User privilege escalation method supporting mandatory access control
A mandatory access control and user technology, applied in the direction of digital data authentication, can solve problems such as process security attributes not being set correctly, users unable to perform privileged operations, and privilege escalation failures. Ease of use effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0035]The present invention will be further described below in conjunction with the accompanying drawings and specific preferred embodiments, but the protection scope of the present invention is not limited thereby.
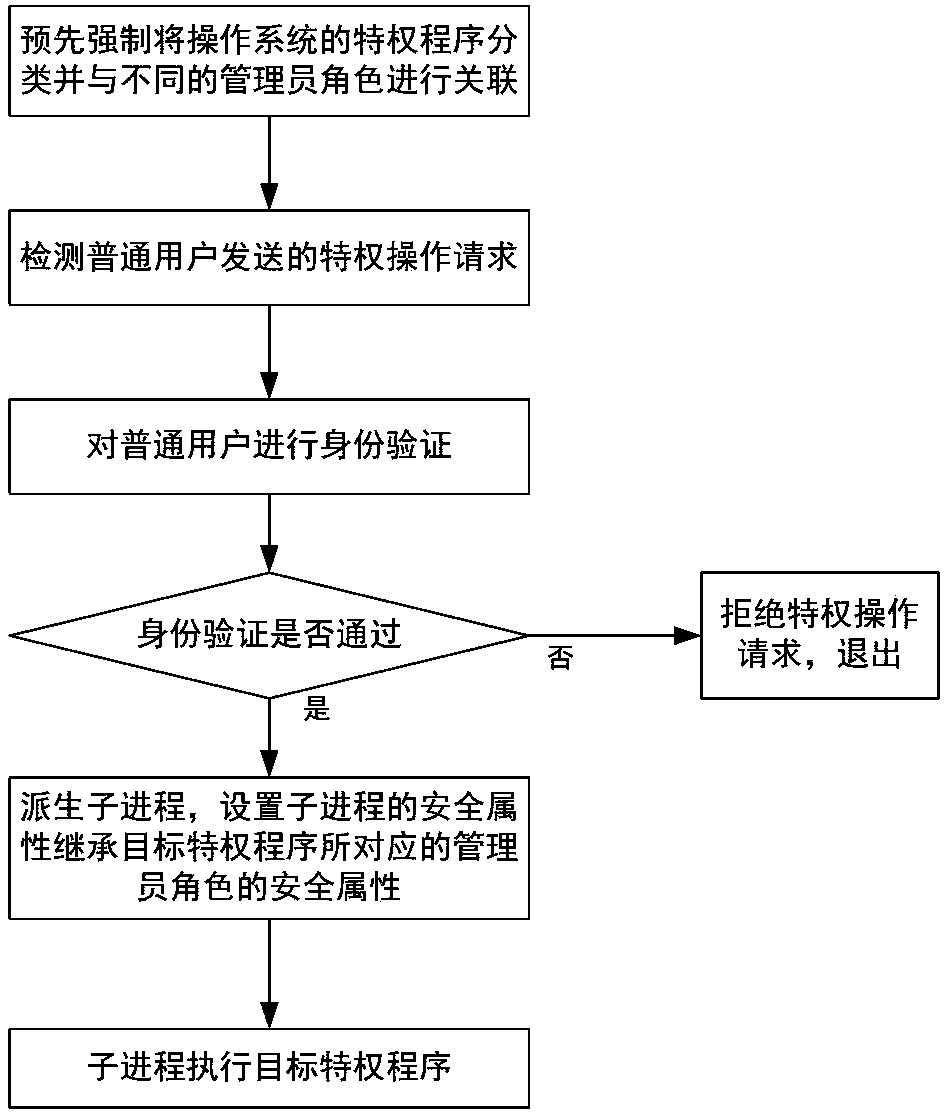
[0036] like figure 1 As shown, the specific implementation steps of the user privilege escalation method that supports mandatory access control in this embodiment are as follows:
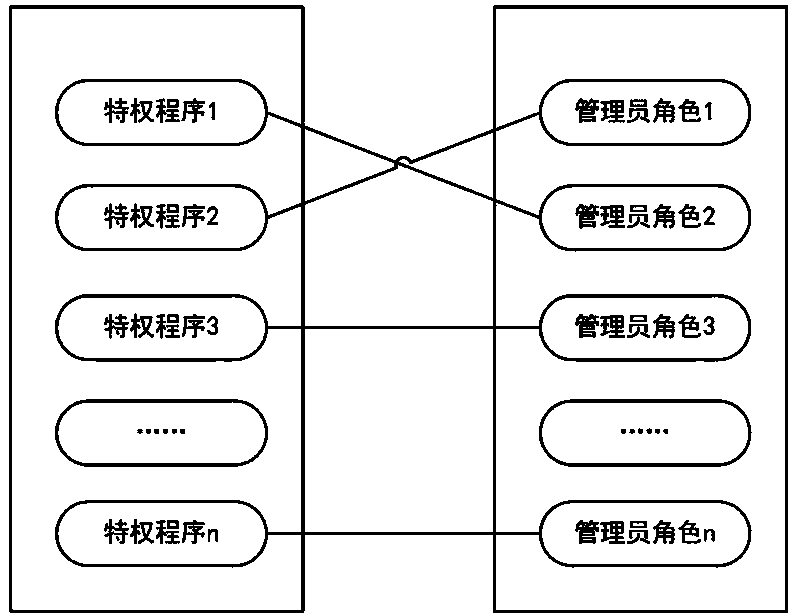
[0037] 1) Pre-forcibly classify the privileged programs of the operating system and associate them with different administrator roles;
[0038] 2) Detect the operation requests of ordinary users, and when a privileged operation request is detected, jump to step 3);
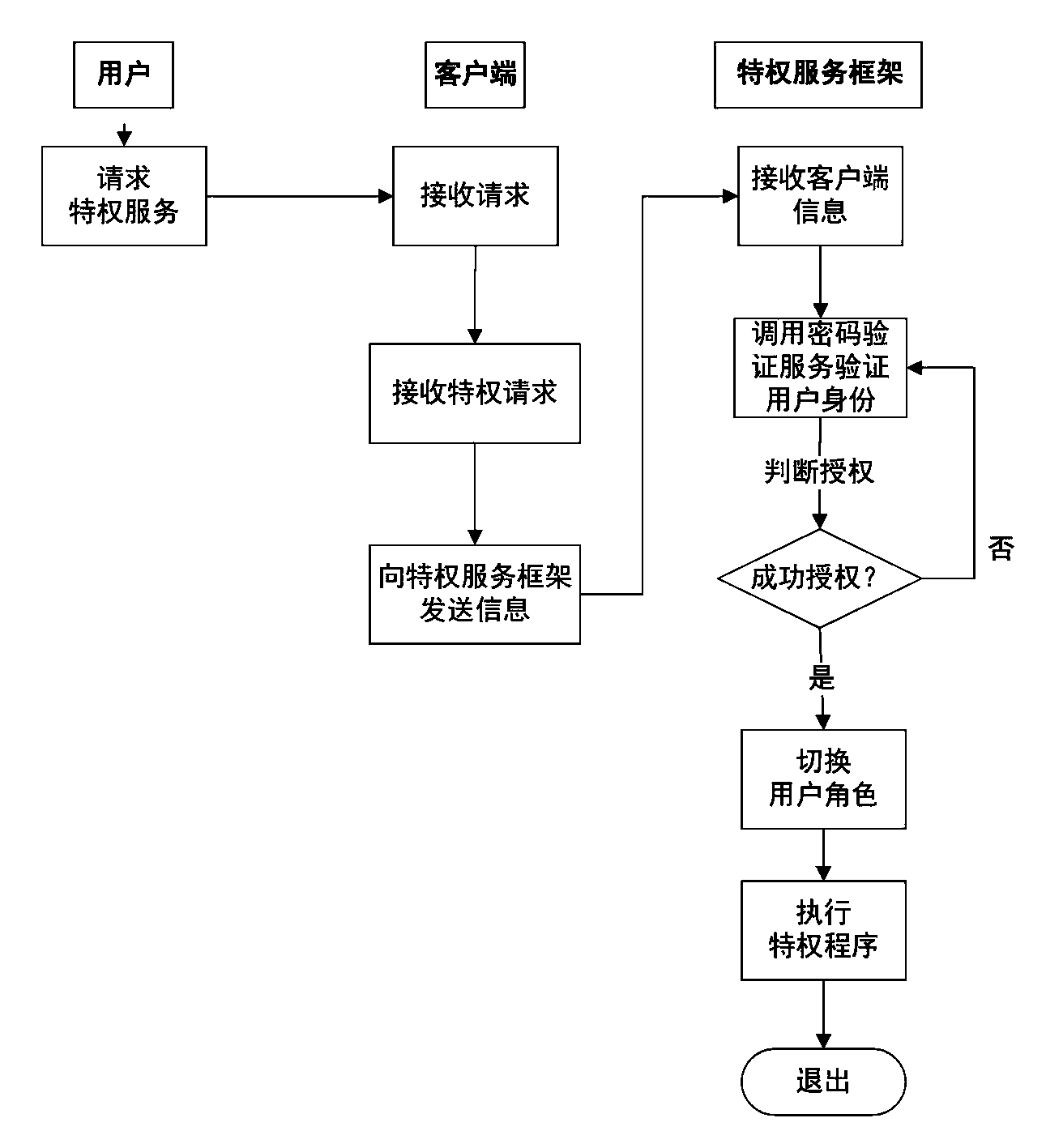
[0039] 3) Authenticate the ordinary user who issued the privileged operation request. If the authentication is passed, the child process is forked, the security attribute of the child process is set, and the security attribute of the child process is inherited from the administrator associated with the target privileged p...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com