Numerical control machine communication interface security protection method and device
A technology of safety protection device and numerical control machine tool, which is applied to electrical components, transmission systems, etc., can solve the problems of DNC network security with potential safety hazards, potential safety hazards, and the lack of supervision and auditing of internal communication of DNC processing network, so as to ensure normal and safe operation. , The effect of protecting the security of communication data and preventing abnormal data from flowing into the CNC system
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment 1
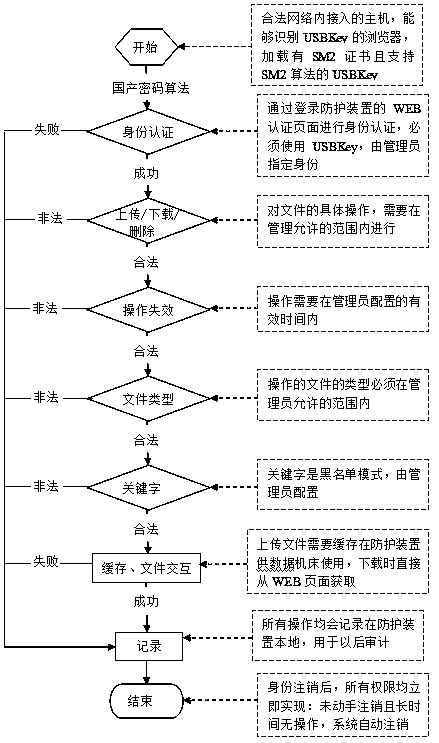
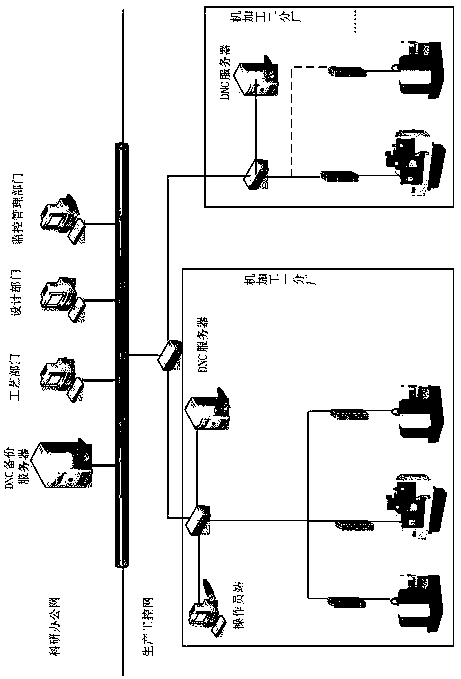
[0027] A security protection method for a communication interface of a numerical control machine tool, the specific method is as follows: monitoring the access of peripheral interfaces in the numerical control machine tool that require access control; devices that need to access the numerical control machine tool are accessed through the access monitoring; The specific control methods include: verifying the identity of the access device, and only allowing access after passing the identity verification; uploading files are provided to CNC machine tools through the cache of access monitoring; downloading files is obtained through the WEB page of access monitoring; all operations on access devices Record and support the audit of USB operation records.
[0028] Any device or host that interacts with the CNC machine tool needs to complete the identity authentication before it can operate the data within the scope of authority, and the identity authentication is based on the domestic...
specific Embodiment 2
[0030] On the basis of specific embodiment 1, the control method also includes the following one, a combination of two or more and any combination sequence:
[0031] Identify the access operation authority of the access device; verify the access time limit of the access device; identify the access file keyword blacklist of the access device; identify the file type authority of the access operation; the access time limit refers to allowing the identity The age of the user's access, and / or the age of certain access rights.
[0032] like figure 1 Shown is a schematic flow chart of an aspect of one embodiment of the present invention.
[0033] Permissions are divided according to users, and user permissions are invalid; it supports the control of file types, the control of file upload, download and deletion, and the control of file content keywords.
specific Embodiment 3
[0034] On the basis of the specific embodiment 1 or 2, the specific method for authenticating the access device is as follows: performing identity authentication by logging into the WEB authentication page of access control, and performing identity authentication using a specified identity authentication medium.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com