Network security verifying device based on improved K-means algorithm
A technology of k-means algorithm and verification device, which is applied in the Internet field, can solve the problems of large amount of attack data, high false positive rate, and cannot handle massive attack data well, and achieves high detection accuracy and false positives. low rate effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
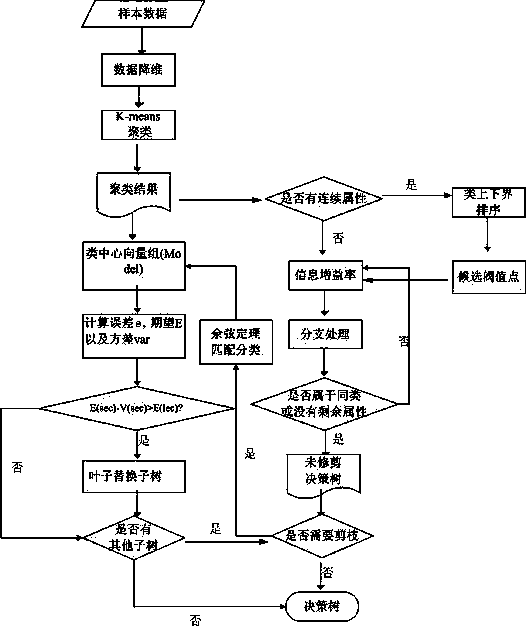
Image
Examples
Embodiment 1
[0116] 1. Implementation of the controllable module
[0117] A firewall separates the Internet, the range, and the management network. Any connection entering the shooting range and management network will pass through the firewall. By adding filter conditions in the firewall rule base, it is possible to check and control the messages entering and leaving the shooting range and management network.
[0118] Second, the implementation of the data capture module
[0119] The key to the success of the data capture module lies in layer-by-layer checks: the more layers of data capture, the better the effect. This module captures suspicious traffic and abnormal behaviors entering and leaving the system as follows:
[0120] Step 1: As an access control layer device, the firewall can not only be used for data control, but also record the activities in and out of the honeypot. Since any activity in and out of the honeypot is considered suspicious, a firewall is used to capture suspic...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com