Network theft behavior detecting method based on HTTP flow analysis
A detection method and flow analysis technology, applied to electrical components, transmission systems, etc., can solve problems such as unpredictable difficulty and different communication protocols
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0034] The present invention will be described in further detail below in conjunction with the examples, but the protection scope of the present invention is not limited thereto.
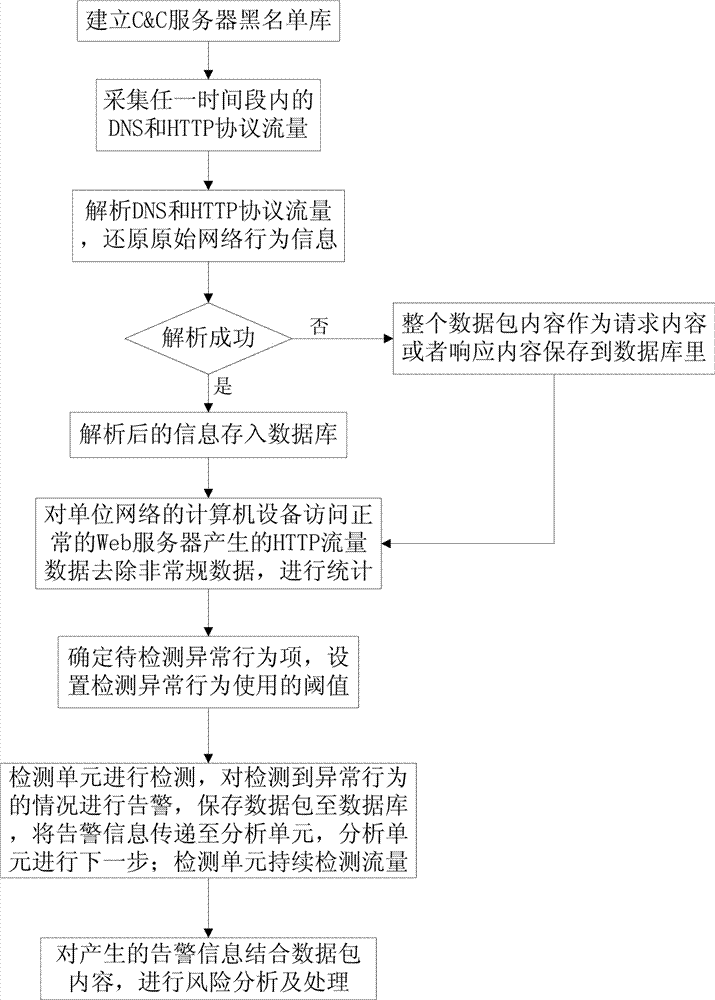
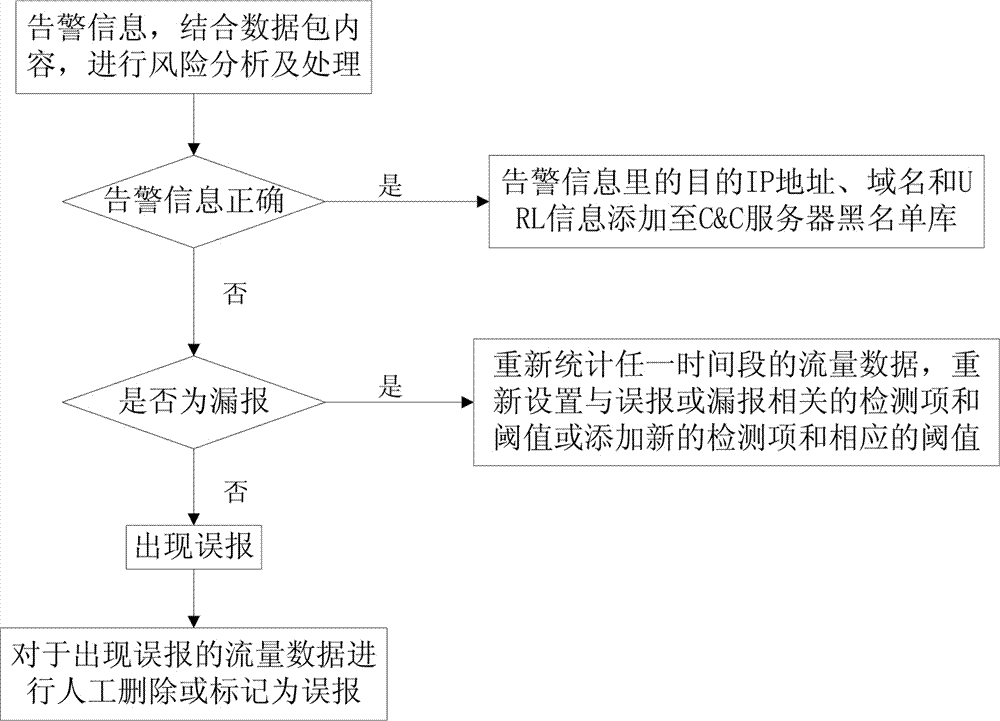
[0035] The invention relates to a network stealing behavior detection method based on HTTP flow analysis. Due to the obvious difference between the network behavior characteristics of malicious software when transmitting sensitive data and the behavior characteristics of human access to web servers under normal circumstances, through the analysis of tools based on HTTP protocol to transmit sensitive data and the network behavior characteristics of What are the abnormal behavior characteristics in the HTTP traffic; for a period of time, the HTTP traffic data generated by the computer equipment in the internal network of the unit (that is, the network protected by this detection method) to access the normal Web site is counted in multiple dimensions, as a reference, to determine The threshold for dete...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com