Control method for Bluetooth security management
A control method and security management technology, which is applied in the control field of Bluetooth security management, can solve problems such as risks, lack of Bluetooth communication equipment management capabilities, inability to identify and control management, etc., and achieve the effect of simple implementation methods
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
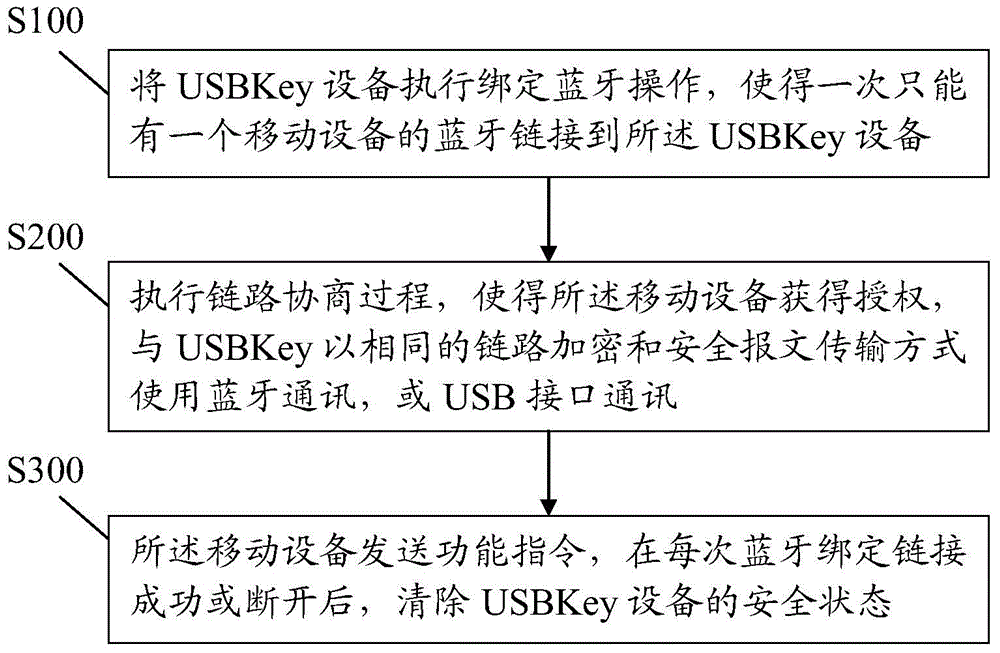
[0011] Certain terms are used, for example, in the description and claims to refer to particular components. Those skilled in the art should understand that hardware manufacturers may use different terms to refer to the same component. The specification and claims do not use the difference in name as a way to distinguish components, but use the difference in function of components as a criterion for distinguishing. As mentioned throughout the specification and claims, "comprising" is an open term, so it should be interpreted as "including but not limited to". "Approximately" means that within an acceptable error range, those skilled in the art can solve the technical problem within a certain error range and basically achieve the technical effect. The subsequent description of the specification is a preferred implementation mode for implementing the application, but the description is for the purpose of illustrating the general principle of the application, and is not intended...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com