Cluster routing method based on multi-factor trust mechanism
A multi-element and routing technology, applied in wireless communication, advanced technology, electrical components, etc., can solve the problems of evaluating node credibility, lack of instructions, and poor operability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
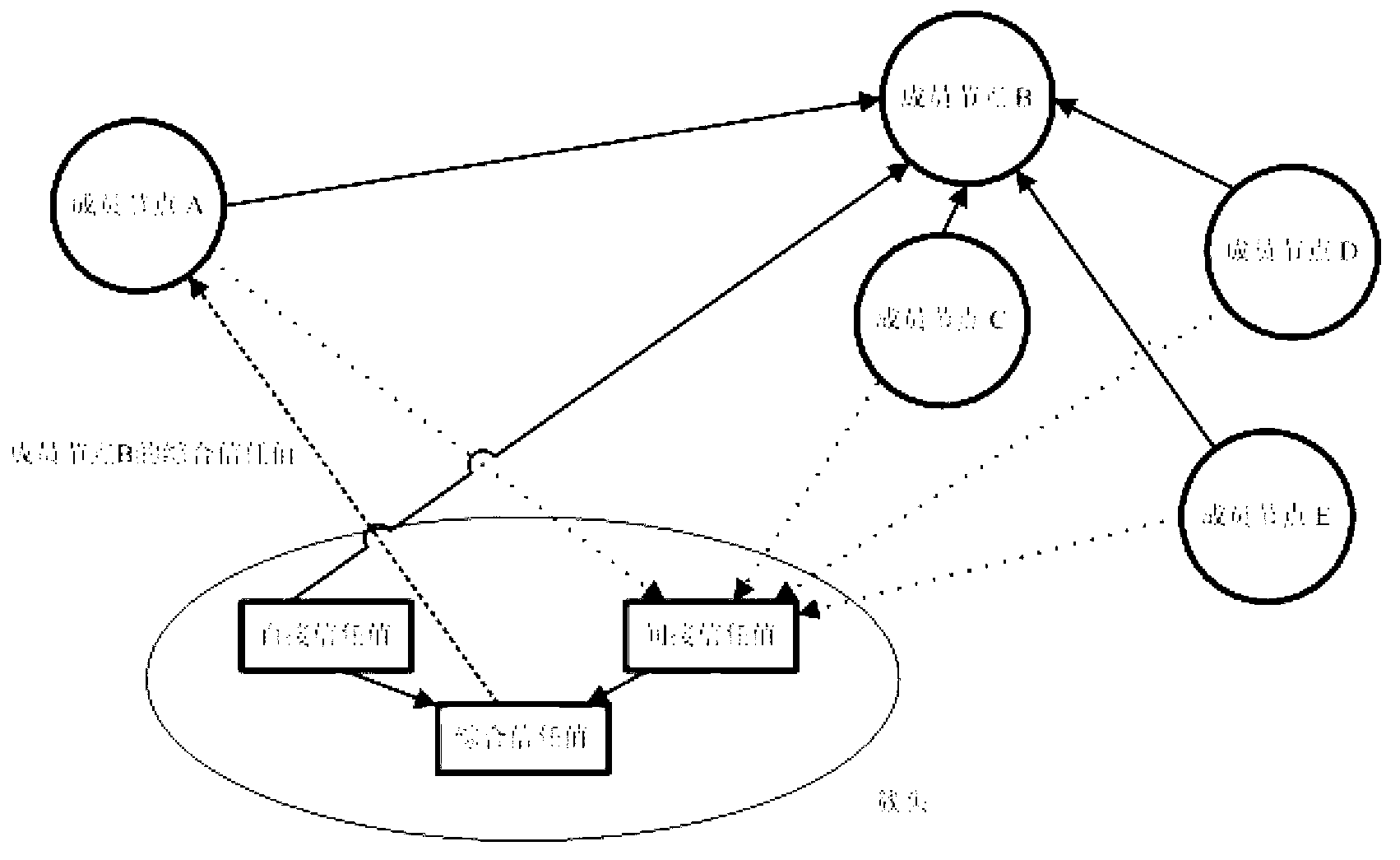
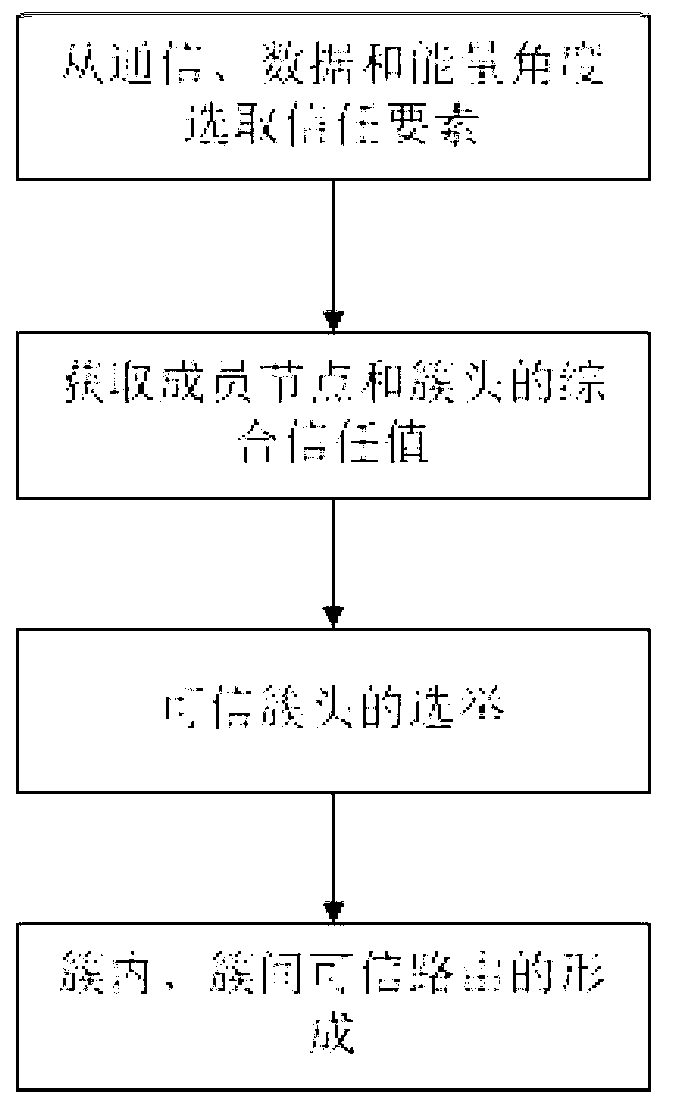
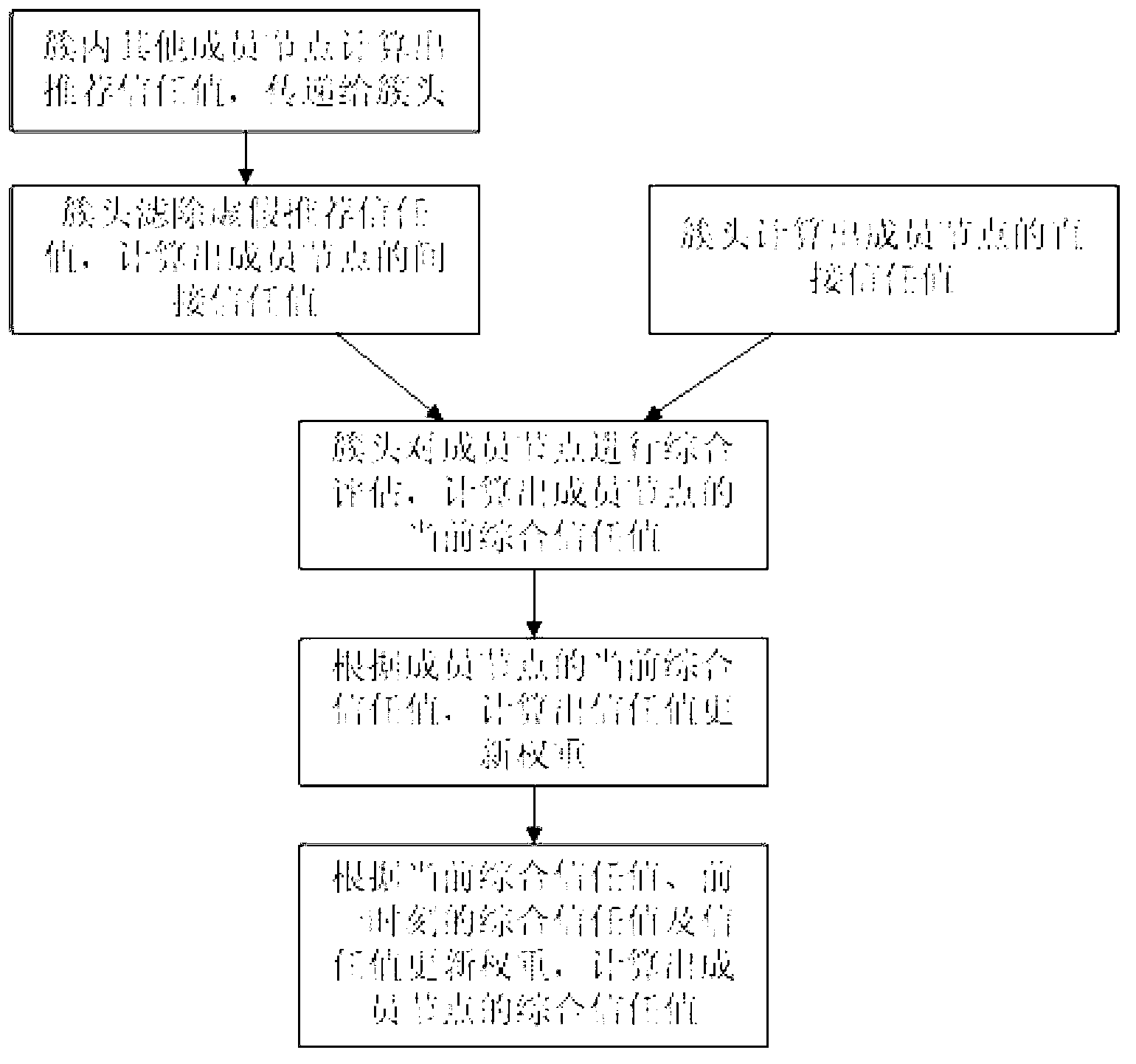
Image
Examples
specific Embodiment
[0054] 1. Selection of trust factors
[0055] The trust mechanism selects six trust elements from the perspective of communication, data and energy, namely:
[0056] (1) Data integrity, which can be expressed as:
[0057] T 1 i , j ( t ) = [ 100 × IP i , j ( t - t 0 ) TFP i , j ( t - t 0 ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com