Computer immune system design method and realization
A computer system, computer technology, applied in computer security devices, computing, instruments, etc., can solve the problems of lack of immunity, inability to system security protection, inability to fully protect computer system security, etc., to achieve the effect of improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
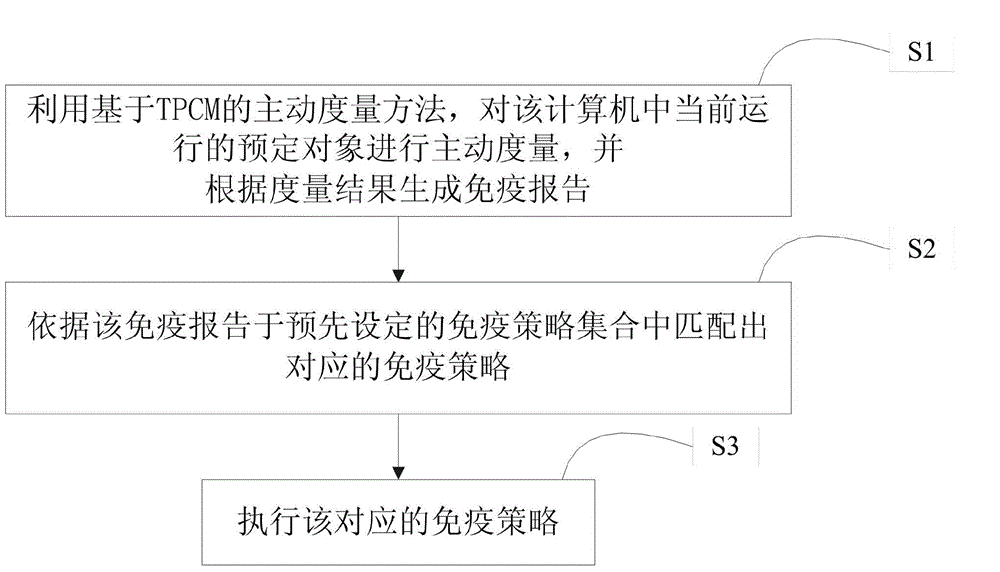
[0035] The specific implementation process of the present invention will be described in detail below in conjunction with the embodiments.
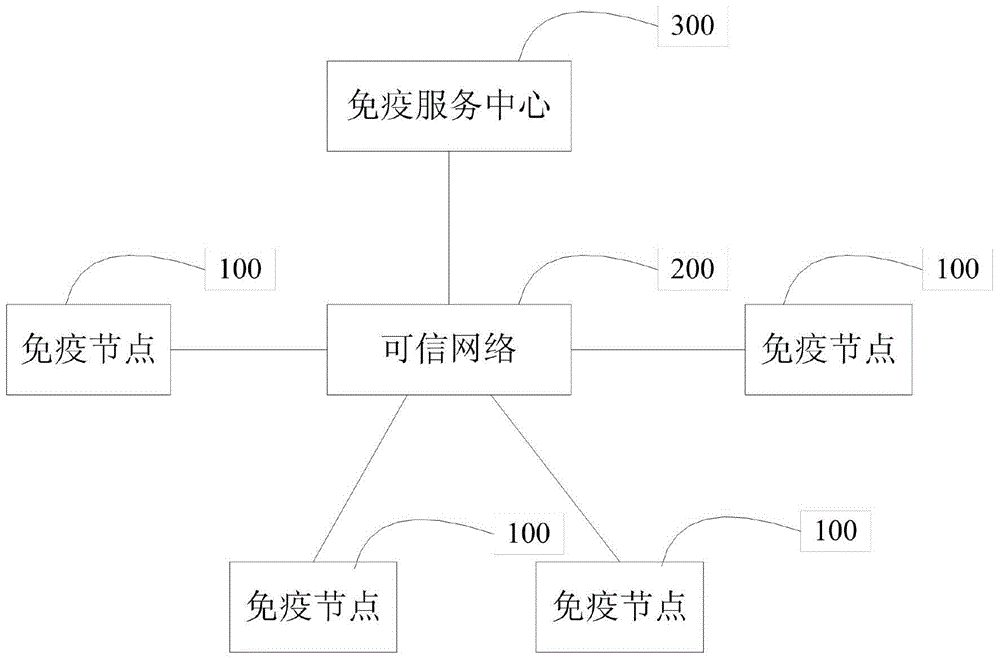
[0036] Similar to the human immune system, computer immunity is a new calculation model of active immunity that coexists with calculation and protection. It can identify "self" and "non-self" components in time, thereby destroying and repelling harmful substances entering the body. Such as figure 1 Shown is a schematic diagram of the overall architecture of the immune system of the present invention.
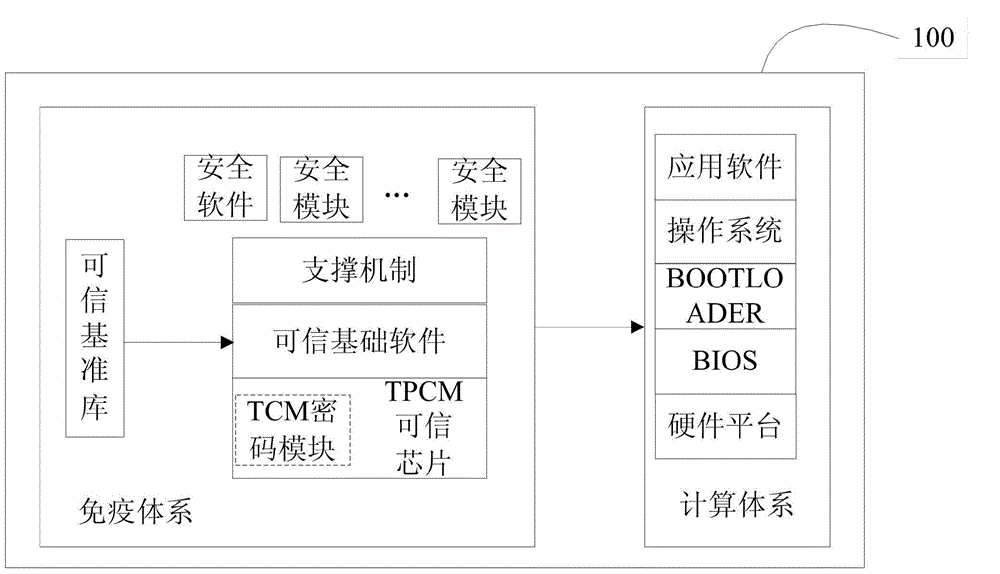
[0037] The overall architecture of the computer immune system is composed of multiple immune nodes 100 , a trusted network 200 and an immune service center 300 . Multiple immunization nodes 100 and the immunization service center 300 are connected to each other through the trusted network 200 . The immune node 100 is a terminal after computer immune modification. The immunization service center 300 can provide each immunization node 100 ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com