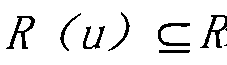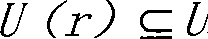Patents
Literature
74 results about "Threat model" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Threat modeling is a process by which potential threats, such as structural vulnerabilities can be identified, enumerated, and prioritized – all from a hypothetical attacker’s point of view. The purpose of threat modeling is to provide defenders with a systematic analysis of the probable attacker’s profile, the most likely attack vectors, and the assets most desired by an attacker. Threat modeling answers questions like “Where are the high-value assets?”, “Where am I most vulnerable to attack?”, “What are the most relevant threats?”, and “Is there an attack vector that might go unnoticed?”.
Threat modeling and analysis
ActiveUS9602529B2Easy to understandMitigate and further mitigate riskError detection/correctionPlatform integrity maintainanceData streamInformation system
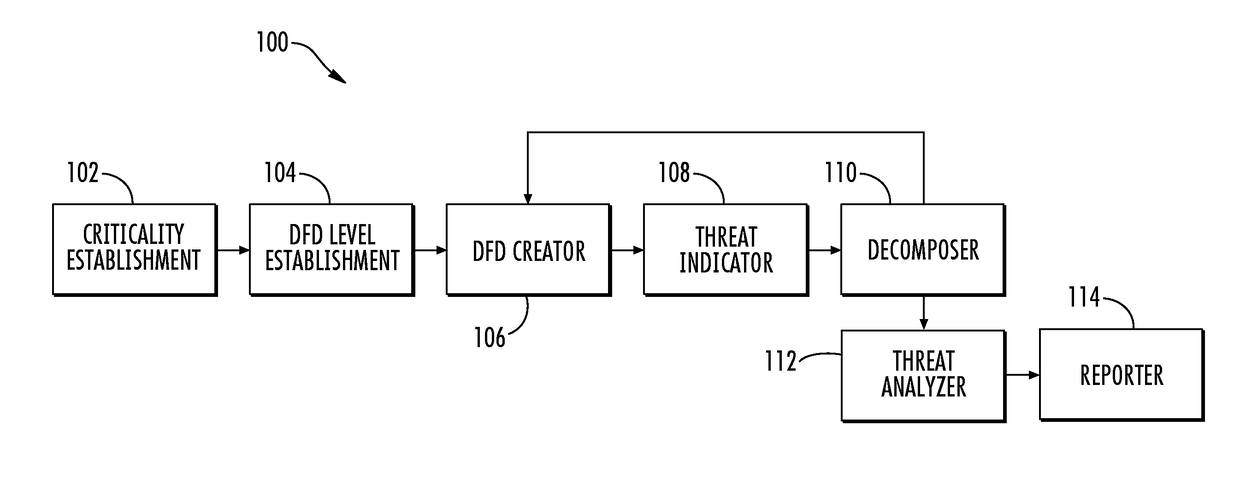
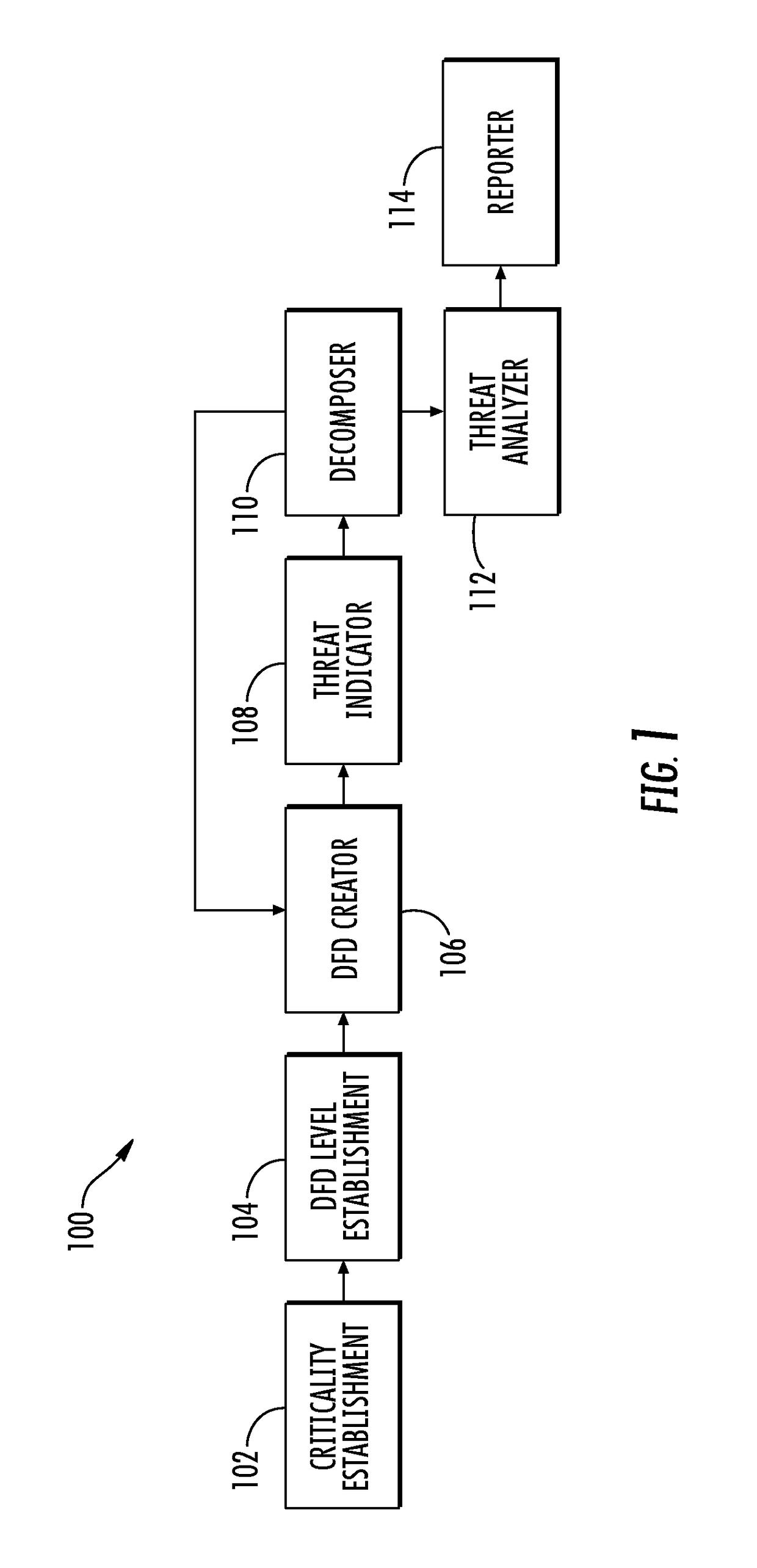
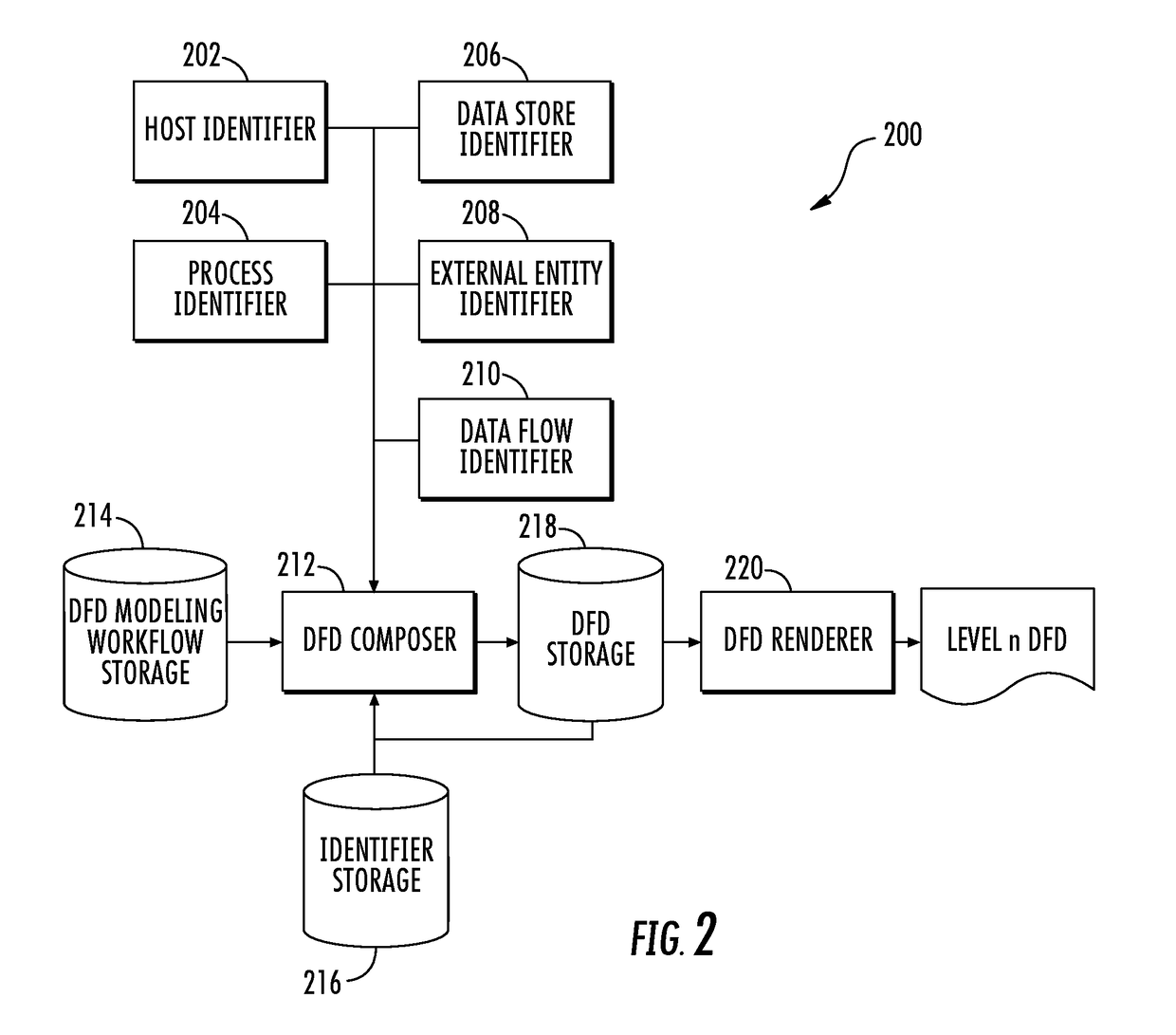
A system is provided for modeling and analysis of cybersecurity threats may include a data flow diagram (DFD) creator, threat indicator and threat analyzer. The DFD creator may identify elements of an information system, and compose a DFD including nodes and edges representing components and data flows of the information system. The threat indicator may identify a cybersecurity threat to a particular element of the information system, and add a secondary node representing the cybersecurity threat to the DFD to thereby produce a threat-model DFD for the information system. In metadata associated with the nodes, edges and secondary node, the DFD creator and threat indicator may provide structured information including attributes of the components, data flows and cybersecurity threat. And the threat analyzer may perform an analysis of the cybersecurity threat based on the threat-model DFD and metadata associated with the nodes, edges and secondary node thereof.
Owner:THE BOEING CO
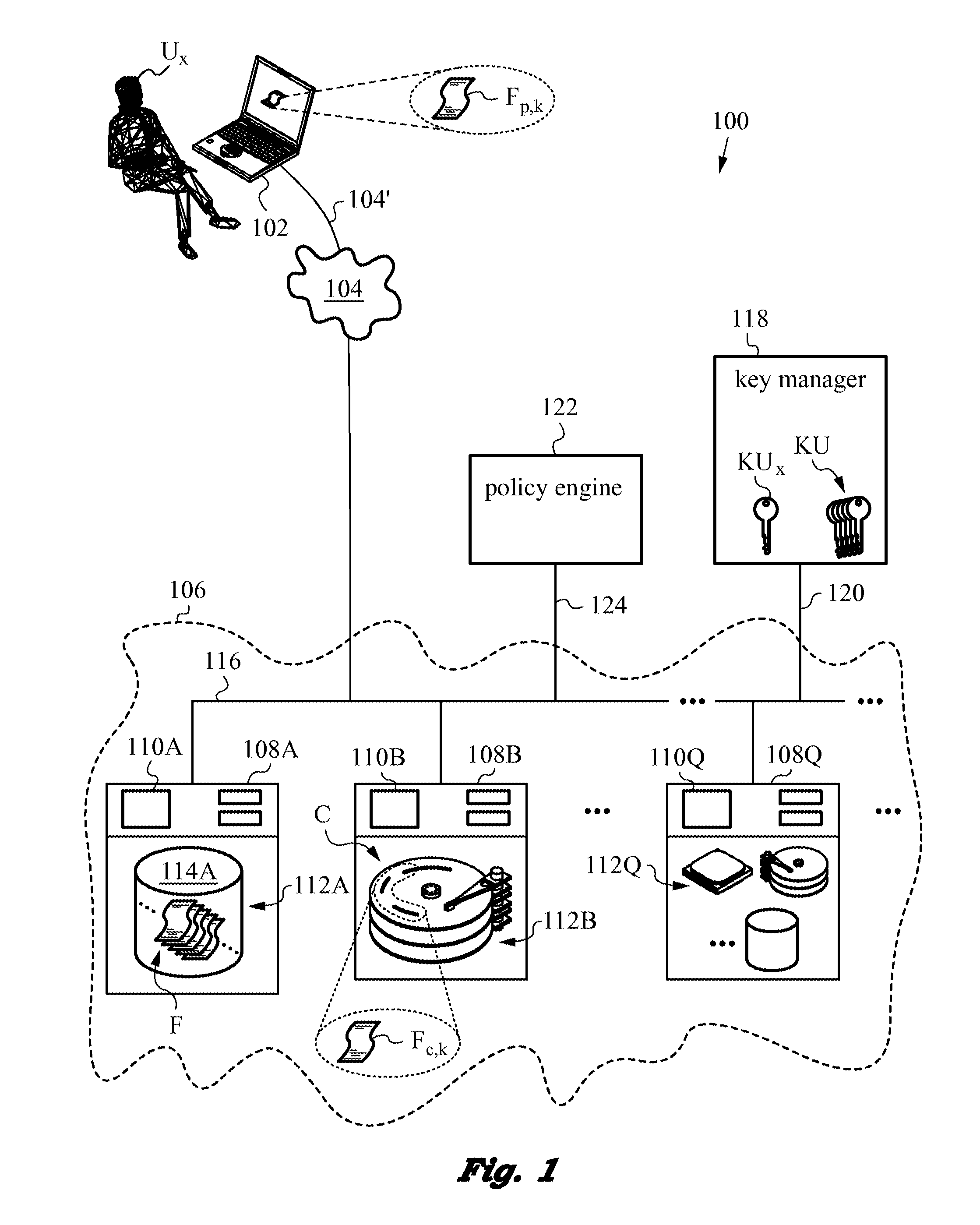
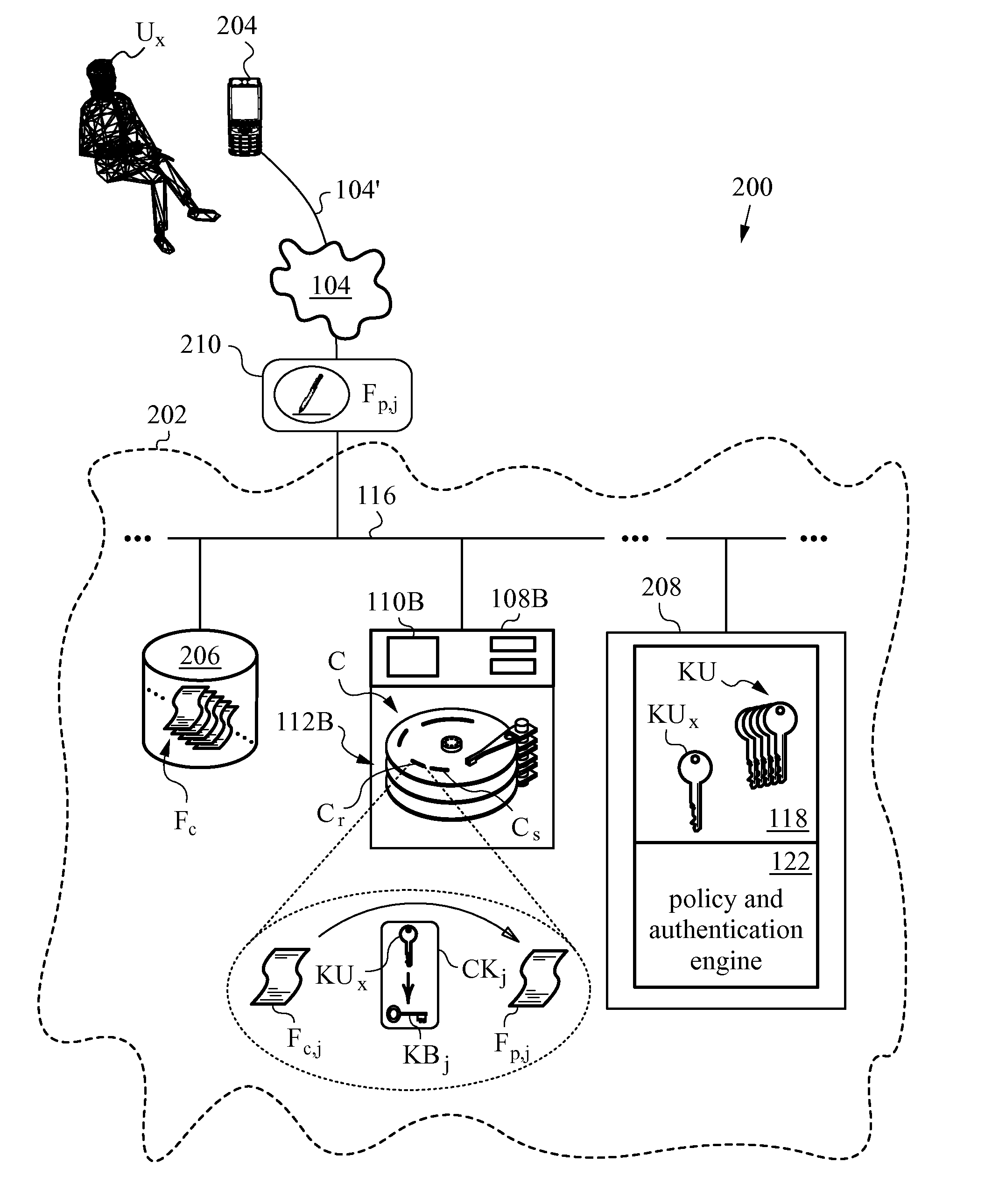
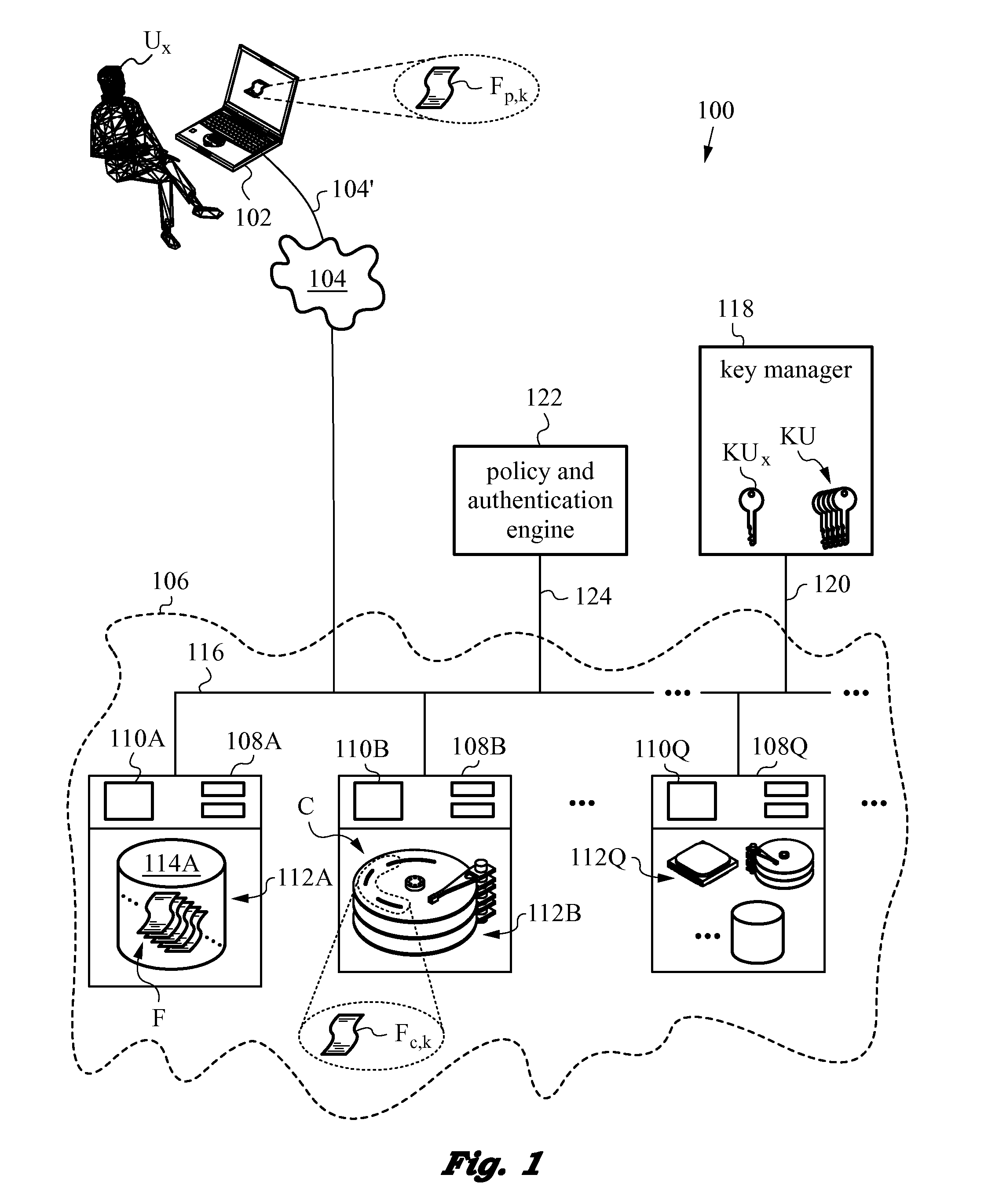
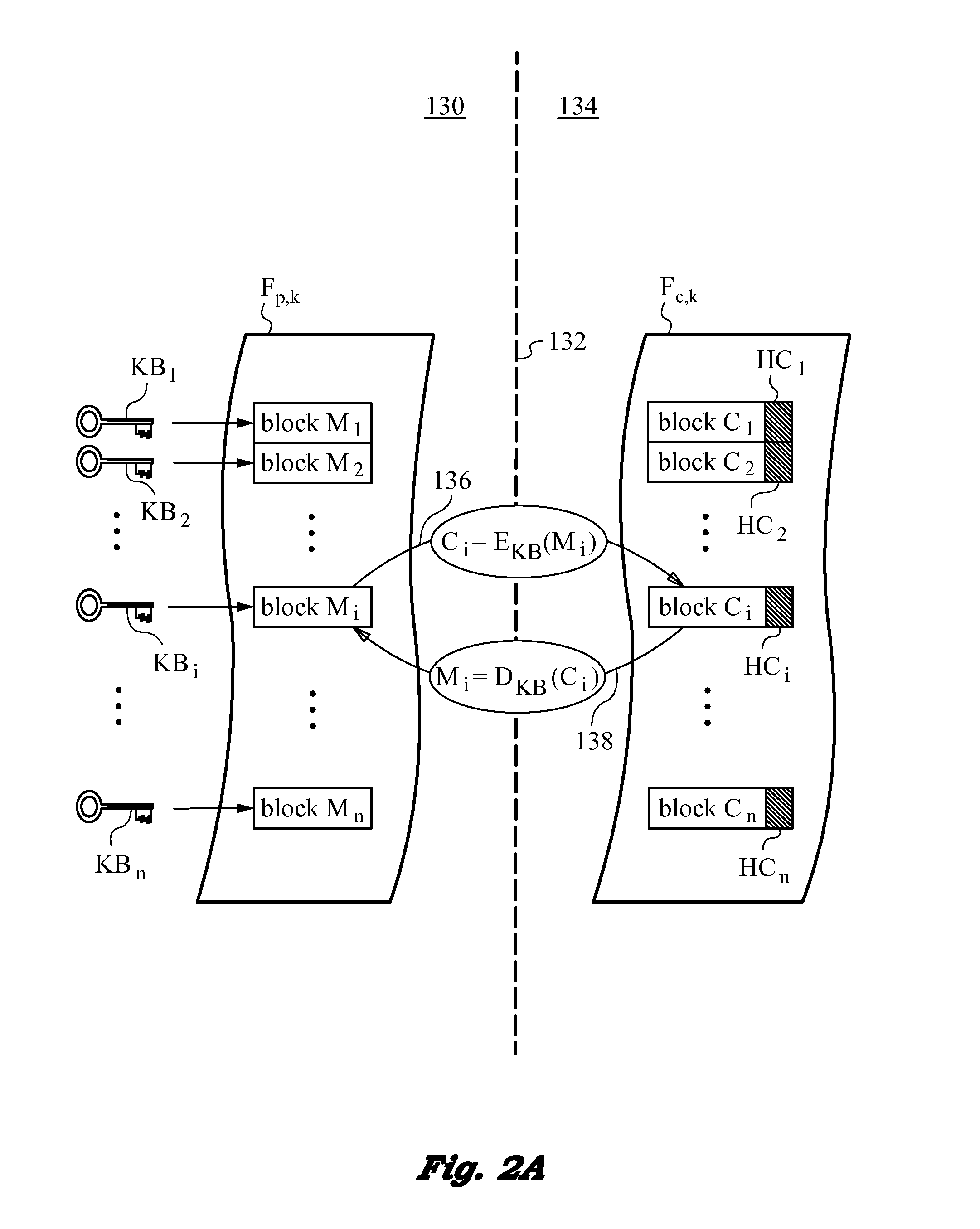
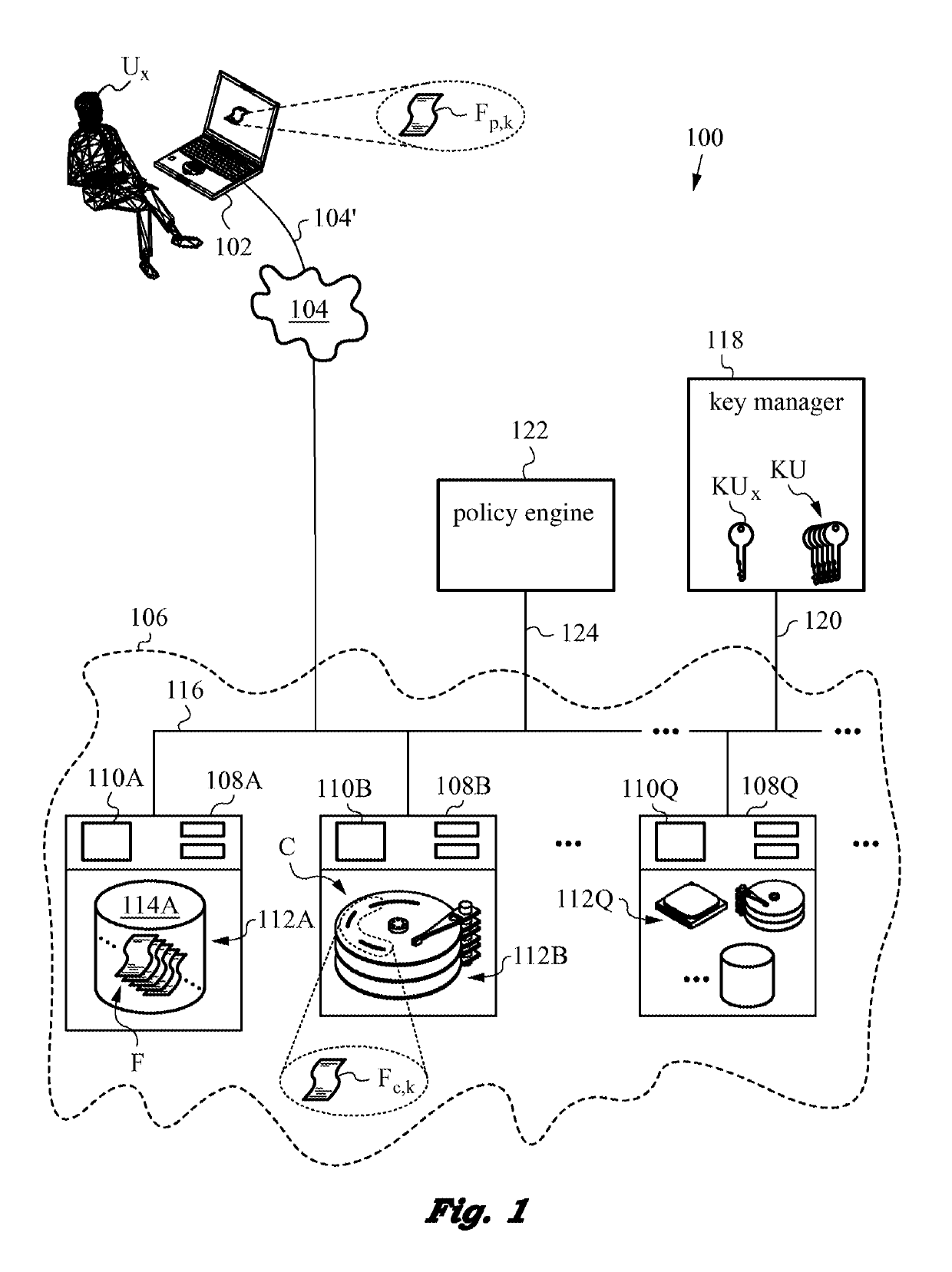
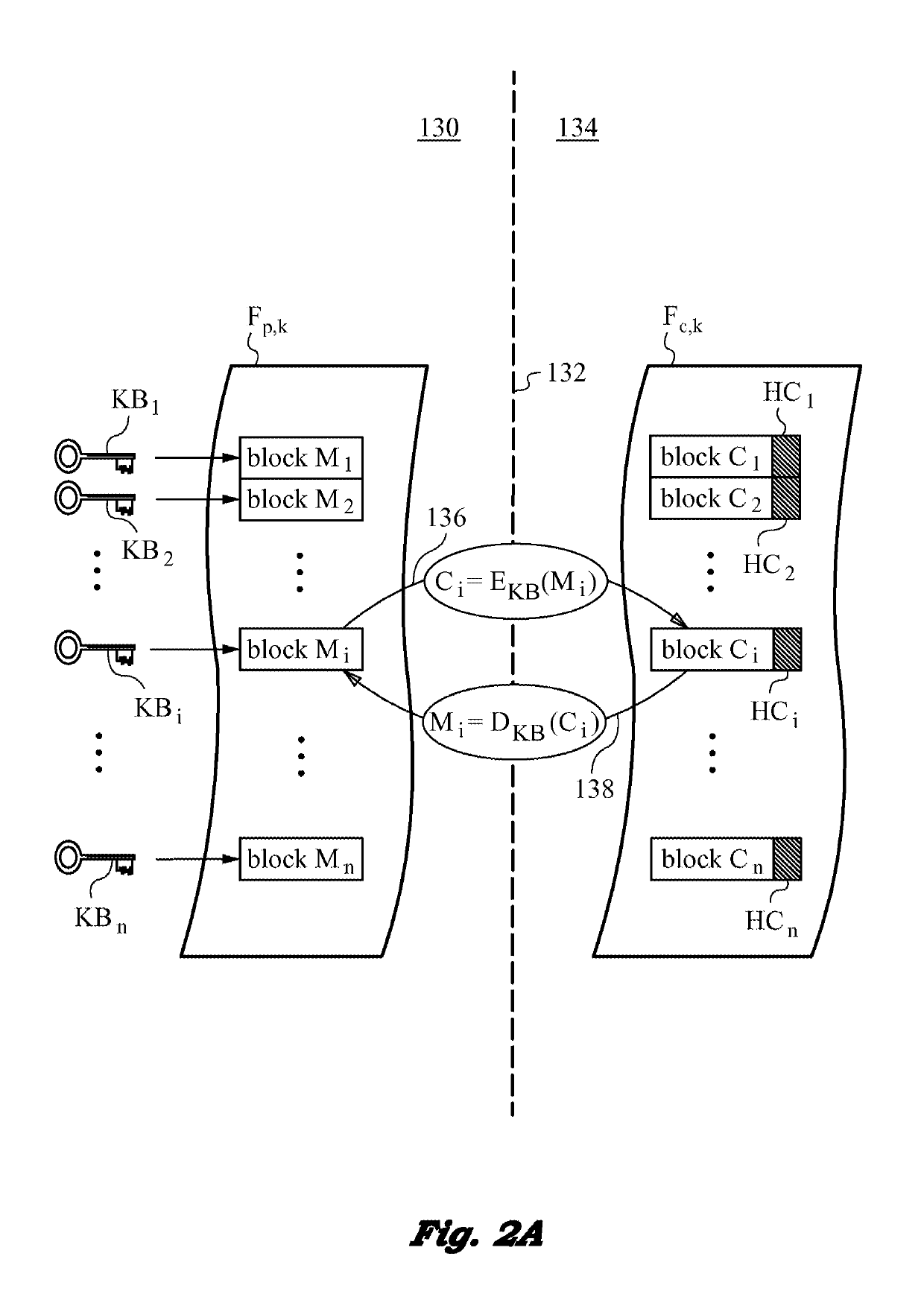
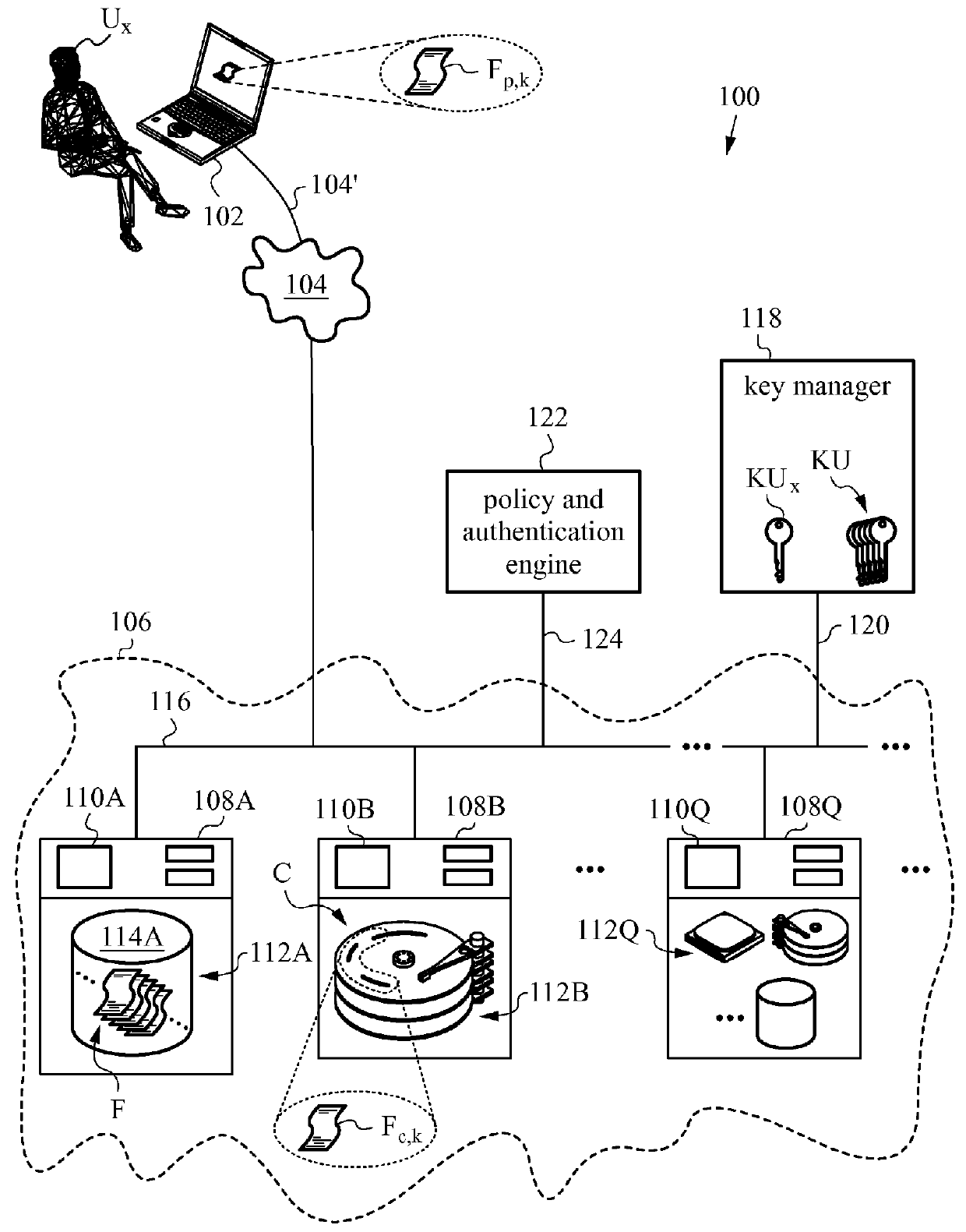
Securing files under the semi-trusted user threat model using per-file key encryption
ActiveUS20160277373A1Improve security levelEnsure integrityInterprogram communicationComputer security arrangementsFile allocationCiphertext
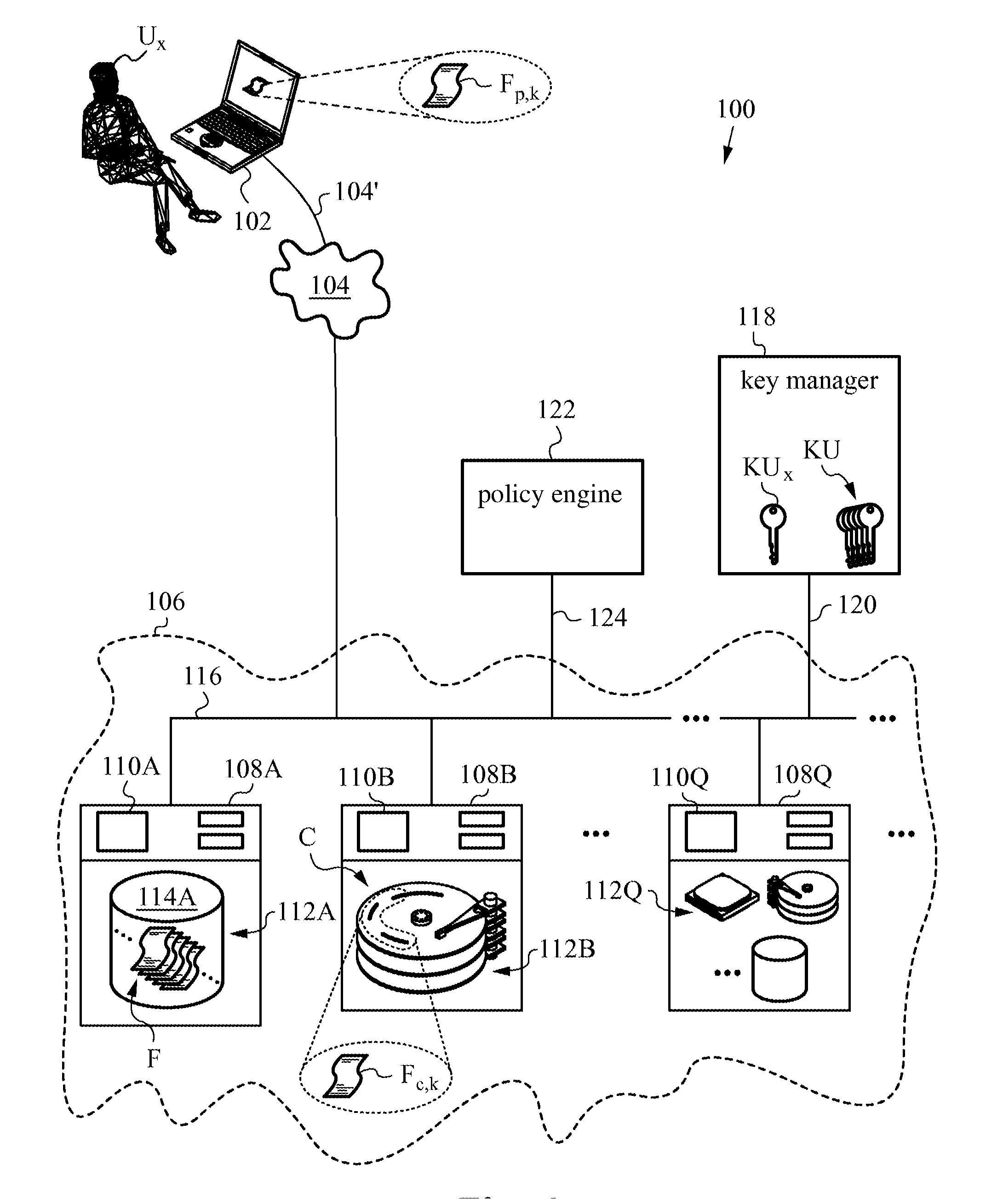
A computer system and methods for securing files in a file system with storage resources accessible to an authenticable user using an untrusted client device in a semi-trusted client threat model. Each file is secured in the file system in one or more ciphertext blocks along with the file metadata. Each file is assigned a unique file key FK to encrypt the file. A wrapping key WK assigned to the file is used for encrypting the file key FK to produce a wrapped file key WFK. The file is encrypted block by block to produce corresponding ciphertext blocks and corresponding authentication tags. The authentication tags are stored in the file metadata, along with an ID of the wrapping key WK, wrapped file key WFK, last key rotation time, an Access Control List (ACL), etc. The integrity of ciphertext blocks is ensured by authentication tags and the integrity of the metadata is ensured by a message authentication code (MAC).
Owner:ZETTASET
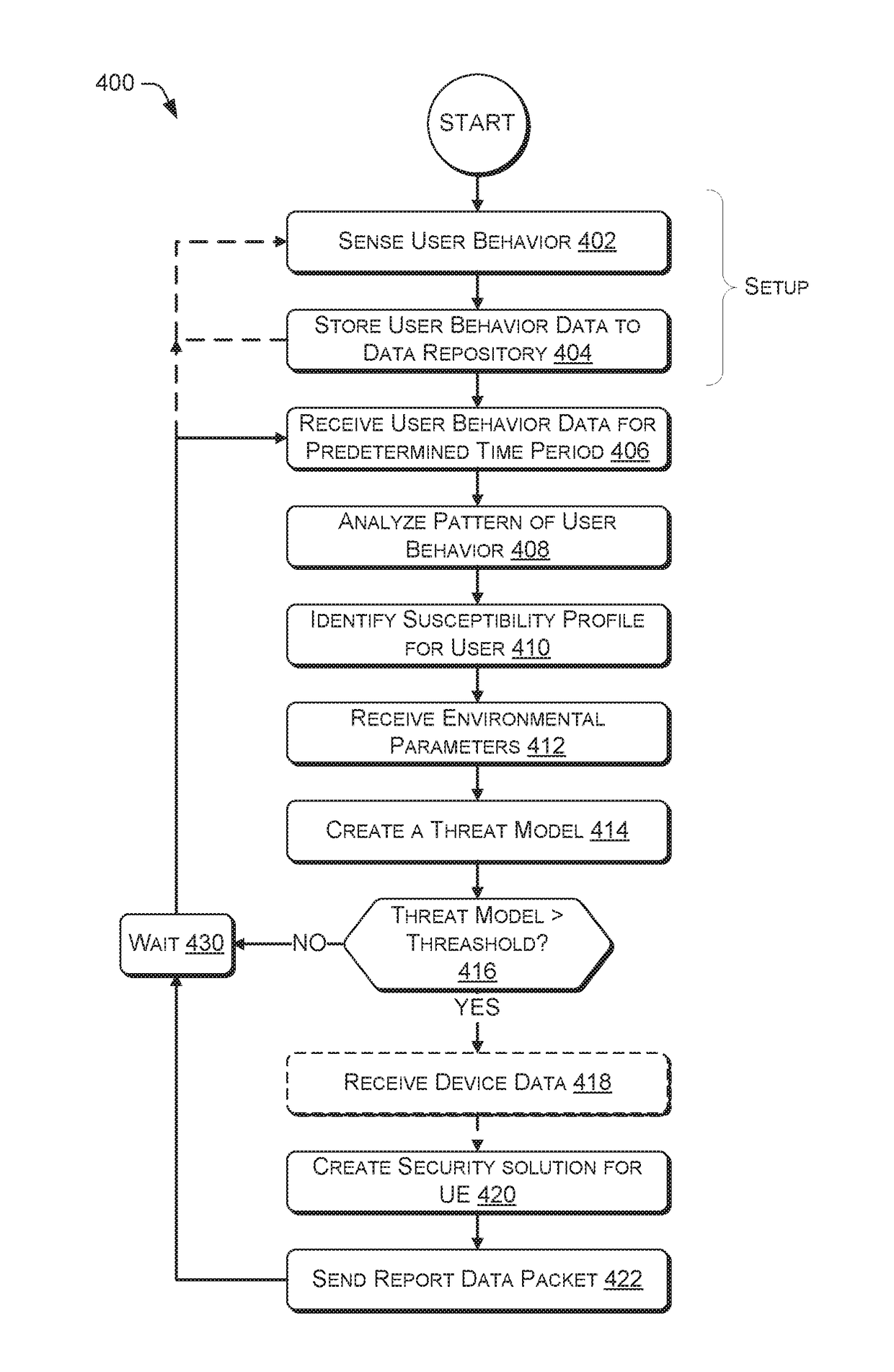
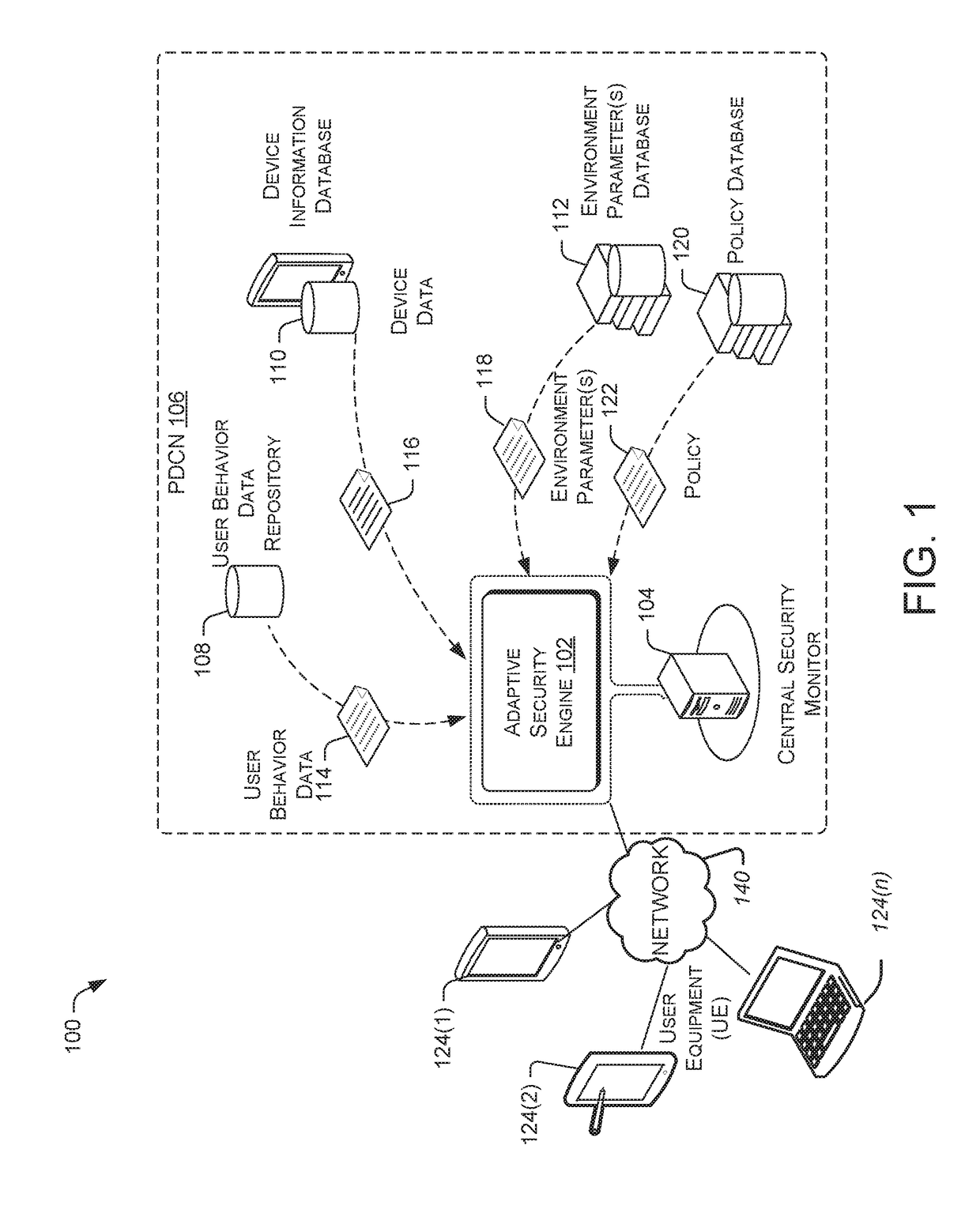
Security via adaptive threat modeling
A methods and systems of providing security based on an identified susceptibility profile of a user are provided. Behavioral data related to an account of a user is received for a predetermined period. The behavioral data is analyzed for a pattern of on-line behavior of the user. A susceptibility profile of the user is created based on the pattern of on-line behavior. Environment parameters are received from a database. A security threat model is created based on the susceptibility profile and the environment parameters. A report data packet based on the created threat model is sent to an account of the user.
Owner:T MOBILE USA
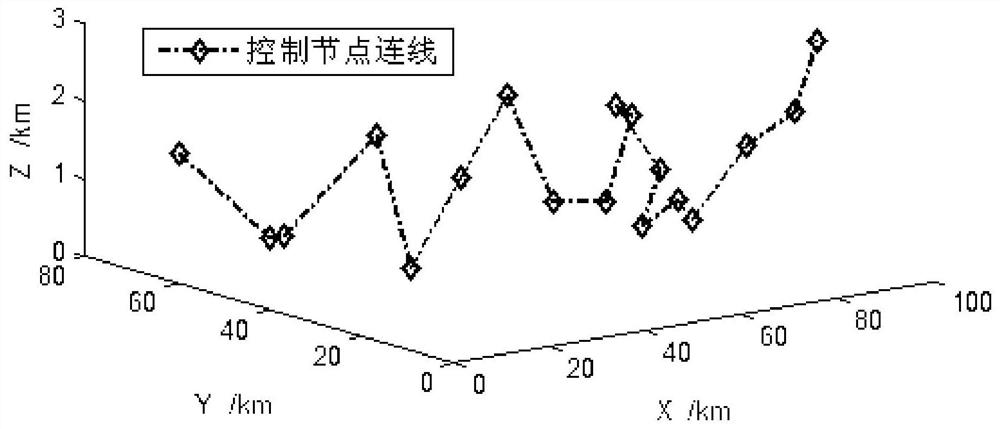
Method of planning three dimensional route of unmanned plane by means of improved artificial fish swarm algorithm
InactiveCN107392388AReduce complexityImprove search capabilitiesForecastingArtificial lifeOptimum routeLandform
The invention discloses a method of planning three dimensional route of an unmanned plane by means of an improved artificial fish swarm algorithm. The method of planning three dimensional route of an unmanned plane by means of an improved artificial fish swarm algorithm is used for carrying out static state planning of route and real-time dynamic re-planning of route when an unmanned plane executes a single task. The method of planning three dimensional route of an unmanned plane by means of an improved artificial fish swarm algorithm includes the steps: constructing a digital map through a landform model and a simplified threat model, considering the influence of space division granularity on the complexity of an optimizing control algorithm, and realizing division of space according to a fence self-adaptive algorithm; realizing static state route planning by means of an improved artificial fish swarm algorithm; and considering the time factor, constructing a threat prediction model based on a dynamic Bayesian network, predicting the unexpected threat, combined with flight constraint of the unmanned plane, obtaining the re-planning starting point, and realizing global route dynamic re-planning by means of the improved artificial fish swarm algorithm. The method of planning three dimensional route of an unmanned plane by means of an improved artificial fish swarm algorithm has the advantages of reducing the complexity of a route optimizing control algorithm, improving the optimum route searching capability, and satisfying the practical route planning demand.
Owner:NANCHANG HANGKONG UNIVERSITY
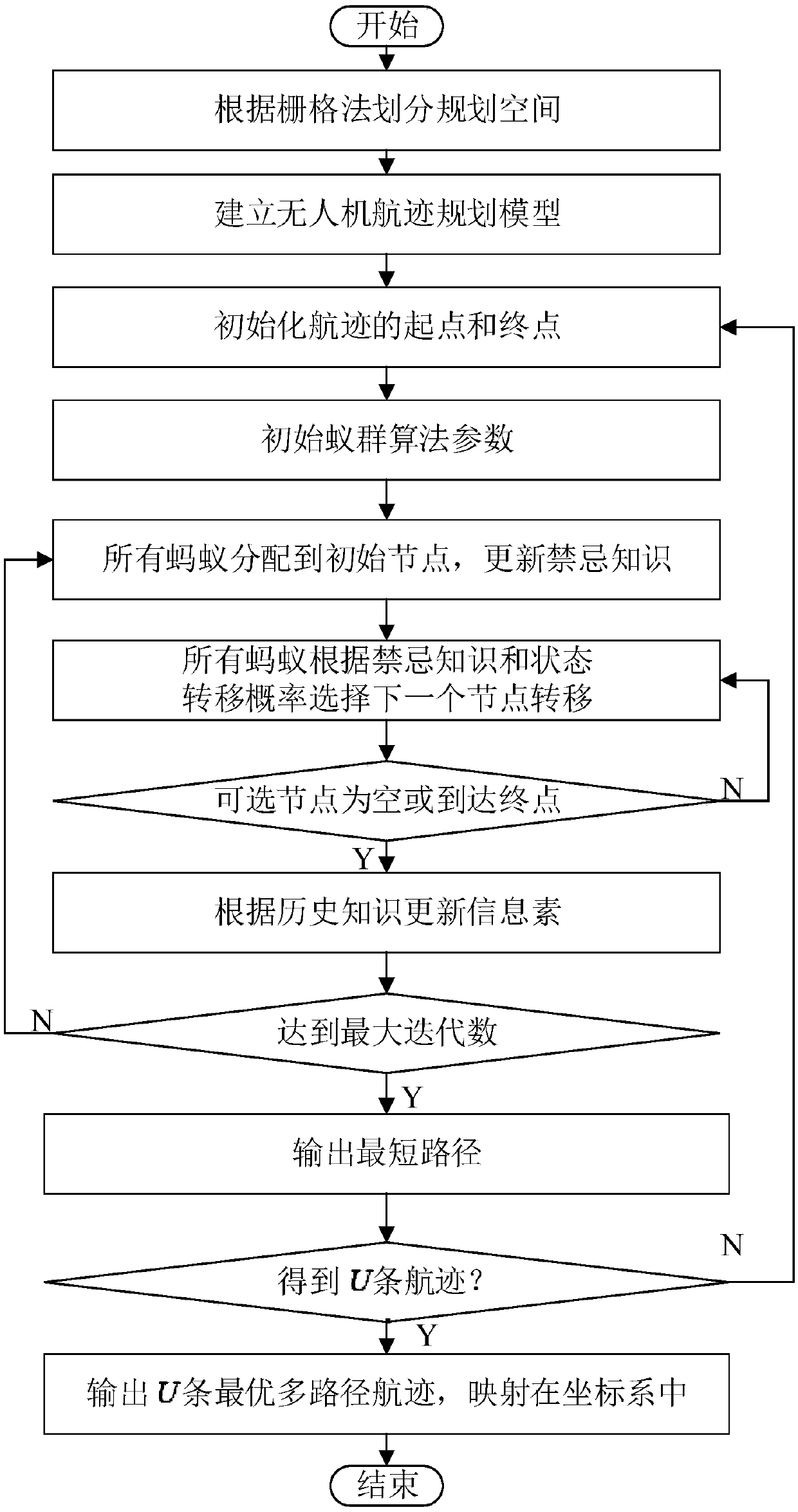
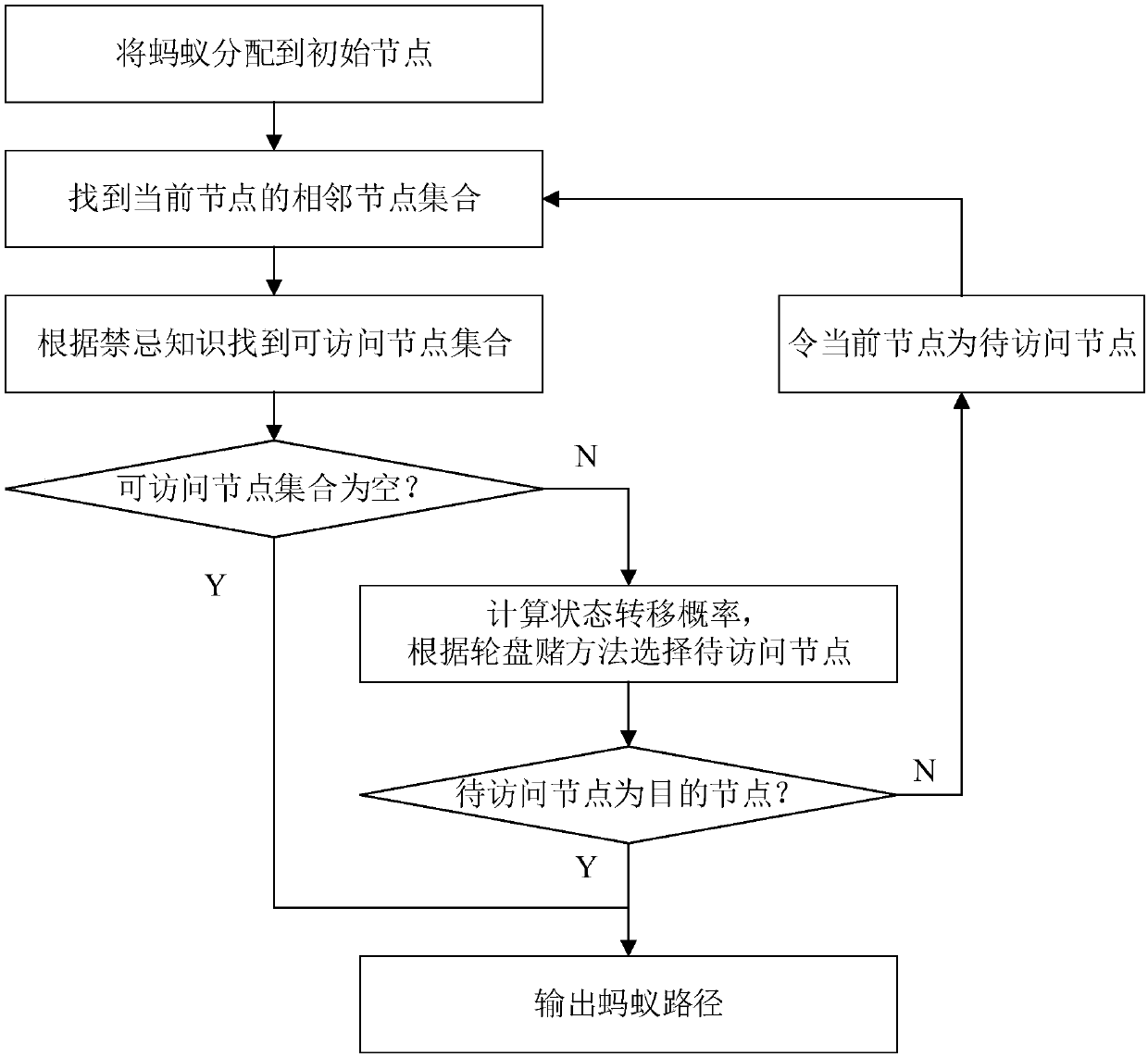
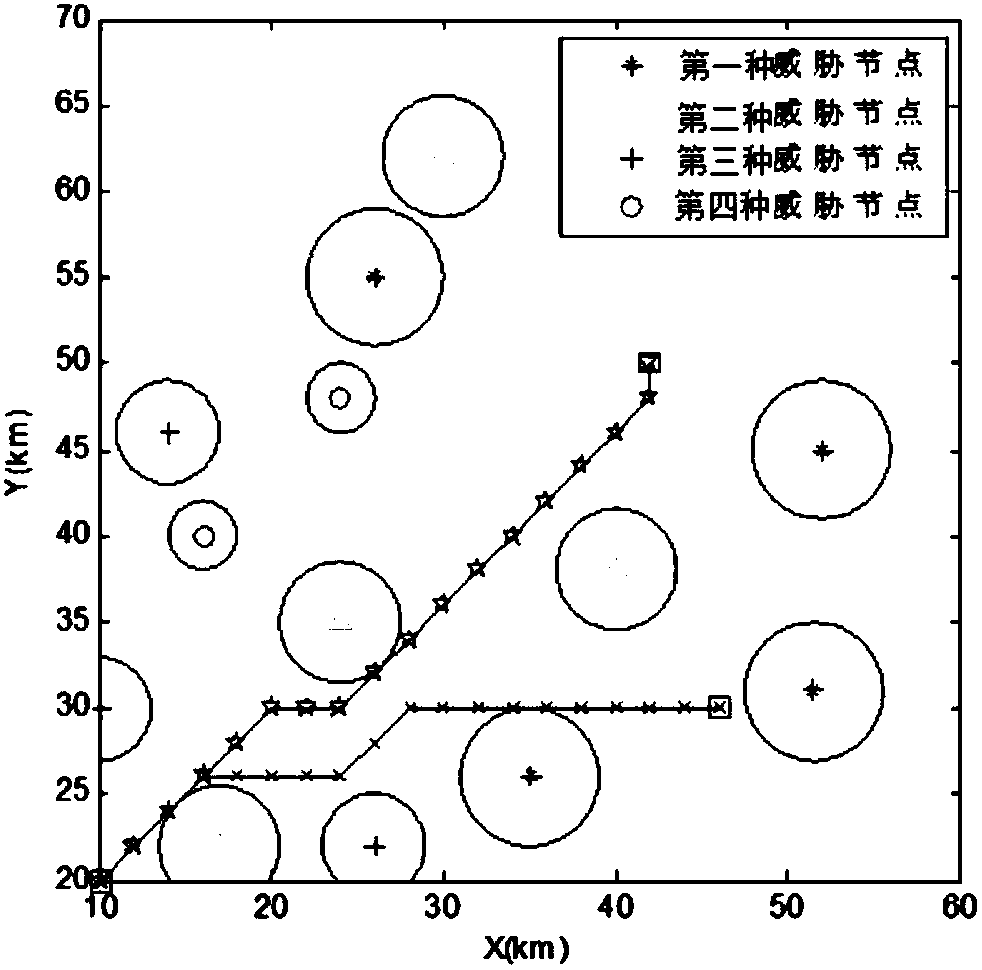
Multi-unmanned aerial vehicle track planning method based on culture ant colony search mechanism
ActiveCN107622327ASolving multipath trajectory planning problemsWide applicabilityForecastingBiological modelsNODALSimulation
The invention provides a multi-unmanned aerial vehicle (UAV) track planning method based on a culture ant colony search mechanism, which includes the following steps: (1) carrying out mesh generationon a standard space according to a grid method; (2) building a multi-UAV track planning model, including the number of UAVs, the start and end points and a threat model; (3) initializing the start point and the end point; (4) initializing an ant colony algorithm, including: initializing an ant colony and calculating a heuristic factor and a guide factor; and (5) assigning all ants to an initial node, and updating taboo knowledge; selecting next node for transfer according to the taboo knowledge and the state transfer probability until there is no optional node or a destination node is selected, updating historical knowledge, and updating pheromones according to the historical knowledge; and outputting a shortest path if the maximum number of iterations is achieved, and continuing the process until U multi-UAV optimal multi-path tracks are obtained. The problem that it is difficult to find the optimal flight tracks of unmanned aerial vehicles due to slow search and heavy computing burden is solved, and multi-UAV track planning is realized.
Owner:HARBIN ENG UNIV
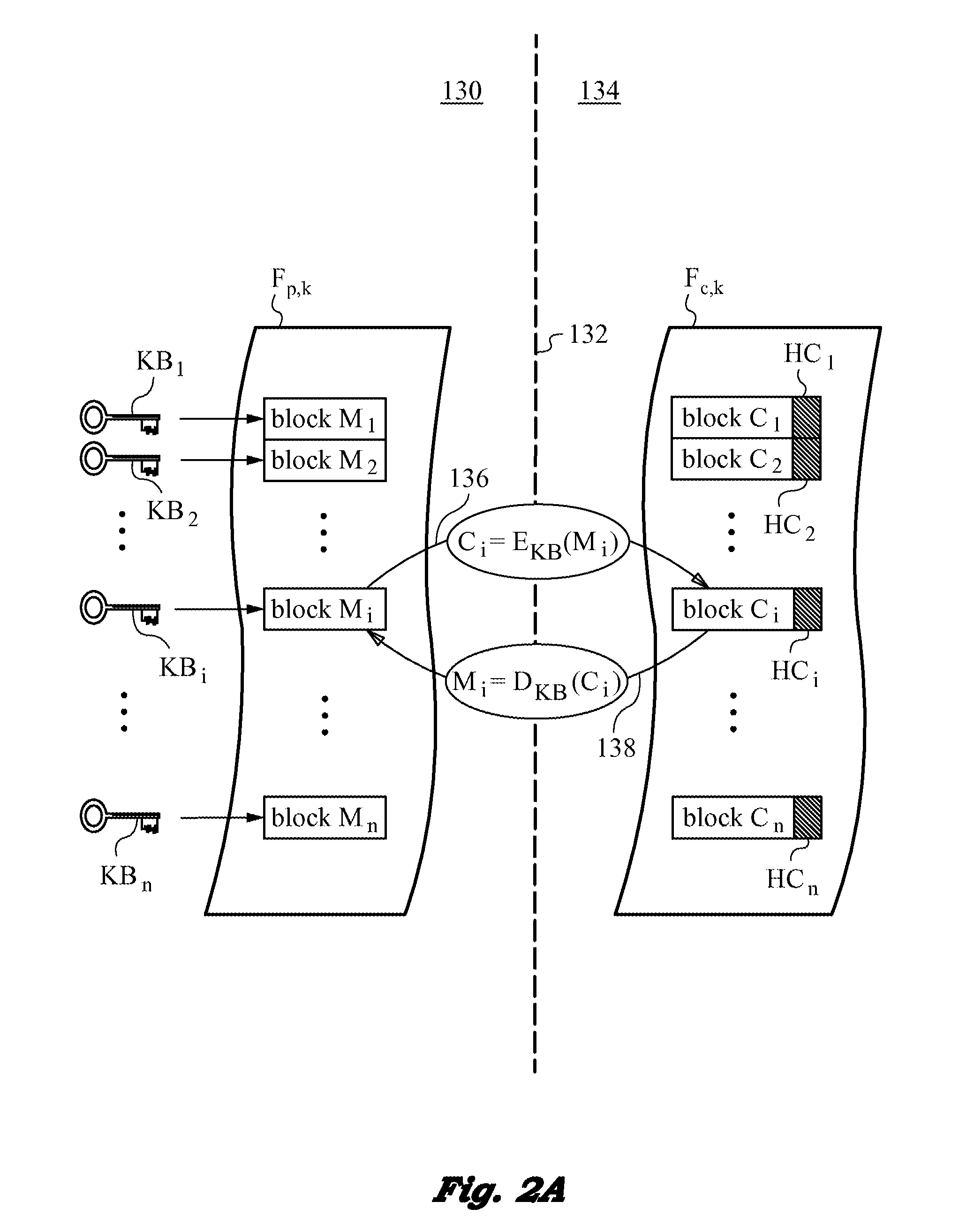
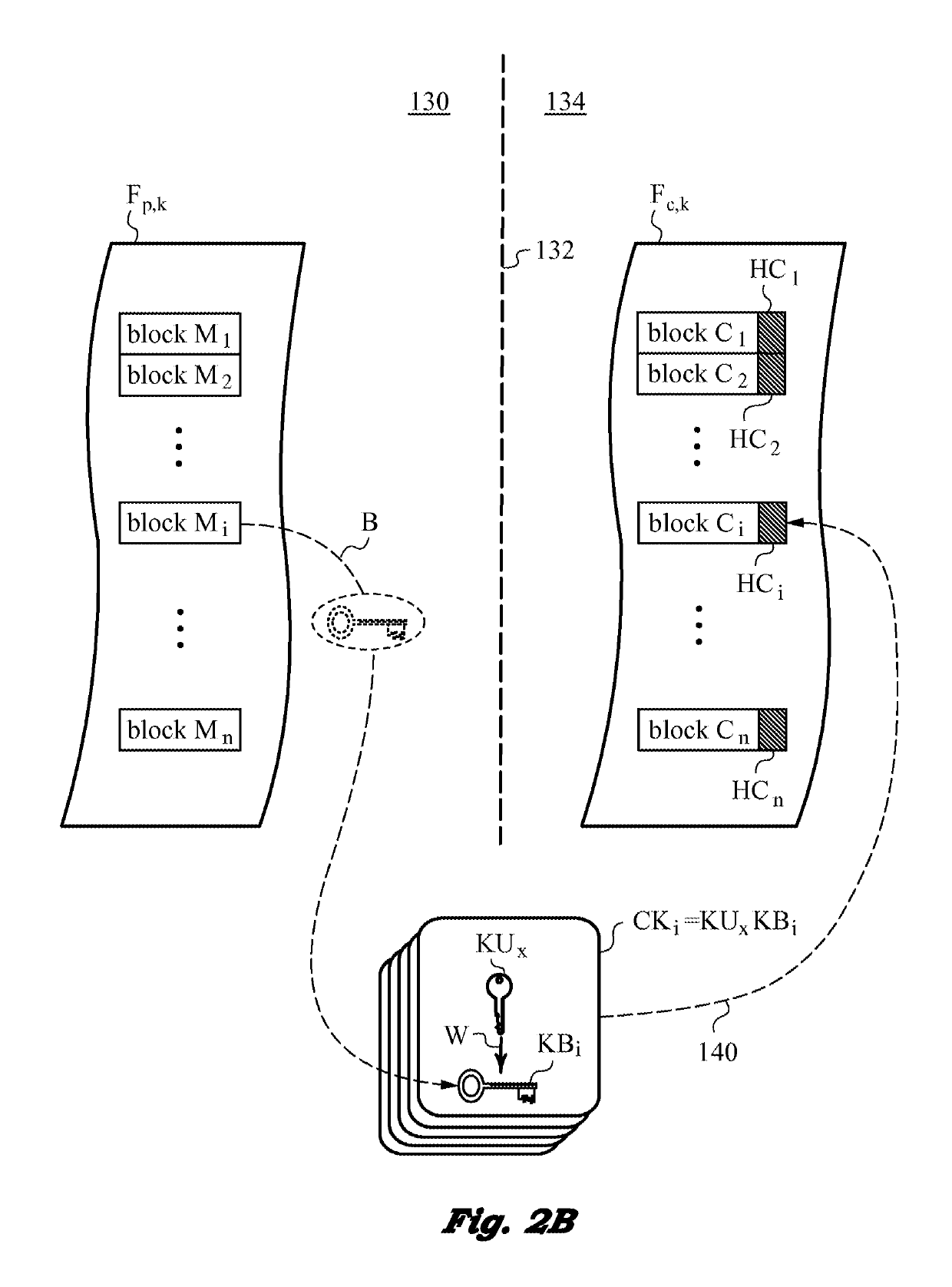
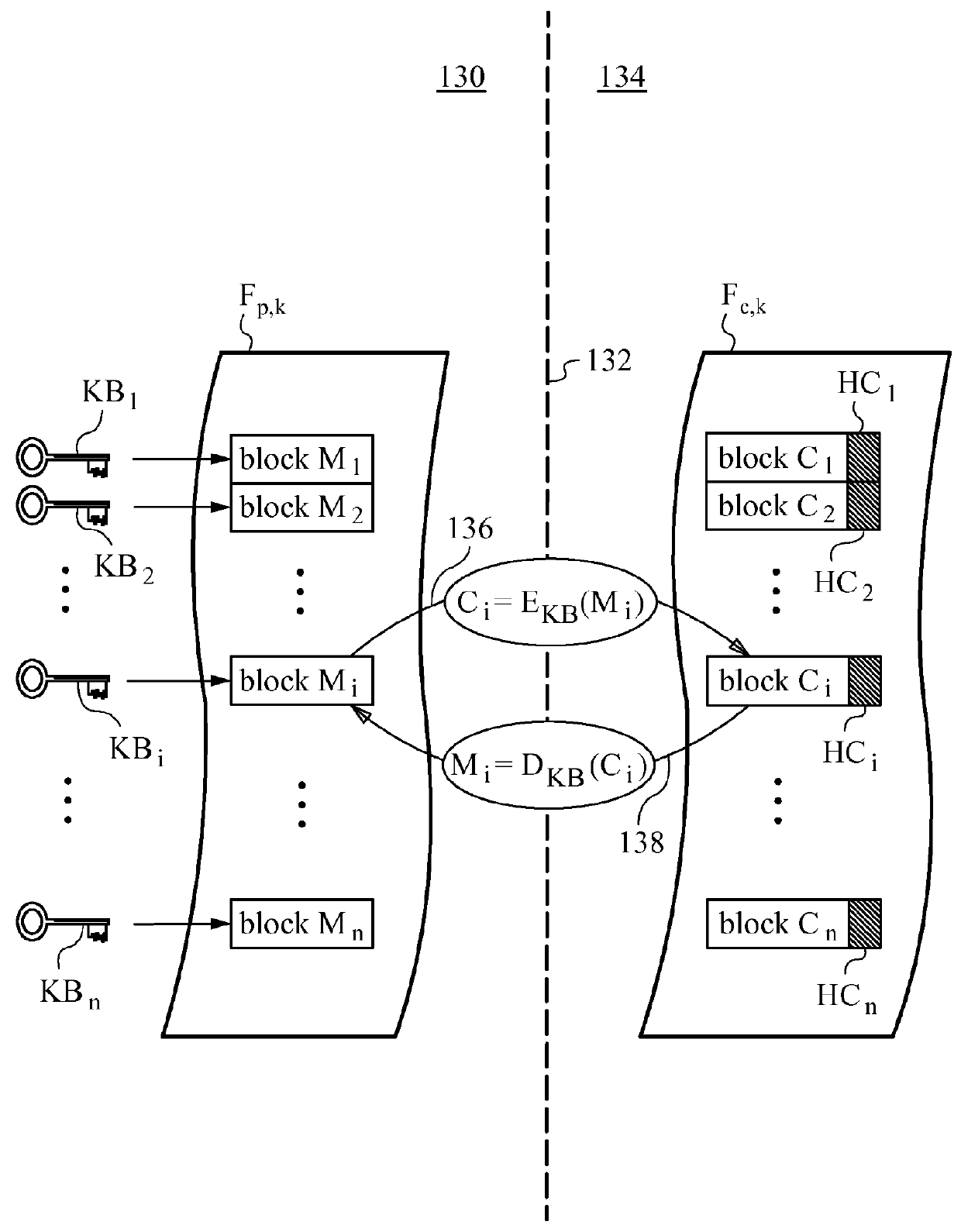
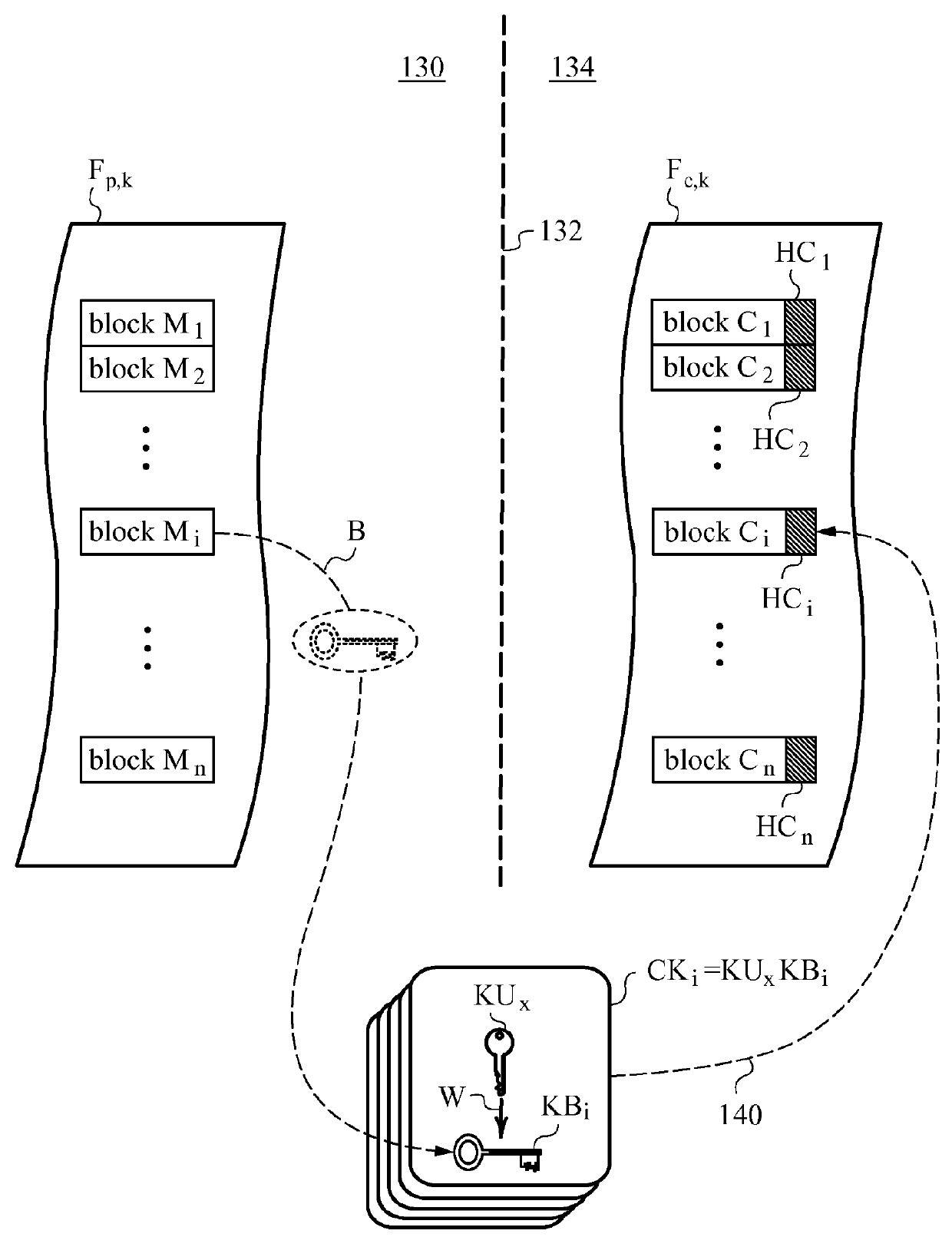
Method of securing files under the semi-trusted user threat model using symmetric keys and per-block key encryption
ActiveUS20150288664A1Rapid and efficientImprove security levelKey distribution for secure communicationMultiple keys/algorithms usageFile systemTrusted client
A computer system and method for securing files in a file system equipped with storage resources that are accessible to an authenticable user operating with an untrusted client device under the semi-trusted client threat model. The file to be secured is stored in one or more blocks belonging to the storage resources along with symmetric per-block key(s) KBi assigned to each of the blocks in the file. The blocks are encrypted with the symmetric per-block keys to obtain encrypted blocks. The user is assigned user key(s) and each per-block key that was used for encryption is in turn encrypted with one of the user's keys to derive wrapped key(s) for each encrypted block. Wrapped key(s) are placed in encrypted block headers and introduce a level of indirection to encrypted file(s) that is appropriate for the semi-trusted client threat model.
Owner:ZETTASET
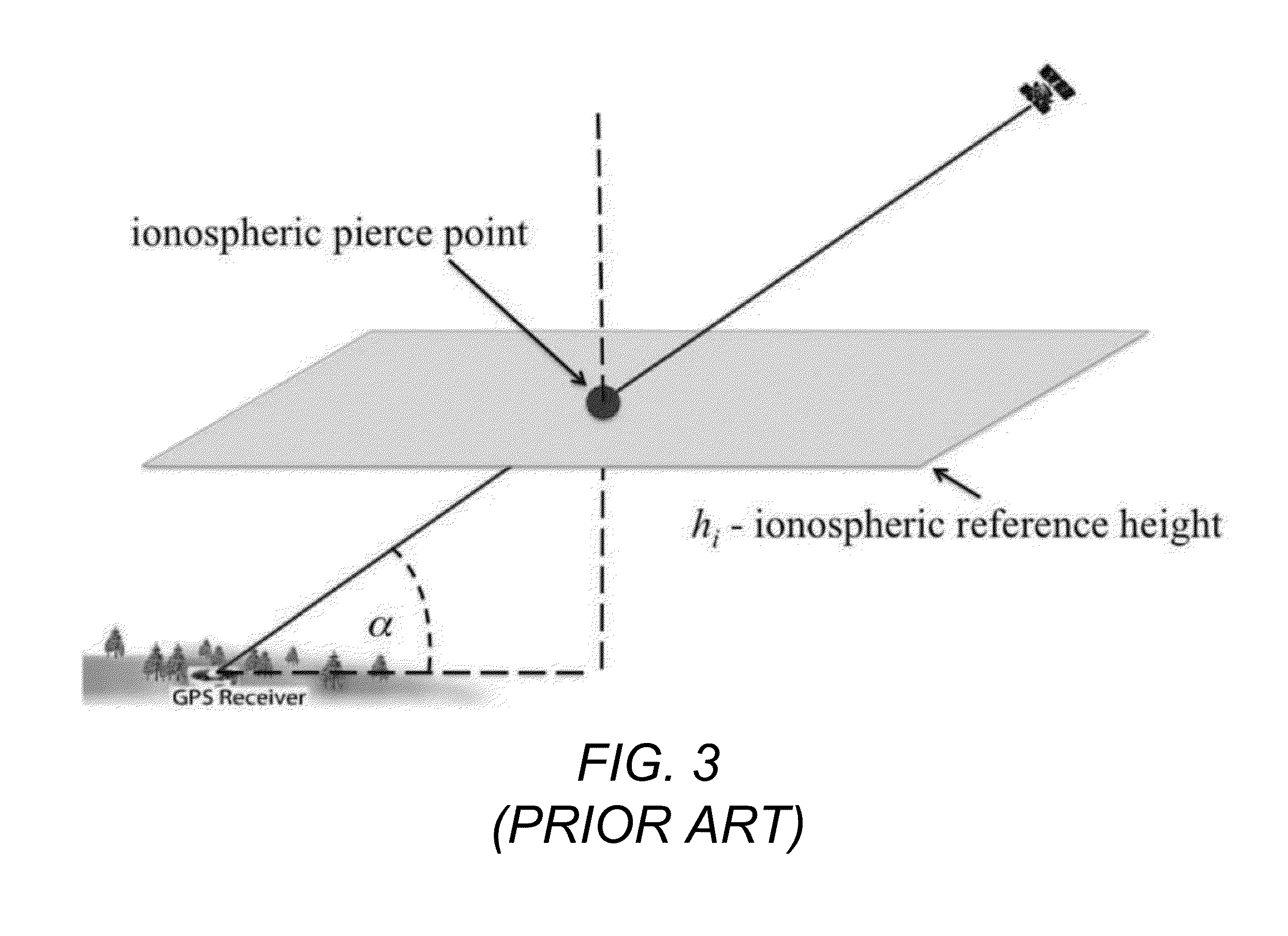
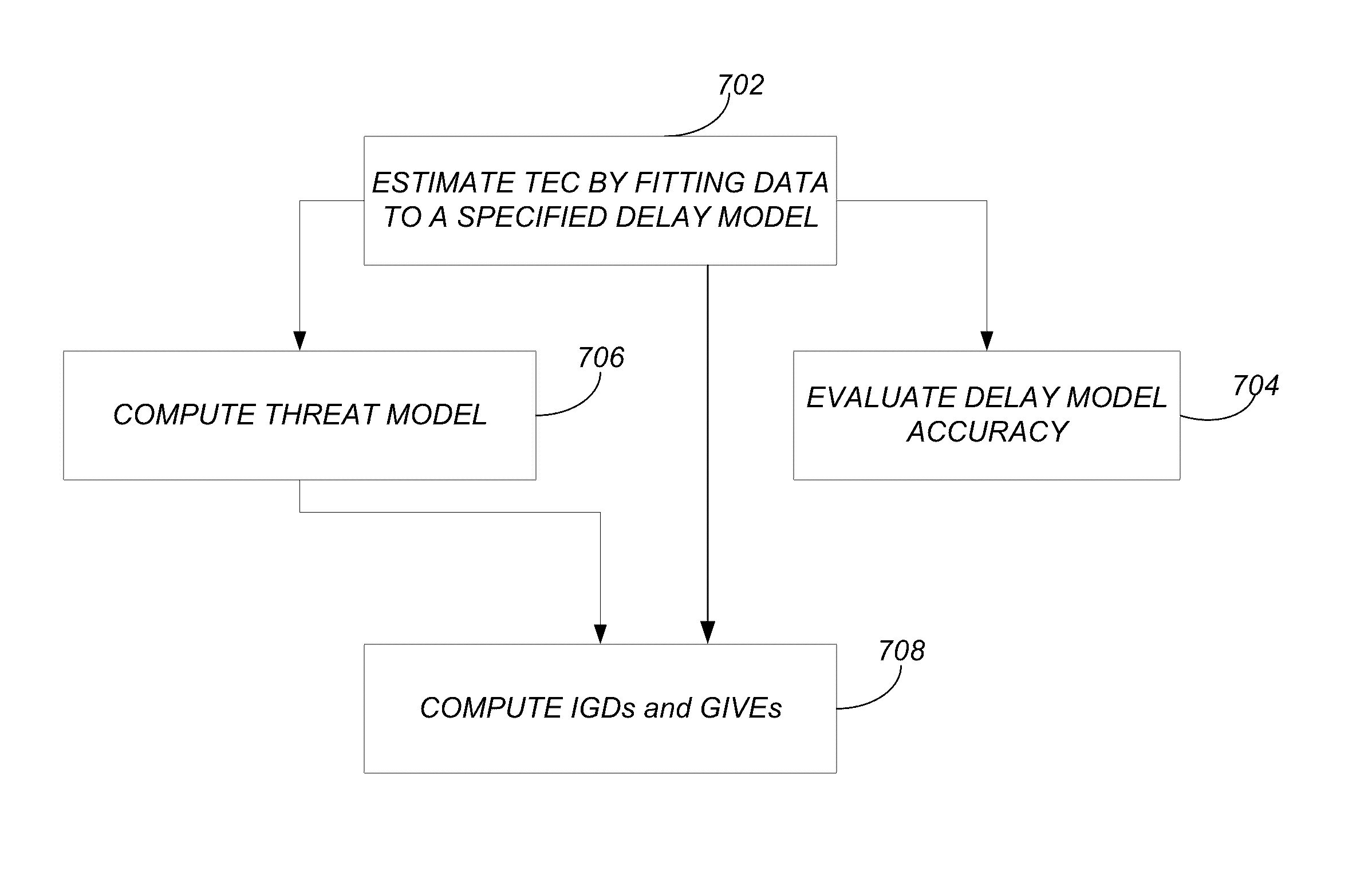
Ionospheric slant total electron content analysis using global positioning system based estimation
ActiveUS20140163938A1Irregularity may varyImproving WAAS availabilityComputation using non-denominational number representationDesign optimisation/simulationTotal electron contentIonospheric heater
A method, system, apparatus, and computer program product provide the ability to analyze ionospheric slant total electron content (TEC) using global navigation satellite systems (GNSS)-based estimation. Slant TEC is estimated for a given set of raypath geometries by fitting historical GNSS data to a specified delay model. The accuracy of the specified delay model is estimated by computing delay estimate residuals and plotting a behavior of the delay estimate residuals. An ionospheric threat model is computed based on the specified delay model. Ionospheric grid delays (IGDs) and grid ionospheric vertical errors (GIVEs) are computed based on the ionospheric threat model.
Owner:CALIFORNIA INST OF TECH
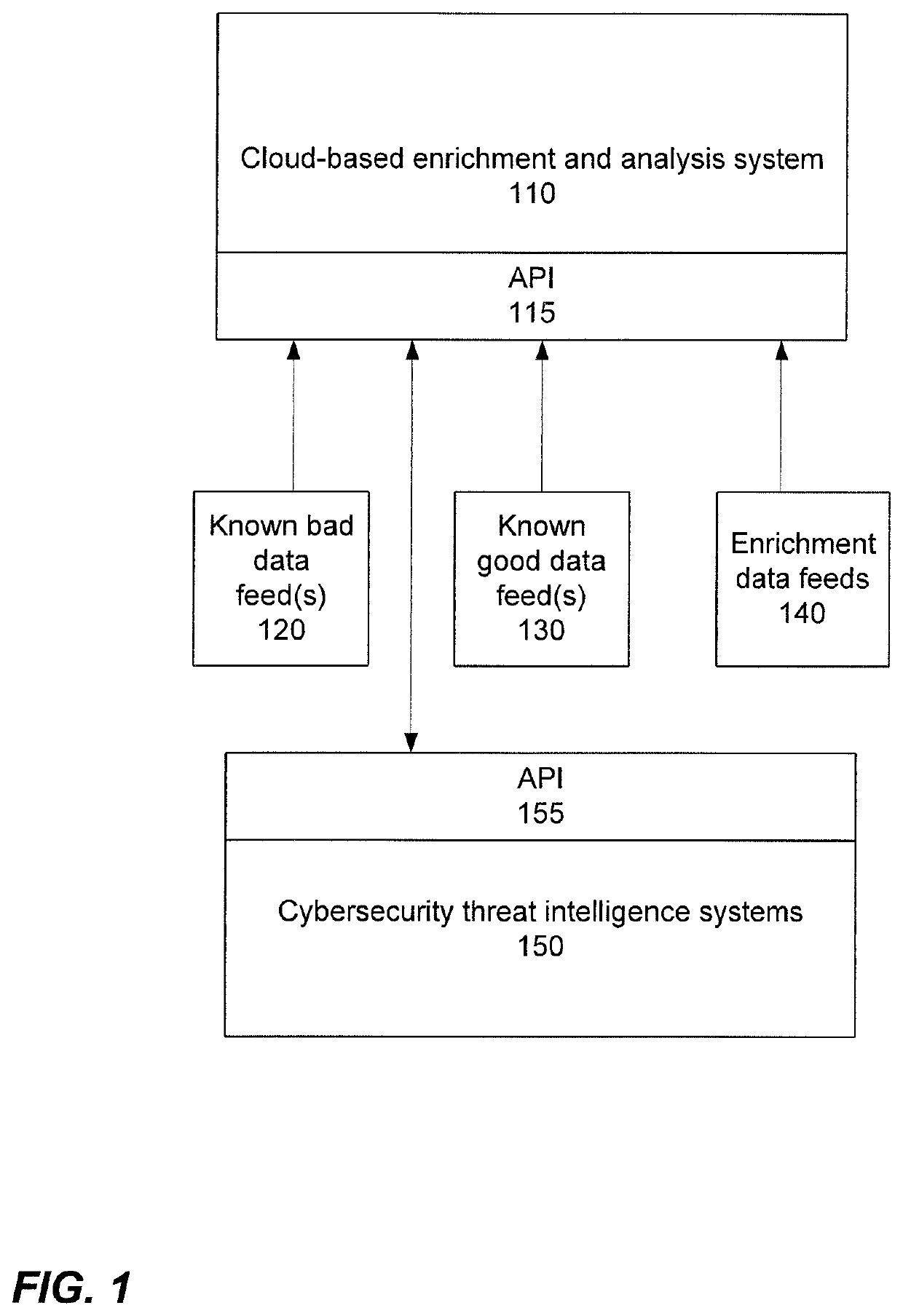
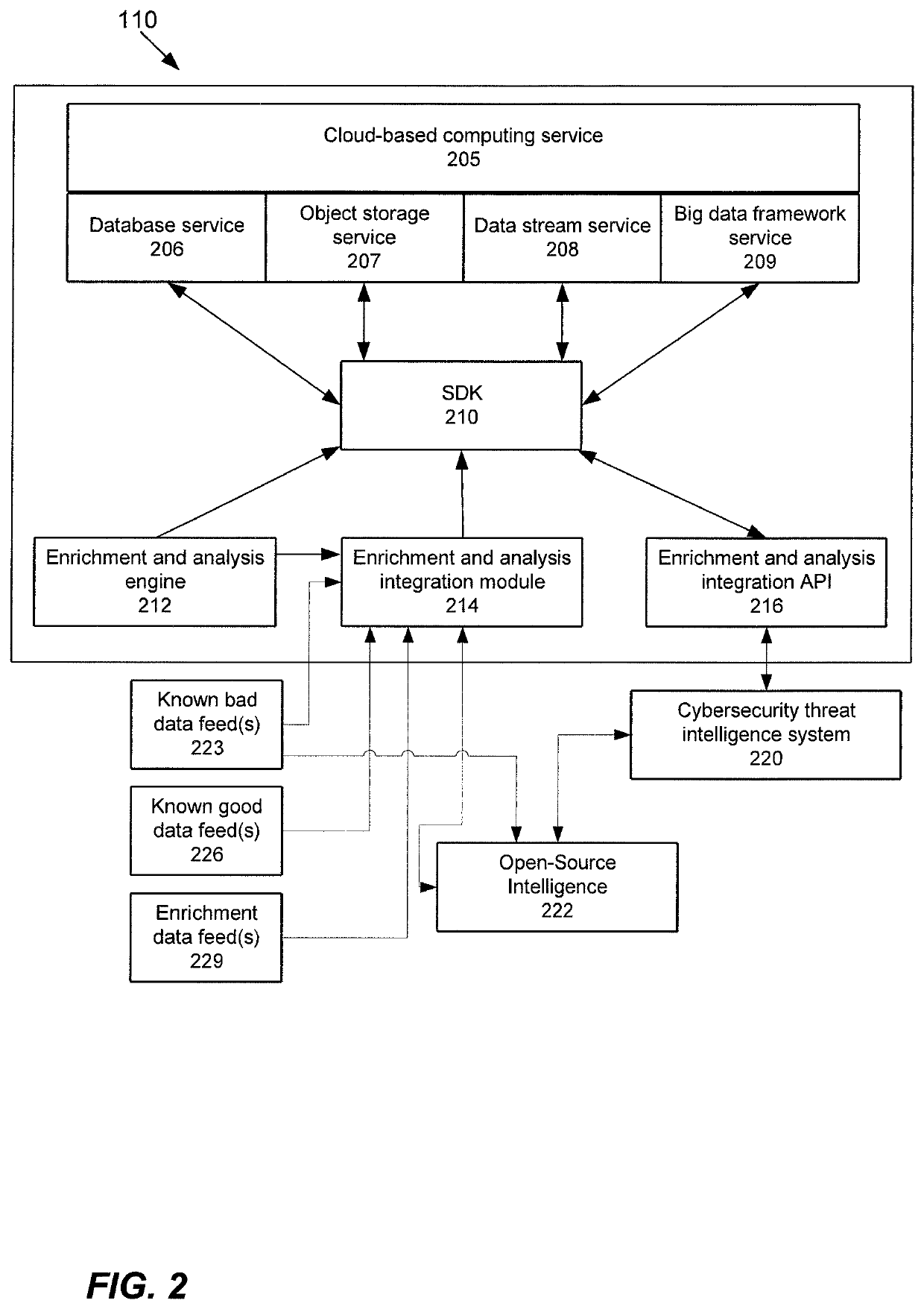
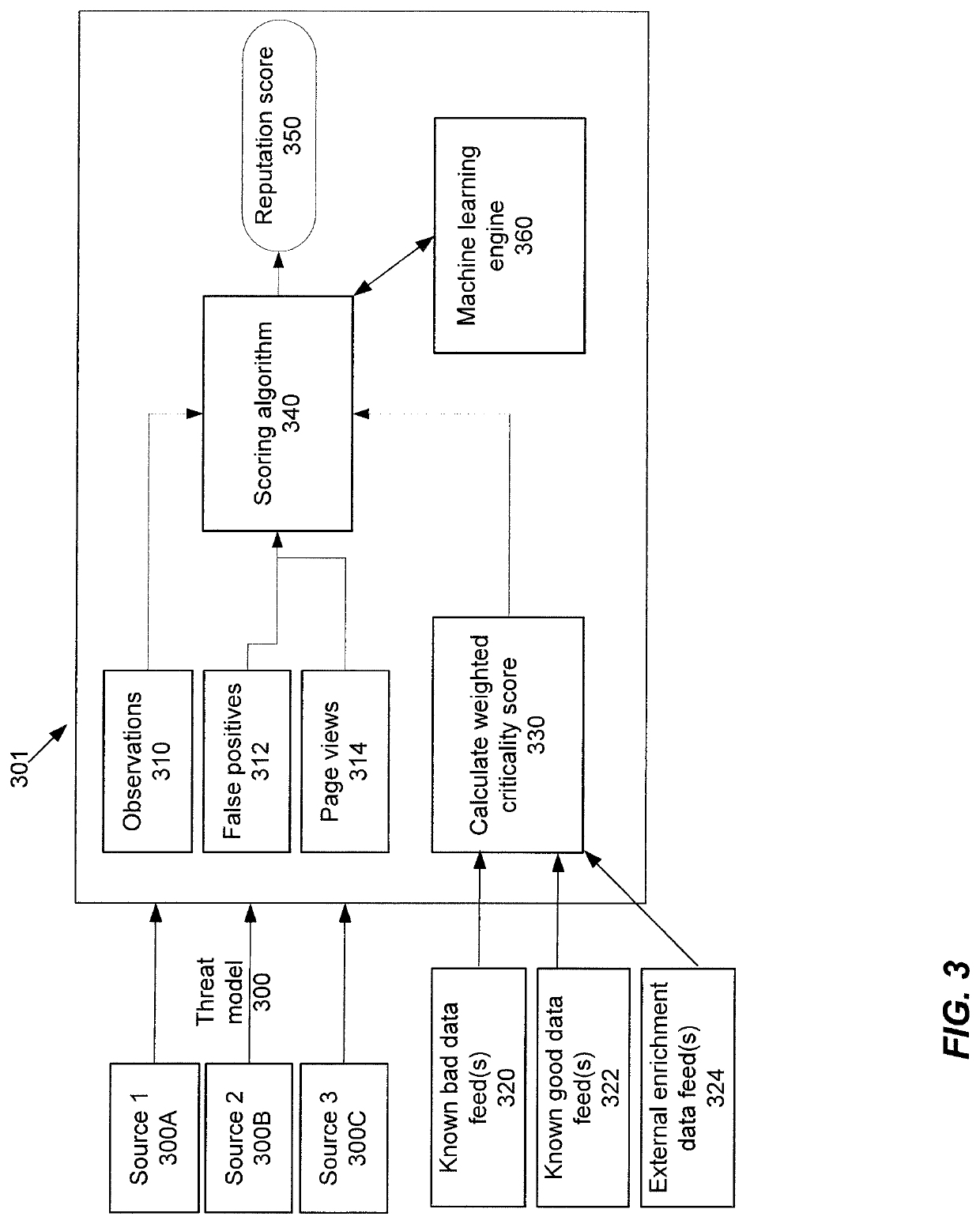
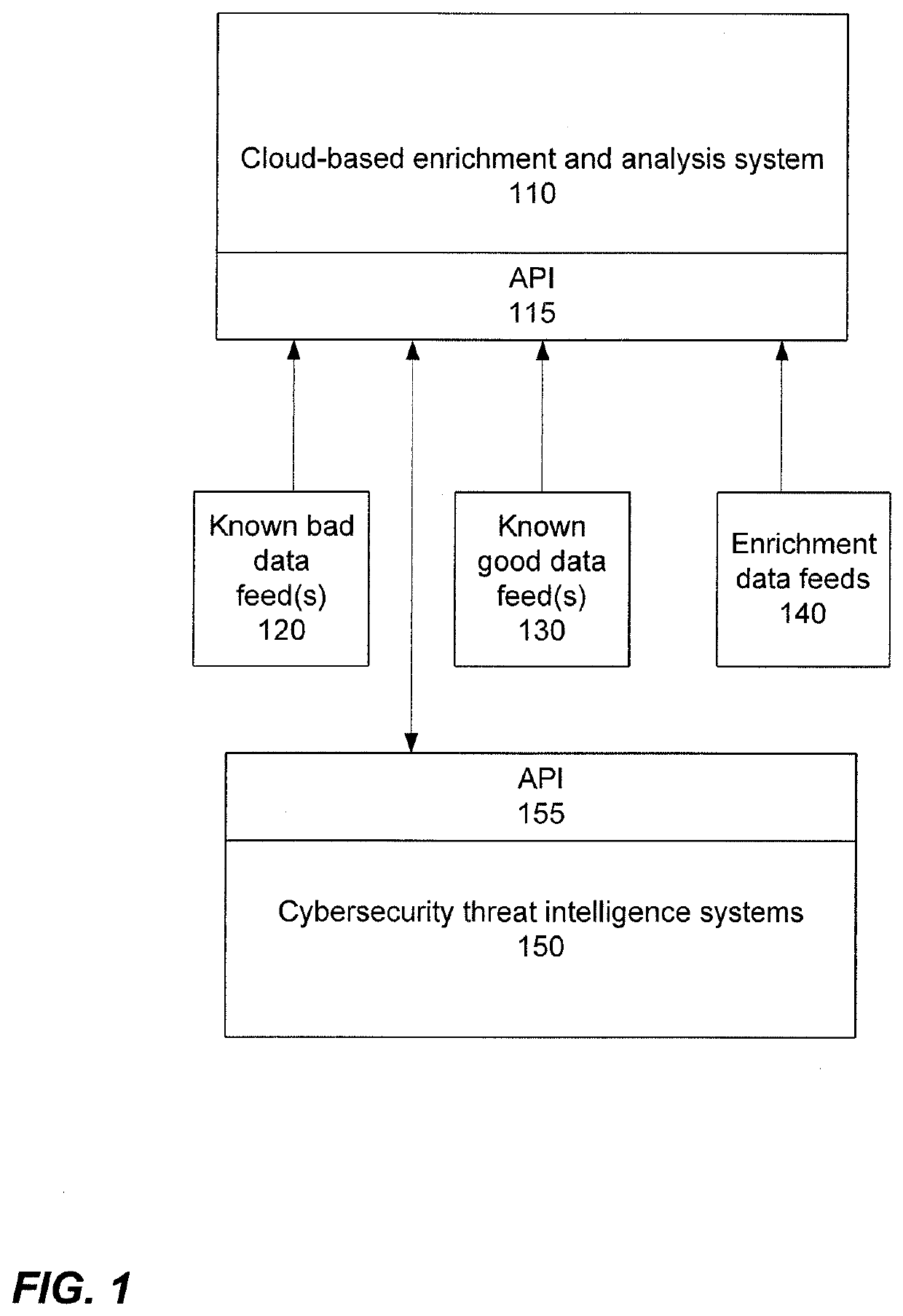
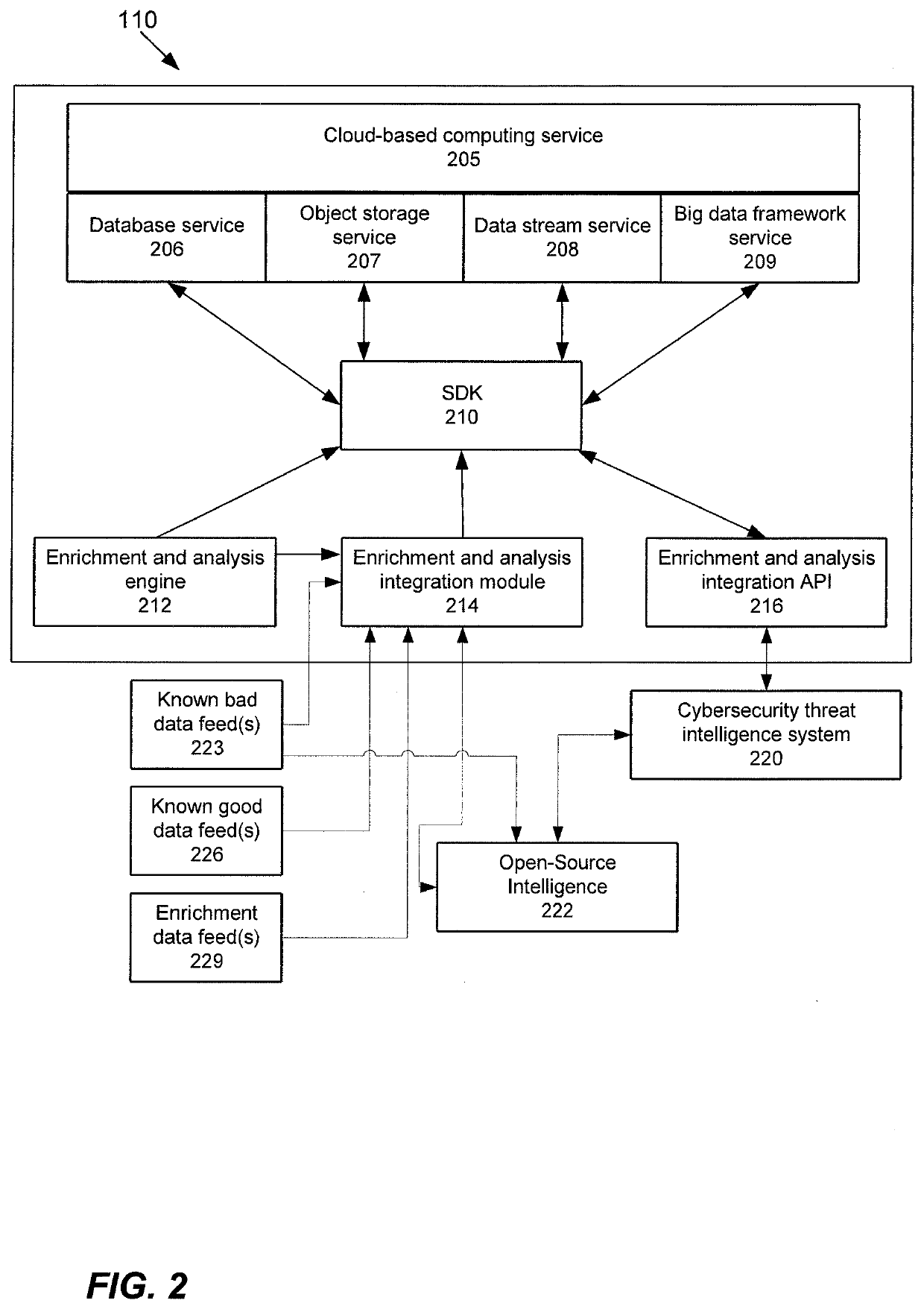
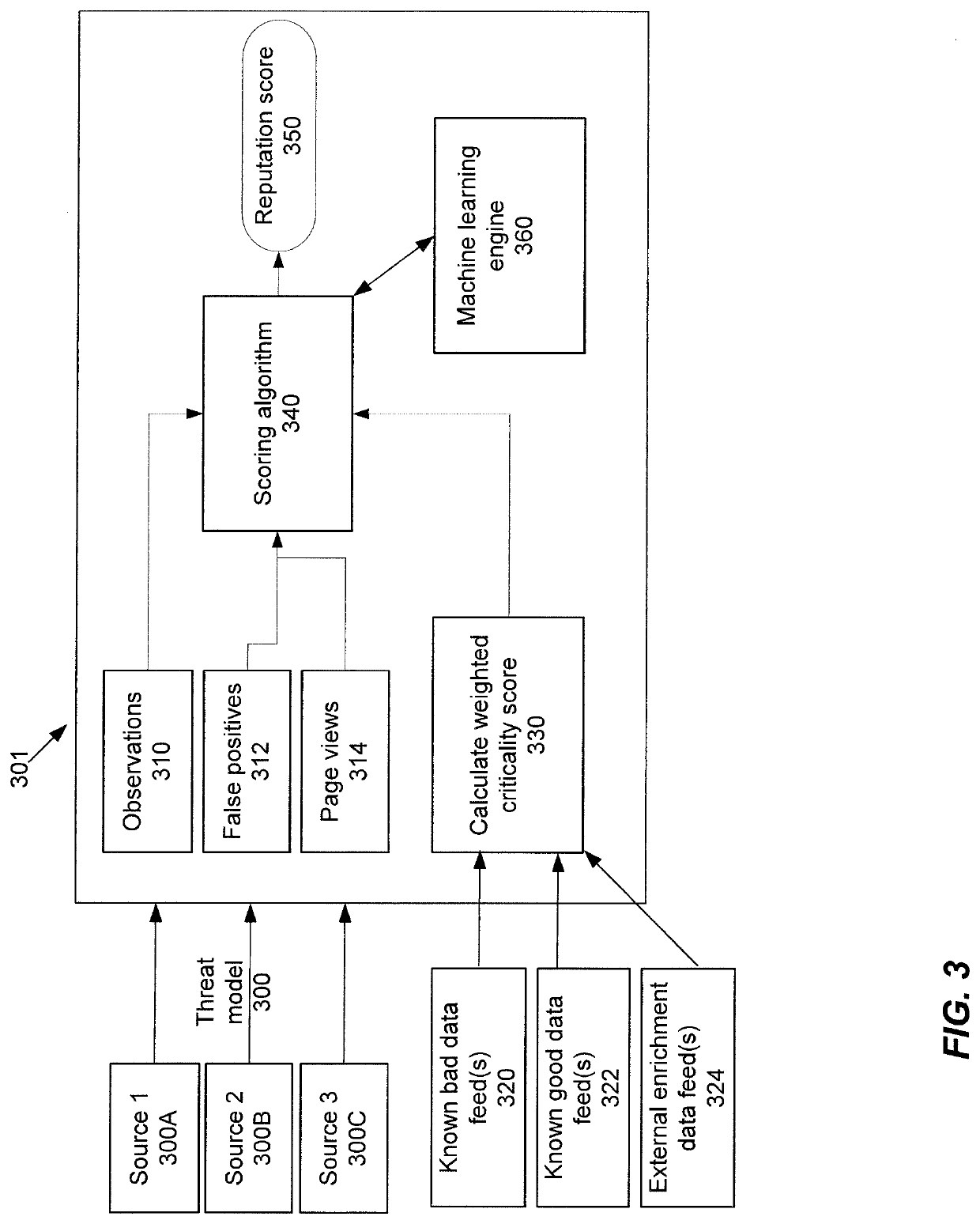
Enrichment and analysis of cybersecurity threat intelligence and orchestrating application of threat intelligence to selected network security events
Techniques are disclosed which can provide an orchestrated response to a cybersecurity threat. This orchestrated response may be based upon, at least in part, a reputation score. Threat model(s) may be received that identify cybersecurity threat(s). An indication of observations, false positives, and / or page views for the threat may be obtained. Data feeds may be received including known good data feeds, known bad data feeds, and enrichment data feeds. The data feeds may provide information about one or more indicators of compromise (IOC). For each IOC, a weighted criticality score may be determined. The weighted criticality score may be mapped to a corresponding point value. An aggregated score may be determined based upon at least the corresponding point value. A reputation score may be computed, and in some configurations, provided to a user.
Owner:THREATCONNECT INC
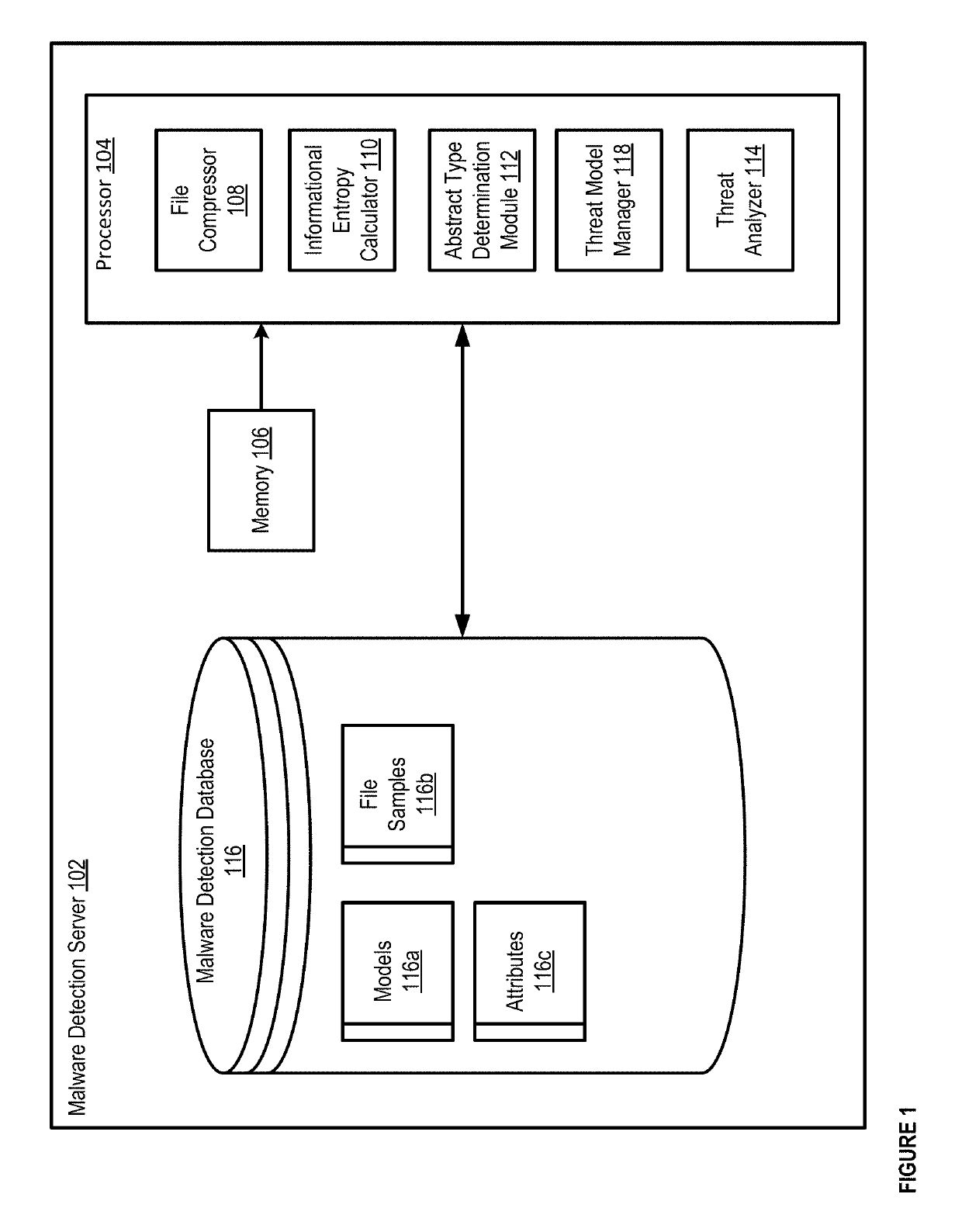
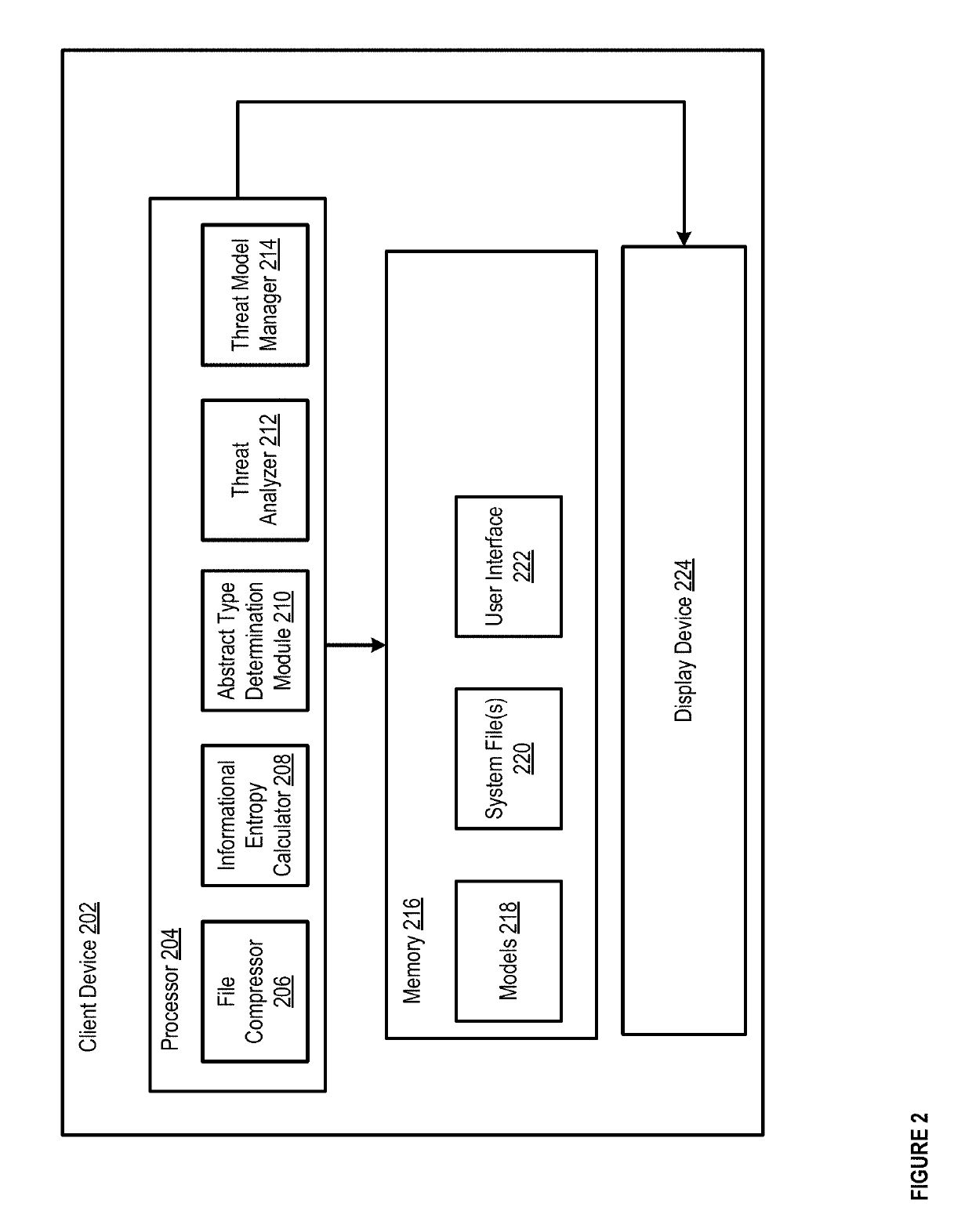
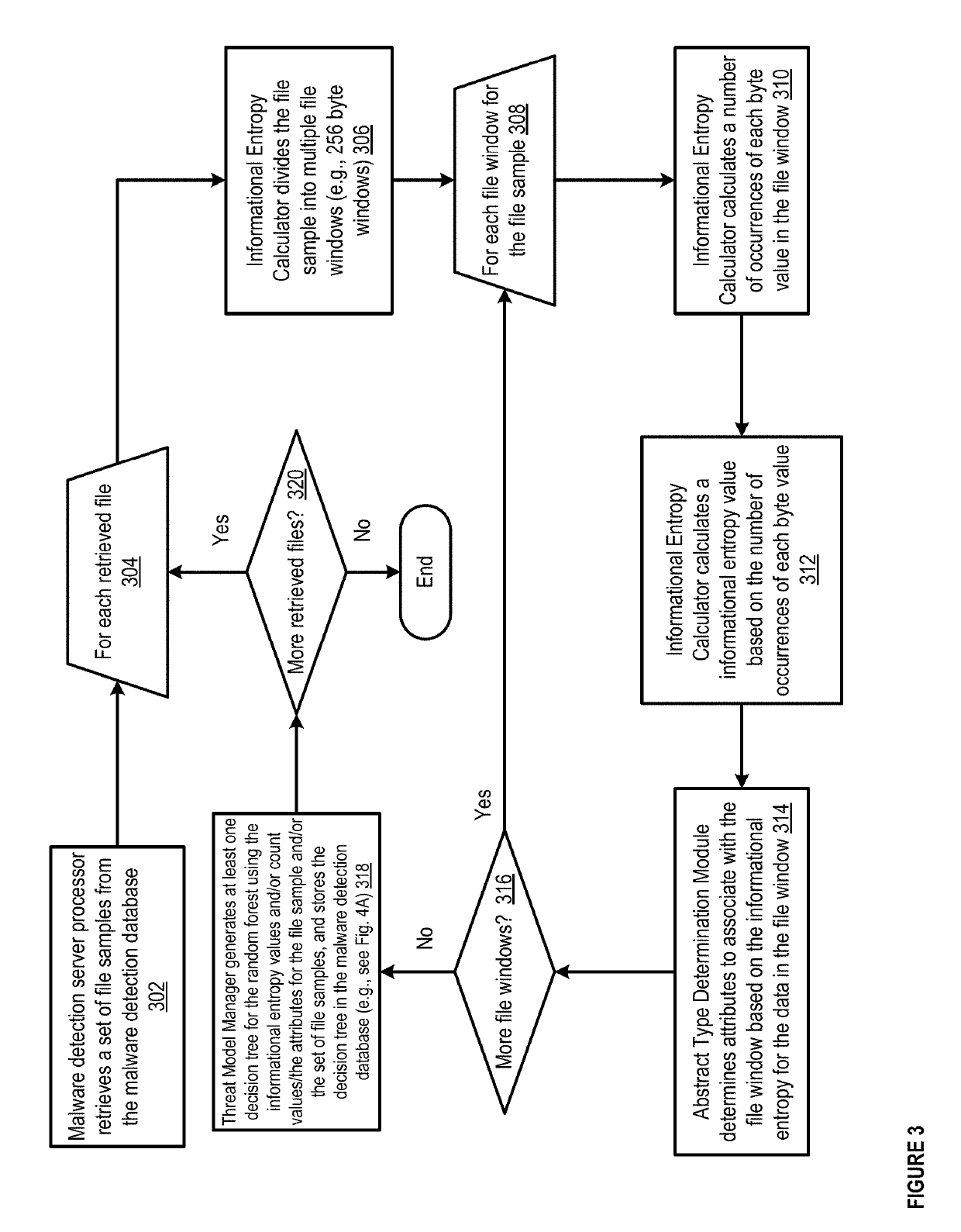
Methods and apparatus for machine learning based malware detection
Apparatus and methods describe herein, for example, a process that can include receiving a potentially malicious file, and dividing the potentially malicious file into a set of byte windows. The process can include calculating at least one attribute associated with each byte window from the set of byte windows for the potentially malicious file. In such an instance, the at least one attribute is not dependent on an order of bytes in the potentially malicious file. The process can further include identifying a probability that the potentially malicious file is malicious, based at least in part on the at least one attribute and a trained threat model.
Owner:INVINCEA
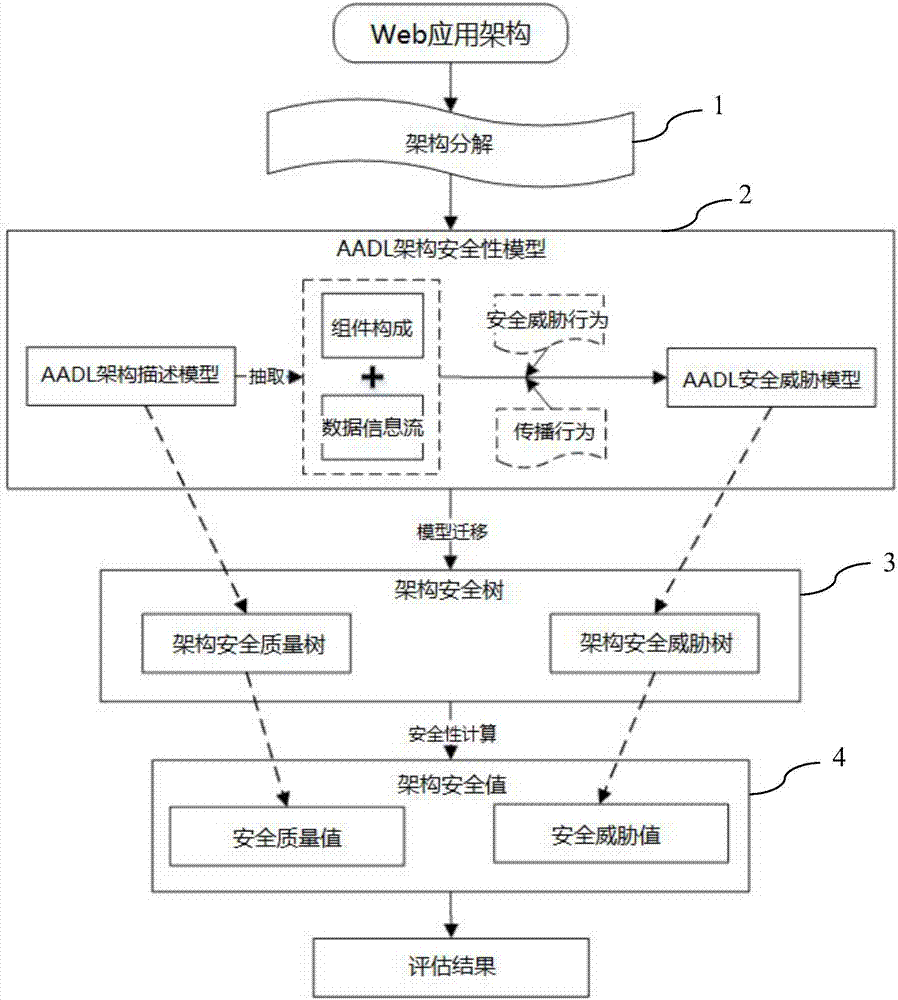
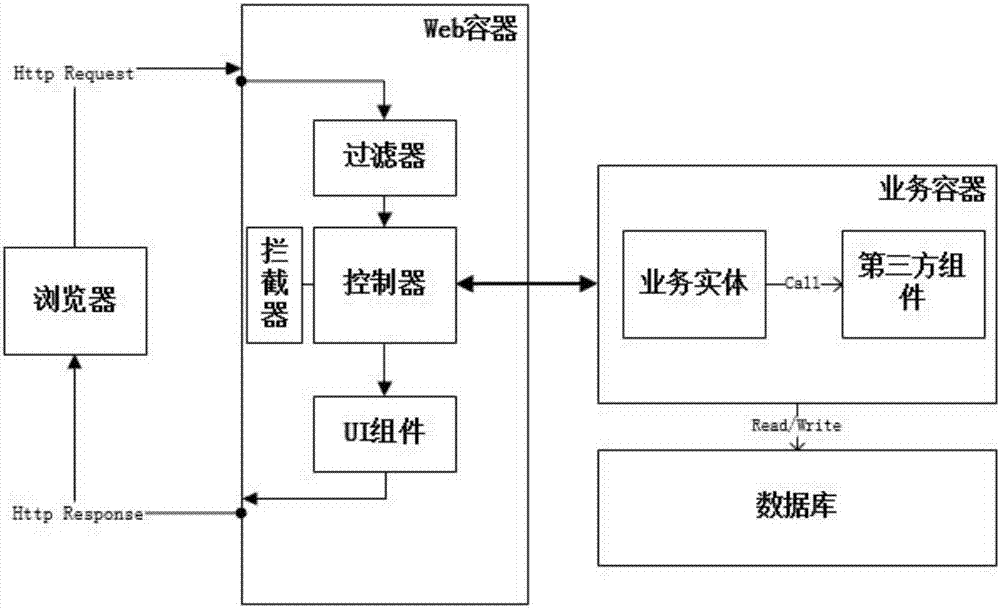
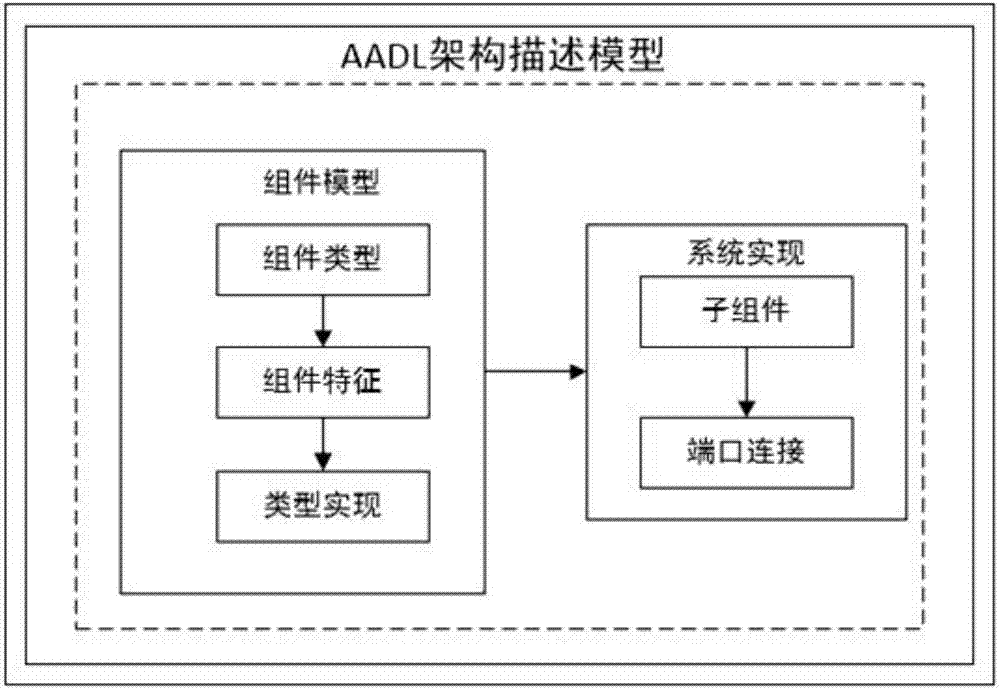
Evaluation method for Web application architecture security based on AADL
ActiveCN107103244AMeasurable Security Assessment ElementsReduce dependencyPlatform integrity maintainanceWeb applicationDesign stage
The invention discloses an evaluation method for the Web application architecture security based on AADL. The evaluation method includes the steps that (1) a Web application architecture is decomposed; (2) an AADL architecture security model is established, wherein an AADL architecture description model and an AADL architecture security threat model are established; (3) an architecture security tree model is generated, and comprises an architecture security quality tree and an architecture security threat tree; (4) an architecture security value and an architecture security threat value are calculated. According to the evaluation method for the Web application architecture security based on AADL, the security of the architecture can be actively evaluated in the design stage of the Web application architecture to assist architecture designers in discovering the security problems existing in the Web application architecture as early as possible, the security quality of the architecture is improved, and therefore the Web application security is improved.
Owner:TIANJIN UNIV
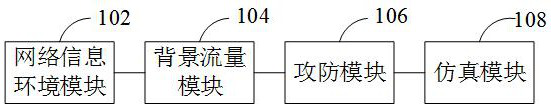
Multi-view network attack and defense simulation system
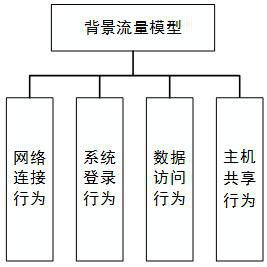
The invention relates to a multi-view network attack and defense simulation system. The system comprises: a network information environment module used for configuring hardware information and software information and establishing a network information system model through the hardware information and the software information; a background flow module which is used for simulating behavior information of a user in the network environment to obtain a background flow model; an attack and defense module which is used for establishing a network threat model according to the network threat behaviorand establishing a network defense model according to the network defense behavior; a simulation module which is used for constructing a network attack and defense adaptive model according to the network information system model, the background flow model, the network threat model and the network defense model, acquiring preset network attack and defense simulation data, inputting the network attack and defense simulation data into the network attack and defense adaptive model, and outputting network attack and defense element data. By adopting the method, network attack and defense deductioncan be easily realized.
Owner:NAT UNIV OF DEFENSE TECH
Internal threat model establishing method based on layered mapping
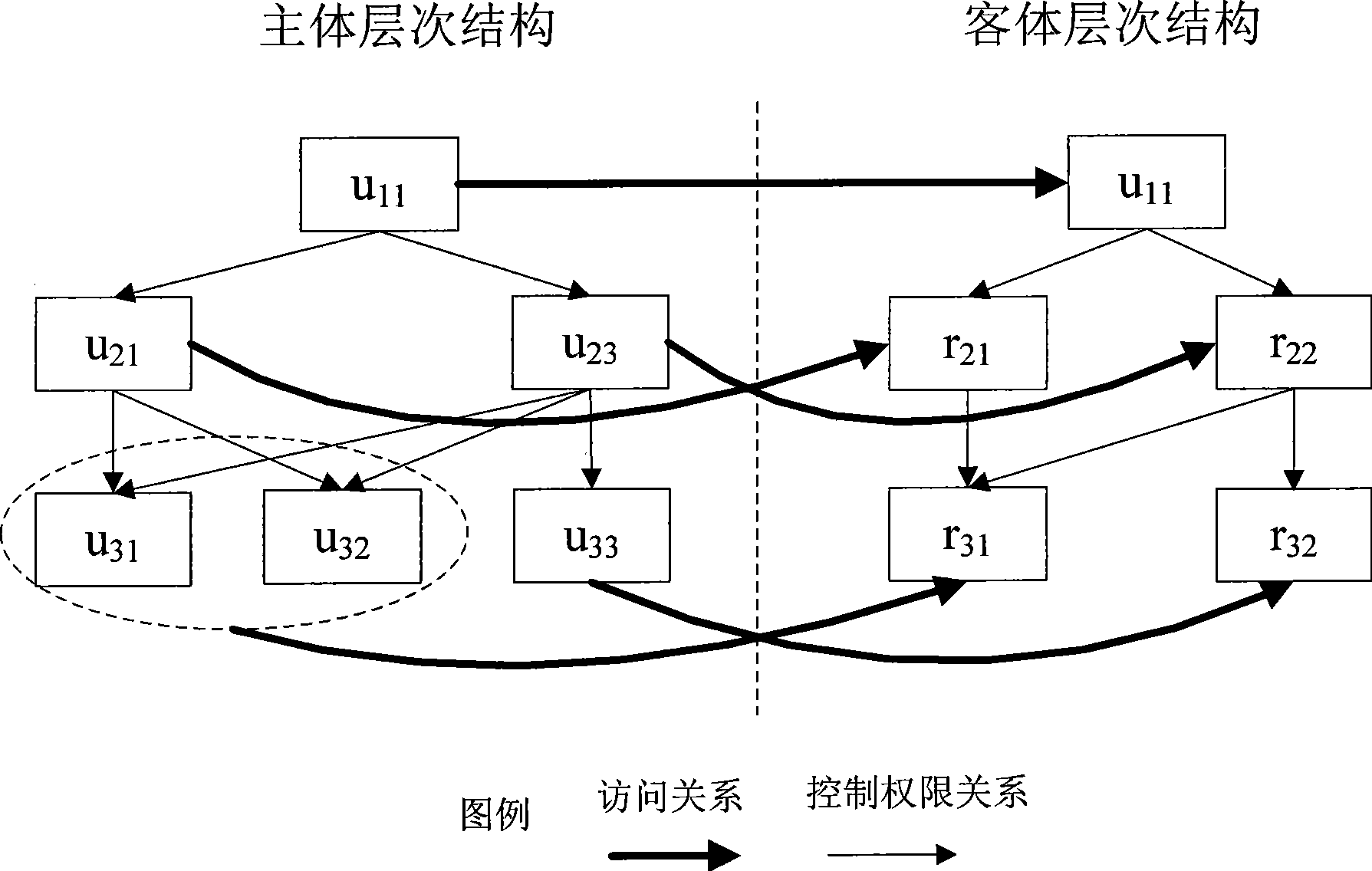
InactiveCN101505216ASensitive detection of insider threatsImprove accuracySecuring communicationHierarchical database modelSystem safety
The invention provides a method for establishing an internal threat model based on layered mapping. The method comprises the following steps: establishing a partial ordering relation by using resource access control authority of a user defined by an access control relation of a system on resources, and establishing hierarchical models of a subject and an object according to the partial ordering relation; establishing mapping between the subject hierarchical model and the object hierarchical model according to the access control relation between the subject and the object so as to form a hierarchical quantized model which overall describes internal threat characteristics of the system from the subject aspect and the object aspect; quantizing the internal threat characteristics related to the subject and the object by using an analytic hierarchy process, and interrelating the internal threat characteristics of the subject and the internal threat characteristics of the object according to the mapping relation between the subject model and the object model to realize fusion of the internal threat characteristics of the subject and the object. The fusion realizes simultaneously monitoring of the internal threat characteristics of the subject and the object, so that a system security administrator can comprehensively observe a variation regulation of the threat inside the system from real-time evaluation and detection data of the system internal threat, and discover the internal threat in time.
Owner:XIDIAN UNIV +1
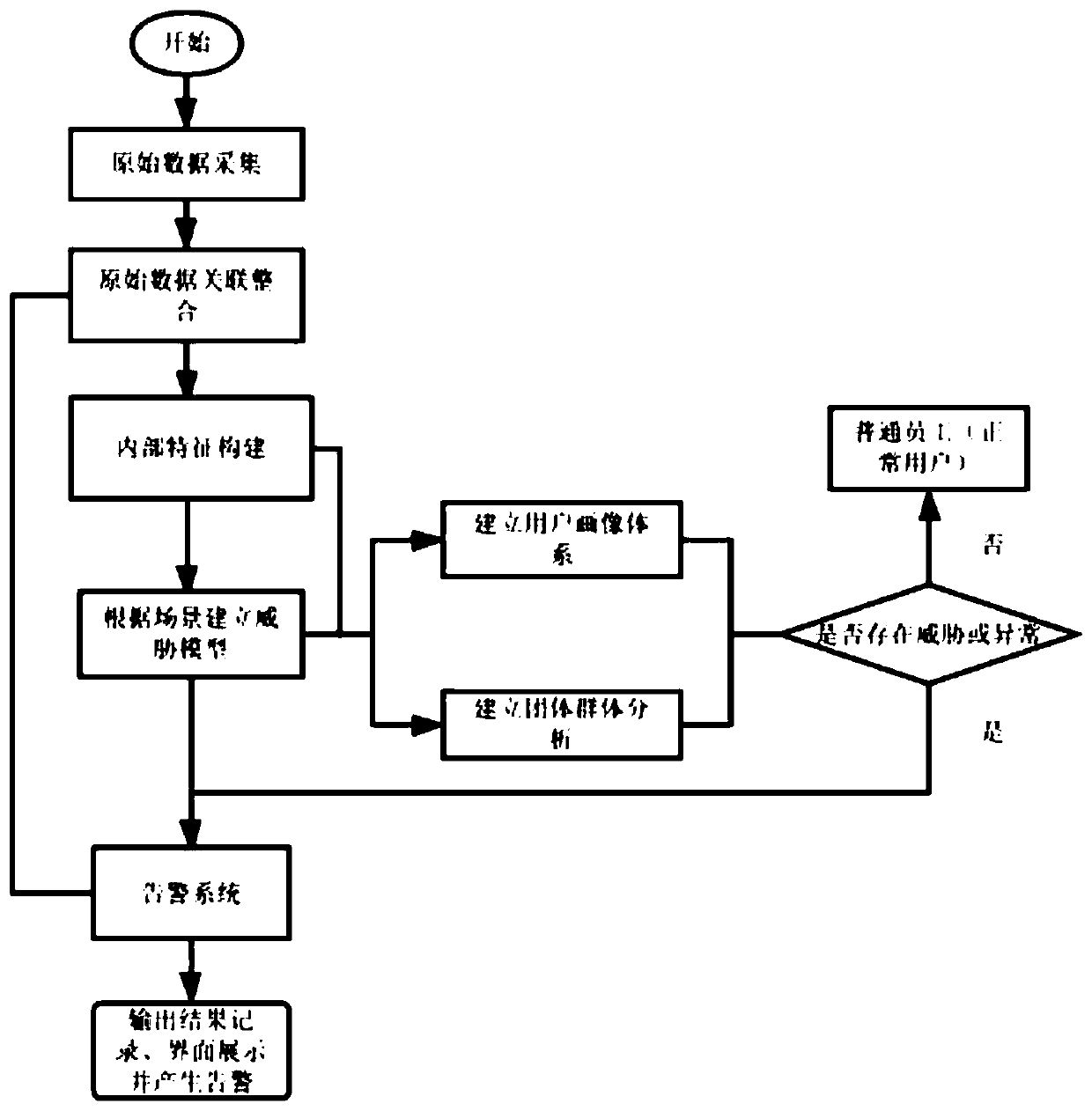
Employee demission tendency detection method
InactiveCN110880075AImprove work efficiencyCharacter and pattern recognitionOffice automationOriginal dataHuman resource management
The invention discloses an employee demission tendency detection method, and aims at solving the problems existing in existing demission tendency judgment. The method comprises the following specificsteps: step 1, collecting original data of employees; step 2, integrating the original data, constructing internal features by adopting a UEBA method (a user and entity behavior analysis method), andestablishing a threat model; and step 3, establishing a user portrait system and a group analysis system according to the threat model and the original data to judge whether a threat exists or not, ifthe judgment result is that the threat or abnormity exists, outputting warning information to human resource management, and if the judgment result is that no threat or abnormity exists, stopping working. According to the invention, an internal employee behavior analysis method is established by using various intranet data such as OA system data, and the change of the work emotion and attitude ofthe employee is discovered in time, so that the departure tendency of the employee is analyzed and judged, the loss of talents and assets can be stopped in time, and the application prospect is wide.
Owner:SHANGHAI GUAN AN INFORMATION TECH
Dynamic route planning method of unmanned aerial vehicle
InactiveCN109445463AAvoid dynamic threats in timePosition/course control in three dimensionsTerrainCost estimation models
The invention relates to a dynamic route planning method of an unmanned aerial vehicle, which adopts the following steps: 1) establishing a route cost estimation model: a communication signal threat model and a terrain surface threat model are constructed, and the communication signal threat model and the terrain surface threat model are weighted and superimposed to form a comprehensive threat model, and on the basis of the comprehensive threat model the planning route evaluation is achieved; 2) computing a flight route: a comprehensive coordinate set random flight path set is constructed, thedynamic renewal of the flight path set according to the threat change situation is achieved, and a track point set in the planned flight path is optimized to select the most safe flight path for eachaircraft. The dynamic route planning method of an unmanned aerial vehicle takes into account flight route selection problems such as flight safety, flight range and aircraft performance. The resultsshow that the real-time planning and route optimization of global optimal flight path in complex environment can avoid all kinds of dynamic threats in time and improve flight safety and reliability.
Owner:SHANDONG UNIV OF TECH
System for generation and reuse of resource-centric threat modeling templates and identifying controls for securing technology resources
ActiveUS20170331835A1Reduce exposureDigital data protectionTransmissionResources of a ResourceComputer program
Systems, computer program products, and methods are described herein for creating reusable resource-centric threat models and identifying controls for securing resources within a network. The present invention is configured to determine that an internal resource in a network requires protection from unauthorized external access; electronically receive information associated with the internal resource within the network; determine one or more threat vectors associated with the internal resource; electronically retrieve from a controls library, a control template associated with a resource category matching the resource category of the internal resource; and apply the control template to the internal resource.
Owner:BANK OF AMERICA CORP
Securing files under the semi-trusted user threat model using per-file key encryption
ActiveUS10298555B2Key distribution for secure communicationEncryption apparatus with shift registers/memoriesFile allocationCiphertext
A computer system and methods for securing files in a file system with storage resources accessible to an authenticable user using an untrusted client device in a semi-trusted client threat model. Each file is secured in the file system in one or more ciphertext blocks along with the file metadata. Each file is assigned a unique file key FK to encrypt the file. A wrapping key WK assigned to the file is used for encrypting the file key FK to produce a wrapped file key WFK. The file is encrypted block by block to produce corresponding ciphertext blocks and corresponding authentication tags. The authentication tags are stored in the file metadata, along with an ID of the wrapping key WK, wrapped file key WFK, last key rotation time, an Access Control List (ACL), etc. The integrity of ciphertext blocks is ensured by authentication tags and the integrity of the metadata is ensured by a message authentication code (MAC).
Owner:ZETTASET
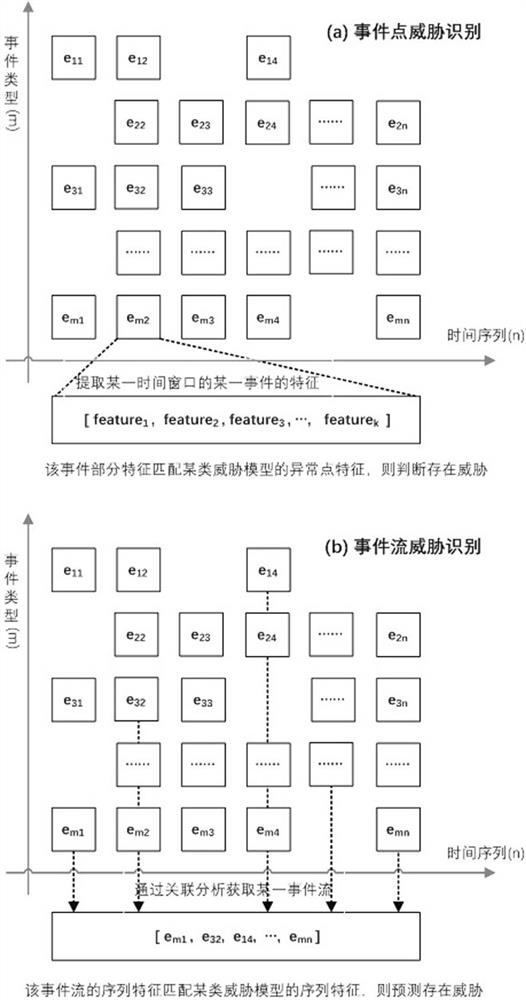
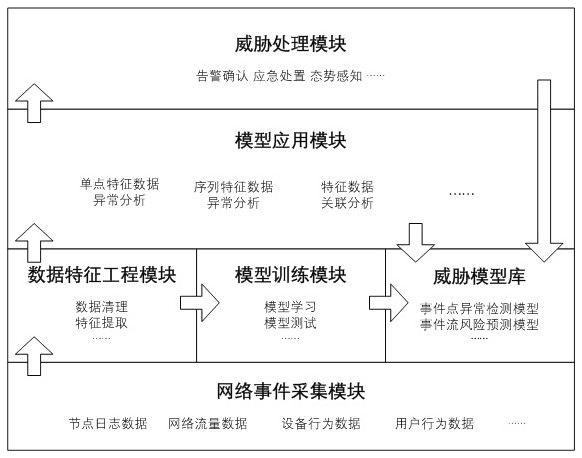
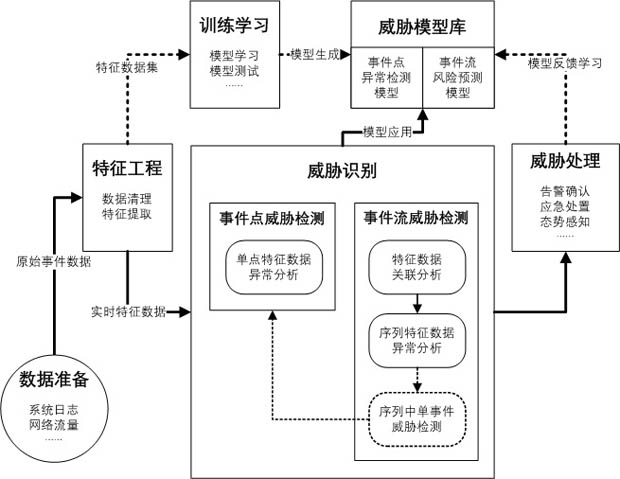
Network security threat identification method based on event detection mode
PendingCN114039758ARealize intelligent analysisAchieve forecastSecuring communicationAttackEngineering
The invention relates to a network security threat identification method based on an event detection mode. According to the method, feature engineering processing is performed on event big data of each node of a network, model learning training is performed on the data after feature engineering processing according to two modes of event points and event streams, and two types of model knowledge of an event point anomaly detection model and an event stream risk prediction model are generated. On the basis of model knowledge, for threat identification of a single-point event, a matching value of an event feature and a certain threat model abnormal point feature is calculated to judge whether a potential threat exists or not; for threat identification of a plurality of associated events similar to multi-step attacks, firstly, a feature sequence of the associated events is obtained by using an association analysis algorithm, and then a matching value of a sequence feature of an event stream and a sequence feature of a certain threat model is calculated to predict whether potential threats exist or not. According to the method, instant threat identification and hidden threat mining can be realized, and the level of network security operation and maintenance is greatly improved.
Owner:CHINA YOUKE COMM TECH
Ionospheric slant total electron content analysis using global positioning system based estimation
ActiveUS9576082B2Design optimisation/simulationSatellite radio beaconingTotal electron contentIonospheric heater
A method, system, apparatus, and computer program product provide the ability to analyze ionospheric slant total electron content (TEC) using global navigation satellite systems (GNSS)-based estimation. Slant TEC is estimated for a given set of raypath geometries by fitting historical GNSS data to a specified delay model. The accuracy of the specified delay model is estimated by computing delay estimate residuals and plotting a behavior of the delay estimate residuals. An ionospheric threat model is computed based on the specified delay model. Ionospheric grid delays (IGDs) and grid ionospheric vertical errors (GIVEs) are computed based on the ionospheric threat model.
Owner:CALIFORNIA INST OF TECH
Method of securing files under the semi-trusted user threat model using symmetric keys and per-block key encryption
ActiveUS9363247B2Key distribution for secure communicationDigital data information retrievalFile systemTrusted client
A computer system and method for securing files in a file system equipped with storage resources that are accessible to an authenticable user operating with an untrusted client device under the semi-trusted client threat model. The file to be secured is stored in one or more blocks belonging to the storage resources along with symmetric per-block key(s) KBi assigned to each of the blocks in the file. The blocks are encrypted with the symmetric per-block keys to obtain encrypted blocks. The user is assigned user key(s) and each per-block key that was used for encryption is in turn encrypted with one of the user's keys to derive wrapped key(s) for each encrypted block. Wrapped key(s) are placed in encrypted block headers and introduce a level of indirection to encrypted file(s) that is appropriate for the semi-trusted client threat model.
Owner:ZETTASET
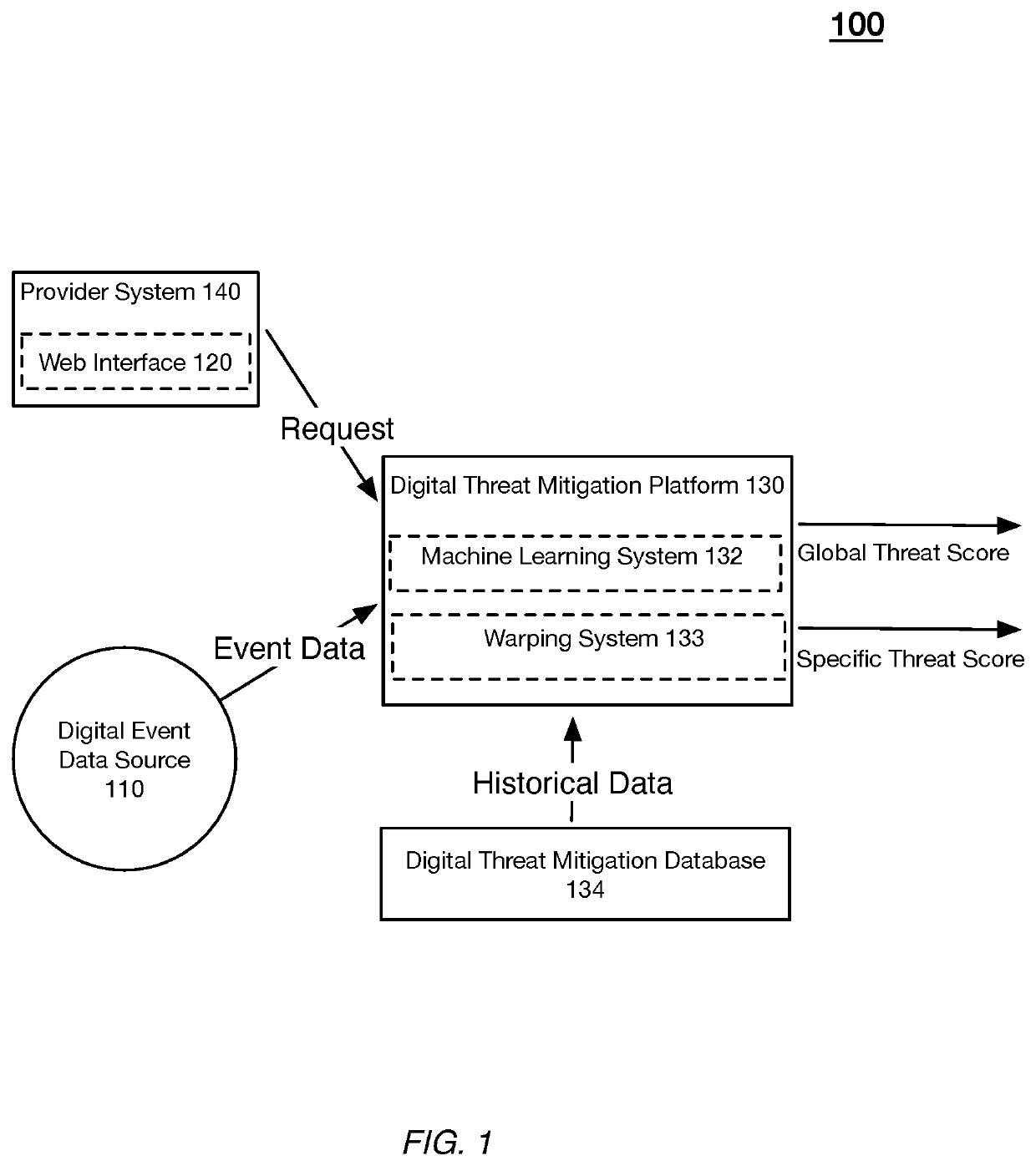
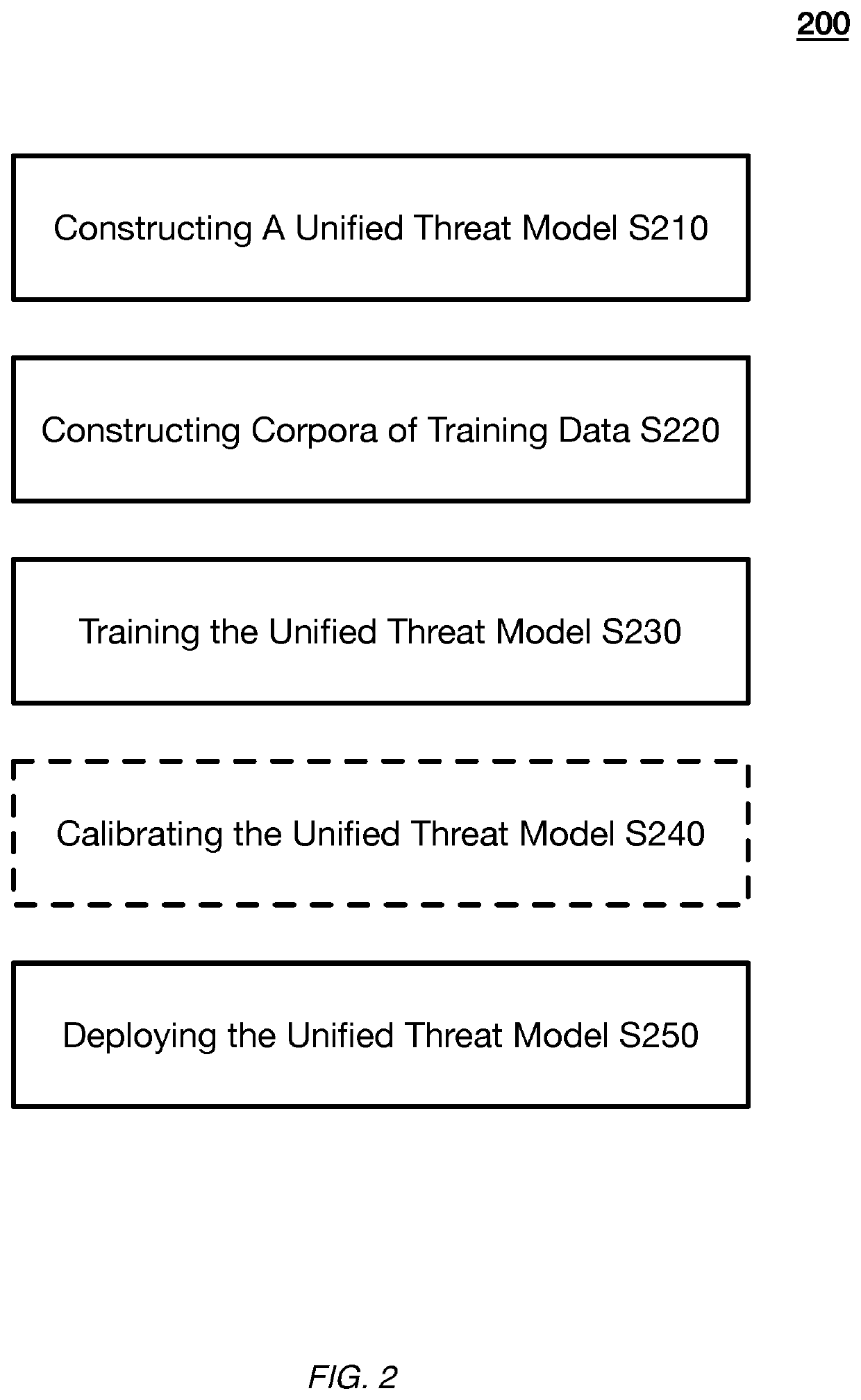
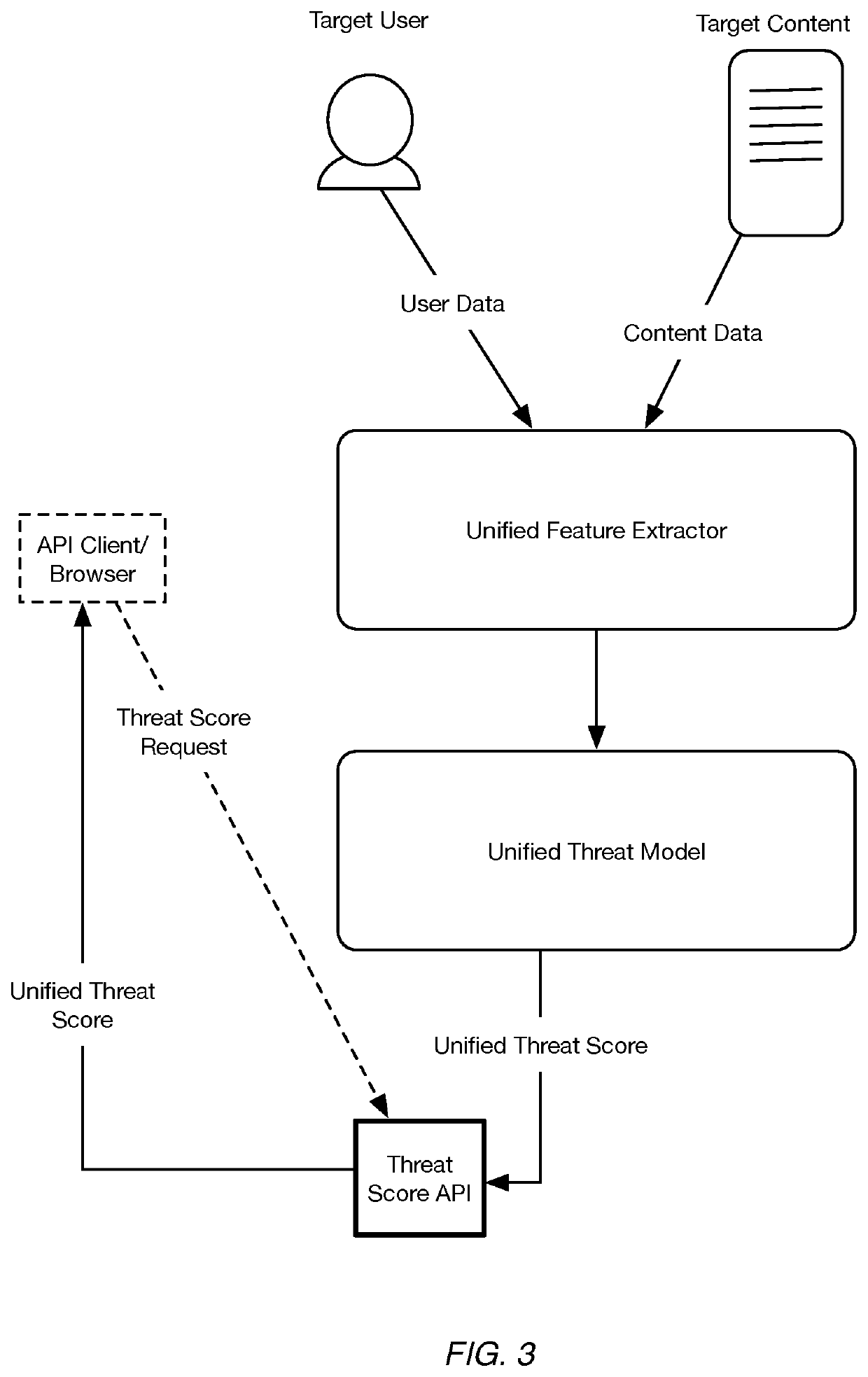
Systems and methods configuring a unified threat machine learning model for joint content and user threat detection
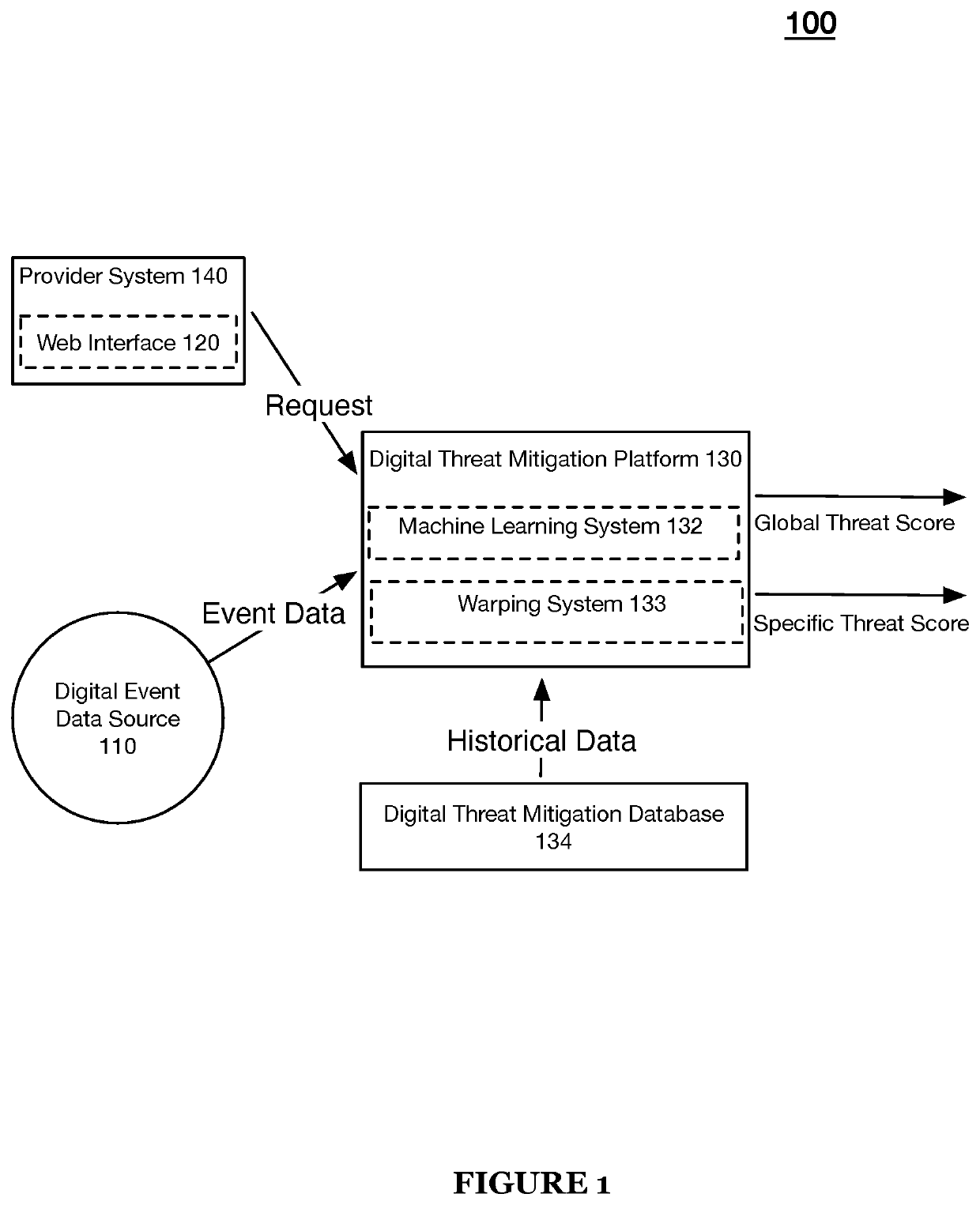
A machine learning-based system and method for identifying digital threats includes a threat service that: implements a unified threat model that produces a unified threat score that predicts both of: a level of threat of a piece of online content, and a level of threat that a target user will create a harmful piece of online content; wherein: implementing the unified threat model includes: receiving event data comprising historical content data for the target user and content data of the pending piece of online content and historical user digital activity data and real-time user activity data; and providing input of content feature data and user digital activity feature data to the unified threat model; and the unified threat model produces the unified threat score based on the content and the user digital activity data; and computes a threat mitigation action based on an evaluation of the threat score.
Owner:SIFT SCI INC
Method and system for detecting malicious file
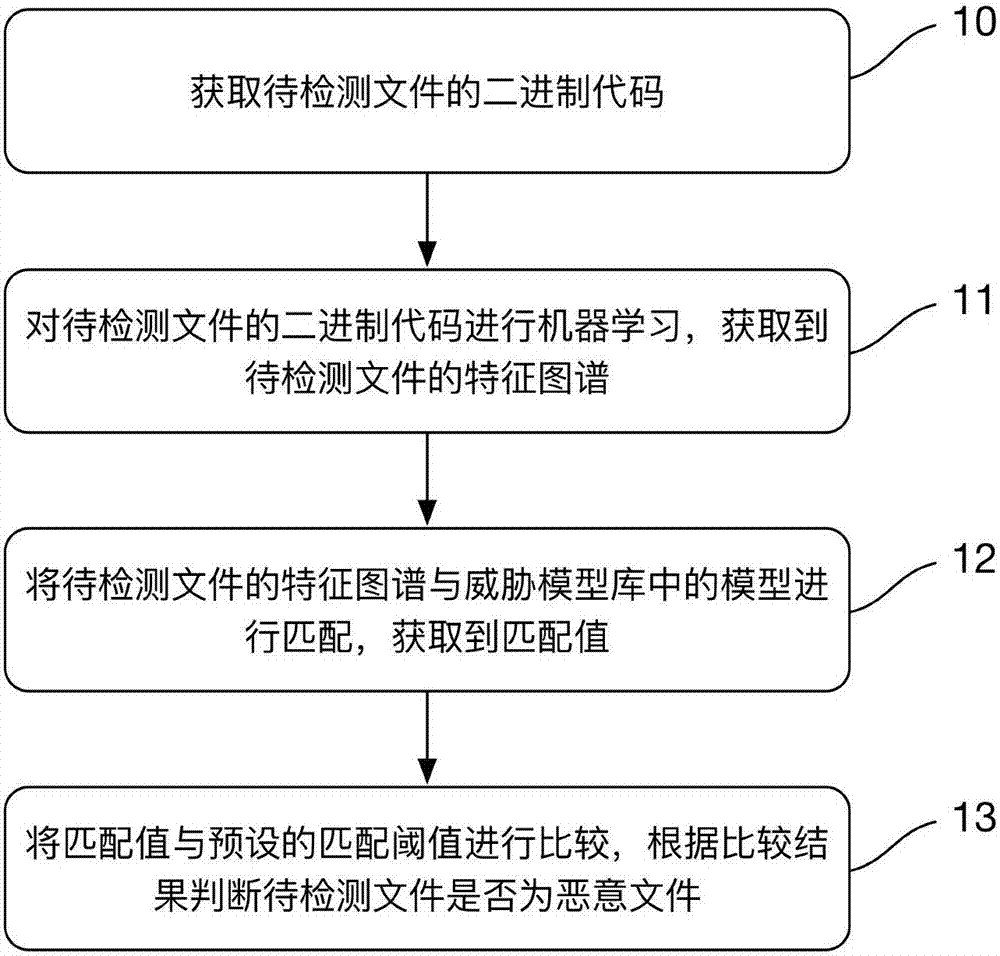
InactiveCN106897621AAvoid remedyAvoid clearingPlatform integrity maintainanceBehavioral analyticsTime-Consuming
The invention discloses a method and system for detecting a malicious file. The method comprises the steps that a binary code of a to-be-detected file is obtained; the binary code of the to-be-detected file is subjected to machine learning, and a specific chromatogram of the to-be-detected file is obtained; the specific chromatogram of the to-be-detected file is matched with a model in a threat model base, and a matching value is obtained; the matching value is compared with a preset matching threshold, and whether the to-be-detected file is the malicious file or not is judged according to the comparison result. According to the method and system for detecting the malicious file, manual inspection replacement is not needed, behavioral analysis is not needed, and it is not required that a feature code is created manually; most threat infection can be stopped before intruding into a user and a system, so that time-consuming and labor-consuming remediation and removal are avoided.
Owner:NUBIA TECHNOLOGY CO LTD
Systems and methods for configuring and implementing a card testing machine learning model in a machine learning-based digital threat mitigation platform
Owner:SIFT SCI INC
Intelligent vehicle threat estimation system and method based on variable-structure Bayesian network
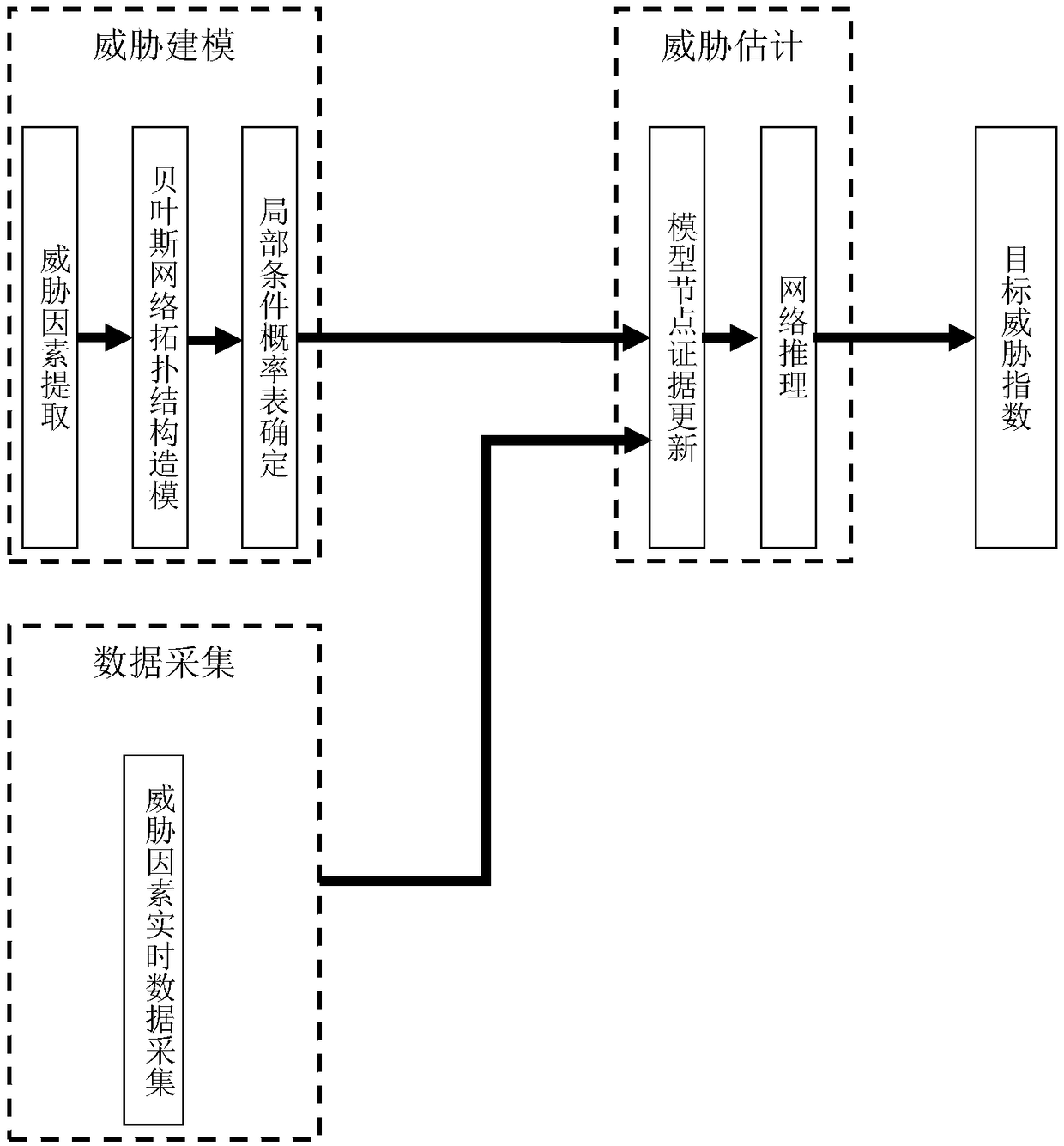
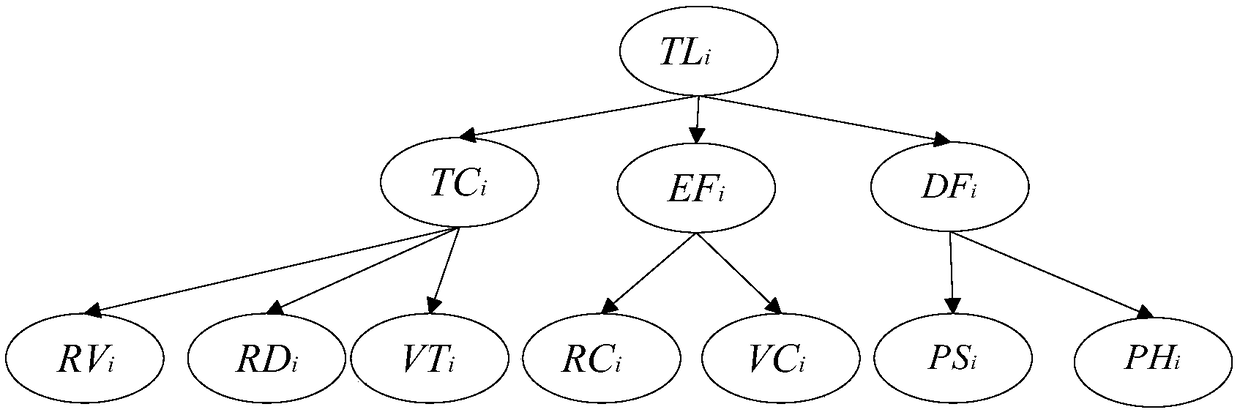
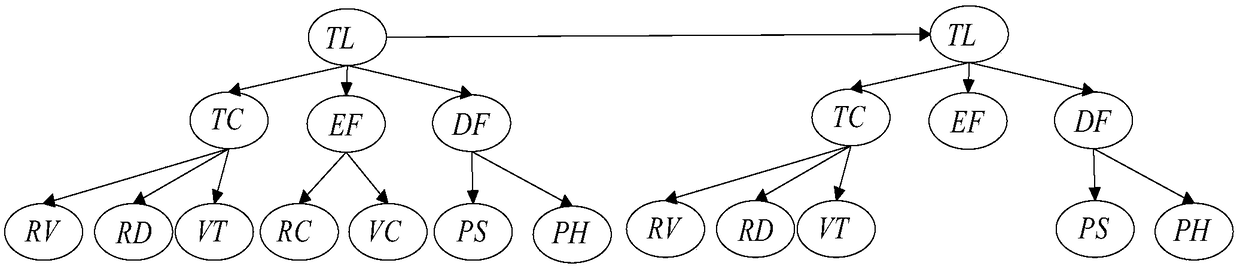
PendingCN109063940AFully awareEffective cognitionCharacter and pattern recognitionResourcesNODALData acquisition
The invention, which relates to the field of the intelligent vehicle cognitive technology, claims for protection of an intelligent vehicle threat estimation system and method based on a variable-structure Bayesian network thereby evaluating a threat degree of a moving target to a vehicle. The system is composed of a threat modeling module, a data collection module and a threat estimation module. At a threat modeling stage, factors affecting intelligent vehicle threat estimation are determined, wherein the factors include an external environmental factor, a target characteristic factor and a driver factor; a topology of a Bayesian network model is constructed; and then a local condition probability table of the model is determined. During the driving process, the data acquisition module uses sensors to collect real-time data of various influence factors; the threat estimation module reconstructs corresponding variable nodes only for quickly changing factors according to changing rates of all factors to obtain a variable-structure Bayesian network model and then carries out reasoning calculation to obtain a target threat index. Therefore, the performance of intelligent vehicle threatestimation can be improved effectively.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
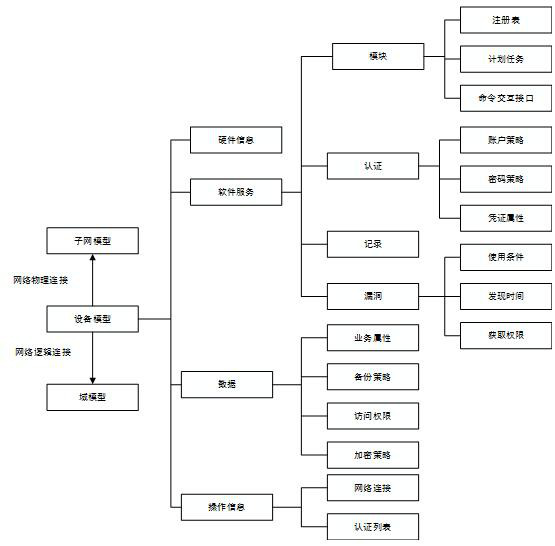
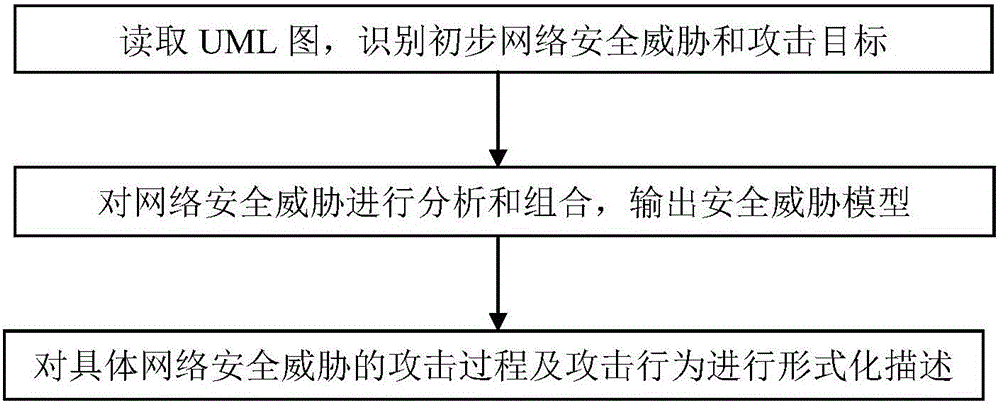
Network security threat evaluation method and system for substation monitoring system
The invention provides a network security threat evaluation method for a substation monitoring system. The method comprises the steps of firstly, reading a UML graph which describes a monitoring system application scene, and identifying primary network security threats and attack objects of the substation monitoring system; then analyzing and combining the network security threats, outputting a monitoring system security threat model, and refining the model into an attack tree; and finally, carrying out formalized description on the attack processes and attack behaviors of the specific network security threats, and outputting the attack processes and attack behaviors in an Object-Z format. Correspondingly, the invention also provides a matched network security threat evaluation system for the substation monitoring system. According to the method provided by the invention, the network security threats of the monitoring system can be described qualitatively, and the network security threats are visual and clear; and the threat attack behaviors are described by use of a formalized mathematical language, and therefore, corresponding defensive measures can be provided.
Owner:NR ELECTRIC CO LTD +1
Machine learning-based change control systems
PendingUS20210201270A1Improve reliabilityImprove securityEnsemble learningCharacter and pattern recognitionLearning basedControl system
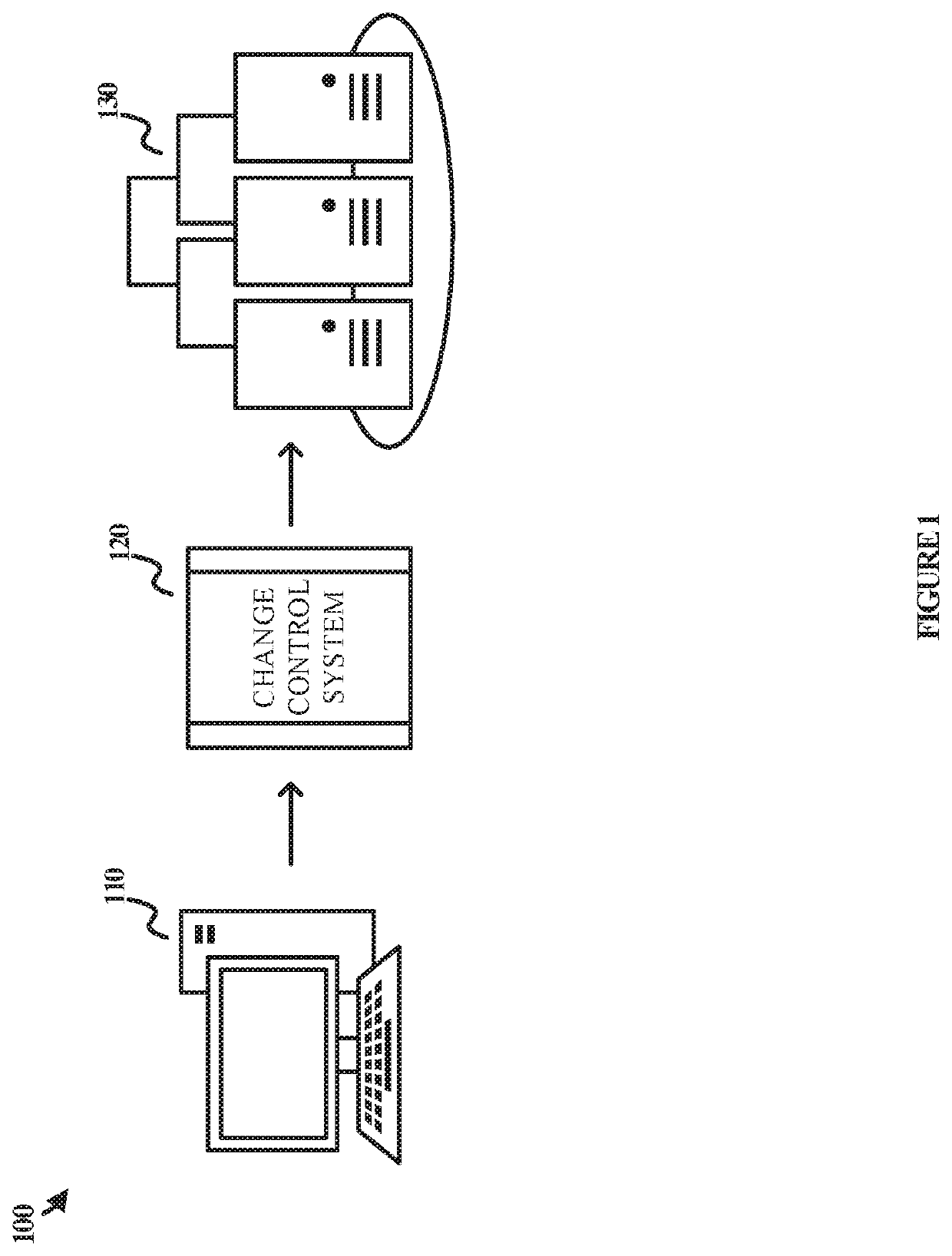
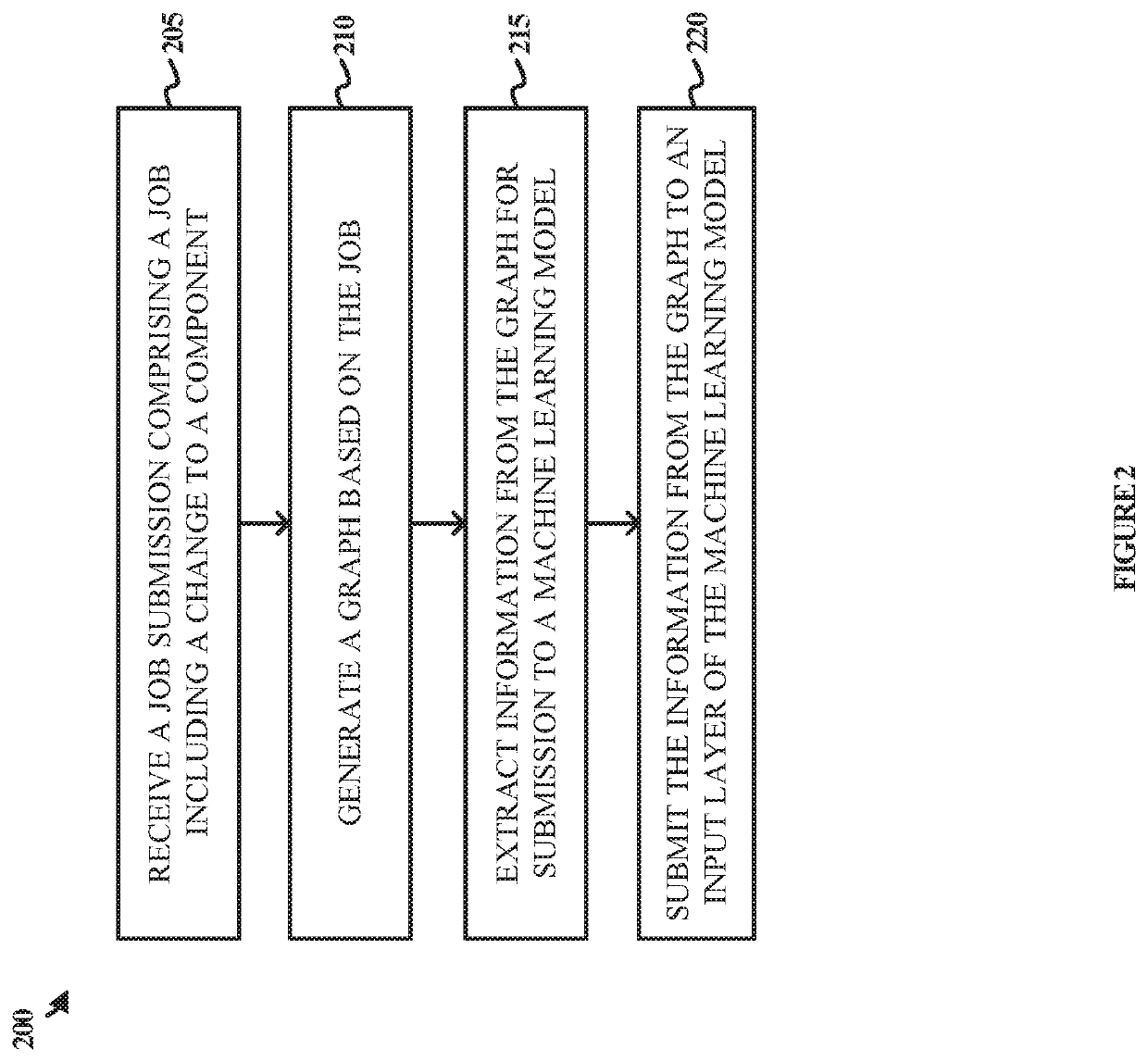
Various embodiments of the present technology generally relate to systems, tools, and processes for change control systems. More specifically, some embodiments relate to machine learning-based systems, methods, and computer-readable storage media for job approvals, logging, and validation of critical functions and tasks based on compliance requirements, threat models, intended outcomes, rules, regulations, and similar restrictions or combinations thereof. Job approvals, rejections, and deferrals may be combined with machine learning techniques to conduct behavioral analysis in some implementations. The system disclosed herein provides for an improvement over existing change control methods requiring manual and time-consuming analysis. The system utilizes a combination of security, compliance, and auditing requirements along with machine-learning based behavior analysis of development, security, and operations functions and actions to determine risk, rejection, approval, or deferral of submissions in an automated manner.
Owner:ORACLE INT CORP
IT computer network threat analysis, detection and containment
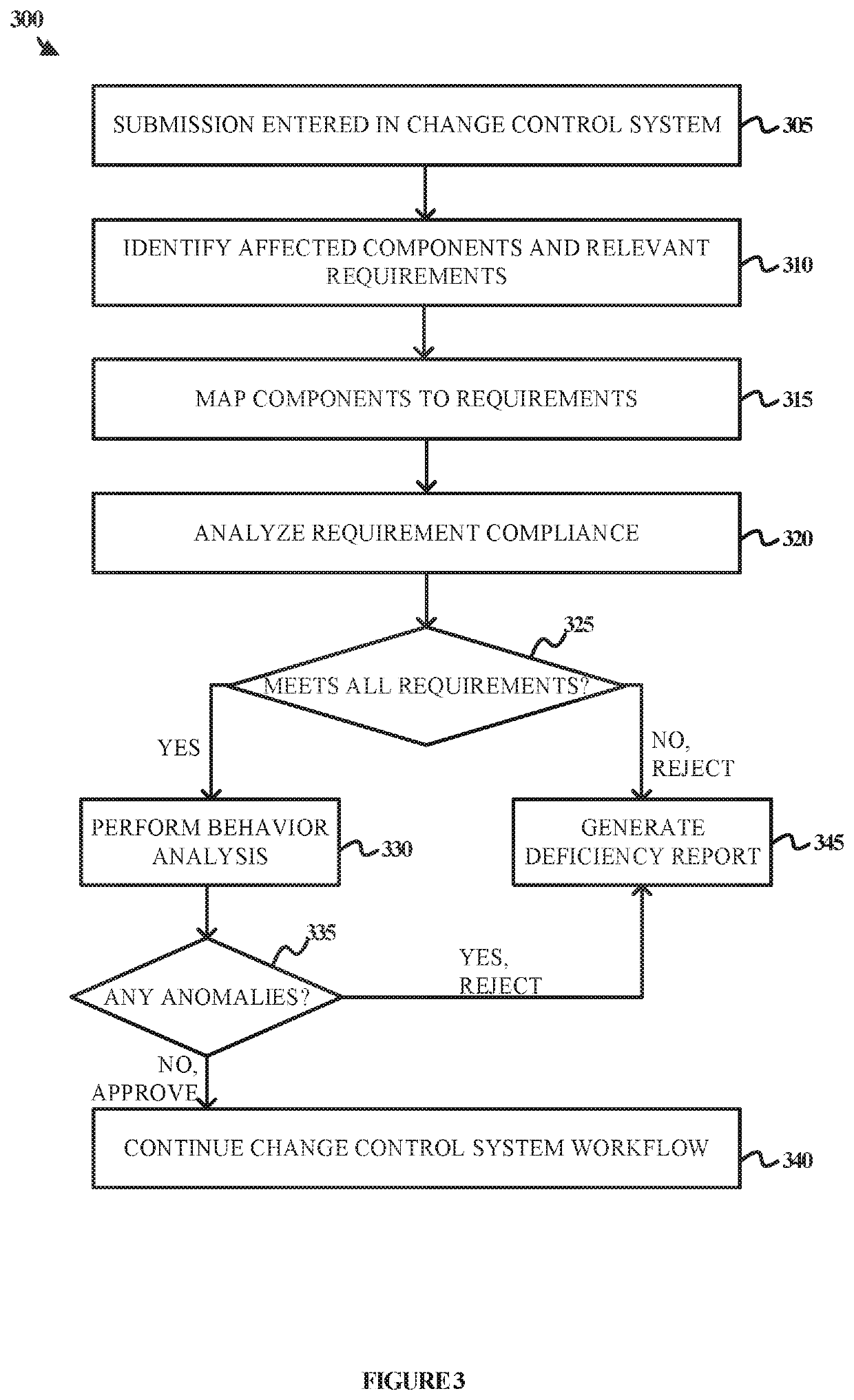
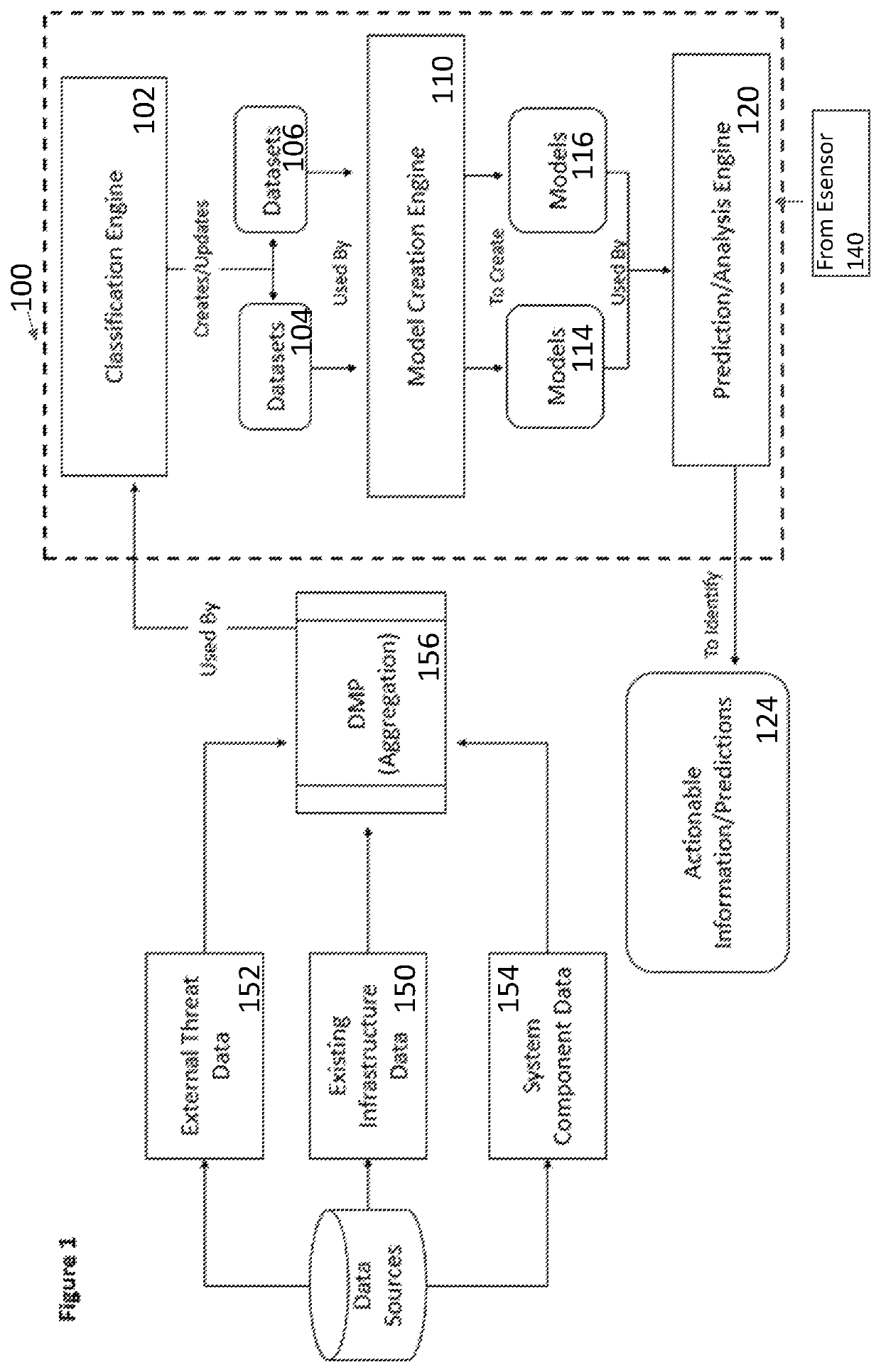
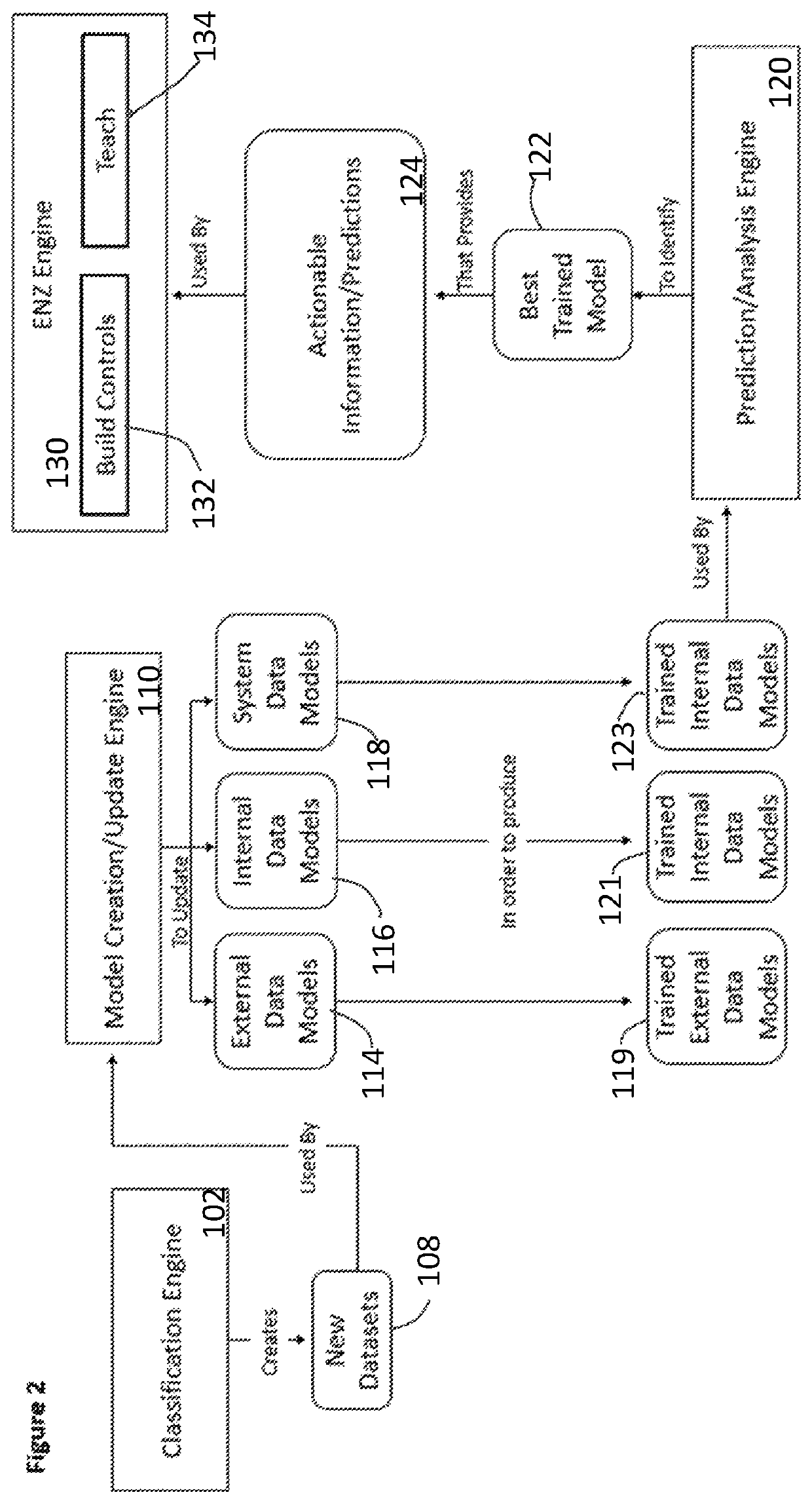
ActiveUS10897472B1Better networkMemory loss protectionError detection/correctionData setData aggregator
A software threat analysis, detection and containment system includes a data aggregation model that receives and aggregates data from a plurality of sources in a computer network, a classification engine that classifies the aggregated data, and a plurality of data sets into which the classified data is stored. A model creation engine creates threat models based on the content of each data set and a prediction and analysis engine generates actionable information and predictions based on the content of each threat model.
Owner:ENIGMA NETWORKZ LLC
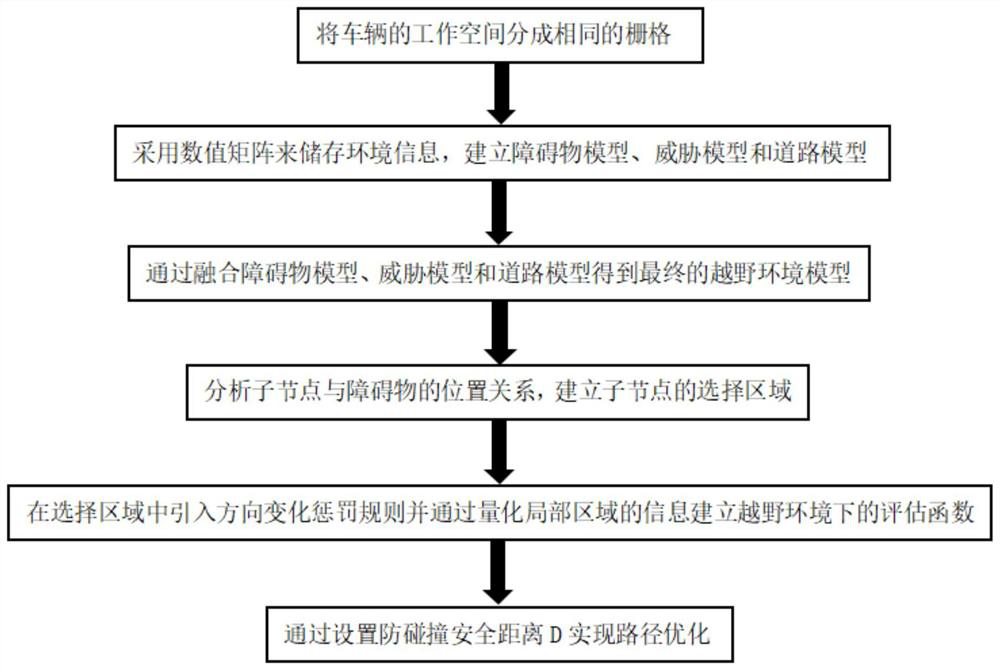
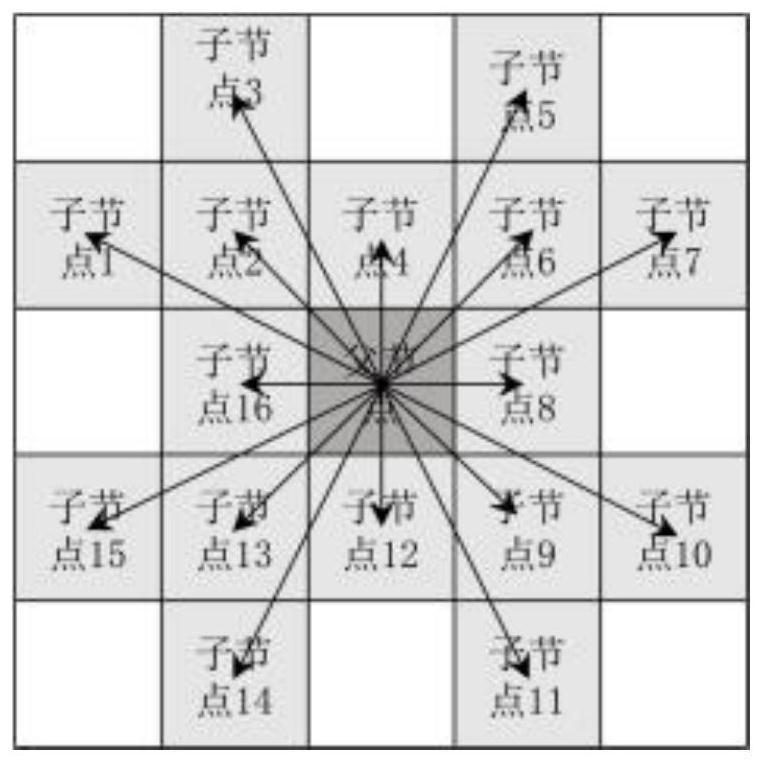
Path planning method based on improved A* algorithm in off-road environment
ActiveCN114706400ARealize a realistic simulationControl smoothnessInternal combustion piston enginesNavigational calculation instrumentsSimulationOperations research
The invention discloses a path planning method based on an improved A * algorithm in an off-road environment, which belongs to the technical field of path planning, and comprises the following steps: dividing a working space of a vehicle into identical grids, and storing environment information by adopting a numerical matrix, an obstacle model, a threat model and a road model are established and fused to obtain a final cross-country environment model, the position relation between child nodes and obstacles is analyzed, and a selection area of the child nodes is established; a direction change penalty rule is introduced into the selected area, and an evaluation function in the off-road environment is established by quantifying information of a local area; and path optimization is realized by setting an anti-collision safety distance D. According to the method provided by the invention, a safe, feasible and efficient driving path can be quickly and effectively planned under the cross-country environment condition under the joint coupling action of obstacles, environmental threats and road conditions, the inflection point number of the planned path is reduced by 4 times compared with that of a traditional A * algorithm, and the efficiency is improved by 30%.
Owner:CHONGQING UNIV OF ARTS & SCI
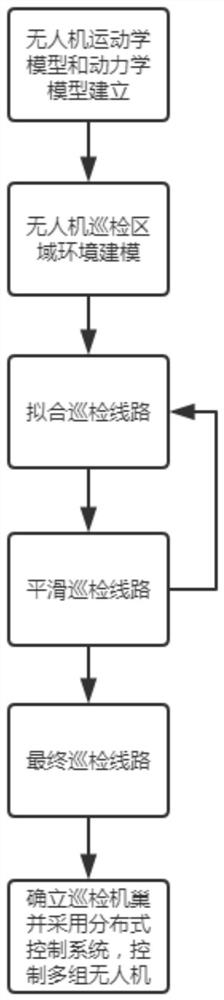
Routing inspection unmanned aerial vehicle nest distribution and information interaction method
ActiveCN111679690AGeometric CADAutonomous decision making processSimulationDistributed control system
The invention discloses a routing inspection unmanned aerial vehicle nest distribution and information interaction method, and belongs to the field of routing inspection unmanned aerial vehicle nest site selection. The routing inspection unmanned aerial vehicle nest distribution and information interaction method comprises the steps of: firstly, analyzing data and related technologies of unmannedaerial vehicles; secondly, substituting the data of the unmanned aerial vehicle into environmental modeling, and establishing an unmanned aerial vehicle maneuvering performance constraint model and threat constraint models, wherein the unmanned aerial vehicle maneuvering performance constraint model comprise a maximum flying range, a maximum climbing angle, a minimum turning radius and a flight speed, and the threat constraint models mainly comprise a terrain threat model, a weather threat model, a man-made threat model and the like; in addition, considering that the unmanned aerial vehicles use terrain to avoid risks, regarding the height as one of track costs; and on the basis of establishing the mechanical constraint model and the threat models, carrying out two-dimensional and three-dimensional static flight path planning of the unmanned aerial vehicle respectively, planning nest positions through covering the whole region by means of flight path planning, and controlling an unmanned aerial vehicle group through using a distributed control system.
Owner:ANHUI JIYUAN SOFTWARE CO LTD
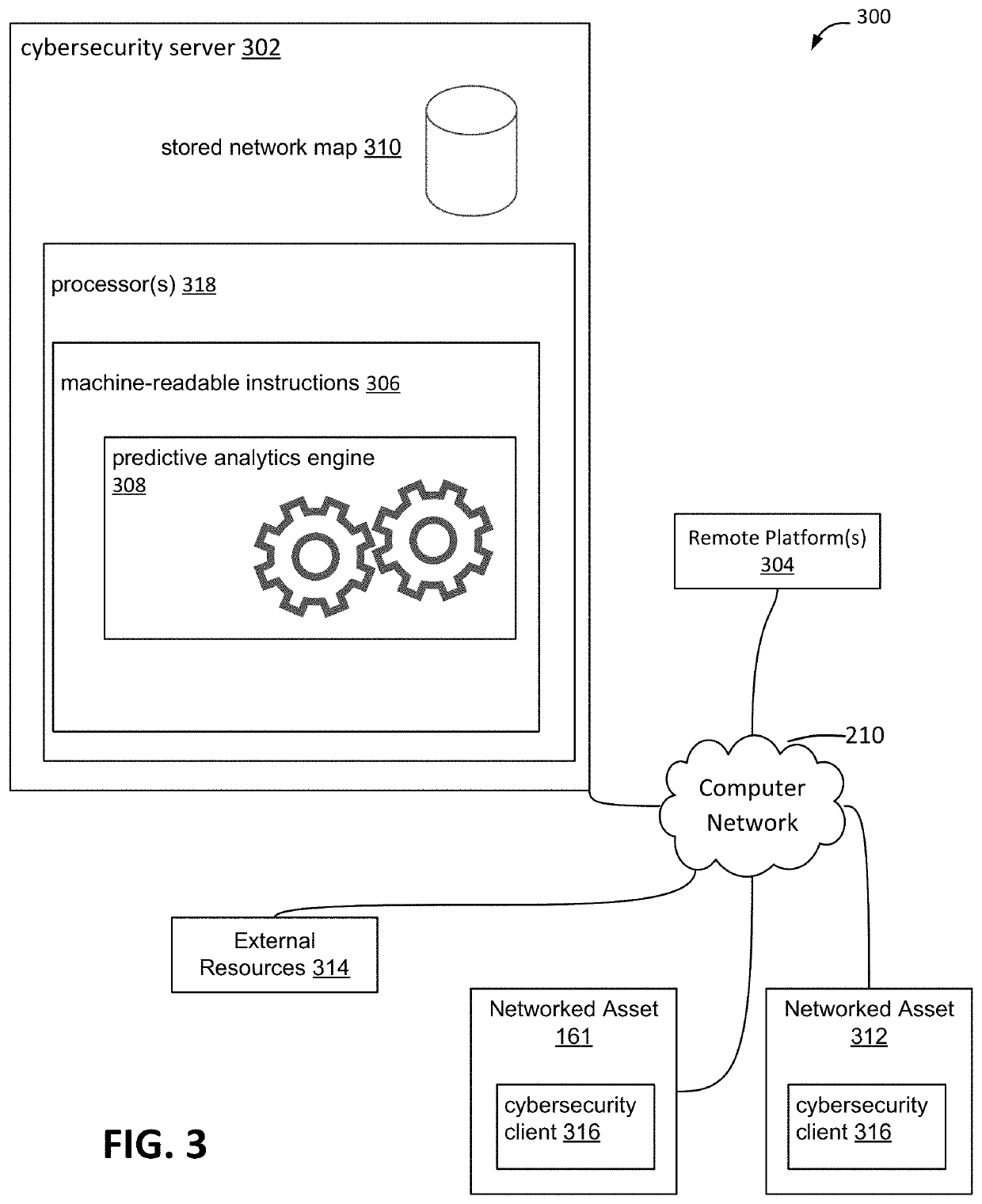
Automated real-time multi-dimensional cybersecurity threat modeling
A plurality of communicatively coupled, networked assets of an organization may be threatened or attacked by a cybersecurity attack or other form of attack. Control mechanisms may be installed and established to protect against specific cybersecurity attacks and other infiltrations. Machine learning and predictive analytics are used to more appropriately match specific attacks and threats against specific control mechanisms, accounting for dimensionality of control mechanisms. The matching of attack patterns and control mechanisms may use test scripts that operate on data pulled from the organization's systems of record. A factor analysis of information risk (FAIR) may be performed and visual threat models may be automatically generated that show the mapping between a threat actor, attack type, control environment including dimensionality, the targeted system, and the impact on the organization.
Owner:BANK OF AMERICA CORP
Enrichment and analysis of cybersecurity threat intelligence and orchestrating application of threat intelligence to selected network security events
Techniques are disclosed which can provide an orchestrated response to a cybersecurity threat. This orchestrated response may be based upon, at least in part, a reputation score. Threat model(s) may be received that identify cybersecurity threat(s). An indication of observations, false positives, and / or page views for the threat may be obtained. Data feeds may be received including known good data feeds, known bad data feeds, and enrichment data feeds. The data feeds may provide information about one or more indicators of compromise (IOC). For each IOC, a weighted criticality score may be determined. The weighted criticality score may be mapped to a corresponding point value. An aggregated score may be determined based upon at least the corresponding point value. A reputation score may be computed, and in some configurations, provided to a user.
Owner:THREATCONNECT INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com