Patents
Literature
106 results about "Threat mitigation" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
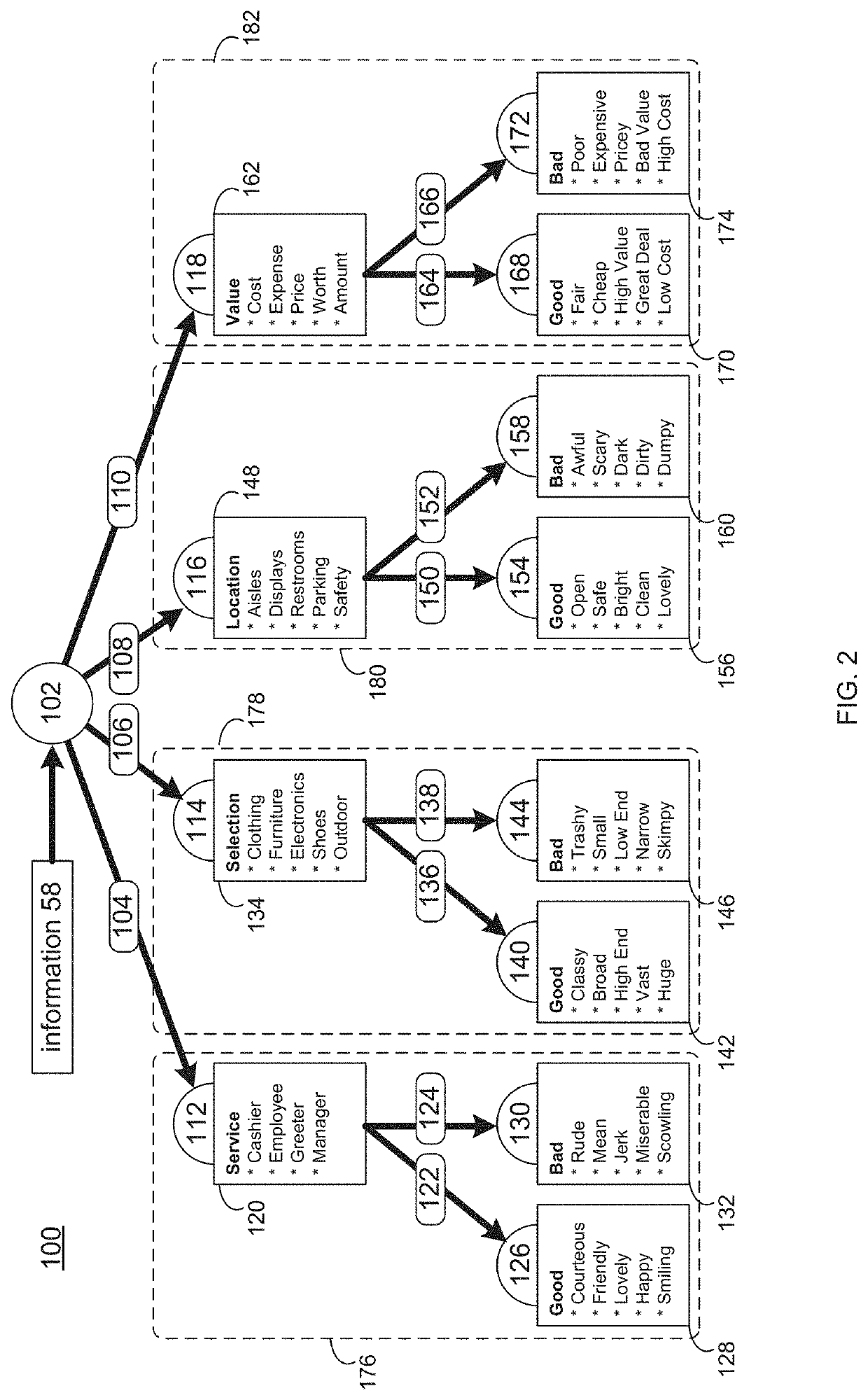
Threat Mitigation is the process used to lessen the extent of a problem or attack by isolating or containing a threat until the problem can be remedied. LEARN MORE ABOUT Threat Mitigation AND RELATED TECHNOLOGIES.
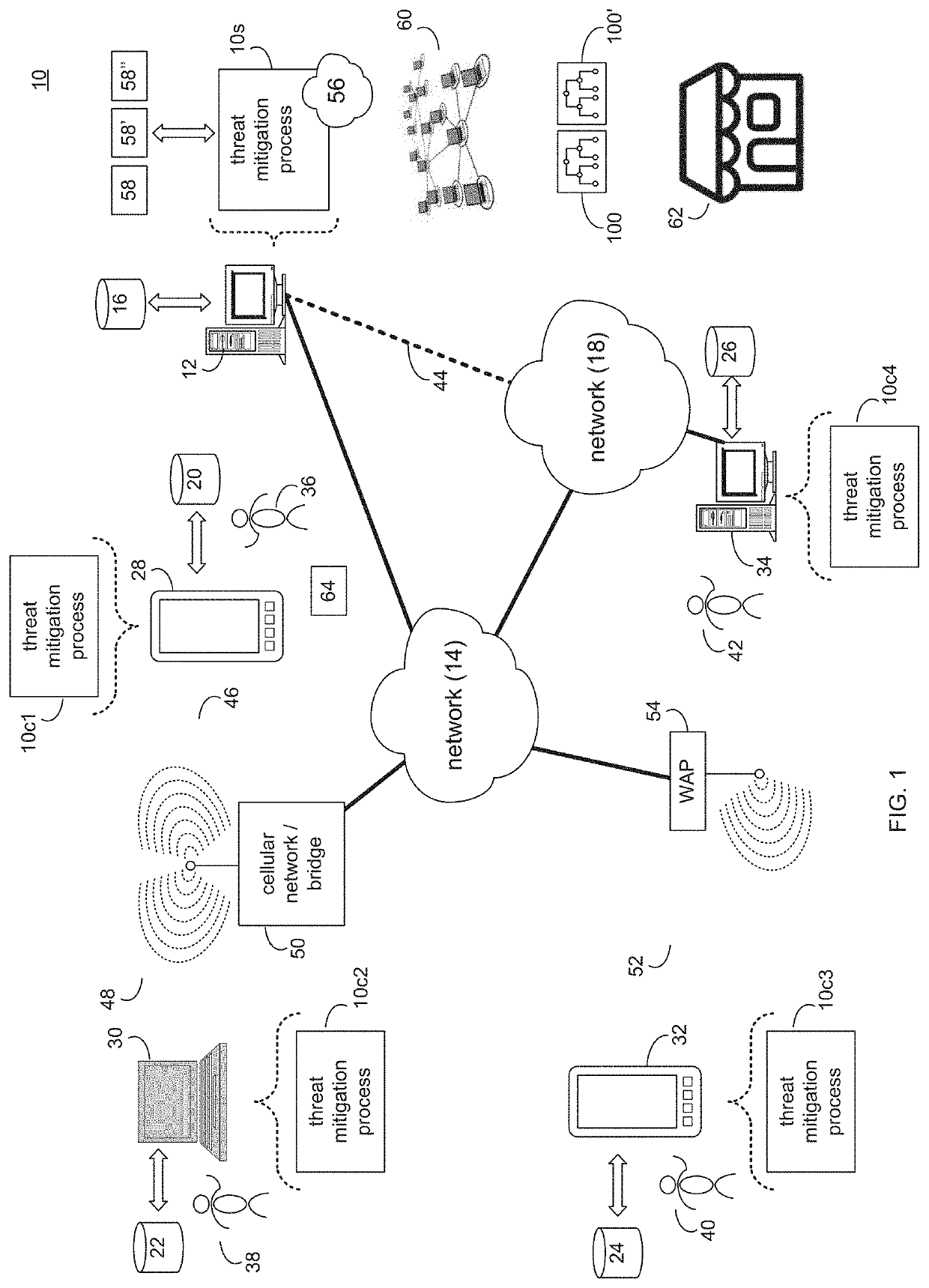
Threat mitigation in a vehicle-to-vehicle communication network
Owner:GM GLOBAL TECH OPERATIONS LLC
Application of advanced cybersecurity threat mitigation to rogue devices, privilege escalation, and risk-based vulnerability and patch management
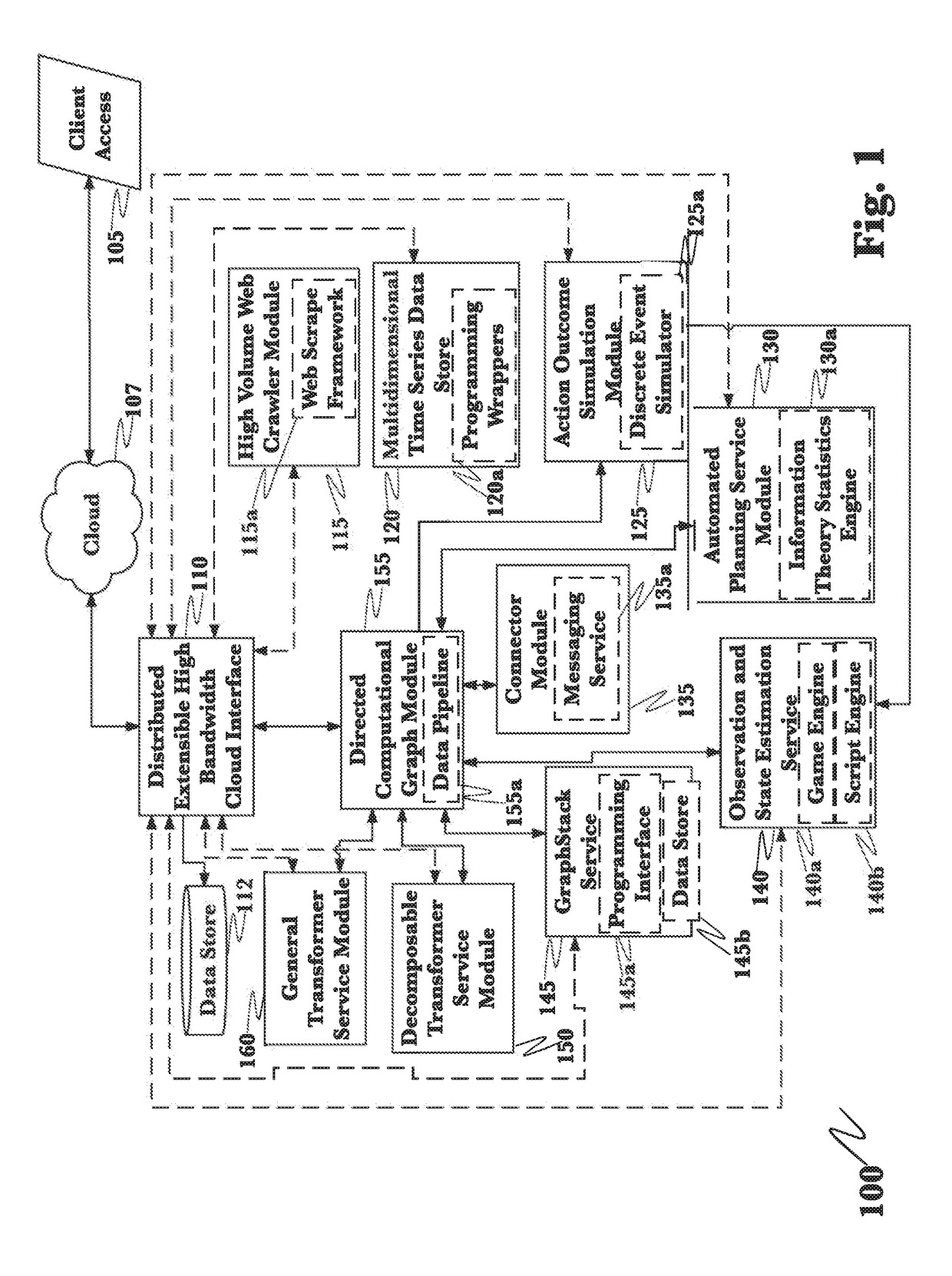
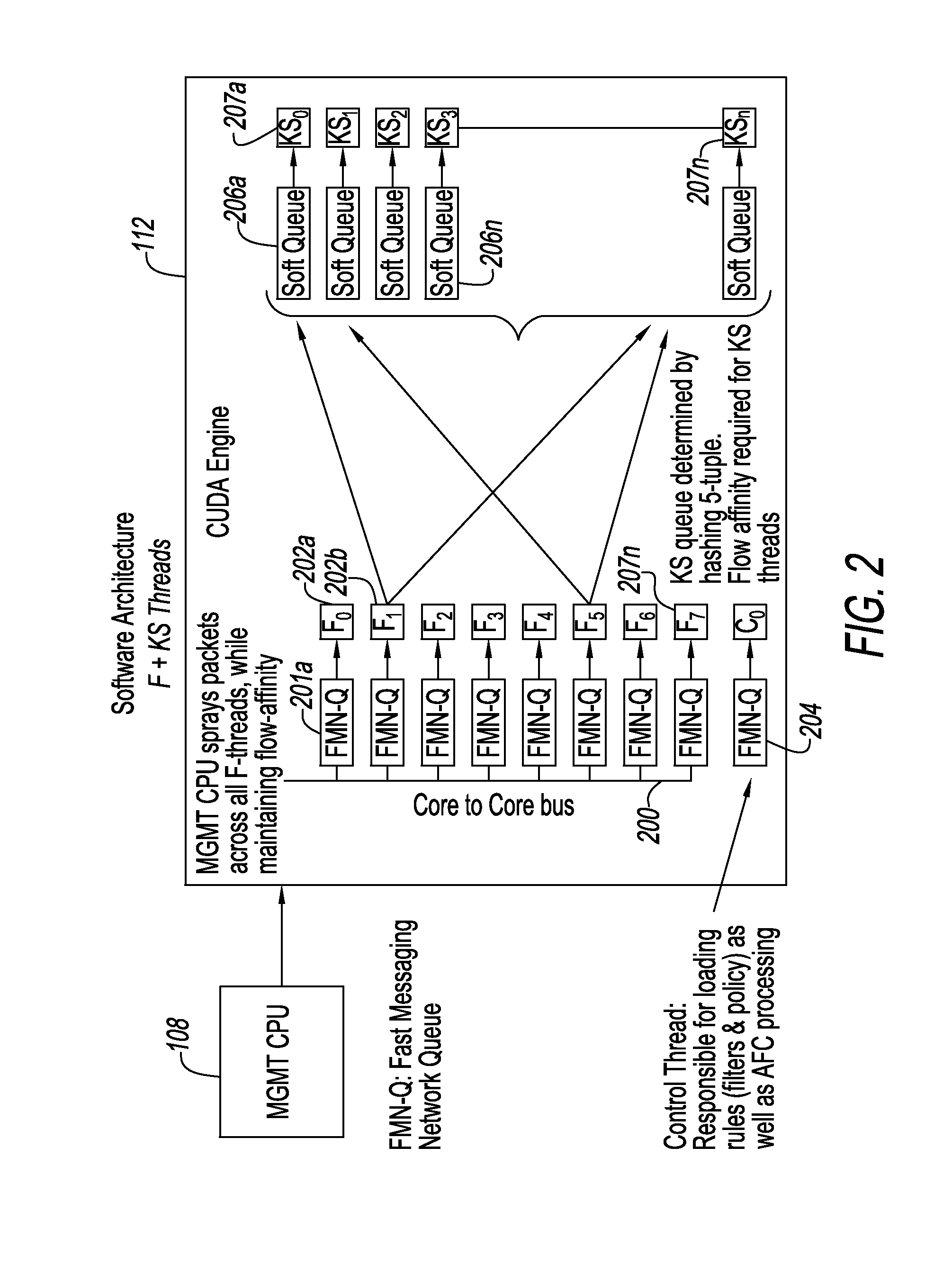
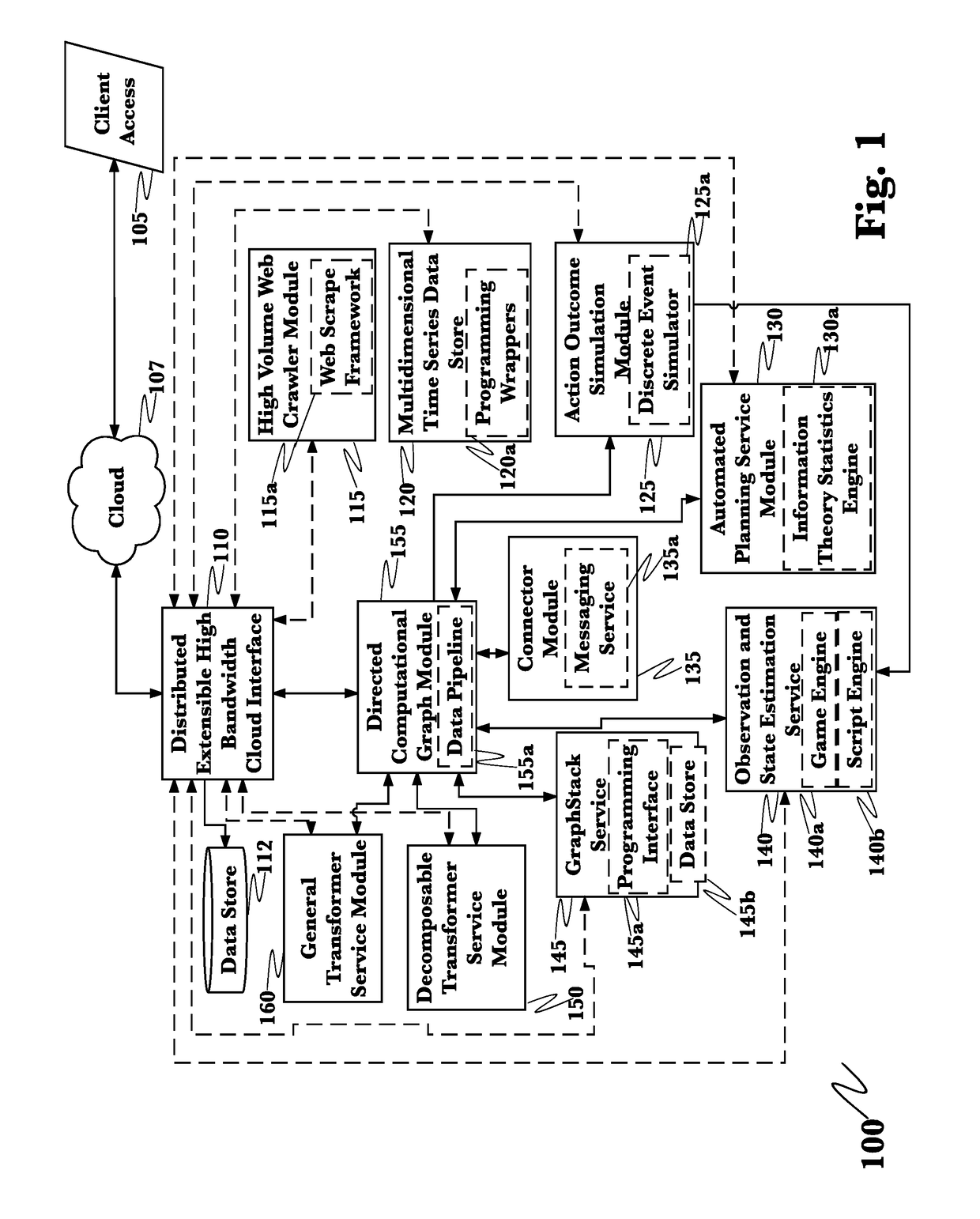
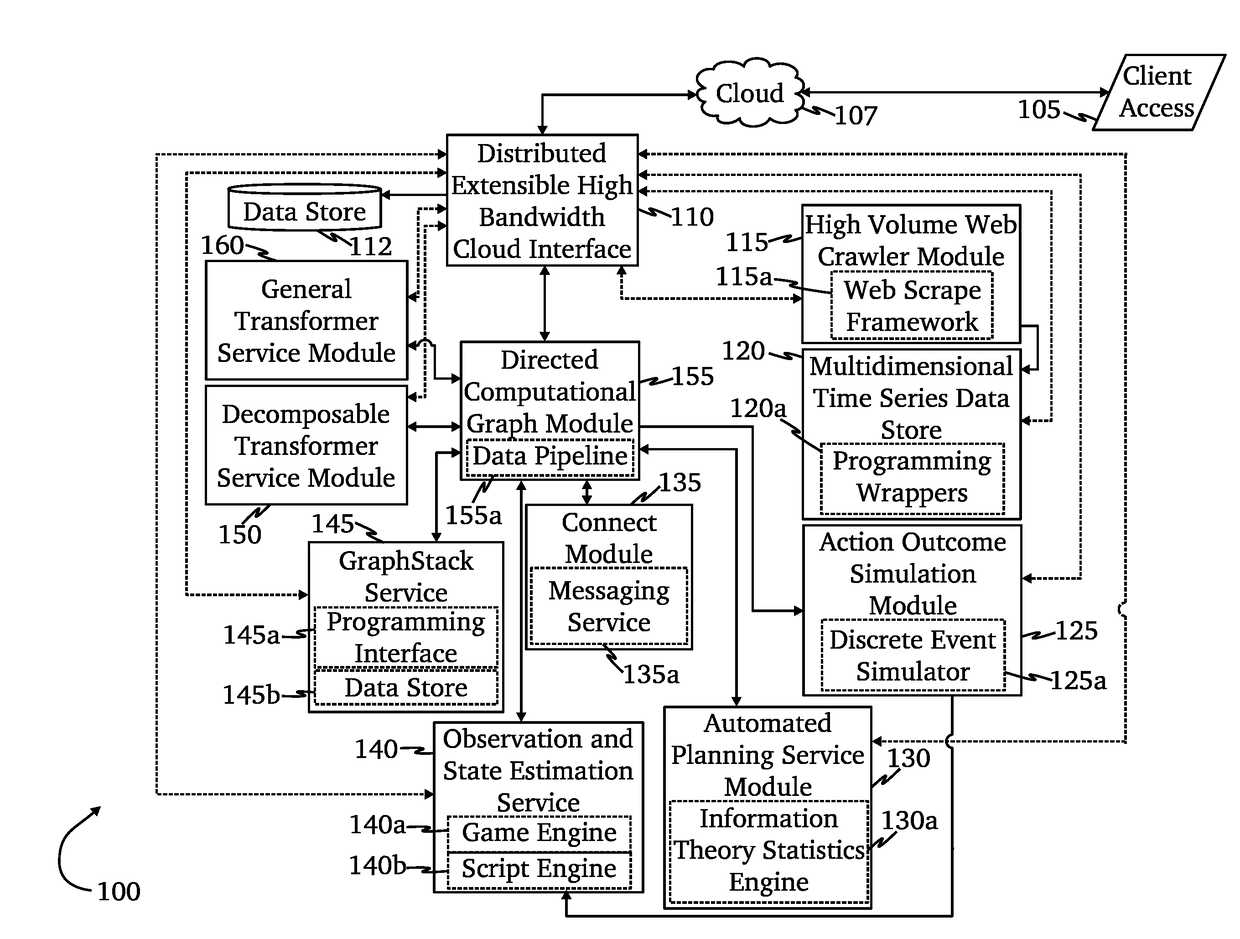
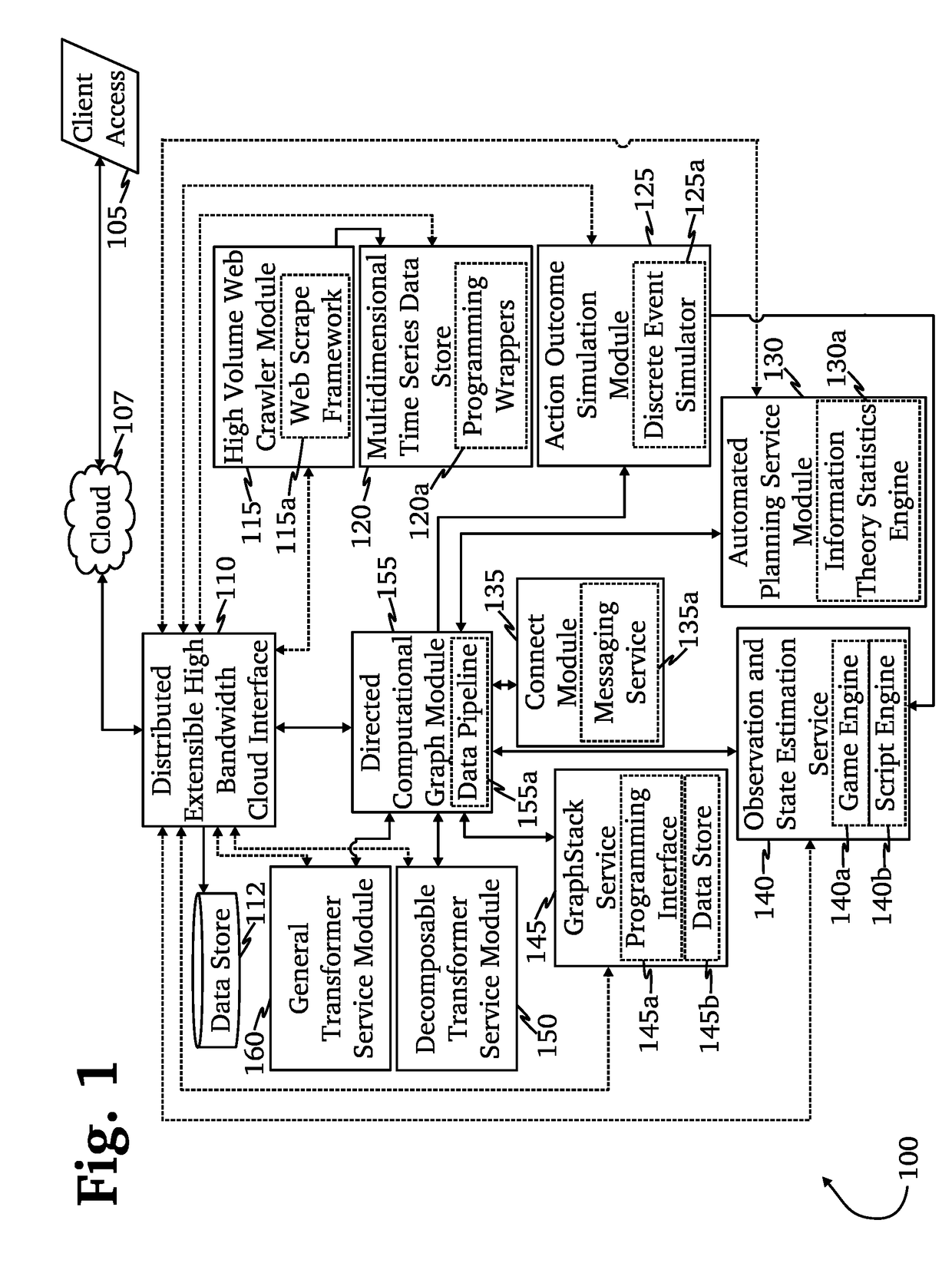
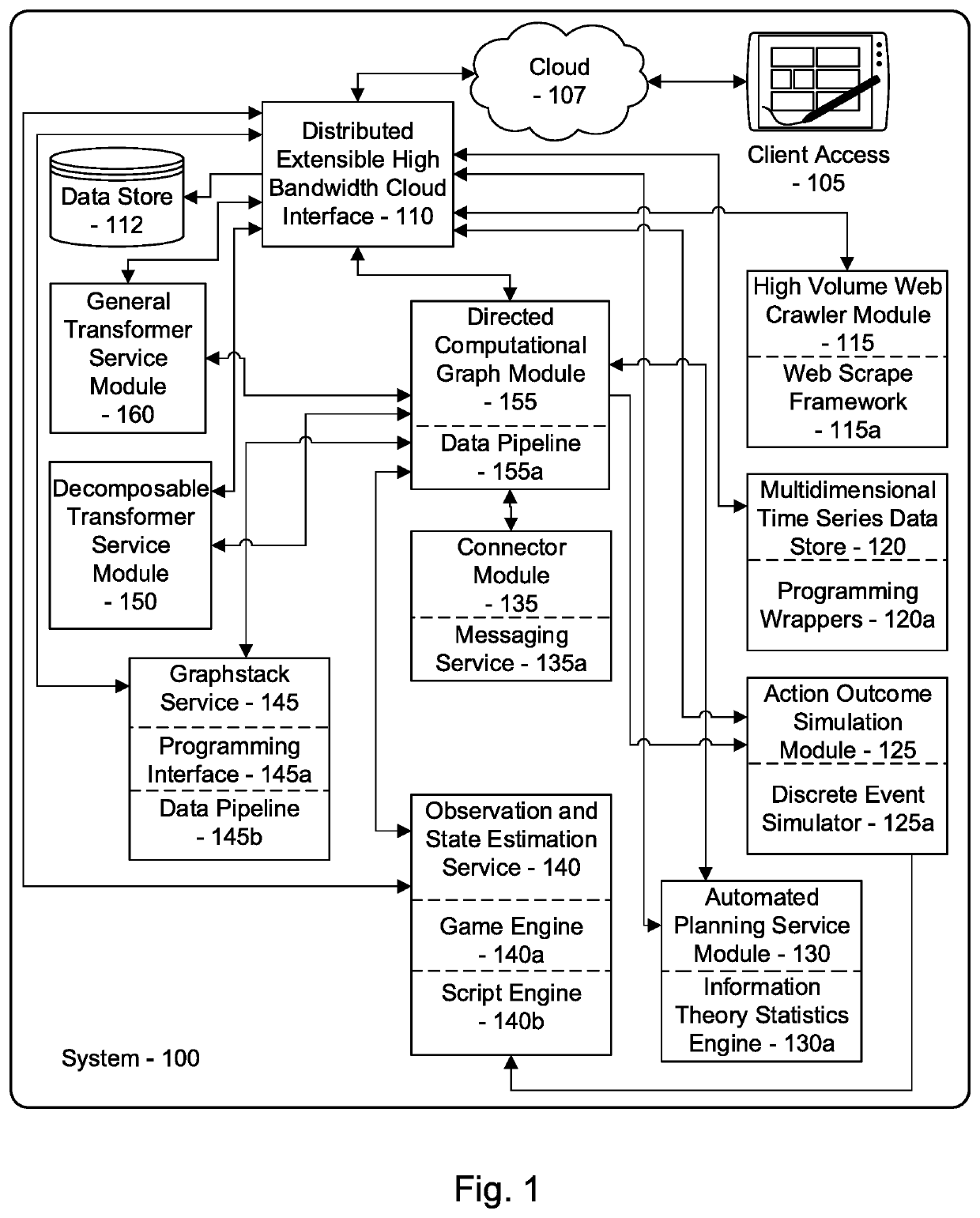
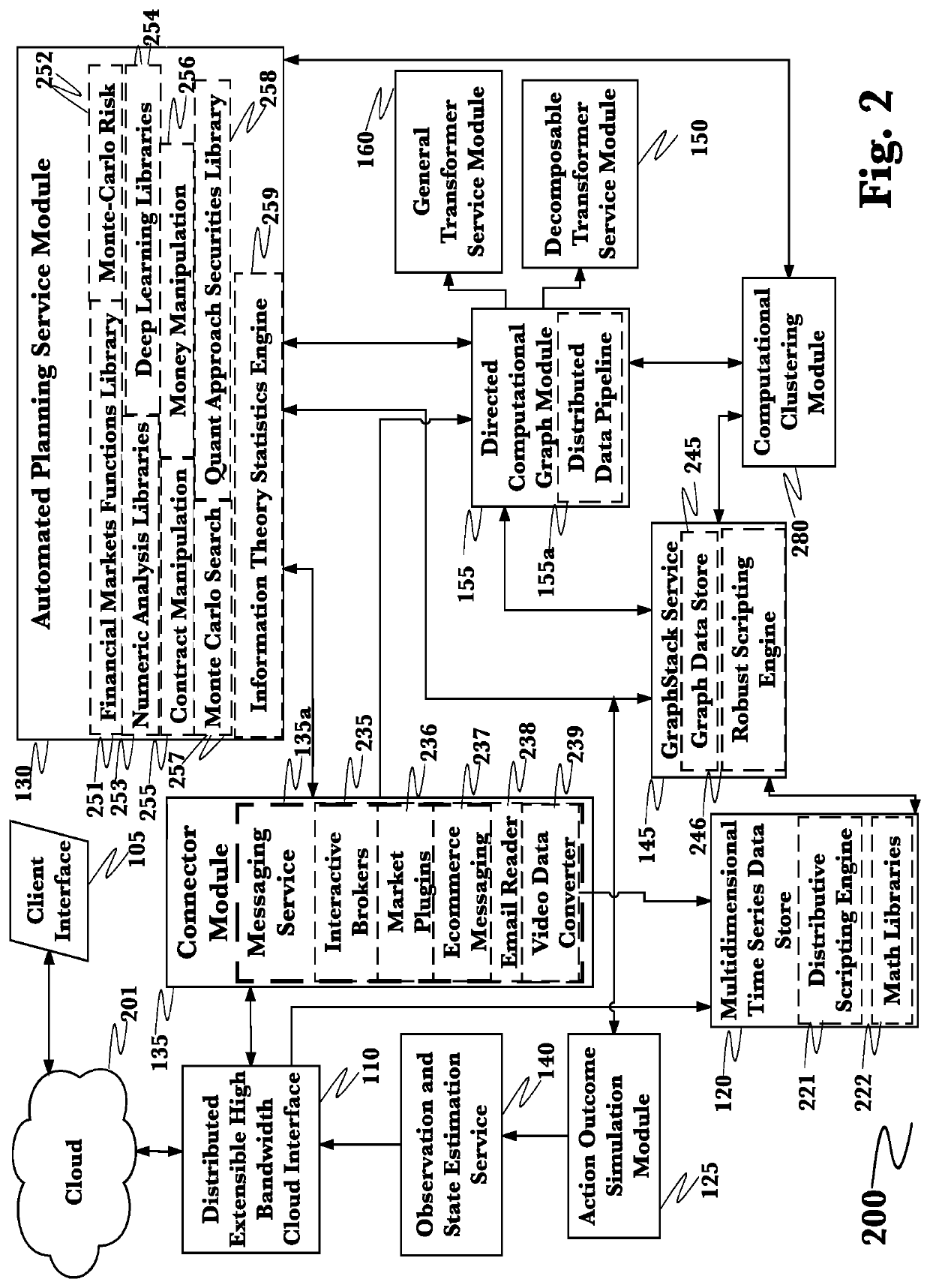
A system for mitigation of cyberattacks employing an advanced cyber decision platform comprising a time series data store, a directed computational graph module, an action outcome simulation module, and observation and state estimation module, wherein the state of a network is monitored and used to produce a cyber-physical graph representing network resources, simulated network events are produced and monitored, and the network events and their effects are analyzed to produce security recommendations.
Owner:QOMPLX INC
Accelerated threat mitigation system
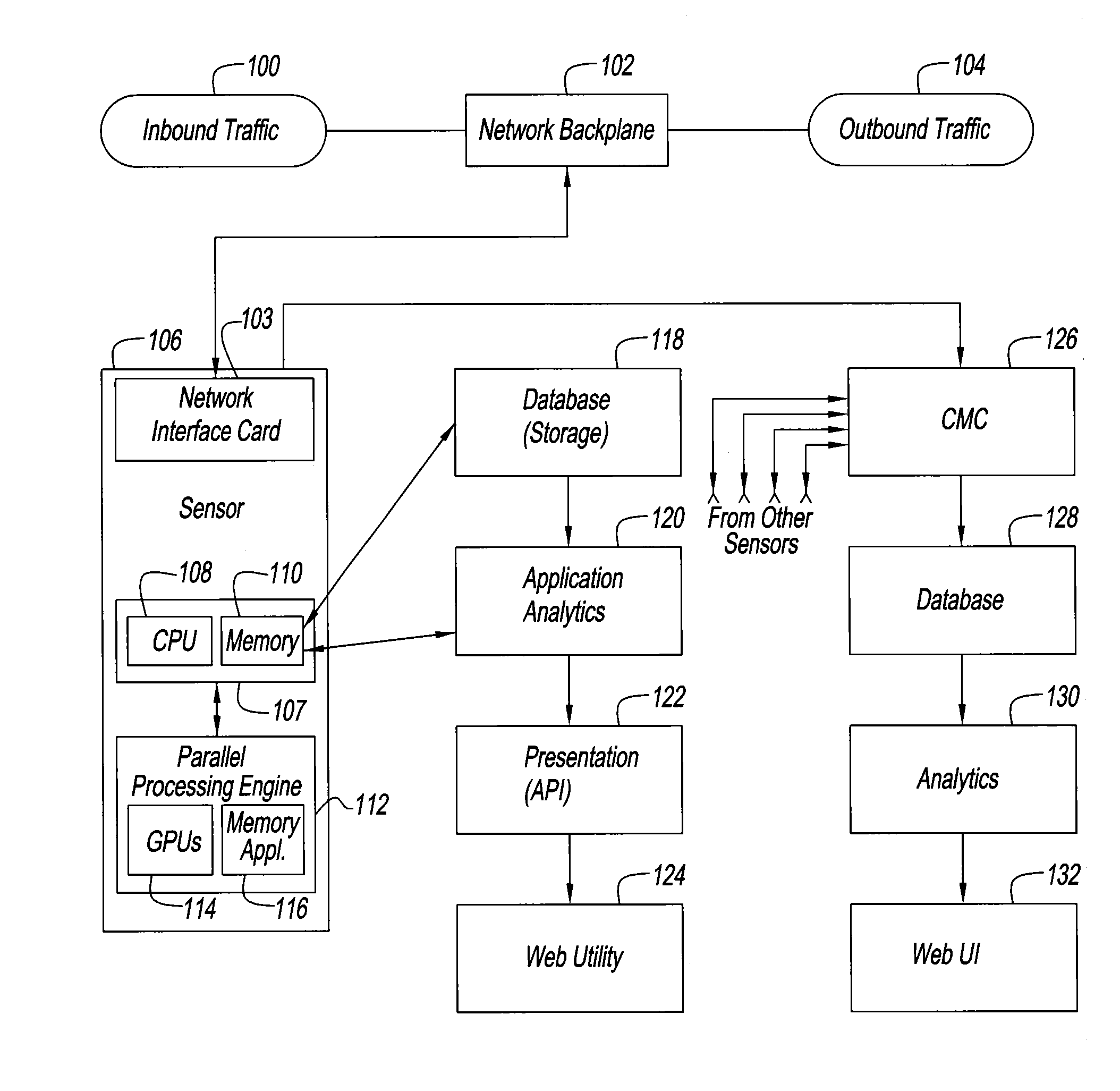
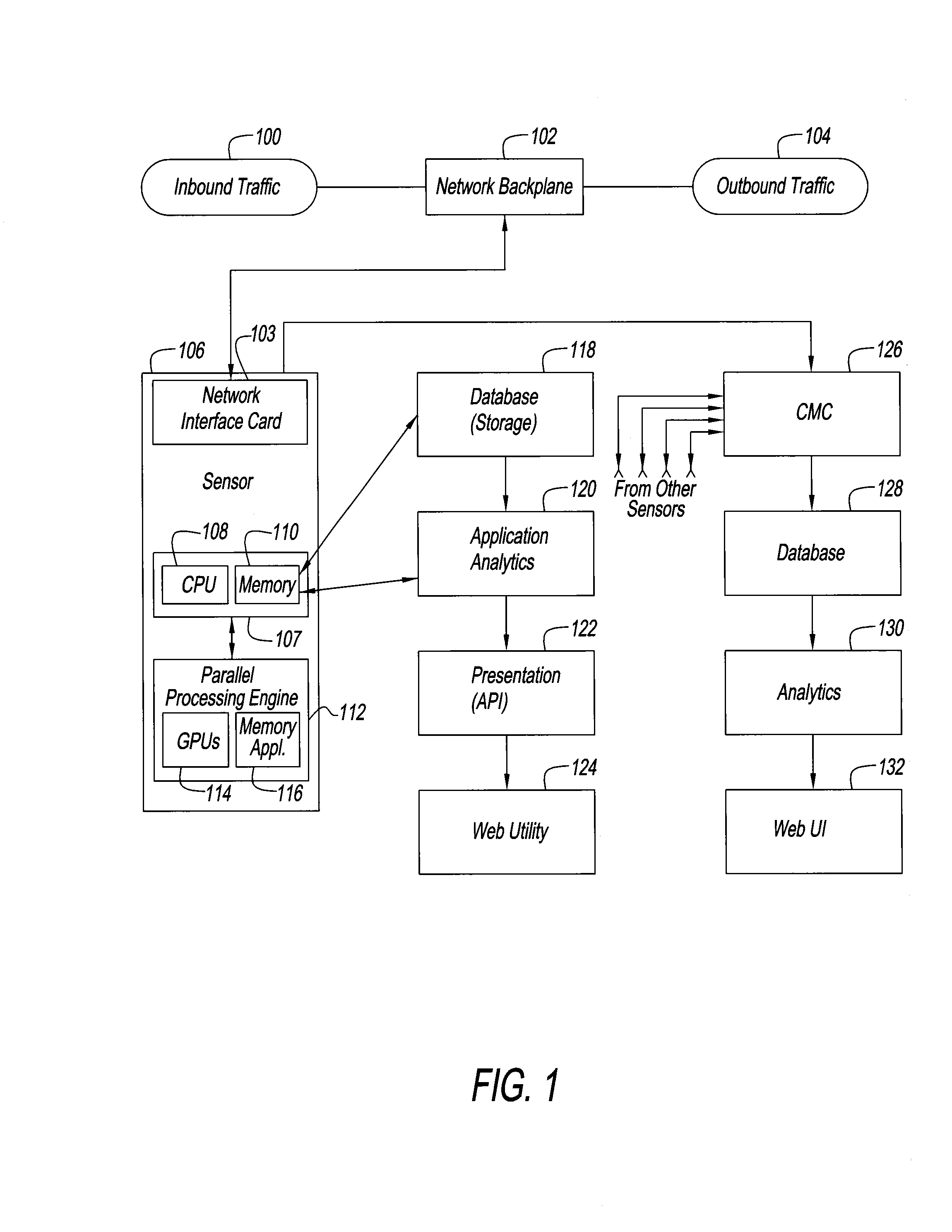
InactiveUS20160191558A1Increase speedImprove performanceMemory loss protectionError detection/correctionFirst pathwayInternet traffic
An intrusion detection and prevention system and method for dealing with threats to computers and computer networks, and in particular to computers and networks connected to the Internet, is disclosed. A sensor receives network traffic. The sensor includes a first processor for managing the network traffic that is received, a first path for the traffic that is received for storing the traffic in a memory for subsequent use, a second path for analyzing the traffic that is received, and for processing the traffic at a speed that is at least as fast as speed of the first path. The second processor is associated with the second path so that some of the traffic is allowed along the first path and other of the traffic is rate limited or not allowed along the first path. The system and method use four tiers of threat detection to successively mitigate a large variety of threats.
Owner:BRICATA
Advanced cybersecurity threat mitigation using behavioral and deep analytics
A system for mitigation of cyberattacks employing an advanced cyber decision platform comprising a time series data store, a directed computational graph module, an action outcome simulation module, and observation and state estimation module, wherein the state of a network is monitored and used to produce a cyber-physical graph representing network resources, simulated network events are produced and monitored, and the network events and their effects are analyzed to produce security recommendations.
Owner:QOMPLX INC
Threat Mitigation in a Vehicle-to-Vehicle Communication Network
ActiveUS20110258435A1User identity/authority verificationTelecommunications linkCommunications system
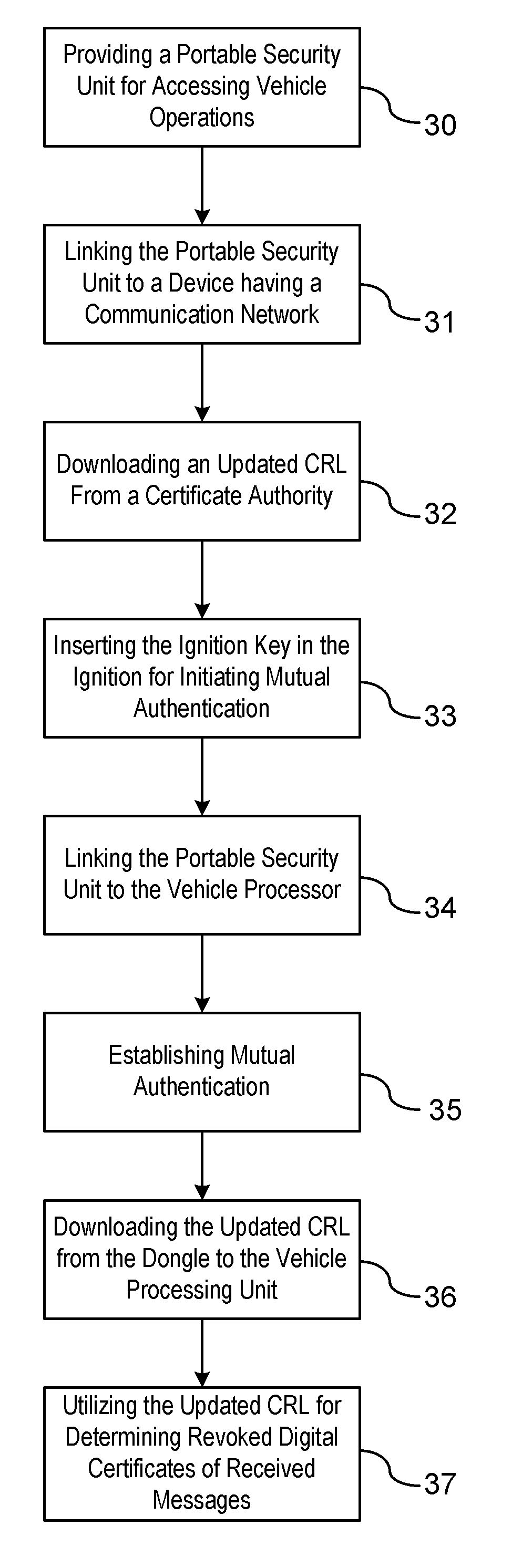
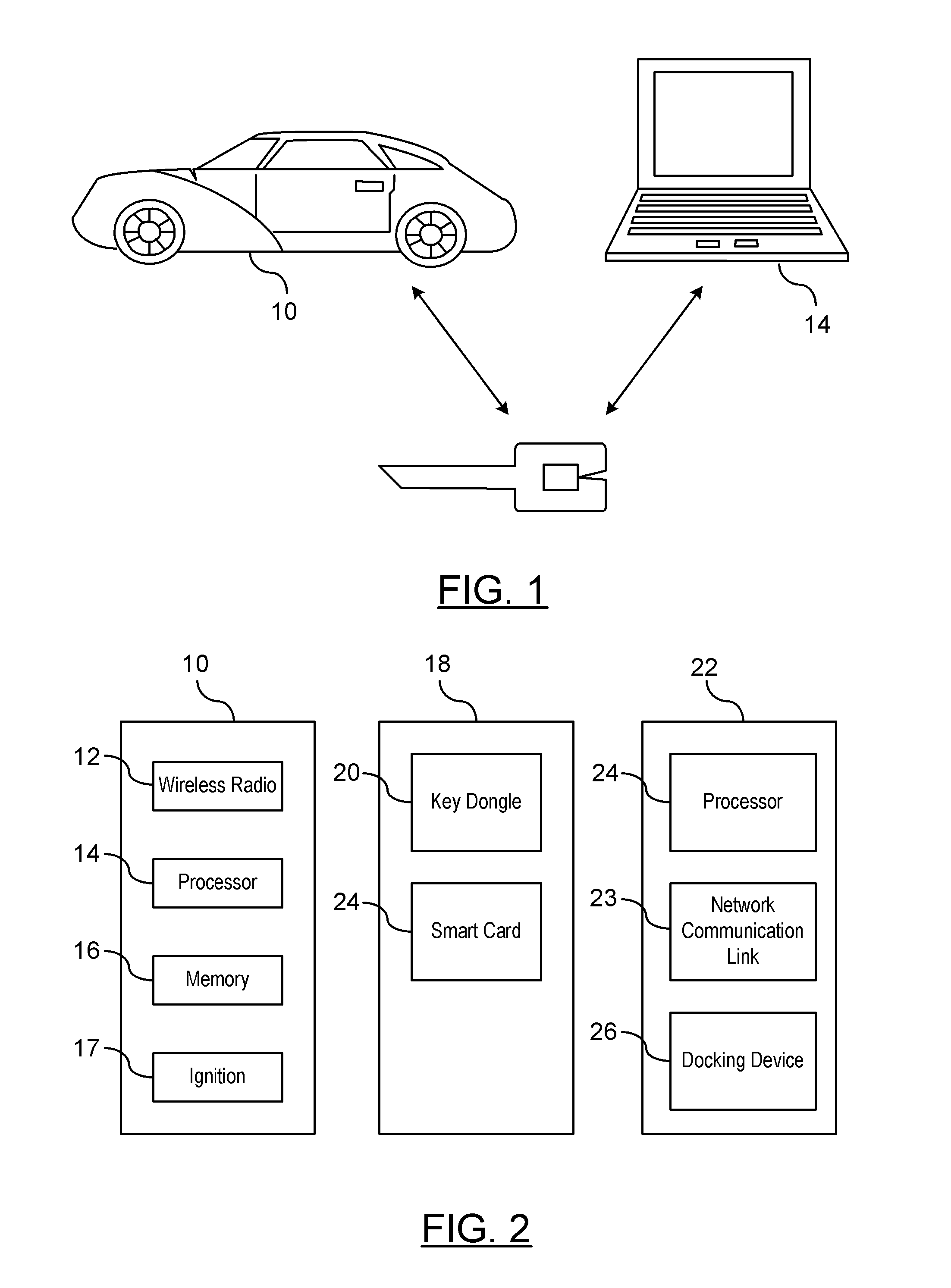
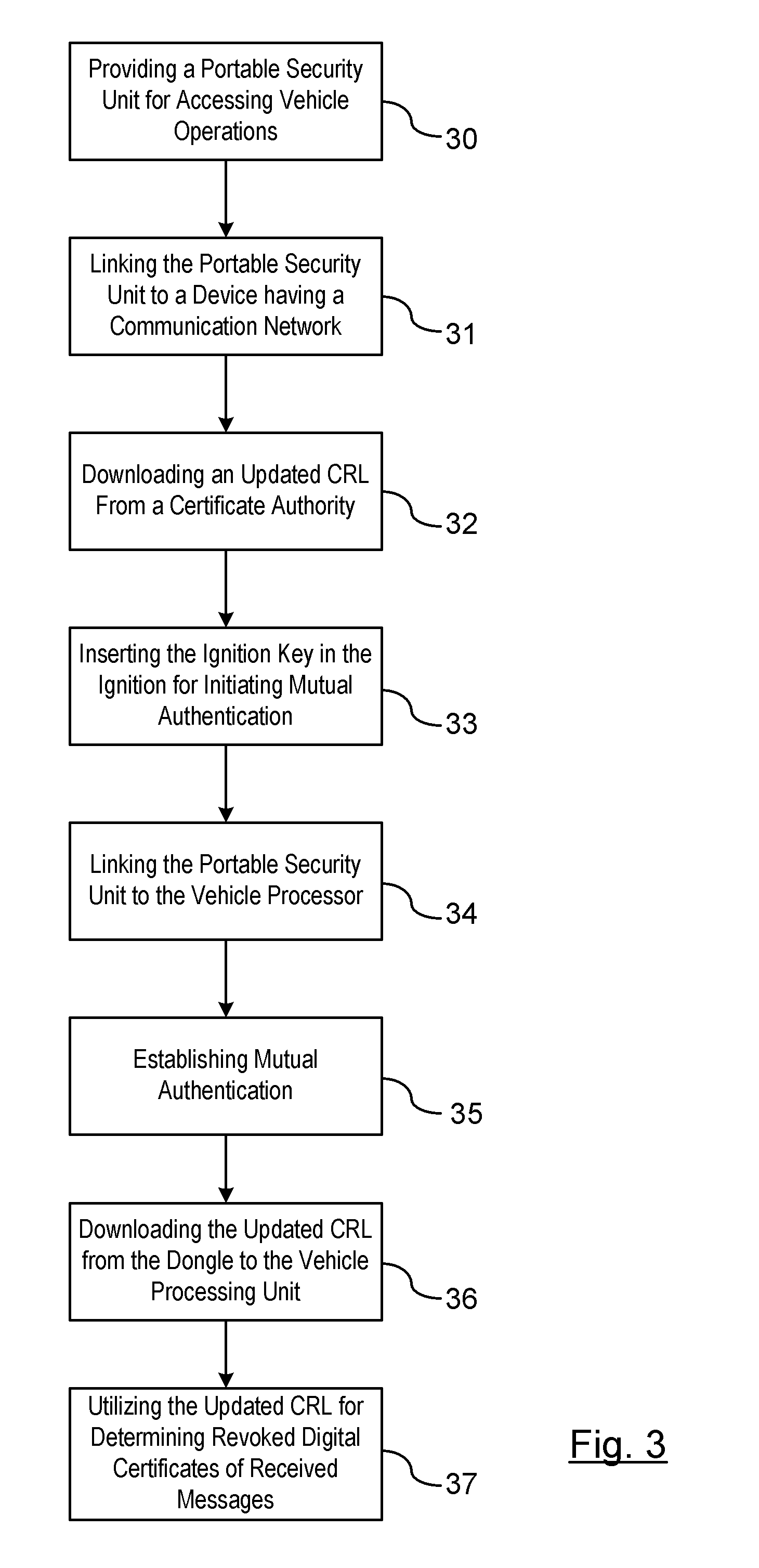
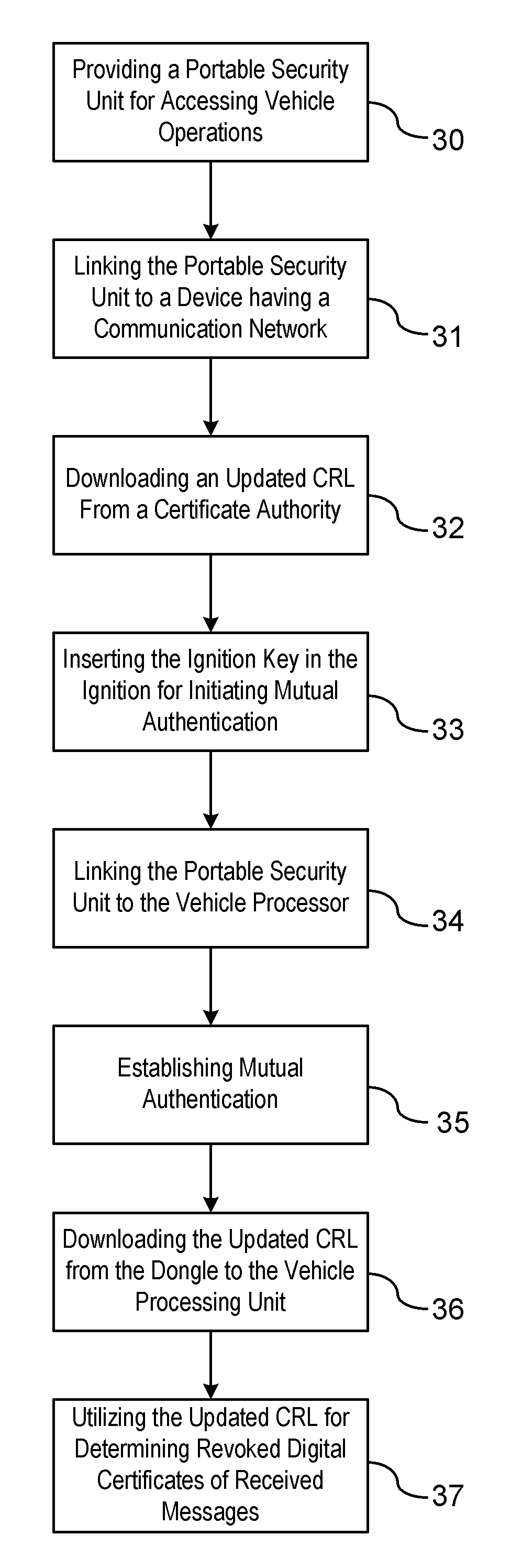
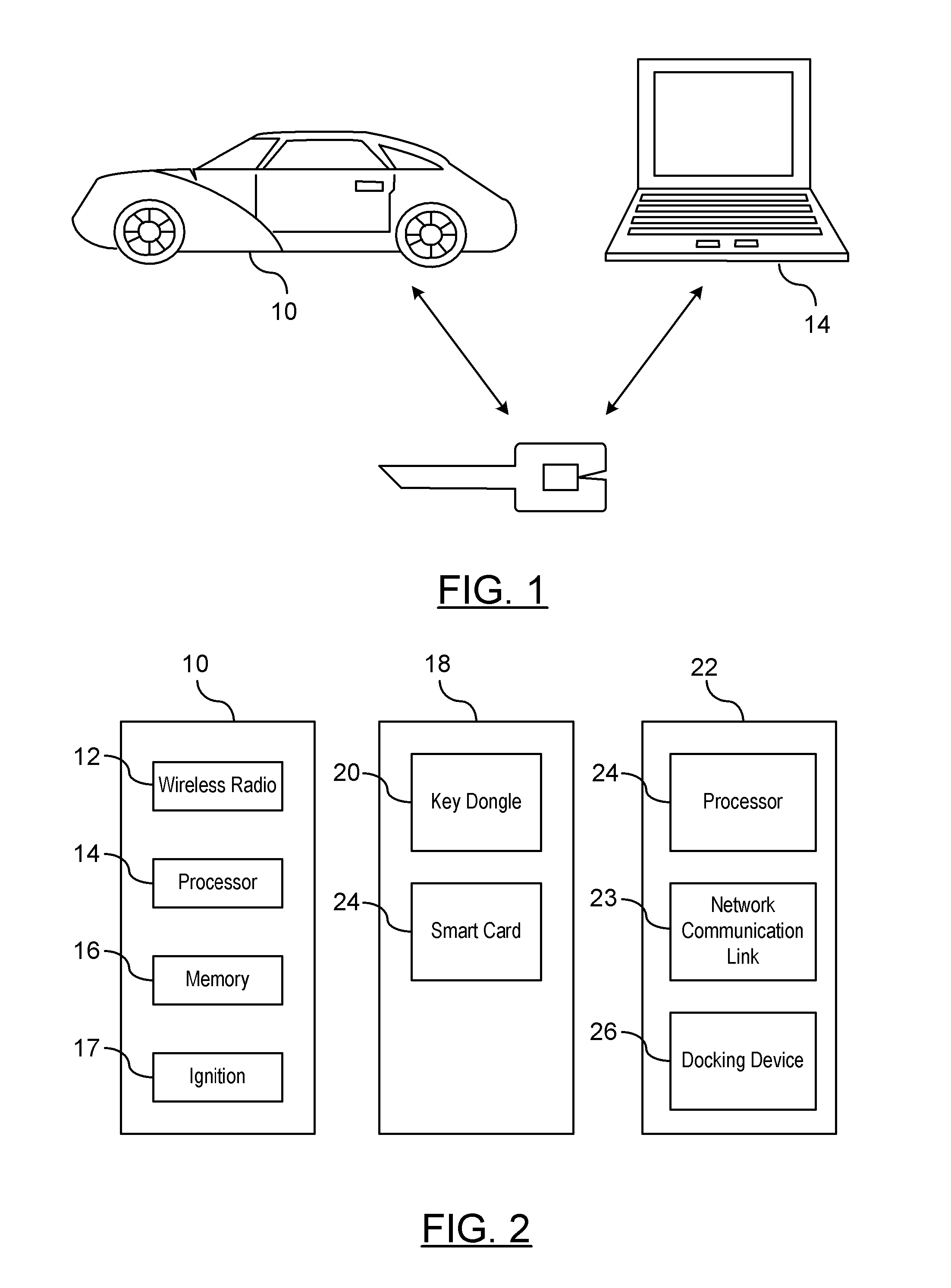
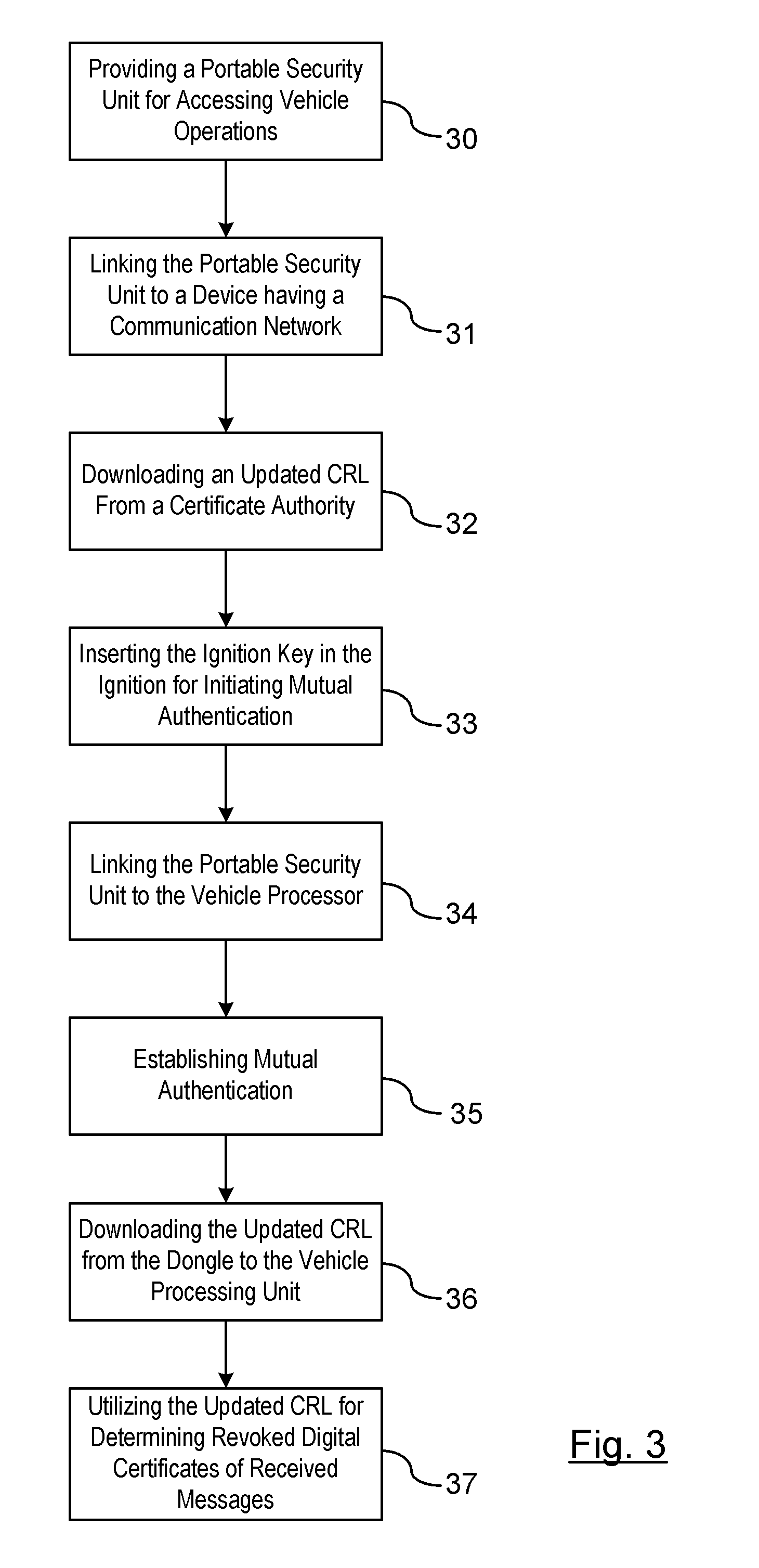
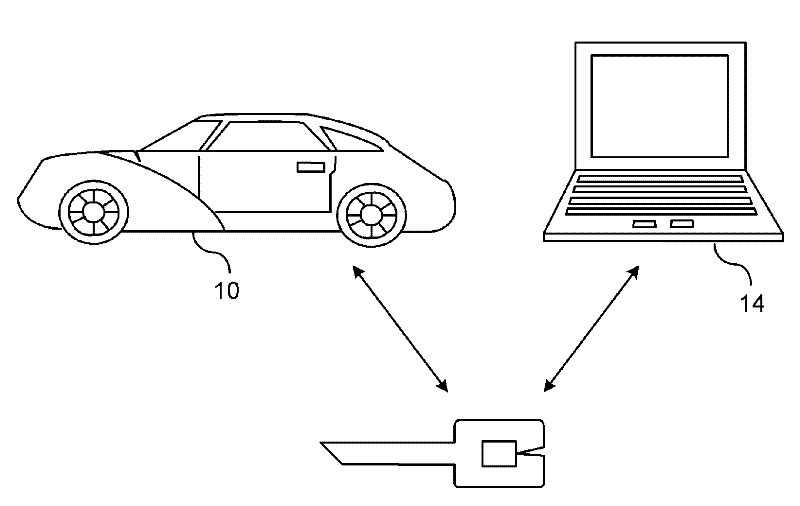
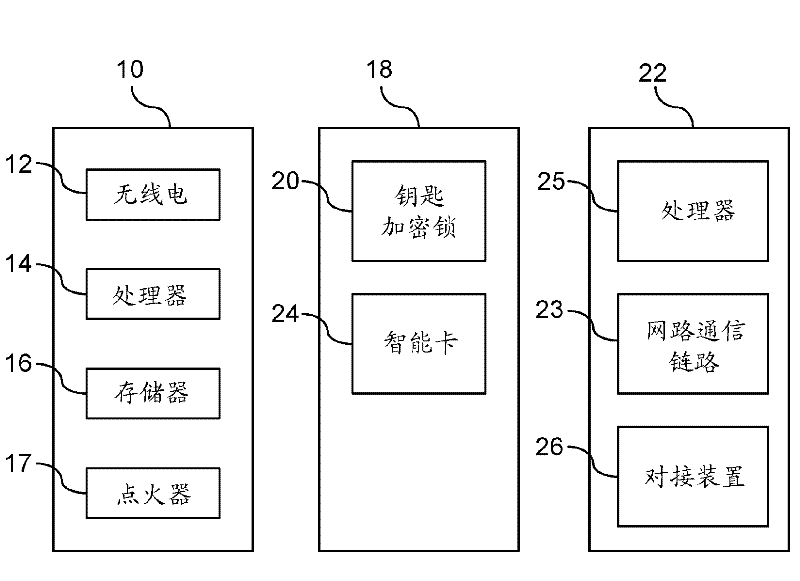
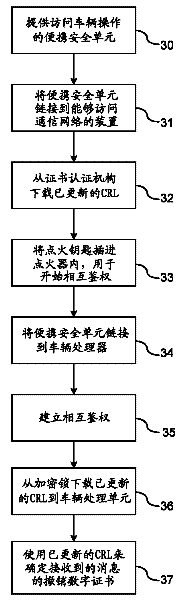
A method is provided for obtaining a certificate revocation list (CRL) for a vehicle in a vehicle-to-vehicle communication system. A portable security unit is provided to access secured operations for the vehicle. The portable security unit is linked to a device having access to a communication network. The communication network is in communication with a certificate authority for issuing an updated CRL. The updated CRL is downloaded from the certificate authority to the portable security unit. At a later time, when a user enters the vehicle, a communication link is established between the portable security unit and a vehicle processor unit. Mutual authentication is exchanged between the portable security unit and the vehicle processing unit. The updated CRL stored in the portable security unit is downloaded to a memory of the vehicle communication system in response to a successful mutual authentication.
Owner:GM GLOBAL TECH OPERATIONS LLC
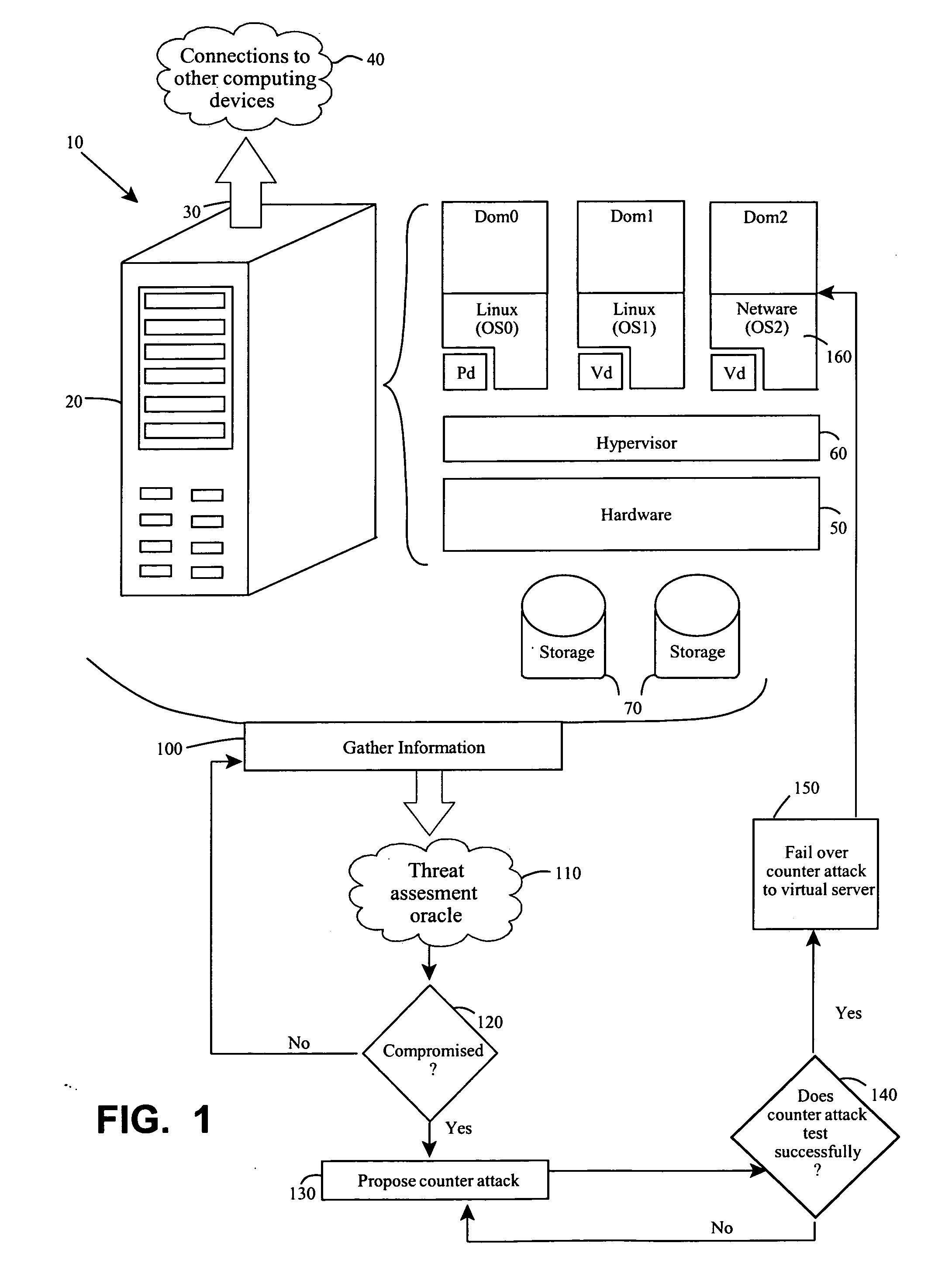
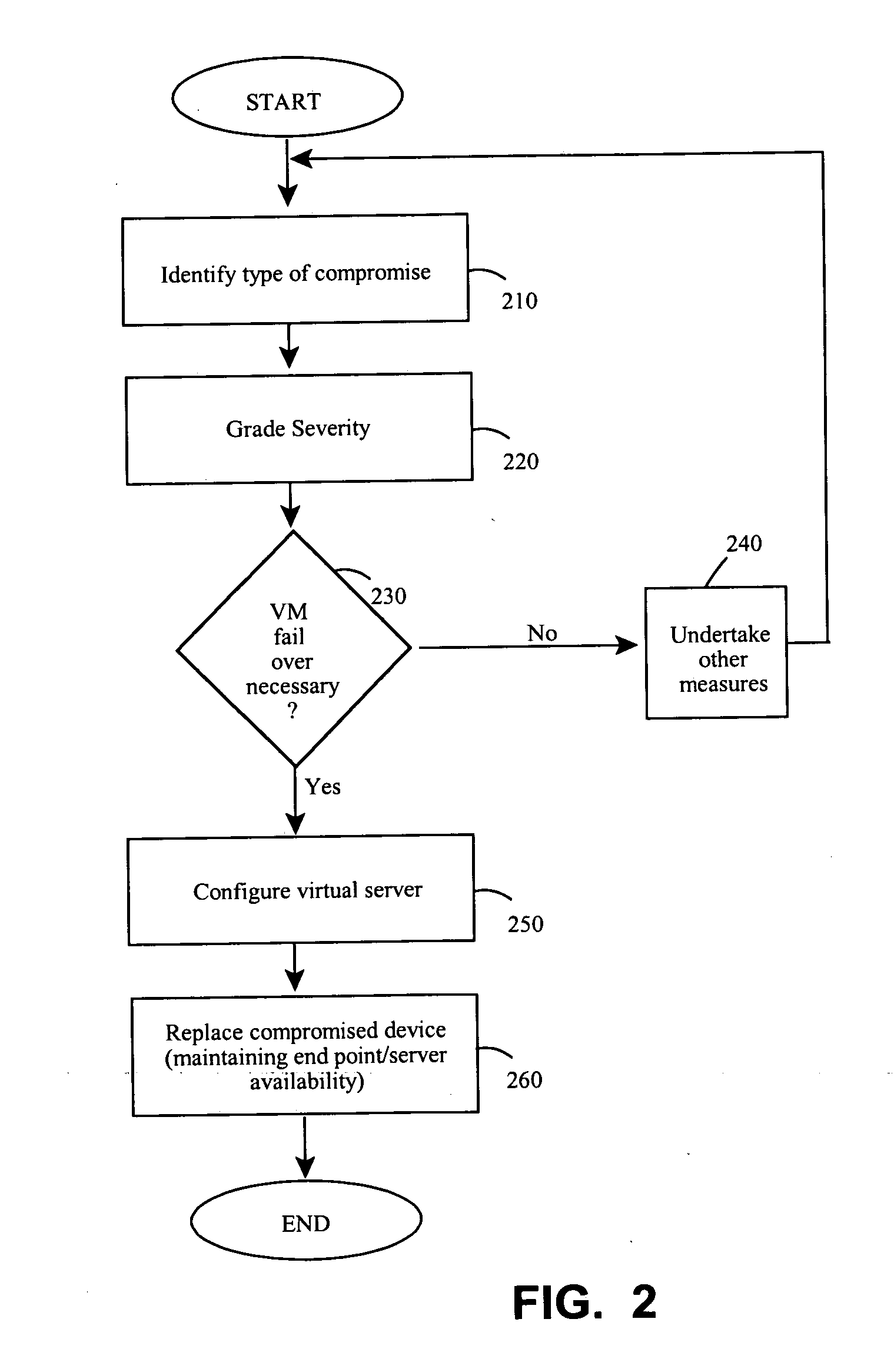
Endpoint security threat mitigation with virtual machine imaging
InactiveUS20110078797A1Quick changeMaintain availabilityMemory loss protectionError detection/correctionCountermeasureEndpoint security
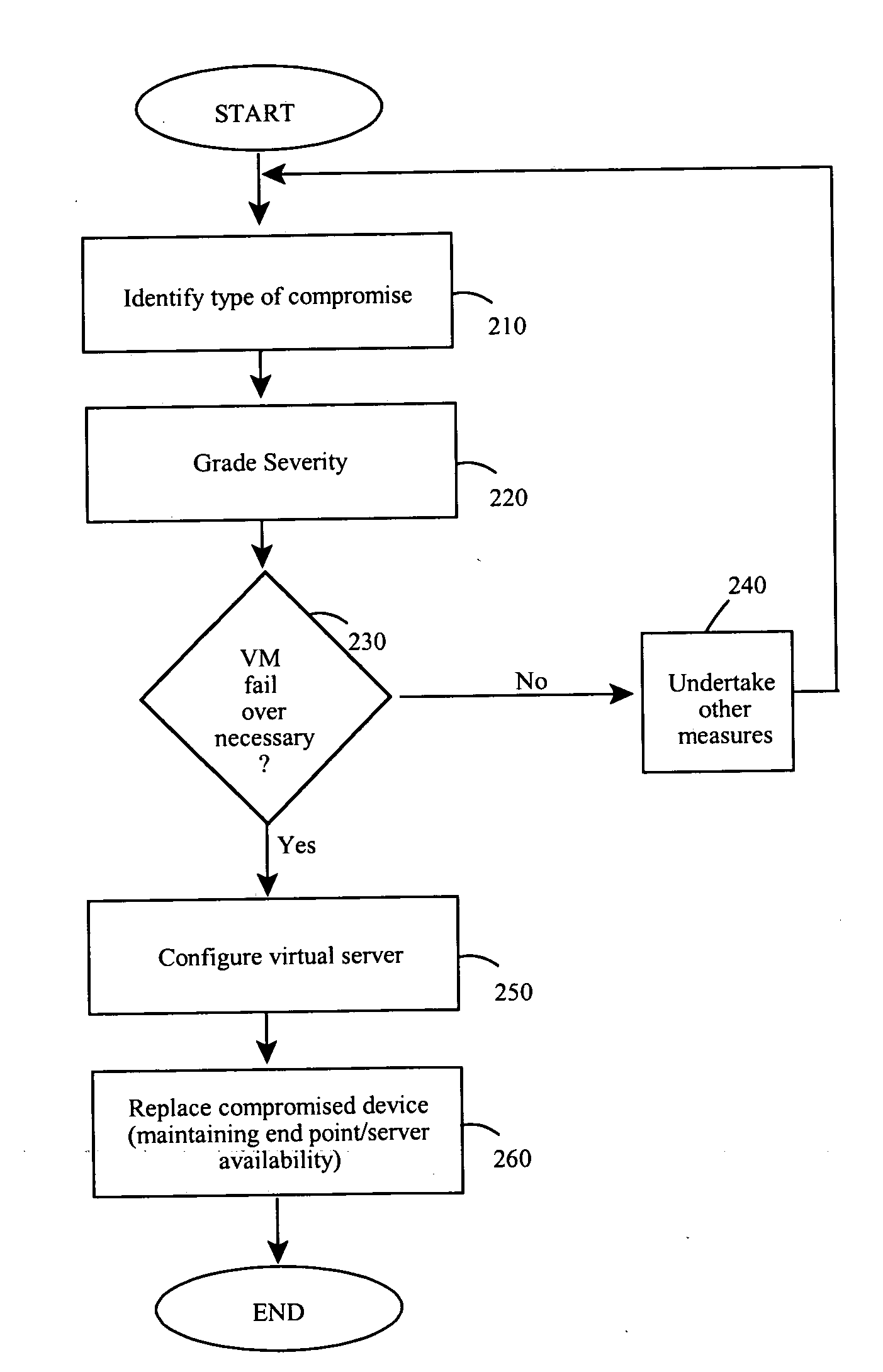
Methods and apparatus involve the mitigation of security threats at a computing endpoint, such as a server, including dynamic virtual machine imaging. During use, a threat assessment is undertaken to determine whether a server is compromised by a security threat. If so, a countermeasure to counteract the security threat is developed and installed on a virtual representation of the server. In this manner, the compromised server can be replaced with its virtual representation, but while always maintaining the availability of the endpoint in the computing environment. Other features contemplate configuration of the virtual representation from a cloned image of the compromised server at least as of a time just before the compromise and configuration on separate or same hardware platforms. Testing of the countermeasure to determine success is another feature as is monitoring data flows to identifying compromises, including types or severity. Computer program products and systems are also taught.
Owner:NOVELL INC
Dynamic threat event management system and method
ActiveUS20070192865A1Improve performanceImprove securityMemory loss protectionError detection/correctionInternet privacyPersonal computer
According to various illustrative embodiments of the present invention, a method for a content-driven threat management system includes creating a threat detection primary object with threat mitigation data using at least one researcher of at least one of software and malicious code, encoding the threat detection primary object with threat mitigation data within an object capable of being transmitted to a personal computer system using a transmission vector update function, and transmitting the threat detection primary object with threat mitigation data to a threat agent using the transmission vector update function. The method also includes updating at least one threat function using the threat agent to update at least one threat functional description of the at least one threat function to include the threat detection primary object with threat mitigation data, and using the threat detection primary object with threat mitigation data to be capable of recognizing at least one threat event based upon the threat detection primary object with threat mitigation data.
Owner:CA TECH INC
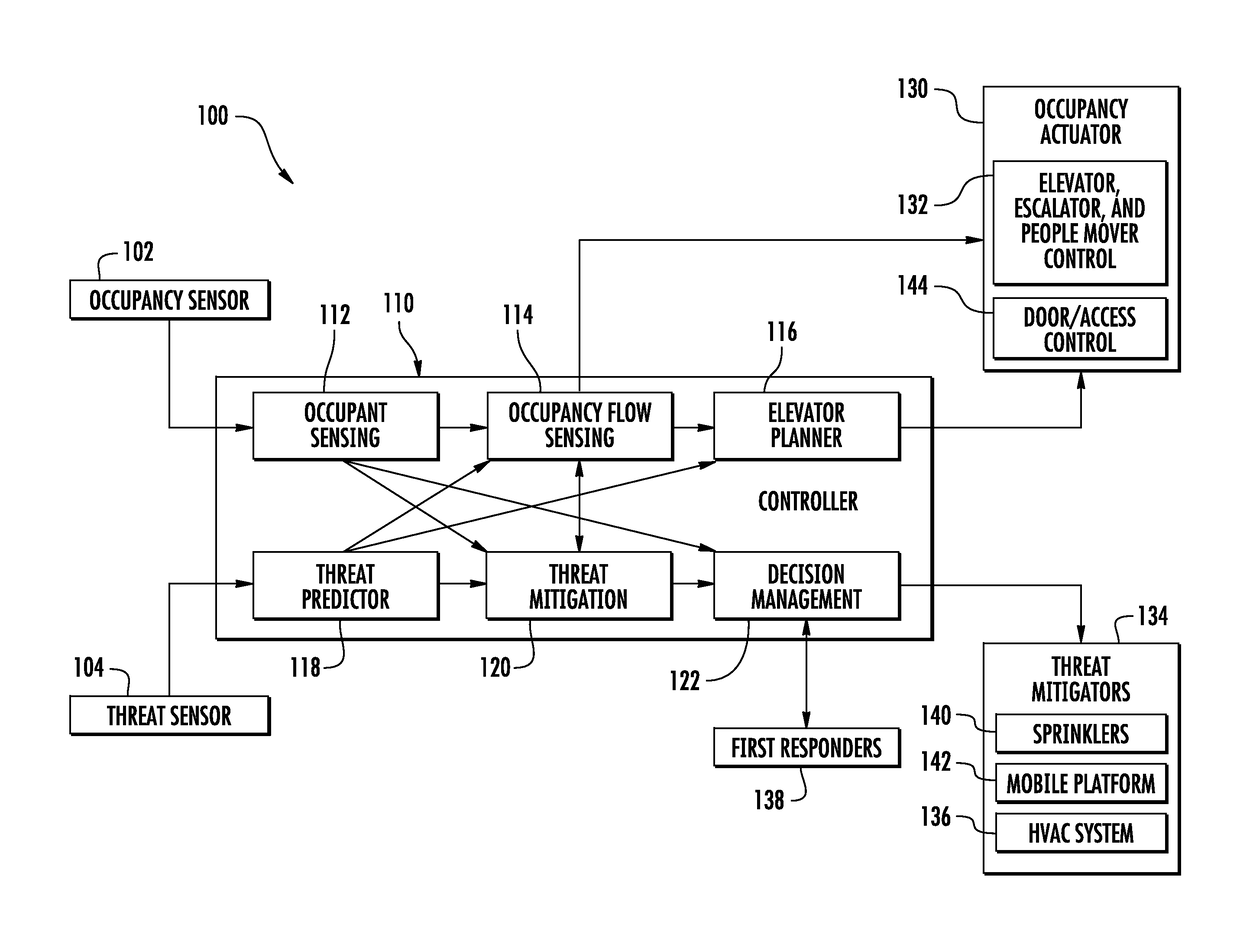
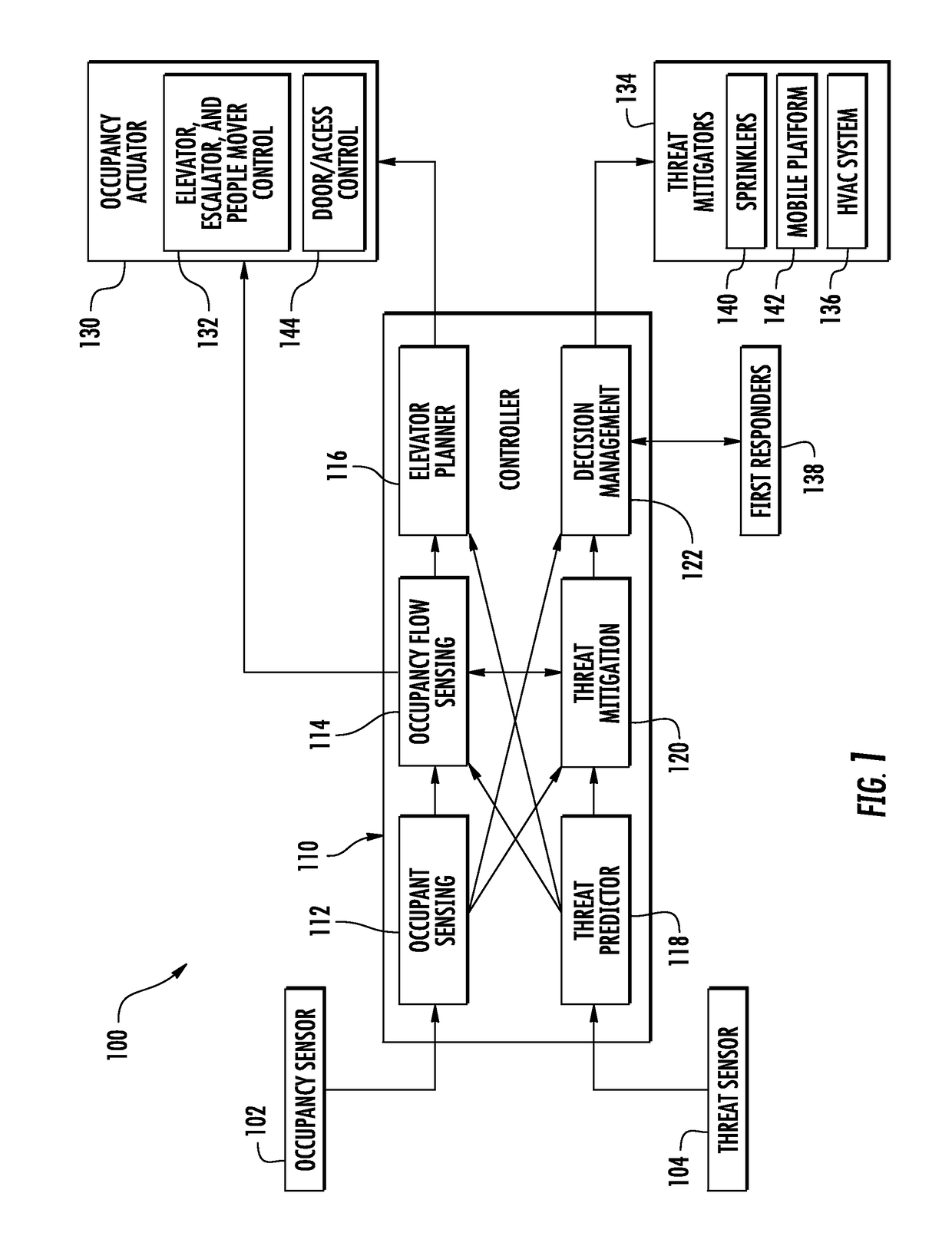
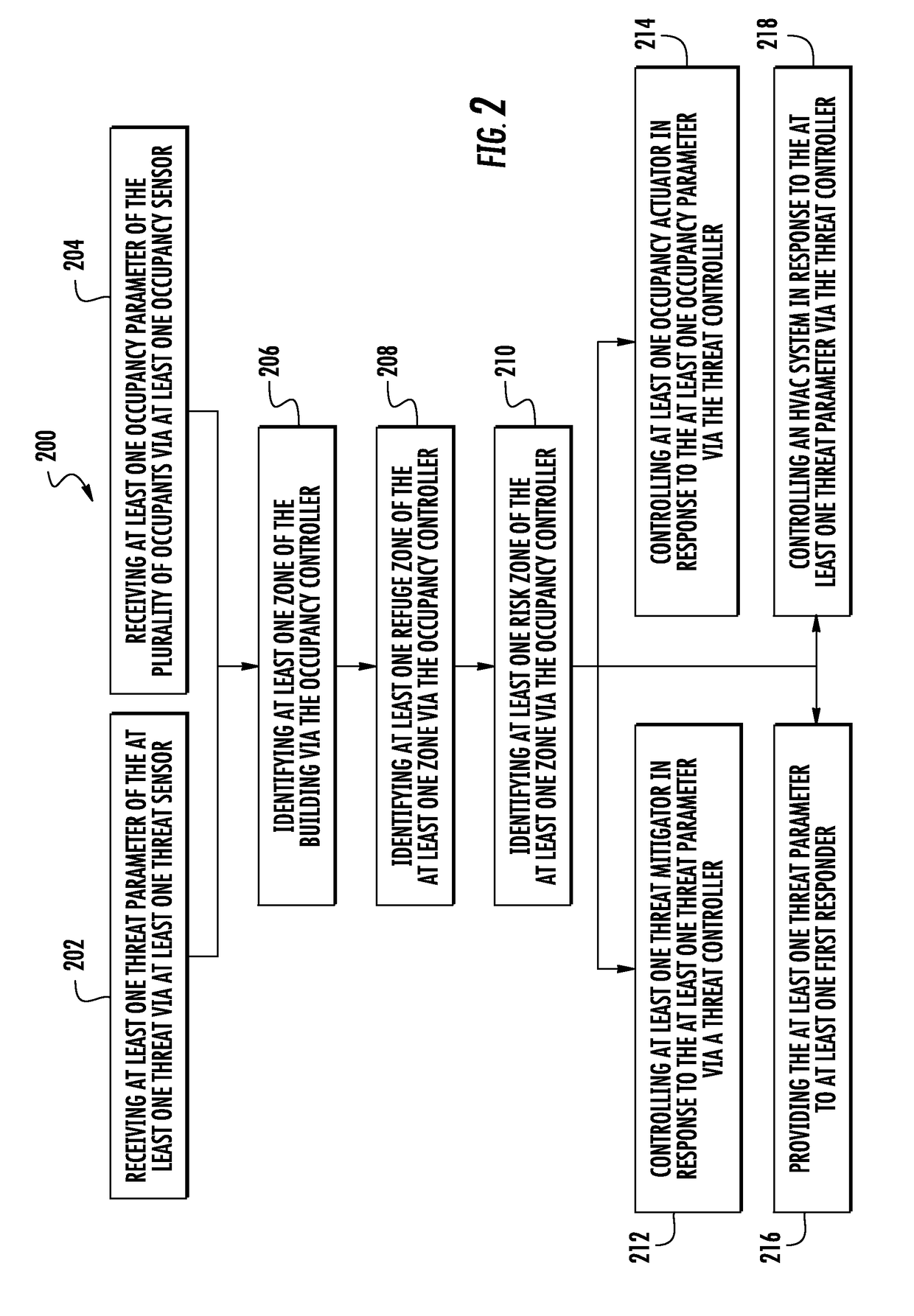
Active threat mitigation control system
InactiveUS20170103633A1Mechanical apparatusLighting and heating apparatusControl systemInternet privacy
A method and system to mitigate at least one threat associated with a building includes receiving at least one threat parameter of the at least one threat via at least one threat sensor, and actively controlling at least one threat mitigator in response to the at least one threat parameter via a threat controller.
Owner:OTIS ELEVATOR CO
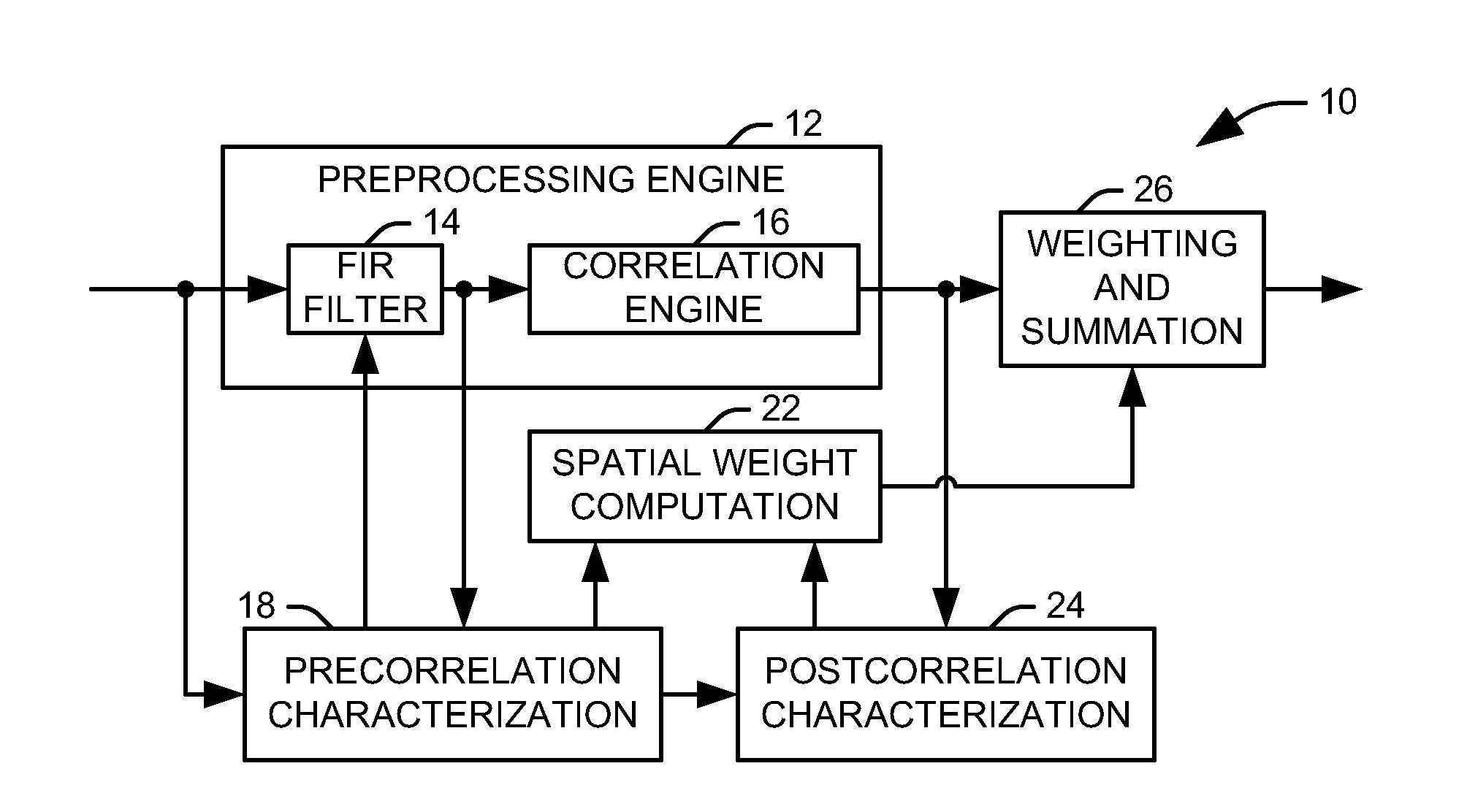
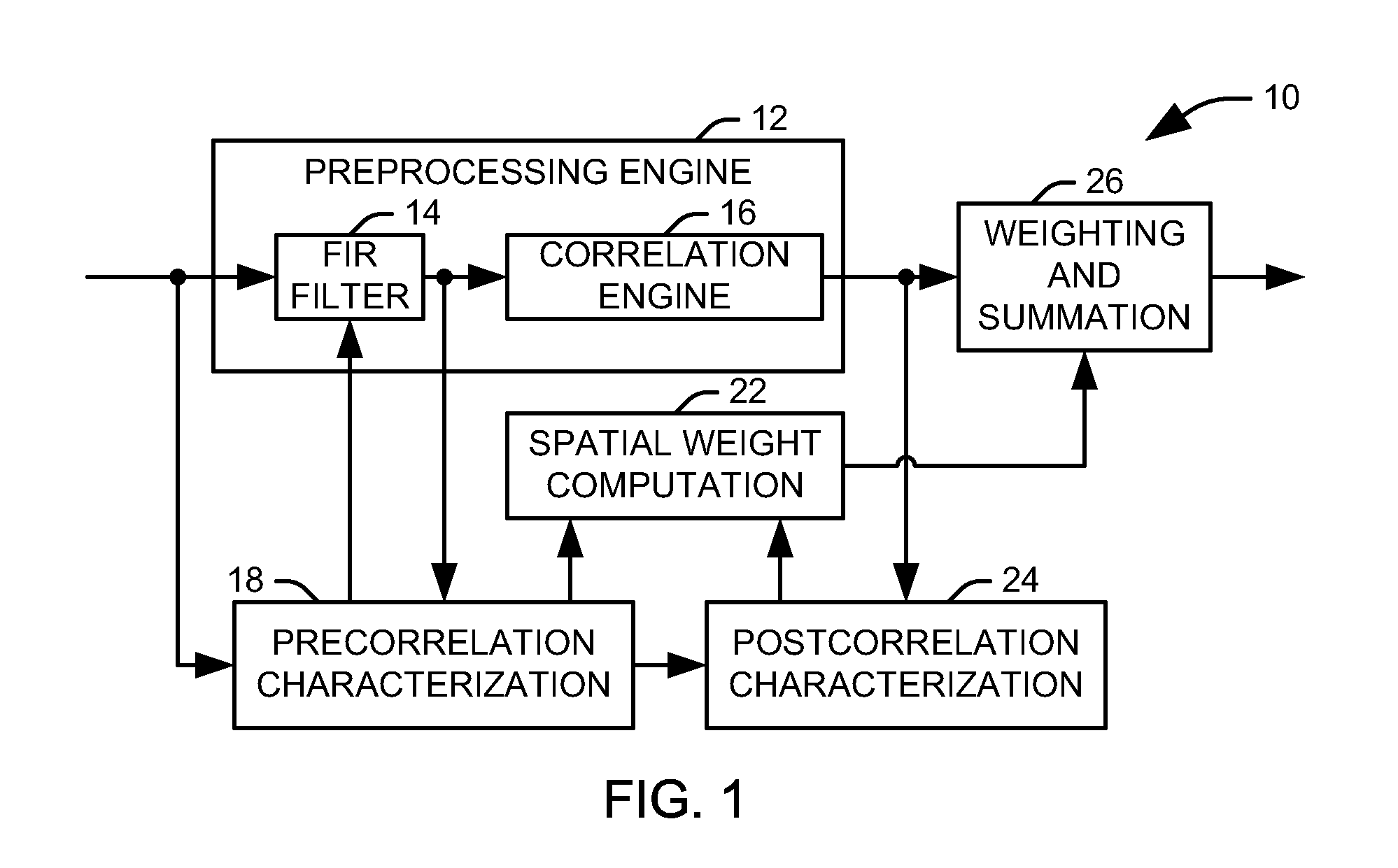
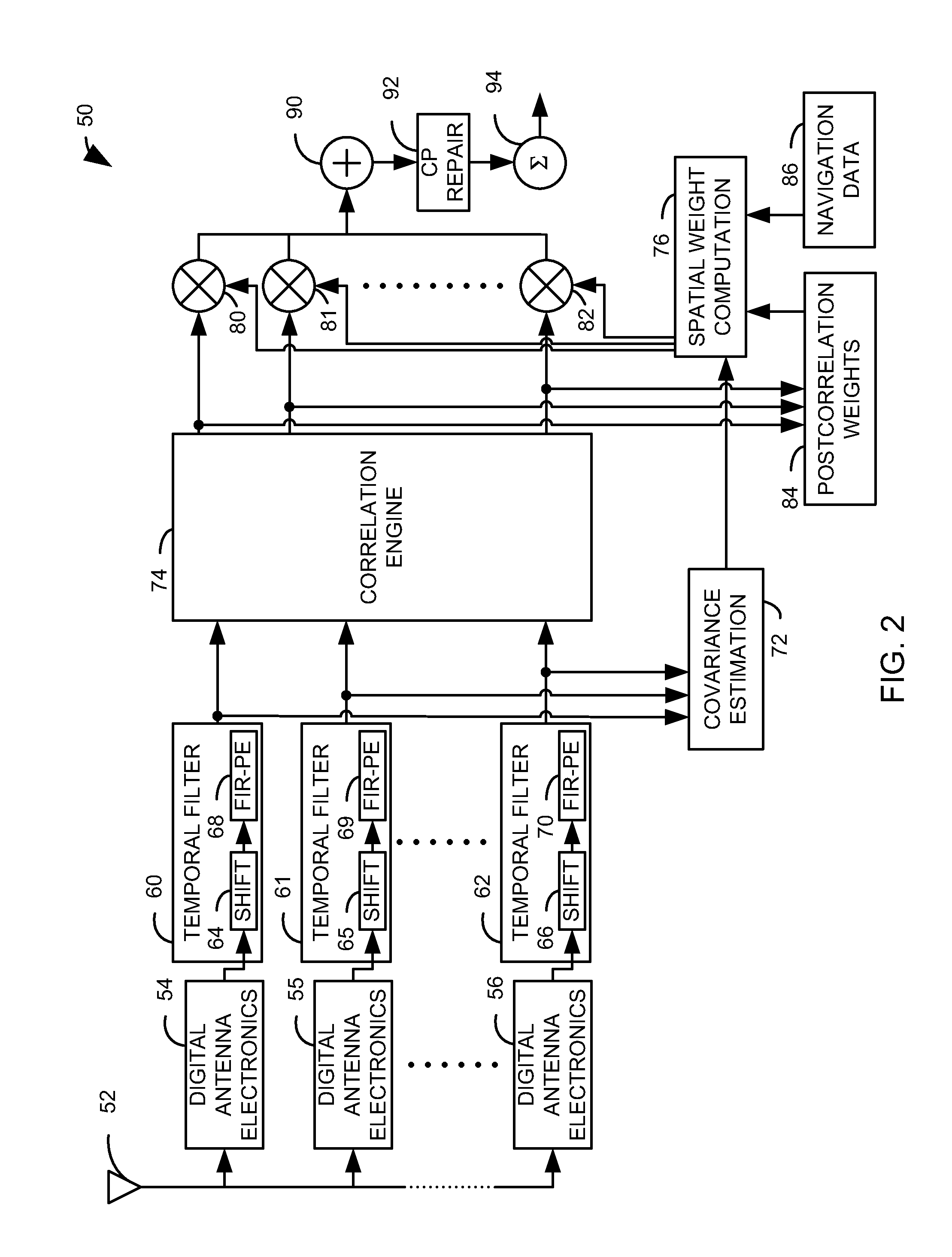
Digital beamforming for simultaneously mitigating weak and strong interference in a navigation system
ActiveUS20130154880A1Mitigate temporally correlated interferenceReduce distractionsSatellite radio beaconingEngineeringHandling system
An adaptive cascaded electronic protection processing system for global navigation satellite system (GNSS) threat mitigation is provided. The system includes a precorrelation characterization component configured to provide at least one parameter characterizing a plurality of received signals. A correlator is configured to provide a plurality of correlation results, each representing one of the plurality of received signals. A spatial weight contribution component is configured to determine an optimal set of digital beam-forming weights via an optimization process according to the at least one parameter. A postcorrelation characterization component is configured to determine at least one constraint on the optimization process according to the plurality of correlation results.
Owner:NORTHROP GRUMMAN GUIDANCE & ELECTRONICS
Advanced cybersecurity threat mitigation for inter-bank financial transactions
ActiveUS20180013771A1Reduce decreaseFinanceDesign optimisation/simulationCyber-attackFinancial transaction
A system for mitigation of cyberattacks employing an advanced cyber decision platform comprising a time series data store, a directed computational graph module, an action outcome simulation module, and observation and state estimation module, wherein the state of a network is monitored and used to produce a cyber-physical graph representing network resources, simulated network events are produced and monitored, and the network events and their effects are analyzed to produce security recommendations.
Owner:QOMPLX LLC
Policy-based network security
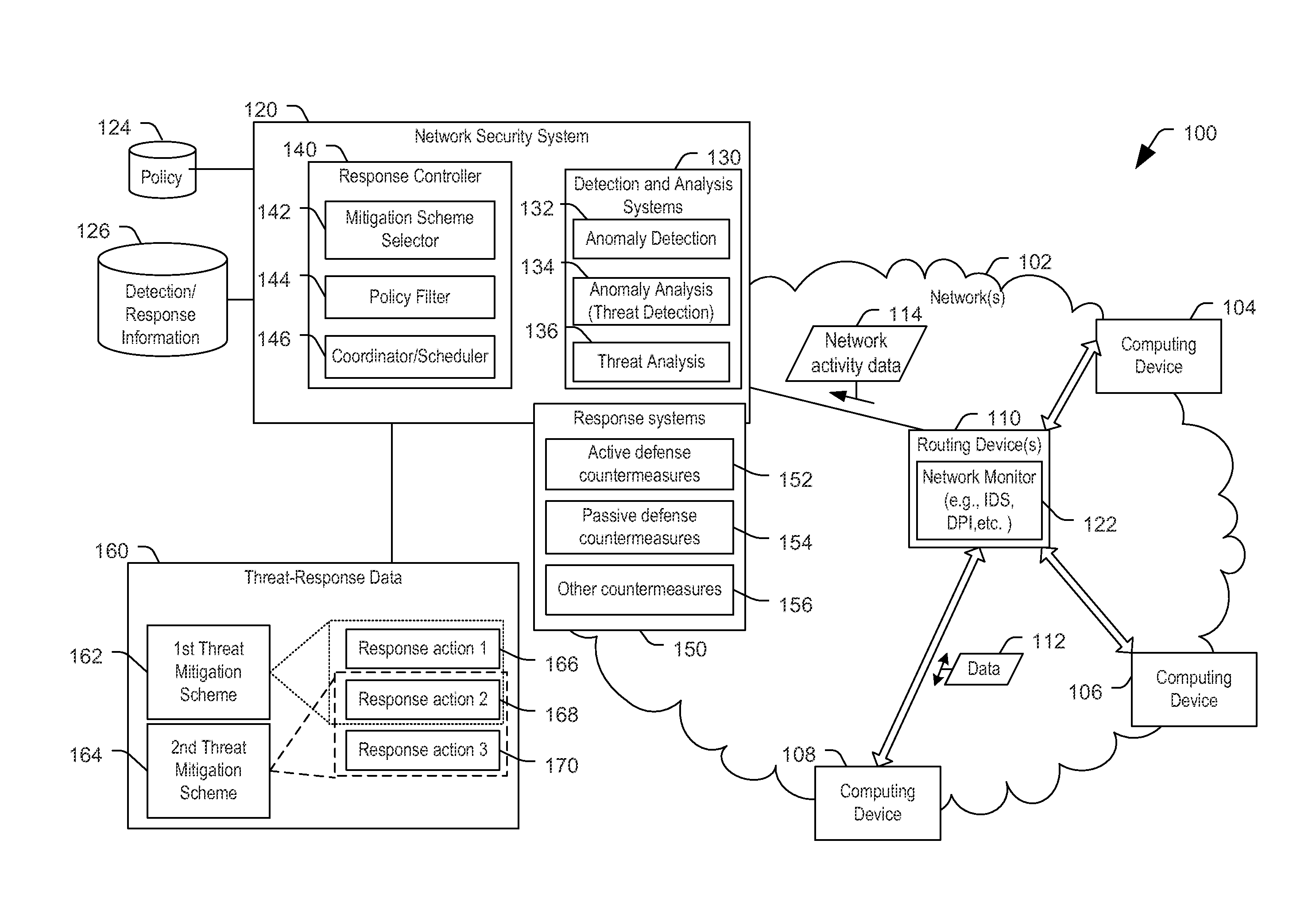
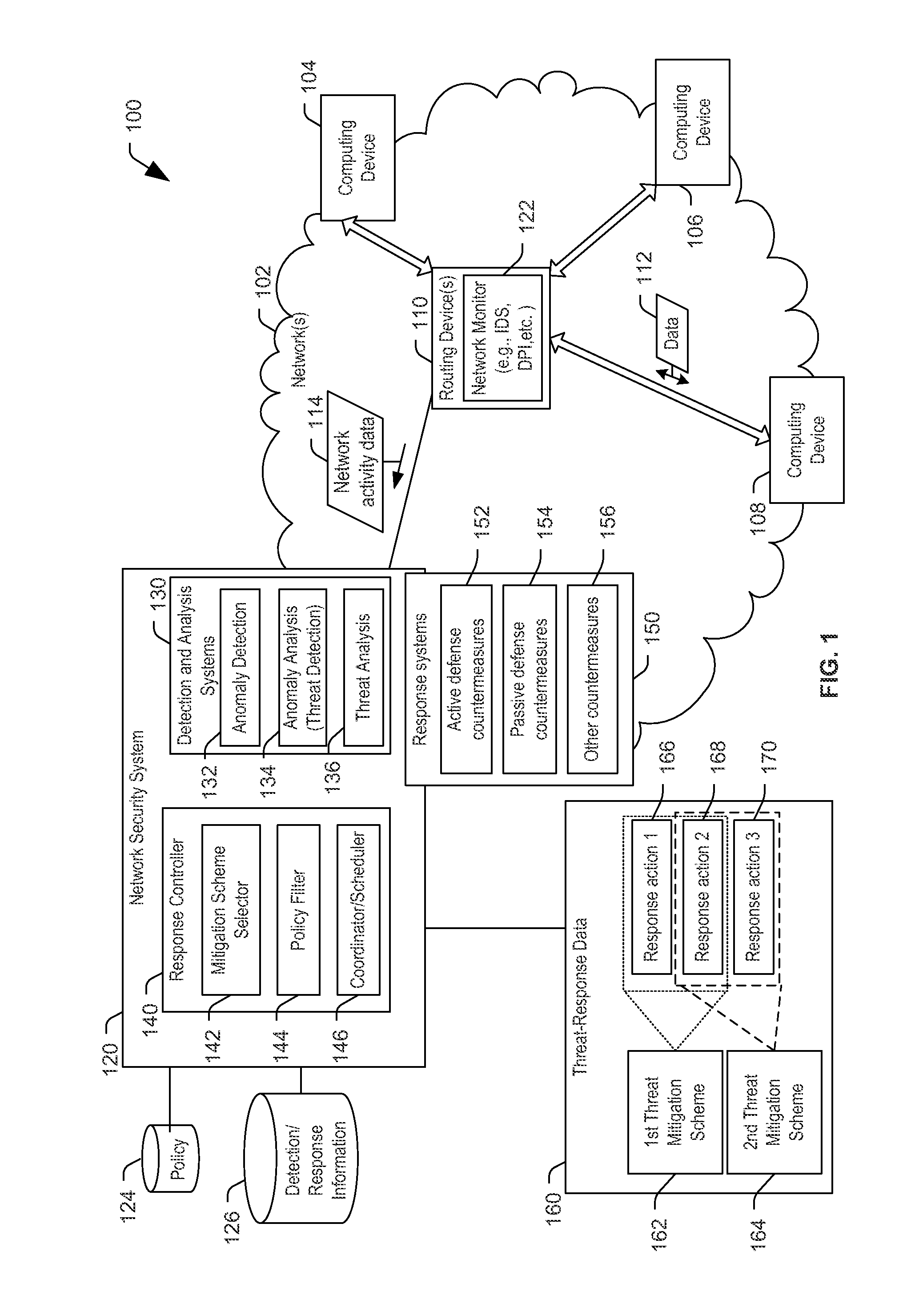
ActiveUS20160182559A1TransmissionSpecial data processing applicationsNetwork activityNetwork security policy
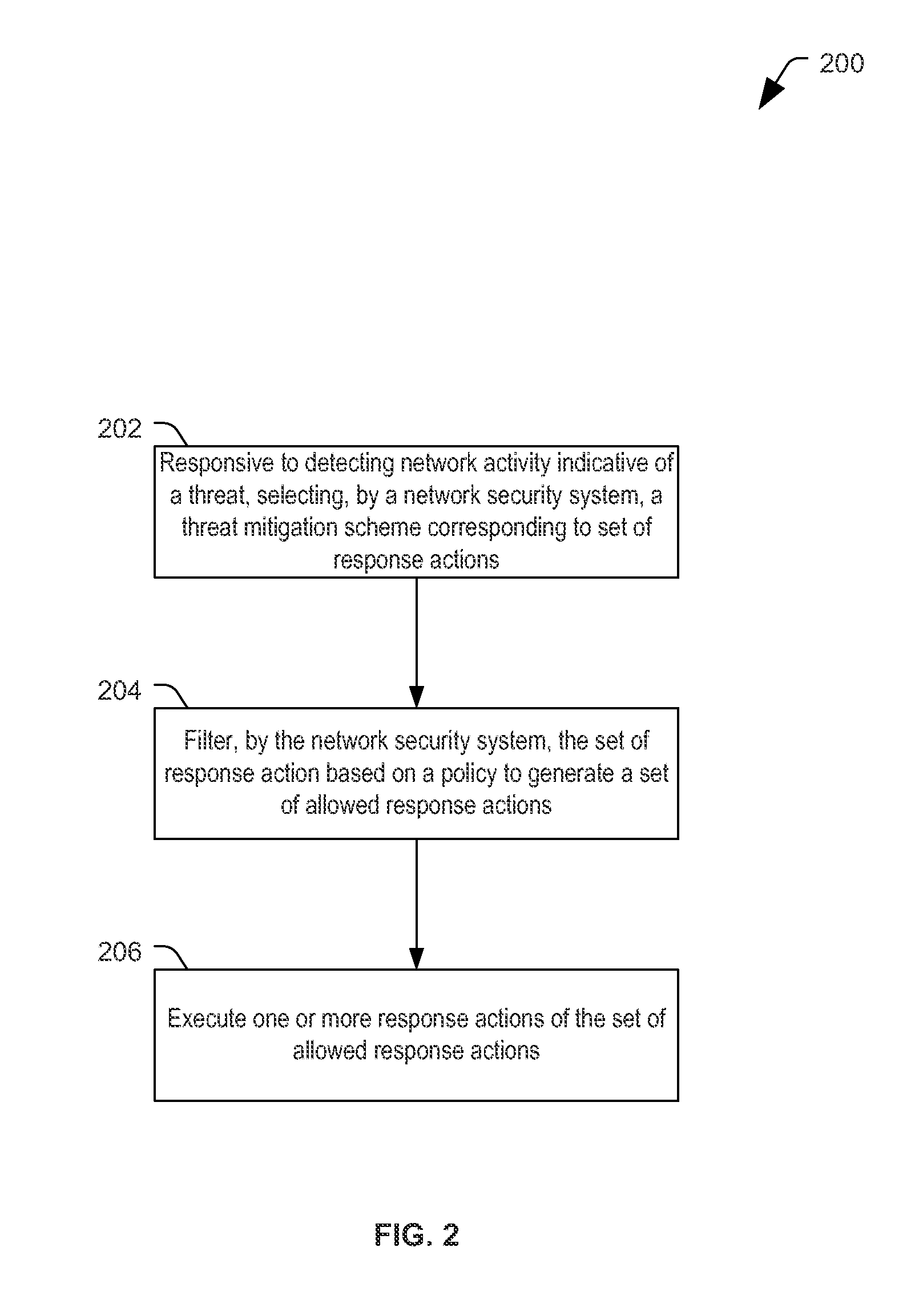
A method includes, responsive to detecting network activity indicative of a threat, selecting a threat mitigation scheme corresponding to a set of response actions. The method also include filtering the set of response actions based on a policy to generate a set of allowed response actions and executing one or more response actions of the set of allowed response actions.
Owner:THE BOEING CO
Host behavior and network analytics based automotive secure gateway
ActiveUS20190104108A1Particular environment based servicesIn-vehicle communicationAnomalous behaviorAutomobile safety
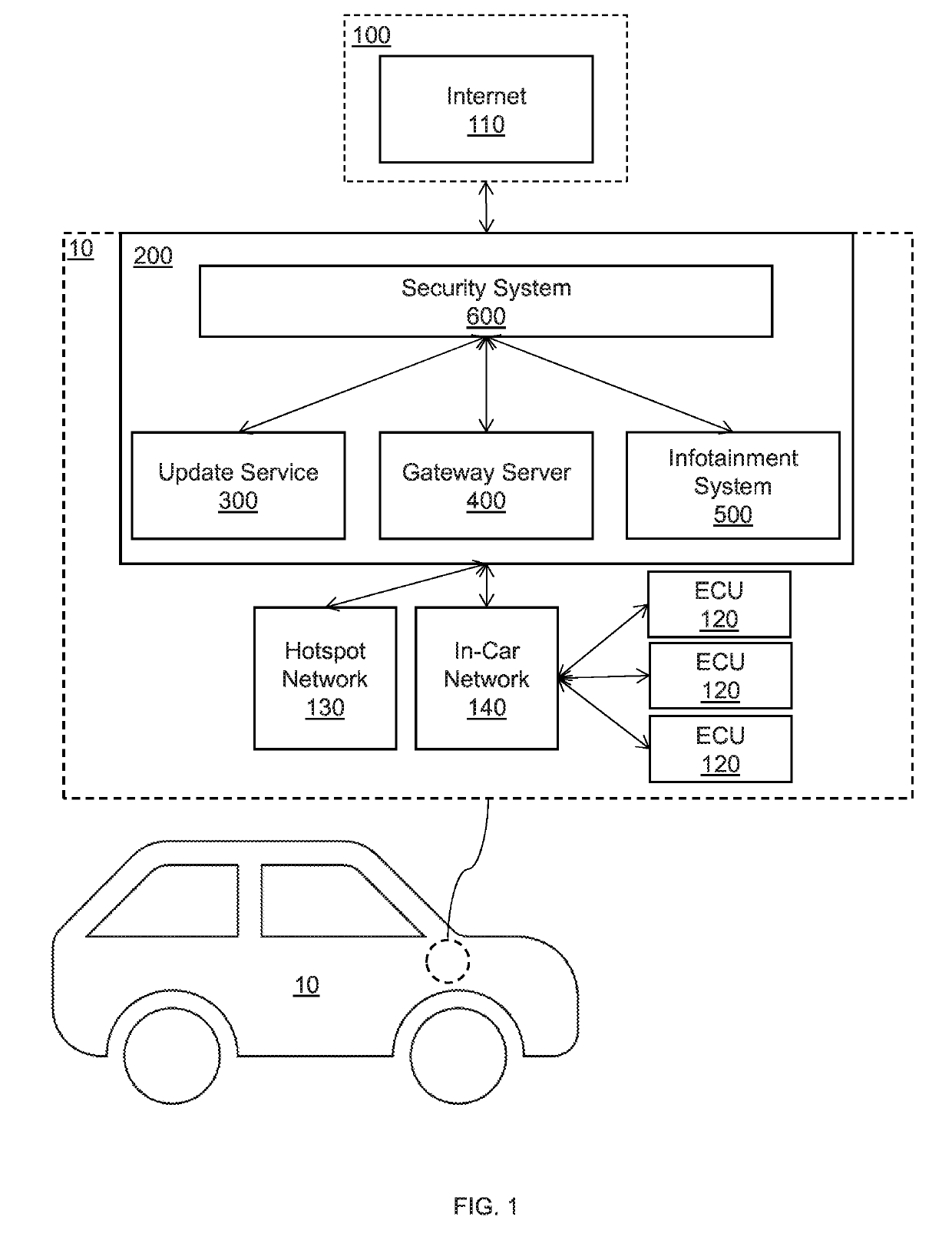
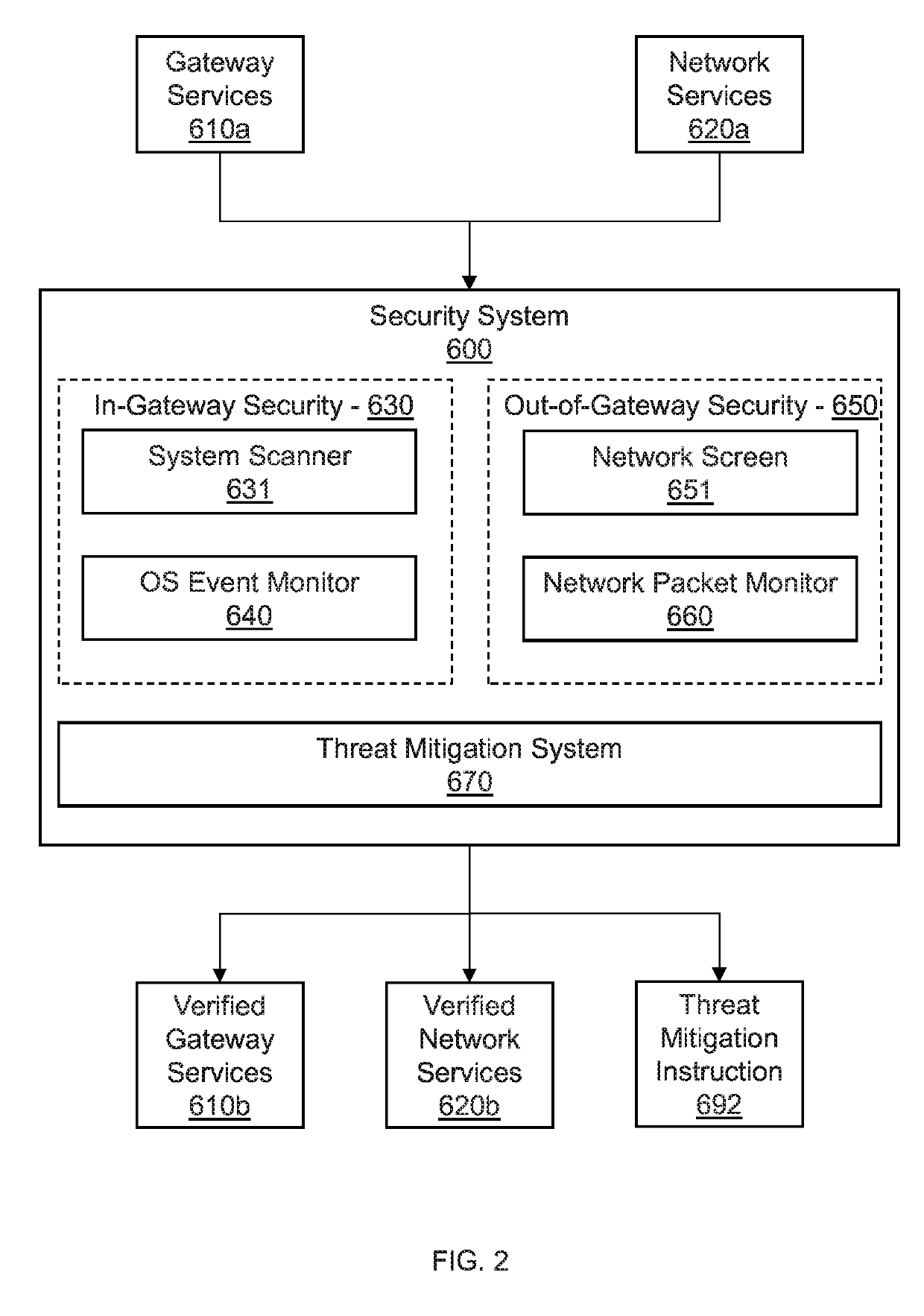
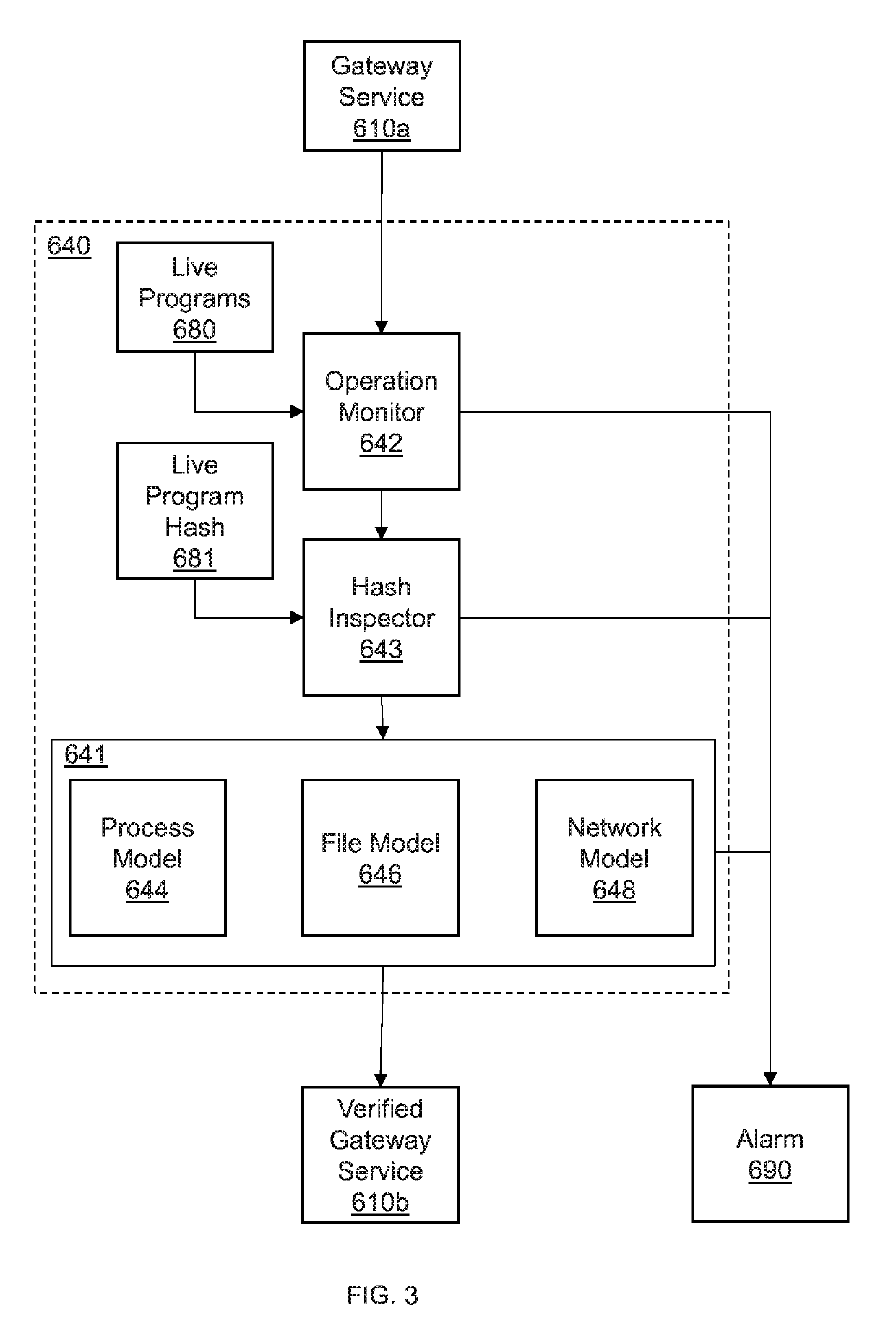
Systems and methods for an automotive security gateway include an in-gateway security system that monitors local host behaviors in vehicle devices to identify anomalous local host behaviors using a blueprint model trained to recognize secure local host behaviors. An out-of-gateway security system monitors network traffic across remote hosts, local devices, hotspot network, and in-car network to identify anomalous behaviors using deep packet inspection to inspect packets of the network. A threat mitigation system issues threat mitigation instructions corresponding to the identified anomalous local host behaviors and the anomalous remote host behaviors to secure the vehicle devices by removing the identified anomalous local host behaviors and the anomalous remote host behaviors. Automotive security gateway services and vehicle electronic control units operate the vehicle devices according to the threat mitigation instructions.
Owner:NEC CORP
Suicide bomber blast threat mitigation system
InactiveUS20110271825A1Disabling suspectReduce harmAmmunition projectilesBlastingShock waveEngineering
A non-lethal, sabot-deployed blast shield mitigates a suicide bomber by wrapping around the bomber and positioning a plurality of protective layers over an explosive device to absorb emitted heat, shock waves, and projectiles if the device is detonated. Stand-offs such as inflatable beams or pillows provide break-away zones between the protective layers, allowing some layers to expand to a point of failure and absorb the maximum possible energy. Inner layers absorb shock waves and heat. One or more outer layers resist projectile penetration. Protective layers can be positioned on opposing sides of a suspect in case two explosive devices are present. Shields can deploy with sufficient energy to knock down a bomber. In embodiments, a plurality of shields can be applied without interference therebetween. In some embodiments, a round shield includes bolas which spread the shield in flight in a cast-net dynamic and wrap around the suspect for shield attachment.
Owner:WARWICK MILLS INC
Predictive malware threat mitigation
ActiveCN102542198AReduce accessReduce riskPlatform integrity maintainanceTransmissionVirtualizationRisk level
Owner:MICROSOFT TECH LICENSING LLC
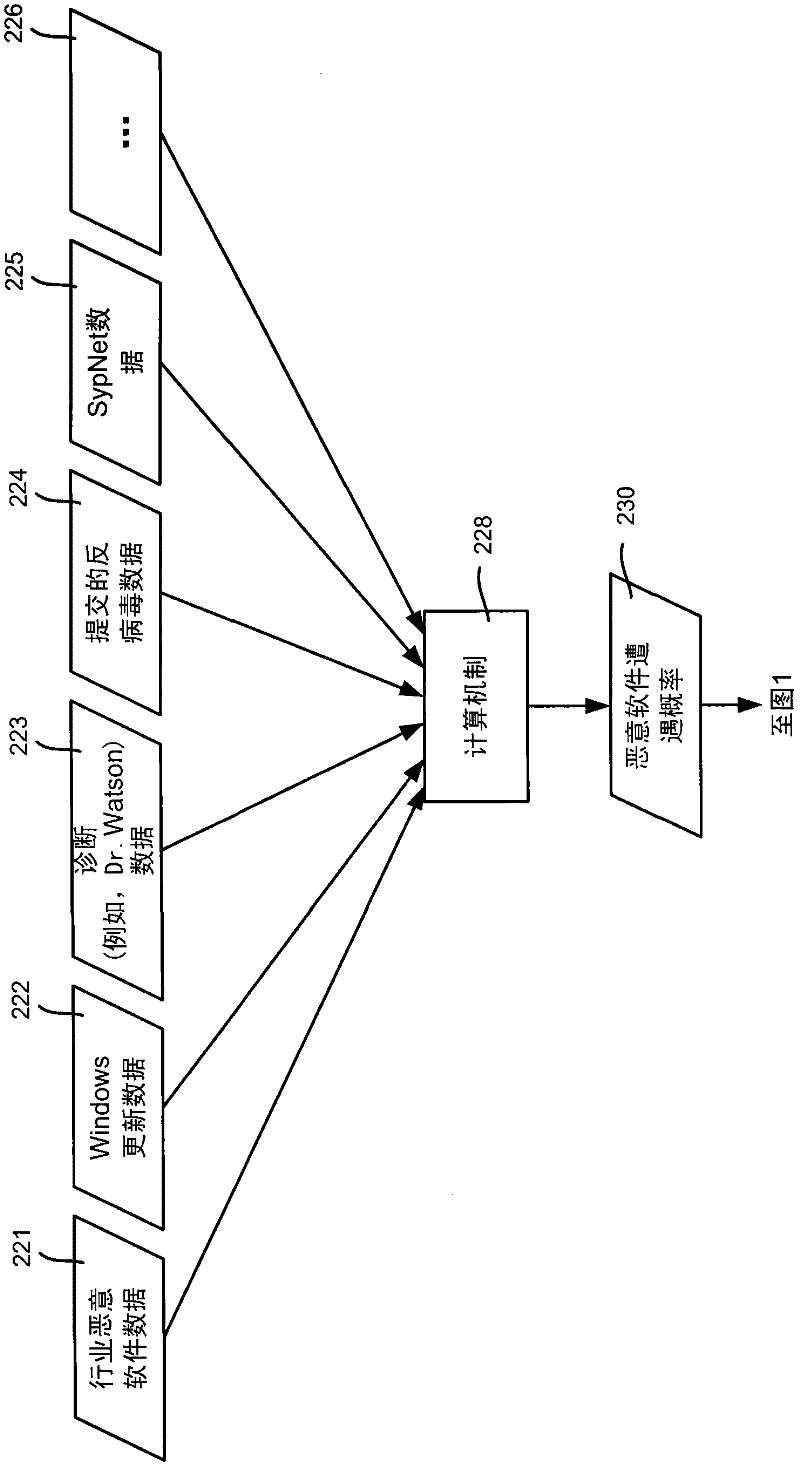
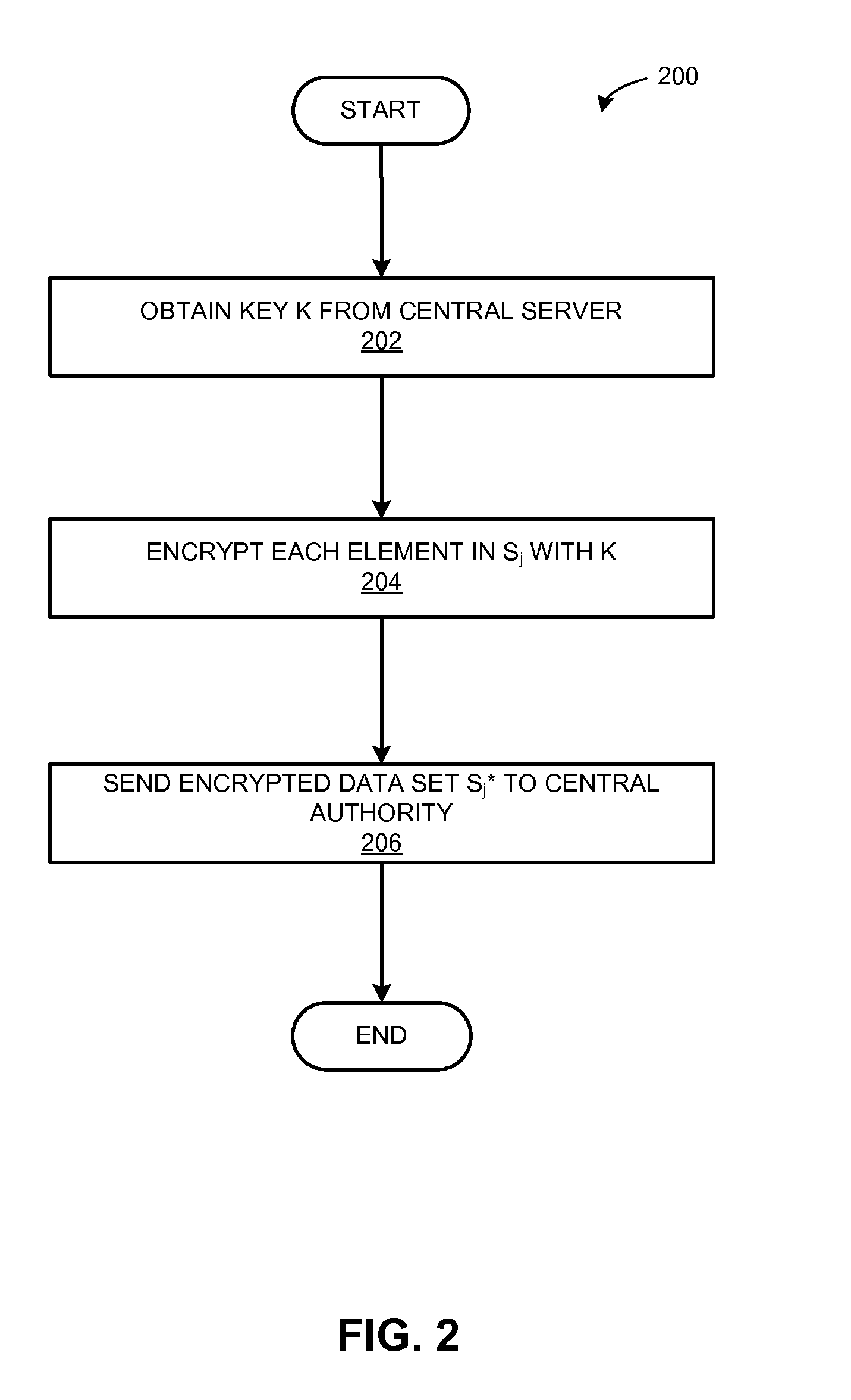
Methods for centralized privacy-preserving collaborative threat mitigation
ActiveUS20150286825A1Promote collaborationNetwork degradationKey distribution for secure communicationDigital data processing detailsPattern recognitionData set
One embodiment of the present invention provides a system to facilitate collaboration for mitigating network threats. During operation, the system receives encrypted data sets from a plurality of entities. The data sets including data describing threats to network security. The system performs privacy-preserving operations on the encrypted data sets, such as private set intersection. The system then computes one or more metrics based on results of the private set intersection computations. The system may generate a similarity matrix based on the one or more metrics, and returns one or more similarity values from the similarity matrix to one or more entities of the plurality of entities.
Owner:XEROX CORP
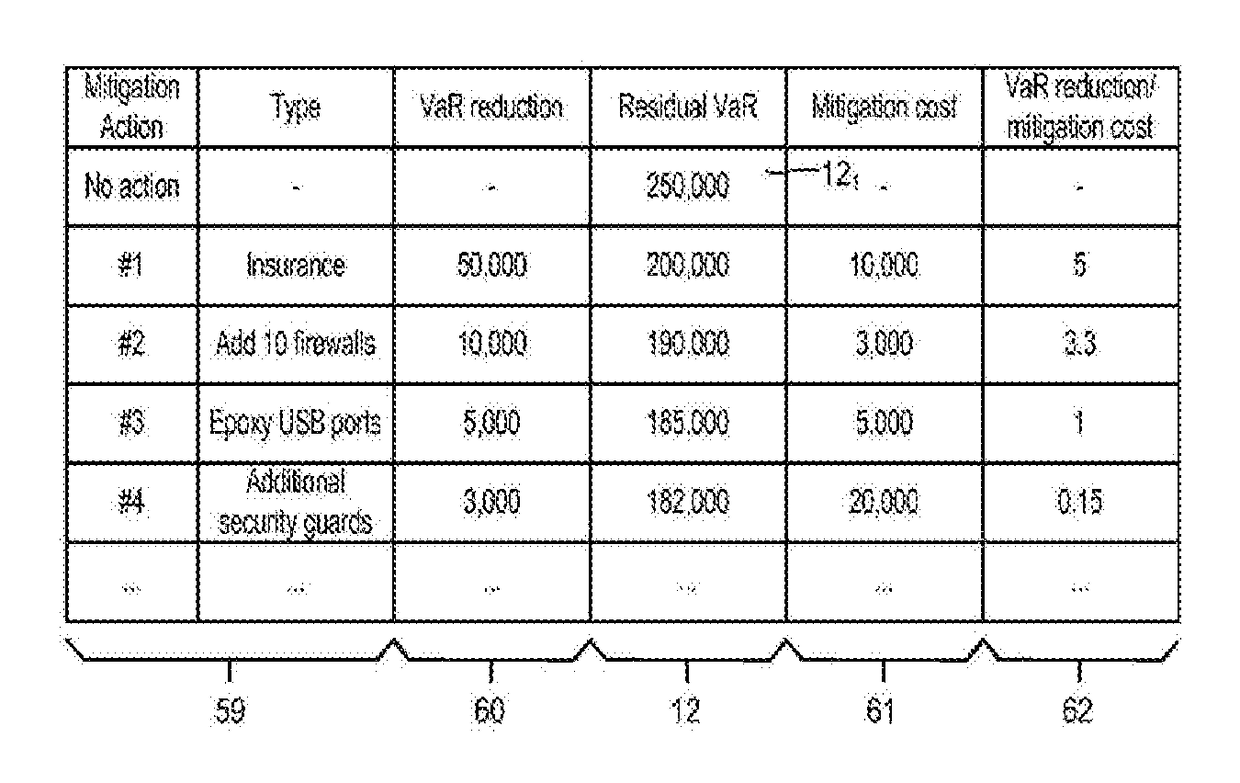
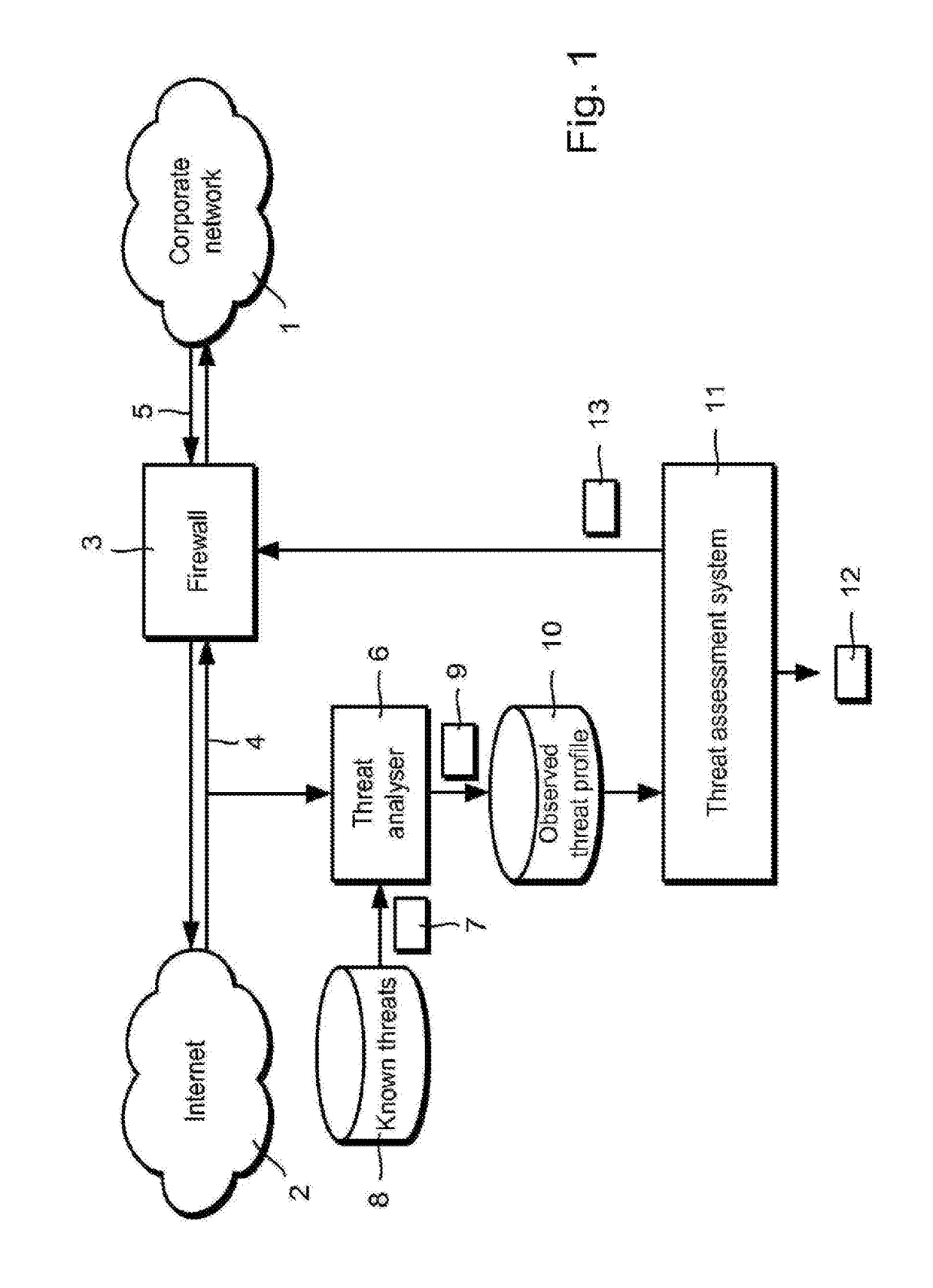
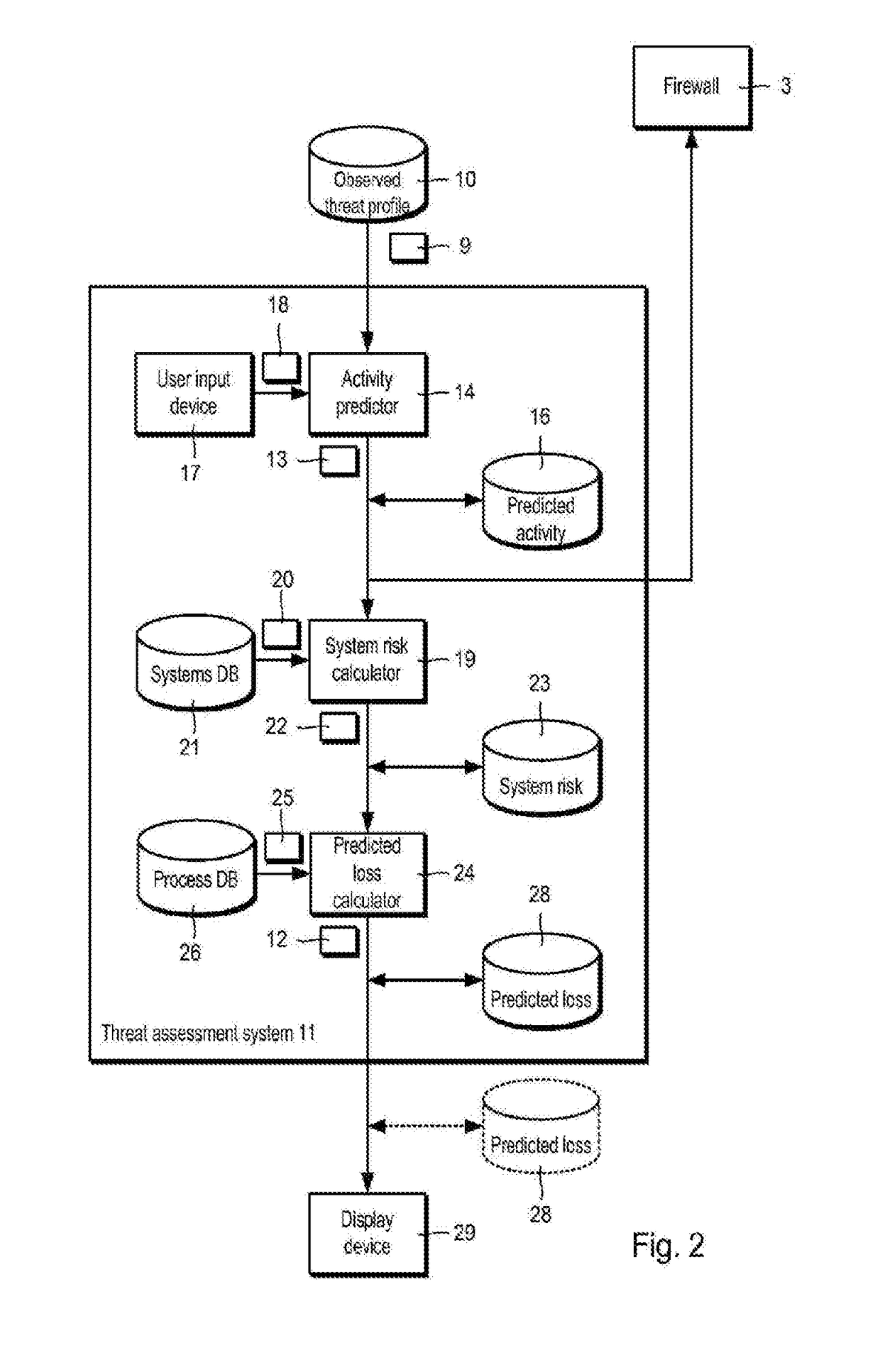
Assessing and Managing Cyber Threats
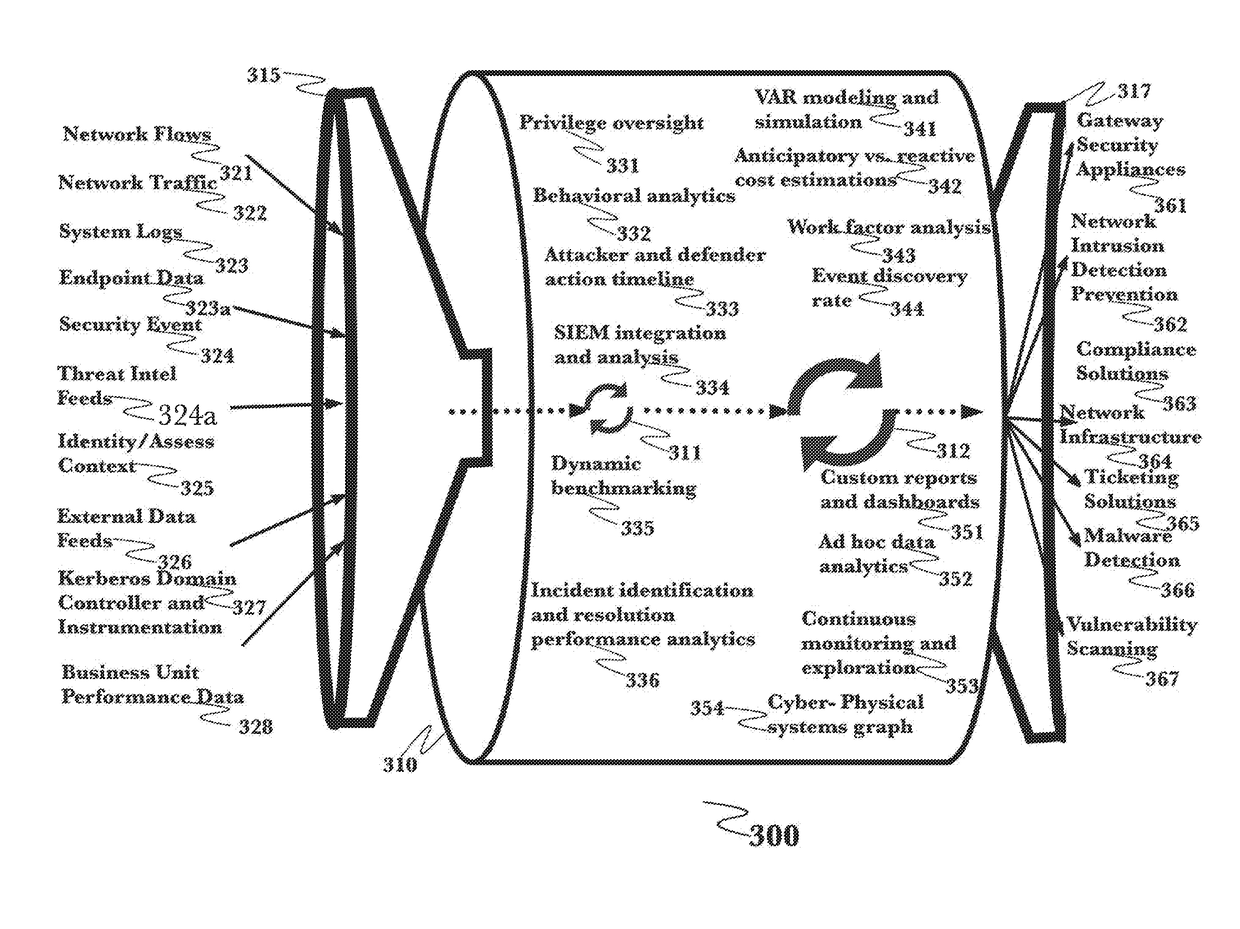
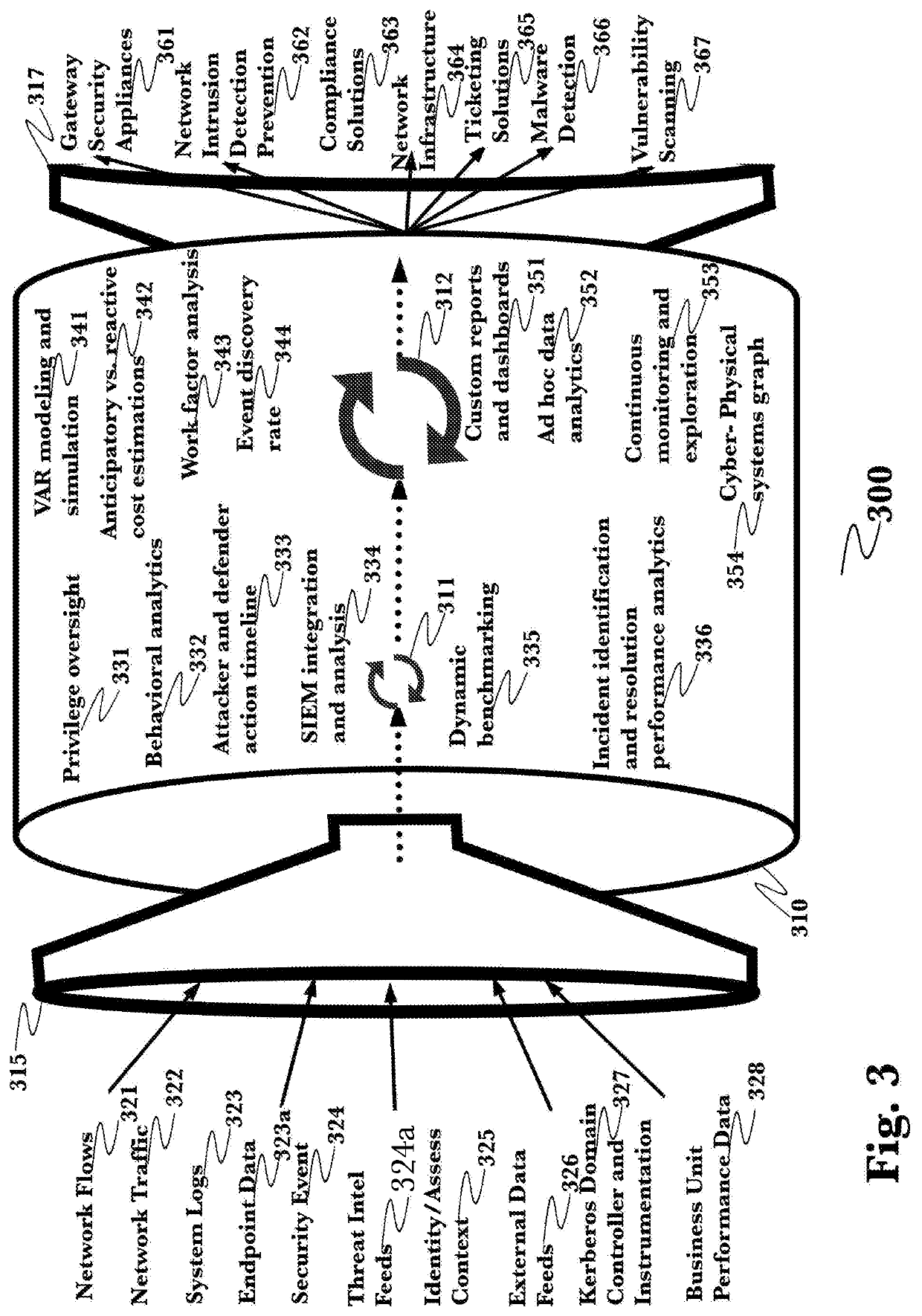
Methods, systems and apparatus, including computer programs encoded on a computer storage medium, for assessing and managing cyber threats. In some implementations, data specifying relationships between I.T. system infrastructures, system categories, operational processes, computer-based threats and mitigation actions is received. A plurality of simulations are performed using a Monte Carlo method, with each simulation involving propagating data through stochastic modeling for a given time window having a beginning and end. Outcomes of the plurality of simulations that include mitigating actions representing the threat mitigation measures of the organization, for a given time window, determine a measure of impact of cyber threats to the organization. The determined measure is provided for output to a user.
Owner:QUANTAR SOLUTIONS
Threat mitigation in a vehicle-to-vehicle communication network
A method is provided for obtaining a certificate revocation list (CRL) for a vehicle in a vehicle-to-vehicle communication system. A portable security unit is provided to access secured operations for the vehicle. The portable security unit is linked to a device having access to a communication network. The communication network is in communication with a certificate authority for issuing an updated CRL. The updated CRL is downloaded from the certificate authority to the portable security unit. At a later time, when a user enters the vehicle, a communication link is established between the portable security unit and a vehicle processor unit. Mutual authentication is exchanged between the portable security unit and the vehicle processing unit. The updated CRL stored in the portable security unit is downloaded to a memory of the vehicle communication system in response to a successful mutual authentication.
Owner:GM GLOBAL TECH OPERATIONS LLC
Dynamic threat event management system and method
InactiveUS9167000B2Improve performanceImprove securityMemory loss protectionError detection/correctionPersonal computerManagement system
According to various illustrative embodiments of the present invention, a method for a content-driven threat management system includes creating a threat detection primary object with threat mitigation data using at least one researcher of at least one of software and malicious code, encoding the threat detection primary object with threat mitigation data within an object capable of being transmitted to a personal computer system using a transmission vector update function, and transmitting the threat detection primary object with threat mitigation data to a threat agent using the transmission vector update function. The method also includes updating at least one threat function using the threat agent to update at least one threat functional description of the at least one threat function to include the threat detection primary object with threat mitigation data, and using the threat detection primary object with threat mitigation data to be capable of recognizing at least one threat event based upon the threat detection primary object with threat mitigation data.
Owner:CA TECH INC
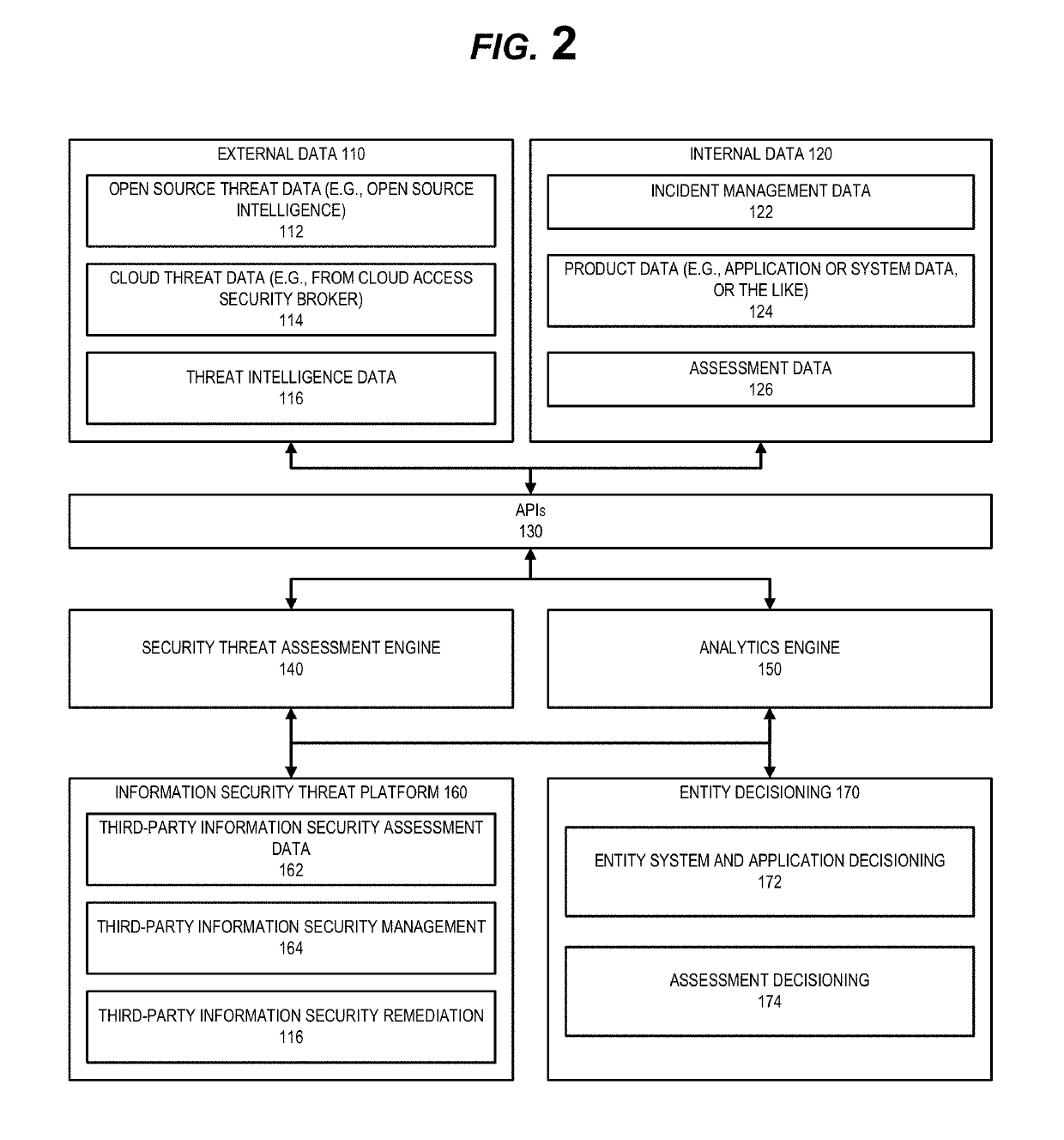
System for information security threat assessment based on data history
The invention utilizes a two-component system to detect third party security threats and drive improved security threat mitigation based on the detection. The first component of the system is a security threat assessment engine, which receives and / or identifies external data and internal data regarding third parties in order to determine information security threats posed by third parties. The second component of the system is an analytics engine, which may comprise a machine learning component which is configured to detect threat patterns and anomalies. In response to the detection of the threat patterns and anomalies the security threat assessment engine may be modified in order to more accurately determine security threats.
Owner:BANK OF AMERICA CORP
Threat mitigation system and method
A computer-implemented method, computer program product and computing system for: allowing a third-party to select a training routine for a specific attack of a computing platform, thus defining a selected training routine; analyzing the requirements of the selected training routine to determine a quantity of entities required to effectuate the selected training routine, thus defining one or more required entities; generating one or more virtual machines to emulate the one or more required entities; and generating a simulation of the specific attack by executing the selected training routine.
Owner:RELIAQUEST HLDG LLC
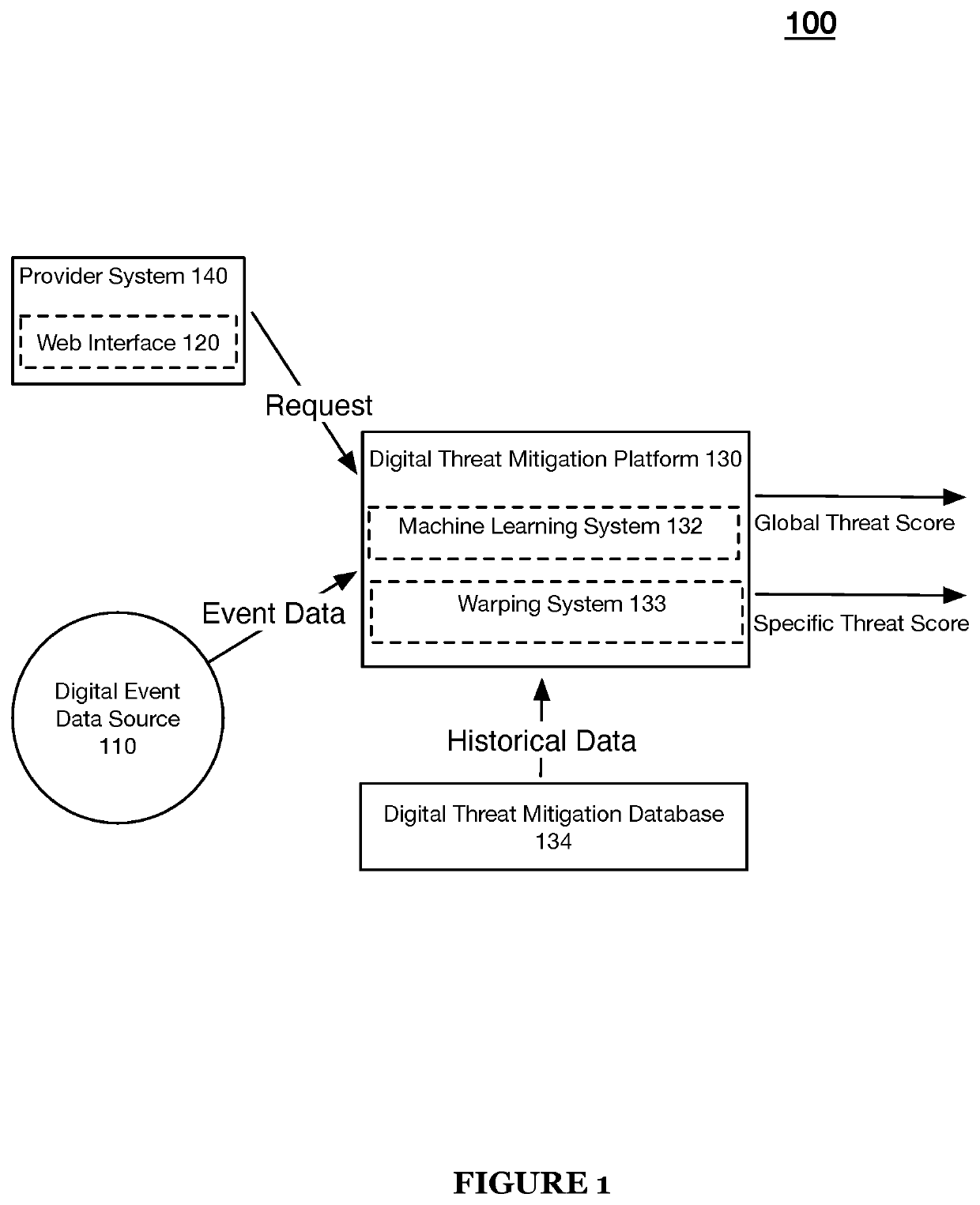
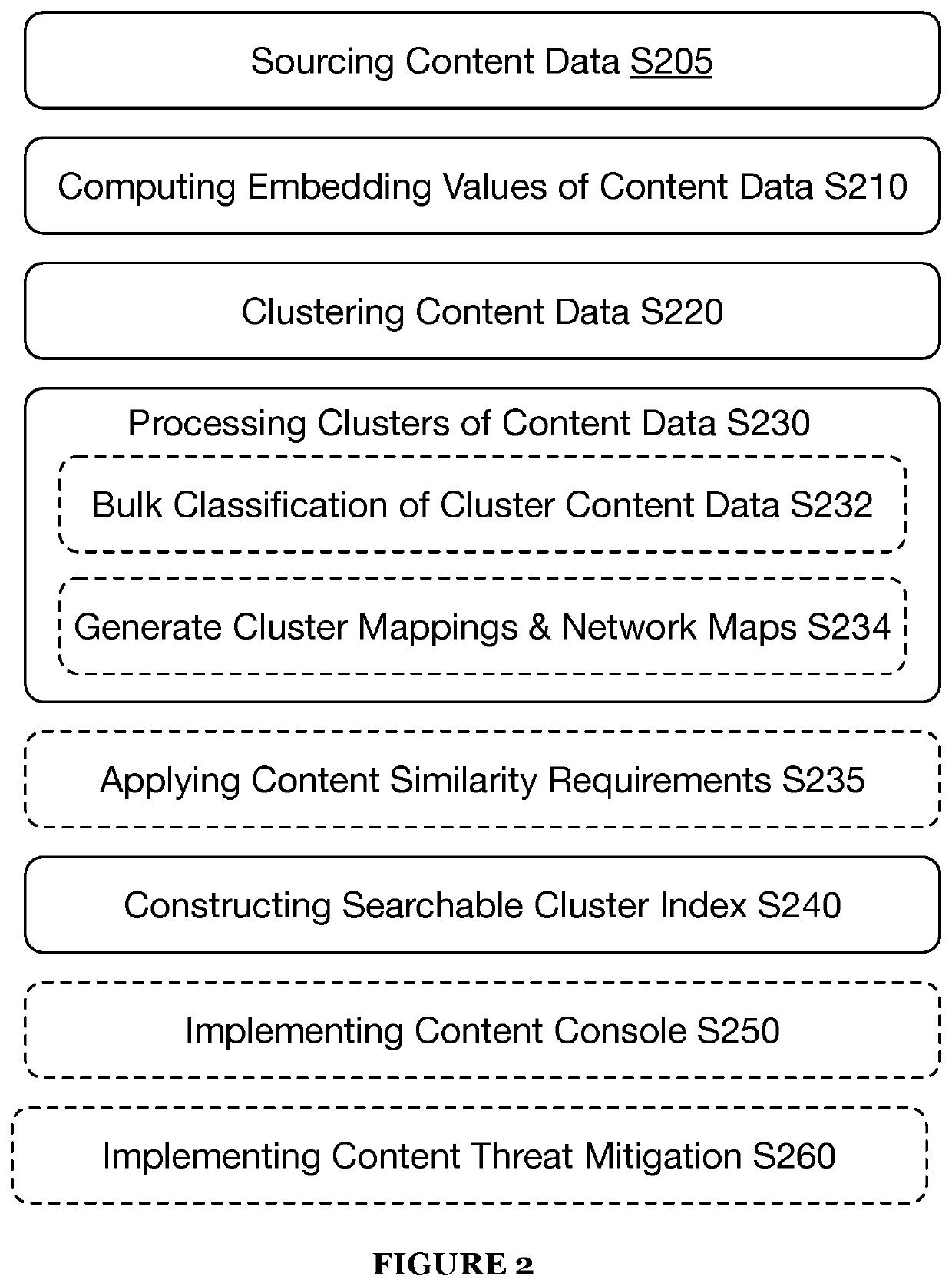
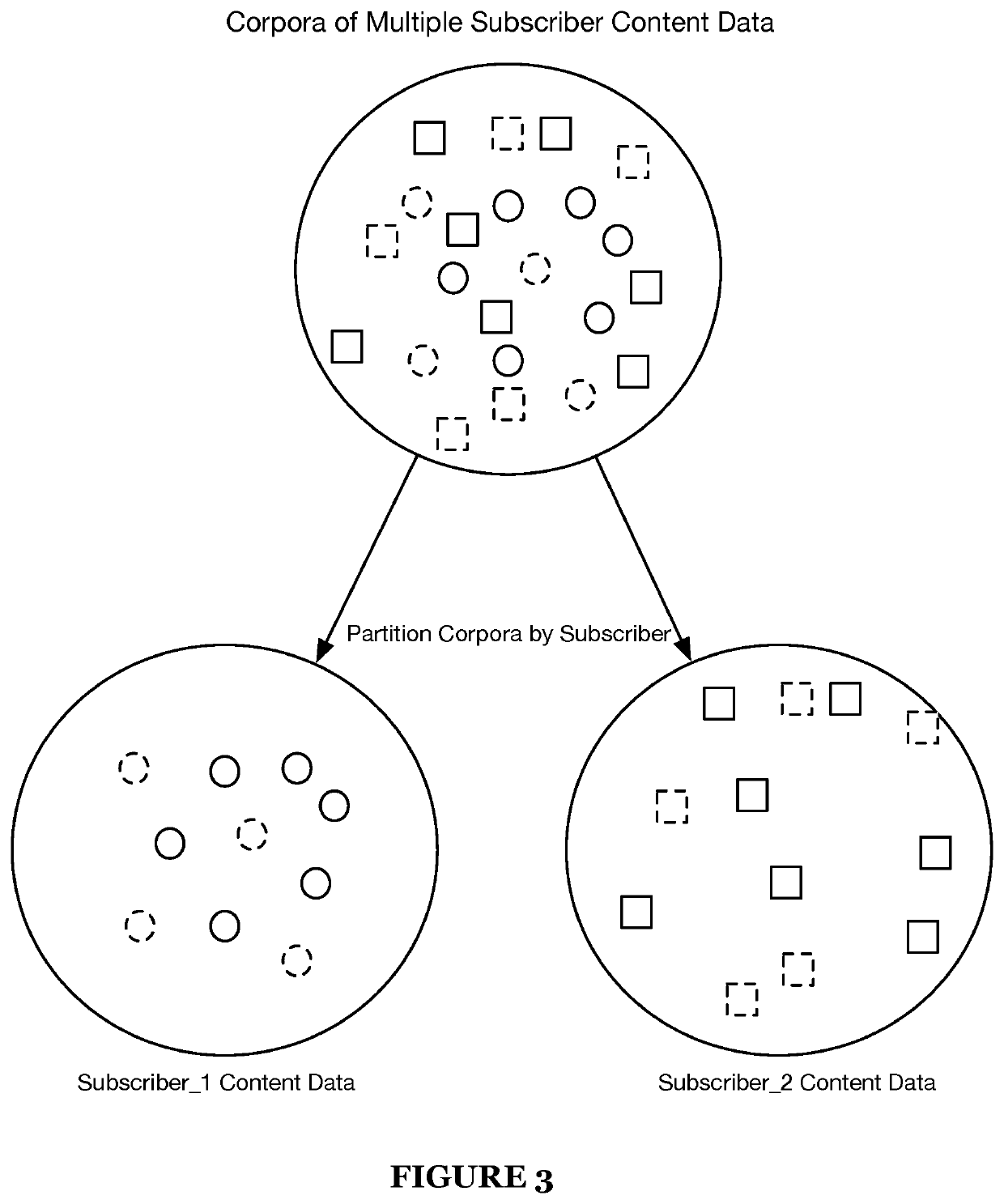
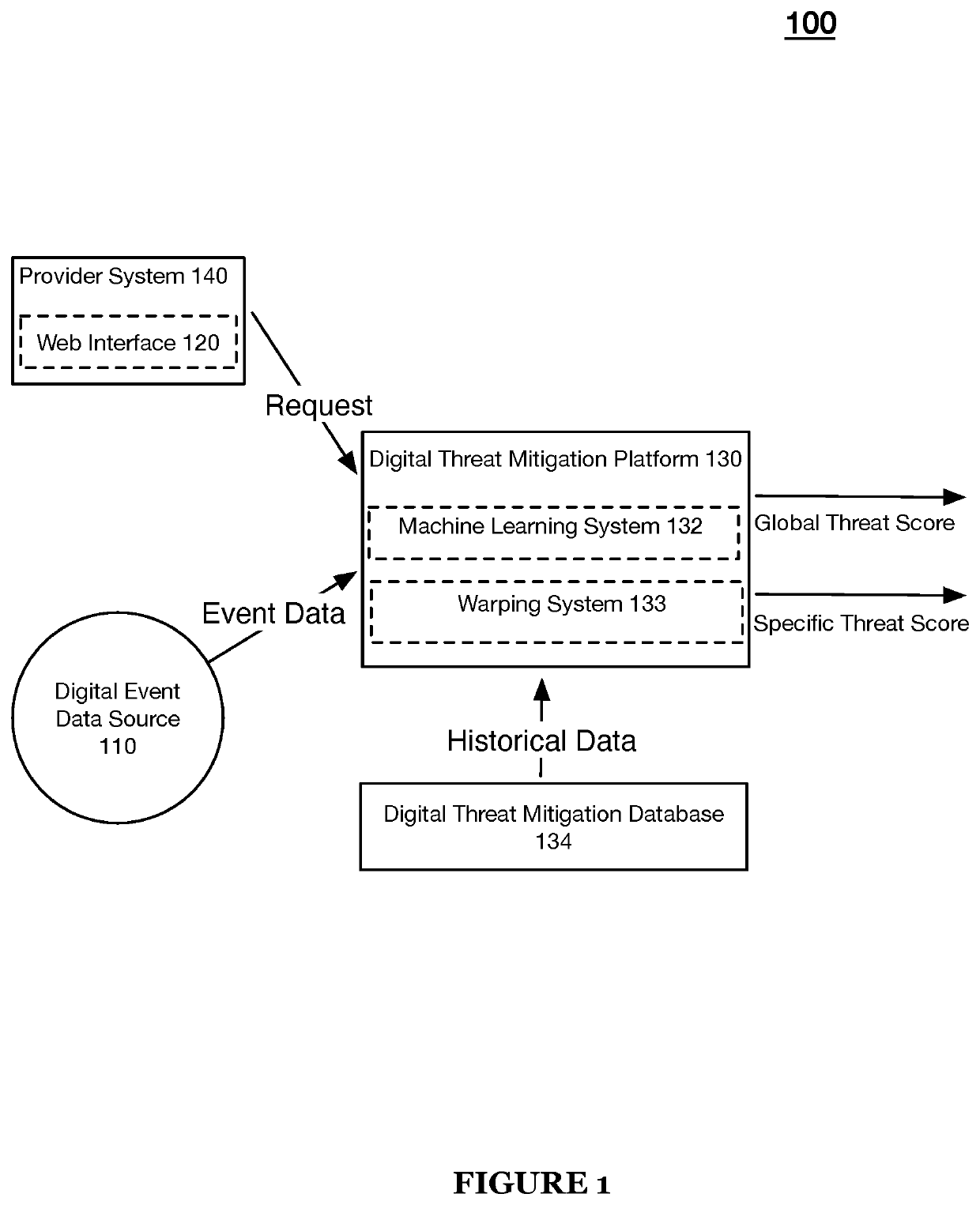
Systems and methods for machine learning-based digital content clustering, digital content threat detection, and digital content threat remediation in machine learning task-oriented digital threat mitigation platform
A machine learning-based system and method for content clustering and content threat assessment includes generating embedding values for each piece of content of corpora of content data; implementing unsupervised machine learning models that: receive model input comprising the embeddings values of each piece of content of the corpora of content data; and predict distinct clusters of content data based on the embeddings values of the corpora of content data; assessing the distinct clusters of content data; associating metadata with each piece of content defining a member in each of the distinct clusters of content data based on the assessment, wherein the associating the metadata includes attributing to each piece of content within the clusters of content data a classification label of one of digital abuse / digital fraud and not digital abuse / digital fraud; and identifying members or content clusters having digital fraud / digital abuse based on querying the distinct clusters of content data.
Owner:SIFT SCI INC
Threat mitigation system and method
A computer-implemented method, computer program product and computing system for: obtaining consolidated platform information for a computing platform to identify one or more deployed security-relevant subsystems; processing the consolidated platform information to identify one or more non-deployed security-relevant subsystems; generating a list of ranked & recommended security-relevant subsystems that ranks the one or more non-deployed security-relevant subsystems; and providing the list of ranked & recommended security-relevant subsystems to a third-party.
Owner:RELIAQUEST HLDG LLC
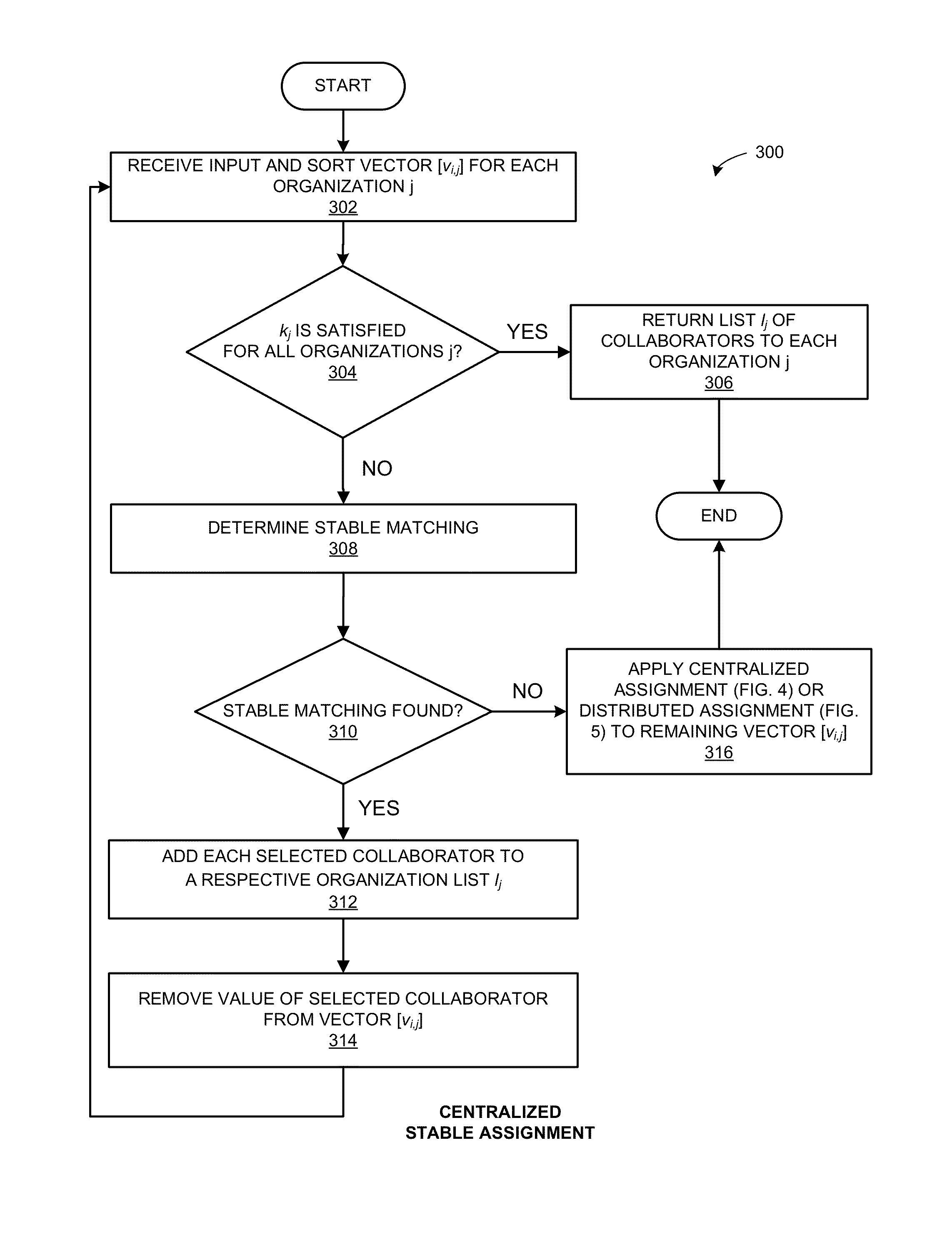
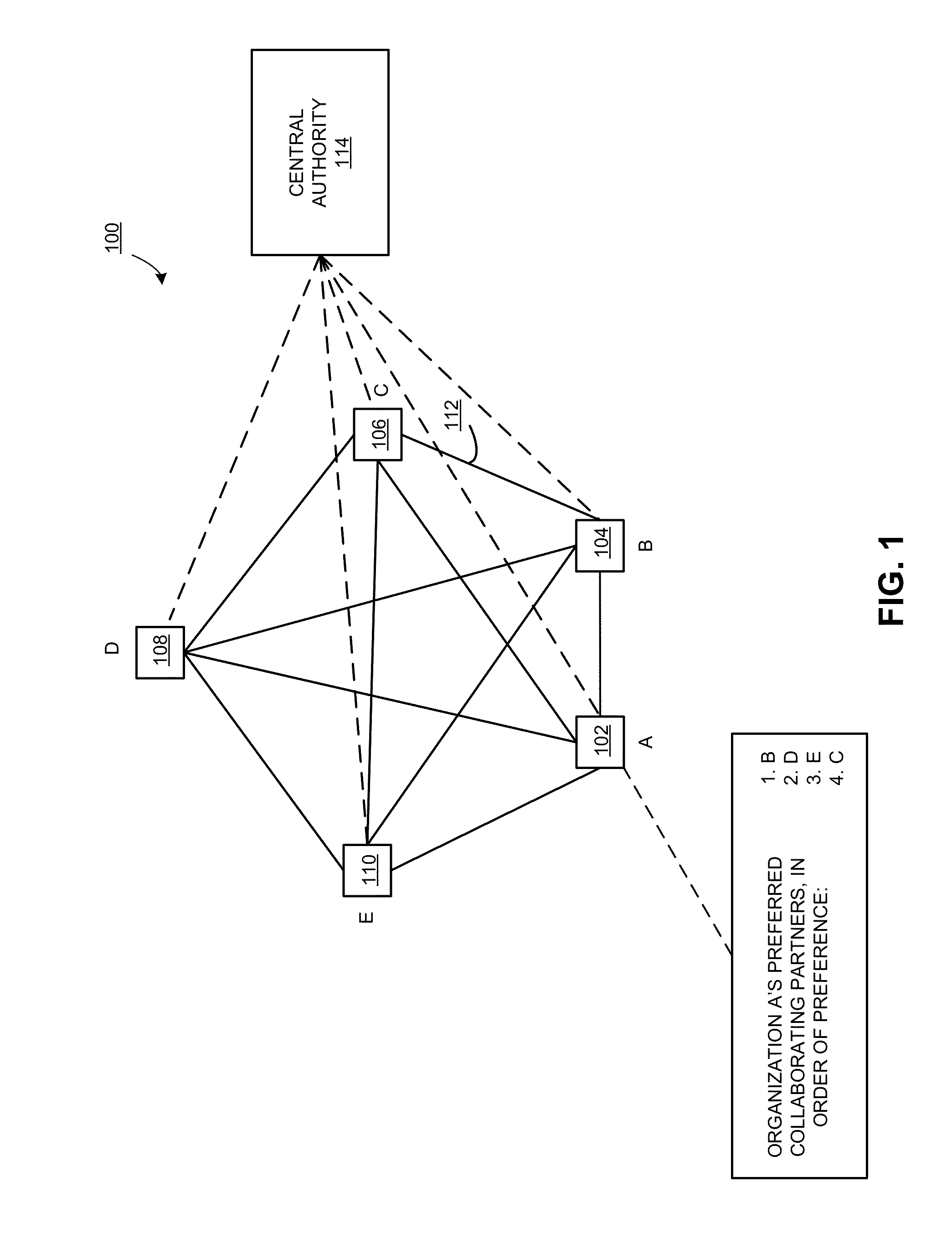
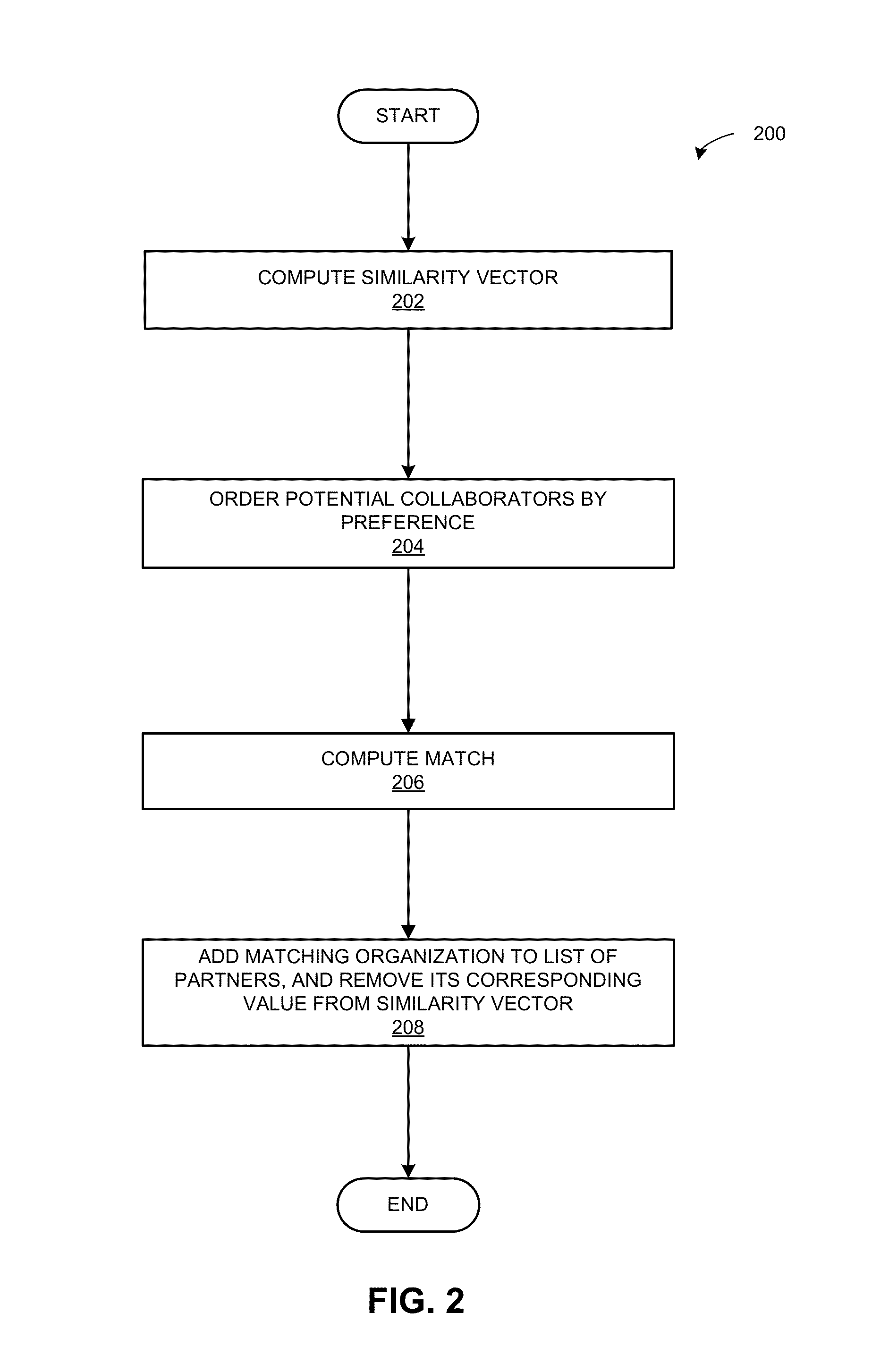
Methods for selection of collaborators for online threat mitigation
ActiveUS20150286824A1Facilitate exchanging security dataDigital data processing detailsAnalogue secracy/subscription systemsMultiple PartnersThreat mitigation
One embodiment of the present invention provides a system for stable selection of collaborating partners for exchanging security data. During operation, the system receives vectors of collaboration values from a plurality of entities. A collaboration value is a measure of an expected benefit of collaborating with a respective entity. The system sorts each of the vectors by the collaboration values of the respective vector. The system then determines matching entities given a number of partners wanted by each organization in N. The system may add matching entities to lists of collaborating partners given the number of partners wanted by each organization in N. Subsequently, the system sends the lists of collaborating partners to facilitate exchanging security data with partners in the list of collaborating partners.
Owner:XEROX CORP
System for generating a communication pathway for third party vulnerability management
The invention utilizes a two-component system to detect third party security threats and drive improved security threat mitigation based on the detection. The first component of the system is a security threat assessment engine, which receives and / or identifies external data and internal data regarding third parties in order to determine information security threats posed by third-parties. The second component of the system is an analytics engine, which may comprise a machine learning component which is configured to detect threat patterns and anomalies. In response to the detection of the threat patterns and anomalies the security threat assessment engine may be modified in order to more accurately determine security threats. The system after identifying a security threat, generates a notification associated with the security threat and transfers the notification to a first set of third parties that may be affected by the security threat.
Owner:BANK OF AMERICA CORP
Advanced cybersecurity threat mitigation using software supply chain analysis
ActiveUS20210021644A1Web data indexingComputer security arrangementsReliability engineeringComputer engineering
A system and method for comprehensive cybersecurity threat assessment of software applications based on the totality of vulnerabilities from all levels of the software supply chain. The system and method comprising analyzing the code and / or operation of a software application to determine components comprising the software, identifying the source of such components, determining vulnerabilities associated with those components, compiling a list of such components, creating a directed graph of relationships between the components and their sources, and evaluating the overall threat associated with the software application based its software supply chain vulnerabilities.
Owner:QOMPLX INC
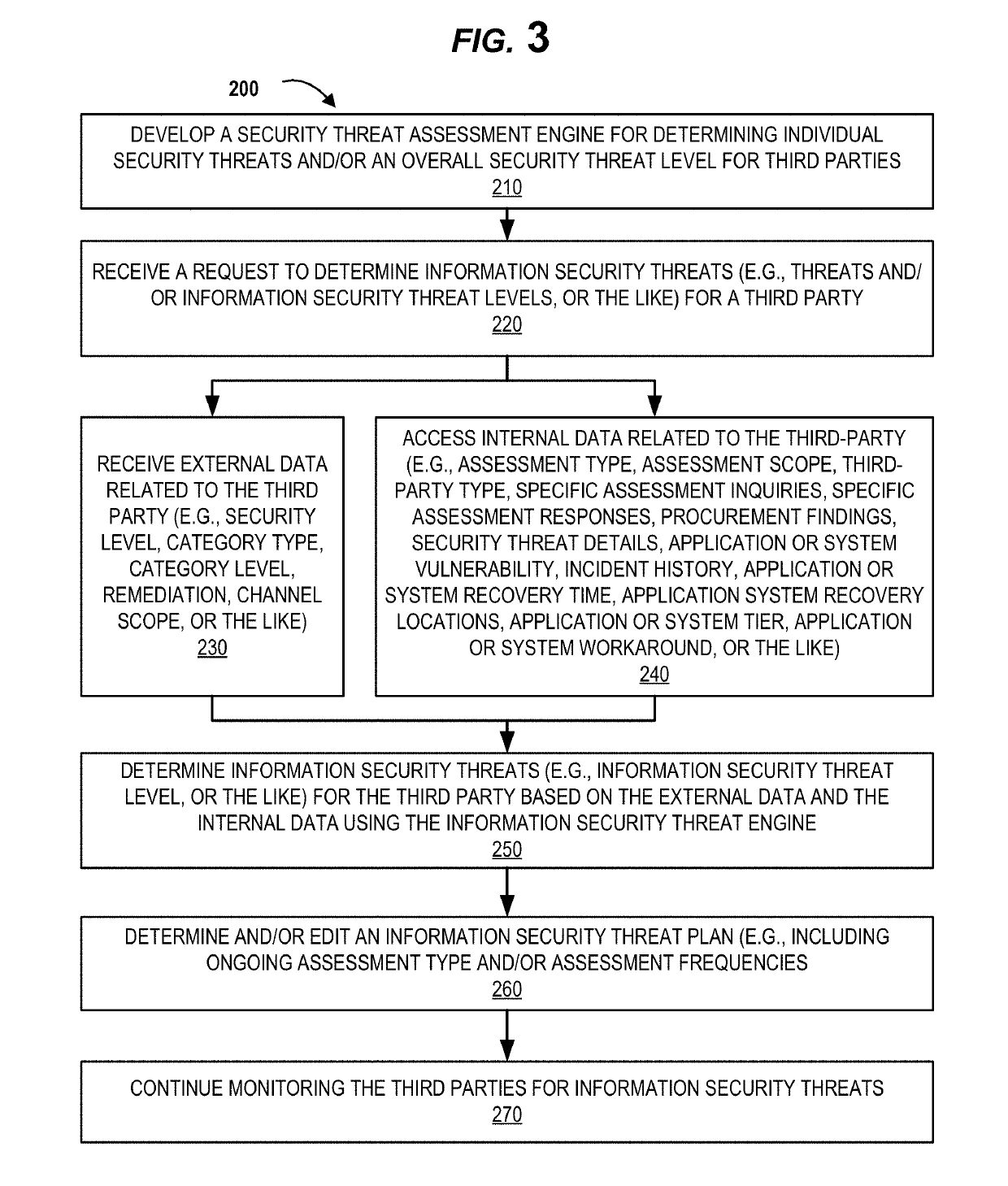
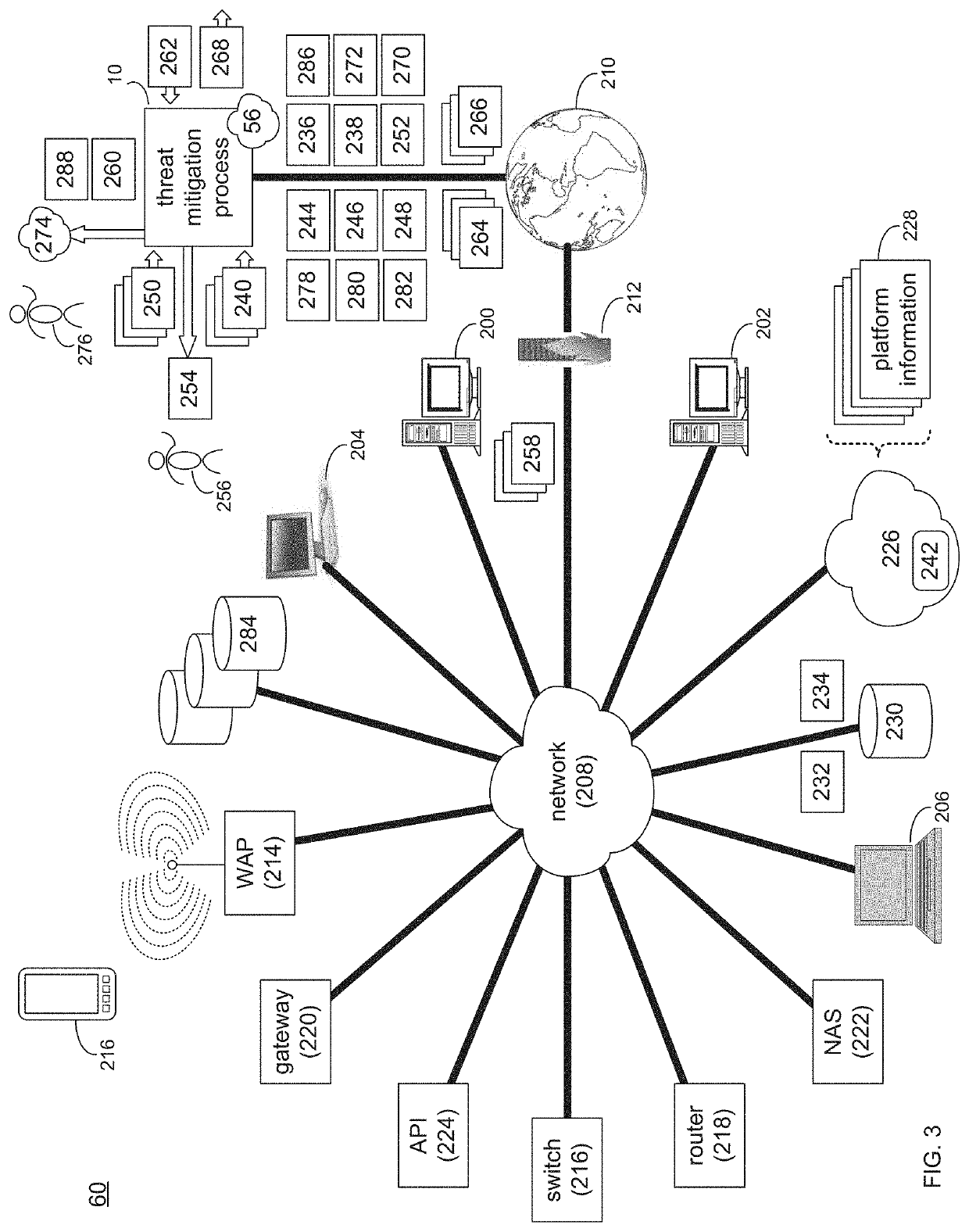
Threat mitigation system and method
ActiveUS20190379705A1Mathematical modelsDesign optimisation/simulationInformation processingComputing systems
A computer-implemented method, computer program product and computing system for: receiving platform information from a plurality of security-relevant subsystems; processing the platform information to generate processed platform information; identifying less threat-pertinent content included within the processed content; and routing the less threat-pertinent content to a long term storage system.
Owner:RELIAQUEST HLDG LLC
Dual band threat warning system
InactiveUS8245928B2Precise deploymentEasy to detectDefence devicesWeapon control systemsGround vehiclesWatercraft
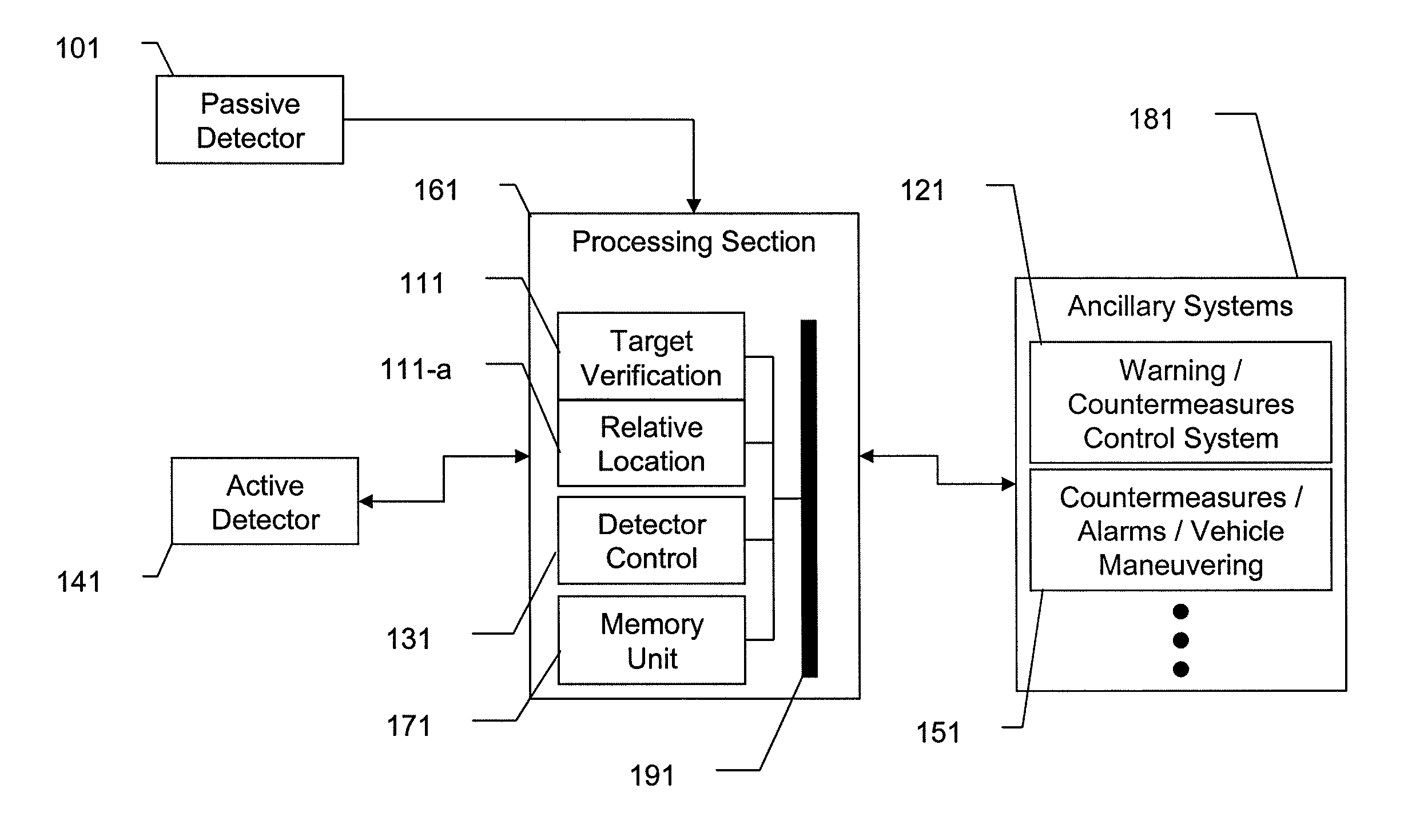
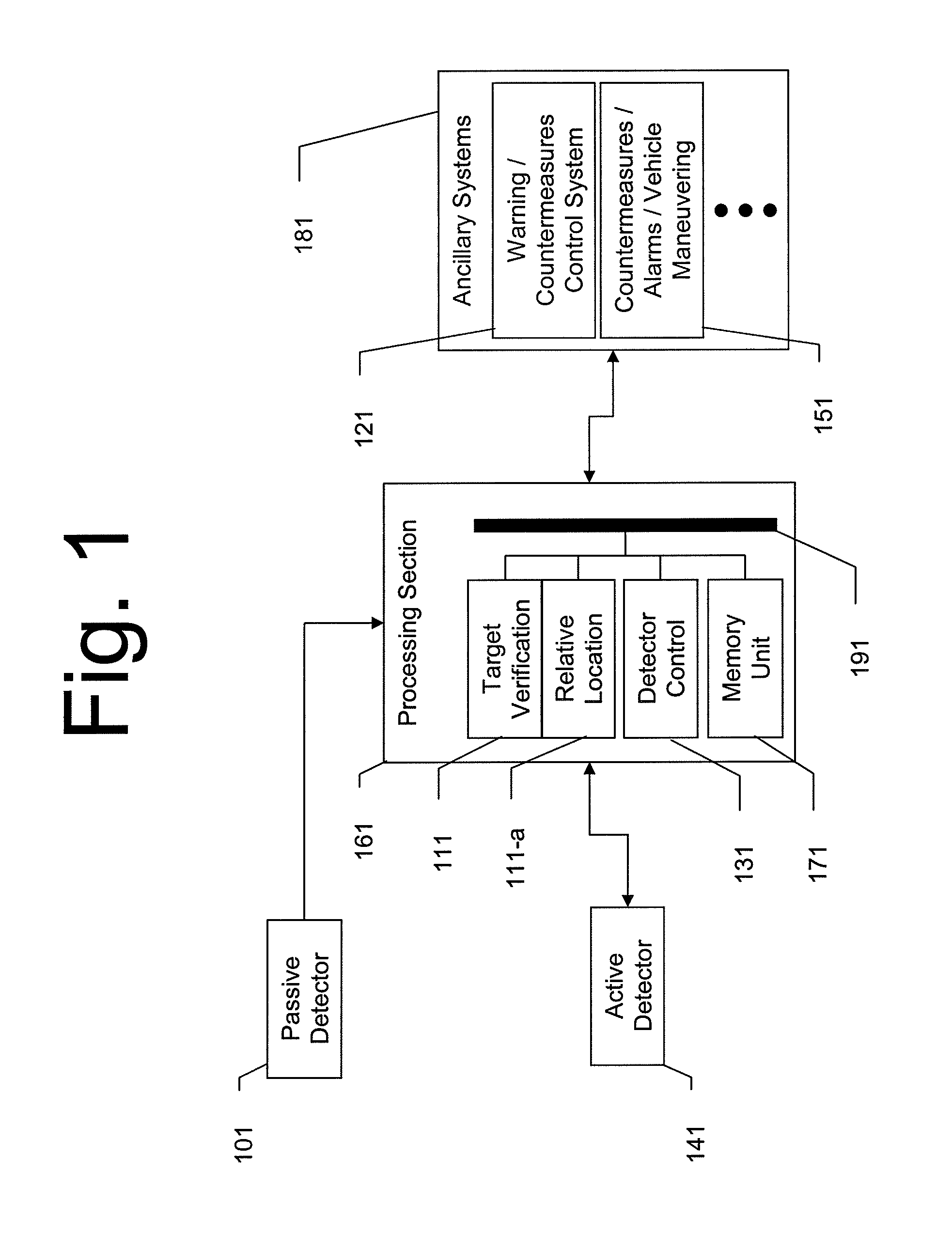
A system and method for dual-band detection of incoming threats using an initial passive detection system and a selectively activated active detection system. Advantages include improved threat detection accuracy, reduction of false alarms, and reduced radiation emission from the active system, thereby making the active system more difficult to detect and reducing irradiation levels of users and bystanders. Variations include systems employing passive optical or electro-optical detectors, systems employing active RADAR or LADAR detectors, and systems connected to alarm signal / threat mitigation systems. The system may be configured for use on ground vehicles or small watercraft. Variations of the system may be specifically configured to detect incoming munitions launches.
Owner:LOCKHEED MARTIN CORP
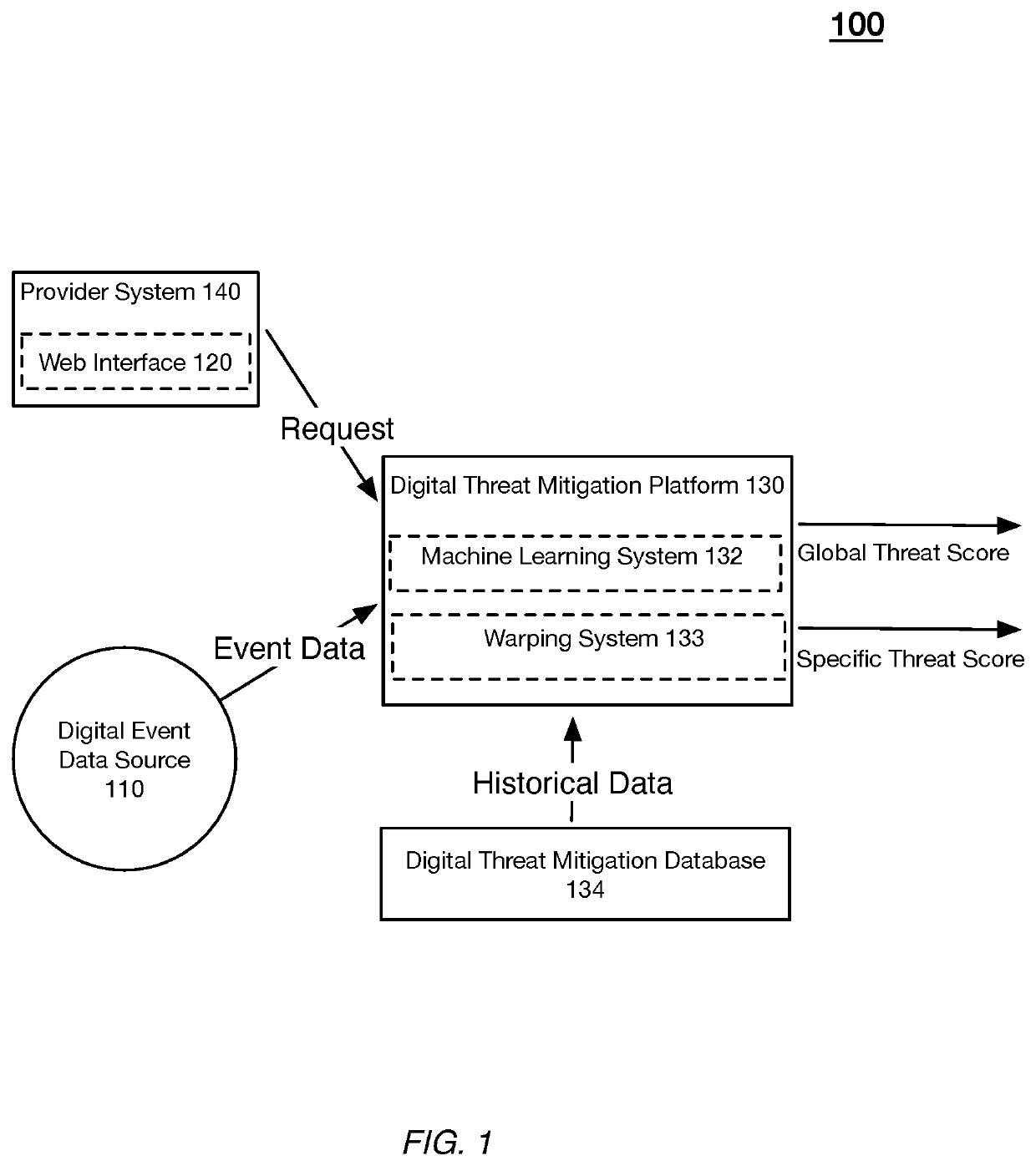
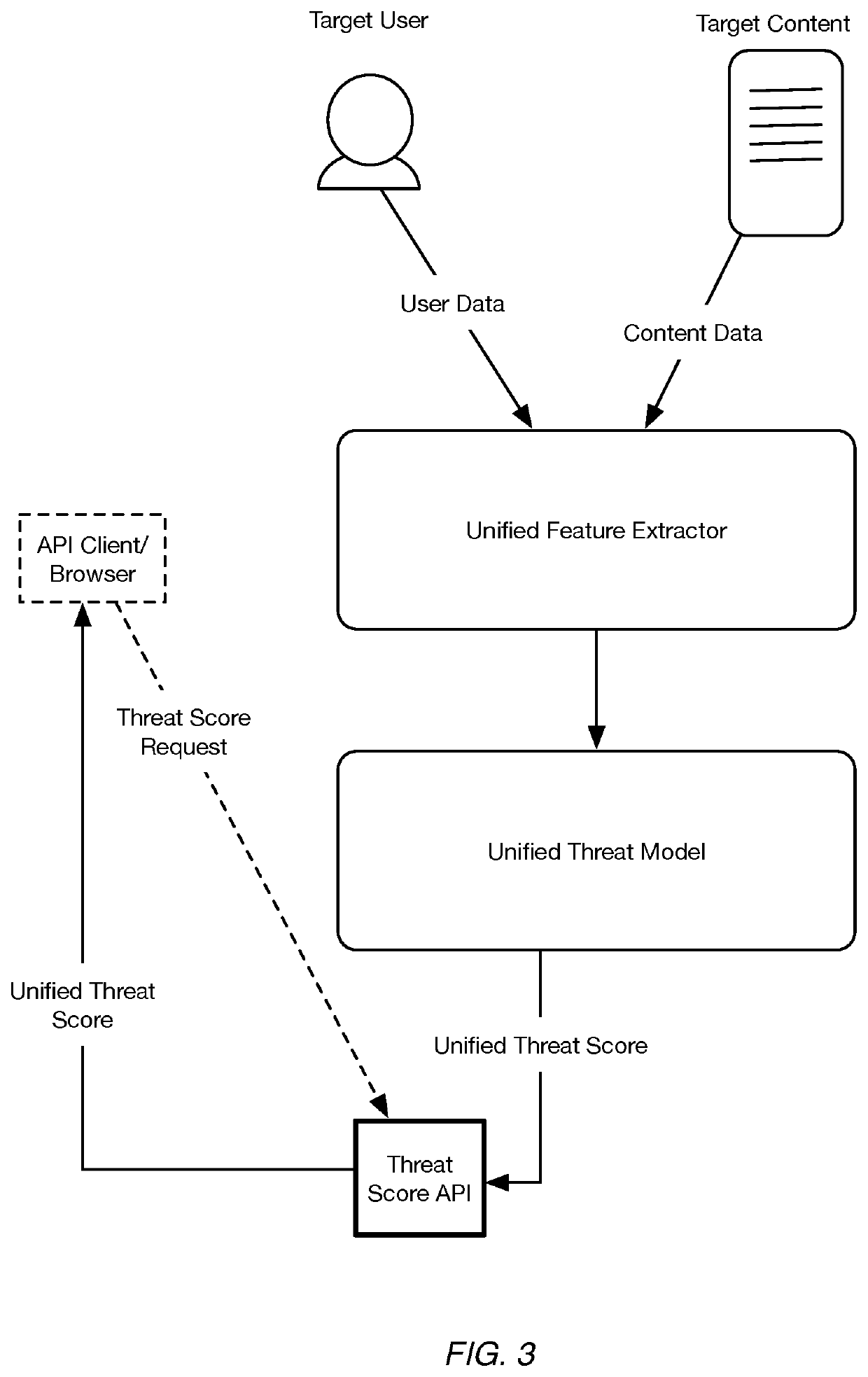
Systems and methods configuring a unified threat machine learning model for joint content and user threat detection
A machine learning-based system and method for identifying digital threats includes a threat service that: implements a unified threat model that produces a unified threat score that predicts both of: a level of threat of a piece of online content, and a level of threat that a target user will create a harmful piece of online content; wherein: implementing the unified threat model includes: receiving event data comprising historical content data for the target user and content data of the pending piece of online content and historical user digital activity data and real-time user activity data; and providing input of content feature data and user digital activity feature data to the unified threat model; and the unified threat model produces the unified threat score based on the content and the user digital activity data; and computes a threat mitigation action based on an evaluation of the threat score.
Owner:SIFT SCI INC
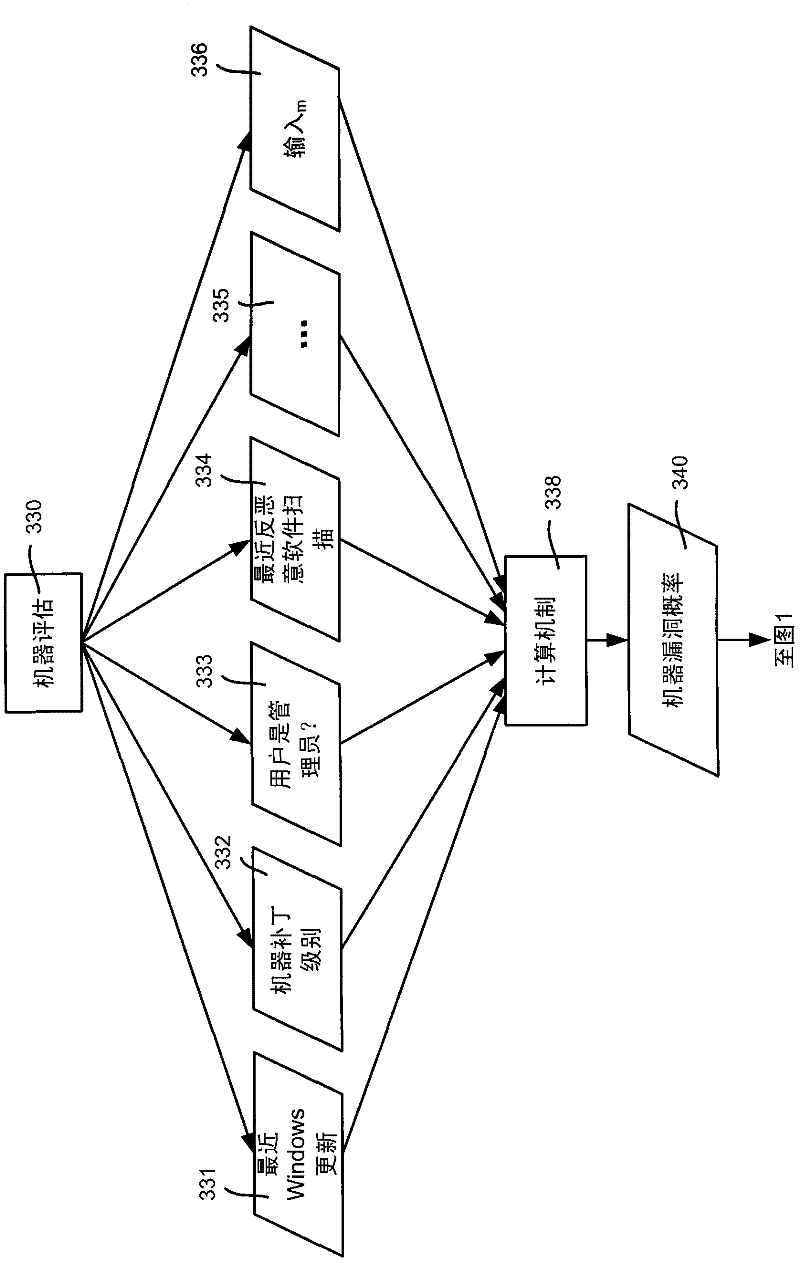
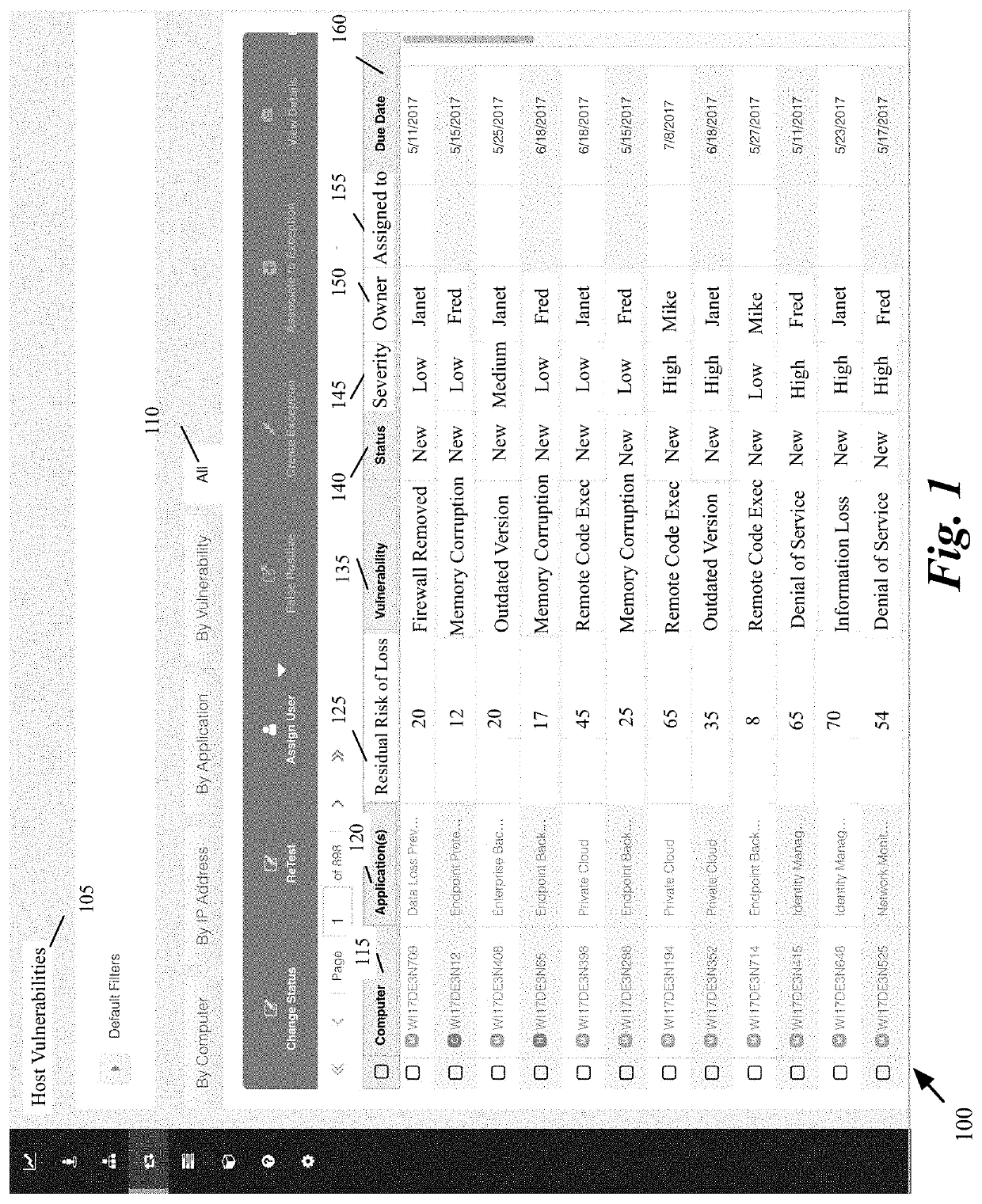
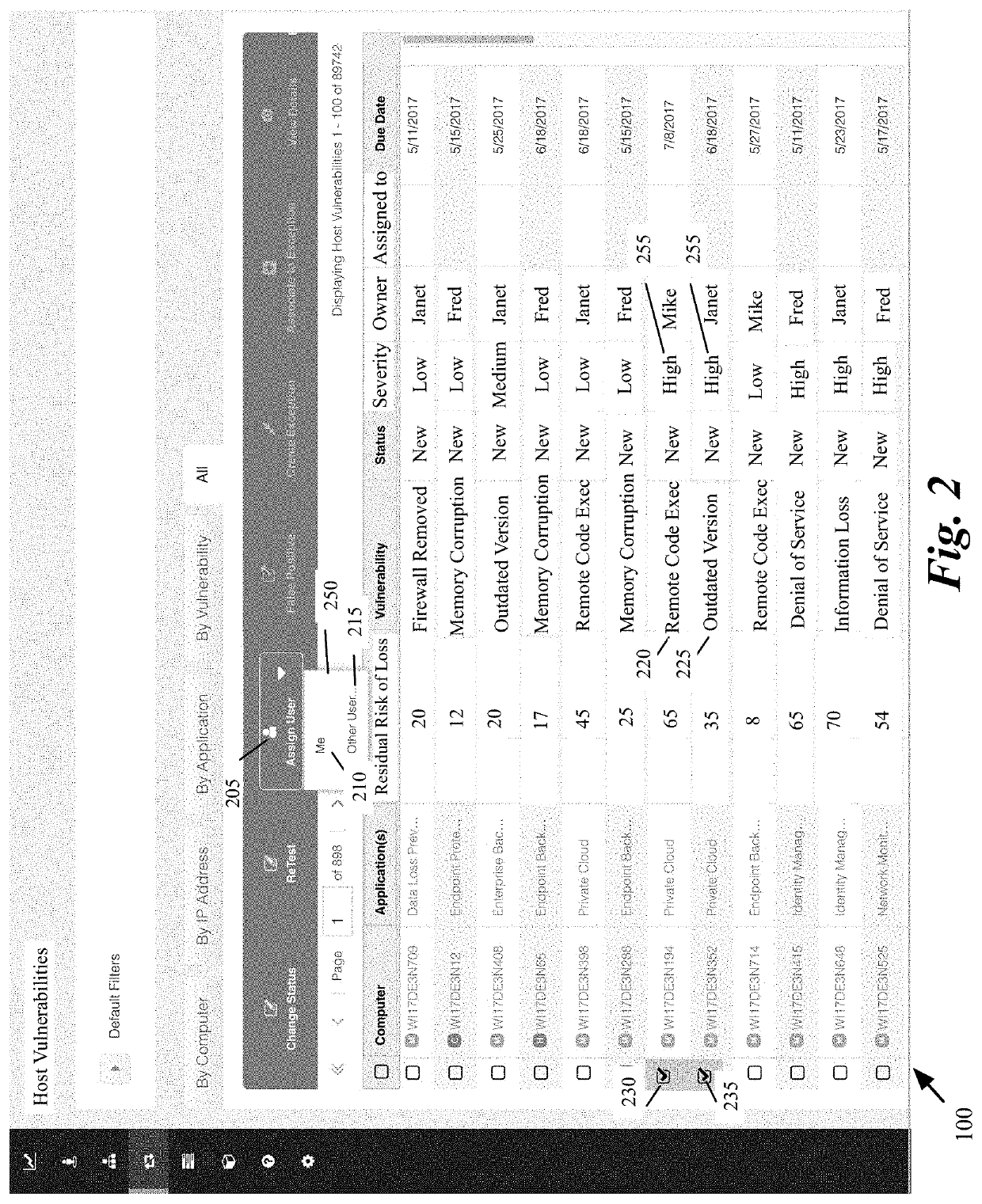
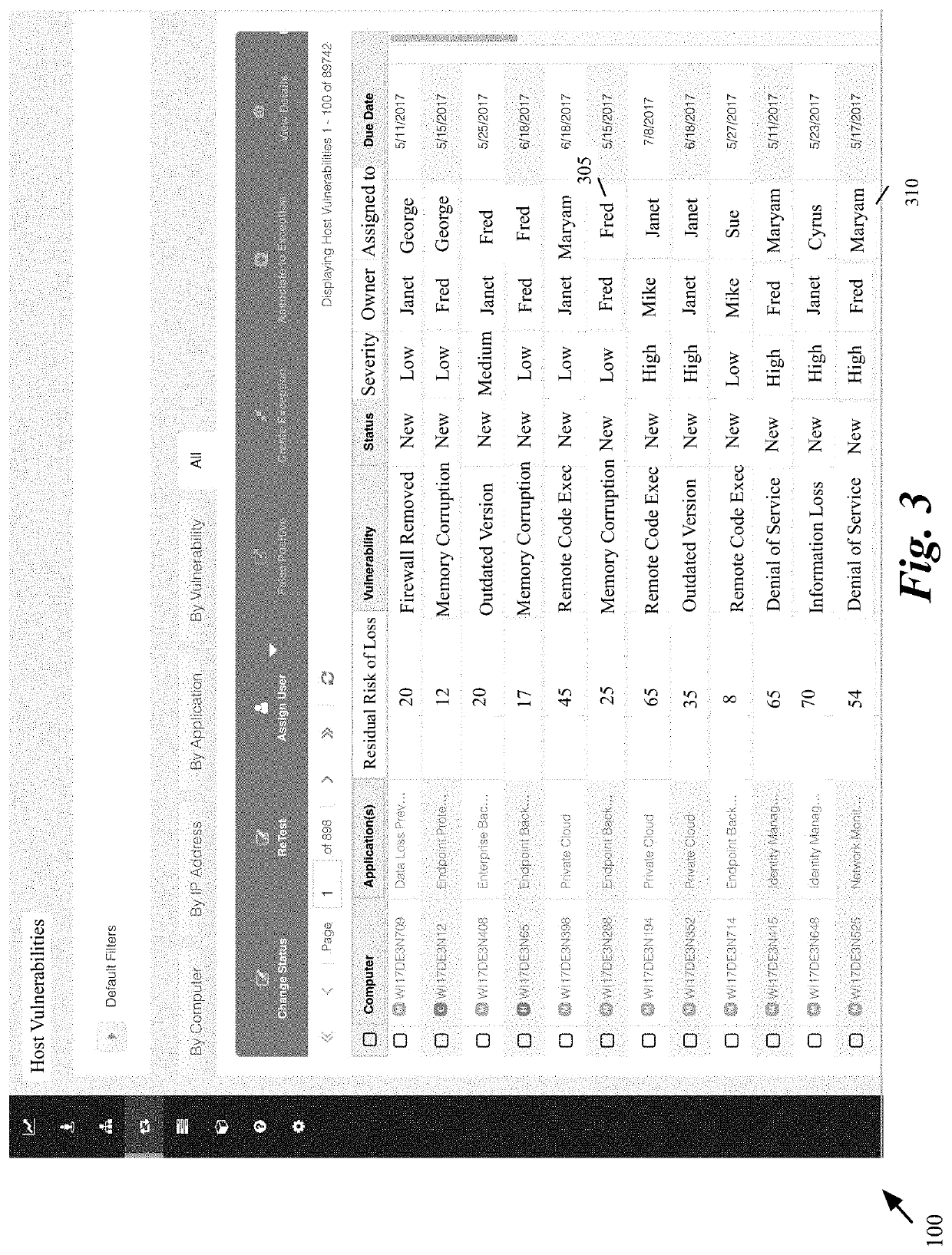
Monitoring and managing credential and application threat mitigations in a computer system
ActiveUS10587644B1Reduce security risksMitigate different riskComputer security arrangementsTransmissionReliability engineeringComputer engineering
A method of monitoring tasks for reducing security risks in a computer system comprising a plurality of computers executing a plurality of applications is provided. The method based on a set of login information, displays a set of risks for a set of applications that execute on the plurality of computers and an identification of a person in a hierarchy supervised by the logged-in person assigned to mitigate each risk. The method also displays the current status of each assigned mitigation.
Owner:CA TECH INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com