A blockchain-based identity authentication method and a blockchain-based identity authentication system
A technology of identity authentication and identity authentication results, which is applied in the field of identity authentication methods and systems based on blockchain, can solve the problems of poor security of unified authentication technology, and achieve high security, time-saving, and fast calculation effects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
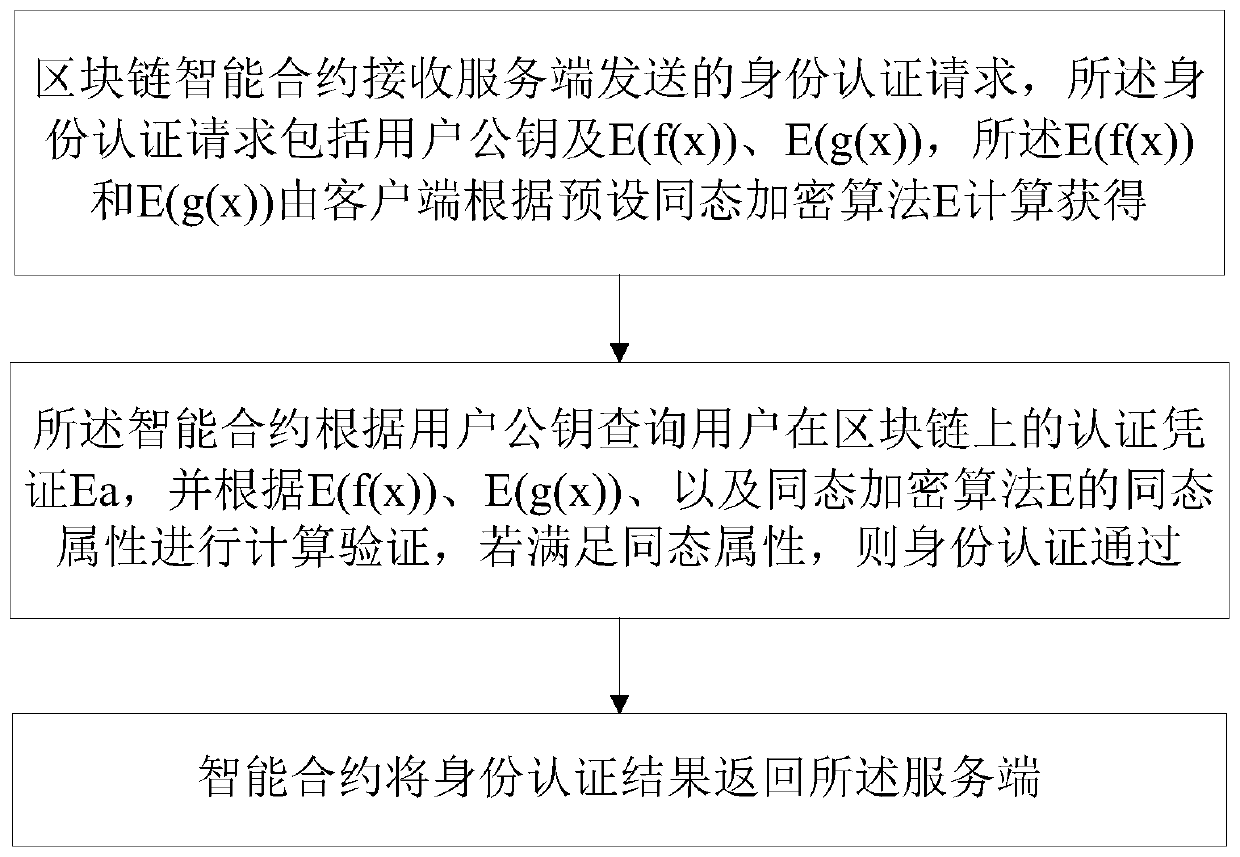
[0050] see figure 1 As shown, the technical solution of this embodiment adopts block chain to carry out unified identity authentication, and its steps are:
[0051] The client receives the preset password x input by the user, and calculates E(f(x)) and E(g(x)) locally according to the preset homomorphic encryption algorithm E;
[0052] The client sends a service request to the server, the service request includes the user public key and E(f(x)), E(g(x)), and the matters to be handled by the client; where f(x)=H 1 (x), g(x)=H 2 (x), where the function H 1 with H 2 are two different one-way hash functions, and H 1 with H 2 The output digits are the same, and the output length is above 256bit;
[0053] The server receives the service request sent by the client, and performs identity authentication through the block chain, and responds to the service request of the client according to the identity authentication result returned by the block chain;
[0054] Specifically, the...
Embodiment 2
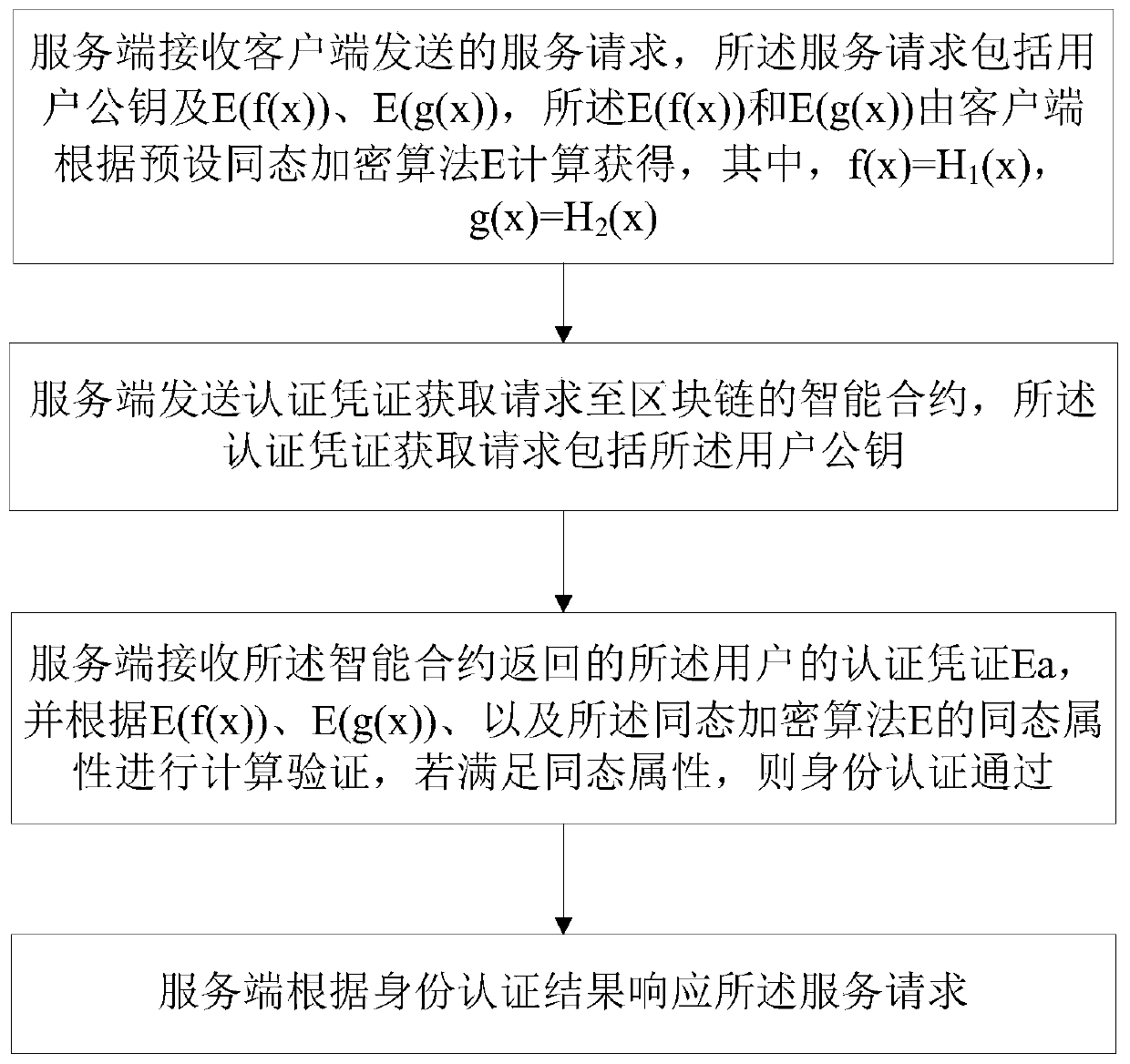
[0074] In this example, see image 3 As shown in , after the server obtains the authentication certificate from the blockchain, it performs identity authentication on the authentication server of the server.
[0075]Specifically, the server receives the service request sent by the client, the service request includes the user public key and E(f(x)), E(g(x)), the E(f(x)) and E( g(x)) is calculated by the client according to the preset homomorphic encryption algorithm E, where f(x)=H 1 (x), g(x)=H 2 (x), where the function H 1 with H 2 are two different one-way hash functions, and H 1 with H 2 The output digits are the same, and the output length is above 256 bits; the server sends an authentication credential acquisition request to the smart contract of the blockchain, and the authentication credential acquisition request includes the user public key; the smart contract searches for the user authentication credential through the user public key And return to the server; t...
Embodiment 3
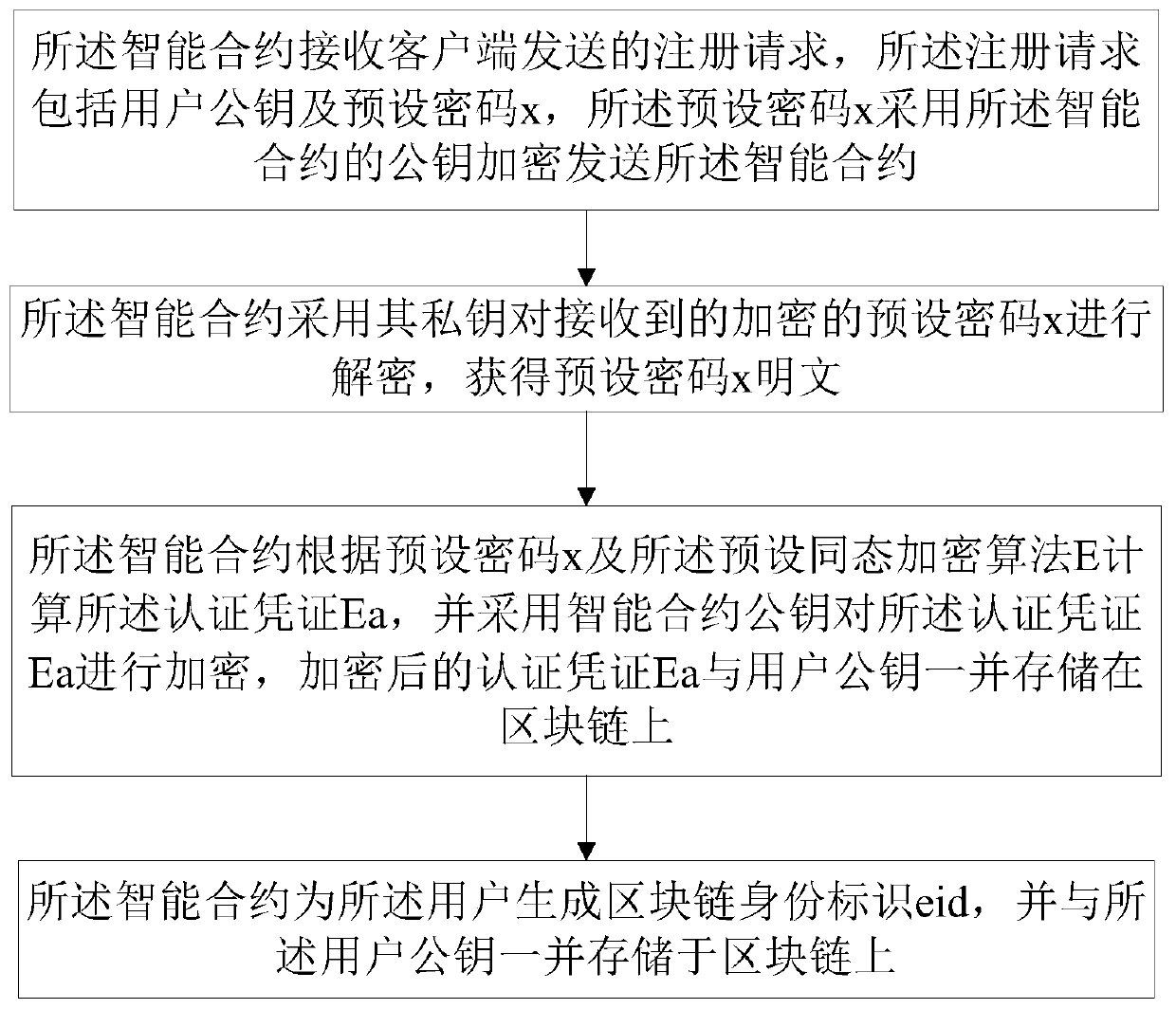
[0078] This embodiment provides a blockchain-based identity authentication system, including a client, a server, and a blockchain. The identity authentication system uses the identity authentication method in Embodiment 1 for unified identity authentication. I won't repeat them here.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com