Relay protection information processing system attack behavior monitoring method and device
A technology of information processing system and relay protection device, applied in circuit devices, safety communication devices, transmission systems, etc., to achieve the effect of improving safety
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
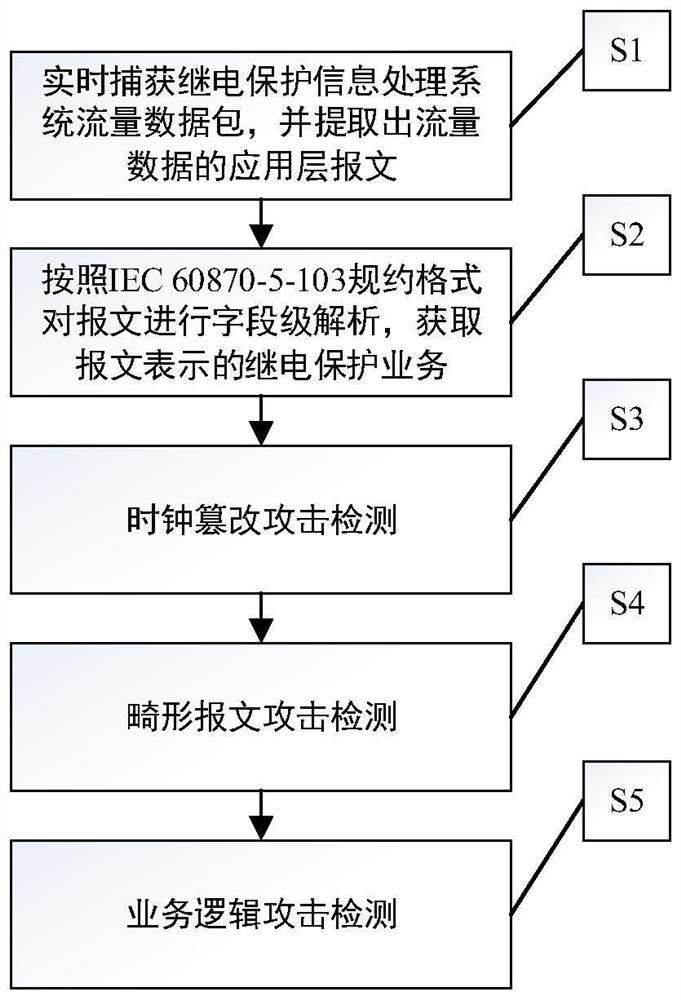
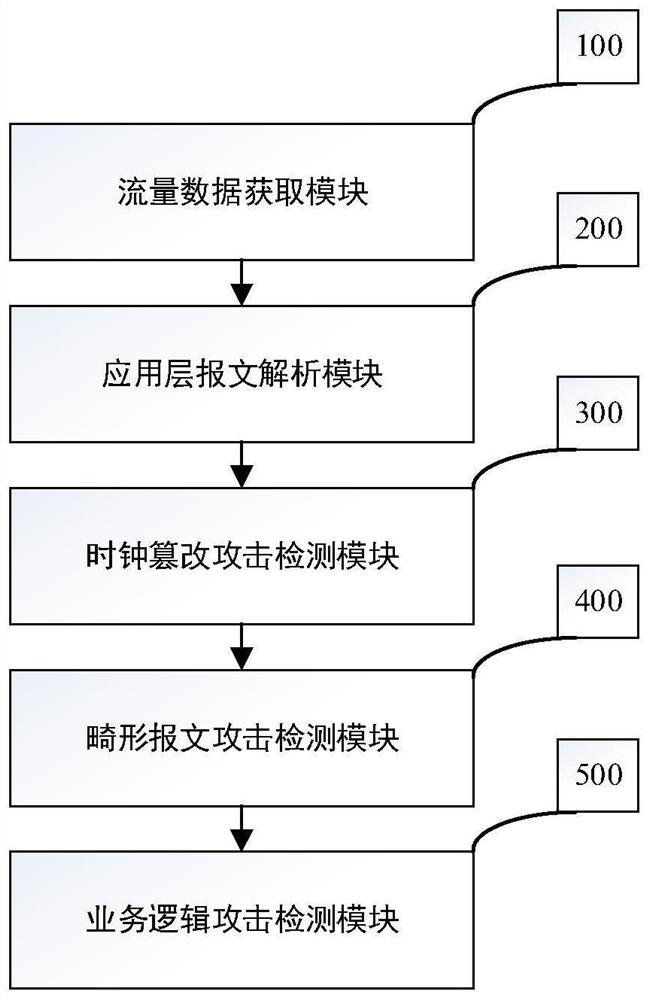
[0057] figure 1 The flow chart of the method for monitoring the attack behavior of the relay protection information processing system provided by the embodiment of the present invention, the specific implementation steps are as follows:
[0058] Step S1: capturing the relay protection information processing system traffic data packets in real time, and extracting the application layer message of the current frame traffic data;
[0059] Step S2: perform field-level analysis on the message according to the IEC 60870-5-103 protocol, obtain the specific value of the message length field, type identifier, transmission reason, information serial number, and clock characteristics, and determine the system service to which the message belongs;
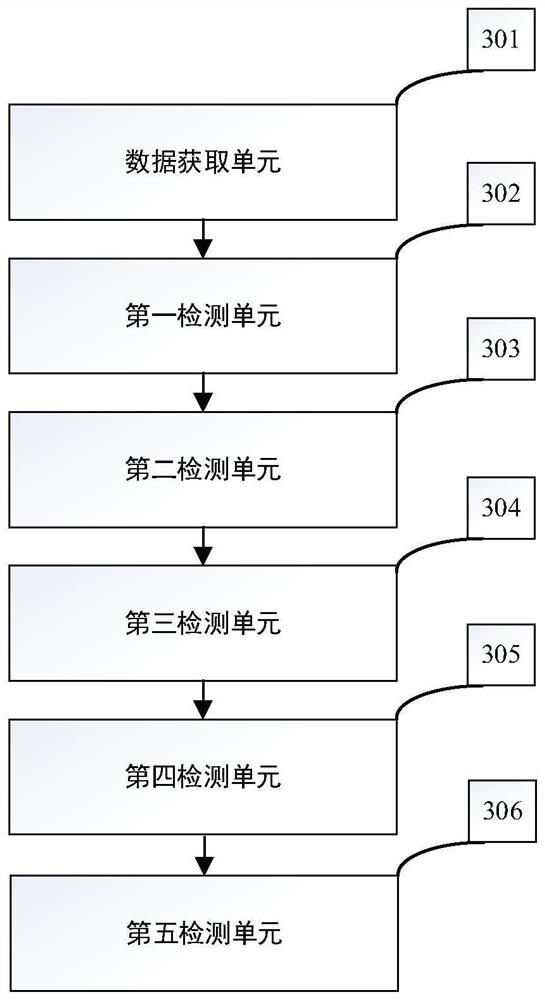
[0060] Step S3: Perform clock tampering attack detection on the packet parsed in step S2, if the clock range, clock logic, clock synchronization, and clock delay of the packet do not conform to normal clock characteristics, it is determined th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com