ROOT-free active defense configuration method and device
A configuration method and active defense technology, applied in computer security devices, instruments, computing, etc., can solve the problems of low monitoring precision and difficult fine-grained behavior
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment approach
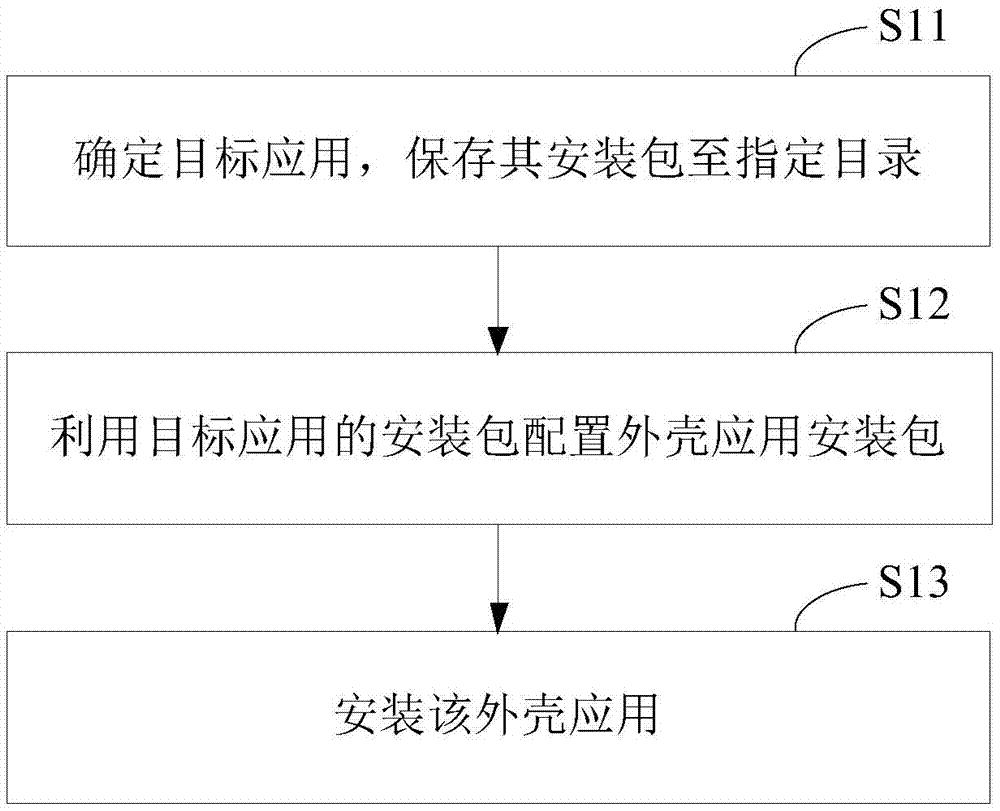
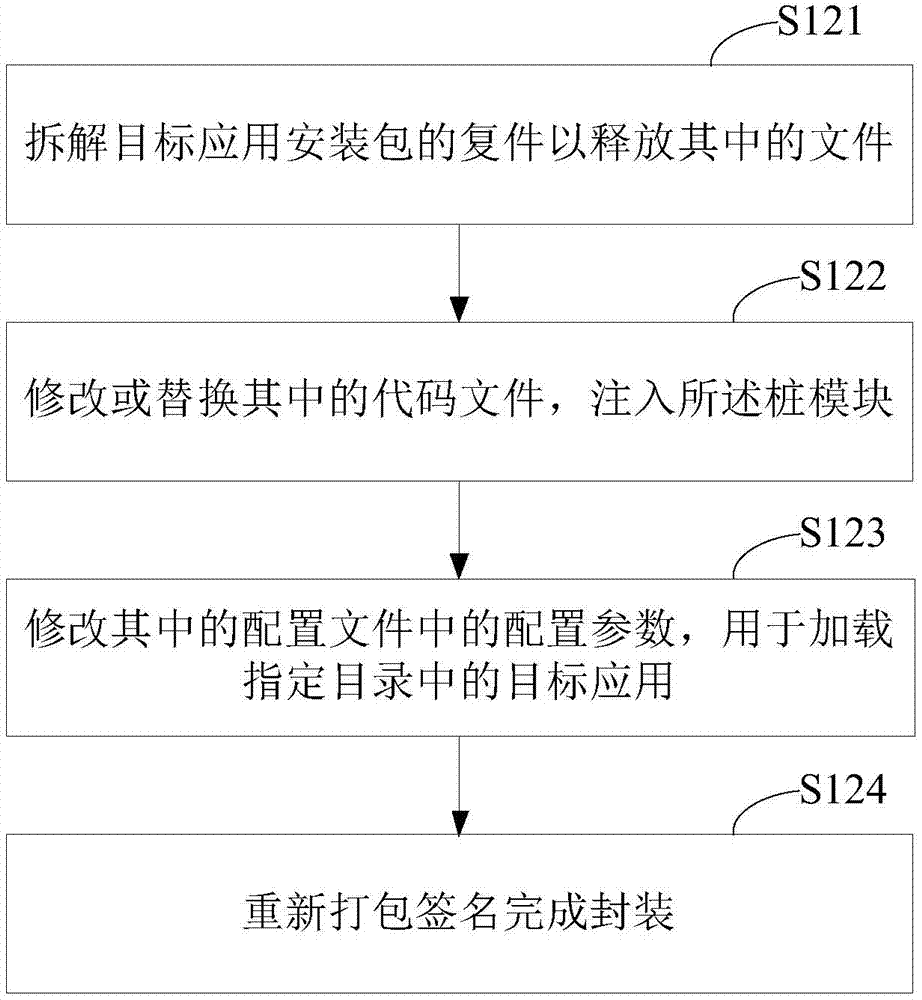
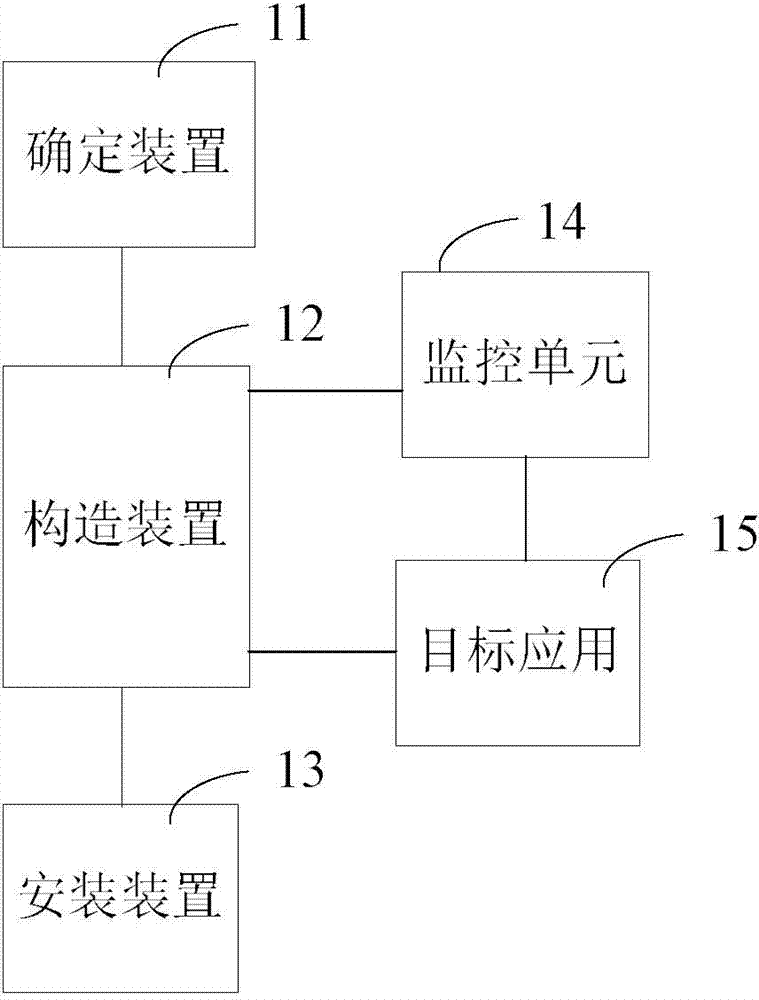
[0082] method one:
[0083] For the application programs that have been installed, the present invention can automatically or be controlled by user instructions to scan these installed application programs, obtain the installation information of these application programs, and display these application programs as a list of candidate target applications in the user interface (see Figure 9 ), providing a corresponding selection switch for each candidate target application in the list in the corresponding indication area of the graphical user interface, and setting the state of these switches by the user, so as to obtain the determination of the specific target application by the user. Specifically, the user can switch the selection switch in the indication area corresponding to a certain target application from the unselected state to the selected state, such as Figure 9 The "monitored" and "click to monitor" two-state switch example in , in this case, it can be considered...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com