System and methods for validating and performing operations on homomorphically encrypted data
a technology of homomorphic encryption and data validation, applied in the field of homomorphic encryption data validation and performing operations on confidential data, can solve the problem of not solving the possible misuse of sensitive data by the service provider itsel
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0026]Although financial applications form the basis of the inventive examples discussed herein, the inventive techniques discussed have application to other forms of confidential data. In this context, the different devices and parties involved in data acquisition, storage, and analysis may be reconsidered as appropriate for the type of confidential data being processed.
[0027]Homomorphic Encryption / Decryption
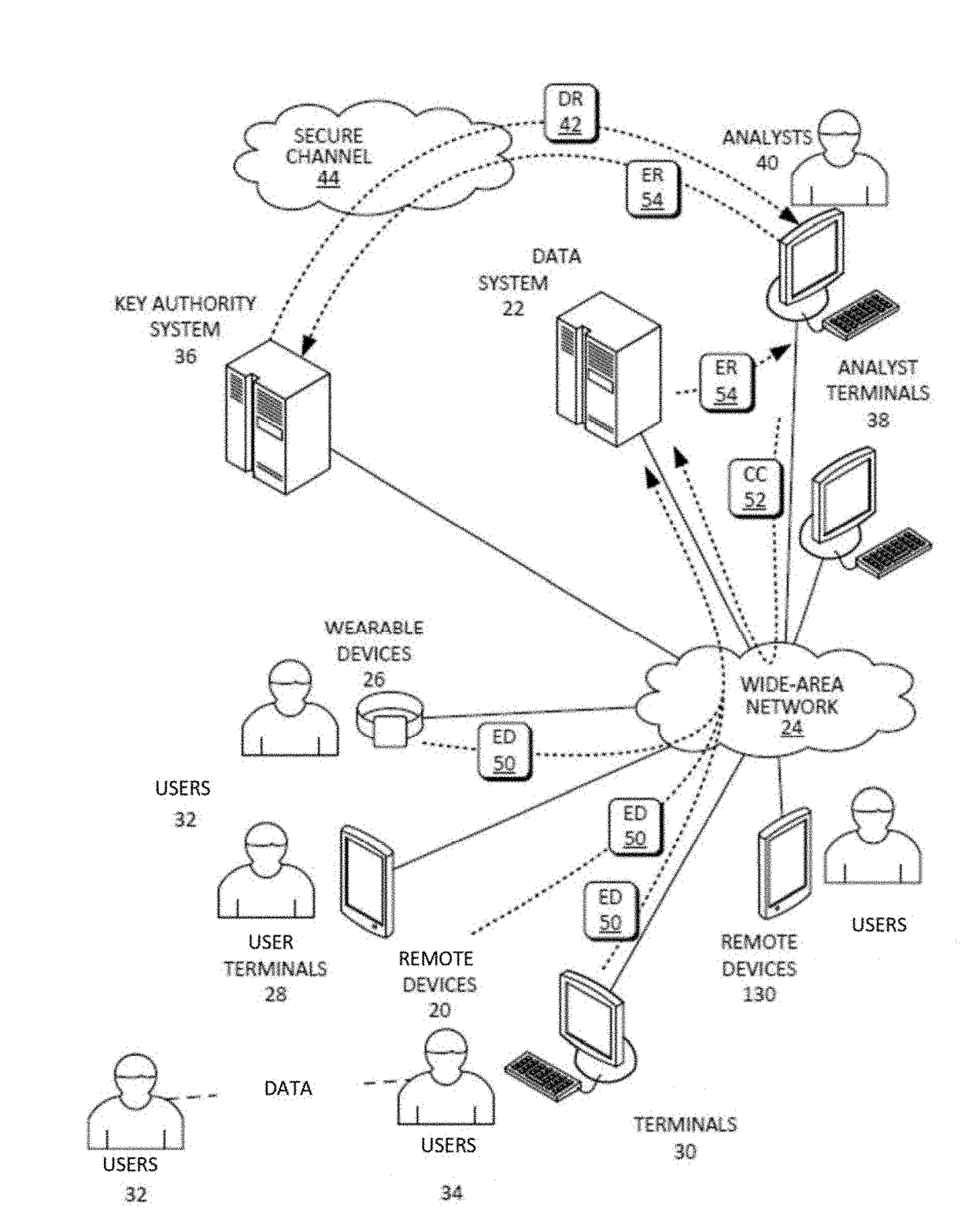
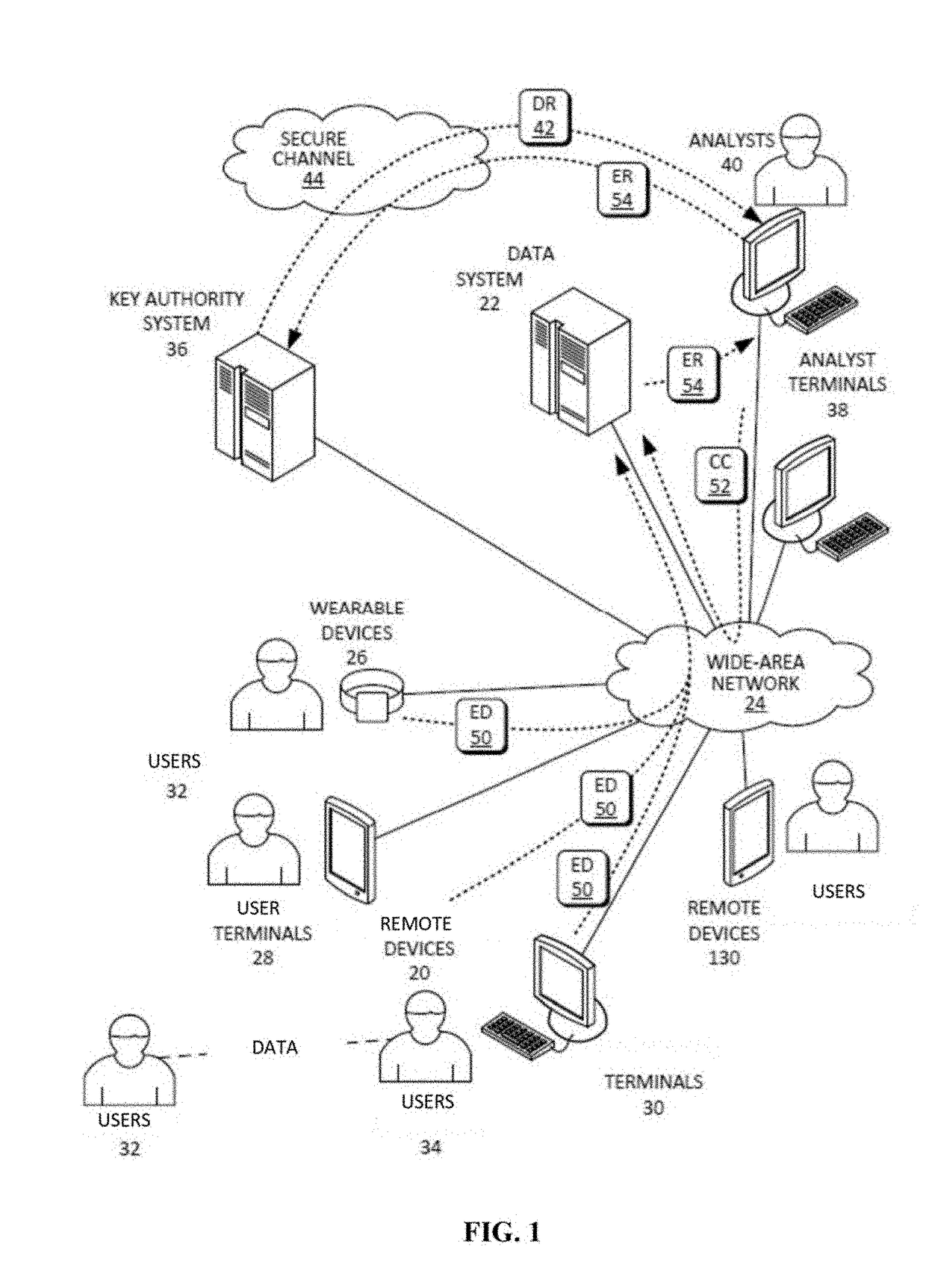
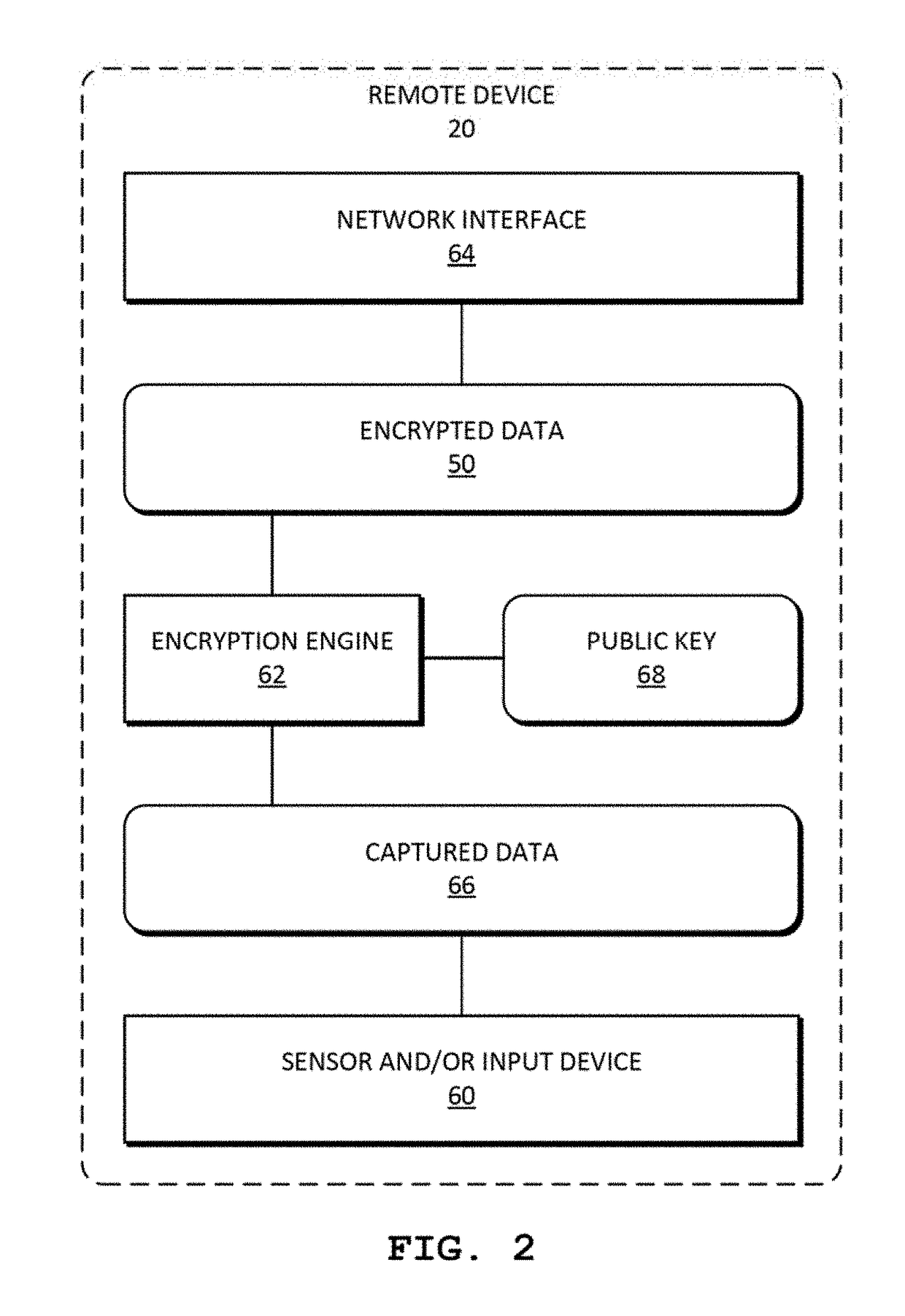
[0028]The homomorphic encryption / decryption operations executed on confidential data may be performed as shown in FIGS. 1-5 and FIGS. 6A-6J. Key generation may be performed at a secure system, such as the key authority system 36. Public keys 68 may be pre-loaded onto the remote devices 20 containing the confidential information (such as a credit card, remote sensor, etc.) prior to deployment of remote devices 20. Alternatively, or additionally, public keys 68 may be made available to the remote devices 20 via a network resource (such as a public cloud), which may be configured ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com