Evaluation method for Web application architecture security based on AADL
A web application and security technology, applied in computer security devices, platform integrity maintenance, instruments, etc., can solve problems such as inaccurate software architecture description accuracy, inability to fully meet security evaluation requirements, and affect the quality of construction models
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0082] The technical solutions of the present invention will be further described in detail below in conjunction with the accompanying drawings and specific embodiments.
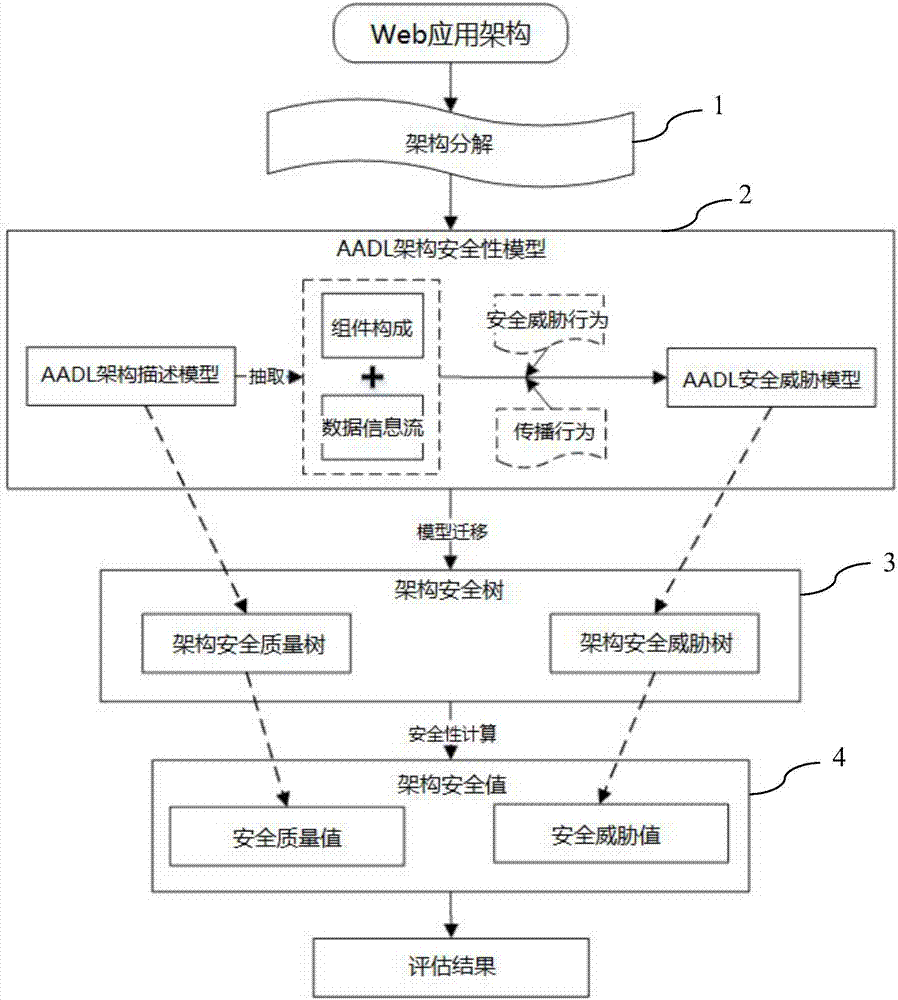
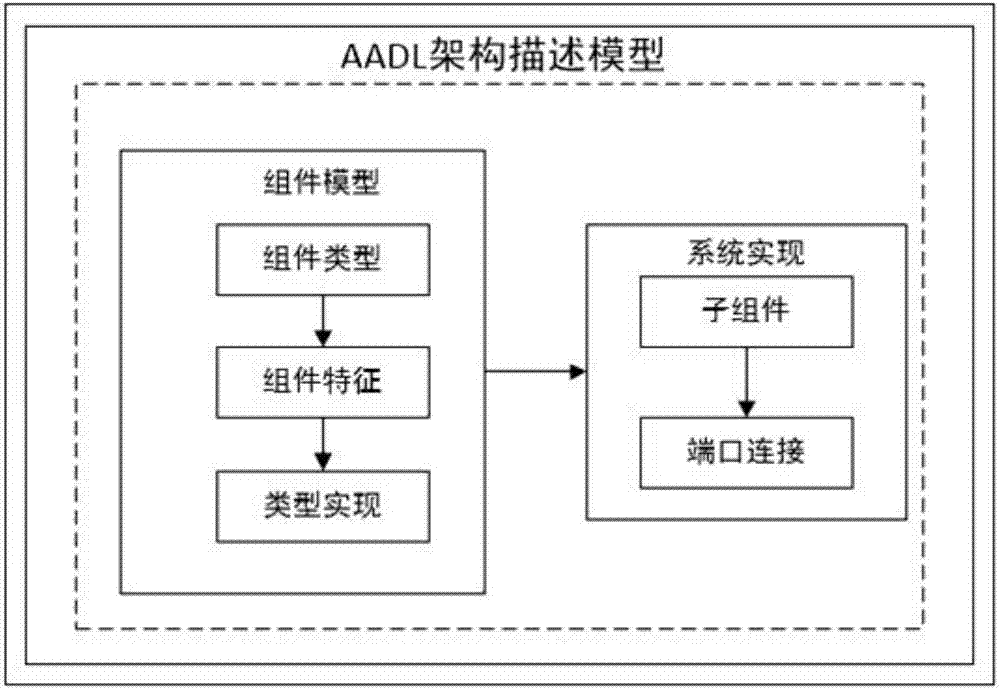
[0083] like figure 1 As shown, it is the overall evaluation process of the AADL-based Web application architecture security evaluation method of the present invention. The method mainly includes four parts. First, it decomposes the Web application architecture; Descriptive analysis is carried out to construct the AADL architecture model; then the architecture security model is generated through the model replacement tool; finally, the architecture security value is calculated according to the security calculation method, and the security evaluation is performed based on the architecture security value. The detailed description of main steps of the present invention is as follows:
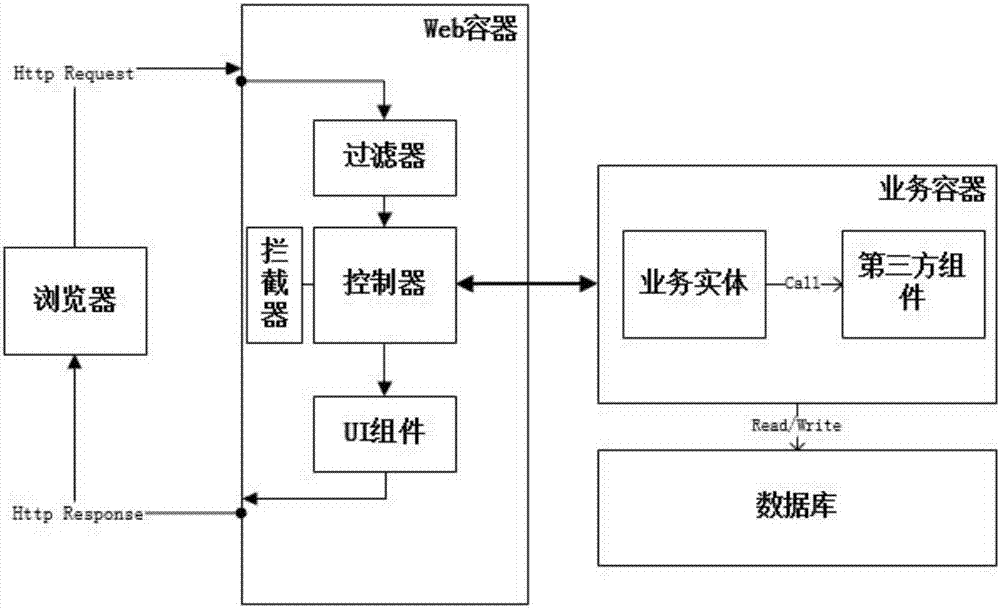
[0084]Step 1. Decomposing the Web application architecture. This step includes two activities: decomposing the Web application ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com