Intrusion detection and analysis system on basis of service data flow of virtual machines
A technology for intrusion detection and virtual services, applied in digital transmission systems, transmission systems, data exchange networks, etc., can solve problems such as insecure configuration and difficult to detect attacks, and achieve the effect of increasing robustness and improving accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0018] In order to make the purpose, technical solution and advantages of the present application clearer, the present application will be further described in detail below in conjunction with the accompanying drawings and specific embodiments.
[0019] In the following description, references to "one embodiment," "an embodiment," "an example," "example," etc. indicate that such described embodiment or example may include a particular feature, structure, characteristic, property, element, or limitations, but not every embodiment or example necessarily includes the specific feature, structure, characteristic, property, element or limitation. Additionally, repeated use of the phrase "according to one embodiment of the present application" does not necessarily refer to the same embodiment, although it may.
[0020] For simplicity, some technical features known to those skilled in the art are omitted from the following description.
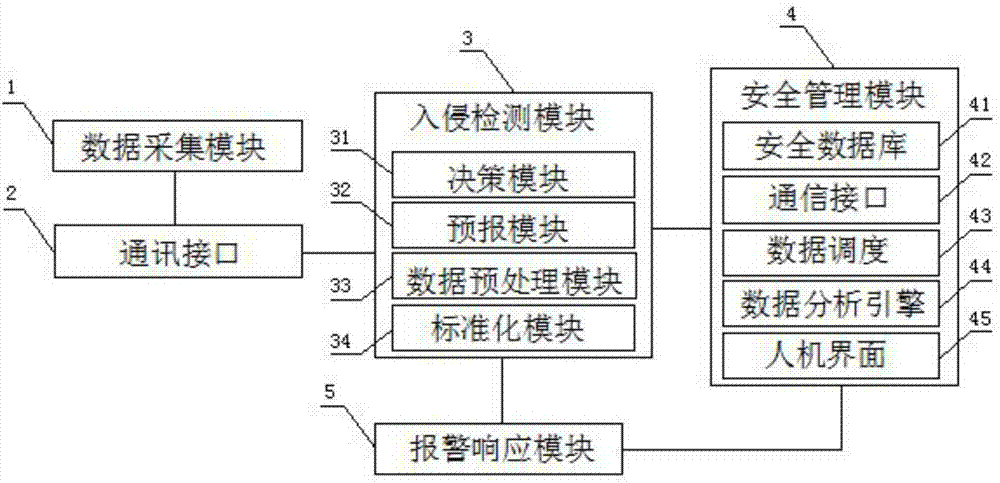
[0021] The intrusion detection and analysis sy...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com