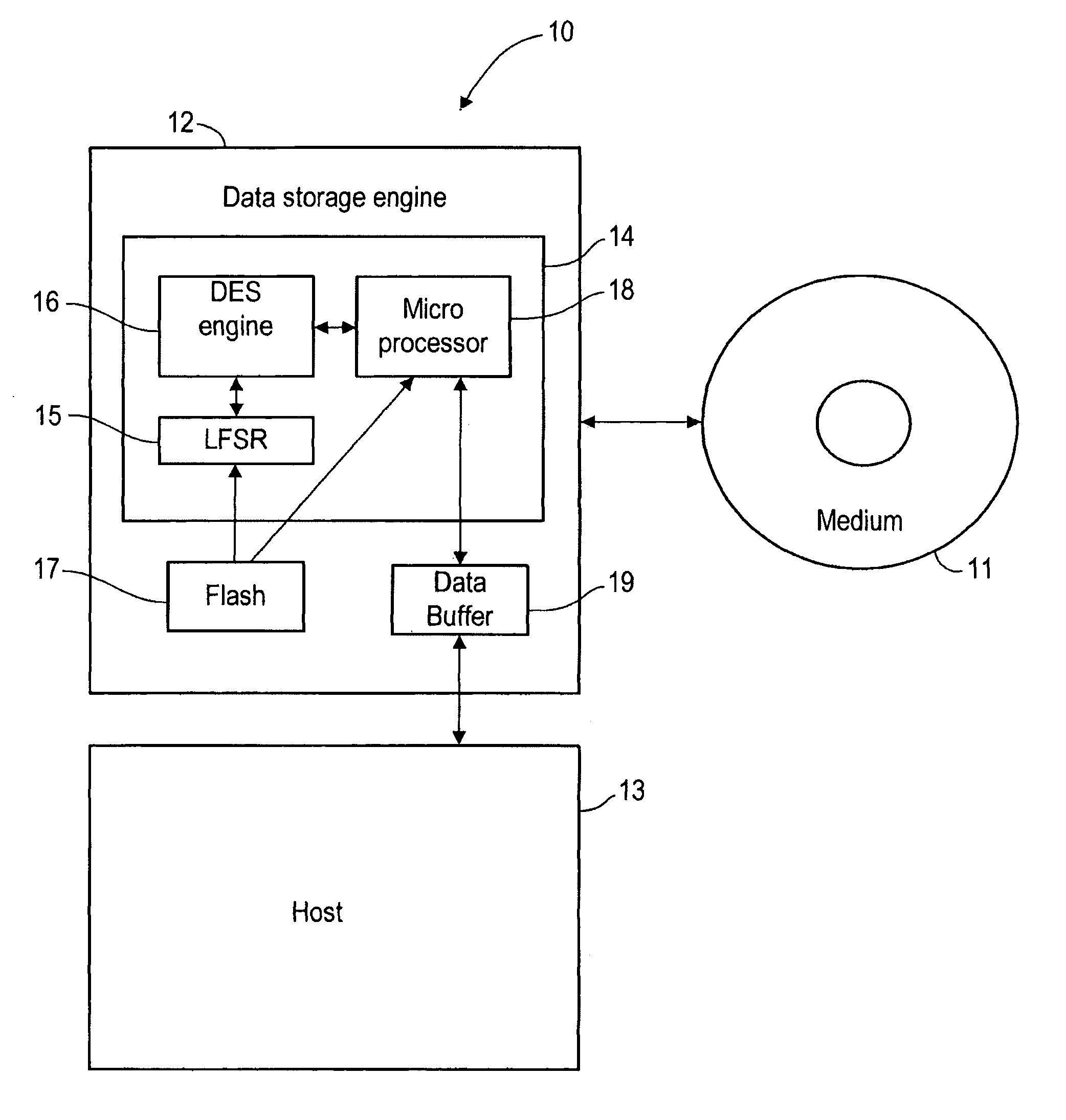
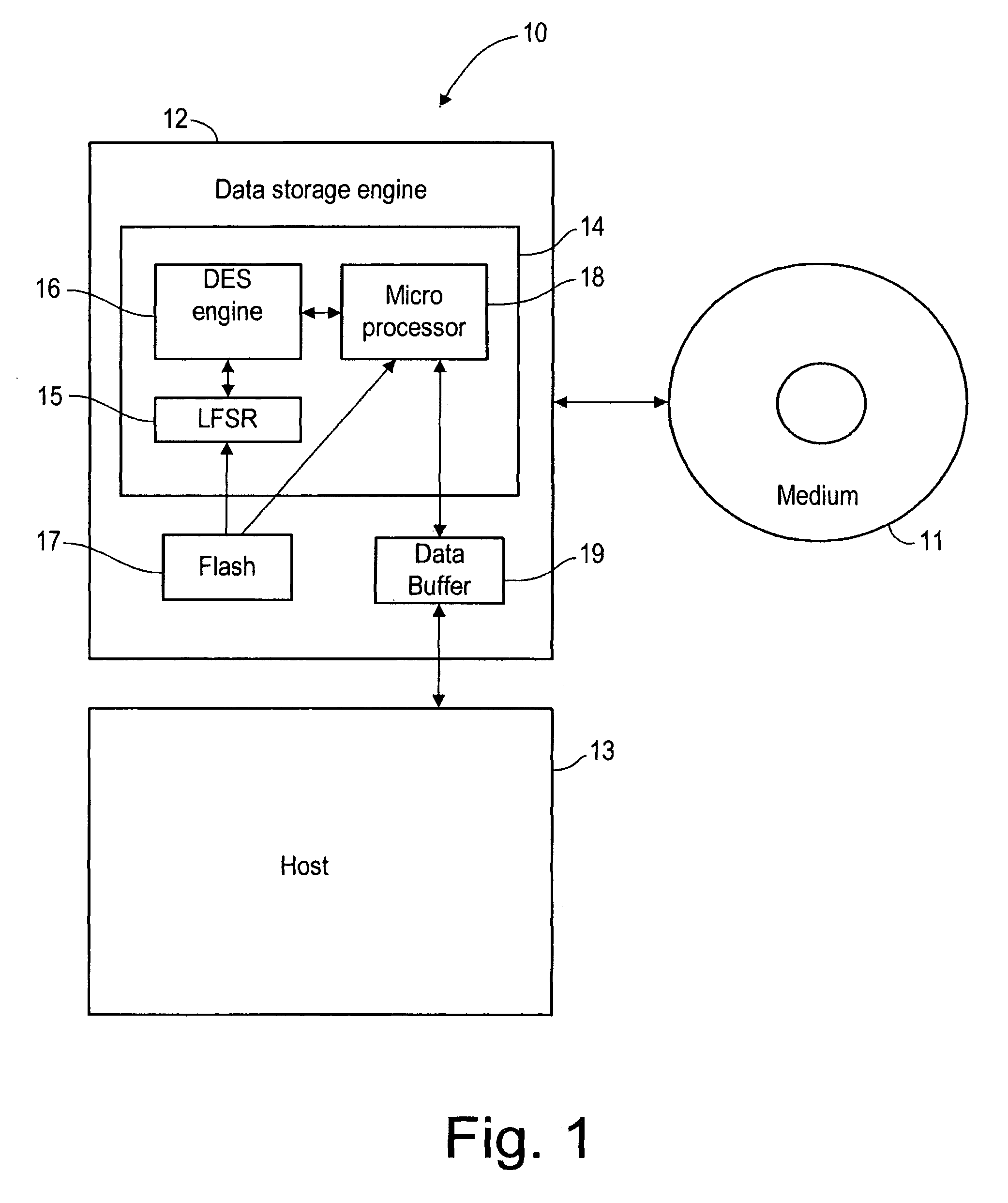
Method of encrypting and decrypting data stored on a storage device using an embedded encryption/decryption means
InactiveUS20090034722A1Improve security levelSufficient level of securityKey distribution for secure communicationUnauthorized memory use protectionData storingData store
Owner:DATAPLAY
Method for authorization of service requests to service hosts within a network
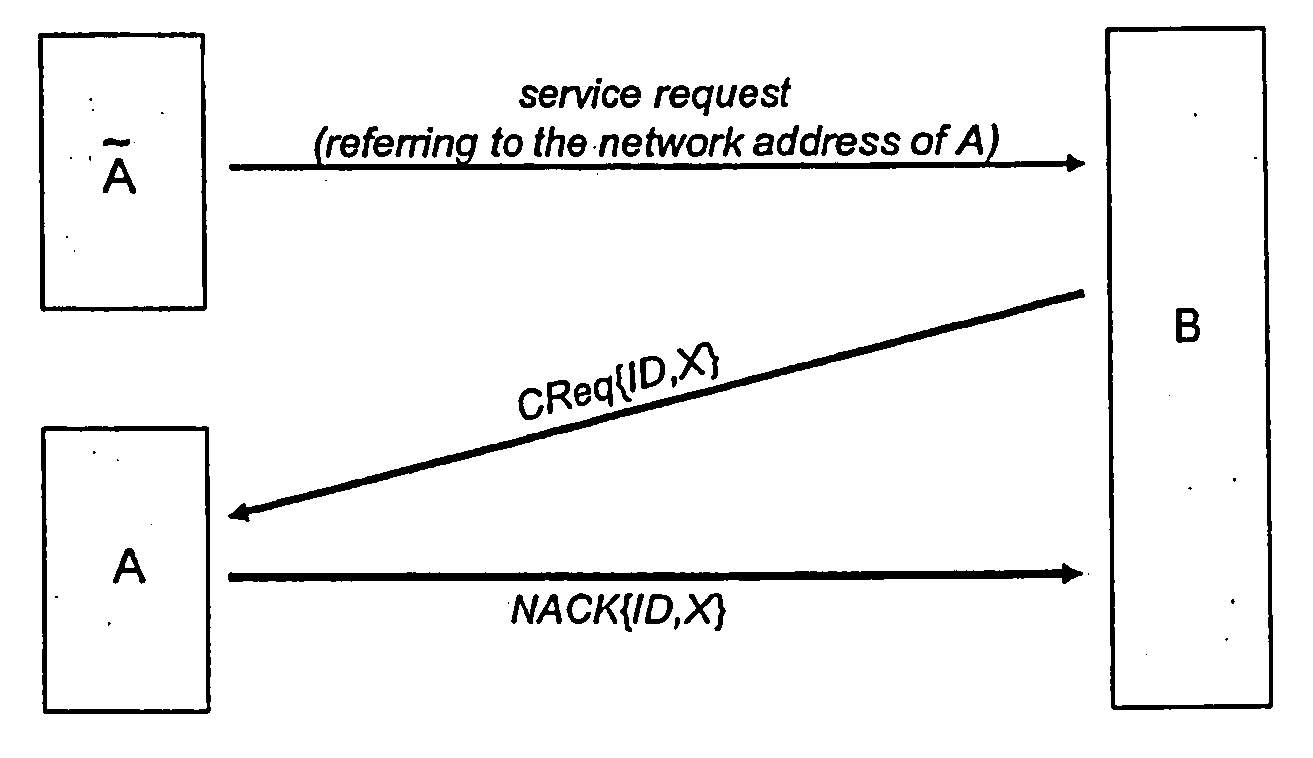
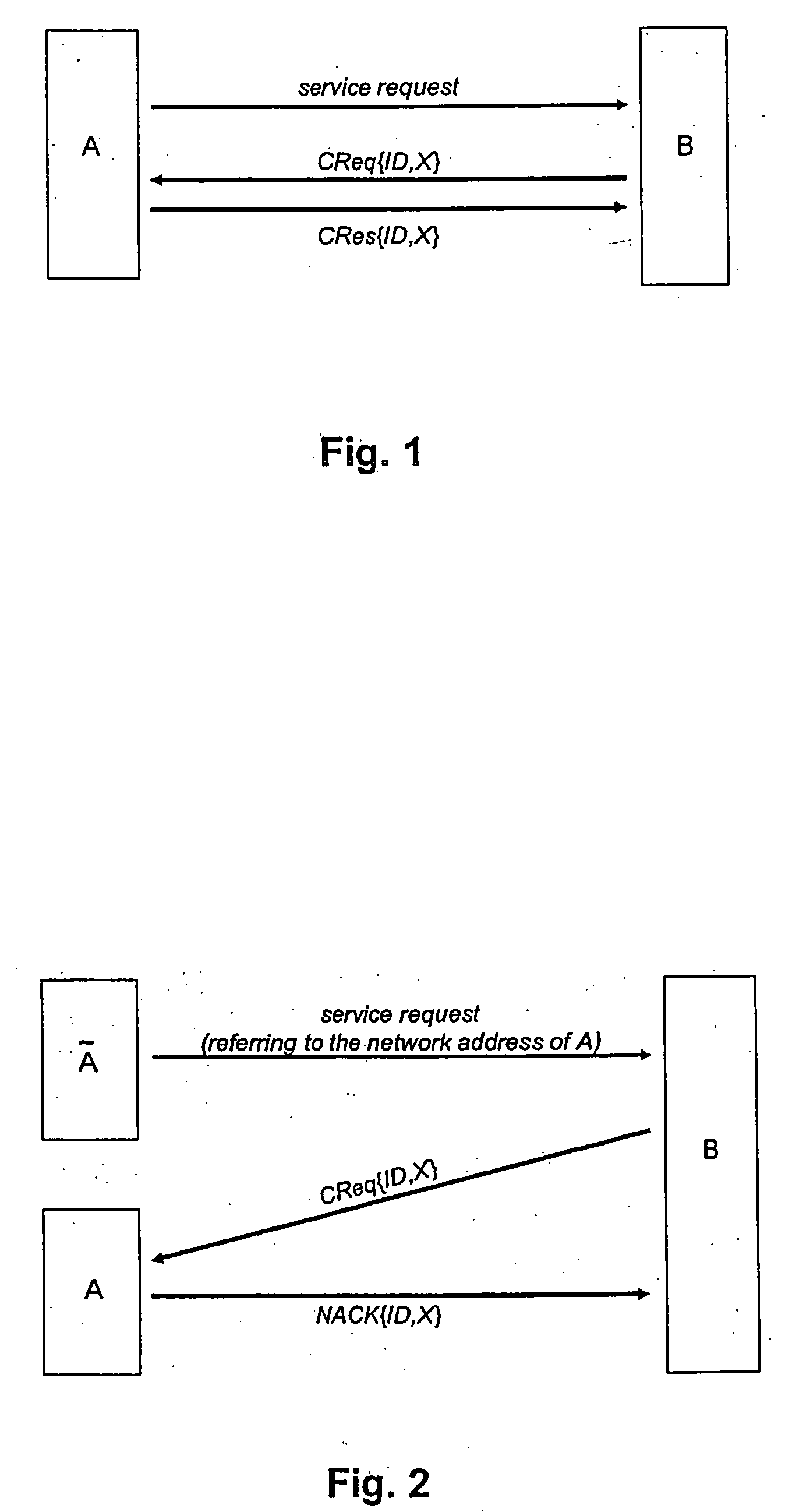
InactiveUS20060107310A1Improvement effortsShorten the timeDigital data processing detailsUser identity/authority verificationNetwork addressAuthorization
A method for authorization of service requests to service hosts within a network, wherein the communication within the network is based on a routing mechanism, according to which user terminals within the network are associated with routable network addresses, is characterized in that the service host sends a nonce included in a request message to the network address of a requesting user terminal, and that the user terminal resends the nonce or a value inferable from the nonce by the service host as well as by the user terminal included in a response message to the network address of the service host.
Owner:NEC CORP
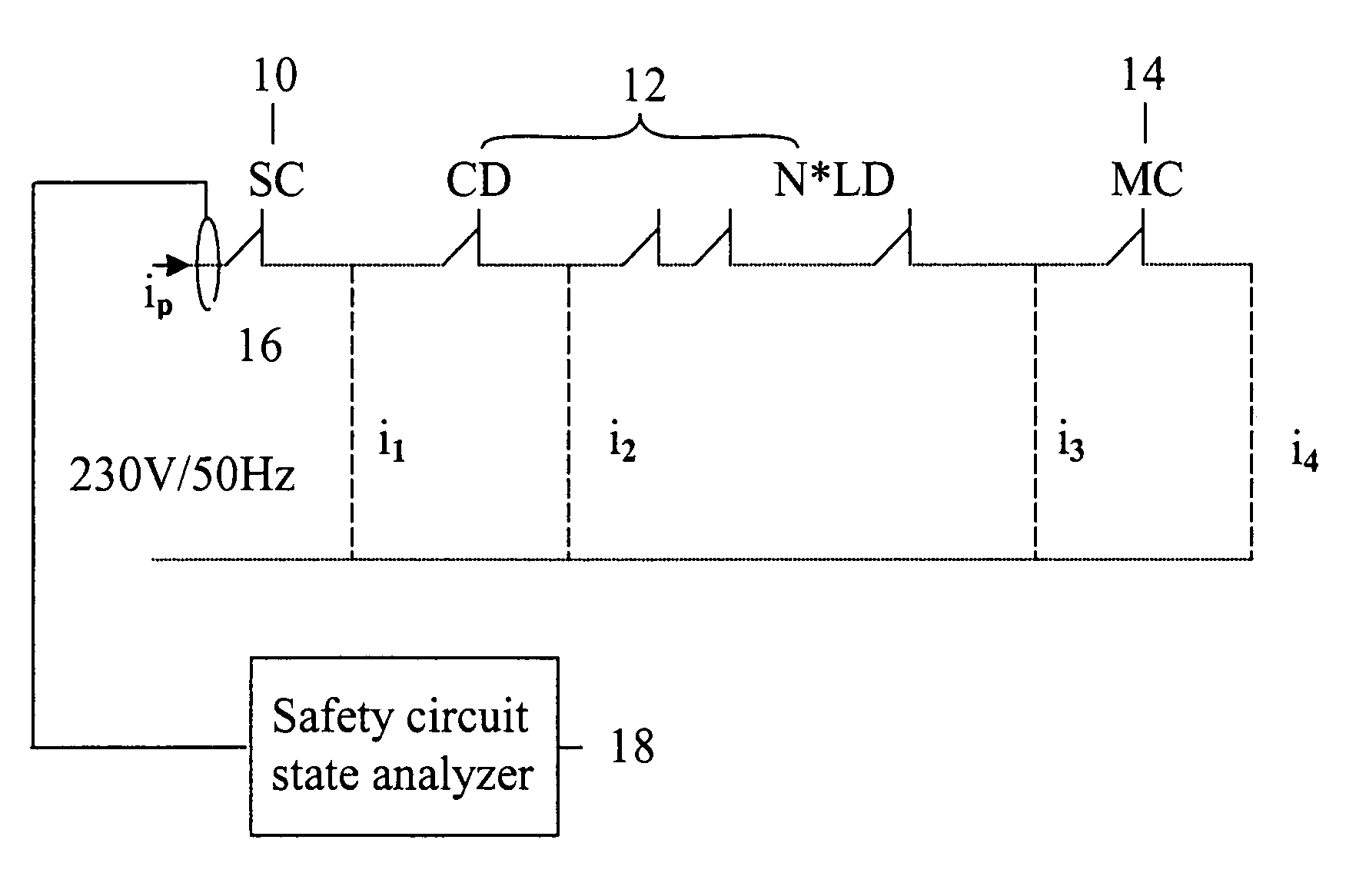
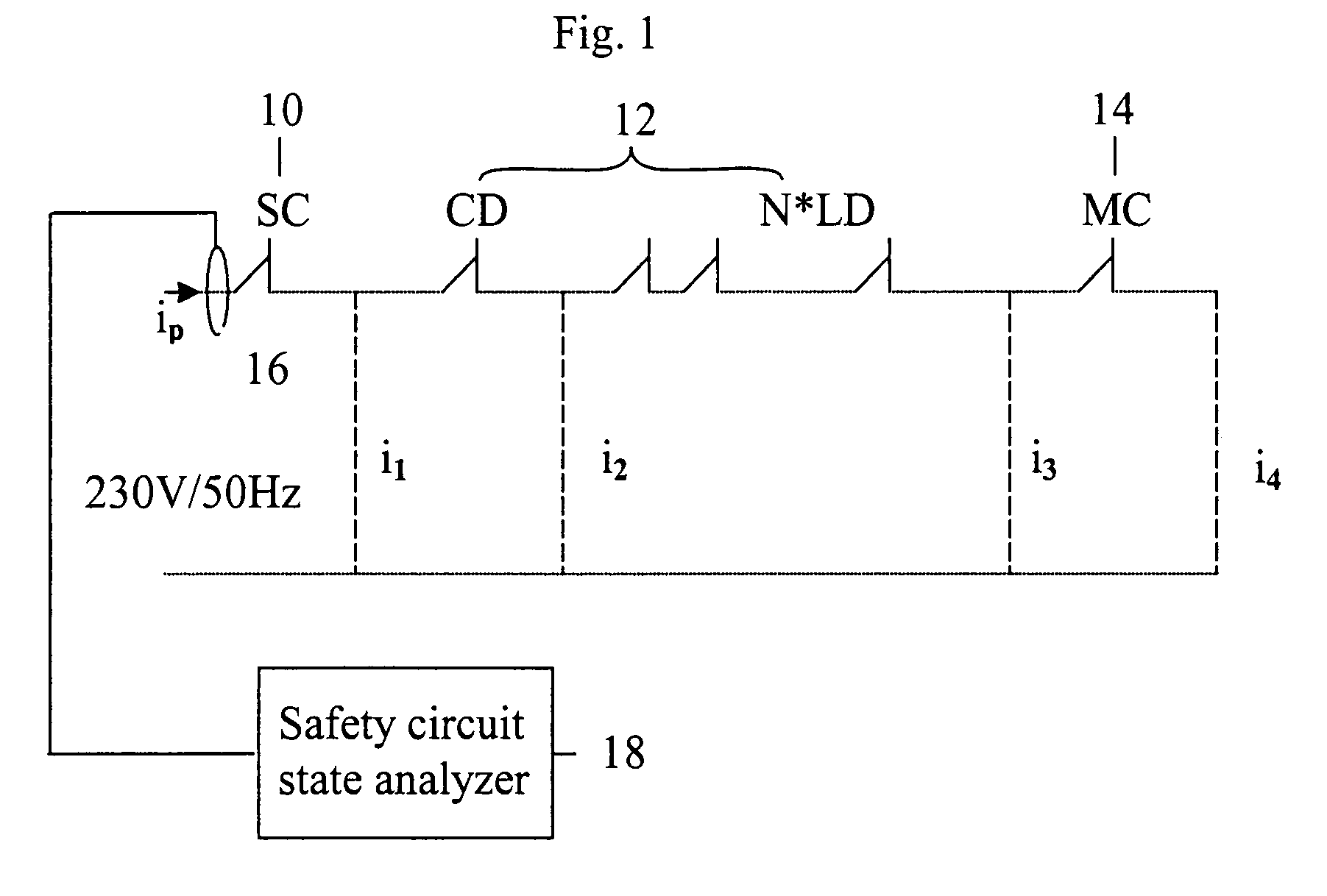
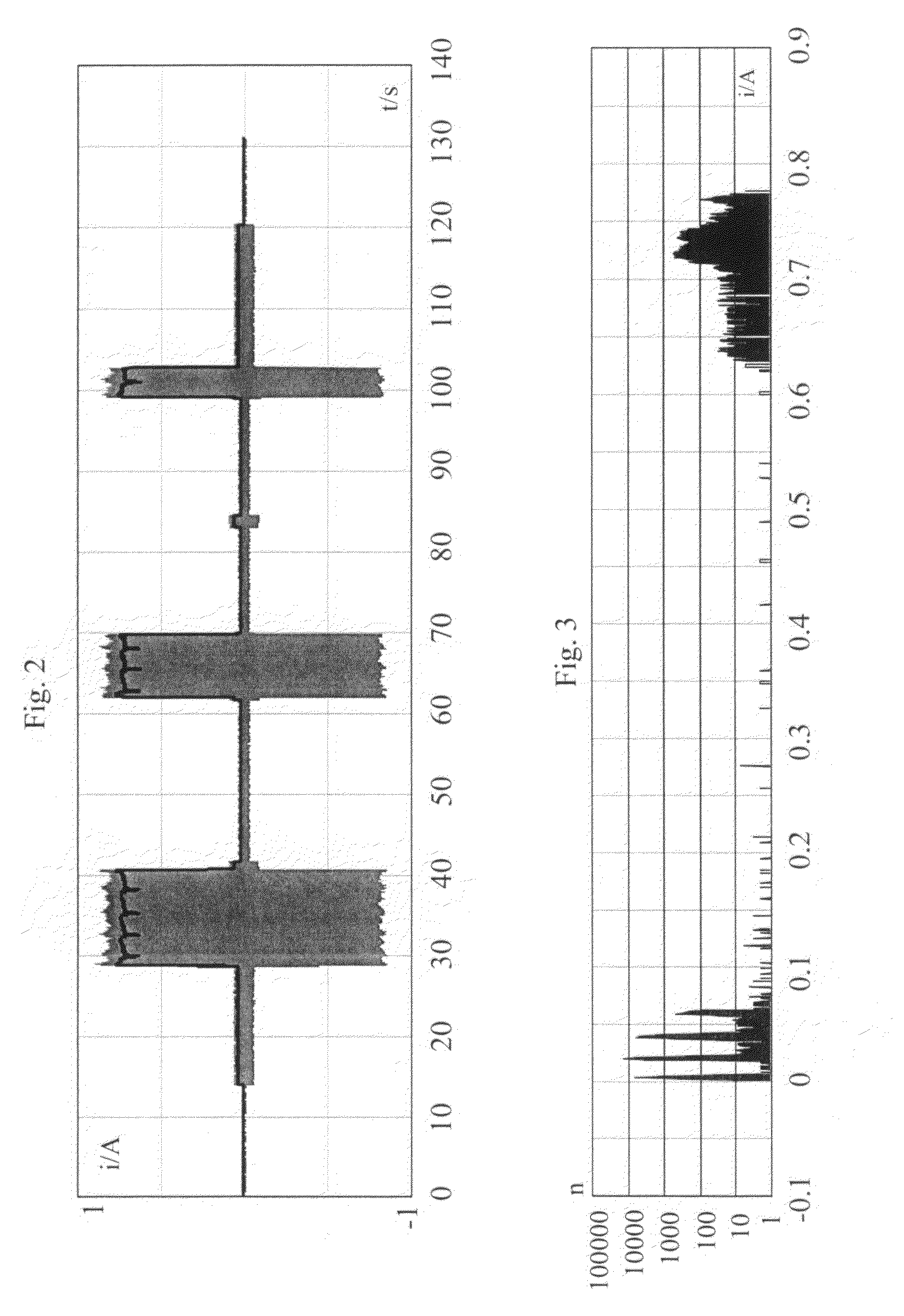
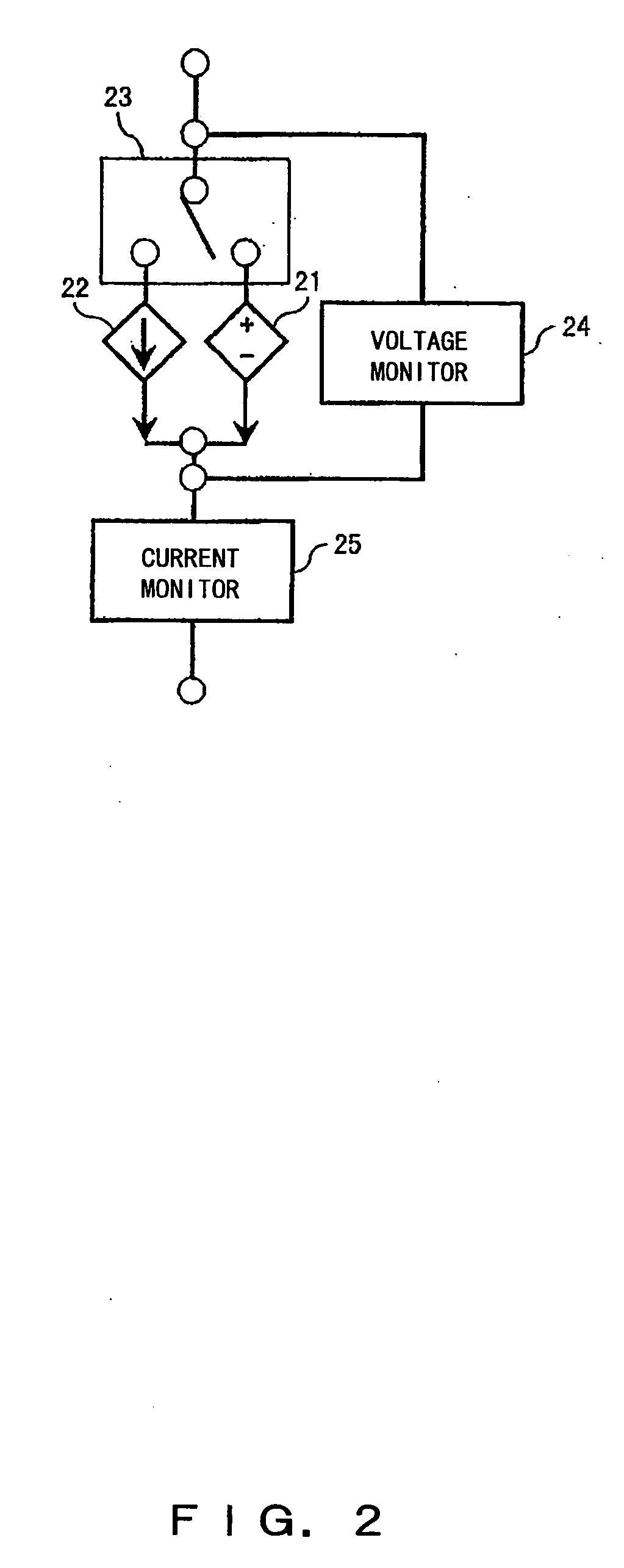
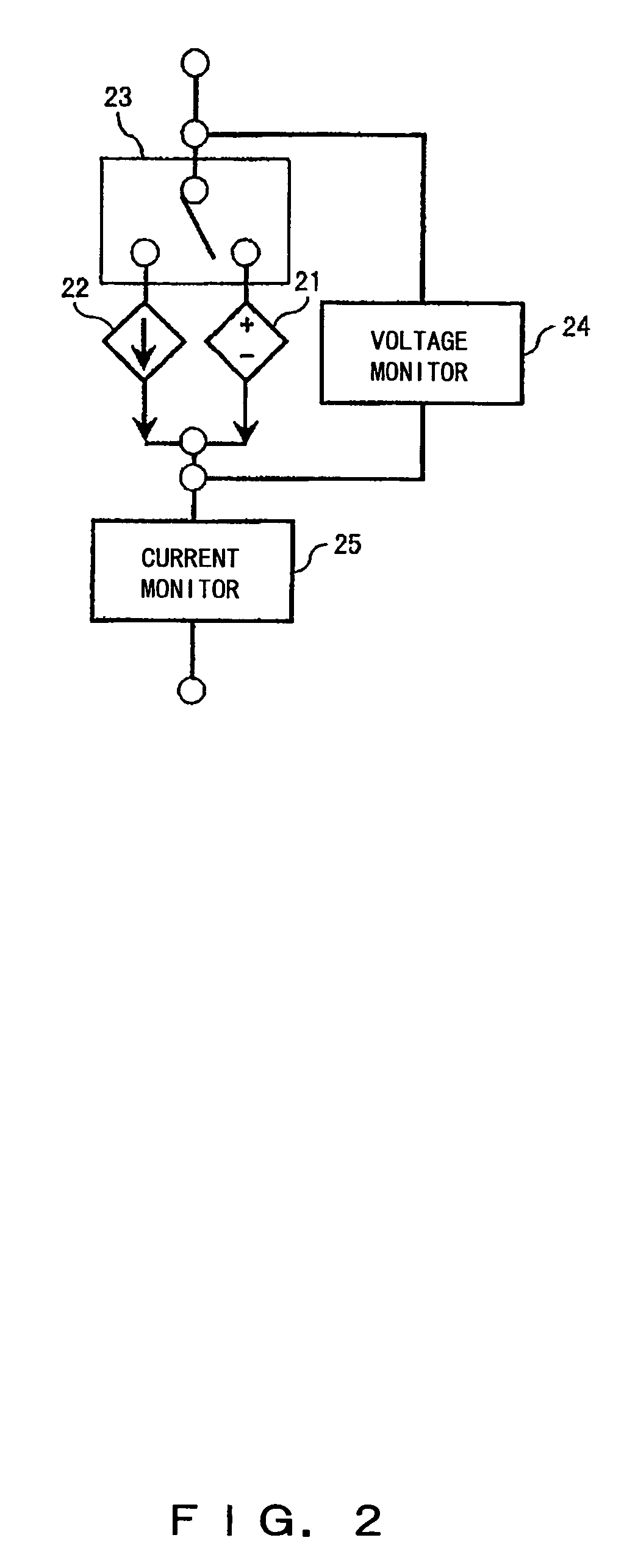
Elevator safety circuit monitoring system and method
ActiveUS7503435B2Reliable measurement resultsEasy to monitorElevatorsBuilding liftsPower flowMonitoring system
The invention concerns a method and a system for monitoring the operation of the safety circuit of an elevator, said safety circuit containing safety switches connected in series with a contactor and a static circuit. In the method, the current flowing in the safety circuit is measured and the state of the safety circuit is determined on the basis of the measured current. The measurement of the safety circuit current is preferably performed without a galvanic connection to the safety circuit. The state of the safety circuit is determined on the basis of the magnitude of the measured current, from which the positions of the safety switches during the current measurement can be inferred.
Owner:KONE CORP
Multiple access apparatus and method using power line
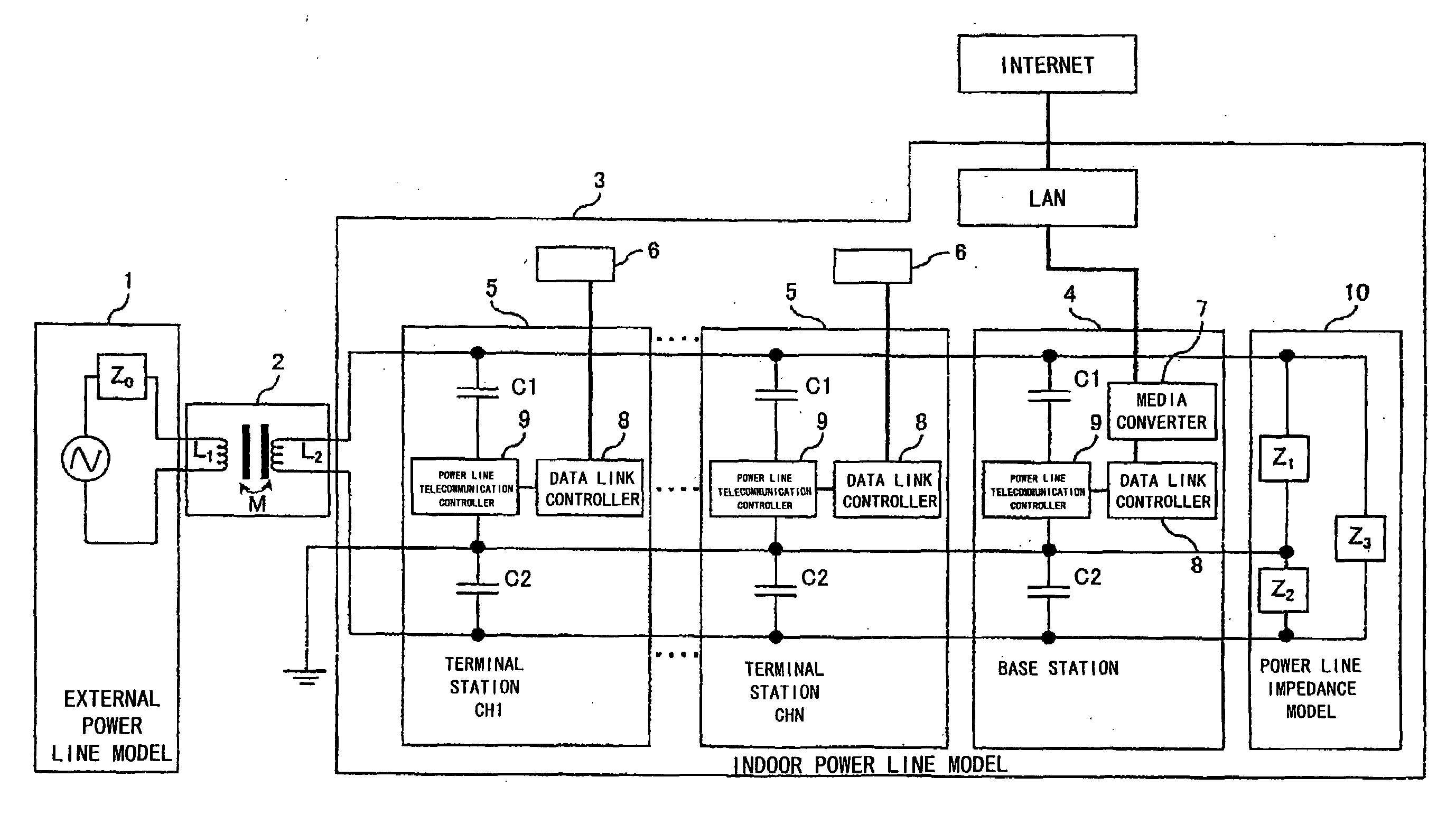
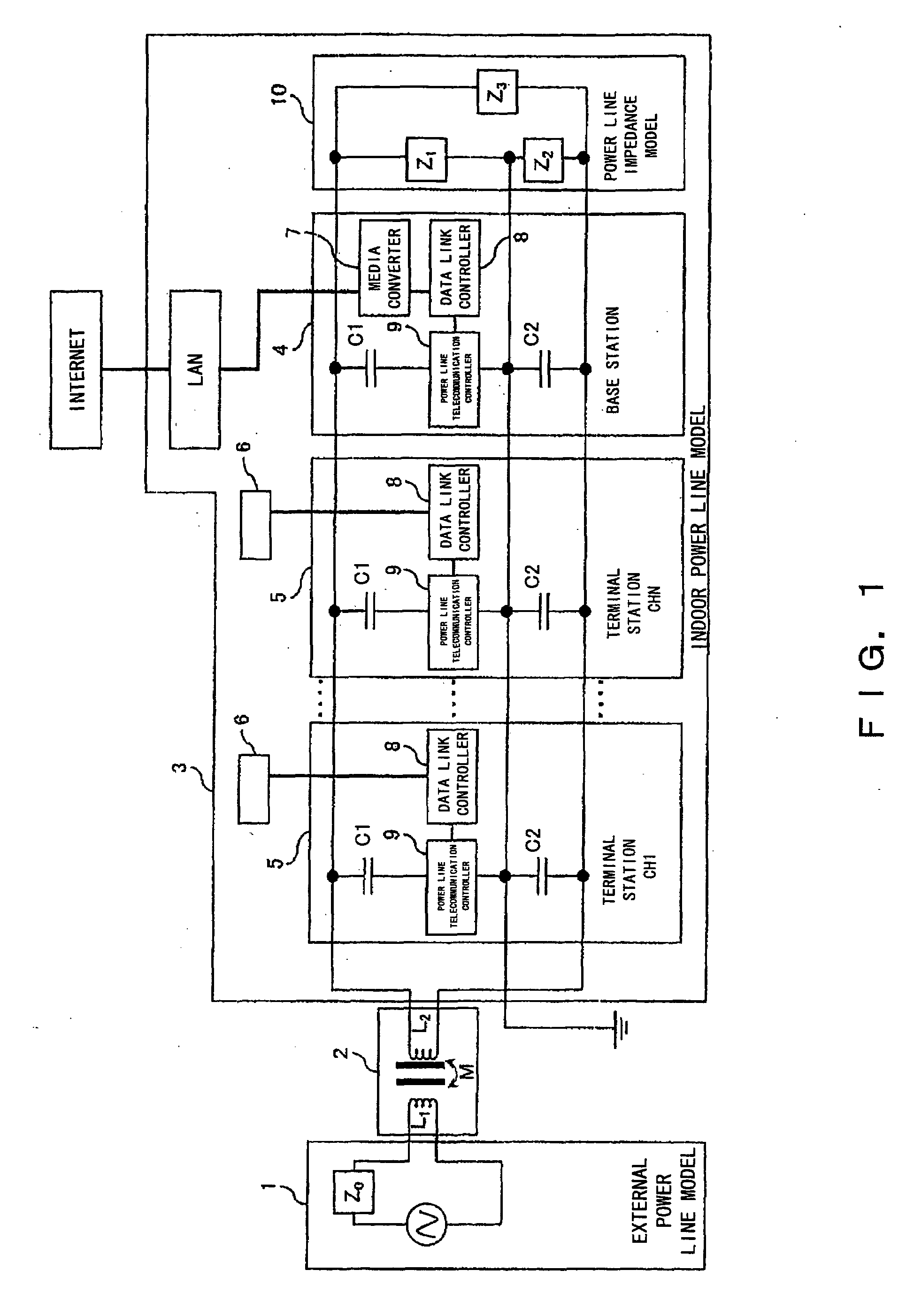
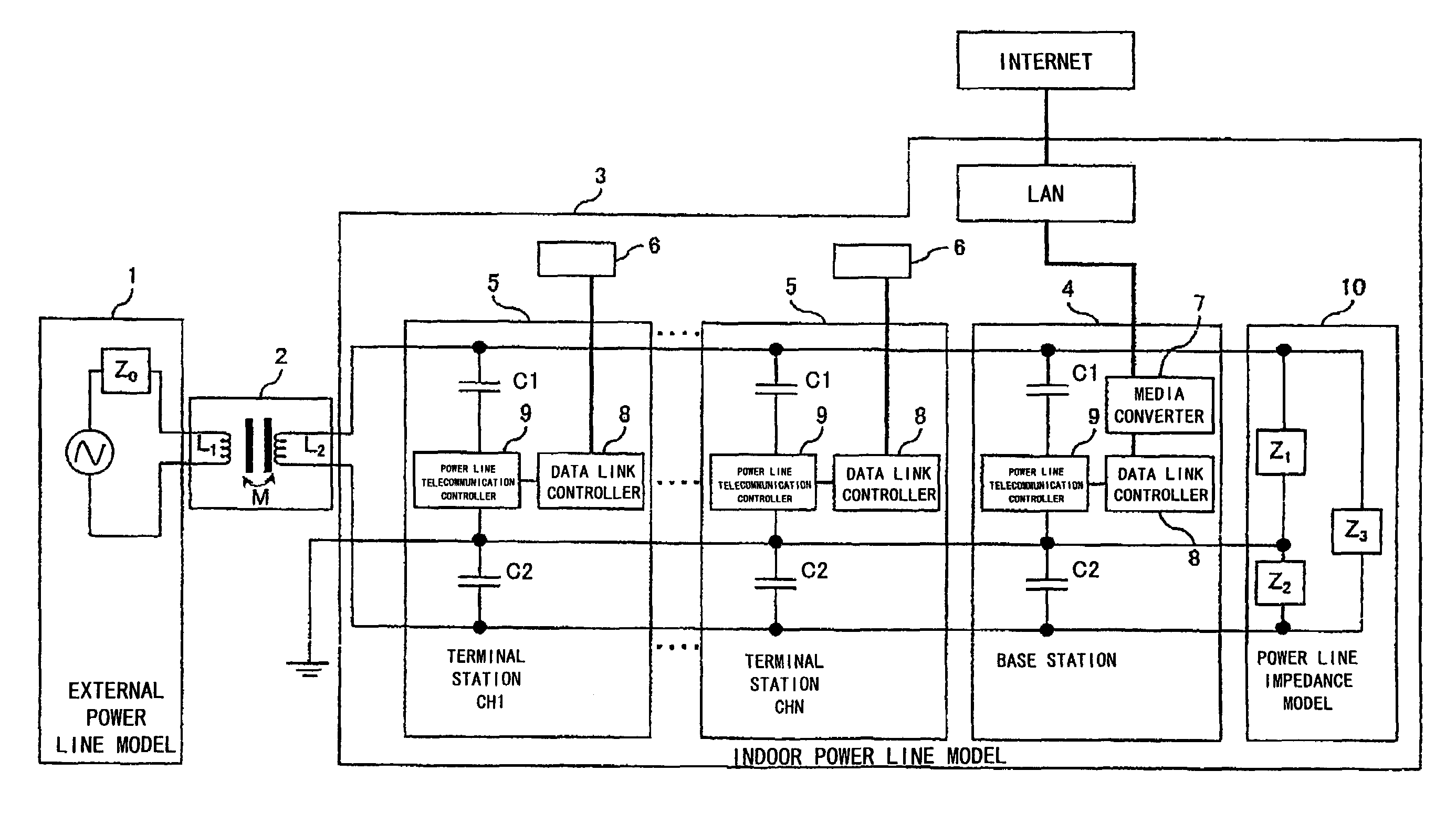
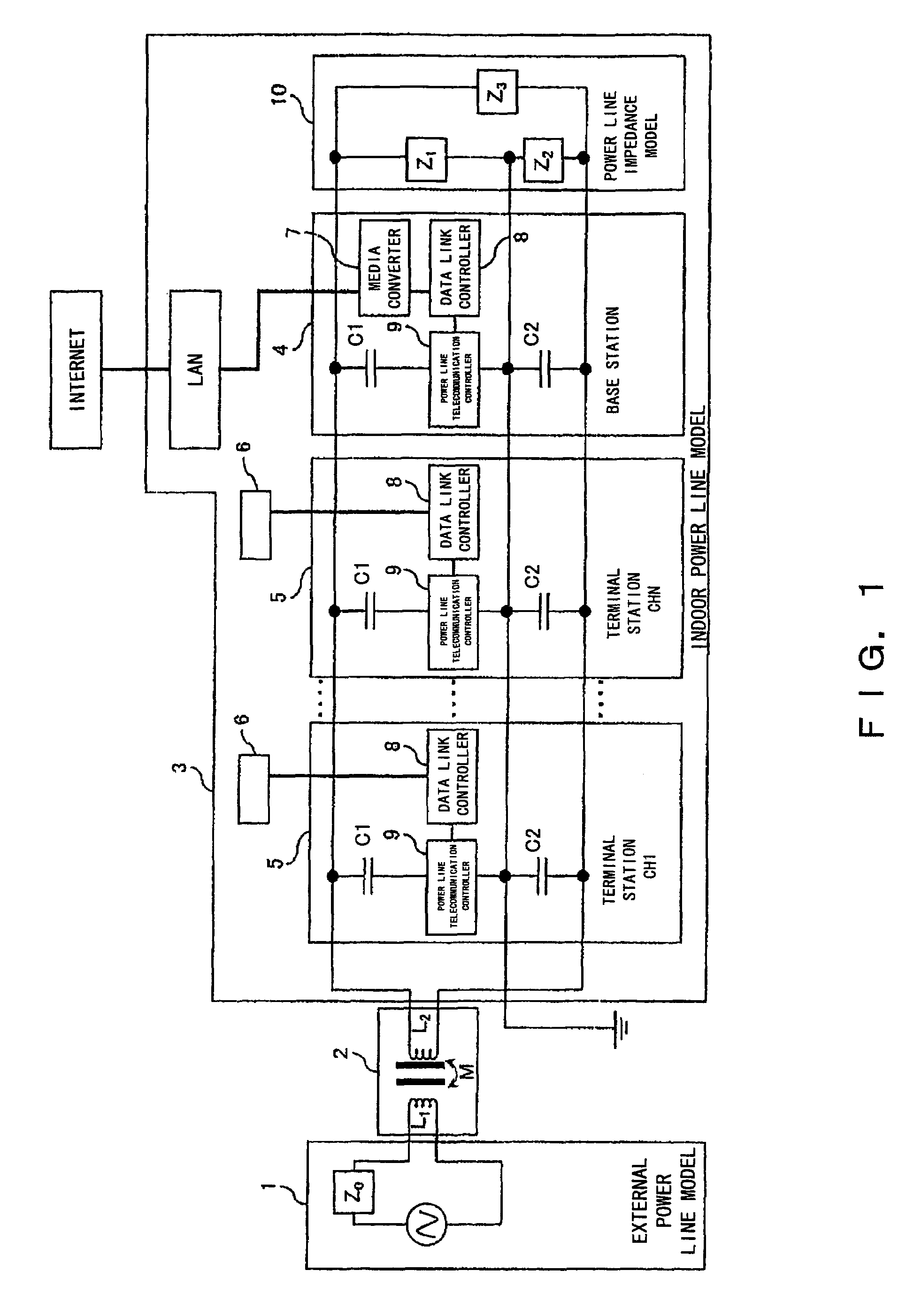
ActiveUS20080107134A1Increase in telecommunication transmission capacitySufficient level of securityTransmission/receiving by adding signal to waveSystems with measurements/testing channelsCode division multiple accessThe Internet
Provided is a telecommunication apparatus and a telecommunication method accomplishing a one-to-many, many-to-one, and many-to-many simultaneous accesses in a power line telecommunication of a code division multiple access (CDMA) by using an AC power line (including the ground).A comprisal includes an external power line model 1, a power distribution board 2 and an indoor power line model 3 which is connected to a power line by way of a capacitor for shutting off a sine wave of a power signal of a low frequency; a terminal station 5 and a base station 4 perform a power line telecommunication by way of a plug outlet; and the terminal station 5 controls and manages electric appliances installed in the indoor power line model 3. The terminal station 5 and base station 4 which are connected to the power line are connected to the Internet by way of a line; the base station 4 comprises a media converter 7 and a data link controller 8 which are connected to an external data bus, and also a power line telecommunication controller 9 for controlling a transmission and reception of an information signal and a synchronous signal; the terminal station 5 comprises a power line telecommunication controller 9 for controlling a transmission and reception of an information signal and a synchronous signal, thereby accomplishing an apparatus and method for carrying out a power line telecommunication.
Owner:SHONAN INSTITUTE OF TECHNOLOGY +2
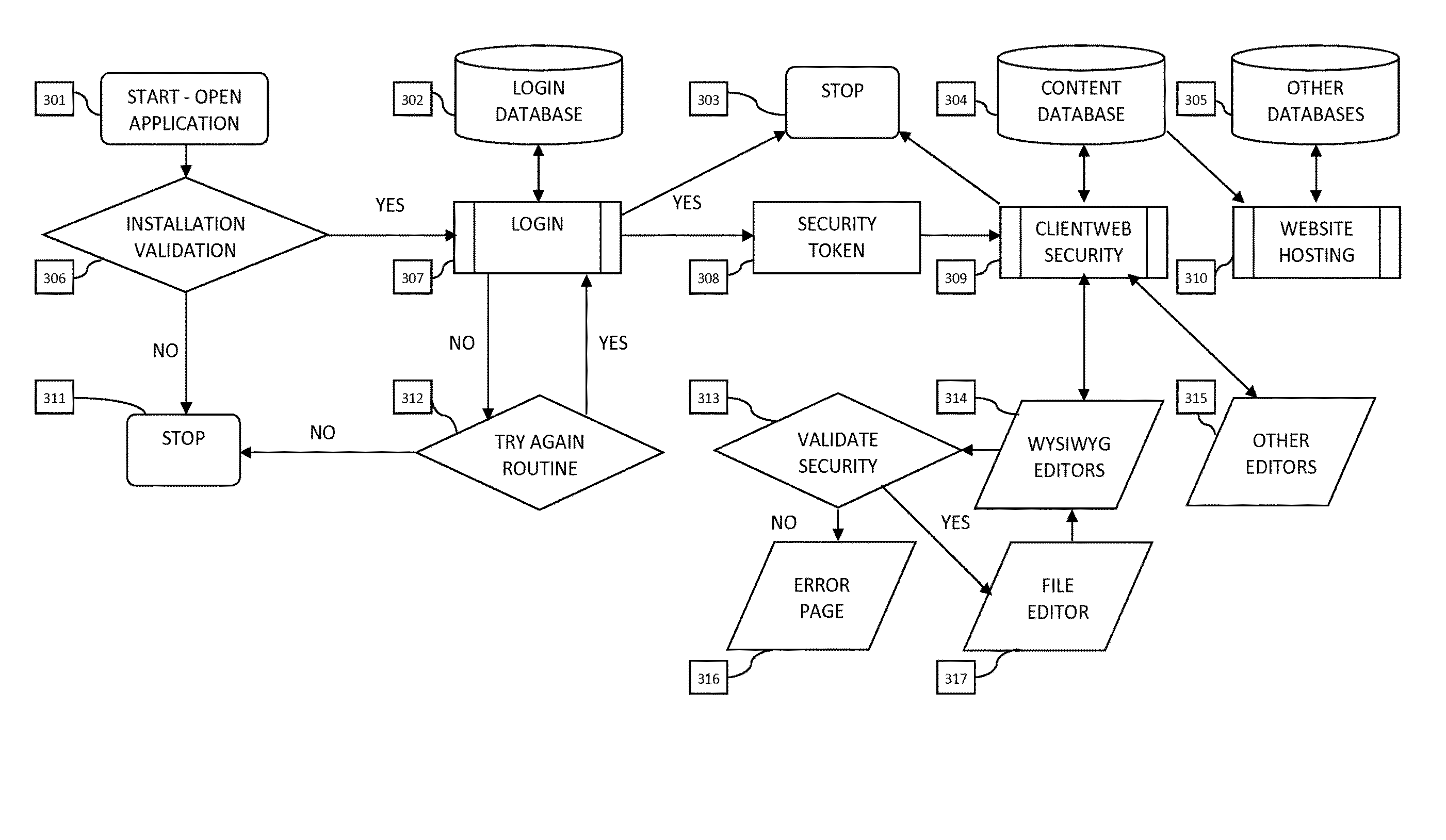
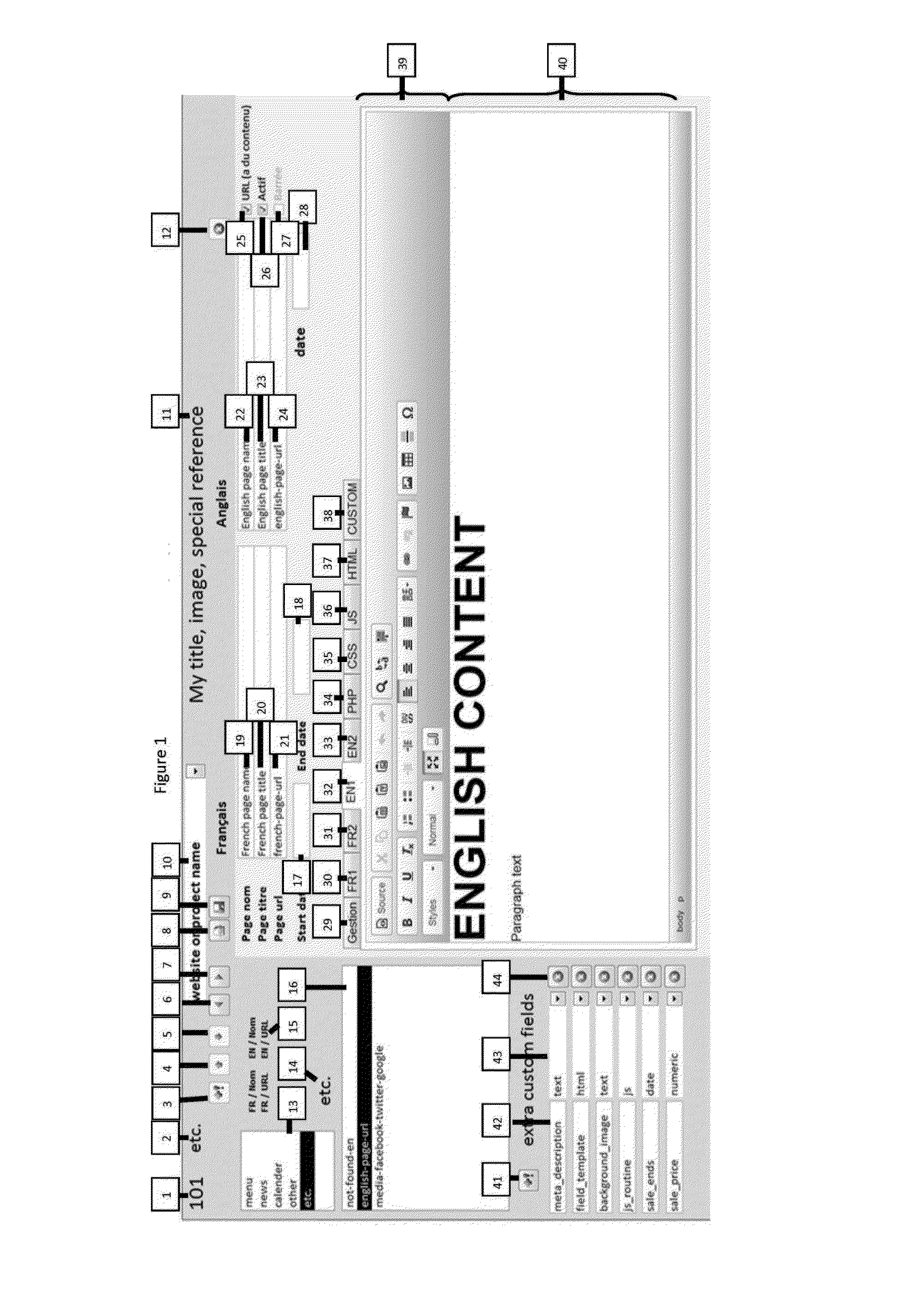
Method and system for securely updating a website
ActiveUS20160255090A1Improve securityControlling the riskDigital data protectionWebsite content managementMulti siteApplication software
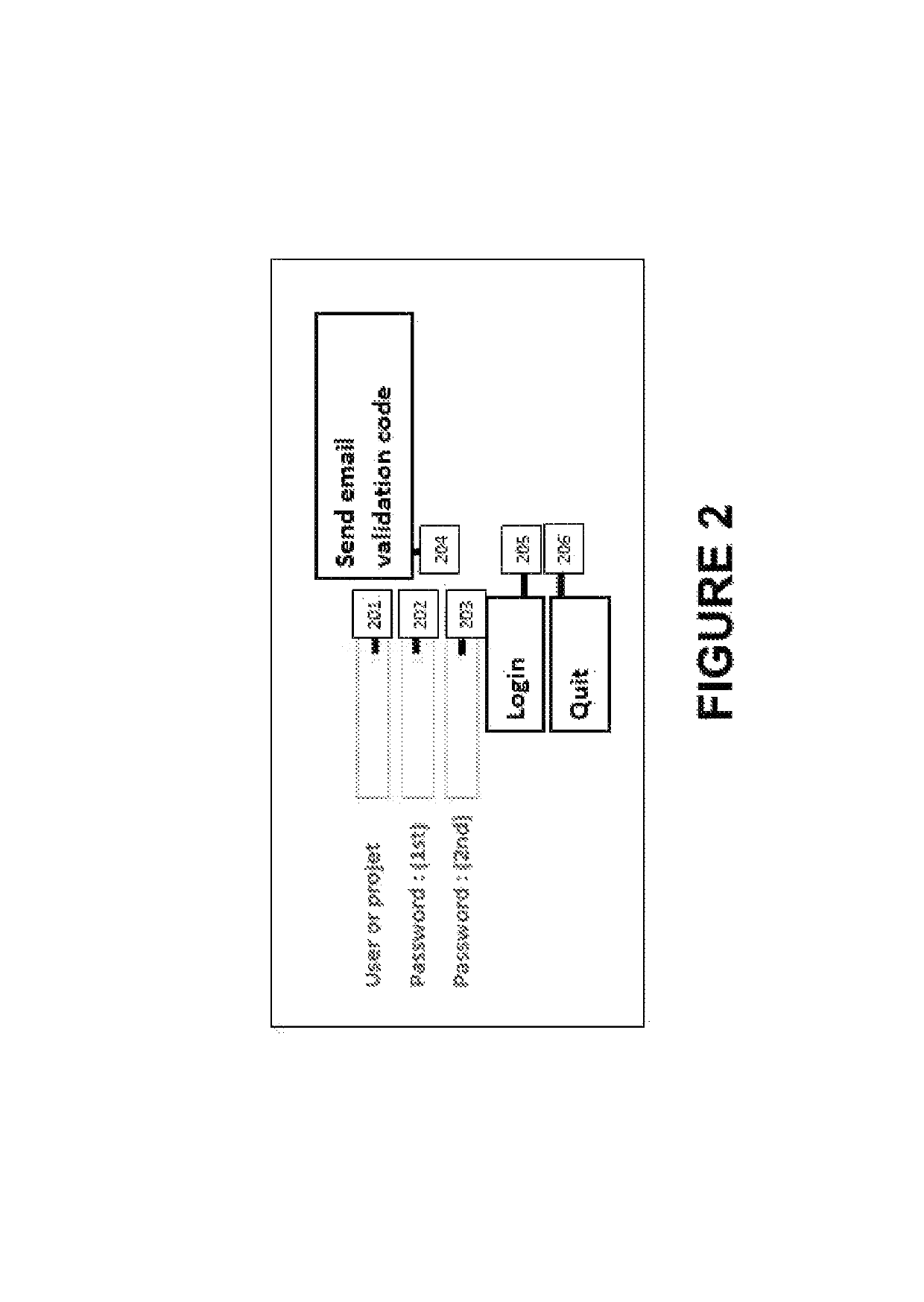
A computer program product for securely updating a website is installed on a computer, uses a WYSIWYG (What You See Is What You Get) editor, and may be used as a multi user, multi site, and multi project with varying per user permissions. A CMS stores the information in a database that can be displayed on a website, and is secured with a hashed password and content can be encrypted. The CMS can store miscellaneous language modes that are color coded such as PHP, JS, CSS, Java, and HTML. There are thus no passwords found in the website source files that make it possible to modify the database content. The security remains solely in the hands of the application and limits hacking. The program product is accessible from a computer-usable or computer-readable medium providing program code for use by or in connection with a computer or any instruction execution system.
Owner:JOHNSTON JR KEVIN
Method of encrypting and decrypting data stored on a storage device using an embedded encryption/decryption means
InactiveUS8001391B2Improve security levelSufficient level of securityKey distribution for secure communicationUnauthorized memory use protectionData storingData store
Owner:DATAPLAY
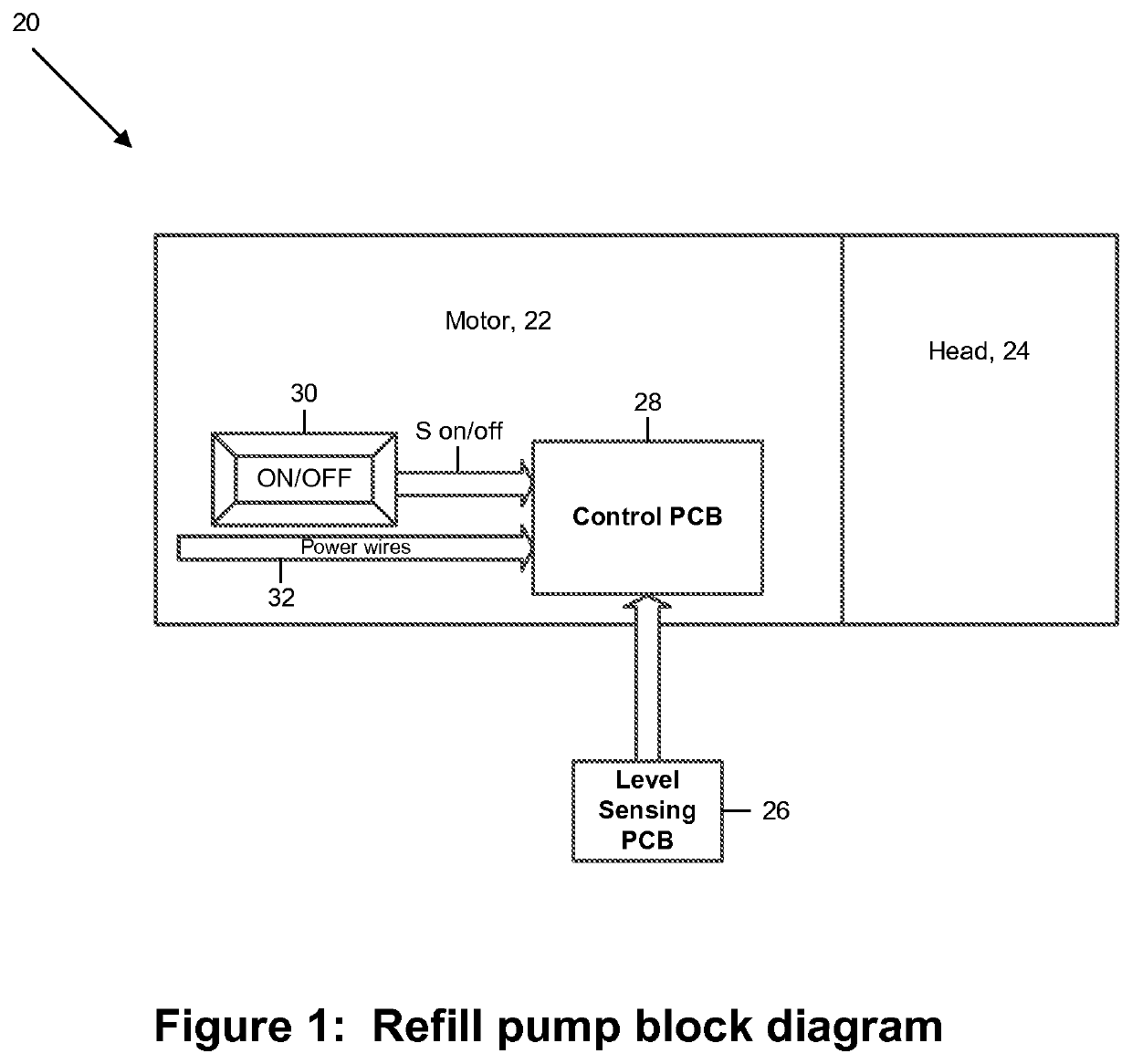
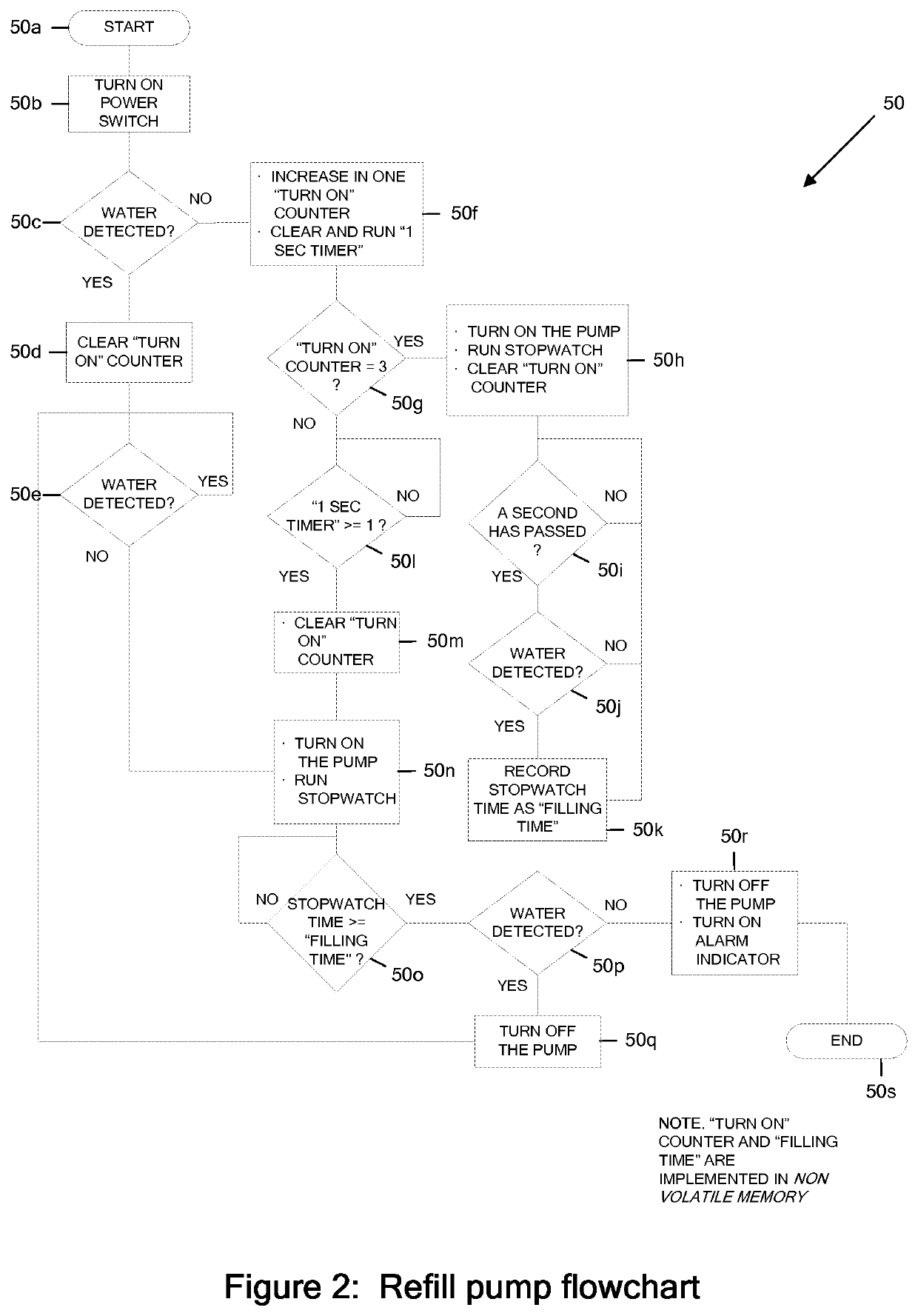
Automatic fill control technique
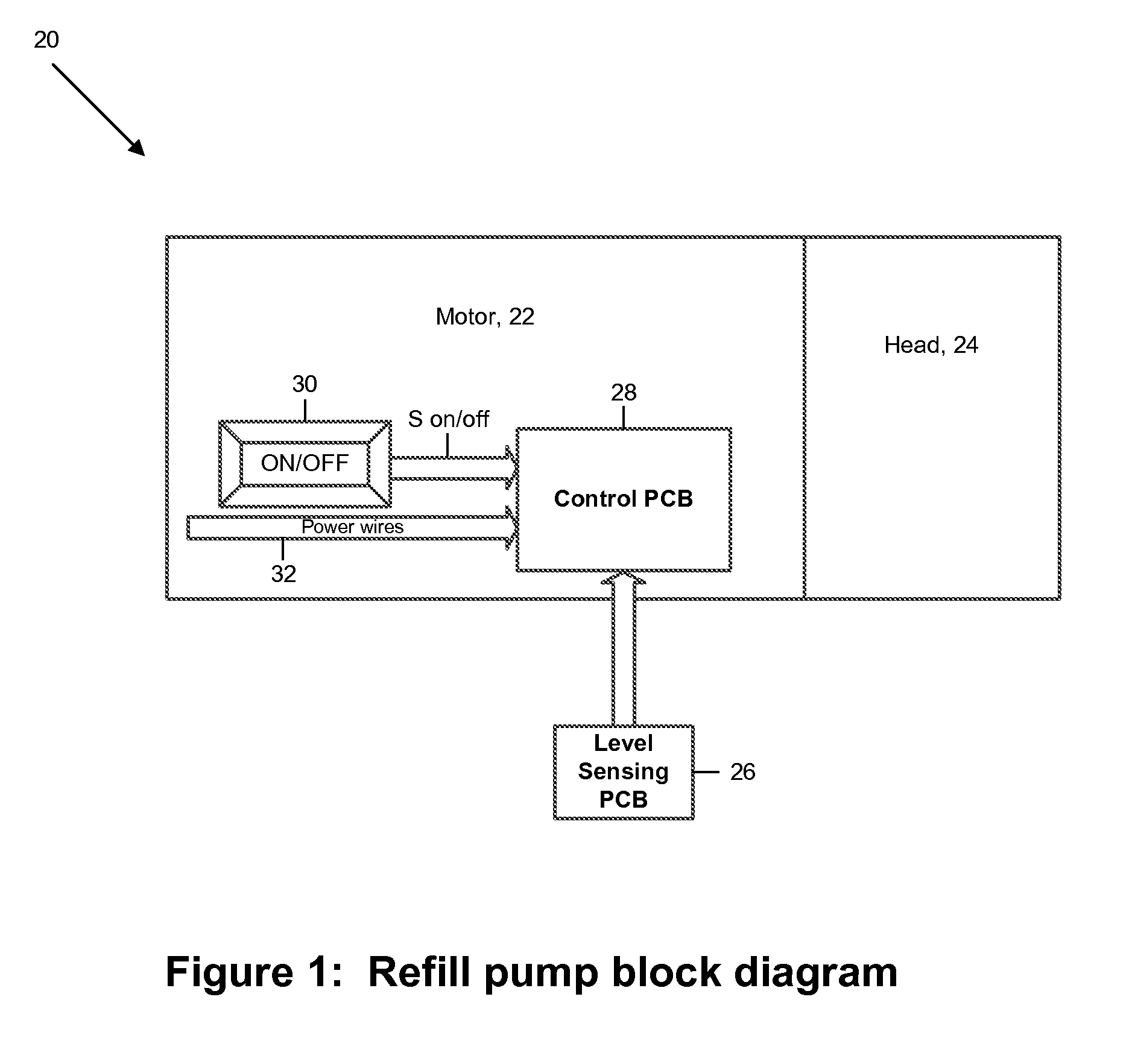
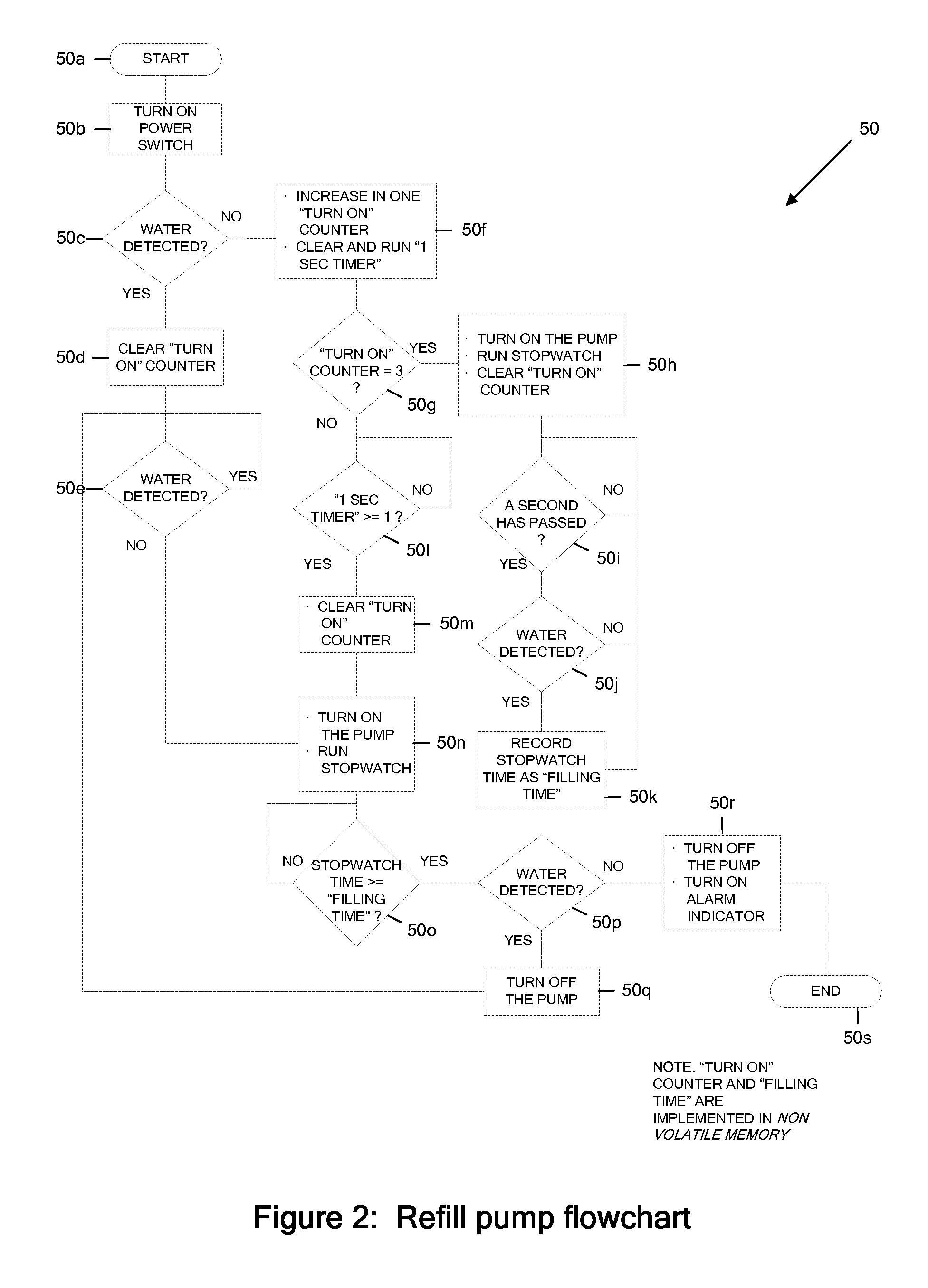
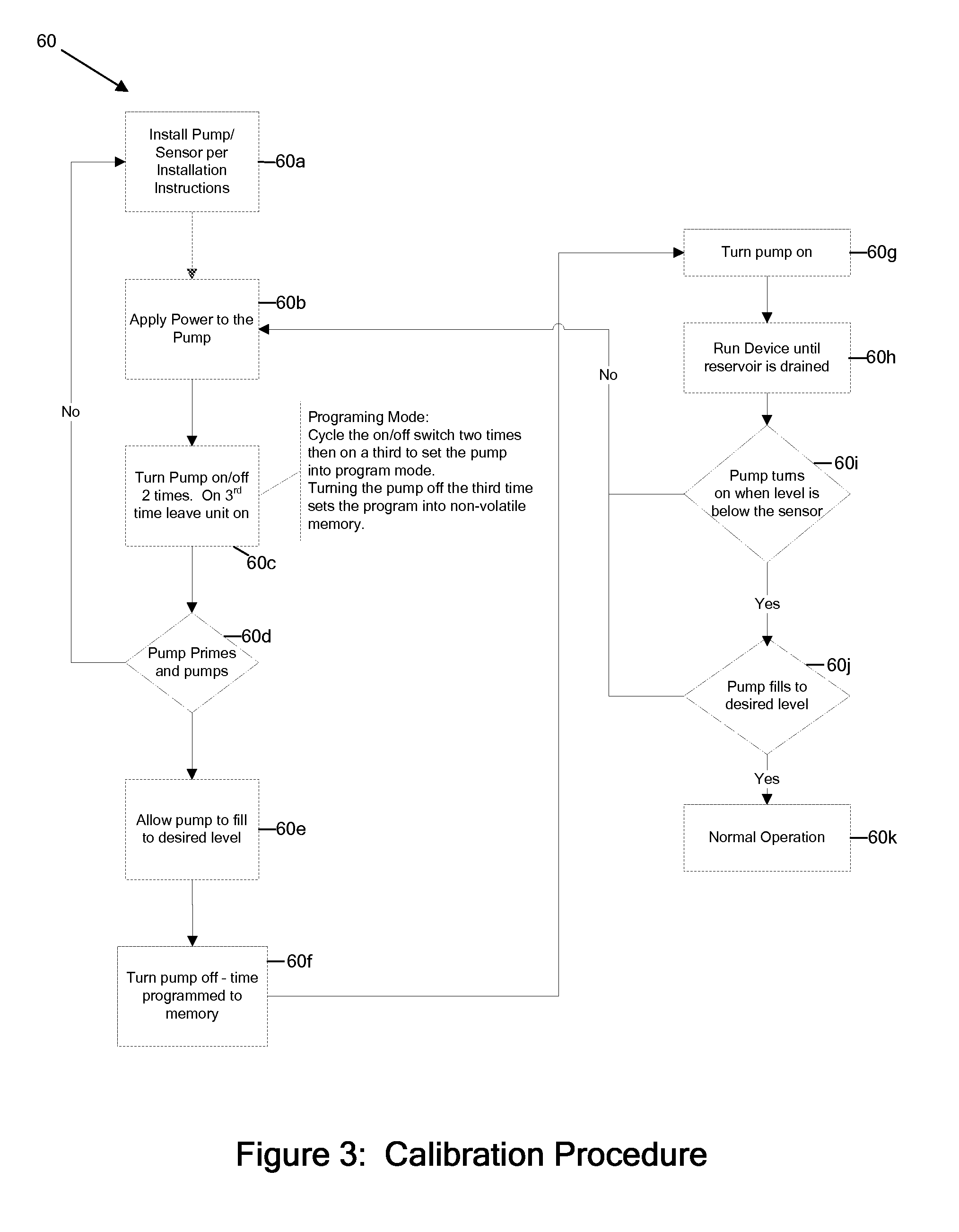
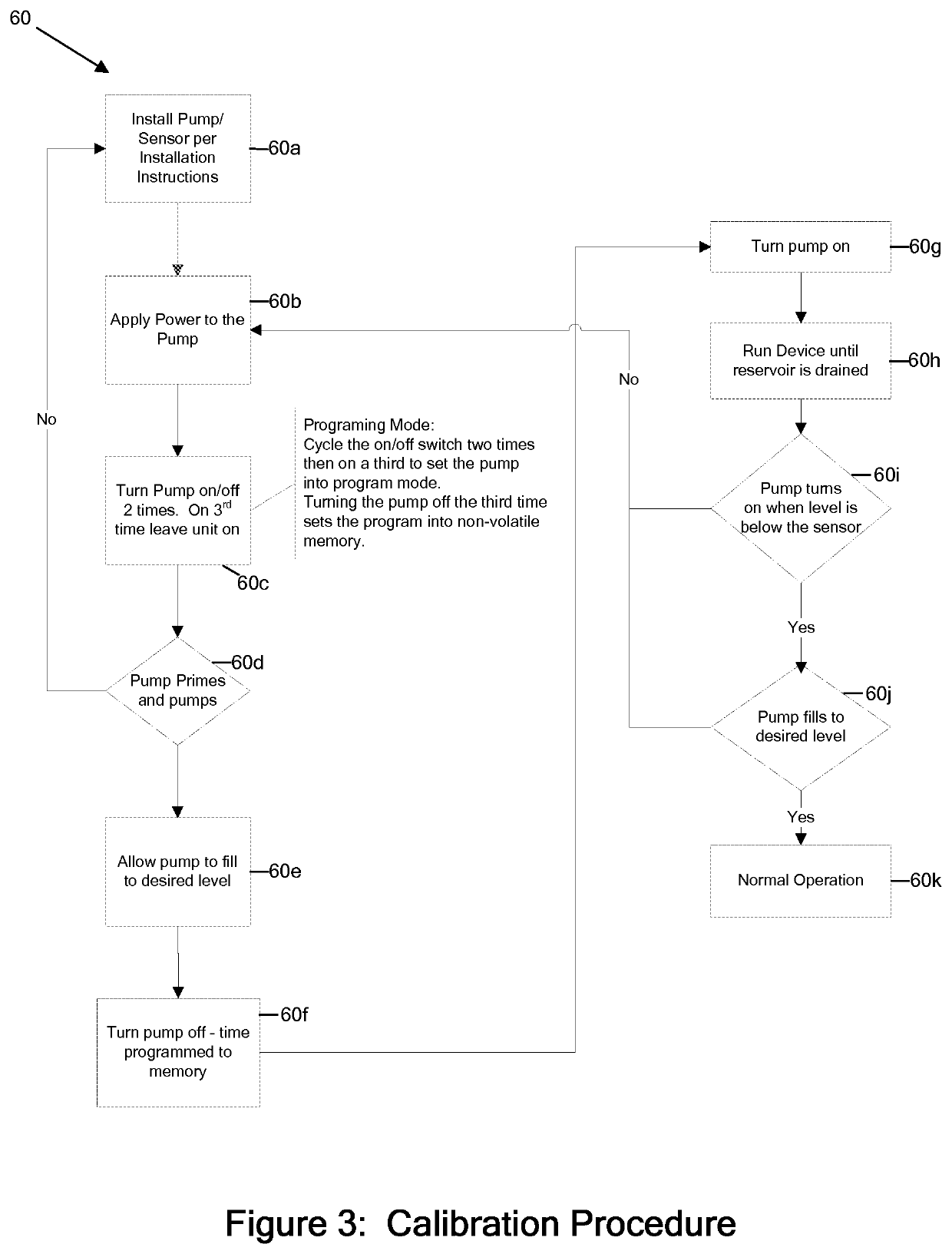
ActiveUS20160048137A1Prevent overflowSufficient level of securityLevel controlFlow control using electric meansEngineeringSignal processing
A pump includes a signal processor that receives signaling containing information about a low level of a liquid sensed in an appliance reservoir to be supplied to an appliance that uses the liquid to dispense a flavored beverage, and also about when the appliance reservoir is refilled based upon an indication that forms part of an appliance reservoir refill level calibration procedure programmed by an appliance user; and determines corresponding signaling containing information about automatically refilling the liquid in the appliance reservoir, based upon the signaling received.
Owner:FLOW CONTROL LLC
Membranes and Membrane Systems
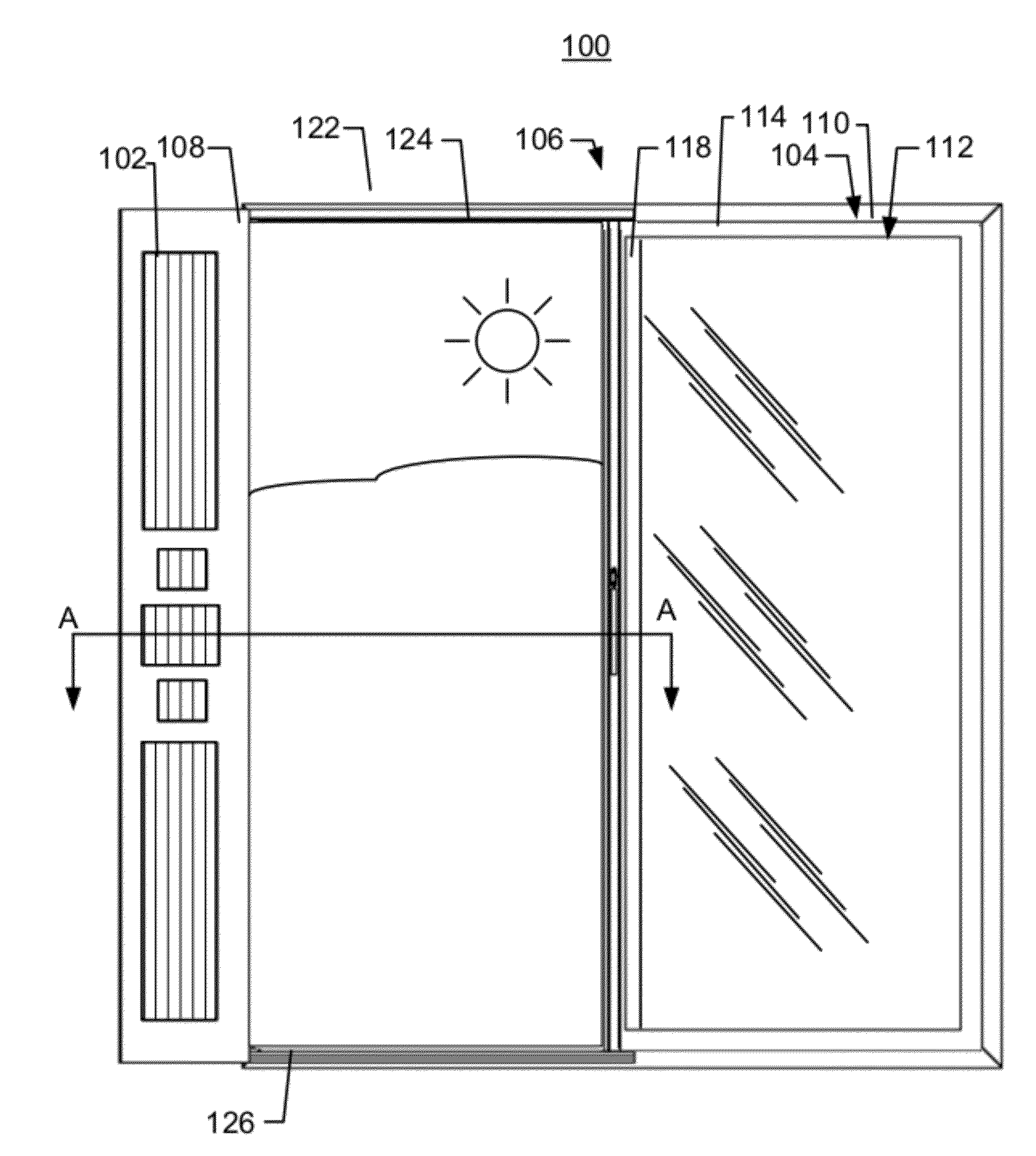
InactiveUS20120031001A1Easy to useSufficient level of securityFixed grillesBuilding locksEnvironmental effectEngineering
Disclosed herein is a window or doorway membrane system for selectively preventing ingress or egress of persons, animals, objects, or other unwanted environmental effects. The system may include a membrane, a first engagement mechanism for securing one end of the membrane to a wall or other anchor point; and a second engagement mechanism for releasably securing the membrane to a active panel of a door or window.
Owner:DORR TOM BRUCE +1
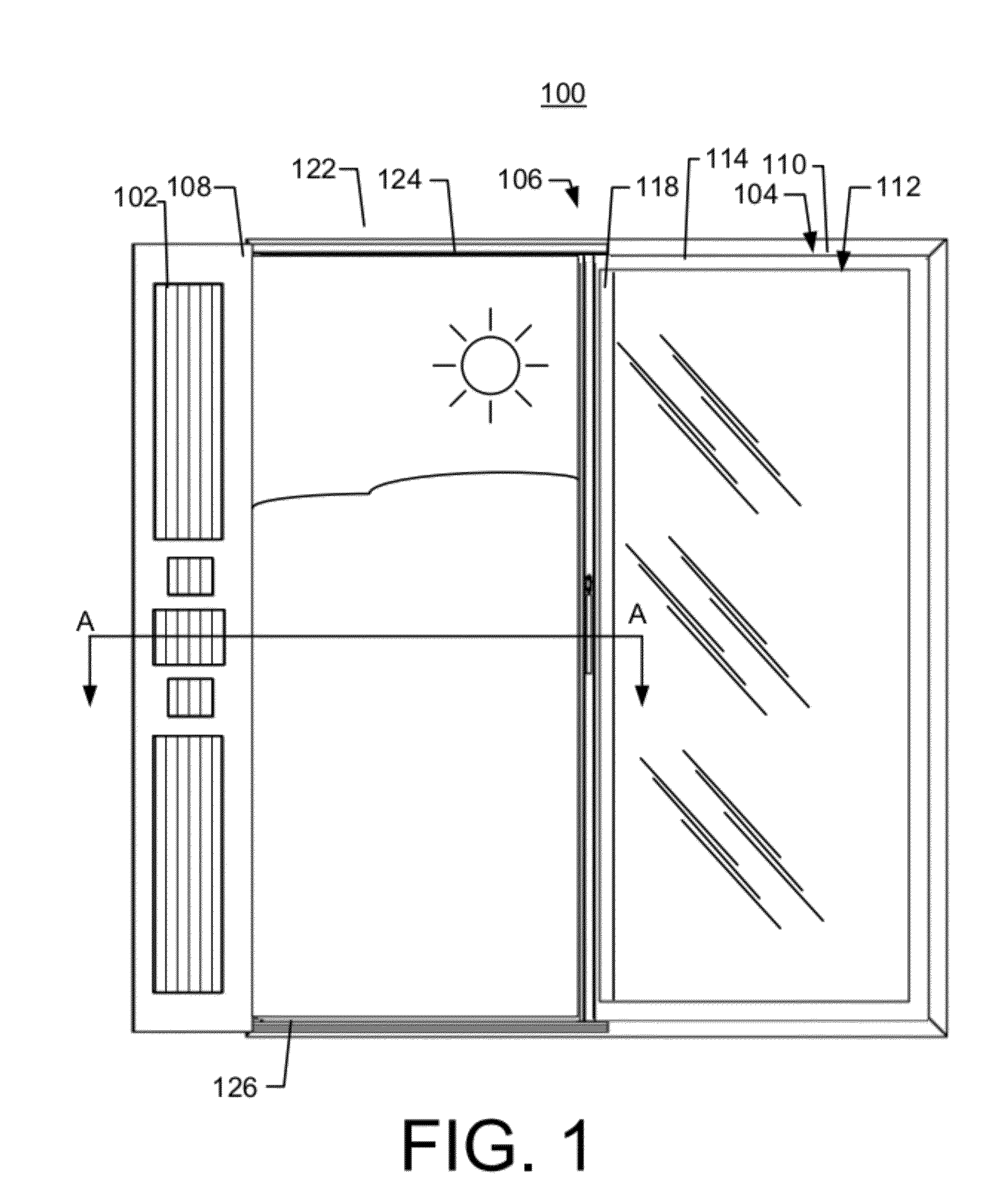
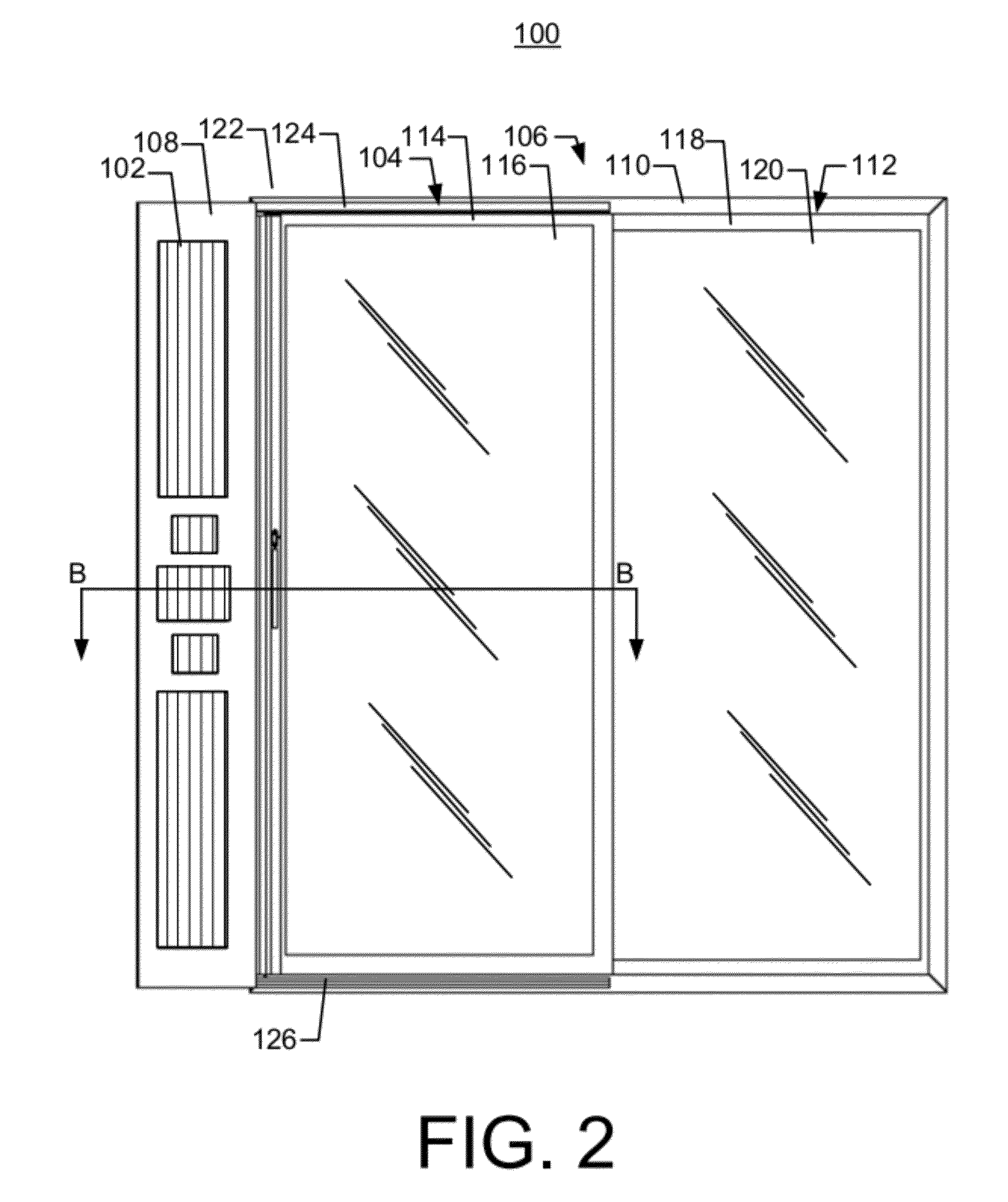
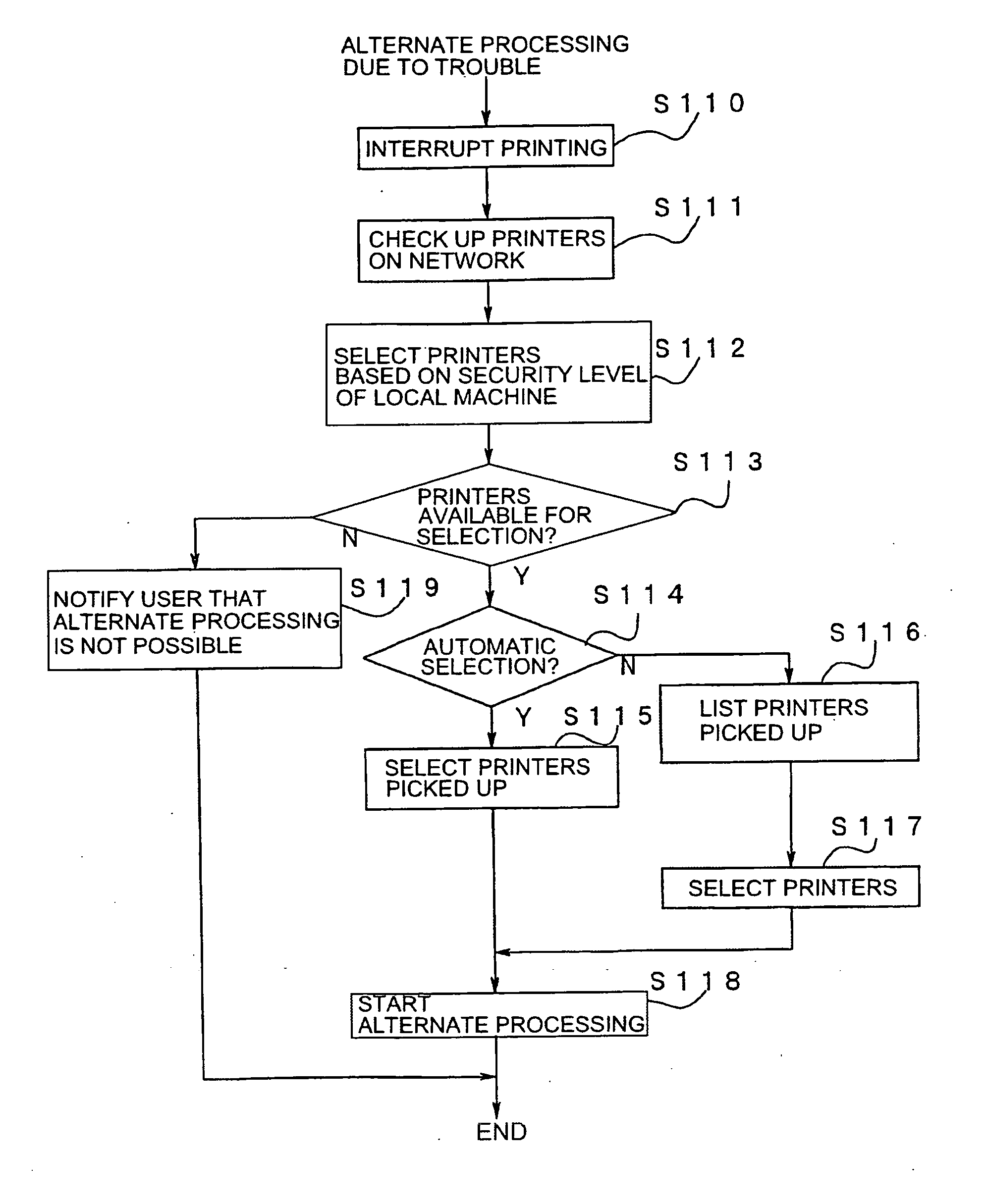
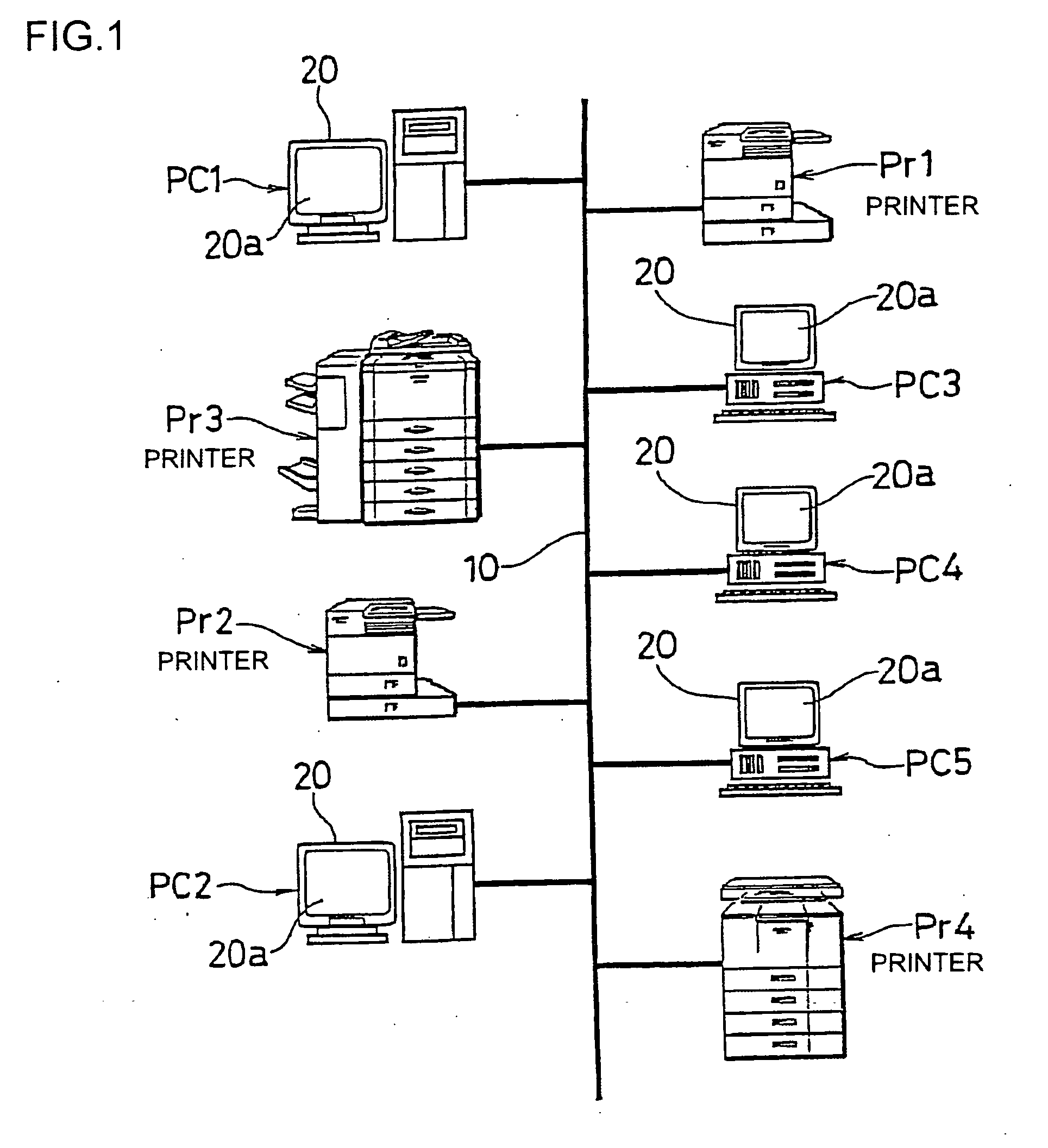
Image processing device and image processing system
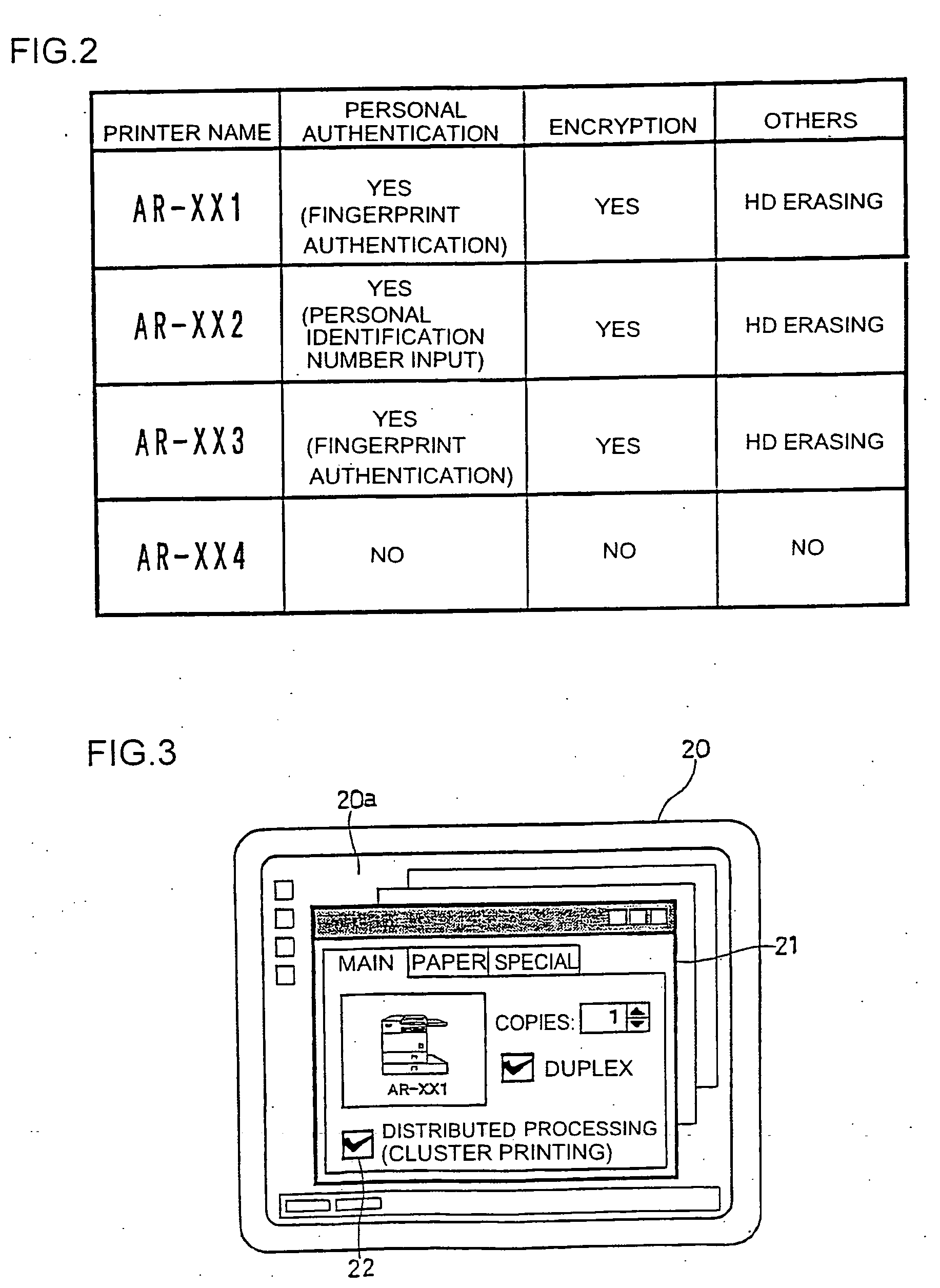
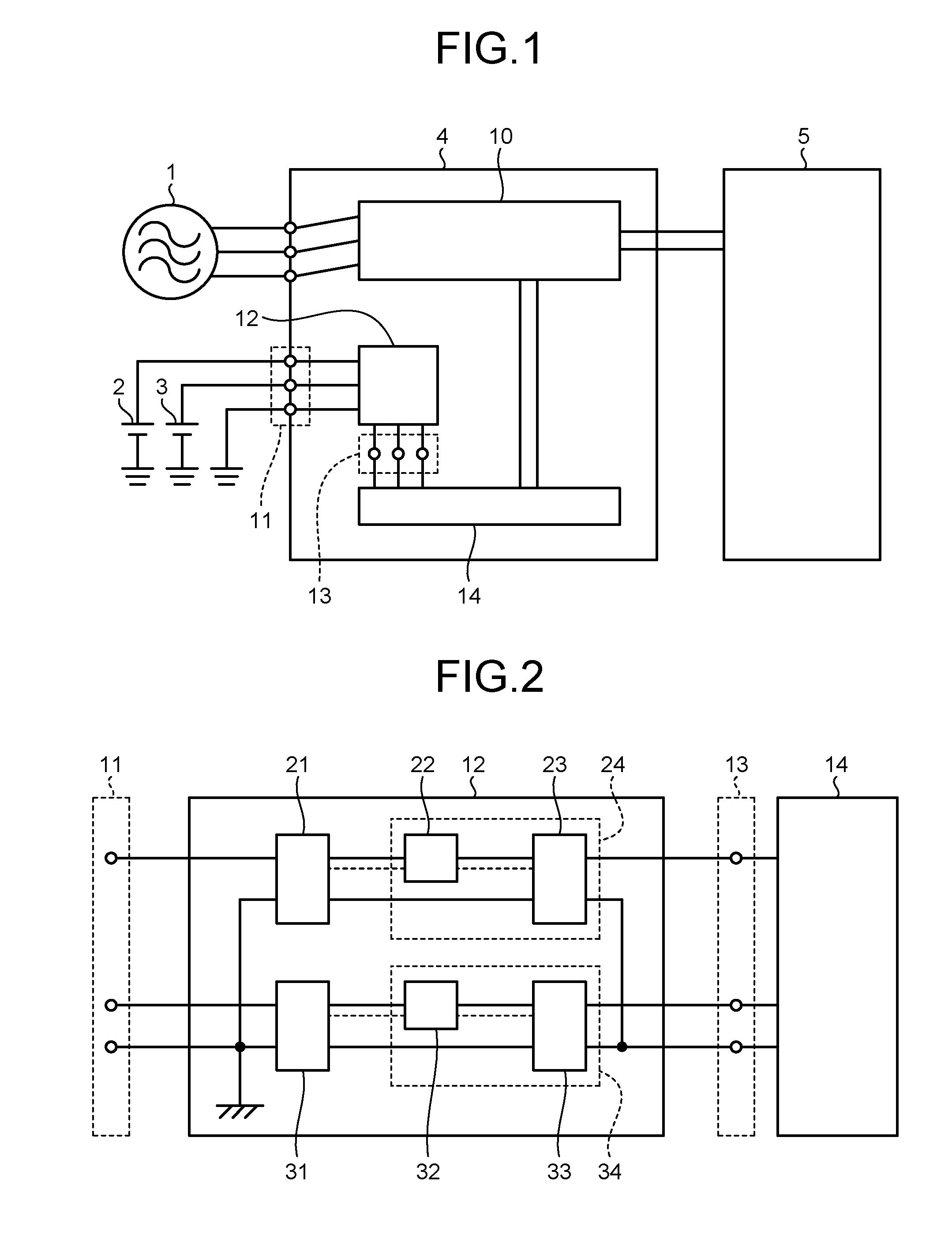
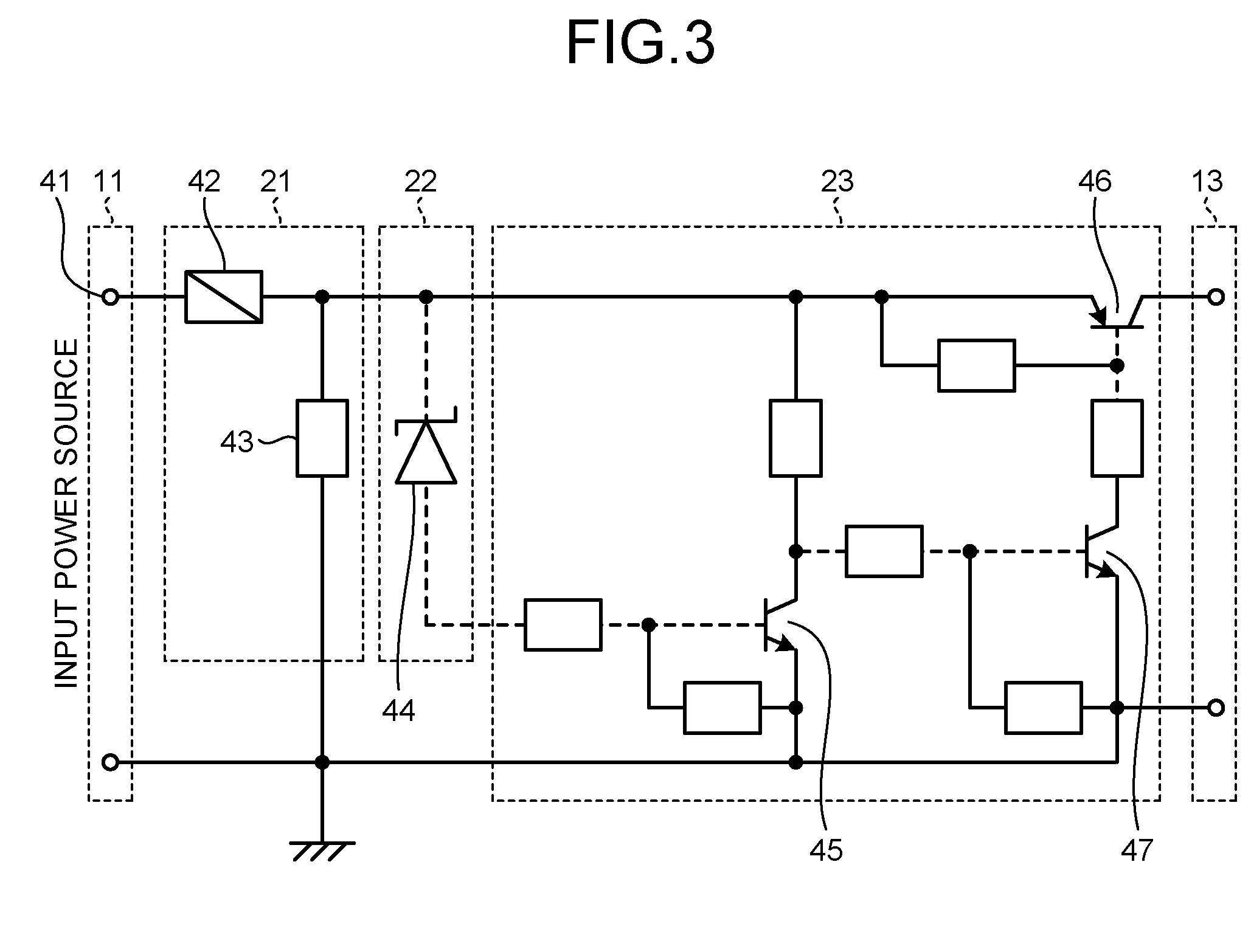
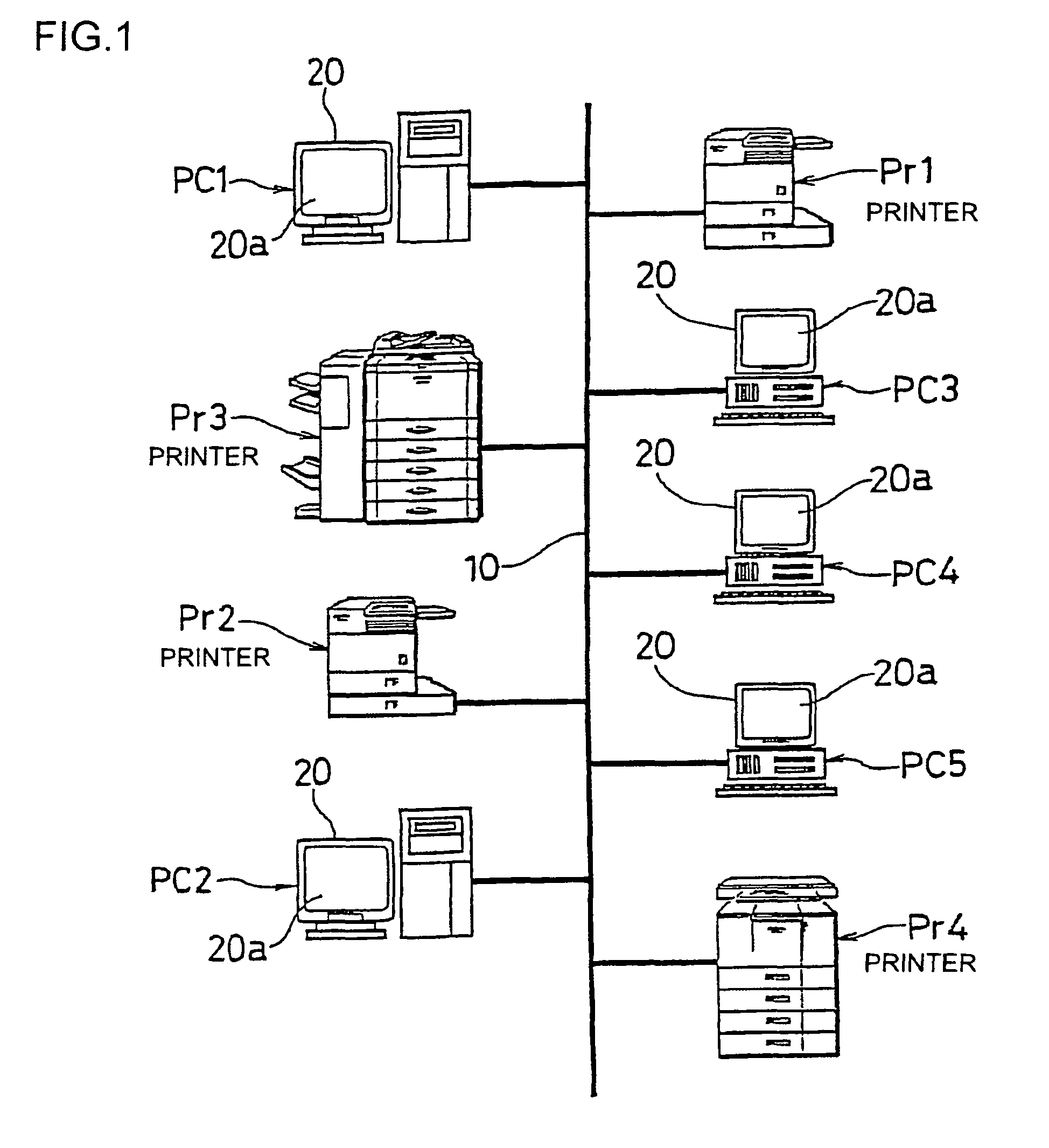
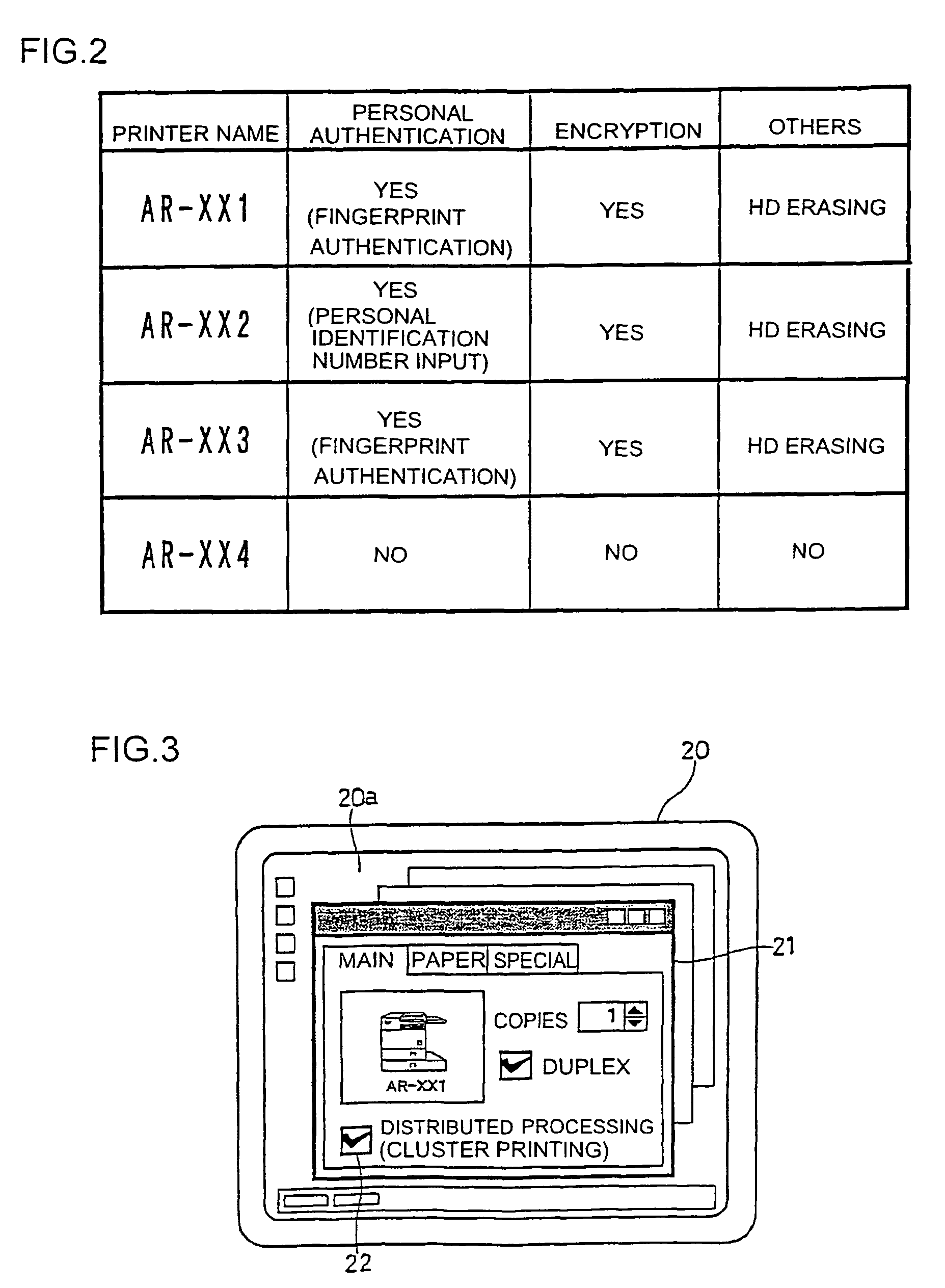
ActiveUS20100141978A1Process is performedStay safeVisual presentation using printersComputer security arrangementsImaging processingComputer graphics (images)
An image processing device includes a plurality of printers (Pr1, Pr2, Pr3, Pr4, . . . ) and a plurality of client machines (PC1, PC2, PC3, PC4, PC5, . . . ). When requesting an image data processing to a printer other than the printer to which an image data processing has been requested firstly, the client machine checks the security level of the other printer to which the image data processing is to be requested before requesting the image data distribution processing to the other printer. When selecting another printer to which the image data distribution processing is to be requested, the security level in each printer is sufficiently considered.
Owner:SHARP KK
Method for manufacturing a sheet by means of compregnation in order to form an area made transparent
InactiveUS20130181434A1Easy to observeSufficient level of securityStampsOther printing matterEngineeringPolymer
The present invention relates to a method for manufacturing a sheet including a substrate made of at least one polymer material, comprising the following consecutive steps: a) compregnating at least one area of the substrate such as to form at least one area made transparent; b) providing the substrate with at least two security elements, respectively on the front and back of the substrate, said at least two security elements each being at least partially stacked on said at least one area made transparent and being placed in a marked manner in relation to one another.
Owner:ARJO WIGGINS SECURITY SAS
Semiconductor integrated circuit and method of testing semiconductor integrated circuit
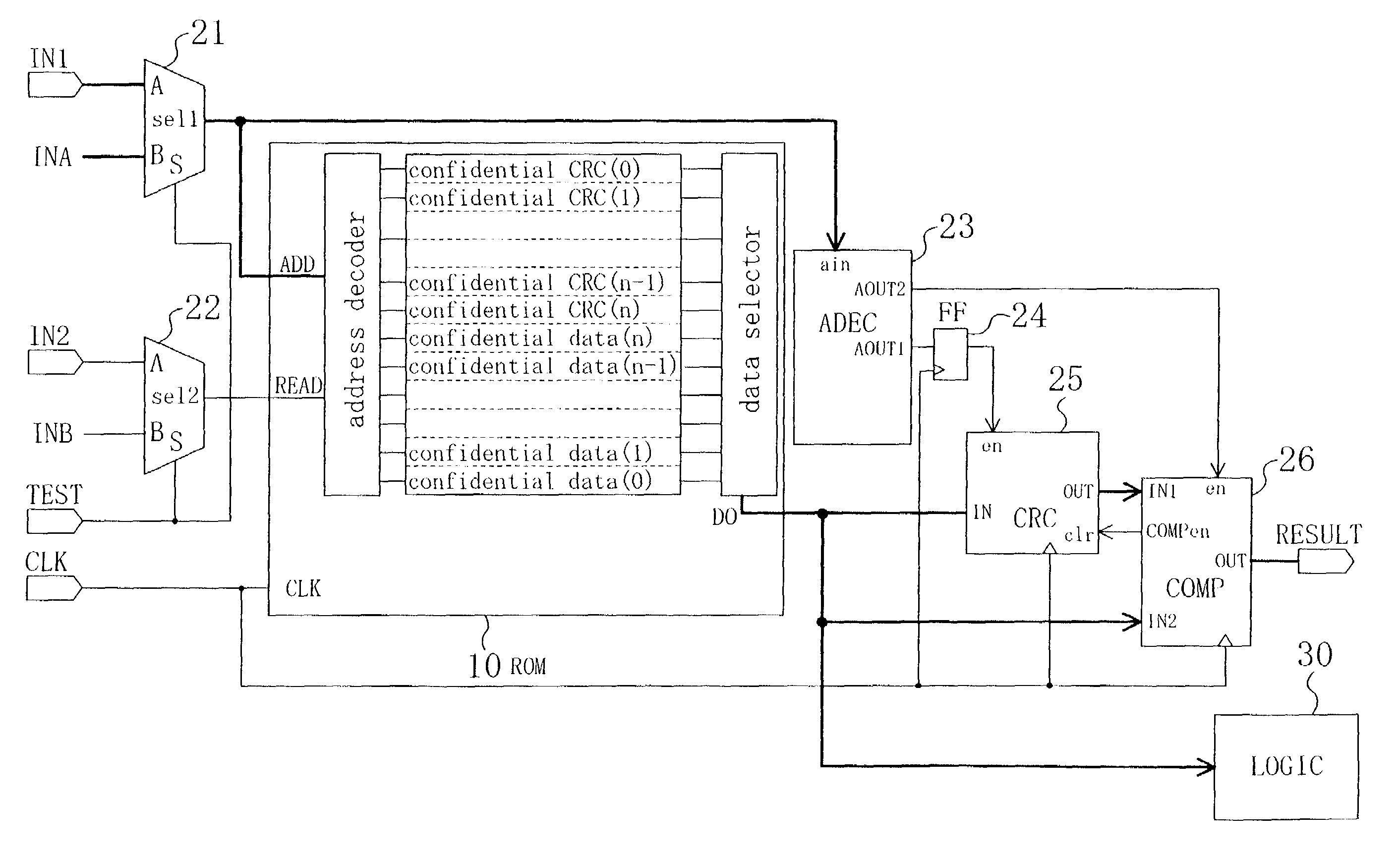
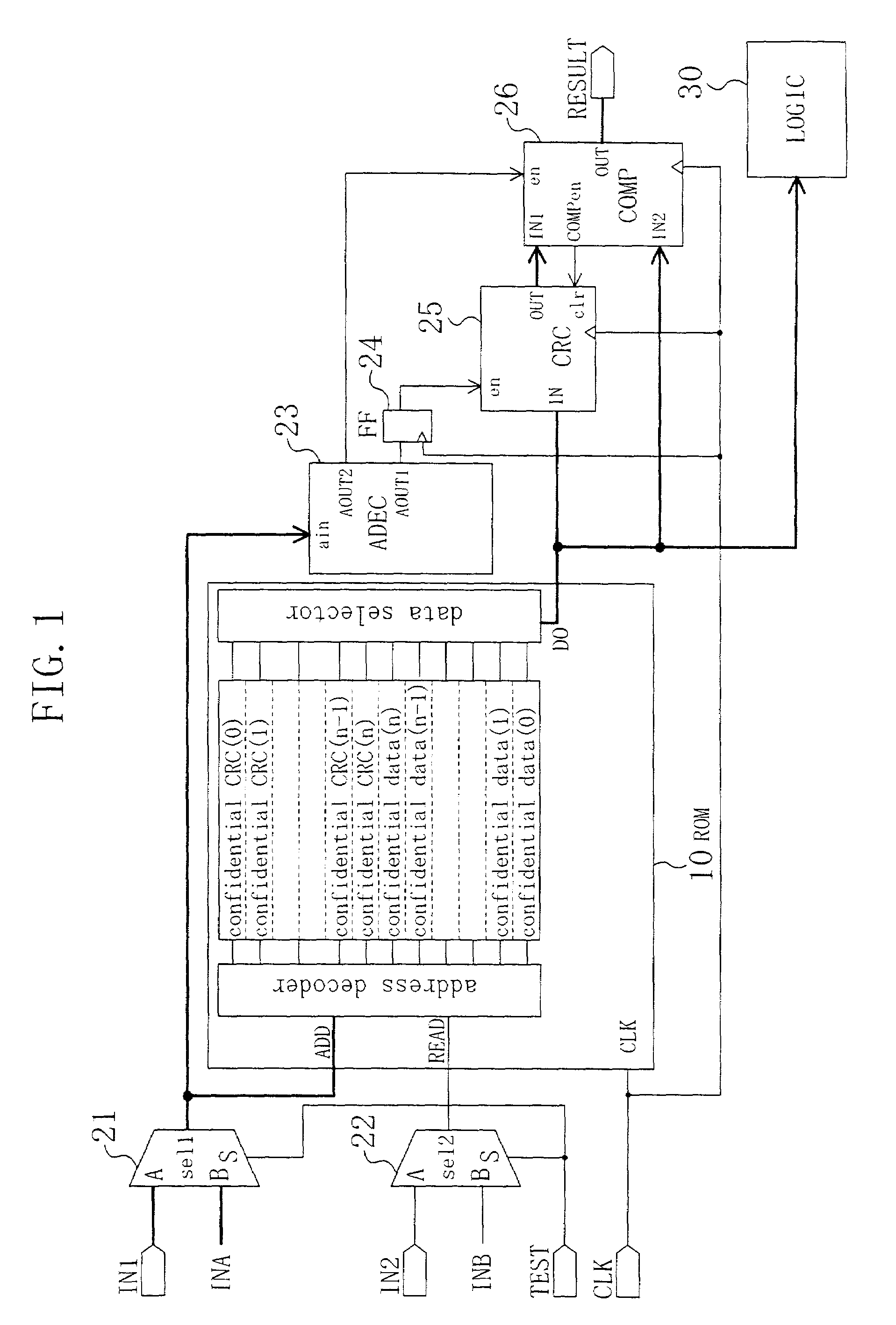
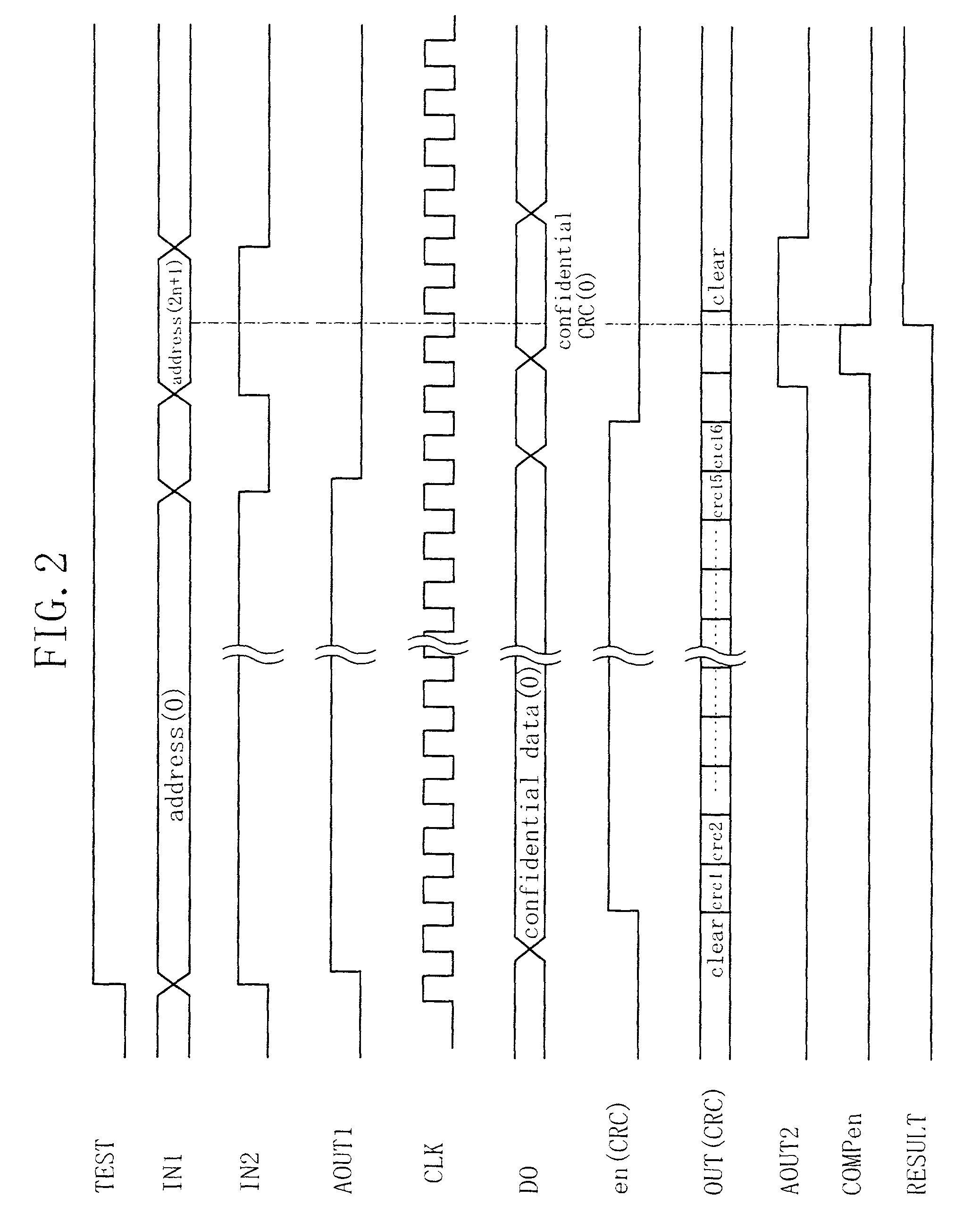
InactiveUS7184545B2Sufficient level of securityWithout decreasing security levelMemory loss protectionRead-only memoriesInternet privacyComparator
Confidential CRC codewords are stored along with confidential data words on a ROM. A checker subjects one of the confidential data words, which has been read out from the ROM, to the same type of calculation as a predetermined calculation that was carried out to produce associated one of the confidential CRC codewords. A comparator compares a result of the calculation performed by the checker to the associated confidential CRC codeword that has been read out from the ROM.
Owner:PANASONIC SEMICON SOLUTIONS CO LTD
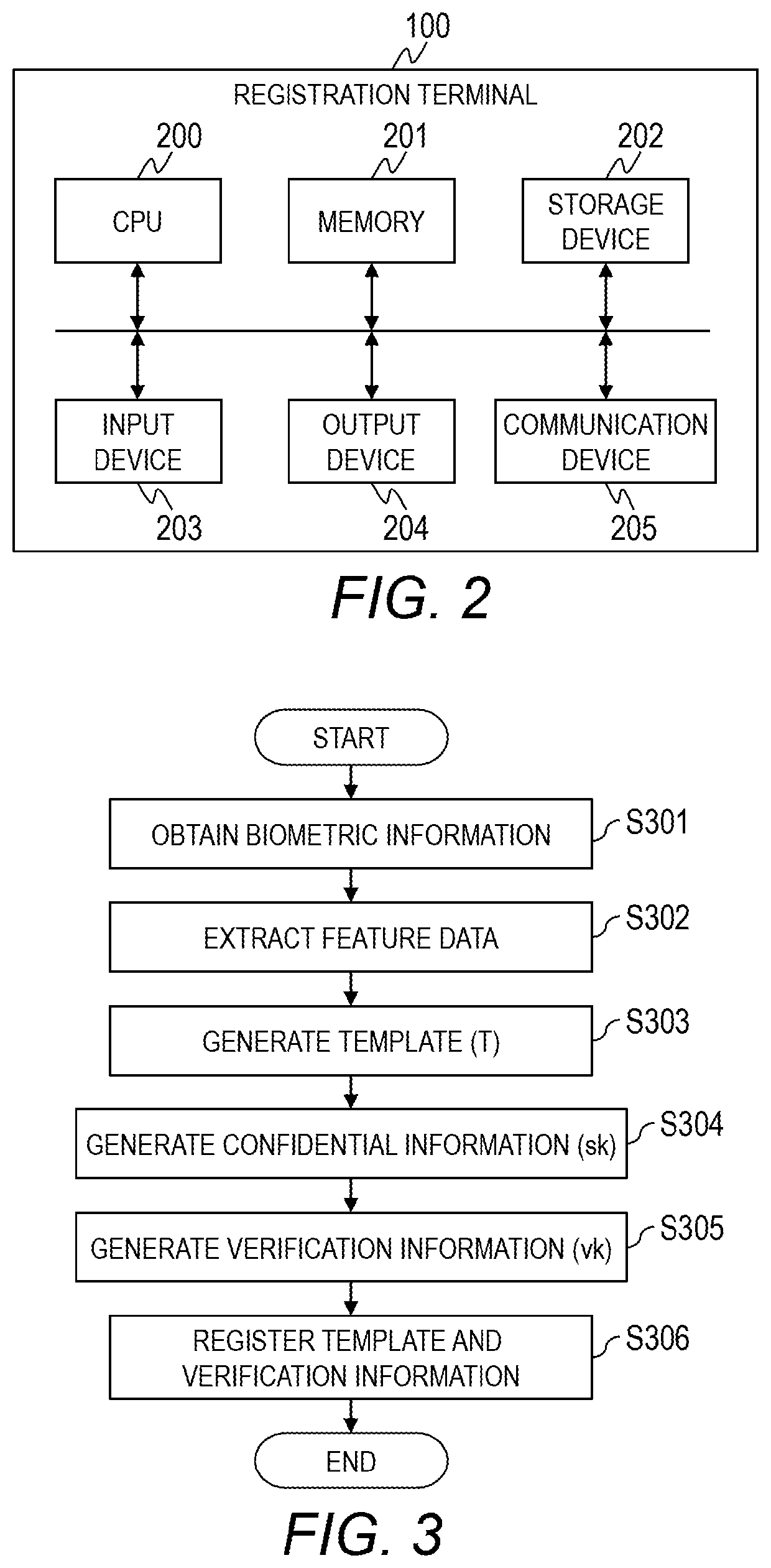
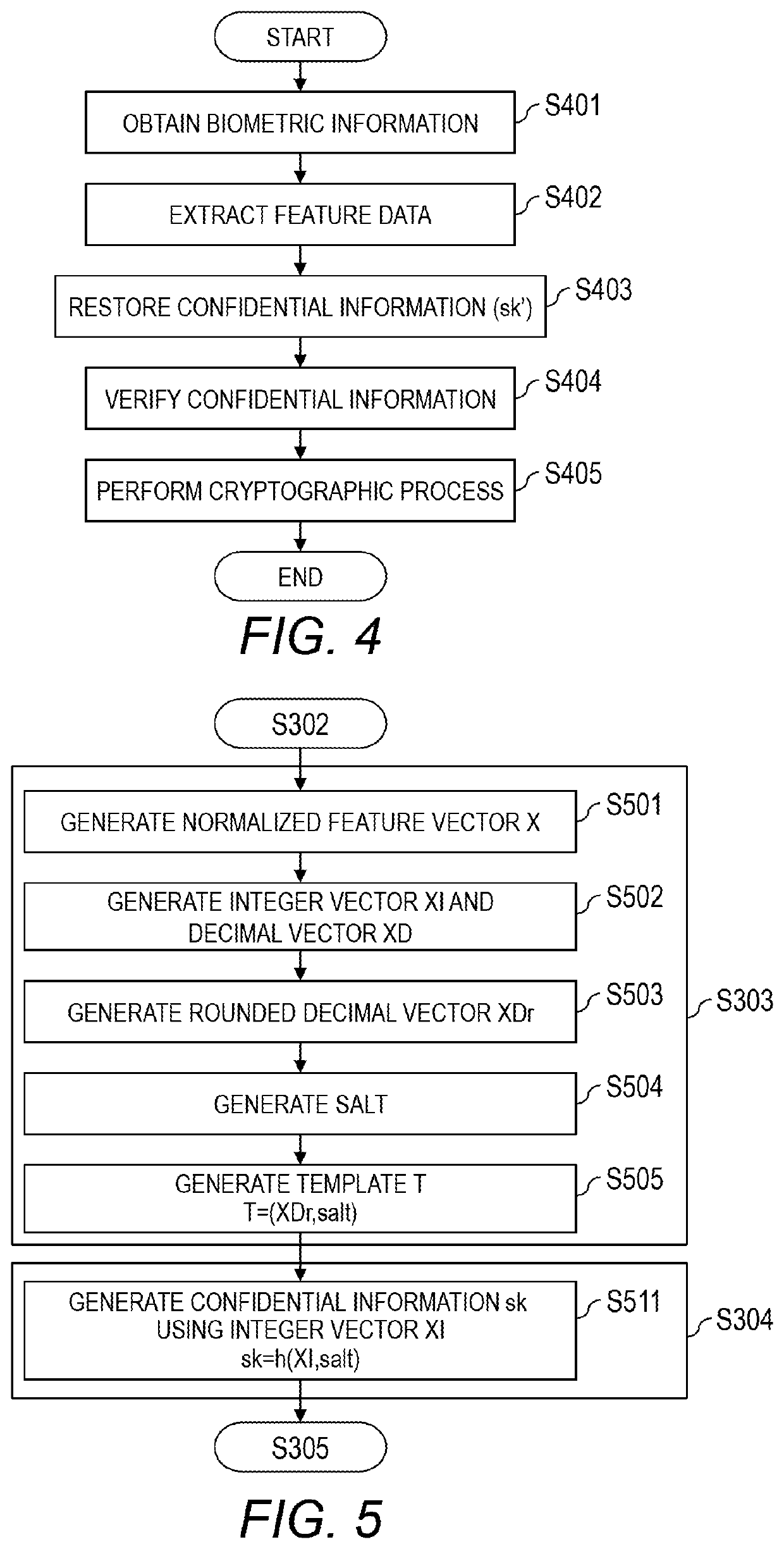
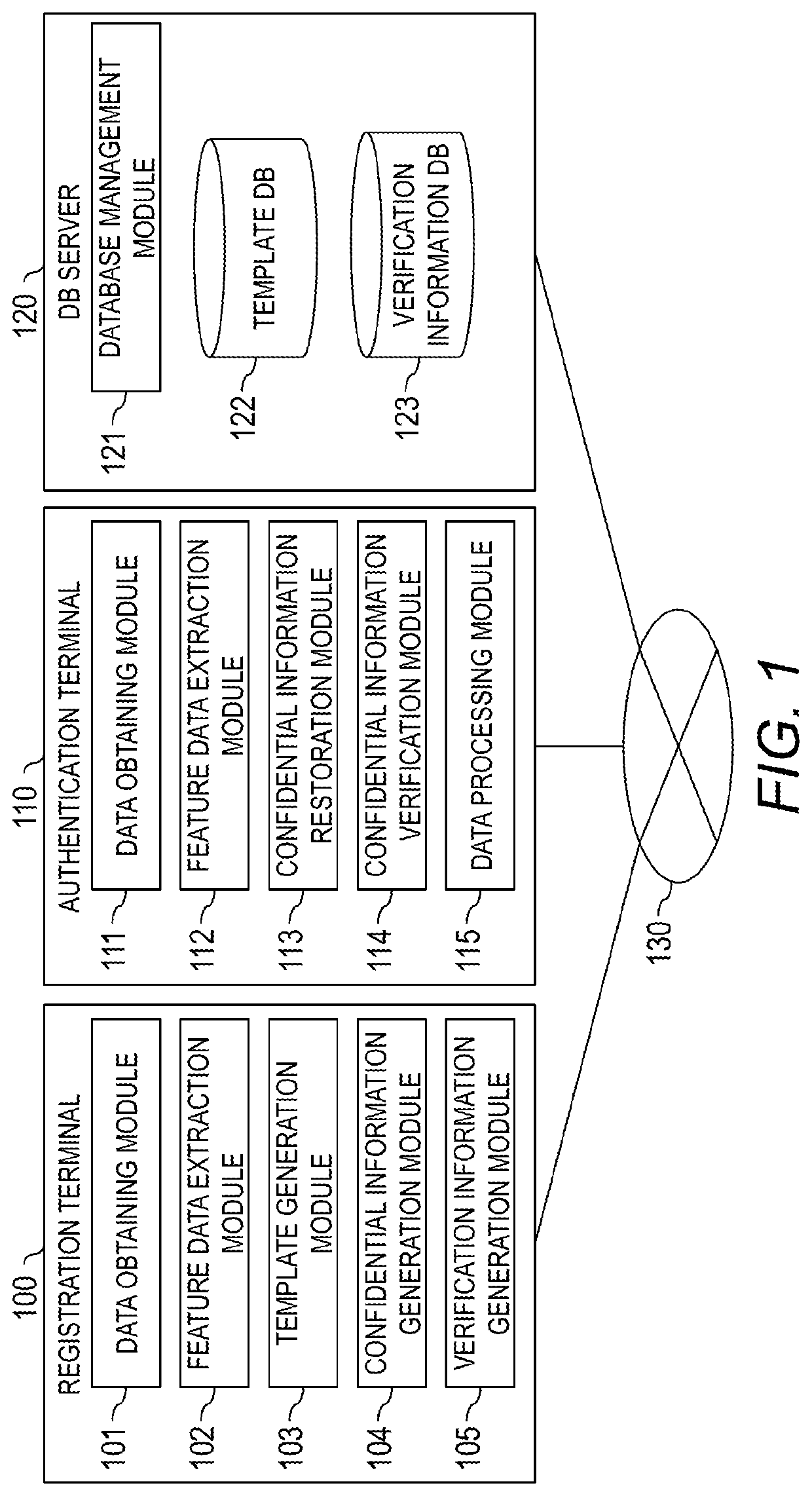
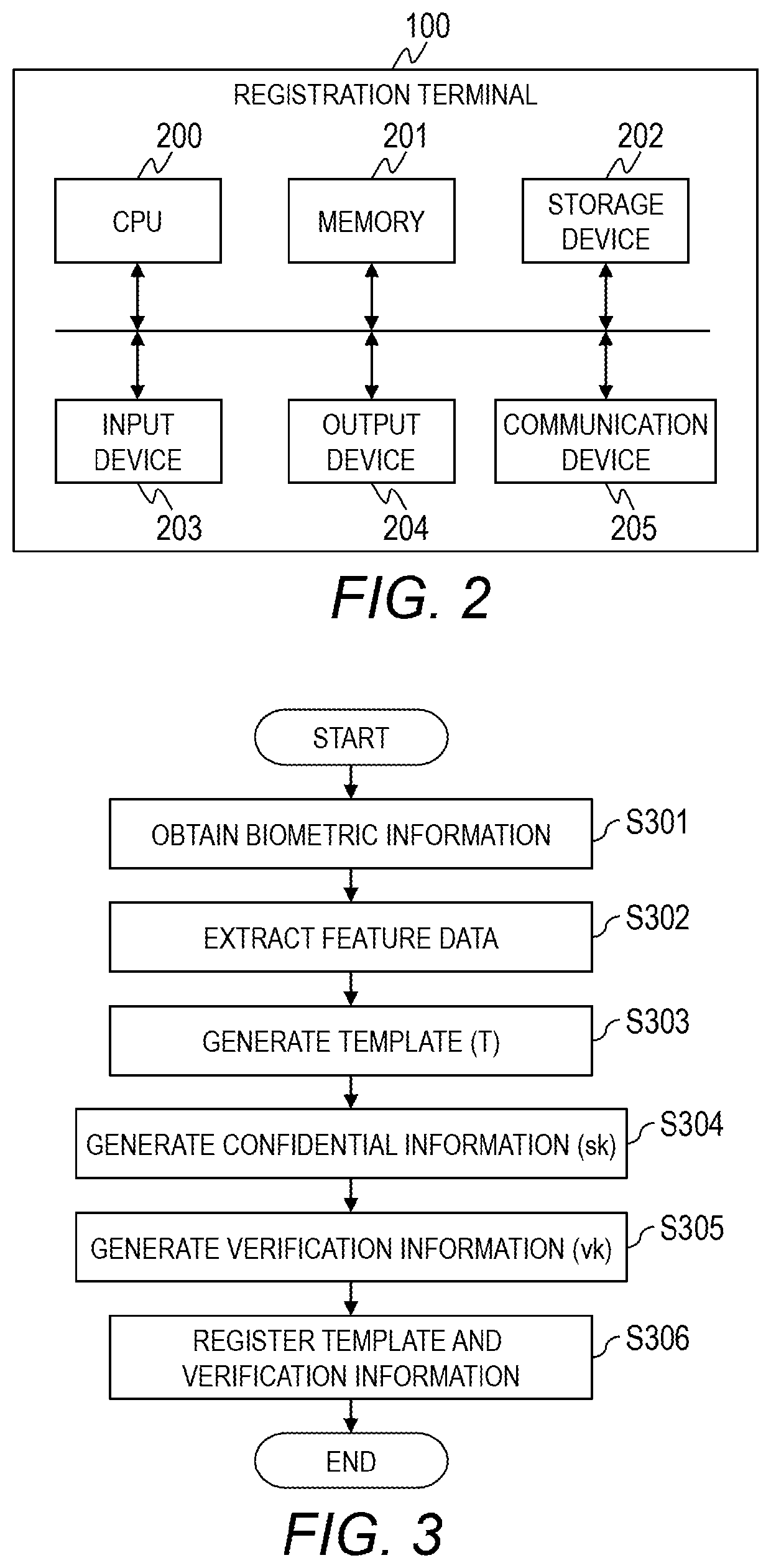
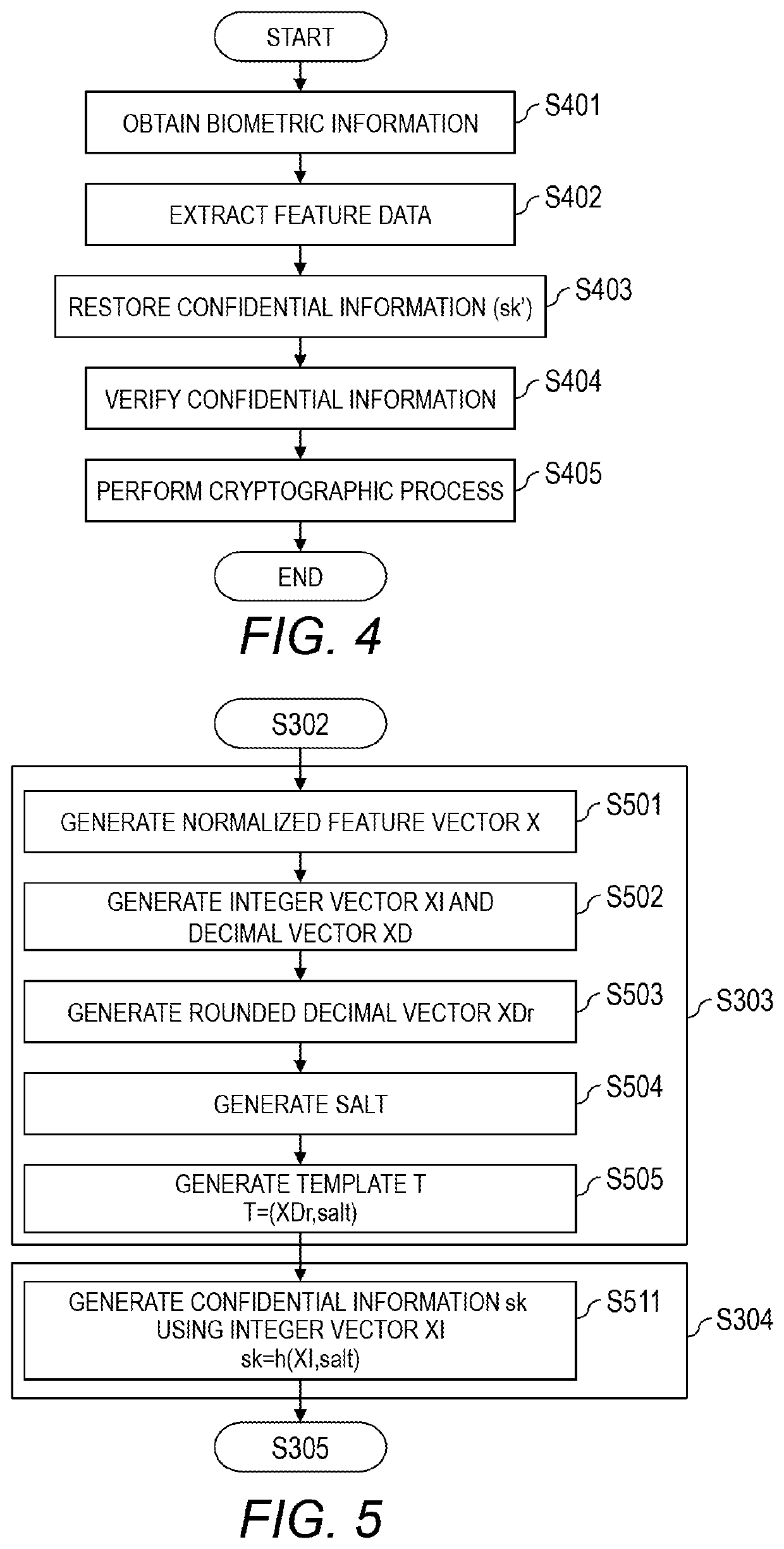
Computer system, verification method of confidential information, and computer
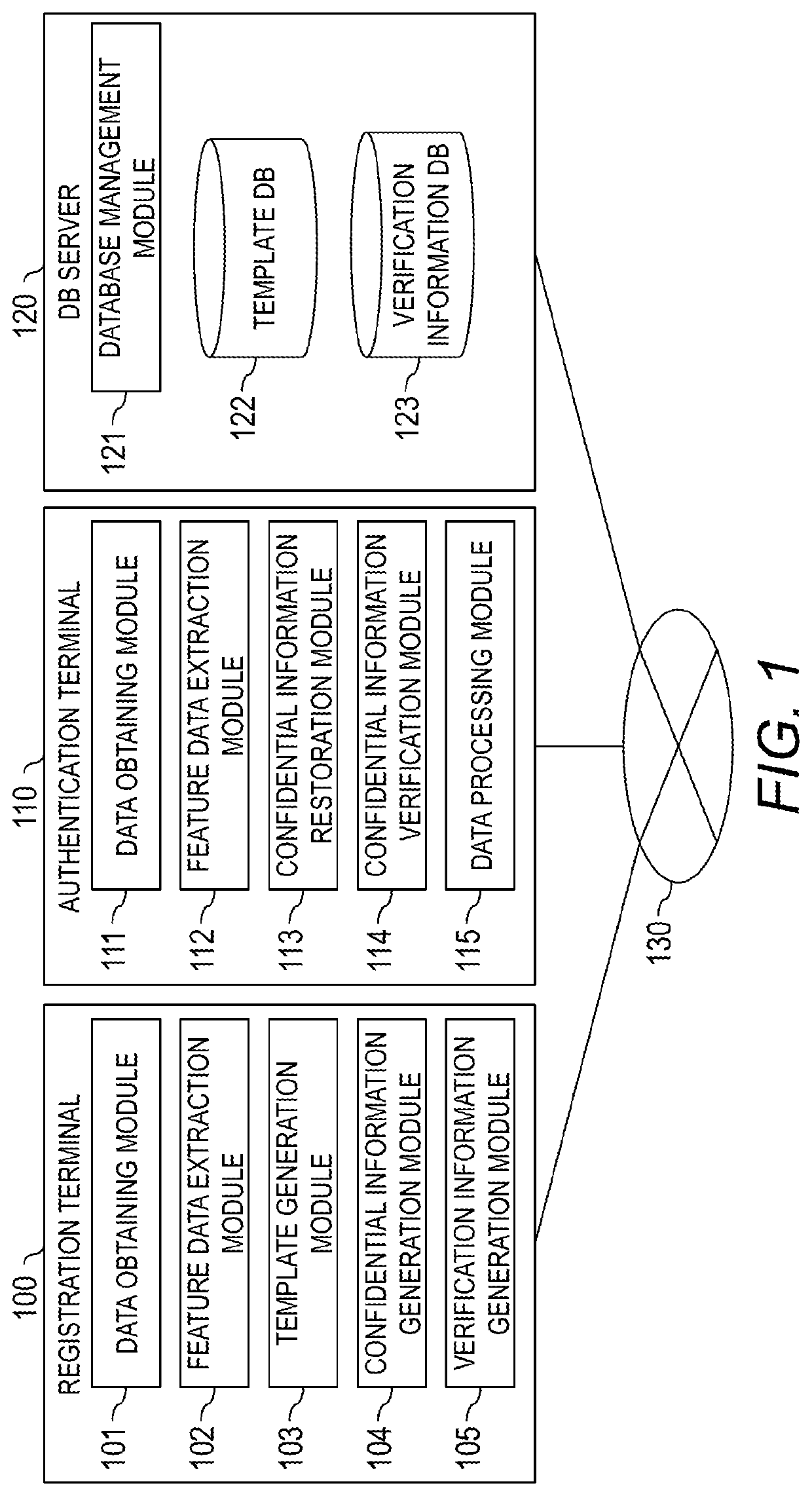
ActiveUS20200019685A1Reduce template sizeDifficult to estimateUser identity/authority verificationDigital data authenticationTemplate basedSecret code
A computer system comprising a computer, wherein the computer is configured to: generate feature data based on biometric information obtained from a user; generate error feature data indicating an error in the biometric information and stationary feature data indicating part other than the error in the biometric information, based on the feature data; generate a template based on the error feature data of the biometric information; generate first confidential information used for cryptographic process based on the stationary feature data of the biometric information, and generate first verification information based on the first confidential information.
Owner:HITACHI LTD
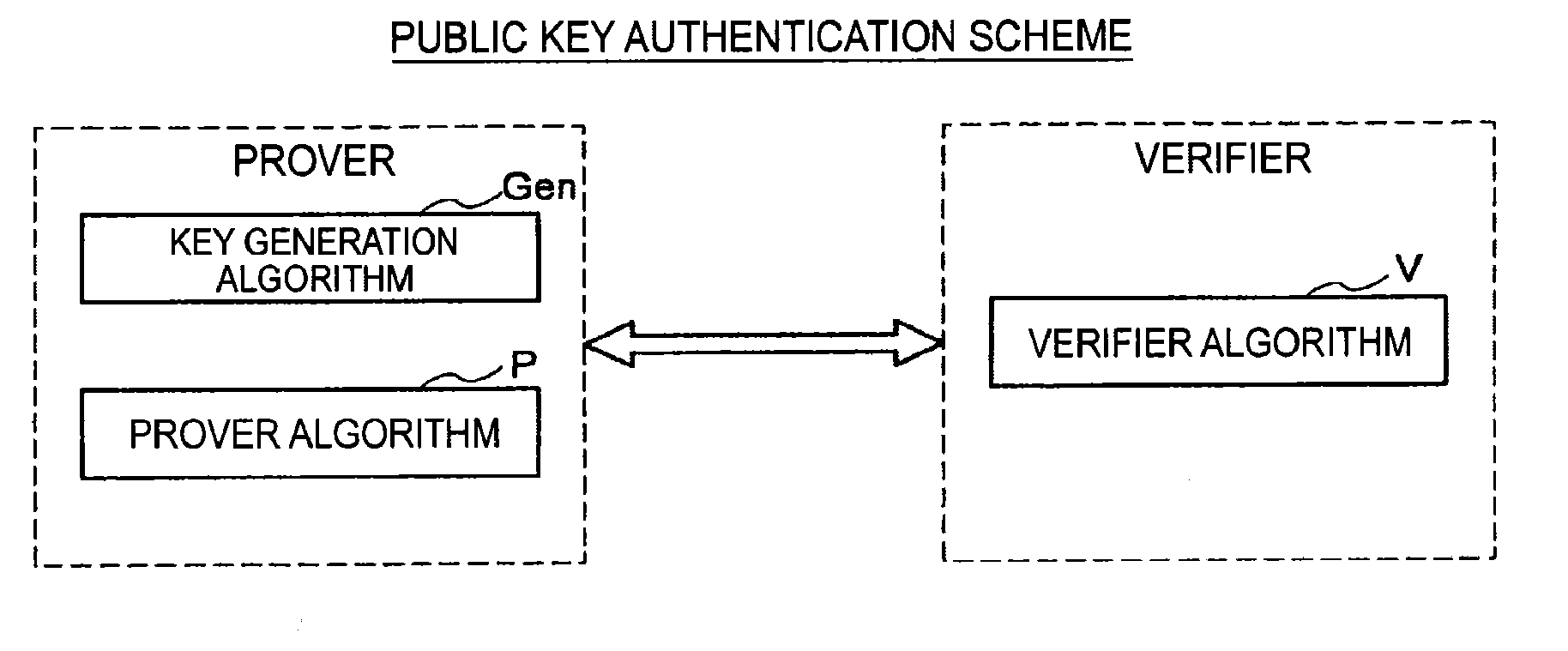
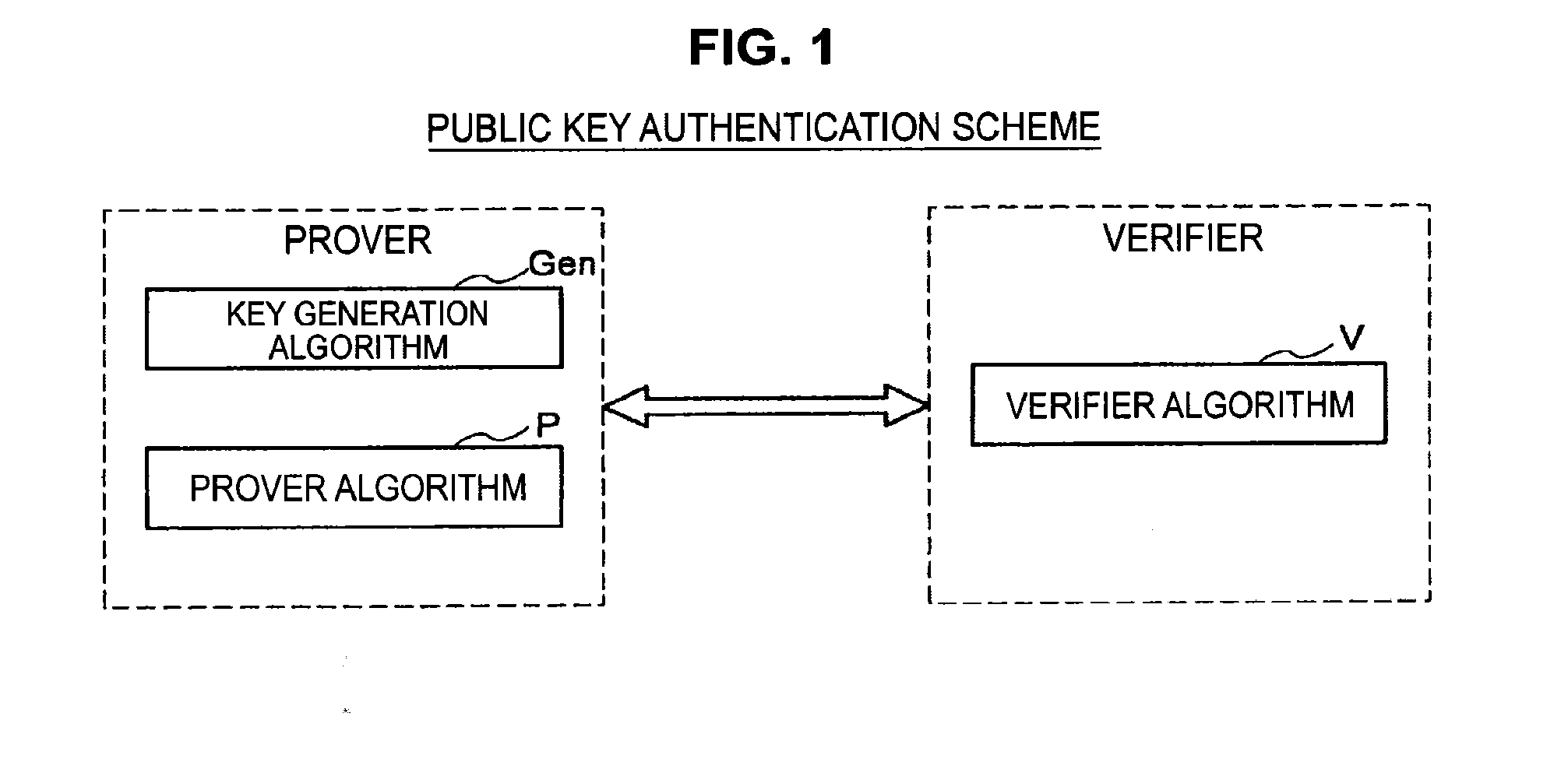
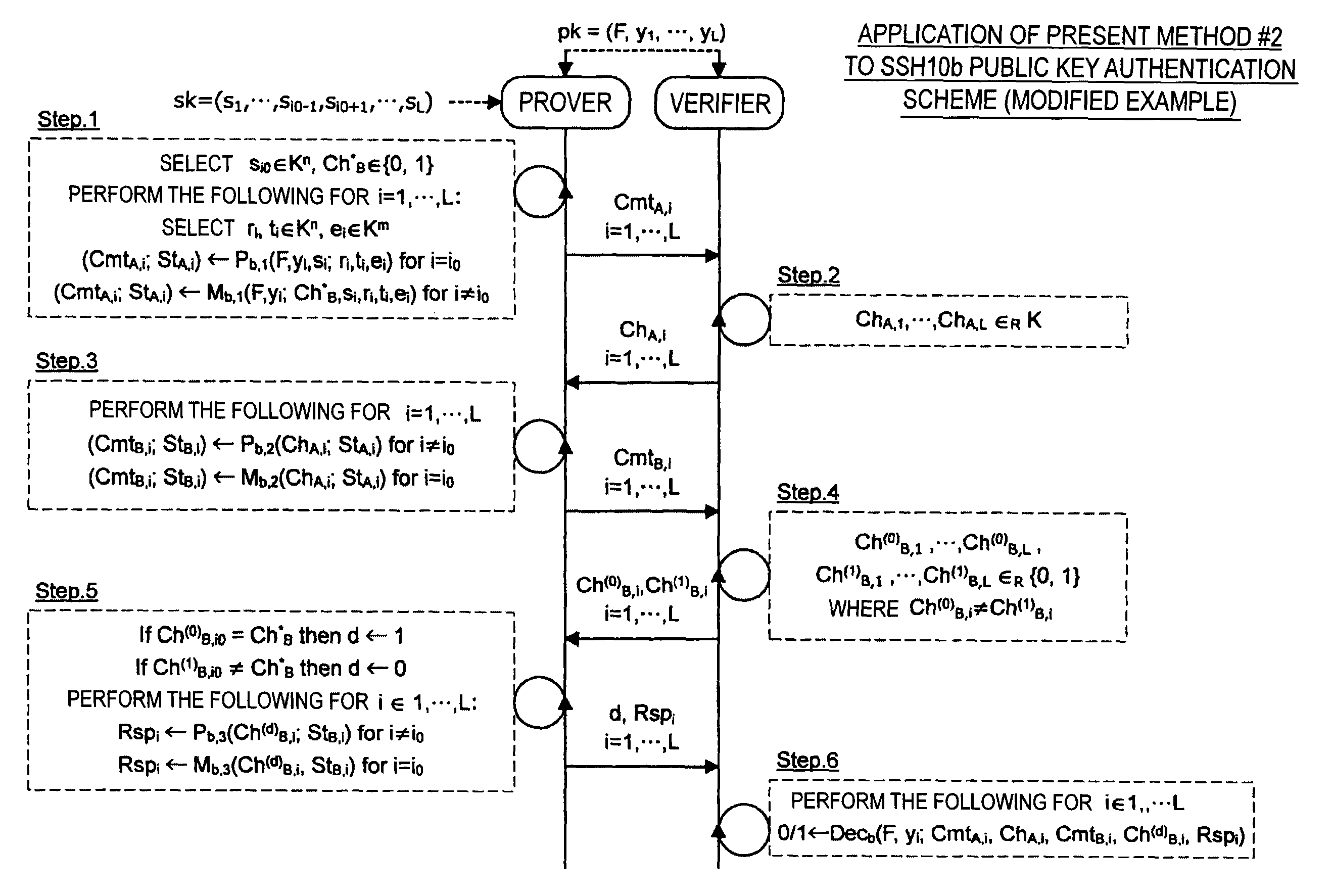
Authentication device, authentication method, and program
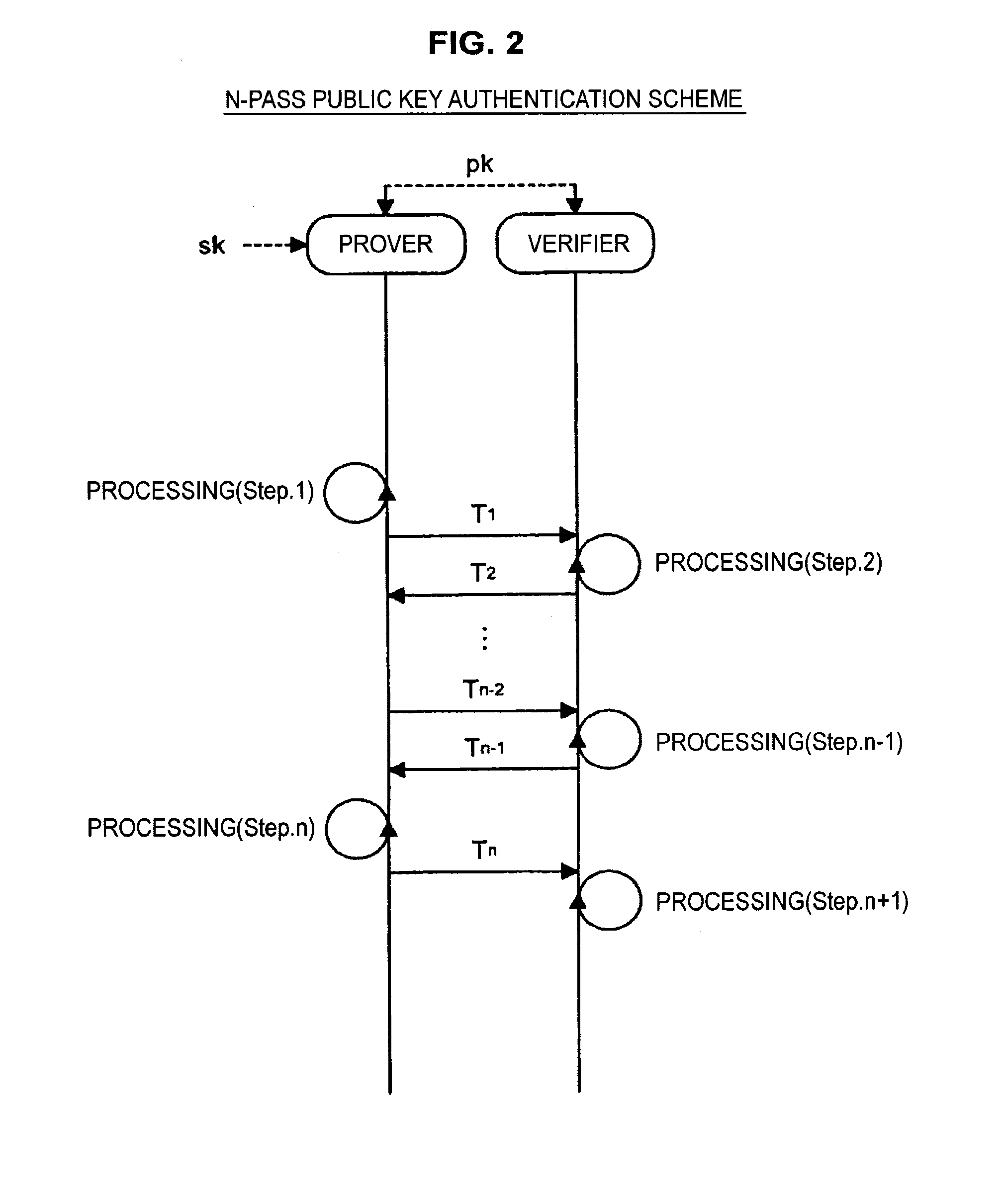
ActiveUS20150256342A1Sufficient level of securityKey distribution for secure communicationPublic key for secure communicationAuthentication
An authentication device includes circuitry that holds L (L≧2) secret keys si (i=1 to L) and L public keys yi that satisfy yi=F(si) with respect to a set F of multivariate polynomials of n-th order (n≧2). The circuitry also performs with a verifier, an interactive protocol for proving knowledge of (L−1) secret keys si that satisfy yi=F(si). The circuitry receives L challenges from the verifier, arbitrarily selects (L−1) challenges from the L challenges received. The circuitry also generates, by using the secret keys si, (L−1) responses respectively for the (L−1) challenges selected, and transmits the (L−1) responses generated.
Owner:SONY GRP CORP
Multiple access apparatus and method using power line
ActiveUS7865169B2Increase in telecommunication transmission capacitySufficient level of securityInterconnection arrangementsTransmission/receiving by adding signal to waveCode division multiple accessAC power
Provided is a telecommunication apparatus and a telecommunication method accomplishing a one-to-many, many-to-one, and many-to-many simultaneous accesses in a power line telecommunication of a code division multiple access (CDMA) by using an AC power line (including the ground).
Owner:SHONAN INSTITUTE OF TECHNOLOGY +2
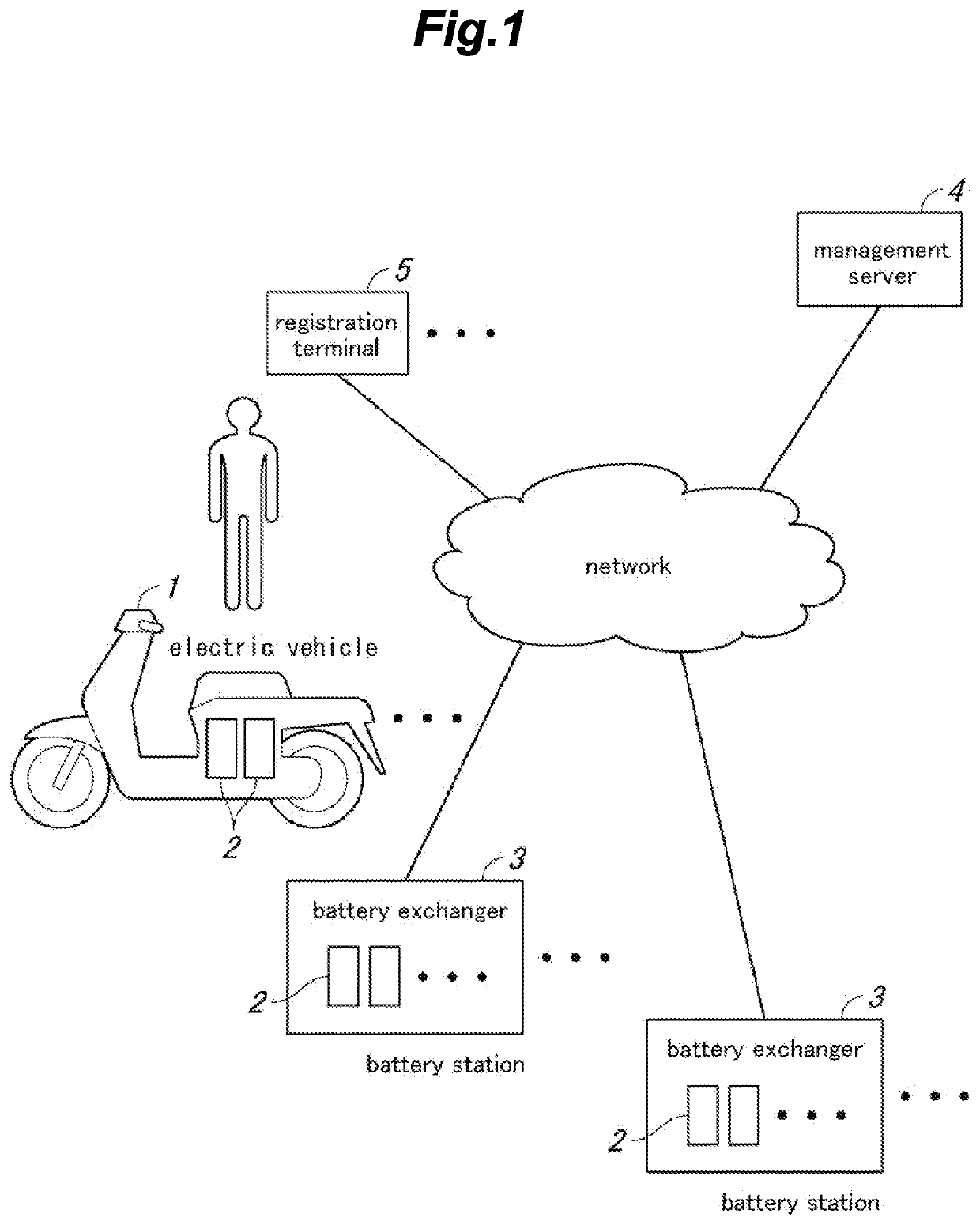
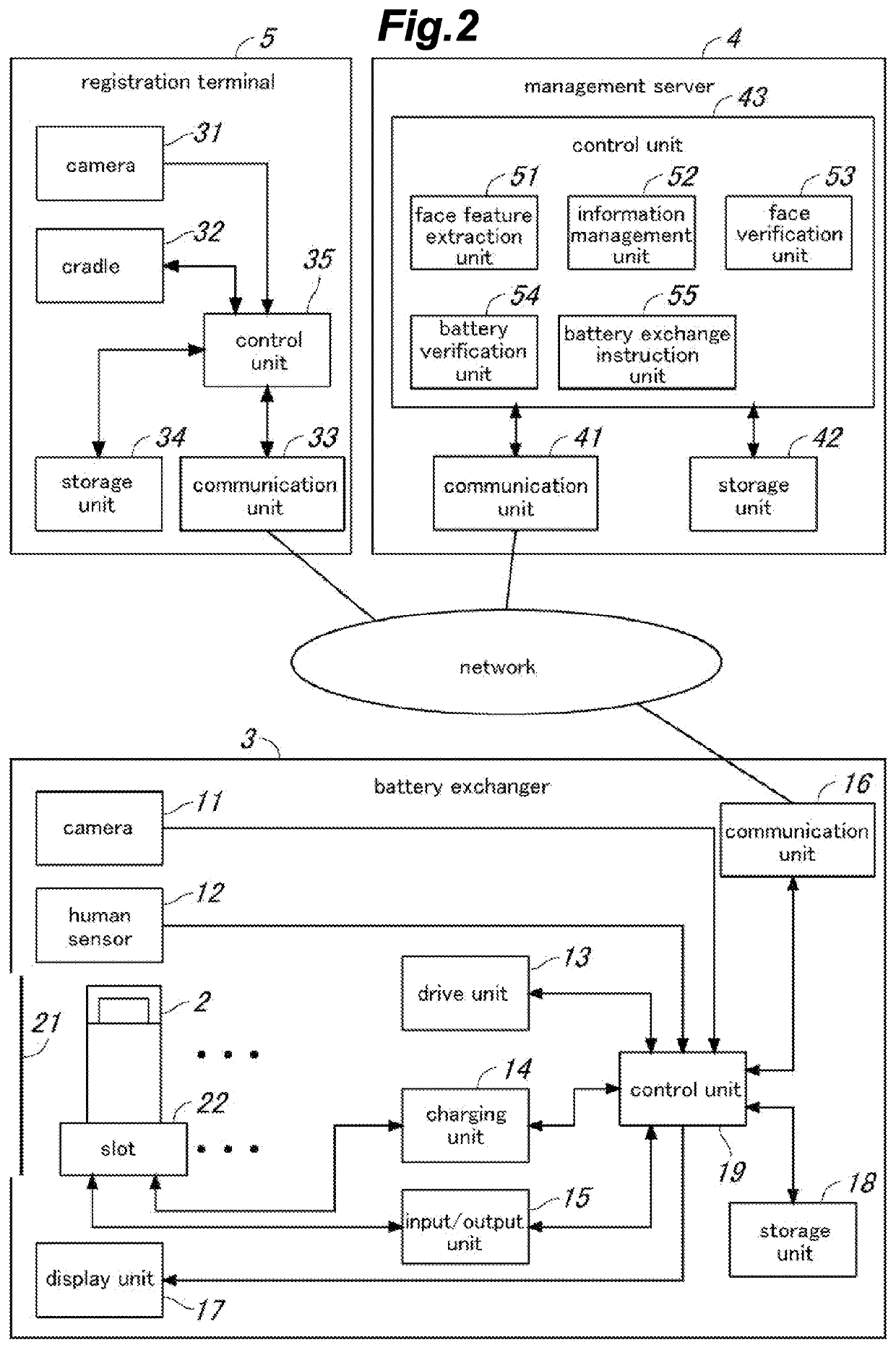
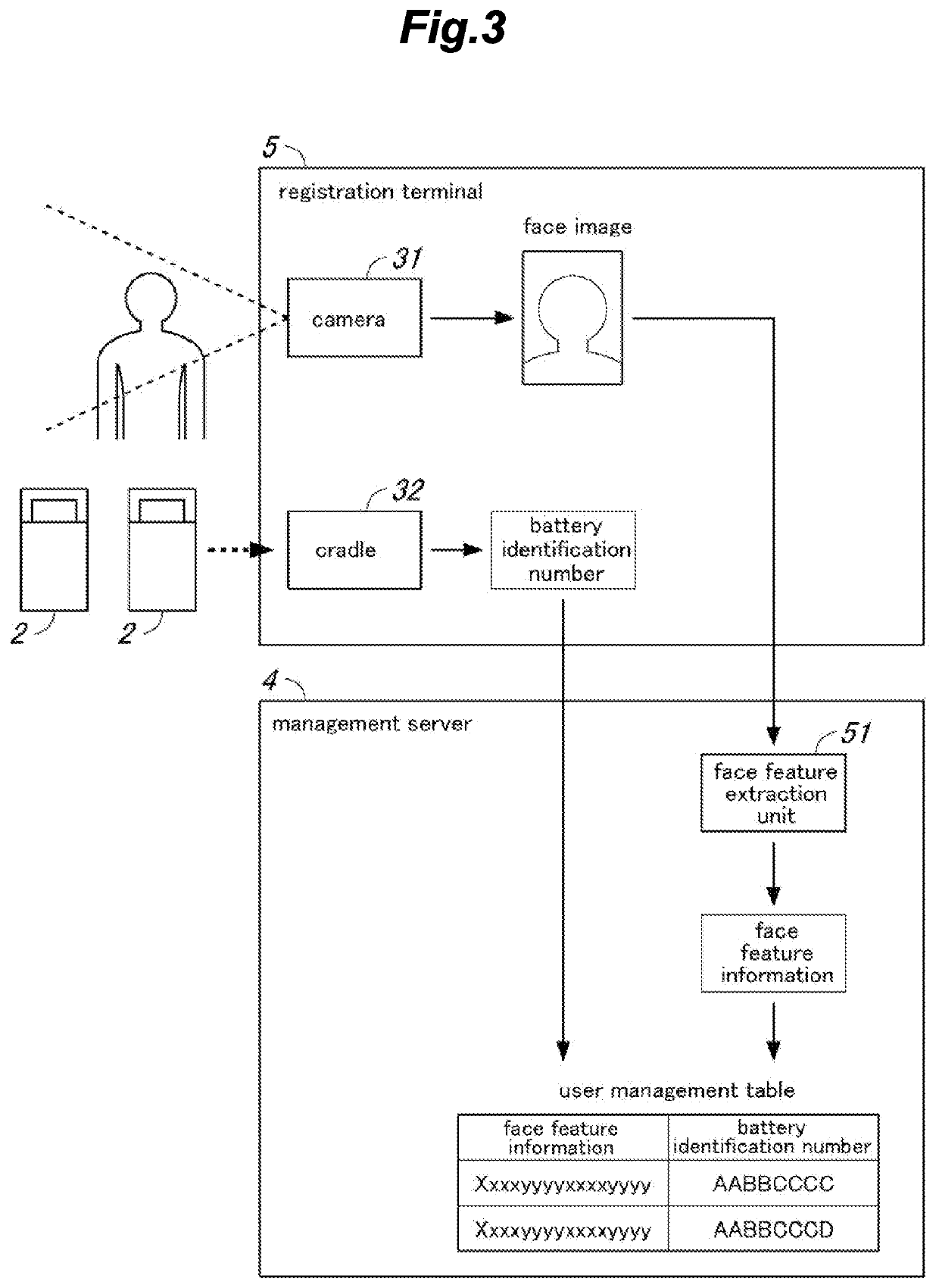
Battery management system and battery management method
PendingUS20210382971A1Sufficient level of securityMinimize effortBatteries circuit arrangementsData processing applicationsUser authenticationEngineering
The time and effort of the user when exchanging batteries can be minimized, and security can be sufficiently ensured in user authentication. A battery exchanger (3) is provided with a camera (11) for capturing an image of a visitor, and a management server (4) performs face verification to determine if the visitor is an authentic user according to face image information of the visitor acquired from the image captured by the camera. Based on the face verification result, the management server determines if battery exchange is permitted, and notifies the determination result to the battery exchanger. Further, based on identification information of the battery pack brought in by the visitor, the management server performs battery verification to determine if the battery pack brought in by the visitor is permitted to be exchanged, and based on the result of the battery verification, determines if the battery exchange should be permitted.
Owner:PANASONIC INTELLECTUAL PROPERTY MANAGEMENT CO LTD
Protection circuit for robot control device
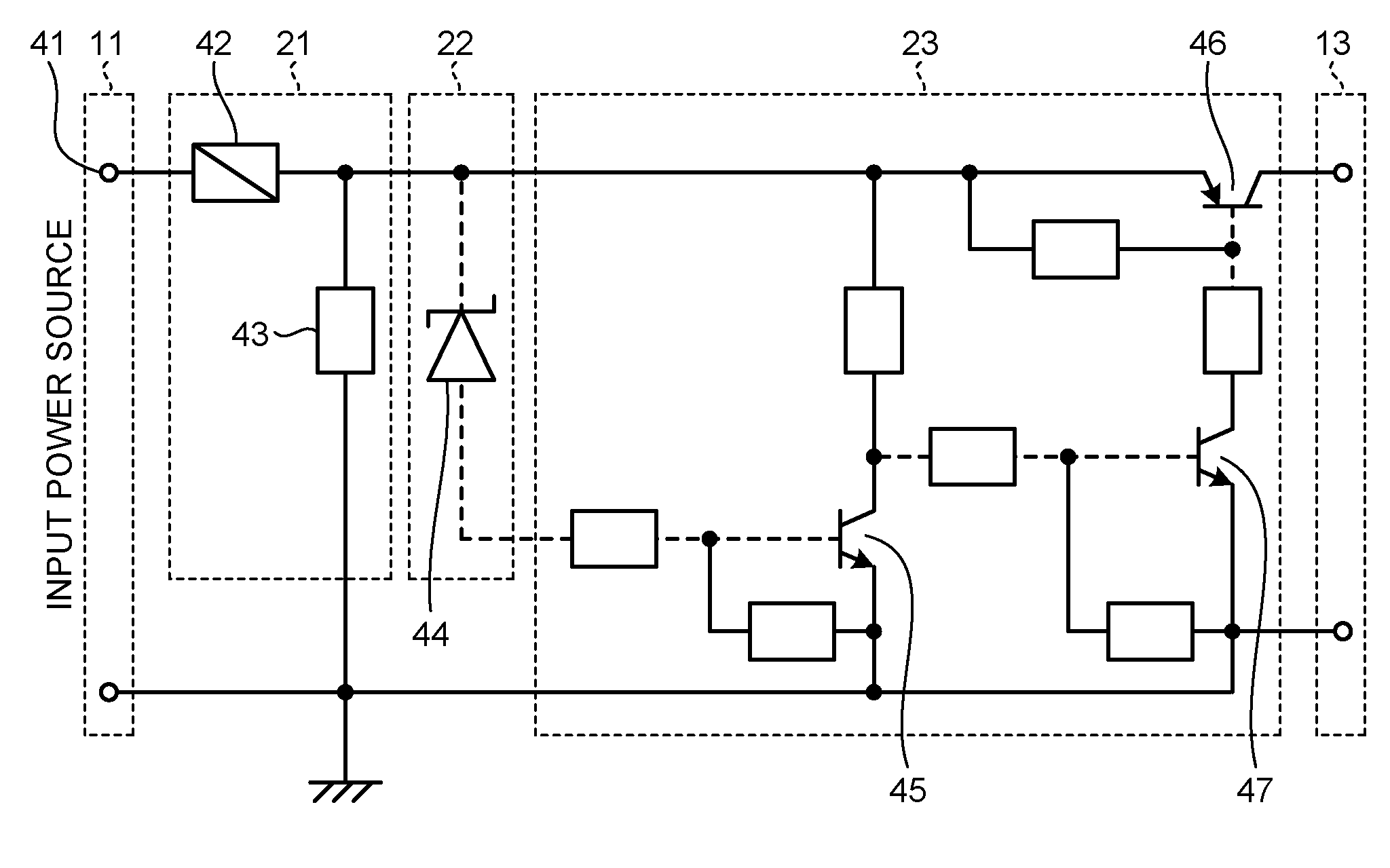
ActiveUS20160285254A1Simple circuit configurationSufficient level of securityDc network circuit arrangementsArrangements responsive to excess currentRobot controlAC power
A first current cut-off unit that cuts off a current input from a power-supply-voltage input terminal connected to an AC power source when a current value of the current exceeds a preset threshold, and a second current cut-off unit that cuts off a current output from the first current cut-off unit when a voltage value of a voltage applied from the power-supply-voltage input terminal exceeds a preset threshold are configured. A current cut-off element provided on a current path from the power-supply-voltage input terminal toward a DC output terminal, and a resistor that draws a current having passed through the current cut-off element toward a ground are provided as the first current cut-off unit.
Owner:MITSUBISHI ELECTRIC CORP
Image processing device and image processing system
ActiveUS8769666B2Improve processing efficiencyGuaranteed security levelDigital data processing detailsUser identity/authority verificationImaging processingComputer graphics (images)
An image processing device includes a plurality of printers (Pr1, Pr2, Pr3, Pr4, . . . ) and a plurality of client machines (PC1, PC2, PC3, PC4, PC5, . . . ). When requesting an image data processing to a printer other than the printer to which an image data processing has been requested firstly, the client machine checks the security level of the other printer to which the image data processing is to be requested before requesting the image data distribution processing to the other printer. When selecting another printer to which the image data distribution processing is to be requested, the security level in each printer is sufficiently considered.
Owner:SHARP KK
Recognition system for determining a position of a braking control device along a train
PendingUS20210197876A1Reduce misreadingReduce harmRailway vehiclesVehicle sub-unit featuresControl engineeringControl theory
A recognition system of a position of a mechatronic braking control device associated with a railway vehicle along a train is described. The recognition system includes a sustaining and fixing support installed on the railway vehicle, an identifying binary coding of the position along the train, and a mechatronic braking control device adapted to be fixed to the sustaining and fixing support and including an optical reading device arranged to detect the identifying binary coding. The mechatronic braking control device determines the position along the train according to the binary coding that is read by the optical reading device.
Owner:FAIVELEY TRANSPORT ITAL SPA
Method and system for securely updating a website
ActiveUS10474444B2Faster and easy to backup siteSufficient level of securityDigital data protectionWebsite content managementMulti siteApplication software
Owner:JOHNSTON JR KEVIN
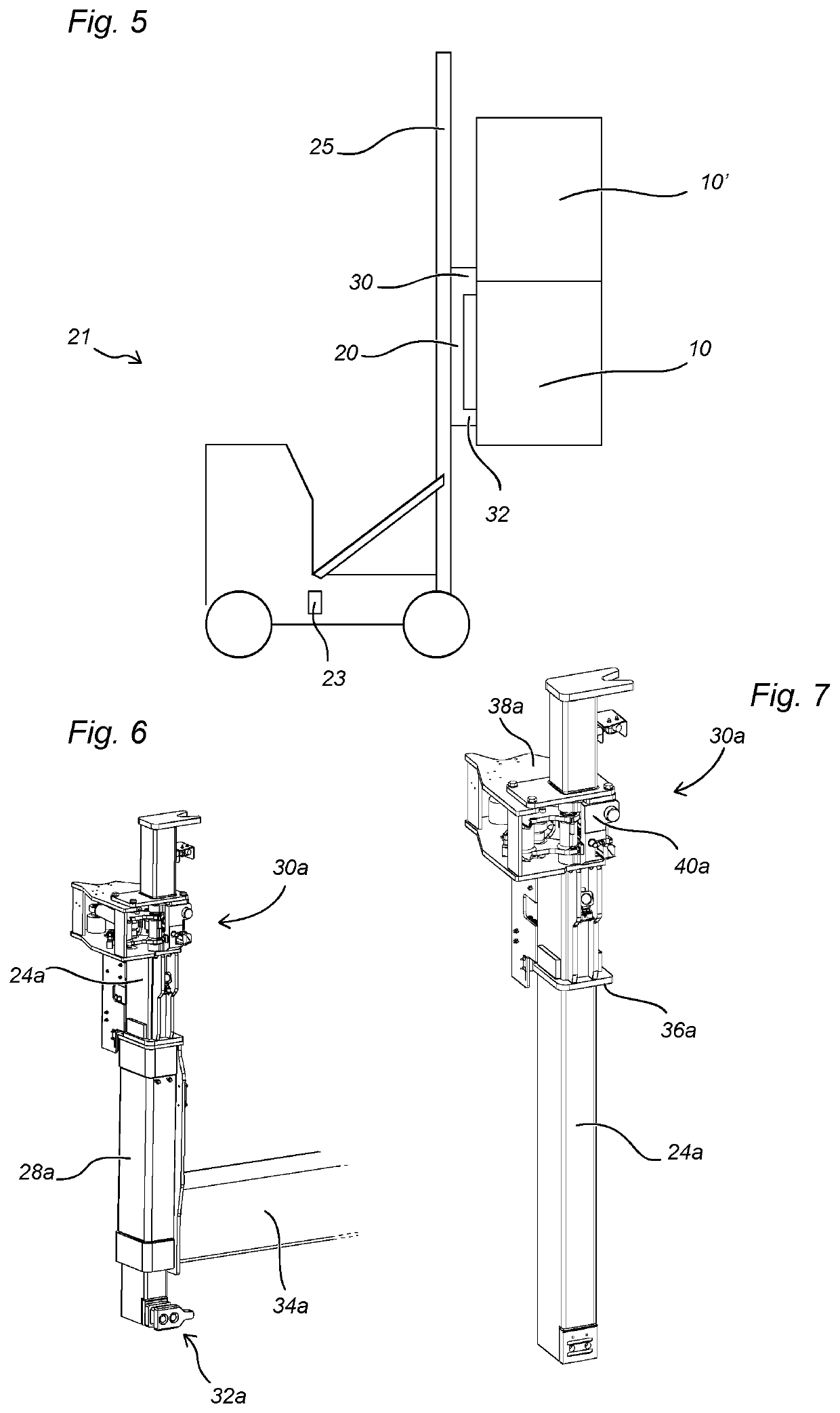
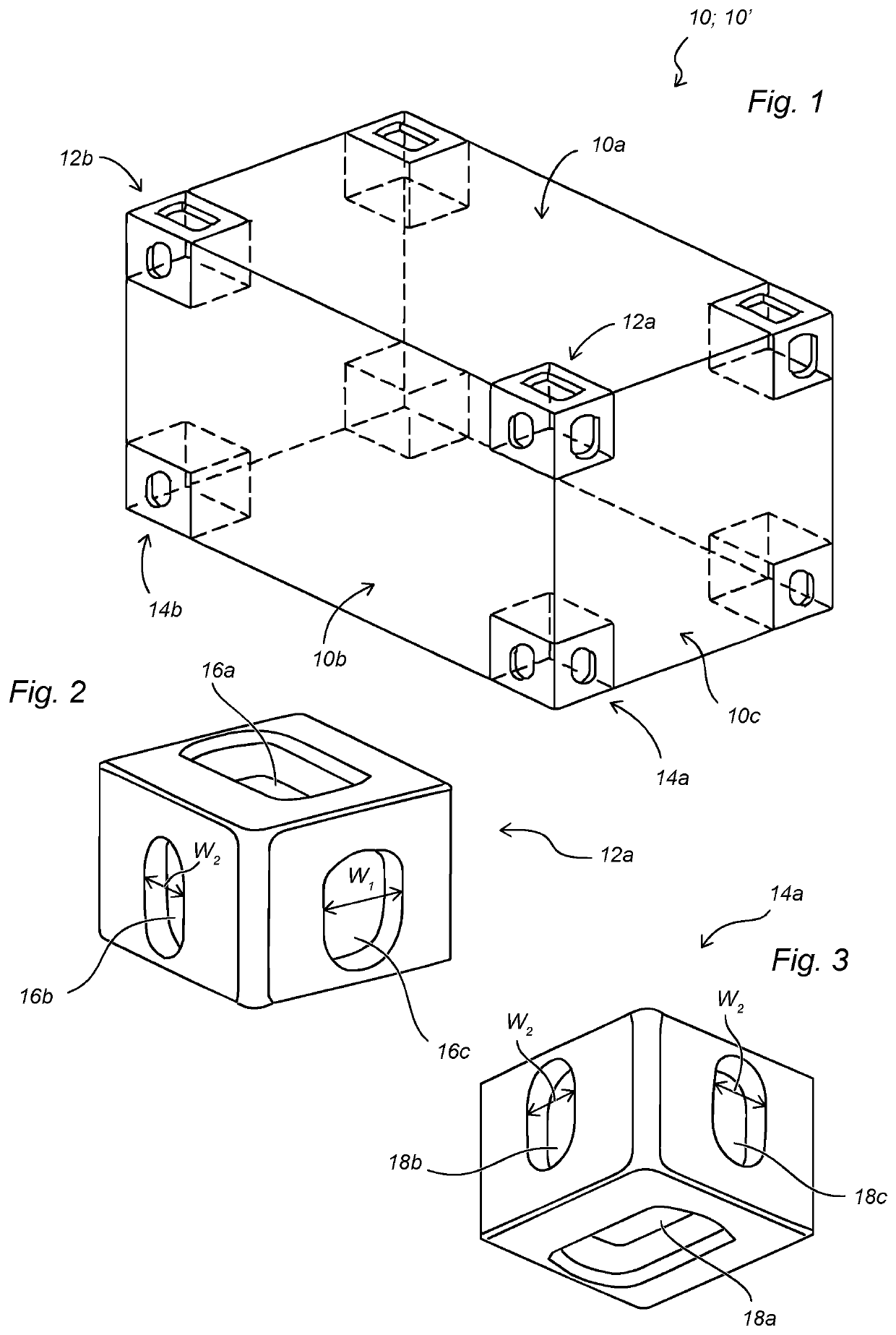
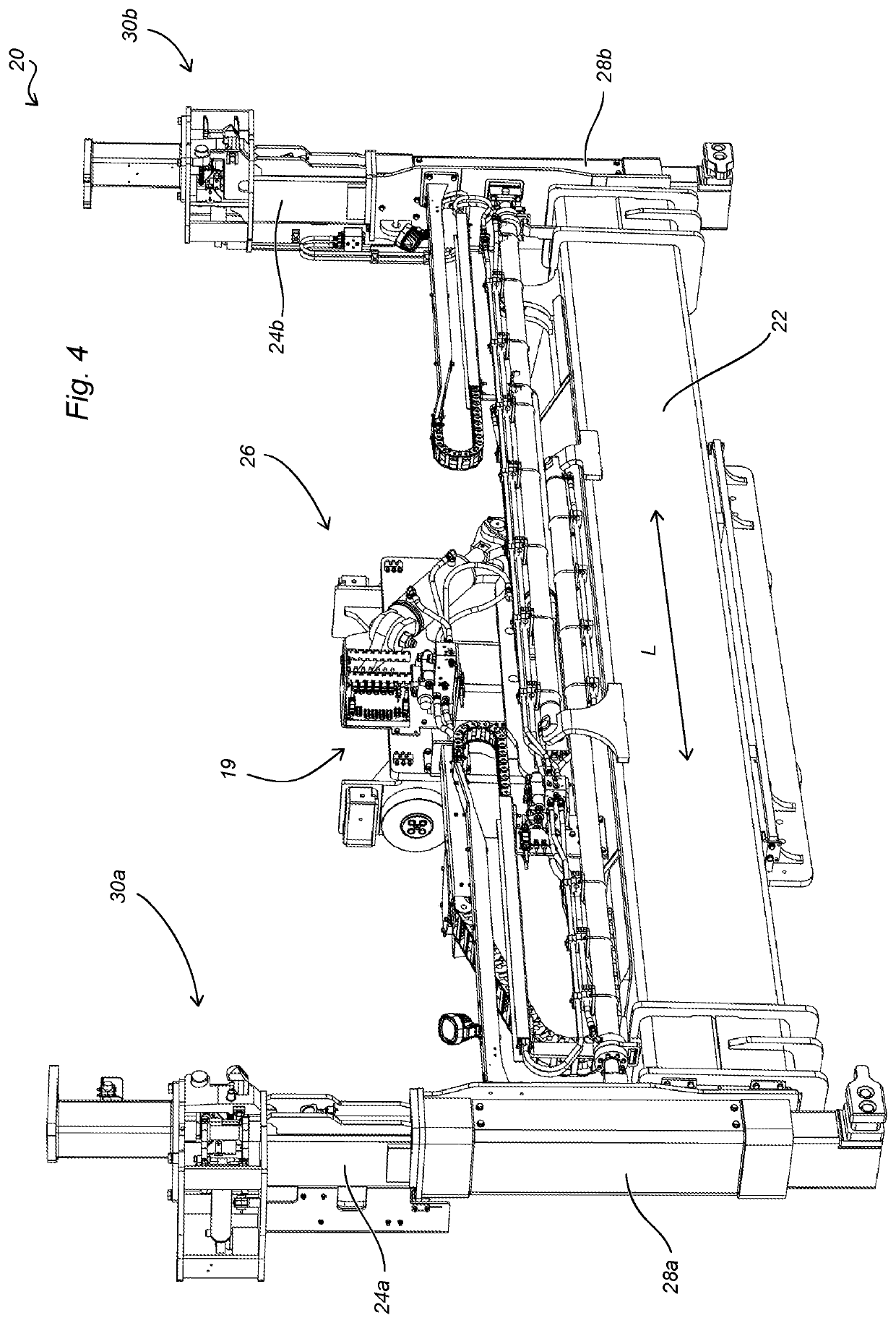
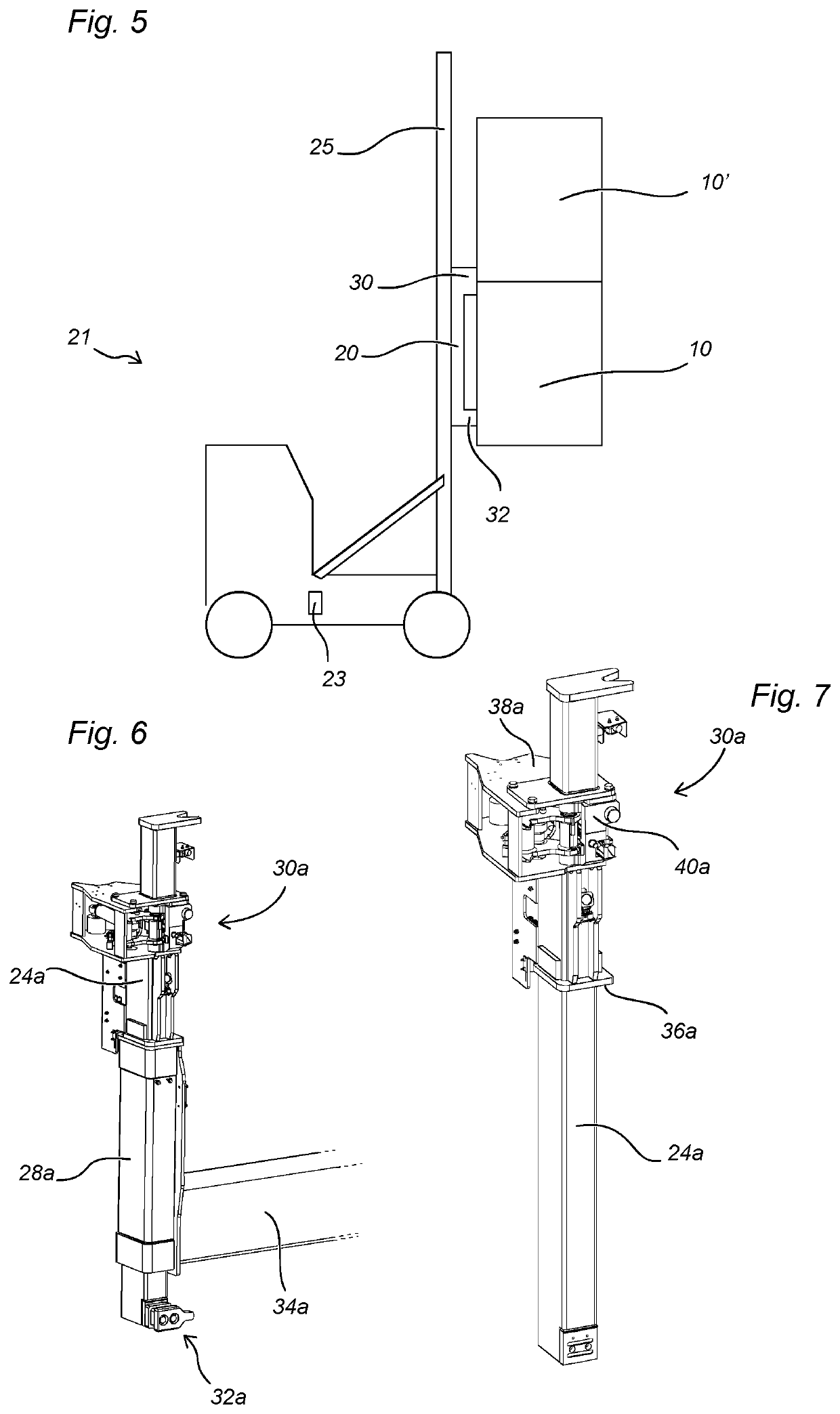
Side lift spreader for lifting intermodal containers, and method of operating a side lift spreader
ActiveUS10913642B2Reduce riskAvoid shockLifting devicesLoad-engaging elementsStructural engineeringMechanical engineering
A side lift spreader (20) for lifting an upper intermodal transport container (10′) and a lower intermodal transport container (10) stacked on each other comprises a container locking arrangement (30) arranged at a first longitudinal end of the spreader, the container locking arrangement (30) comprising an upper male lock insert configured to be connected to a bottom corner casting of the upper container (10′) and a lower male lock insert configured to be connected to a top corner casting of the lower container (10), wherein said container locking arrangement (30) comprises an indicator configured to provide an indication if an attempt is made to connect the lower male lock insert to the bottom corner casting of the upper container (10′).
Owner:ELME SPREADER
Authentication device, authentication method, and program
ActiveUS9076000B2Sufficient level of securityPublic key for secure communicationUser identity/authority verificationAuthentication
An authentication device includes circuitry that holds L (L≧2) secret keys si (i=1 to L) and L public keys yi that satisfy yi=F(si) with respect to a set F of multivariate polynomials of n-th order (n≧2). The circuitry also performs with a verifier, an interactive protocol for proving knowledge of (L−1) secret keys si that satisfy yi=F(si). The circuitry receives L challenges from the verifier, arbitrarily selects (L−1) challenges from the L challenges received. The circuitry also generates, by using the secret keys si, (L−1) responses respectively for the (L−1) challenges selected, and transmits the (L−1) responses generated.
Owner:SONY CORP
Side lift spreader for lifting intermodal containers, and method of operating a side lift spreader
ActiveUS20200079631A1Reduce riskAvoid shockLifting devicesLoad-engaging elementsStructural engineeringMechanical engineering
A side lift spreader (20) for lifting an upper intermodal transport container (10′) and a lower intermodal transport container (10) stacked on each other comprises a container locking arrangement (30) arranged at a first longitudinal end of the spreader, the container locking arrangement (30) comprising an upper male lock insert configured to be connected to a bottom corner casting of the upper container (10′) and a lower male lock insert configured to be connected to a top corner casting of the lower container (10), wherein said container locking arrangement (30) comprises an indicator configured to provide an indication if an attempt is made to connect the lower male lock insert to the bottom corner casting of the upper container (10′).
Owner:ELME SPREADER
Computer system, verification method of confidential information, and computer
ActiveUS11227037B2Sufficient level of securitySmall sizeUser identity/authority verificationDigital data authenticationTemplate basedSecret code
A computer system comprising a computer, wherein the computer is configured to: generate feature data based on biometric information obtained from a user; generate error feature data indicating an error in the biometric information and stationary feature data indicating part other than the error in the biometric information, based on the feature data; generate a template based on the error feature data of the biometric information; generate first confidential information used for cryptographic process based on the stationary feature data of the biometric information, and generate first verification information based on the first confidential information.
Owner:HITACHI LTD
Automatic fill control technique
ActiveUS10838436B2Prevent overflowSufficient level of securityLevel controlFlow control using electric meansControl engineeringLiquid storage tank
A pump includes a signal processor that receives signaling containing information about a low level of a liquid sensed in an appliance reservoir to be supplied to an appliance that uses the liquid to dispense a flavored beverage, and also about when the appliance reservoir is refilled based upon an indication that forms part of an appliance reservoir refill level calibration procedure programmed by an appliance user; and determines corresponding signaling containing information about automatically refilling the liquid in the appliance reservoir, based upon the signaling received.
Owner:FLOW CONTROL LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com