A method to solve the problem of data privacy disclosure in multi-party computing
A technology of data privacy and multi-party computing, applied in the field of information security, can solve problems such as data privacy leakage, achieve the effect of solving data privacy leakage and ensuring scalability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0017] The implementation of the present invention will be described in detail below in conjunction with the drawings and examples.
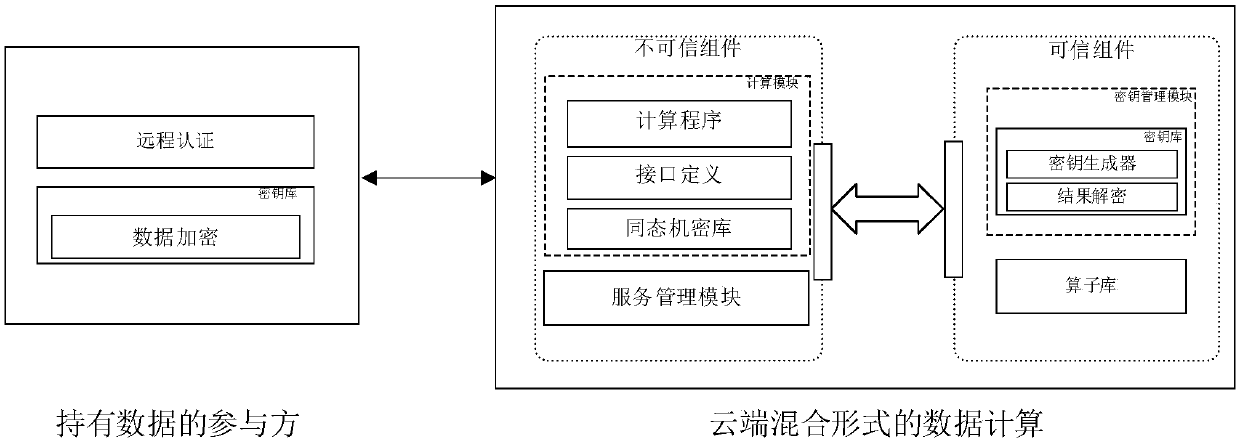
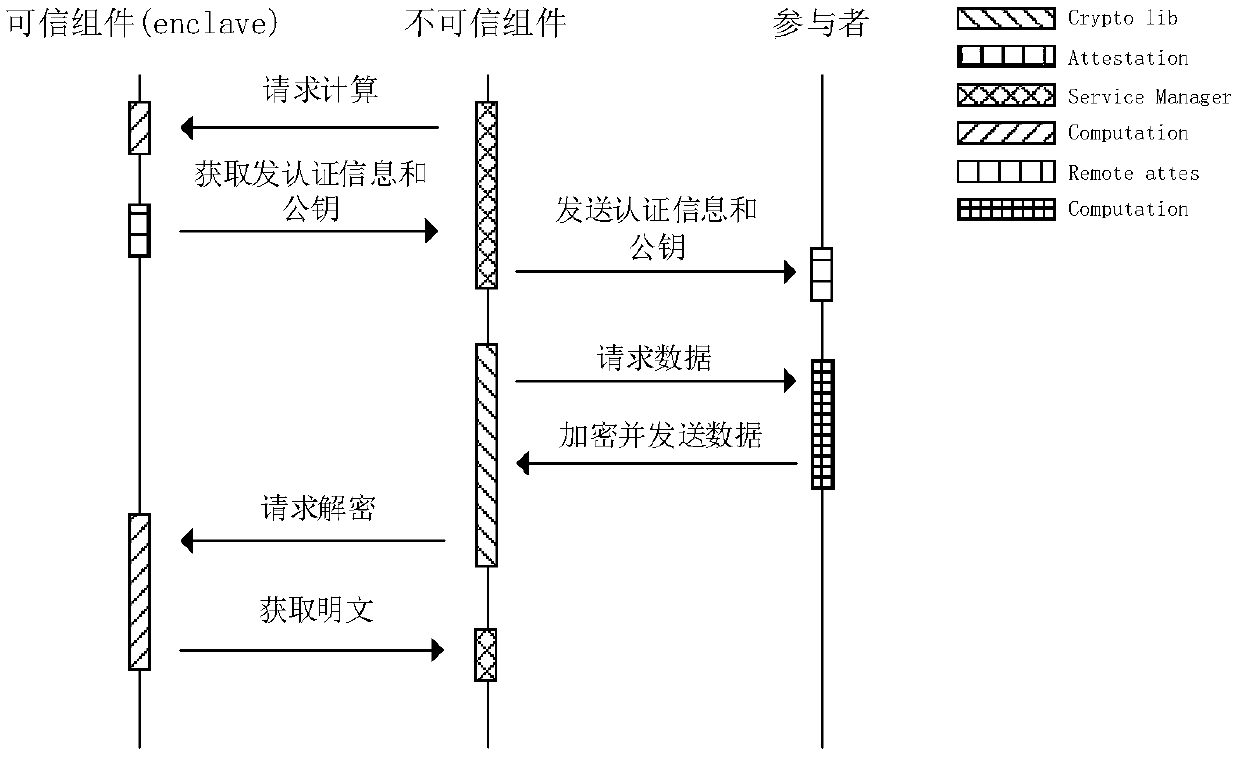
[0018] The present invention solves the problem of data privacy leakage in multi-party computing based on a hybrid computing method realized by combining a hardware-level trusted execution environment and partial homomorphic encryption technology. The entire technical solution can be divided into three parts (taking IntelSGX's hardware-level trusted environment as an example):
[0019] 1) Data analysis and calculation based on mixed forms. This part completes the data analysis and calculation of multiple participants. This part mainly consists of two parts, one part runs in the enclave of Intel SGX (enclave refers to an isolated runtime environment in SGX), and it mainly consists of a key management module and a basic operator module. The key management module It is mainly responsible for creating a public-private key pair in the enclave, and ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com