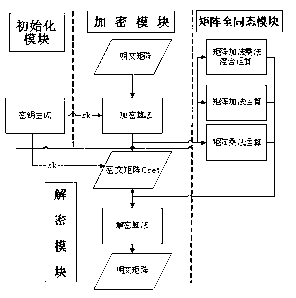
Matrix fully homomorphic encryption method
A technology of fully homomorphic encryption and matrix addition, applied in secure communication devices, digital transmission systems, electrical components, etc., can solve problems such as impracticality and slow speed
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0048] 1. Initialization module: the user specifies the dimension of the key to be generated , Select the key space and matrix element value range, and generate the required key through the key generator.
[0049] The specific steps are as follows:
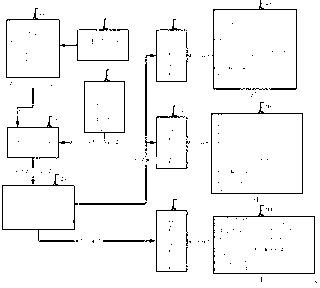
[0050] (1) User input dimension , select the keyspace and the range of element values in the matrix . see figure 2 As shown, the parameters input in Figure 21 are , where G indicates that the key space is .
[0051] (2) Key generator generate key : Includes random integer invertible matrix generator and matrix invertor . The key generation details are as follows:
[0052] a) Generate an invertible matrix : Dimensions of the given matrix , the keyspace and an invertible matrix range of element values in , using a random integer invertible matrix generator to generate an integer invertible matrix , . see figure 2 As shown, 22 in the figure is the generated invertible matrix.
[0053] ...
Embodiment 2
[0073] 1. Initialization module: the user specifies the dimension of the key to be generated , Select the key space and matrix element value range, and generate the required key through the key generator.
[0074] The specific steps are as follows:
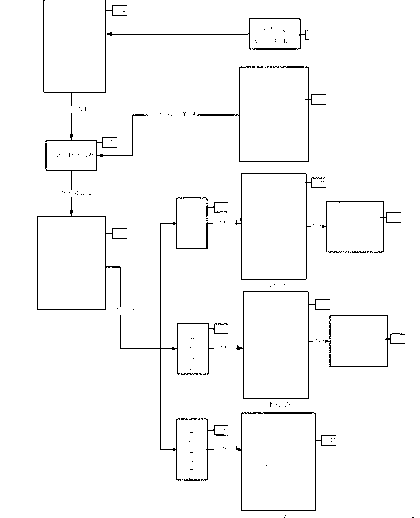
[0075] (1) User input dimension , select the keyspace and the range of element values in the matrix . see image 3 As shown, the parameters input in 31 in the figure are ,in I represents the keyspace and .
[0076] (2) Key generator Generate key: Includes random integer invertible matrix generator and matrix invertor . The key generation details are as follows:
[0077] a) Generate an invertible matrix : Dimensions of the given matrix , the keyspace and an invertible matrix range of element values in , using a random integer invertible matrix generator to generate an integer invertible matrix , . see image 3 As shown, 32 in the figure is the generated invertible matrix.
[0078] b) find...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com