Mimetic defense-based network function deploying method in software defined network
A software-defined network and network function technology, applied in the field of network function deployment based on mimic defense, can solve problems such as network impact, service paralysis, economic loss, etc., and achieve the effect of enhancing security, increasing attack difficulty and attack cost
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
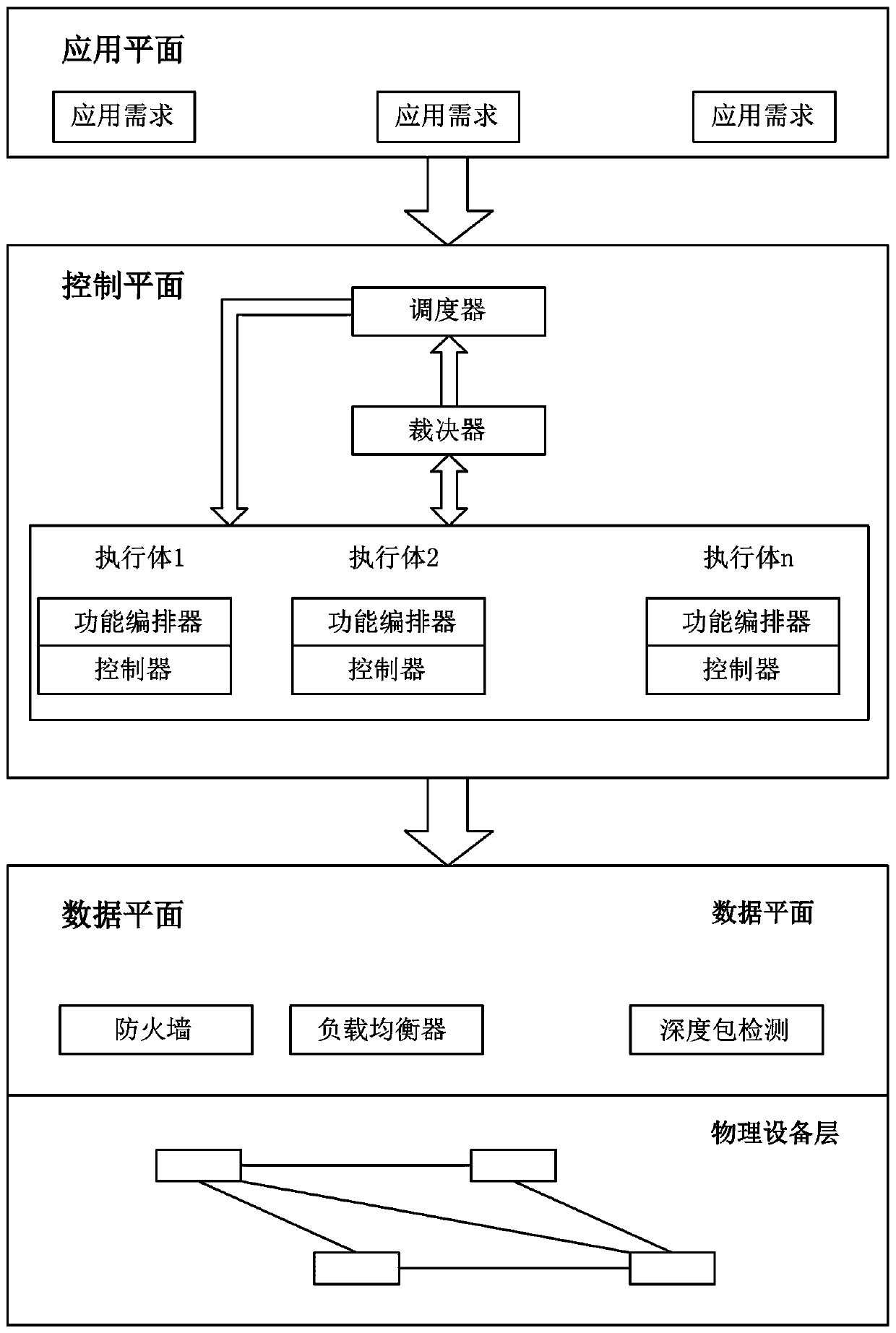
[0037] To improve the reliability and robustness of network function deployment under the software-defined network architecture, according to the above-mentioned mimic defense technology, such as figure 1 As shown, the present invention provides a network function deployment method based on mimic defense in a software-defined network, comprising the following steps:
[0038] Step 1. Deploy virtual network functions on the data plane through virtualization technology.
[0039] Preferably, the data plane includes a physical device layer constructed by an OpenFlow switch and a virtual function layer constructed by different network functions such as network address translation, firewall, and load balancing.
[0040] Step 2, build heterogeneous executive pool, scheduler and arbiter components on the control plane based on the mimic architecture.
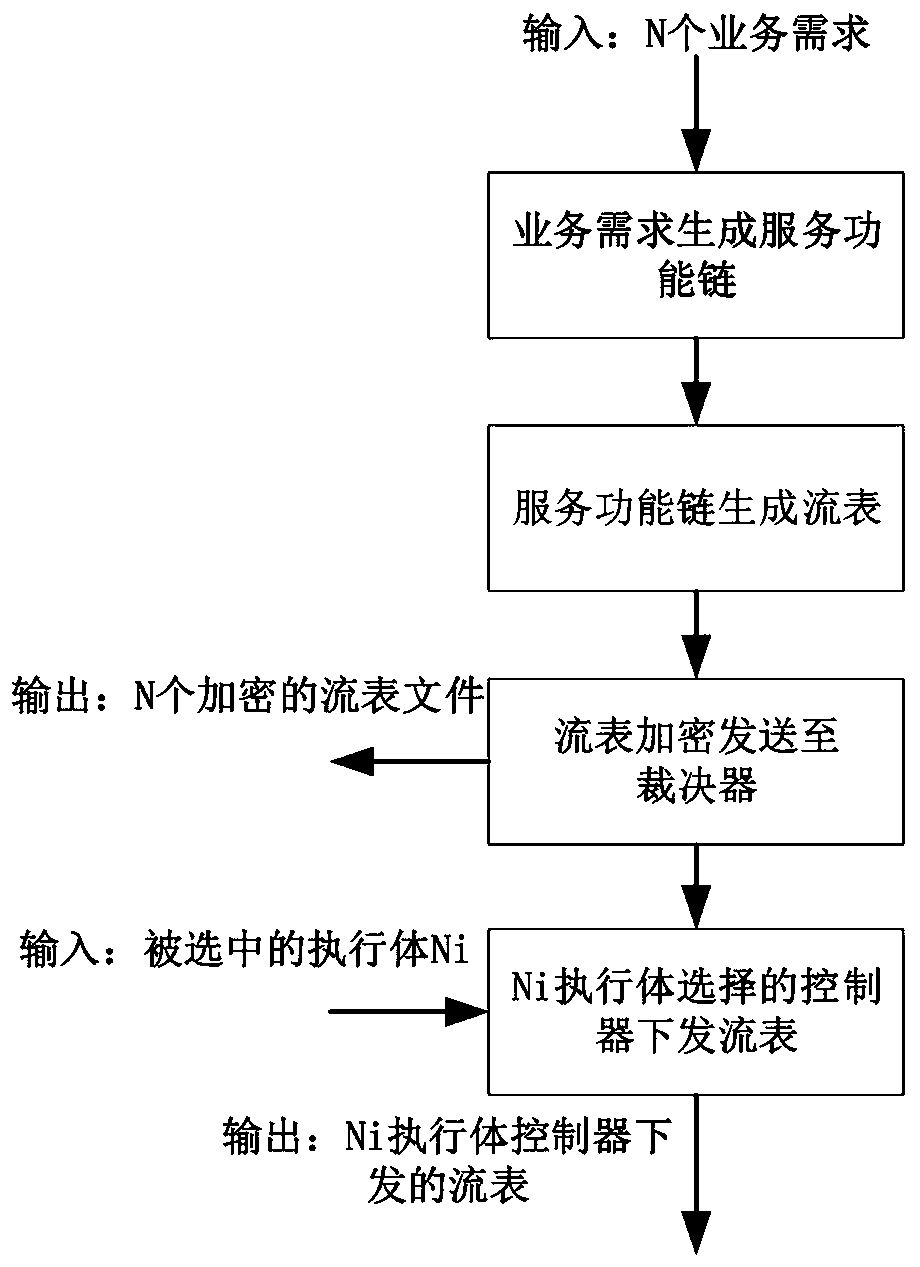
[0041] preferred, such as figure 2 As shown, the scheduler has an input parameter and an output parameter, the input parameter is th...
Embodiment 2
[0062] The difference between this embodiment and Embodiment 1 is that: the function orchestrator is an NFV orchestrator, and the controller is an SDN controller.
[0063] The existing mainstream NFV orchestrators are Womano, Tacker and Mano, and the mainstream SDN controllers are Ryu, Floodlight, OpenDaylight and ONOS. Therefore, in the process of constructing the heterogeneous executive pool, the heterogeneity of the heterogeneous executives in the heterogeneous executive pool can be realized based on the diversity of the controller and the function orchestrator.
[0064] In addition, the degree of heterogeneity of the heterogeneous execution entities in the heterogeneous execution entity pool can be increased through various combinations of the controller and the function orchestrator.
Embodiment 3
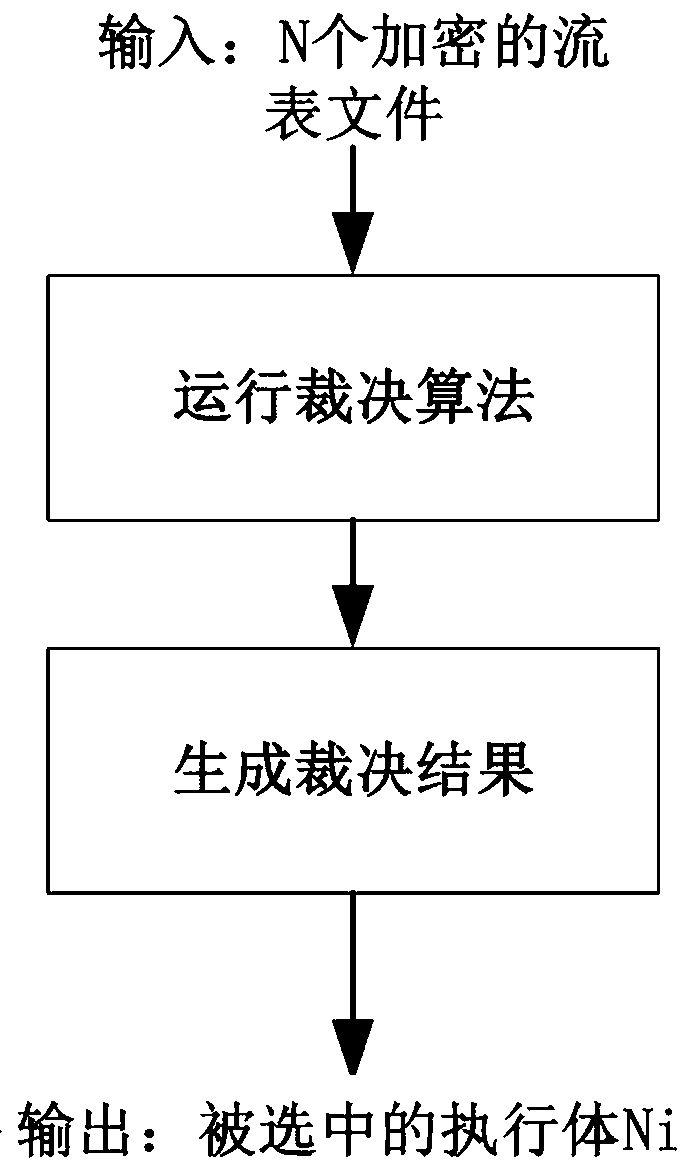
[0066] The difference between this embodiment and embodiment 1 and embodiment 2 is: as Figure 5 shown and Figure 6 As shown, in step 4, after the arbiter divides the N heterogeneous executives into normal heterogeneous executives and abnormal heterogeneous executives, the arbiter also sends abnormal heterogeneous executive information as the ruling result to The scheduler, the scheduler cleans the abnormal heterogeneous execution body according to the ruling result of the arbiter.
[0067] In this embodiment, through the arbiter's abnormal perception of the heterogeneous executives inside the system during the adjudication process, the scheduler can reduce the selection probability of abnormal heterogeneous executives, and further enhance the security of the scheduler's dynamic scheduling.
[0068] For example, for some network core services, due to their high security requirements, when the arbiter finds that there is an exception in a heterogeneous executive body, the inf...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com