Predictive malware threat mitigation
A malicious software, user technology, applied in electrical components, instruments, computing, etc., can solve problems such as occupying application CPU cycles, performance bottlenecks, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
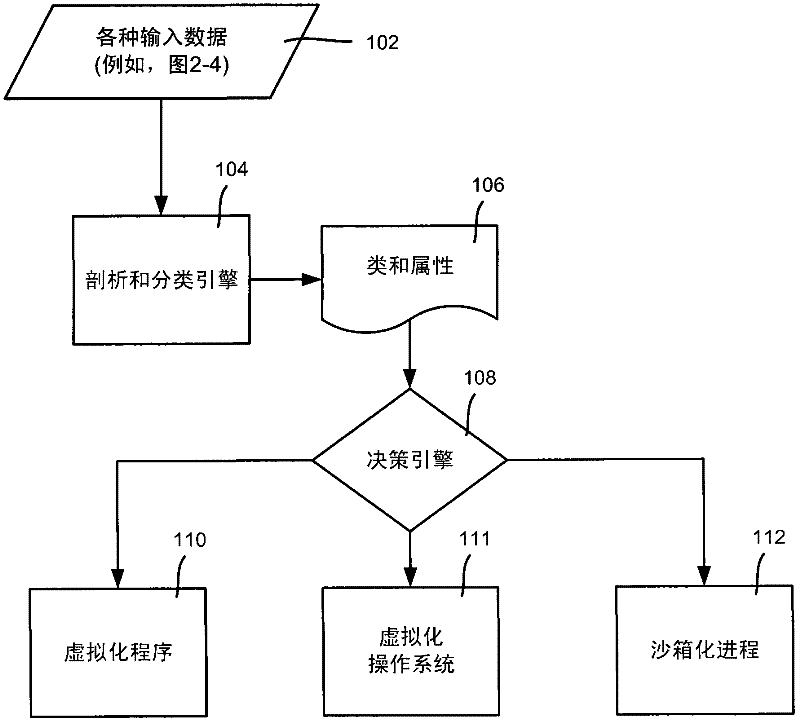
[0019] Aspects of the techniques described herein are generally directed toward providing varying levels of protection from malware based on user profile and / or historical behavior. As will be appreciated, such varying protection levels allow for dynamic strength adjustments of anti-malware products protecting against malware based on user preferences, which improves overall protection against threats, even if not fully compliant from a security standpoint.
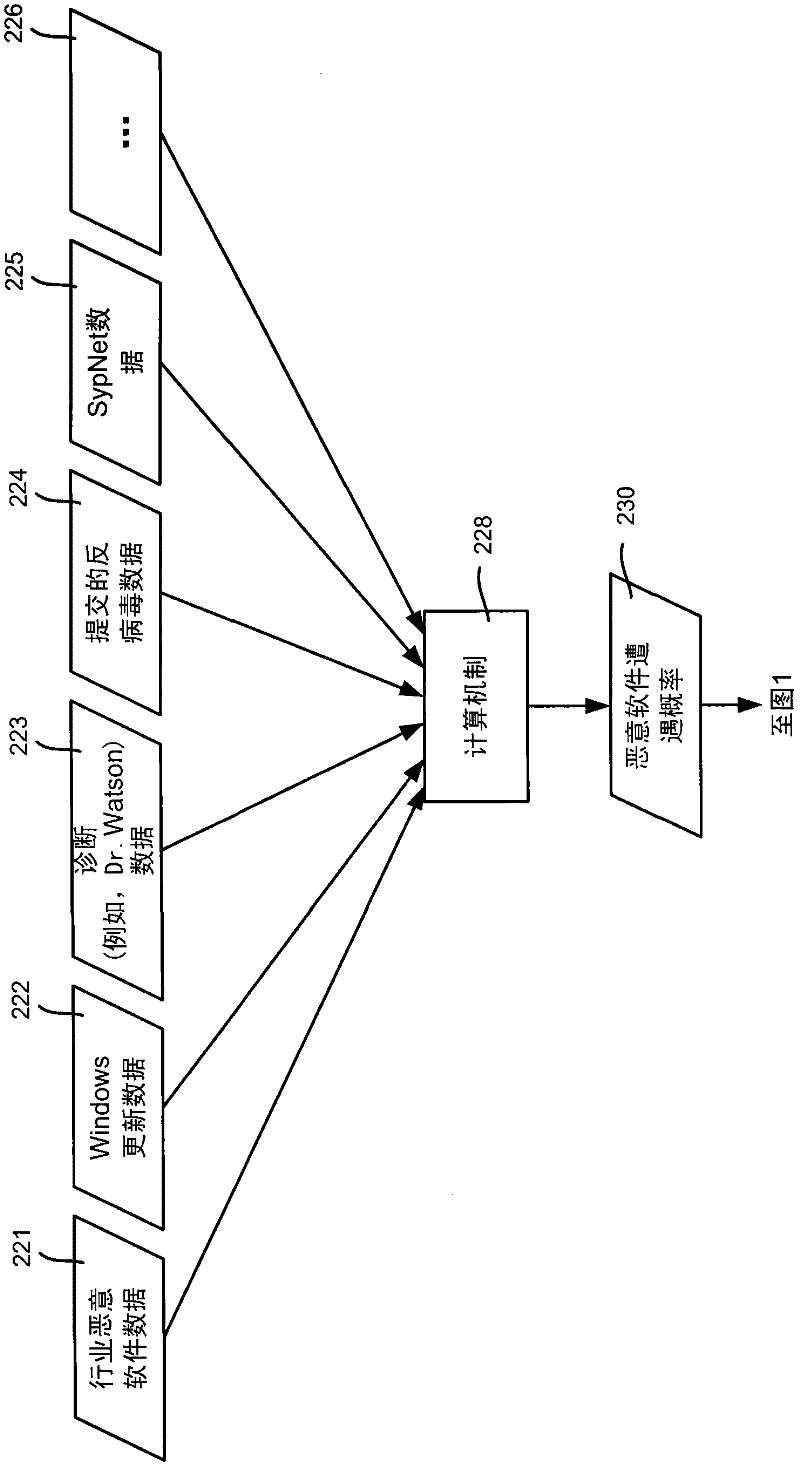
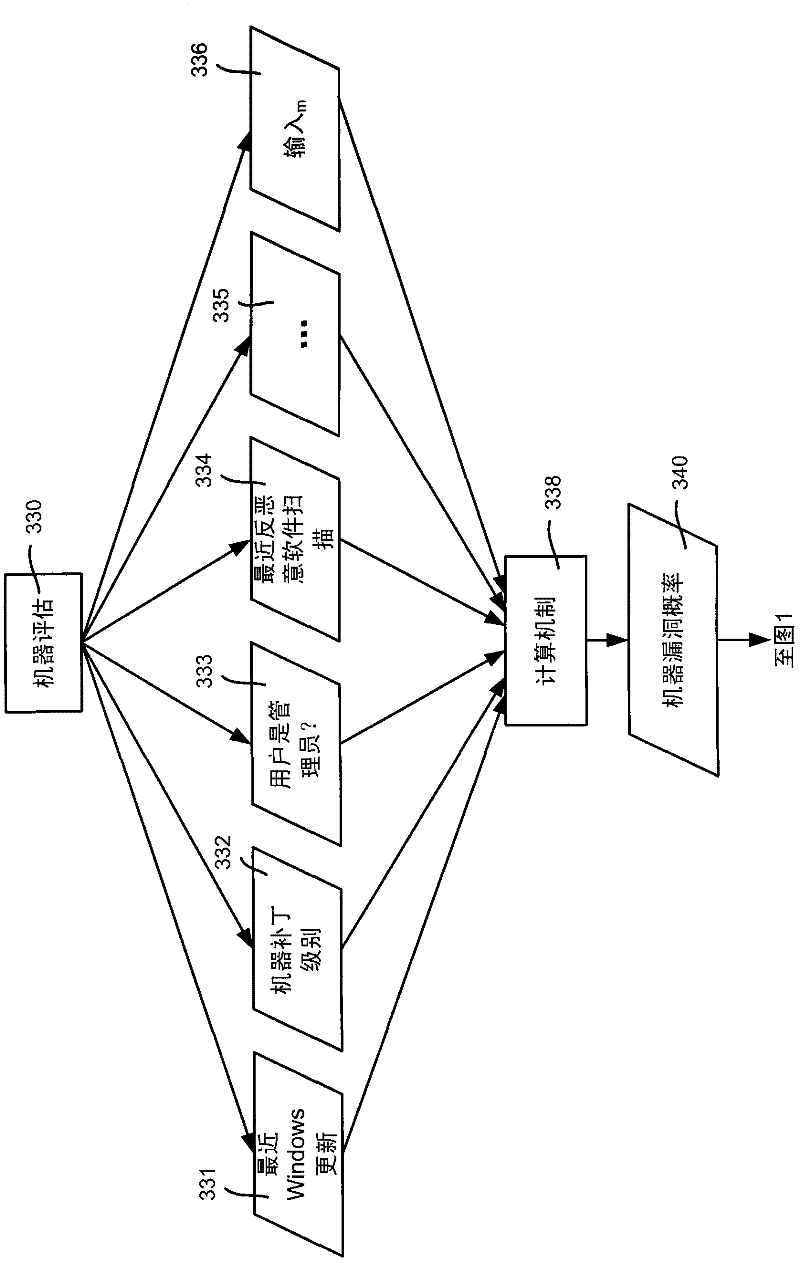
[0020] As will also be appreciated, the techniques described herein profile user habits and machine vulnerabilities based on a variety of data, which may include telemetry, business intelligence, data collected from system anomalies, and data collected from human-induced anomalies. Each user can then be classified according to the profile based on mathematical models and patterns, from which (at runtime) vulnerability scores and protection mechanisms can be calculated. Also described is the ability to impose threshold lev...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com