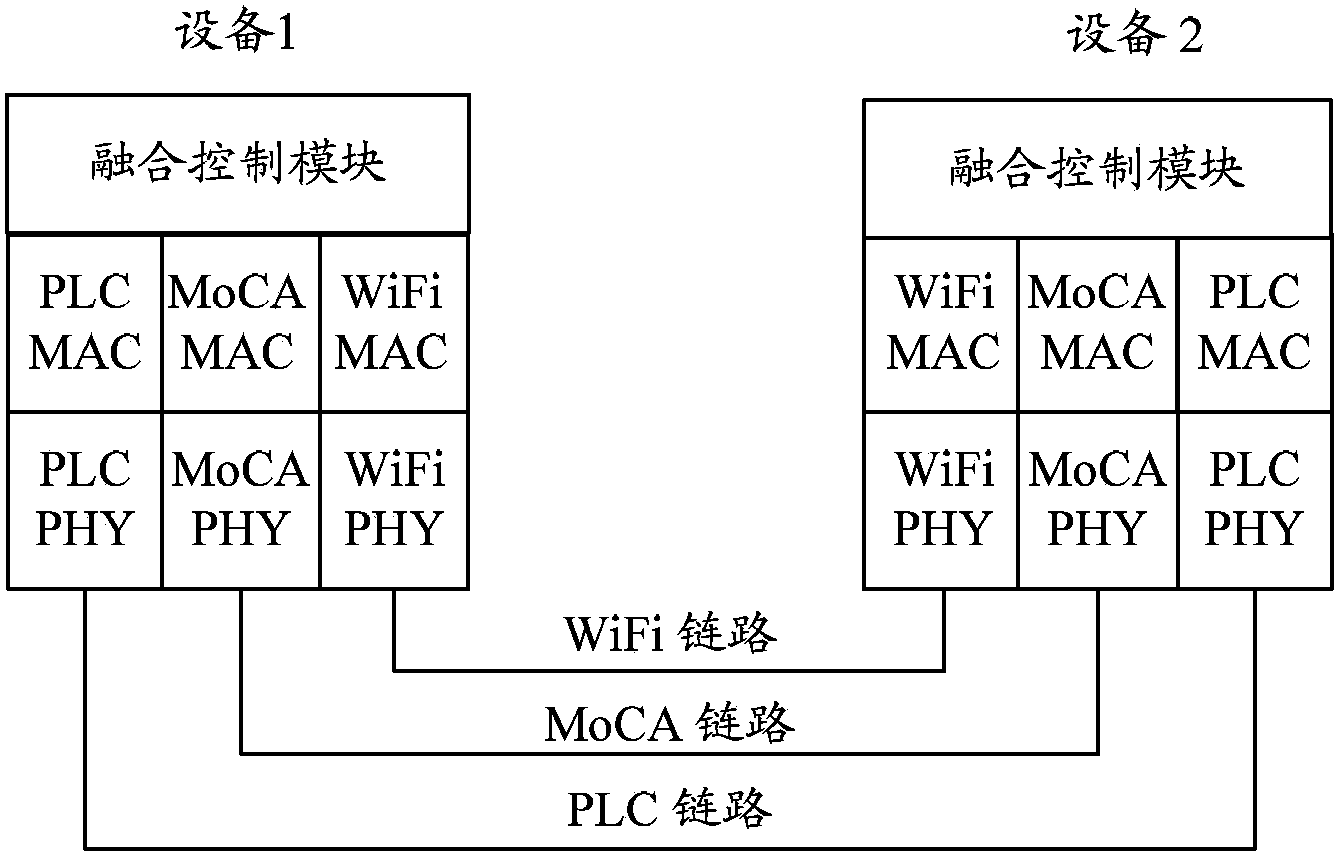
Patents
Literature
53 results about "Link encryption" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
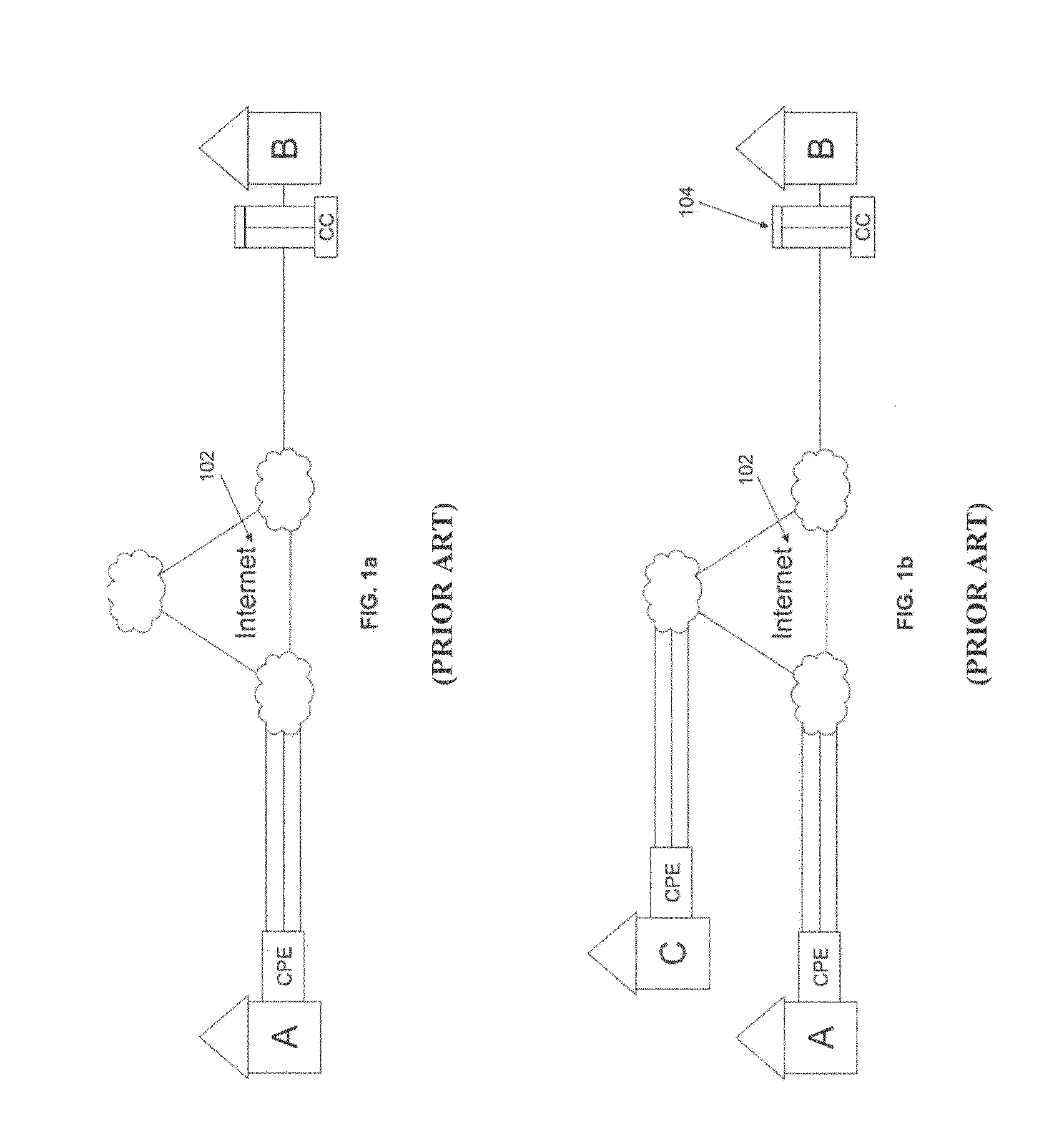
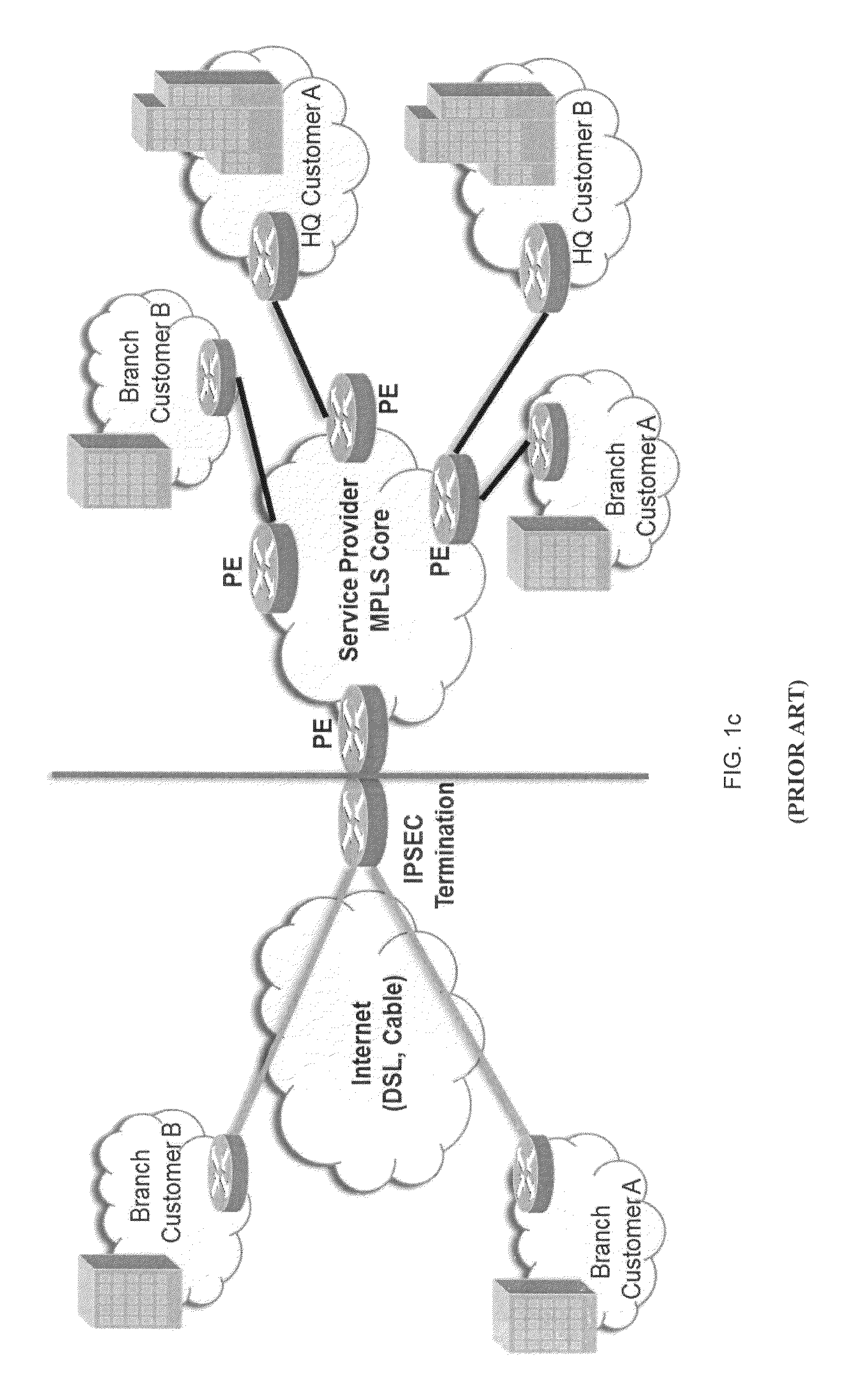
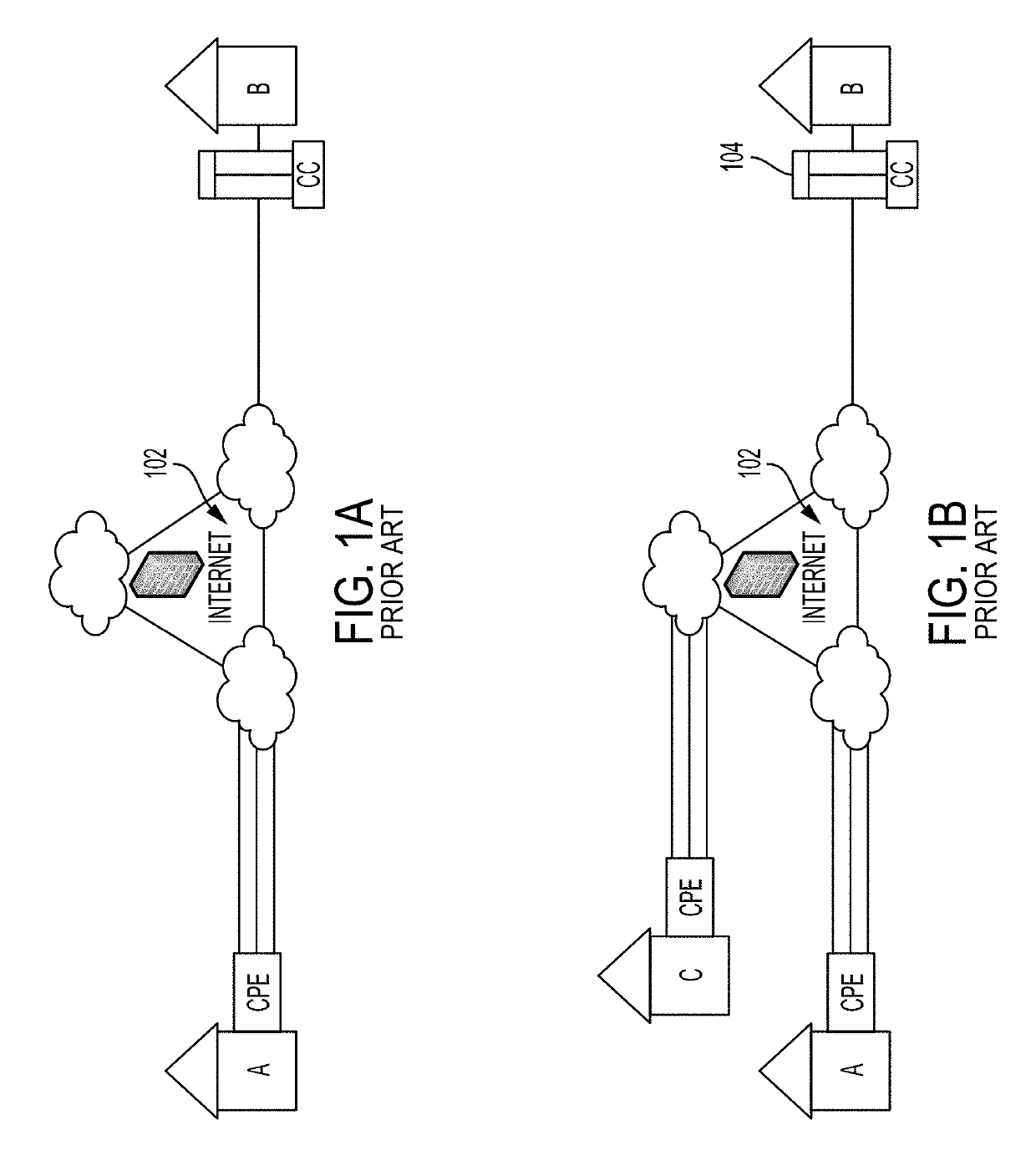
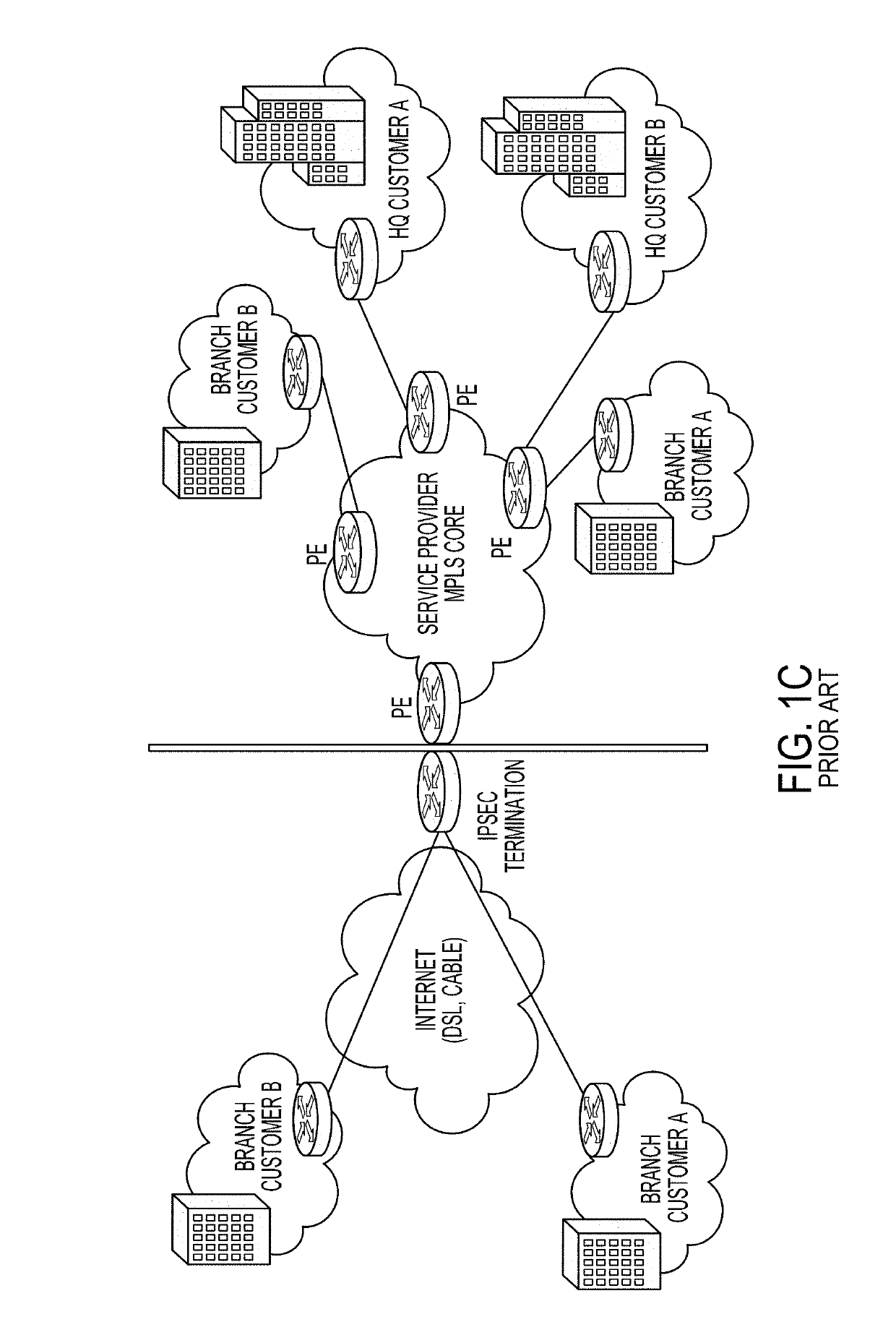
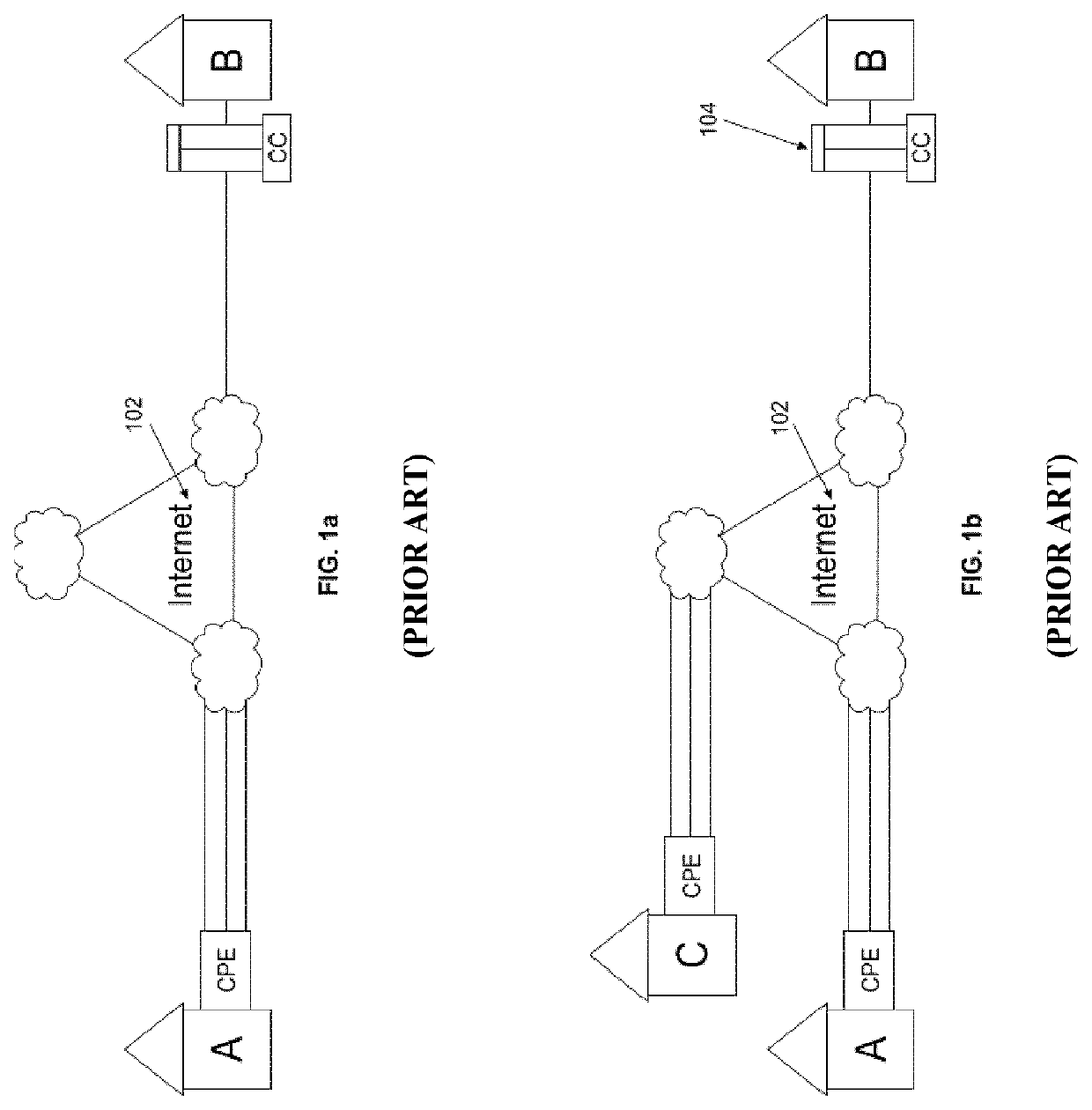
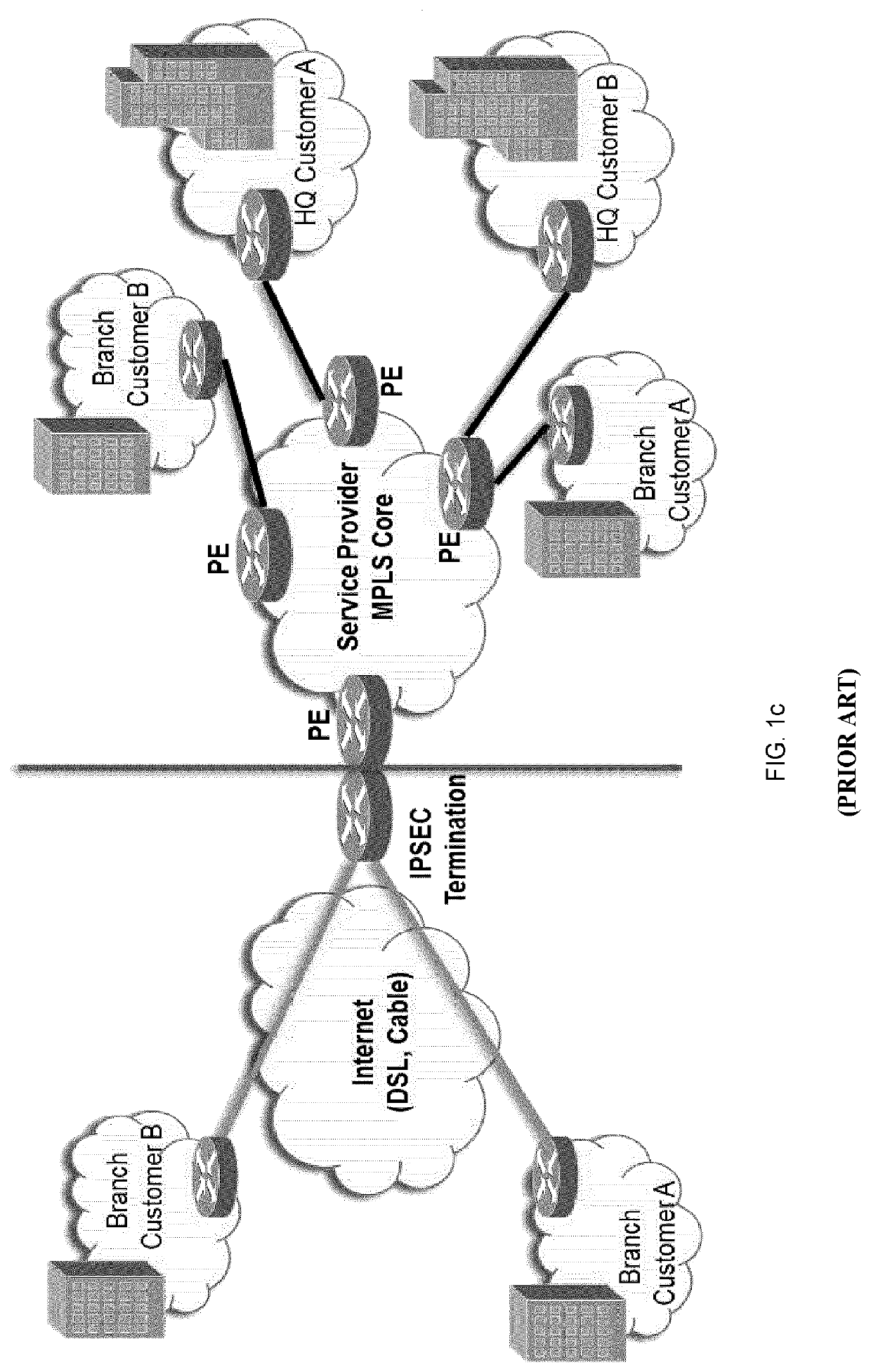
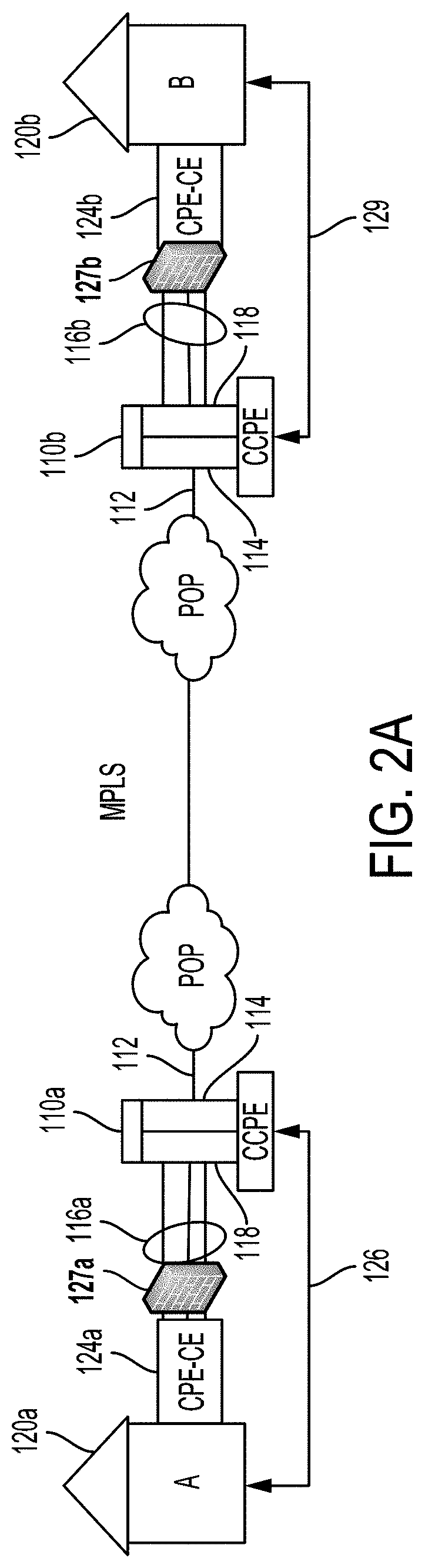
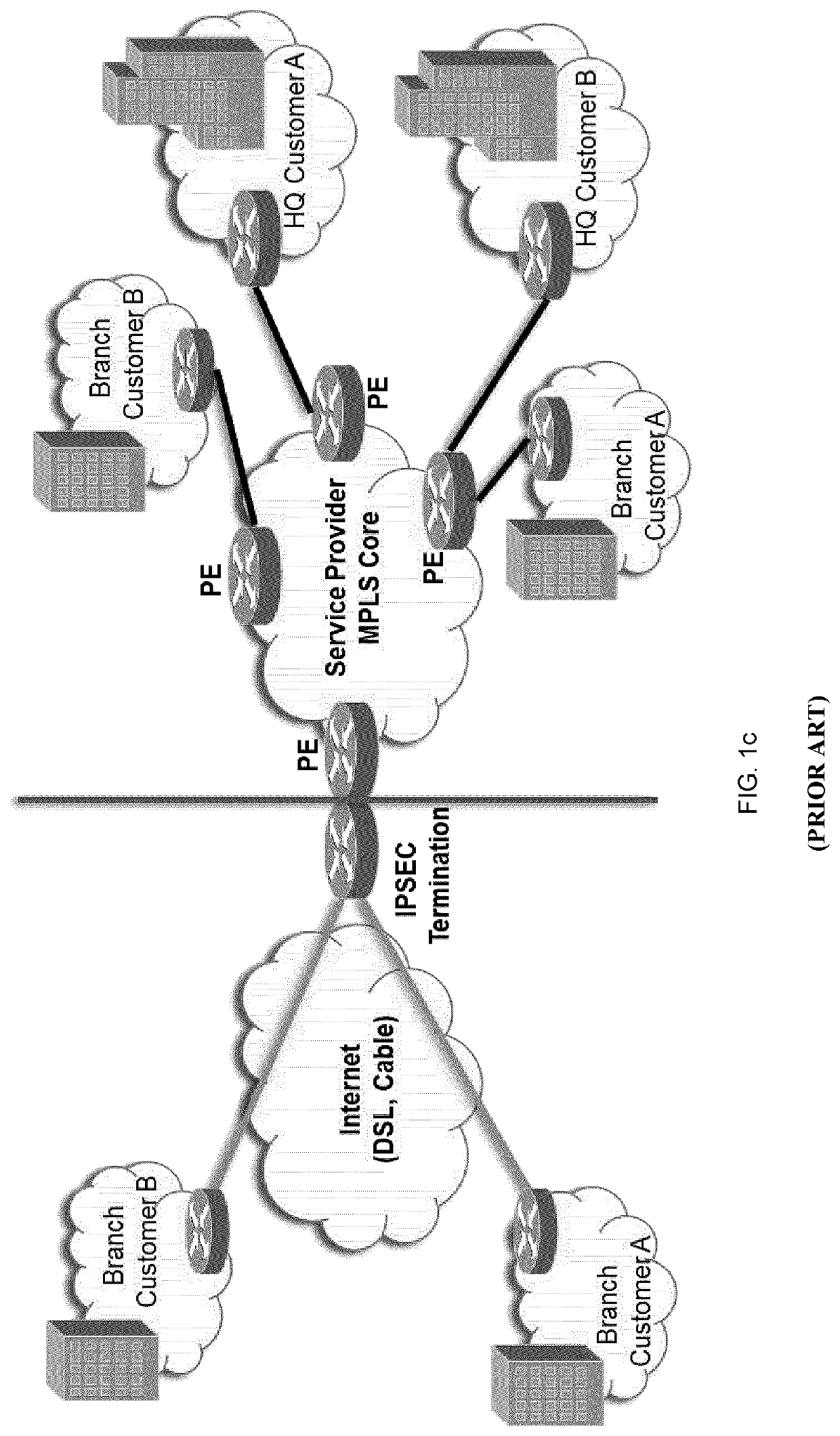
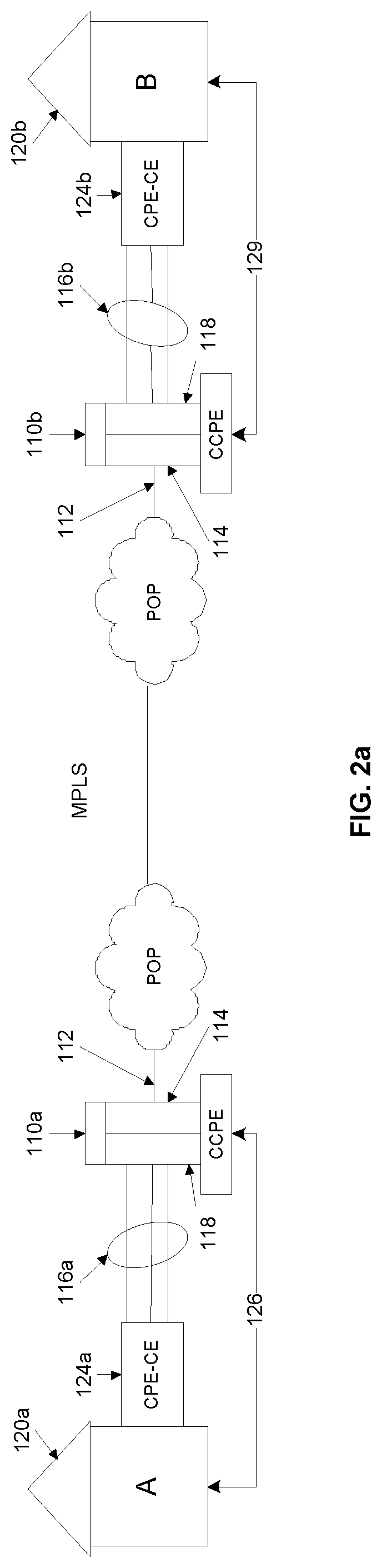
Link encryption is an approach to communications security that encrypts and decrypts all traffic at each network routing point (e.g. network switch, or node through which it passes) until arrival at its final destination. This repeated decryption and encryption is necessary to allow the routing information contained in each transmission to be read and employed further to direct the transmission toward its destination, before which it is re-encrypted. This contrasts with end-to-end encryption where internal information, but not the header/routing information, are encrypted by the sender at the point of origin and only decrypted by the intended receiver.
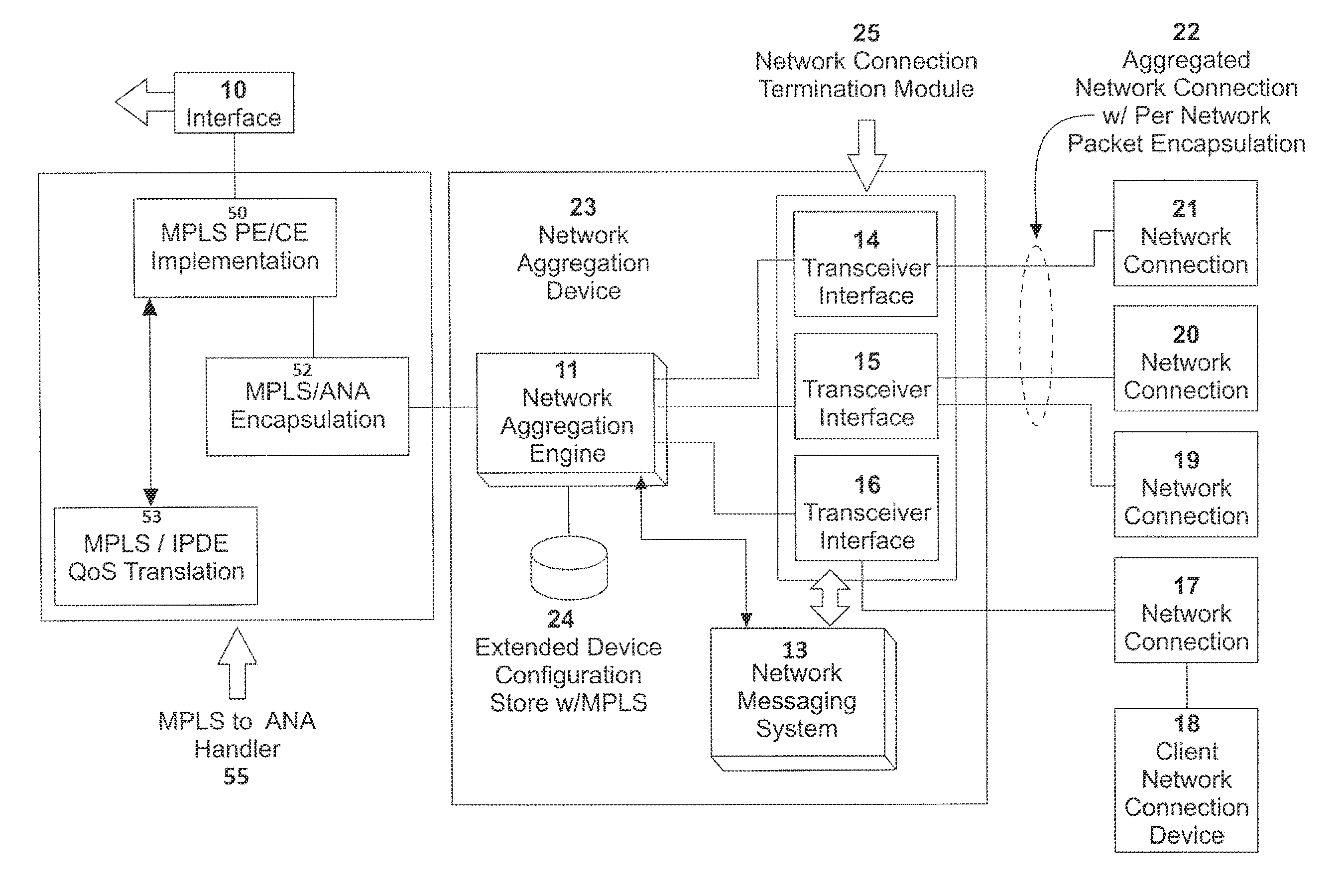
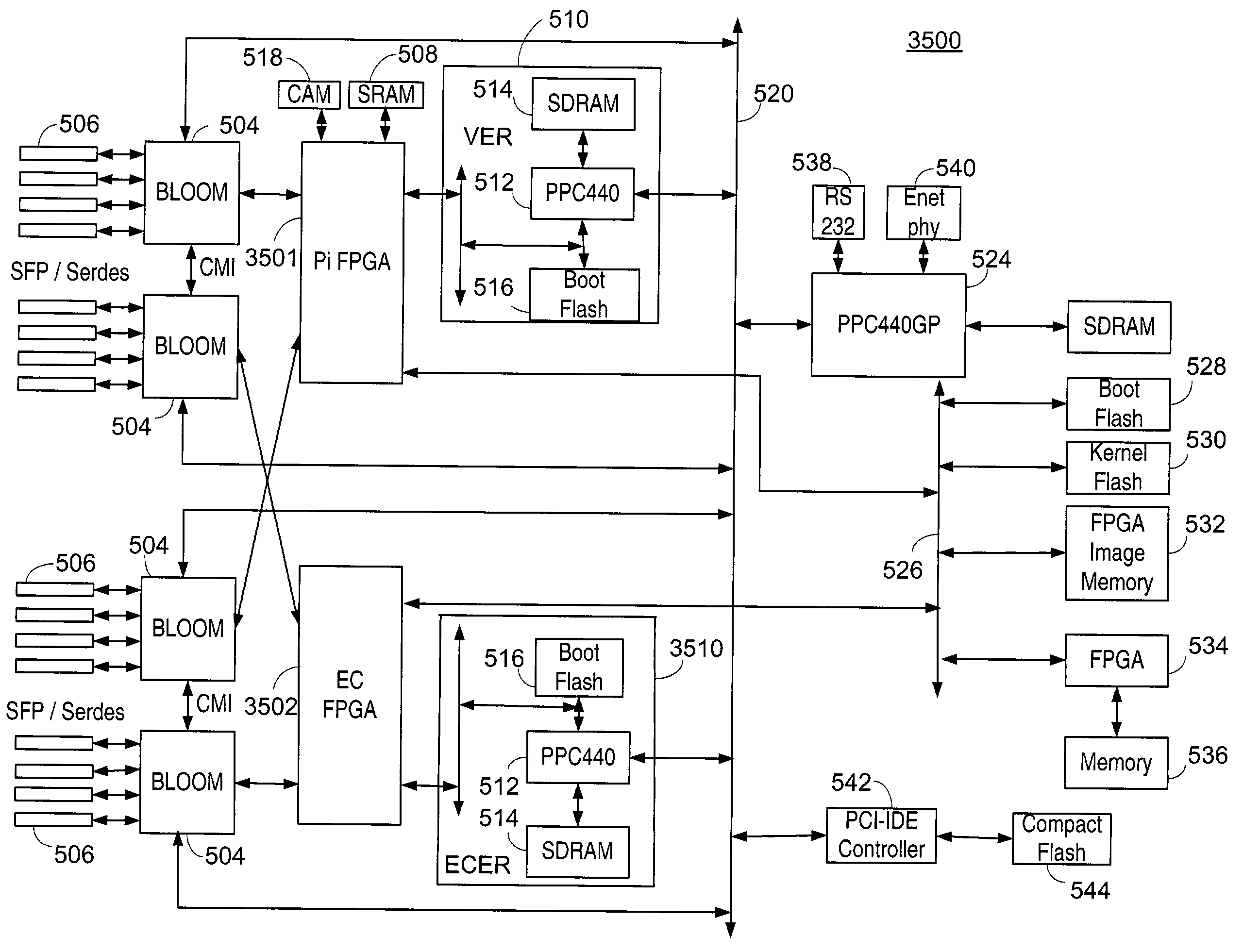
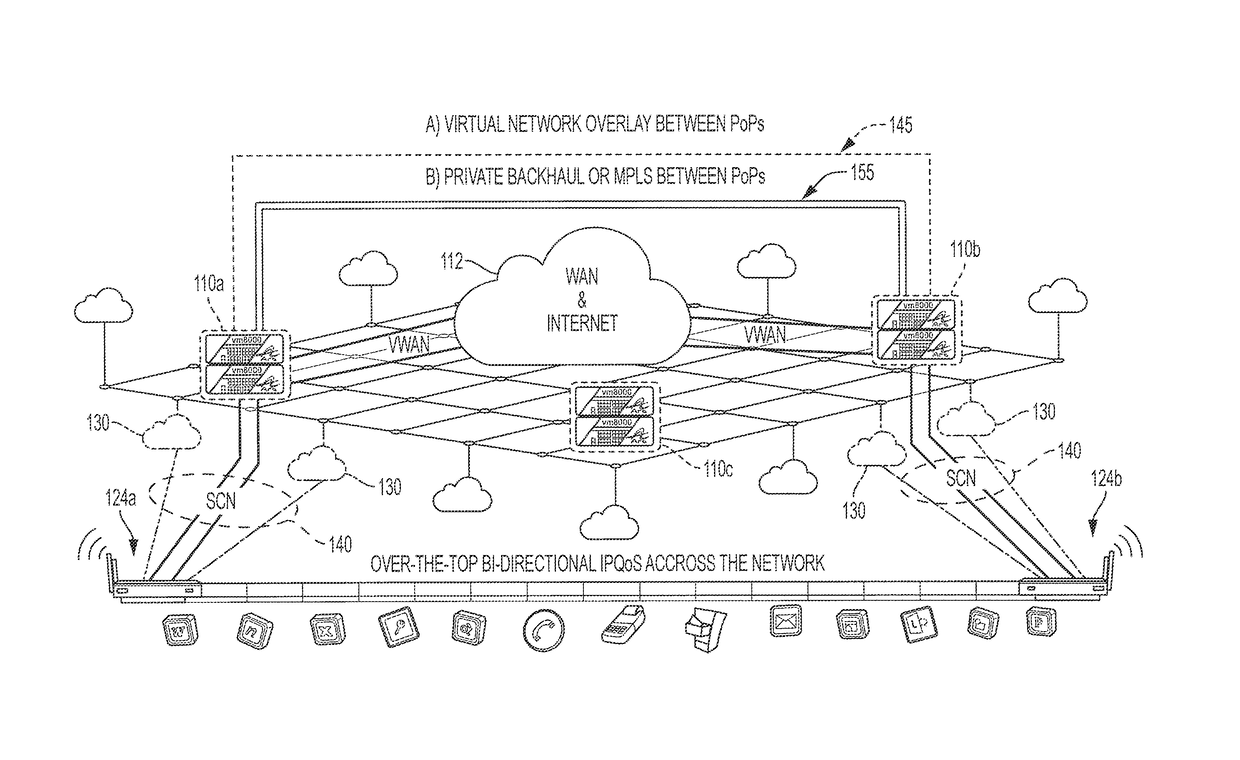
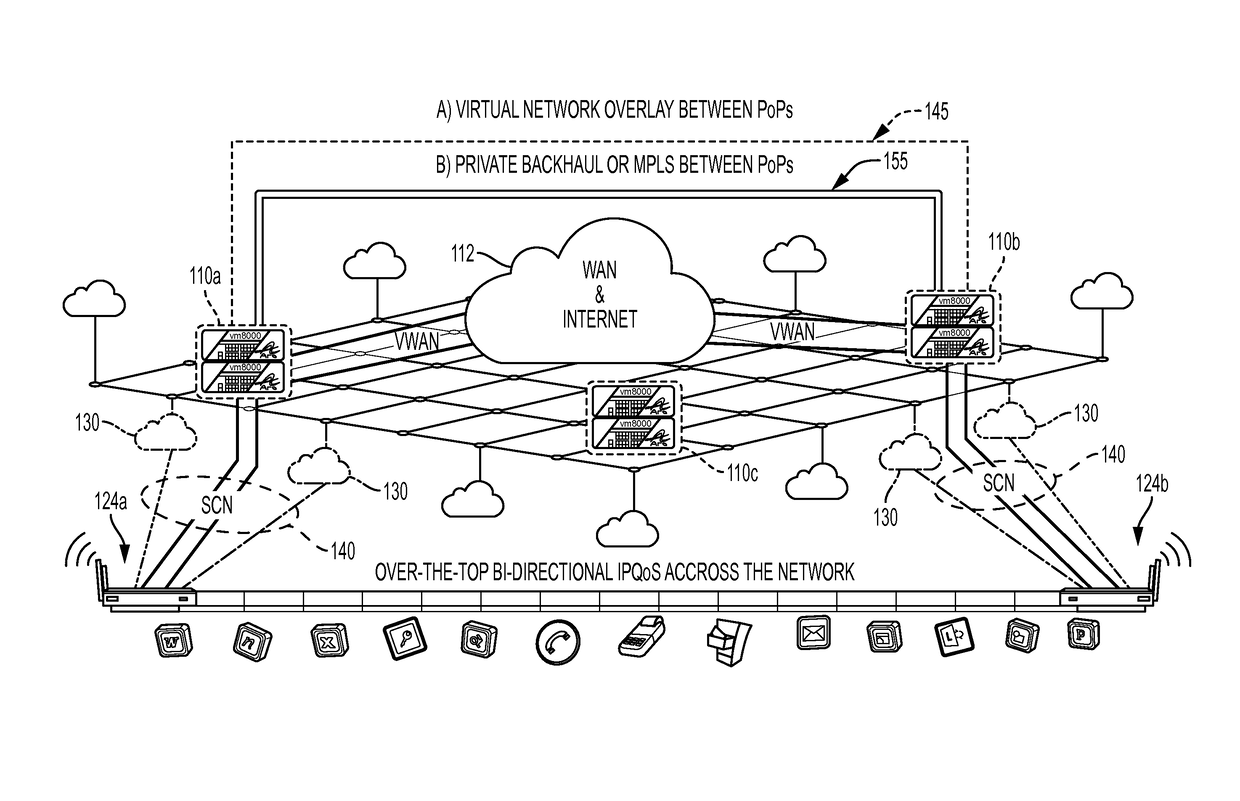
System, apparatus and method for providing a virtual network edge and overlay with virtual control plane
ActiveUS20160072669A1Improve communication performanceImprove throughputDigital computer detailsNetworks interconnectionTraffic capacityNetwork connection
A network system is provided between at least a first client site and a second client site. A client site network component is implemented at least at the first client site, the client site network component aggregating one or more diverse network connections so as to configure an aggregated connection that has increased throughput. At least one network server component may be configured to connect to the client site network component using the aggregated connection. A cloud network controller may be configured to manage the data traffic and a virtual edge providing transparent lower-link encryption for the aggregated connection between the client site network component and the network server component. The network server component includes a virtual control plane interface configured to establish a unicast path between the network server component and each of a plurality of remote network server components.
Owner:ADAPTIV NETWORKS INC
System, apparatus and method for providing a virtual network edge and overlay
ActiveUS20160006672A1Improve communication performanceImprove throughputData switching by path configurationHigh level techniquesTraffic capacityNetwork connection
A network system is provided between at least a first client site and a second client site, the first and the second client site are at a distance from one another. A client site network component is implemented at least at the first client site, the client site network component bonding or aggregating one or more diverse network connections so as to configure a bonded / aggregated connection that has increased throughput. At least one network server component may be configured to connect to the client site network component using the bonded / aggregated connection. A cloud network controller may be configured to manage the data traffic and a virtual edge providing transparent lower-link encryption for the bonded / aggregated connection between the client site network component and the network server component.
Owner:ADAPTIV NETWORKS INC
System, apparatus and method for providing a unified firewall manager
ActiveUS20190182213A1Improve communication performanceImprove throughputTransmissionTraffic capacityNetwork connection
A network system is provided between at least a first client site and a second client site, the first and the second client site are at a distance from one another. A client site network component is implemented at least at the first client site, the client site network component bonding or aggregating one or more diverse network connections so as to configure a bonded / aggregated connection that has increased throughput. At least one network server component may be configured to connect to the client site network component using the bonded / aggregated connection. A cloud network controller may be configured to manage the data traffic and a virtual edge providing transparent lower-link encryption for the bonded / aggregated connection between the client site network component and the network server component.
Owner:ADAPTIV NETWORKS INC
Method for protecting privacy when using a Bluetooth device
InactiveUS7194760B2Privacy protectionDigital data processing detailsNetwork topologiesComputer hardwareBluetooth
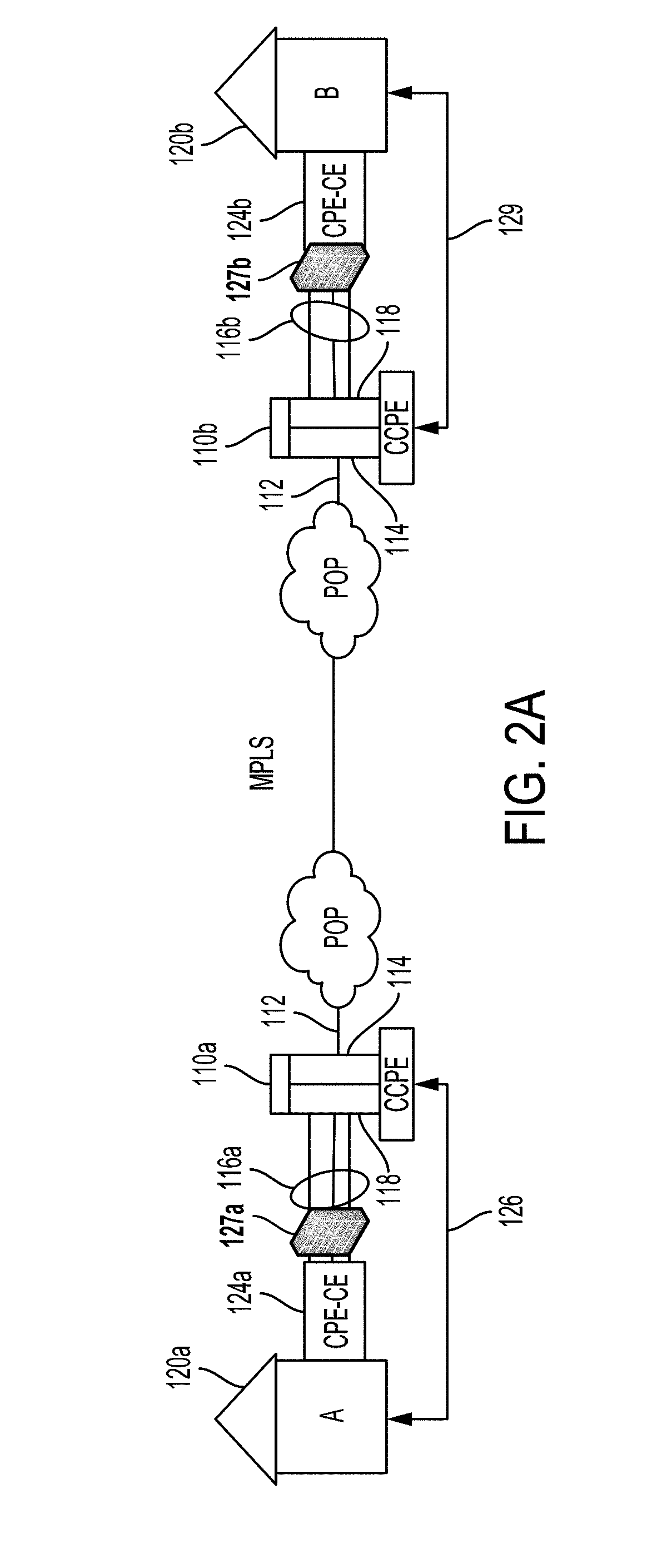
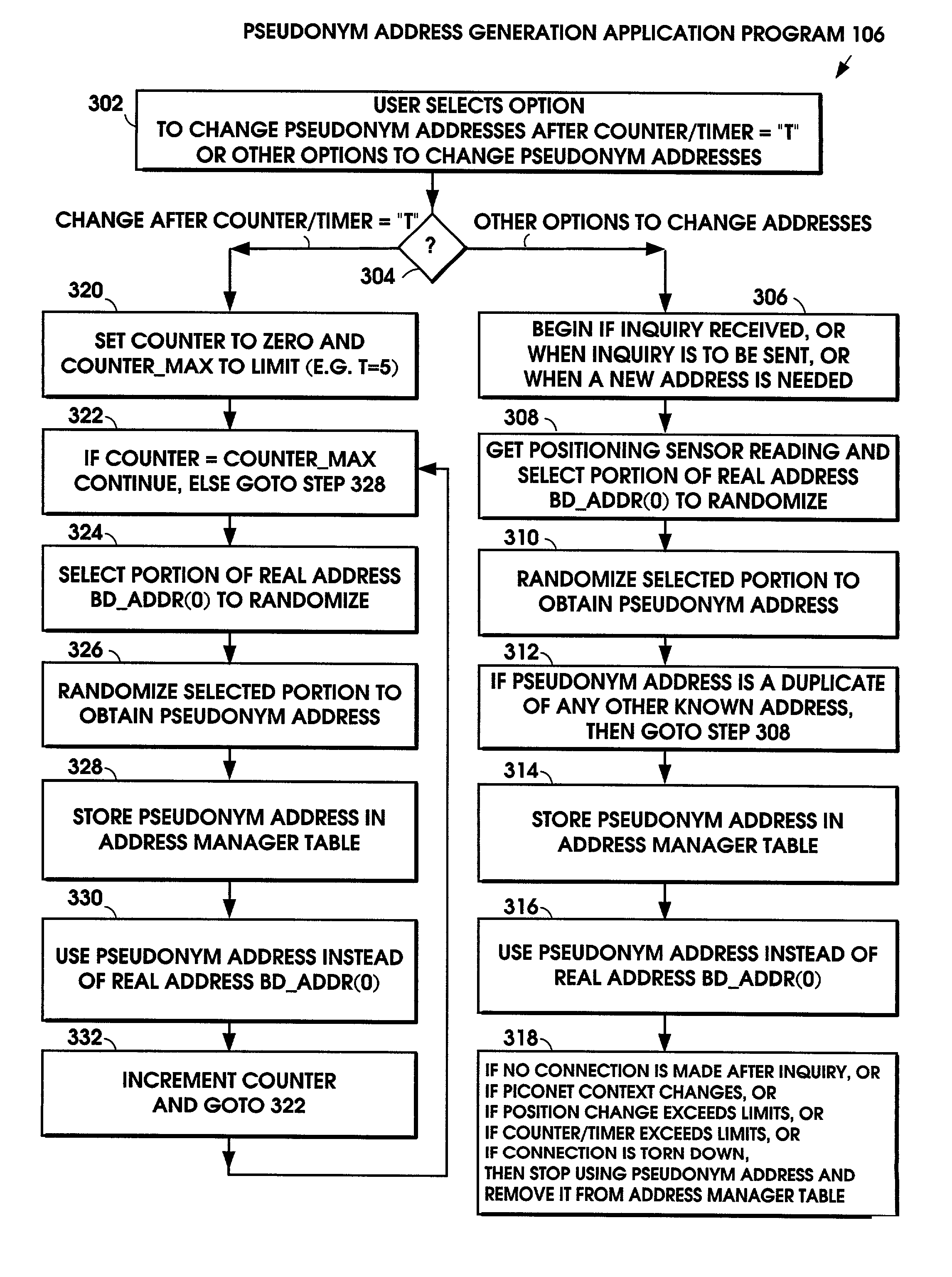
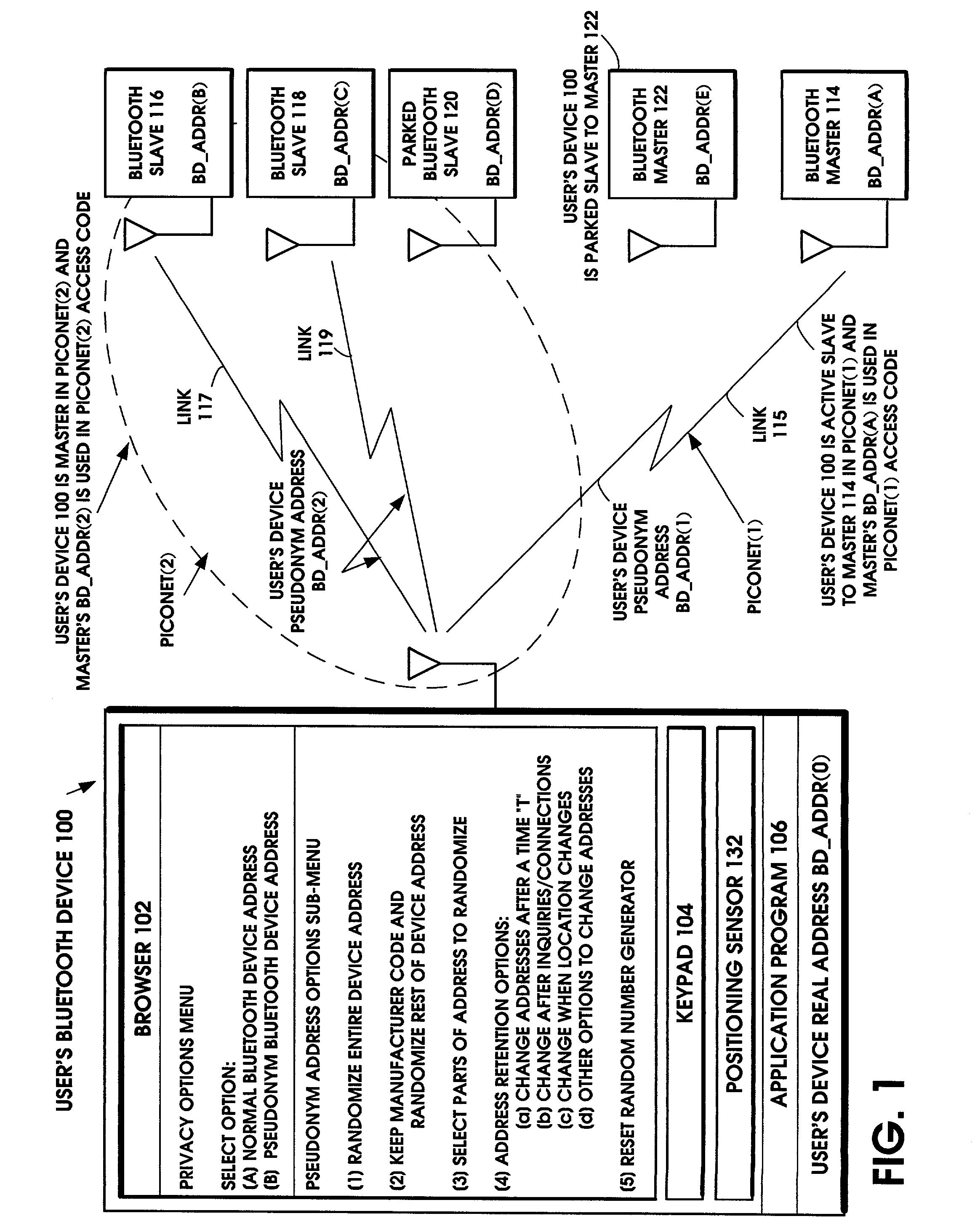
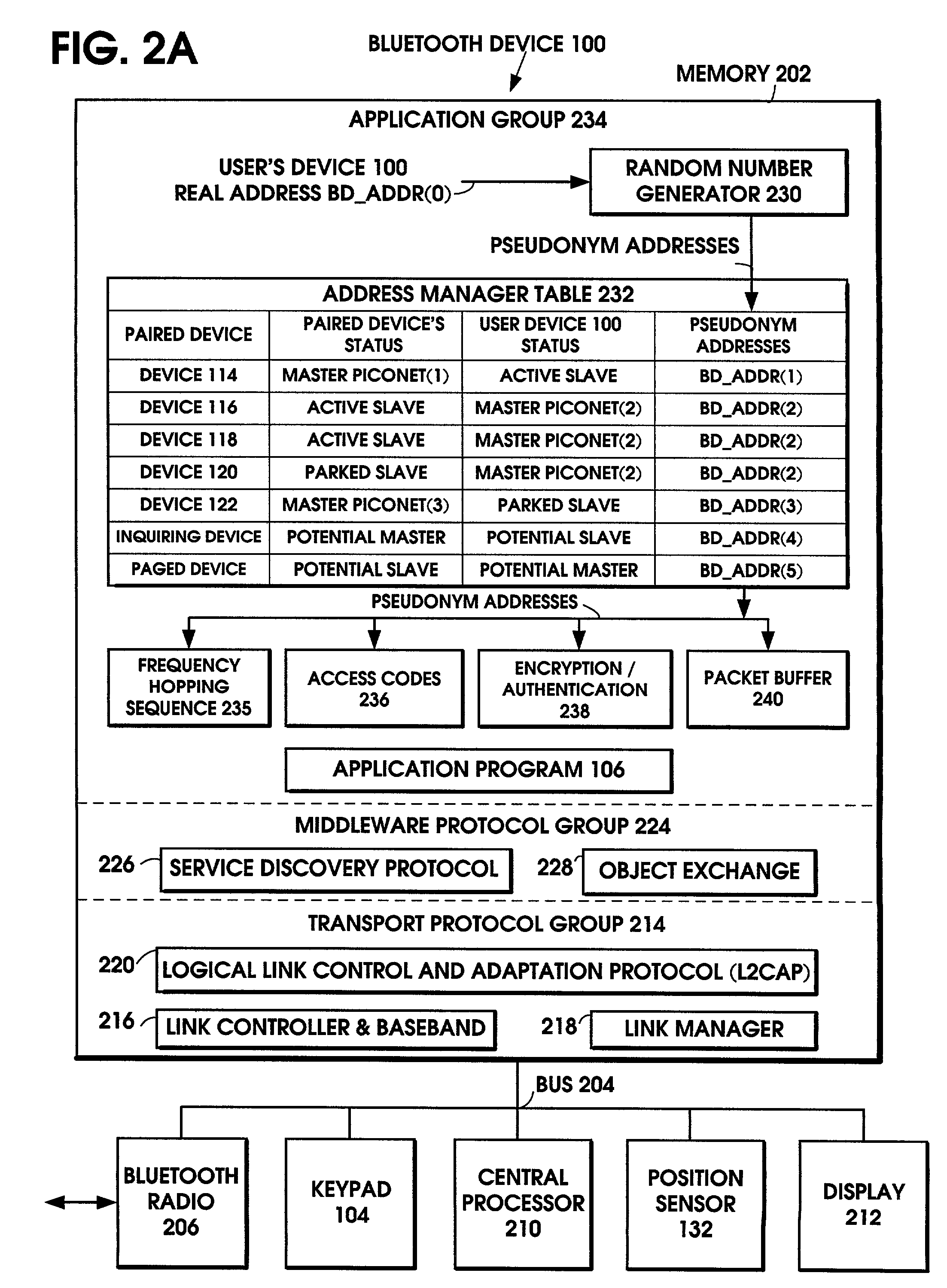
The user's Bluetooth device substitutes a pseudonym address for the Bluetooth Device Address (BD_ADDR). The pseudonym address is a randomized version of the BD_ADDR. The pseudonym address is used in all the functions of the Bluetooth device that normally use the BD_ADDR, including the frequency hopping sequence, the device access code, the initialization key in link encryption, the authentication code, and the various packet addresses. In this manner, the user's privacy is protected by preventing the user's identity, routes, and activities from being correlated with his / her device's address. In addition to the Bluetooth standard, the technique also applies to other wireless standards.
Owner:NOKIA TECHNOLOGLES OY
Security certificate gateway
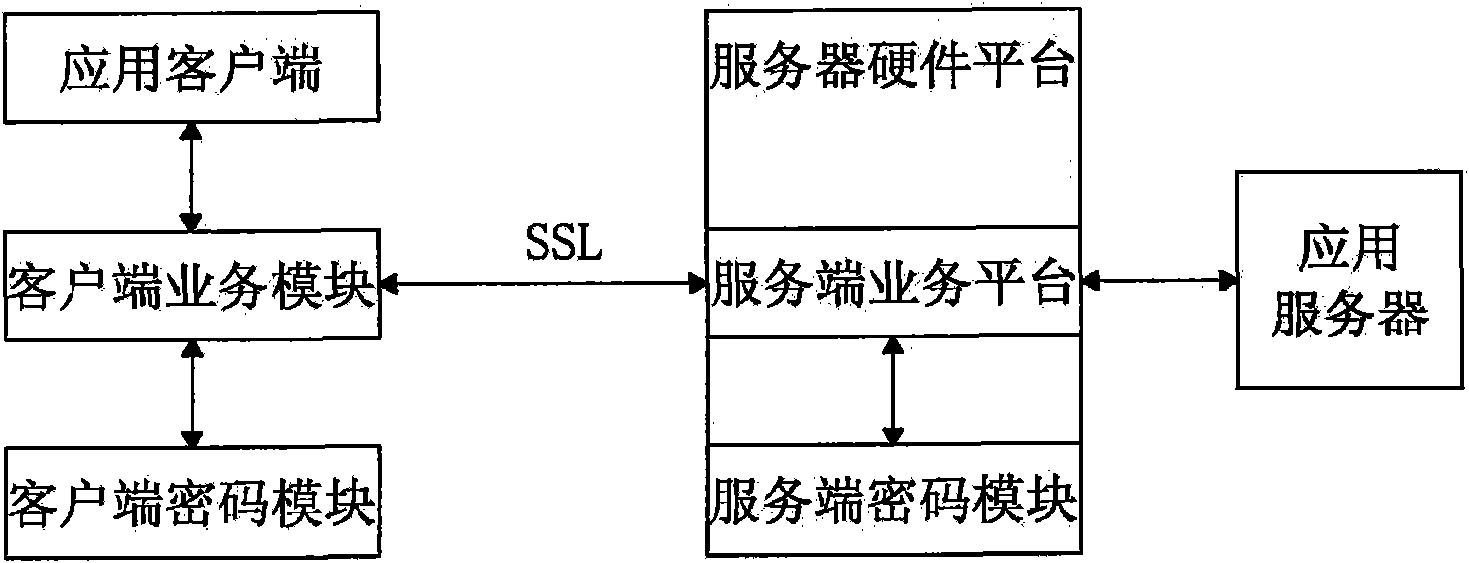
InactiveCN102111349ARealize data transmission securityAchieving Valid AuthenticationNetwork connectionsInternet Authentication ServiceRemote desktop
The invention discloses a security certificate gateway, comprising a client crypto module, a client business module, a service business module and a service crypto module, wherein the client business module is used as an agent of an application client and used for calling the client crypto module and the service business module interactively to build an encrypted connection; and the service business module is used for calling the service crypto module and the service business module to build a secure encrypted channel. Based on the high-strength identity authentication service, the high-strength data link encryption service and the digital signature and authentication service of a digital certificate, the gateway provided by the invention effectively protects secure access of network resources, and supports B / S applications of a hypertext transport protocol (HTTP) and hypertext transfer protocol secure (HTTPS) as well as common C / S applications of a file transfer protocol (FTP), a remote desktop and the like.
Owner:KOAL SOFTWARE CO LTD
Method and apparatus for encryption of data on storage units using devices inside a storage area network fabric
ActiveUS7533256B2Improve securityOptimizationMultiplex system selection arrangementsUnauthorized memory use protectionStorage area networkNetwork link
The capability to encrypt or compress the traffic over network links, thus improving the security of the link on the performance of the links, and the capability to encrypt / decrypt data stored on the storage devices without requiring specialized hosts or storage devices. In a first embodiment, traffic to be routed over a selected link needing encryption and / or compression is routed to hardware which performs the encryption and / or compression and returned for transmission over the link. A complementary unit at the second end of the link routes the received frames to complementary hardware to perform the decryption and / or decompression. The recovered frames are then routed to the target device in a normal fashion. In a variation of this first embodiment the hardware is developed using an FPGA. This allows simple selection of the desired feature or features present in the switch. The switch can be easily configured to perform encryption, compression or both, allowing great flexibility to a system administrator. In a second embodiment frames can be encrypted by a switch and then provided to the storage device in this encrypted manner. The frames from the storage device are decrypted before provision to the requesting host. By performing the encryption and decryption in the switch, conventional hosts and storage devices can be utilized.
Owner:AVAGO TECH INT SALES PTE LTD
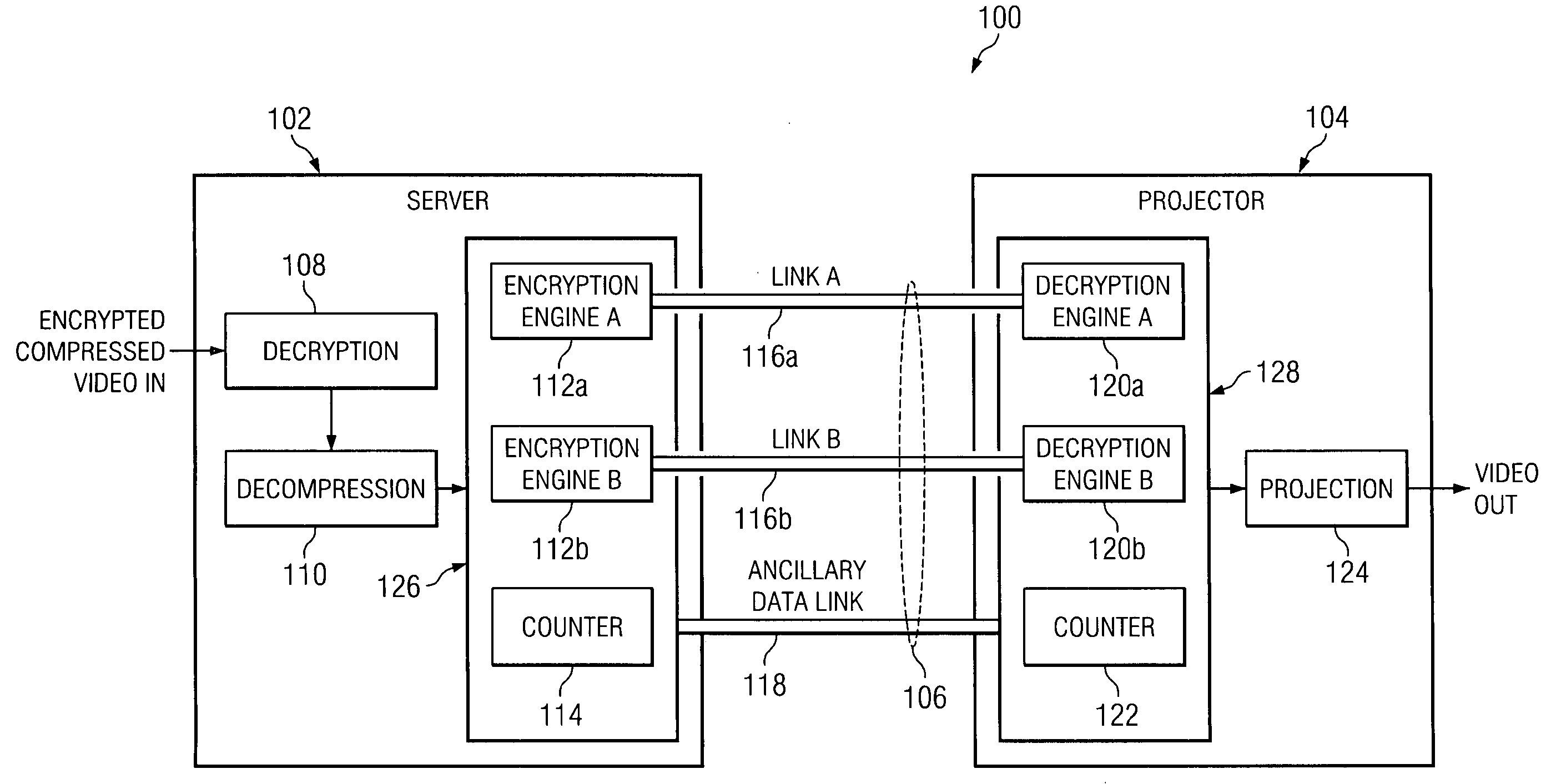
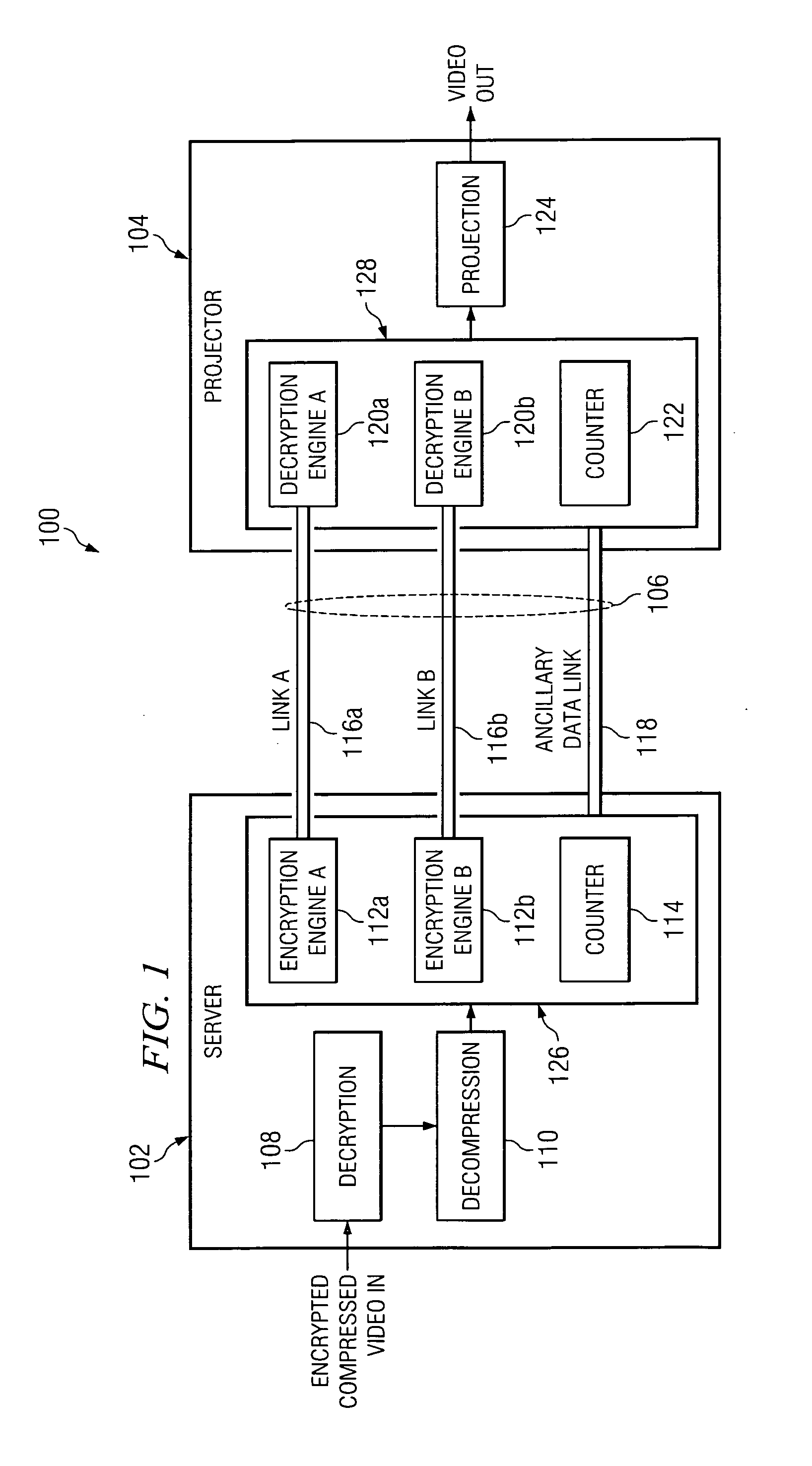
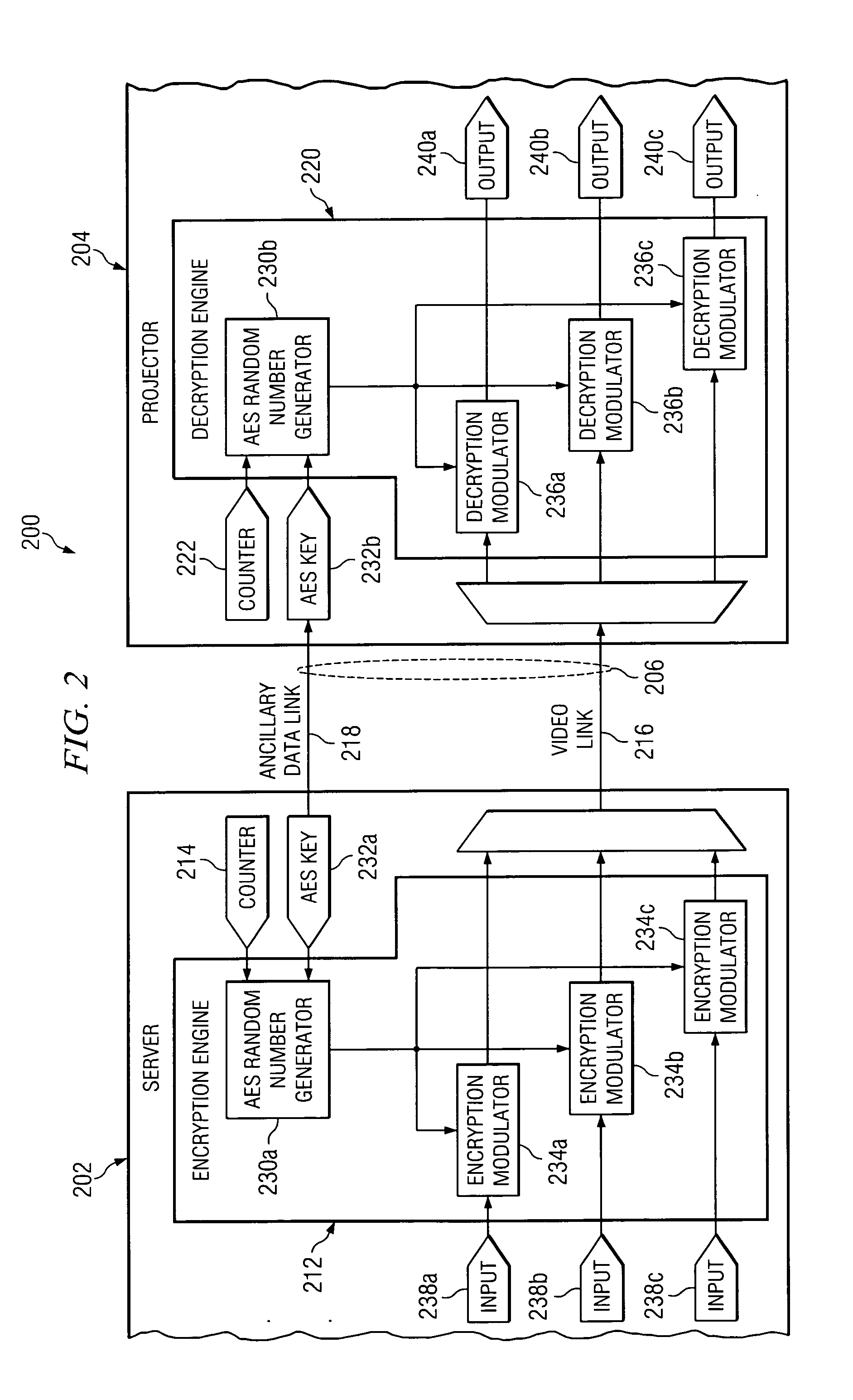
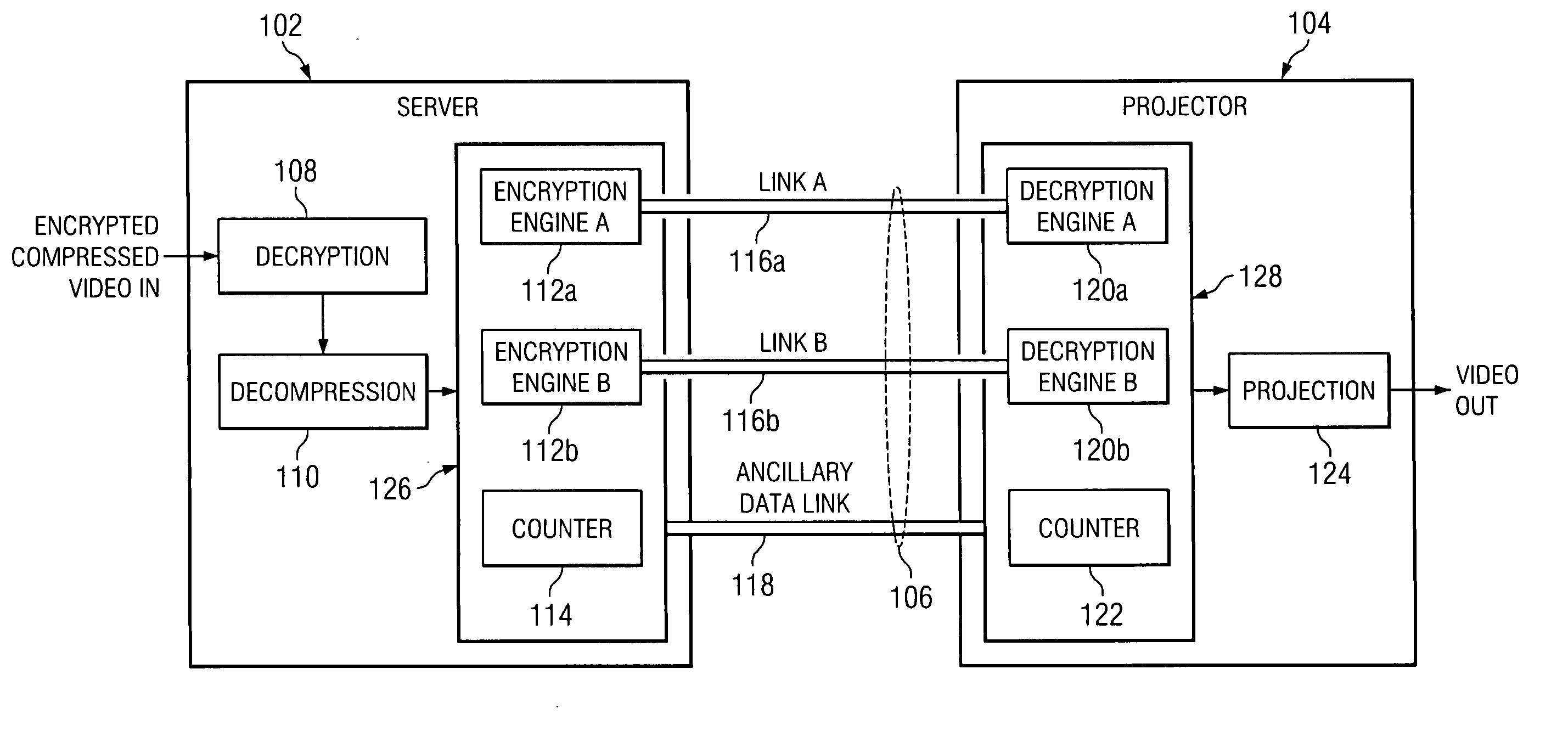
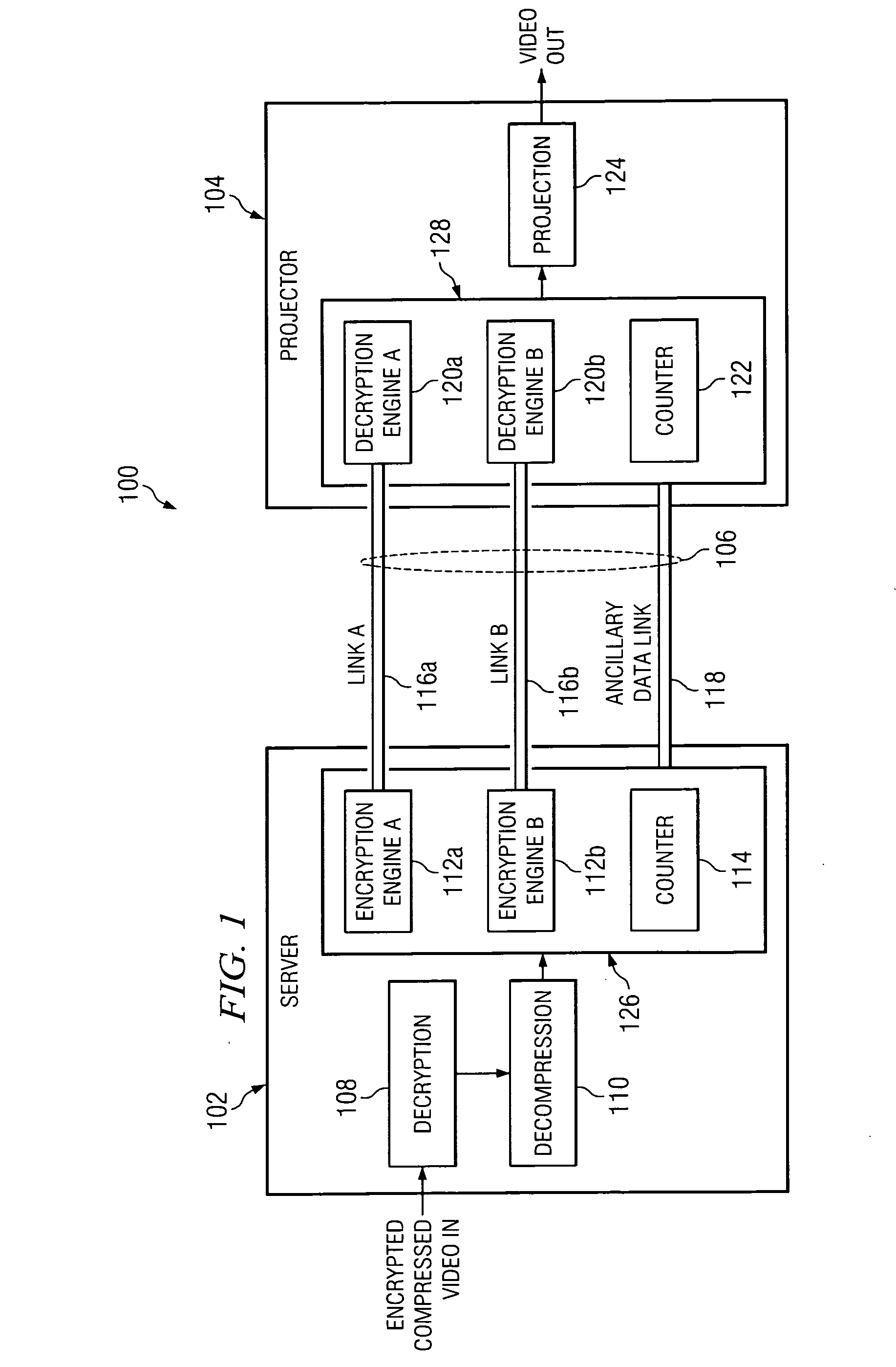
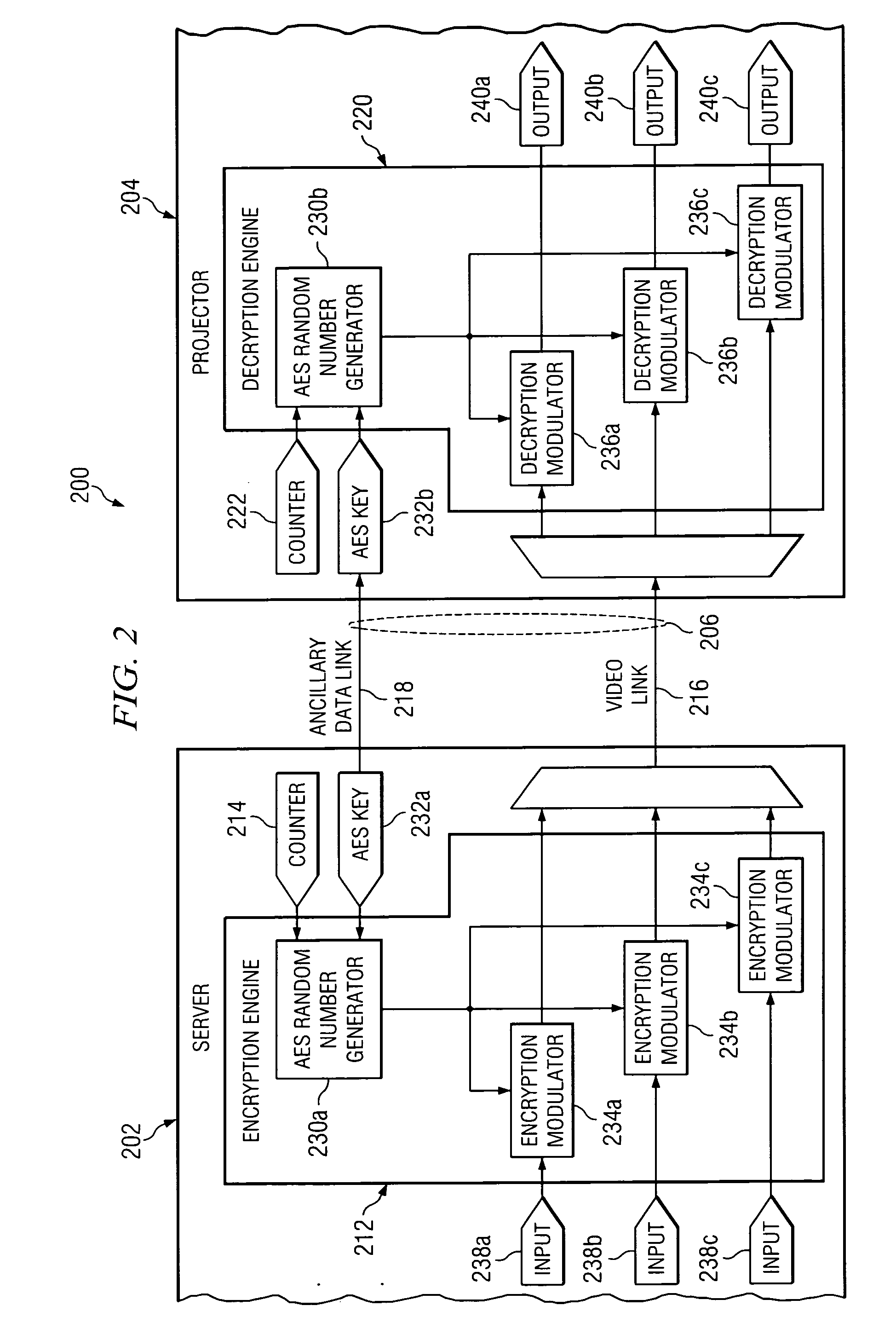
System and method for bit stream compatible local link encryption
ActiveUS20060050883A1Avoid it happening againTelevision systemsSelective content distributionDigital videoLink encryption
In accordance with the teachings of the present invention, a system and method for bit stream compatible local link encryption are provided. In particular embodiments of the present invention, the method includes generating a random number stream using an active line count of a frame of video as an input to a first random number generator in a playback server; encrypting data at the playback server based upon a first deterministic mapping between the first random number stream and the data, wherein the first deterministic mapping prevents the generation of prohibited codes; transporting the encrypted data from the playback server to a digital video projector; generating a second random number stream using the active line count of the frame of video as an input to a second random number generator in the digital video projector; and decrypting the encrypted data at the digital video projector based upon a second deterministic mapping between the second random number stream and the encrypted data.
Owner:TEXAS INSTR INC
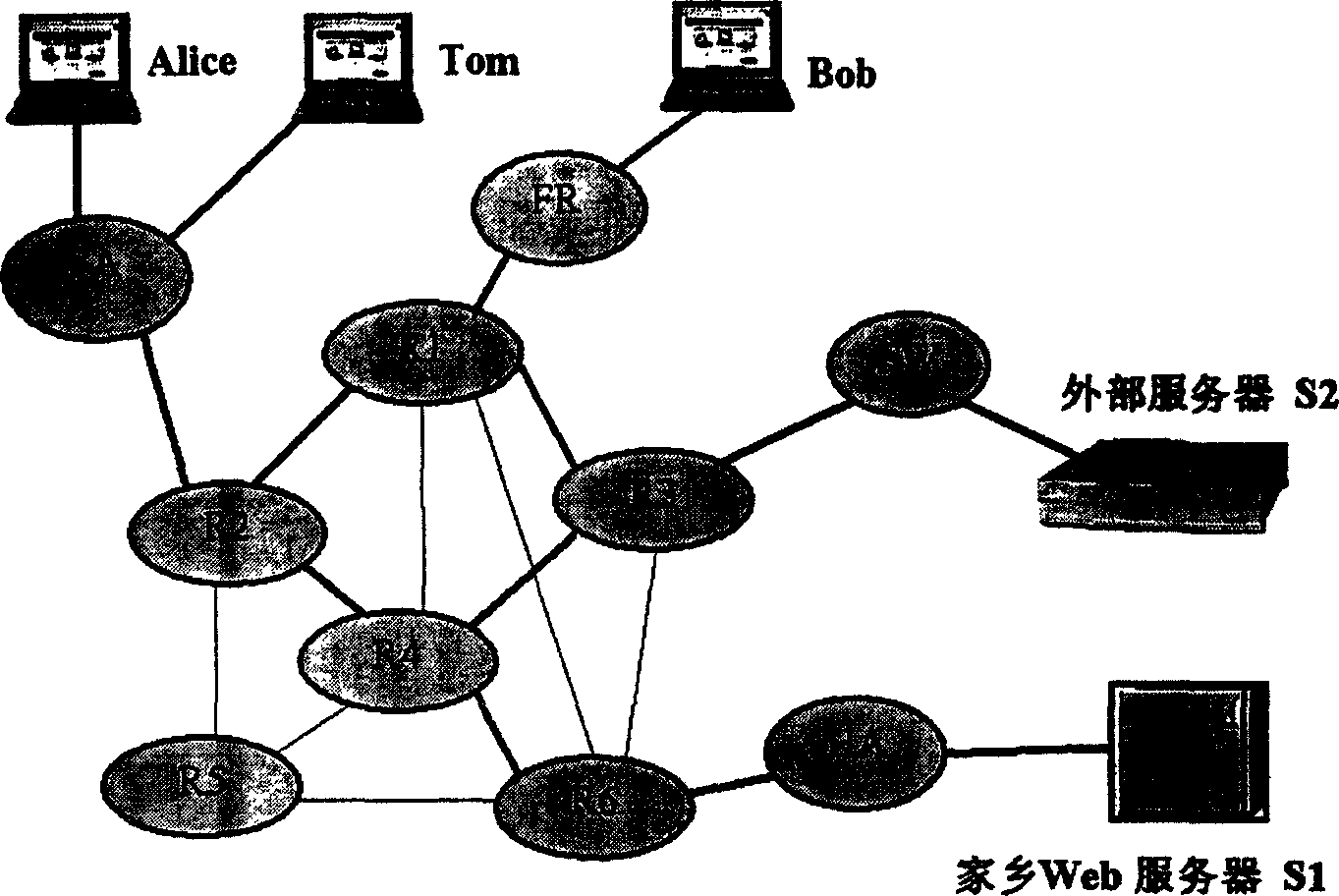
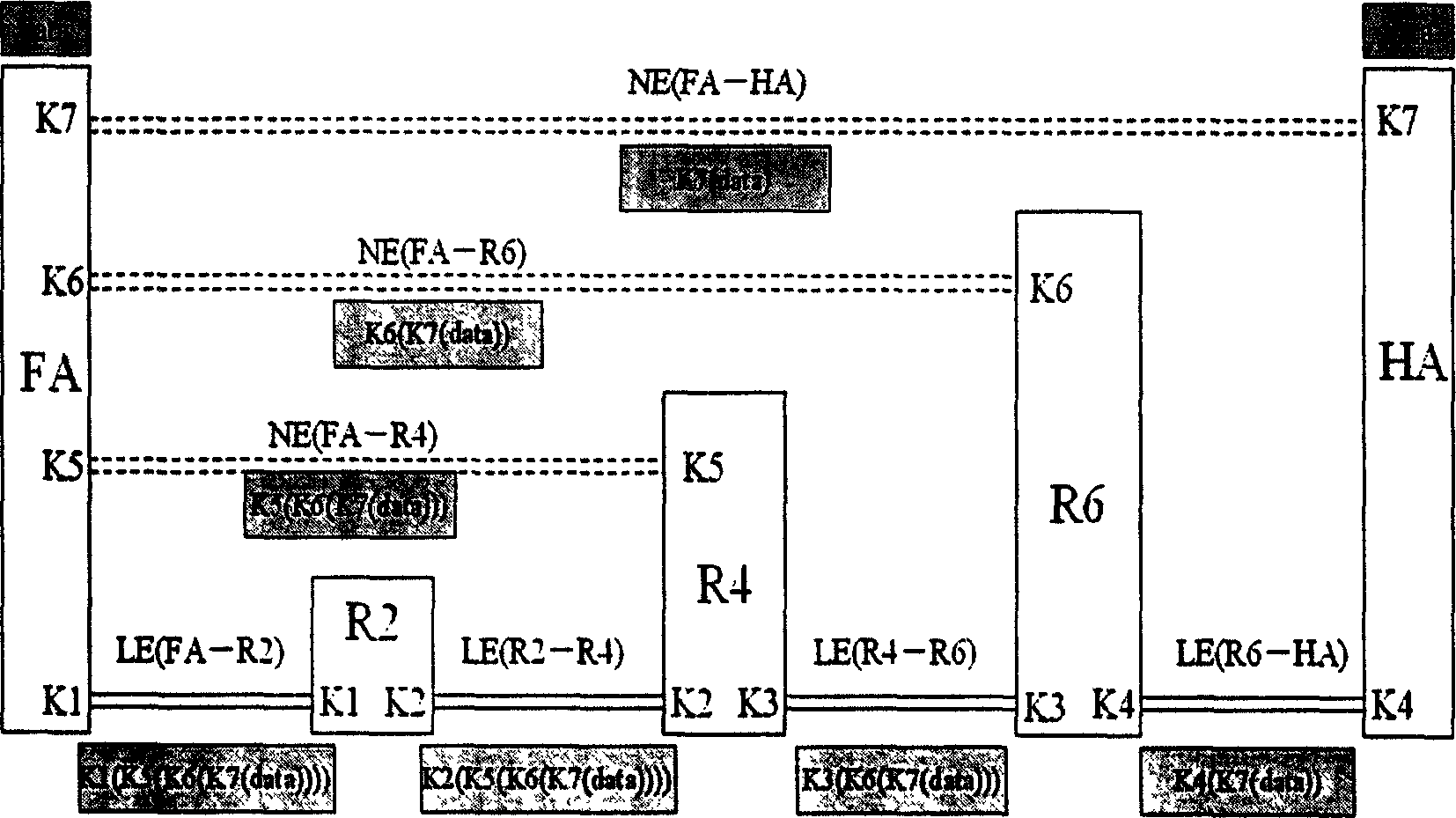
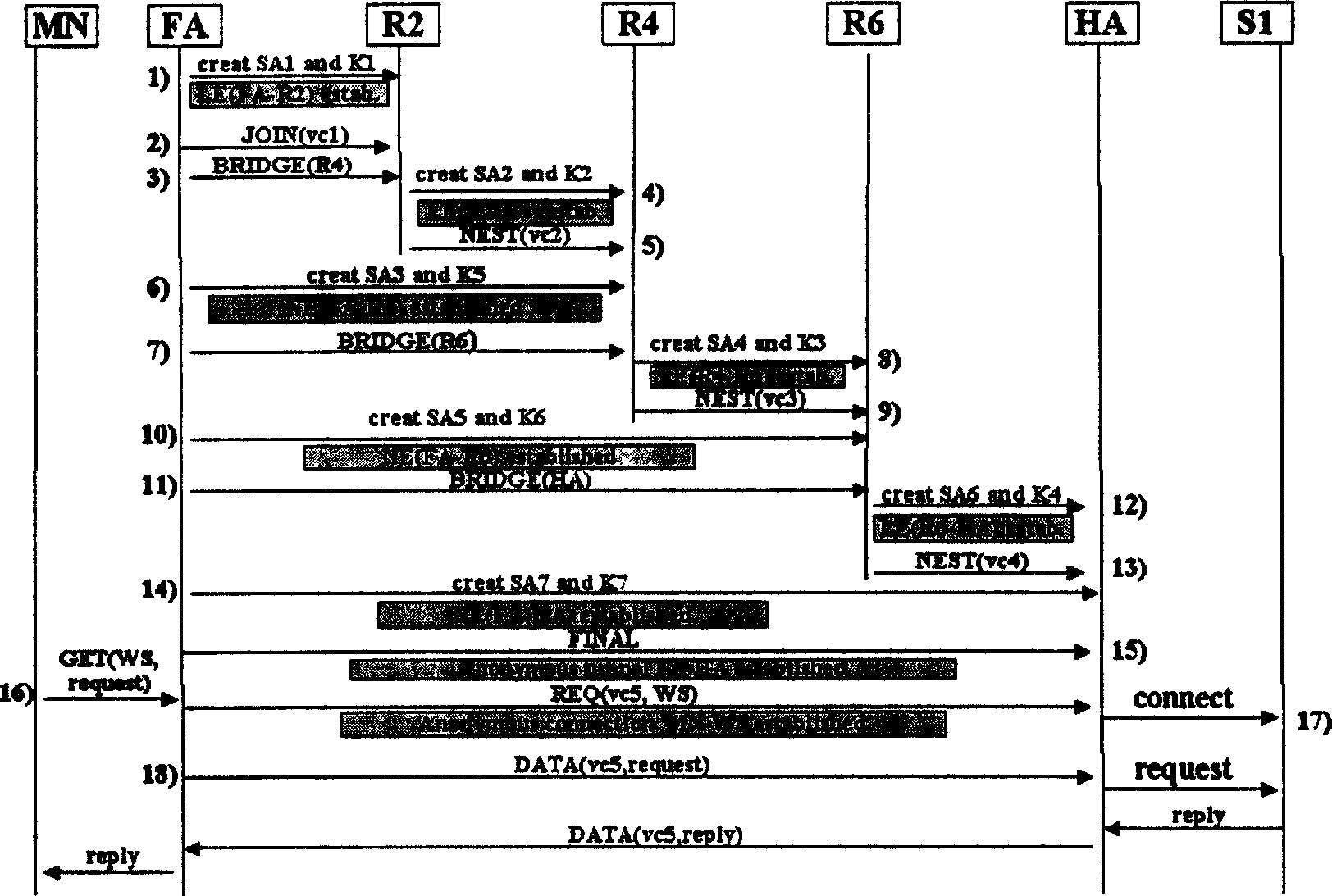
Anonymous connection method of broadband radio IP network
InactiveCN1564508ASave memoryWeak computing powerData switching networksSecuring communicationEncapsulated dataForeign agent
When mobile user logs on network to access host server, foreign agent FA and host agent HA are as network intermediate agent. Anonymity encapsulation method includes following step: selecting anonymous route in network layer, building anonymous connection, carrying out data encapsulation, as well as combination of polygenous network nested anonymous encapsulation and link encryption at intermediate router. Following measures are taken I the invention: encapsulating data packet transmitted, sharing anonymous channel, anonymous connection of distributed type route and anonymous encapsulation etc. The invention optimizes system capability of resisting interior attack to router and exterior attack to physical chain. Advantages are: favorable anonymity, transparency, expansibility and robustness.
Owner:XIDIAN UNIV
System, apparatus and method for providing a virtual network edge and overlay with virtual control plane
ActiveUS20210111998A1Improve communication performanceImprove throughputNetworks interconnectionPathPingNetwork connection
A network system is provided between at least a first client site and a second client site. A client site network component is implemented at least at the first client site, the client site network component aggregating one or more diverse network connections so as to configure an aggregated connection that has increased throughput. At least one network server component may be configured to connect to the client site network component using the aggregated connection. A cloud network controller may be configured to manage the data traffic and a virtual edge providing transparent lower-link encryption for the aggregated connection between the client site network component and the network server component. The network server component includes a virtual control plane interface configured to establish a unicast path between the network server component and each of a plurality of re-mote network server components.
Owner:ADAPTIV NETWORKS INC
System and method for detecting AES random number generator synchronization errors
InactiveUS20060204007A1Number of errorSynchronising transmission/receiving encryption devicesTelevision systemsDigital videoData pack
In accordance with the teachings of the present invention, a system and method for detecting AES random number generator synchronization errors are provided. In particular embodiments of the present invention, the method includes generating a first synchronization word at a playback server, the first synchronization word comprising a 10-bit advanced encryption system word immediately following an advanced encryption system word used to encrypt a final pixel of a final active line of a previous frame of video; placing the first synchronization word in a link encryption metadata message in an ancillary data packet; transmitting the ancillary data packet from the playback server to a digital video projector; extracting the first synchronization word from the link encryption metadata message at the digital video projector; generating a second synchronization word at the digital video projector, the second synchronization word comprising a 10-bit advanced encryption system word immediately following an advanced encryption system word used to decrypt the final pixel of the final active line of the previous frame of video; comparing the first and second synchronization words at the digital video projector; and generating an error message in response to a determination that the first and second synchronization words are not identical.
Owner:TEXAS INSTR INC
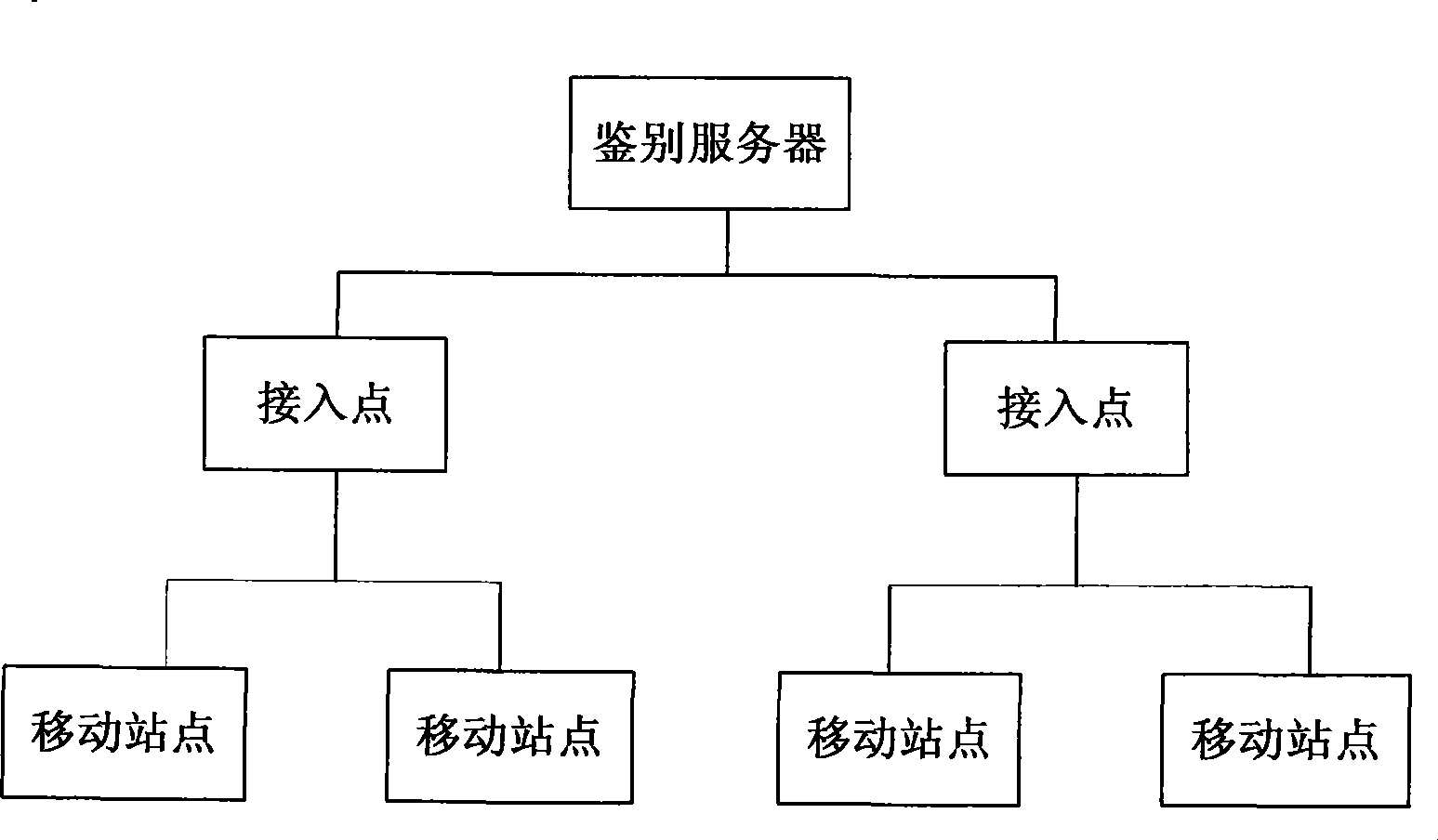
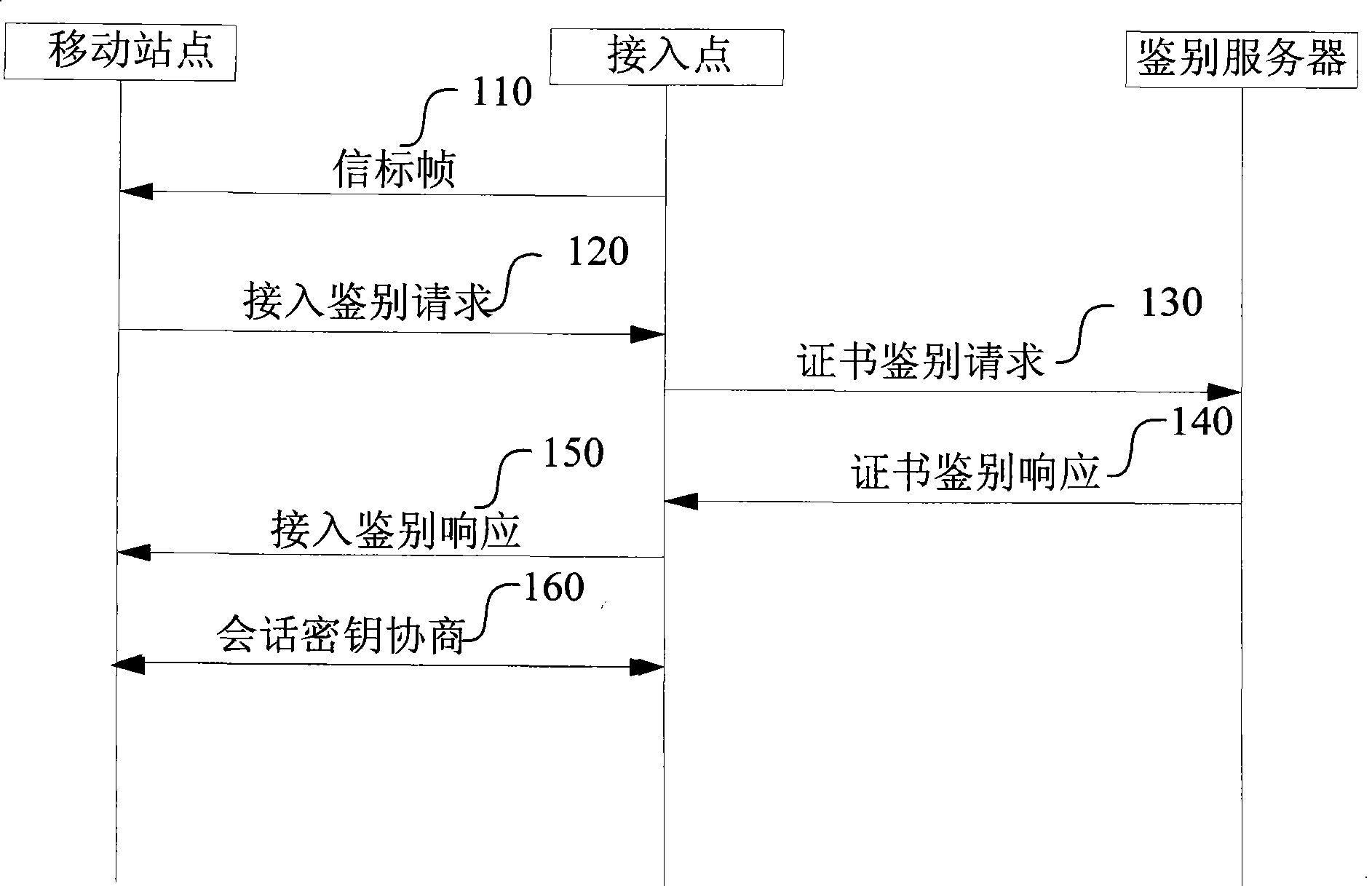
Method and system for assessing wireless local area network
InactiveCN101521881AResolve mutual identificationFix security issuesNetwork traffic/resource managementPublic key for secure communicationElliptic curve Diffie–HellmanCommunication link
The invention provides a method for assessing a wireless local area network, comprising the following steps: a mobile station generates a temporary public key (px) and a temporary private key (sx), and the px and a digital certificate of the mobile station are sent to network side equipment; the network side equipment identifies and recognizes the mobile station and then generates a temporary public key (py) and a temporary private key (sy), and then the network side equipment uses the py and the sy for elliptic curve diffie-hellman (ECDH) calculation so as to generate a key seed and then sends the py to the mobile station; and the mobile station uses the sx and the py for ECDH calculation so as to generate a key seed which is the same as the key seed generated by the network side equipment and then negotiates with the network side equipment by using the key seeds so as to generate a conversation key. The invention also provides a system for assessing the wireless local area network, comprising the mobile station and the network side equipment. The invention combines the advantages of the public key encryption technology and the symmetric key encryption technology and can solve the problems of the identification and the reorganization of both the mobile station and the network side equipment and safety of the encryption of the communication link.
Owner:ZTE CORP
System, apparatus and method for providing aggregation of connections with a secure and trusted virtual network overlay
ActiveUS9929964B2Improve communication performanceImprove throughputBundled link activationNetworks interconnectionPathPingNetwork connection
A network system is provided between at least a first client site and a second client site. A client site network component is implemented at least at the first client site, the client site network component aggregating one or more diverse network connections so as to configure an aggregated connection that has increased throughput. At least one network server component may be configured to connect to the client site network component using the aggregated connection. A cloud network controller may be configured to manage the data traffic and a virtual edge providing transparent lower-link encryption for the aggregated connection between the client site network component and the network server component. The network server component includes a virtual control plane interface configured to establish a unicast path between the network server component and each of a plurality of remote network server components.
Owner:ADAPTIV NETWORKS INC
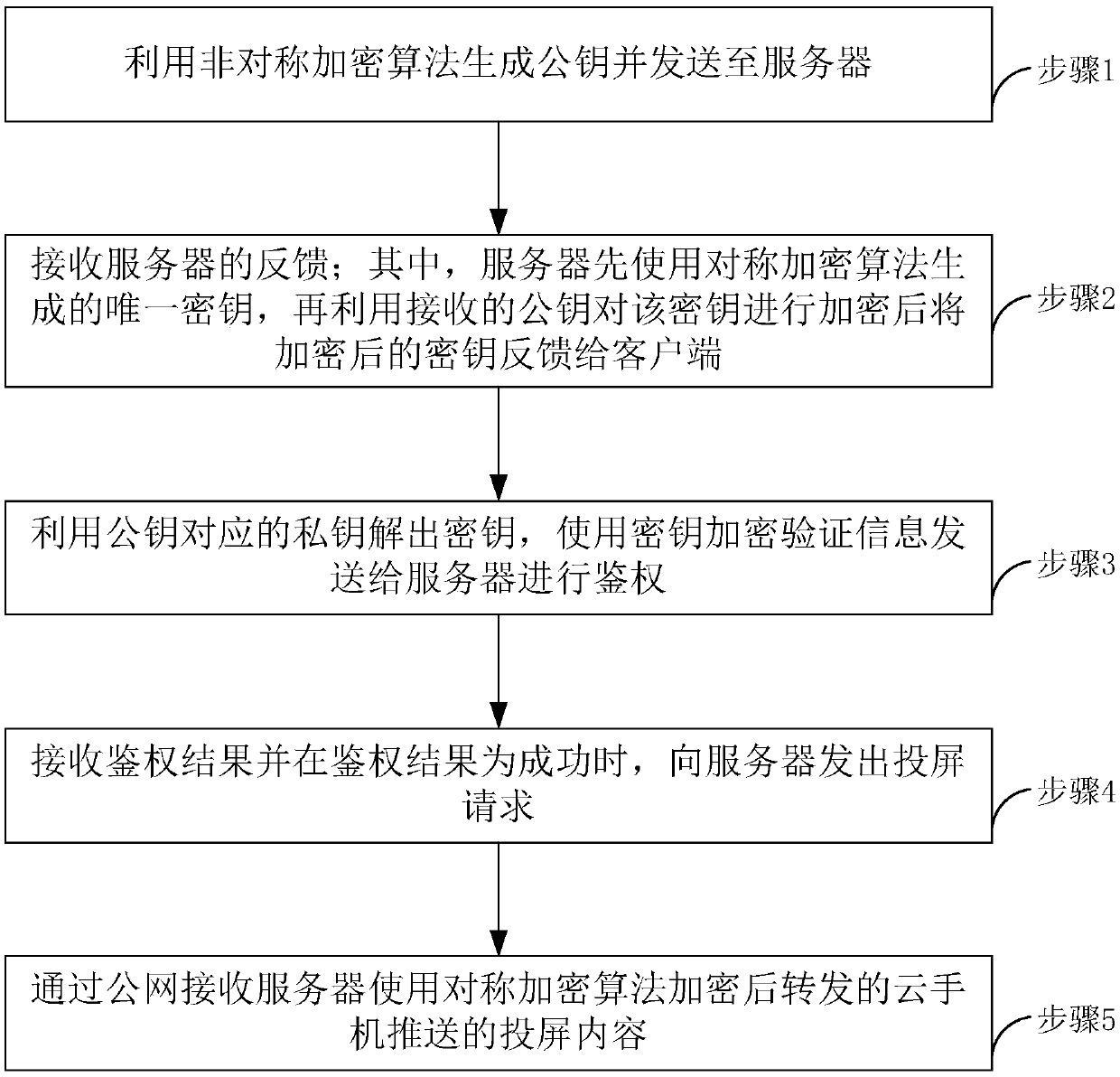
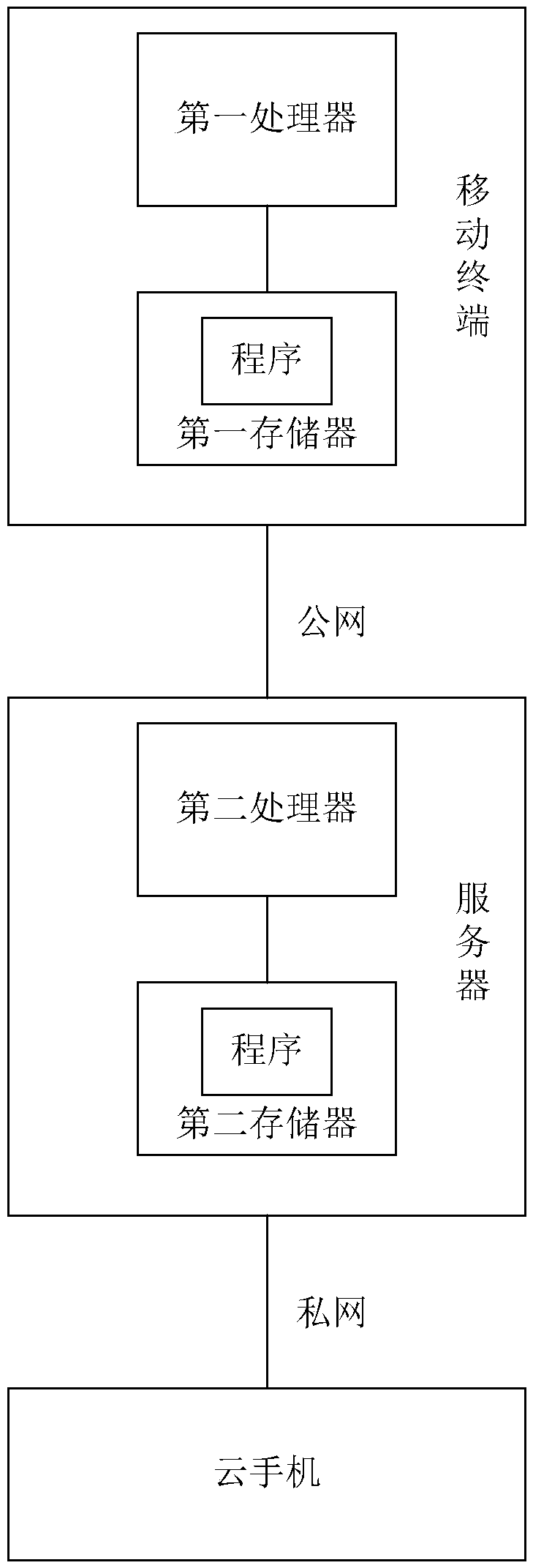
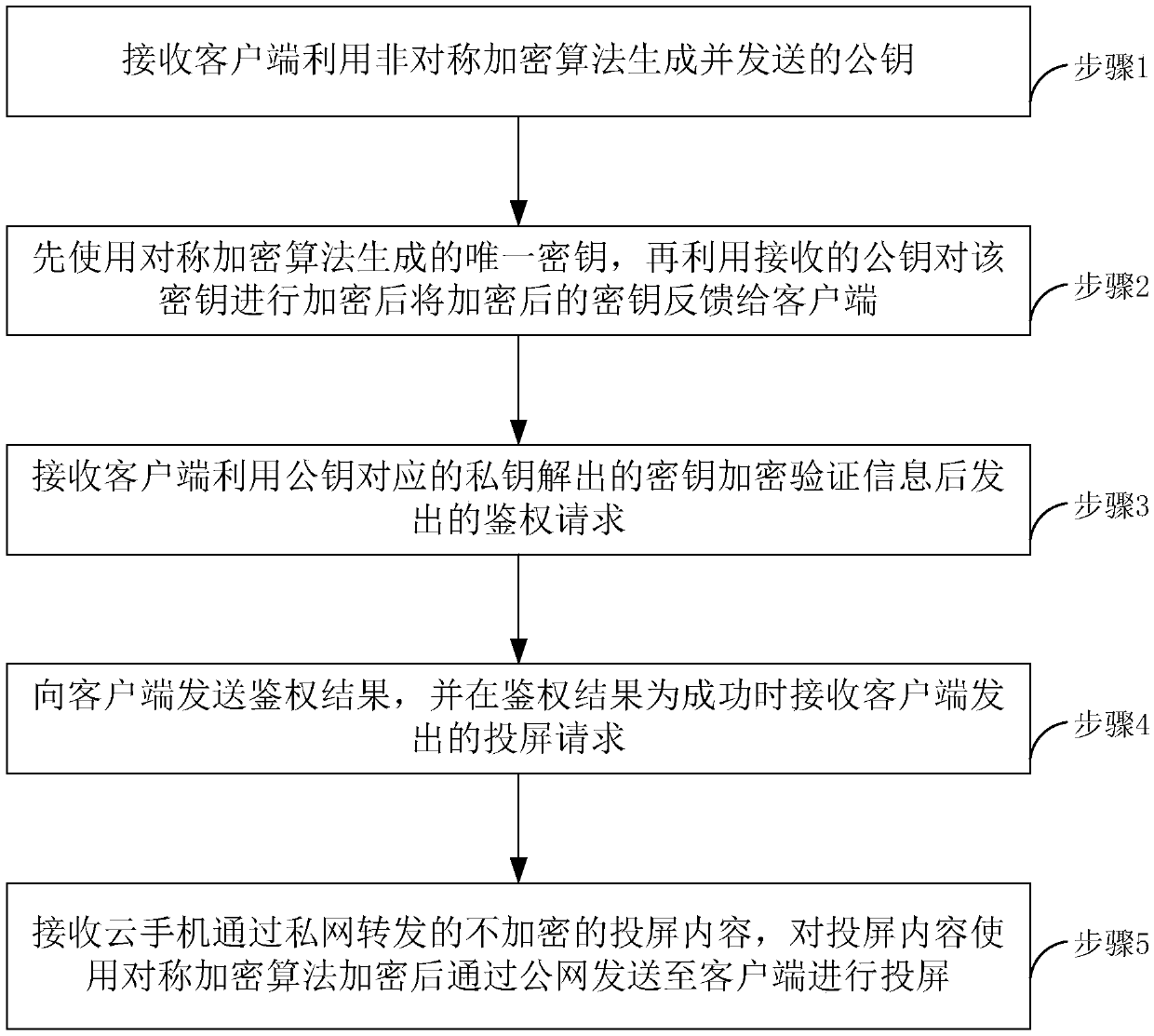
Safe screen projection method of cloud mobile phone, mobile terminal and server
InactiveCN109639697AEnsure safetyTaking into account efficiencyKey distribution for secure communicationMultiple keys/algorithms usagePrivate networkClient-side
The invention relates to the technical field of networks, and relates to a safe screen projection method of a cloud mobile phone, a mobile terminal and a server. The method includes the following steps: generating a public key by using an asymmetric encryption algorithm and sending the public key to the server; receiving feedback from the server, wherein the server firstly uses a symmetric encryption algorithm to generate a unique key, then encrypts the key with the received public key, and then feeds the encrypted key back to the client; decrypting the key by a private key corresponding to the public key, and encrypting verification information by using the key, and sending the verification information to the server for authentication; receiving an authentication result and sending a screen projection request to the server when the authentication result is successful; and using a public network to receive projection content forwarded after being encrypted by the server using the symmetric encryption algorithm and pushed by the cloud mobile phone. The method firstly uses the asymmetric encryption algorithm to realize authentication. After successful authentication, the screen projection is performed and screen projection content transmitted by the private network is not encrypted, while screen projection content transmitted by the public network is encrypted by the symmetric encryption algorithm, so that security is ensured and some links are encrypted with efficiency.
Owner:广州微算互联信息技术有限公司
System, apparatus and method for providing a virtual network edge and overlay
ActiveUS9692713B2Improve communication performanceImprove throughputEnergy efficient ICTFrequency-division multiplex detailsNetworked systemNetwork control
A network system is provided between at least a first client site and a second client site, the first and the second client site are at a distance from one another. A client site network component is implemented at least at the first client site, the client site network component bonding or aggregating one or more diverse network connections so as to configure a bonded / aggregated connection that has increased throughput. At least one network server component may be configured to connect to the client site network component using the bonded / aggregated connection. A cloud network controller may be configured to manage the data traffic and a virtual edge providing transparent lower-link encryption for the bonded / aggregated connection between the client site network component and the network server component.
Owner:ADAPTIV NETWORKS INC
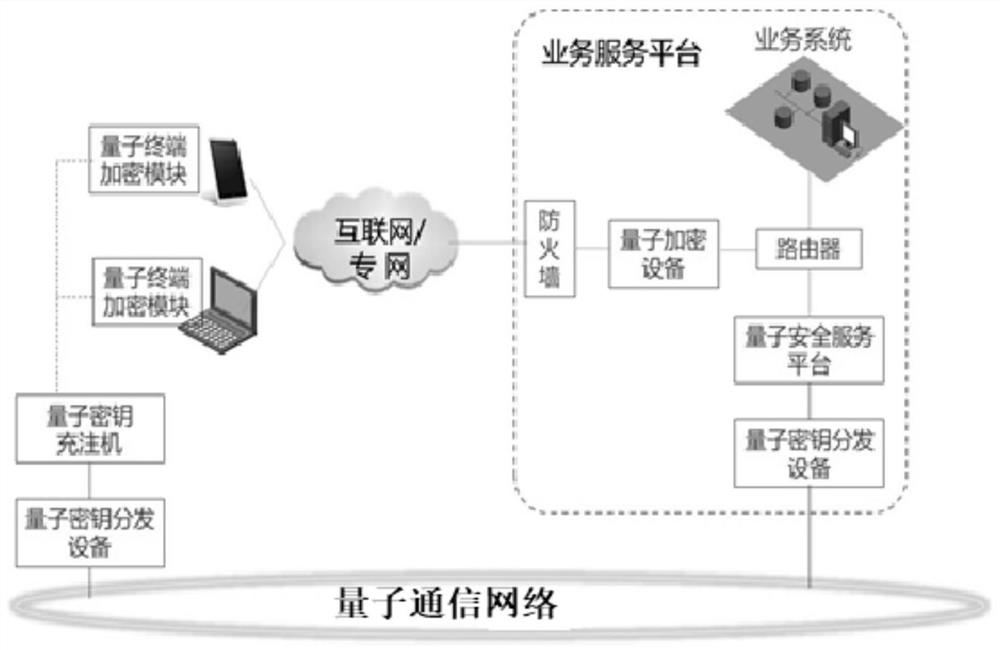
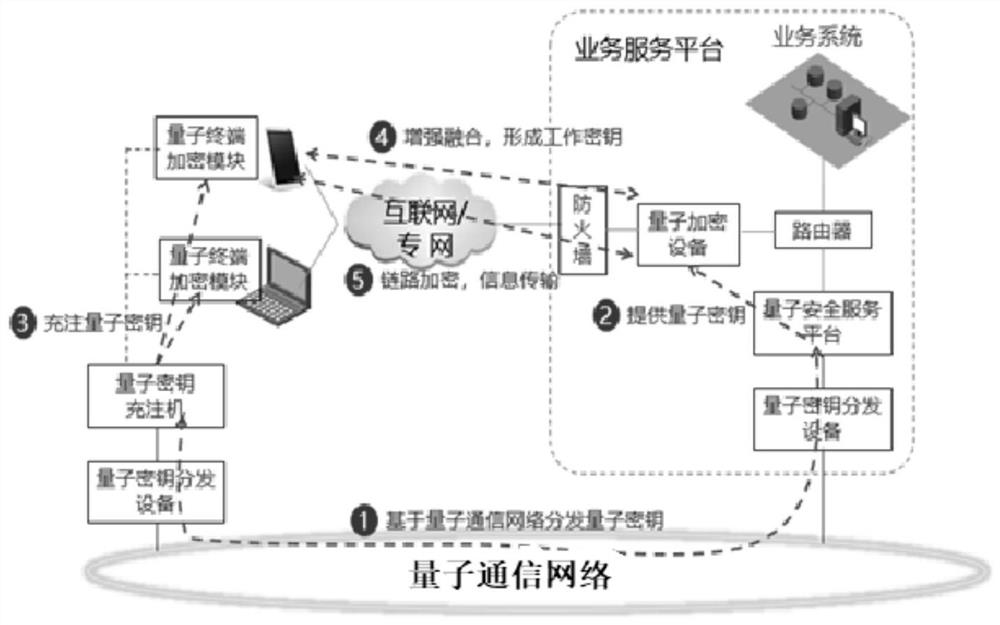
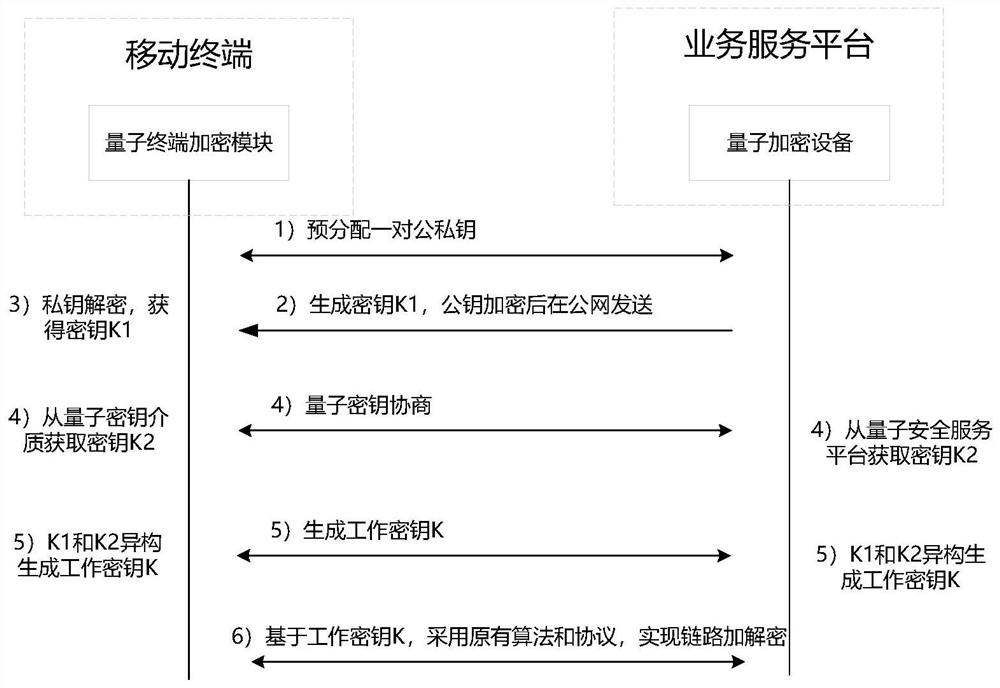
Quantum communication encryption system and method for realizing mobile communication quantum encryption transmission
PendingCN111865589AImprove securityCapable of resisting quantum computingKey distribution for secure communicationHigh level techniquesInformation transmissionLink encryption
The invention provides a quantum communication encryption system for realizing mobile communication quantum encryption transmission and an application method thereof. The quantum communication encryption system comprises a quantum communication network,a quantum key charging machine and quantum key distribution equipment arranged at the quantum key charging machine end, quantum encryption equipment arranged at the service platform end, a quantum security service platform, quantum key distribution equipment arranged at the service platform end, and a quantum terminal encryption module arrangedon the mobile terminal. According to the method, the existing encryption system and process of mobile communication are not changed, the link of information transmission link encryption is not increased, the security of the working key is enhanced, the security of the working key is enhanced and improved by fusing the key distributed by the public and private key system and the key distributed bythe quantum communication technology, and the quantum computing resistance is achieved.
Owner:CAS QUANTUM NETWORK CO LTD
Cinema live-broadcasting authorized management system and method
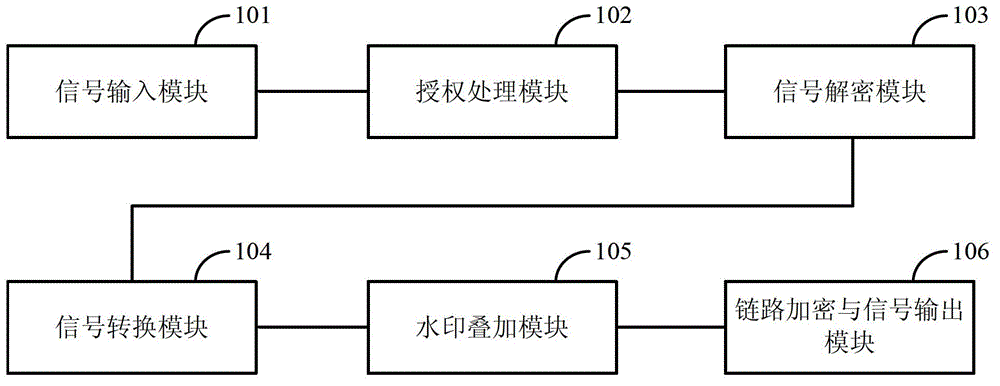
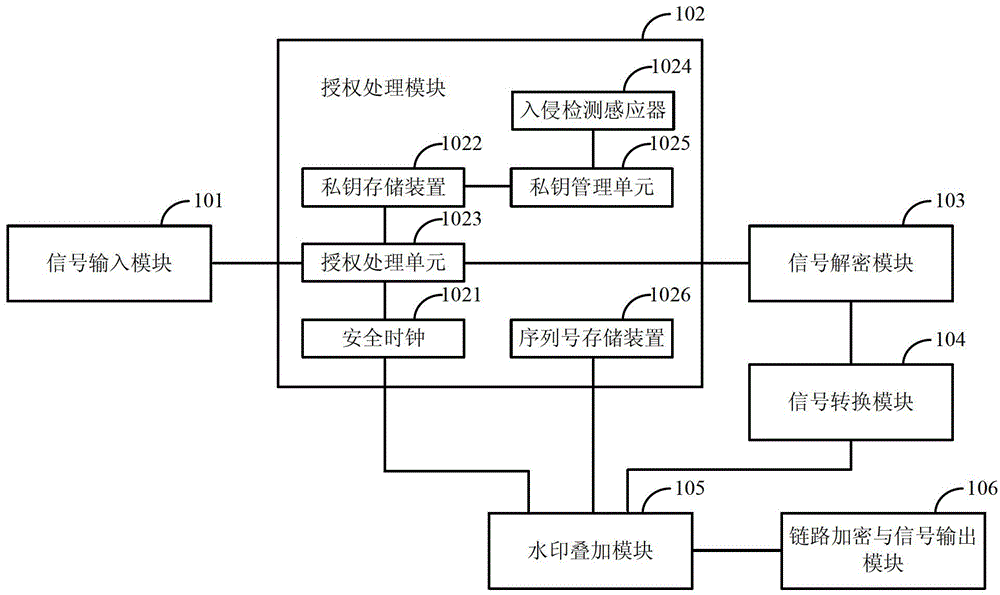
ActiveCN102916812AEffective copyright protectionPublic key for secure communicationUser identity/authority verificationSuperimpositionComputer module
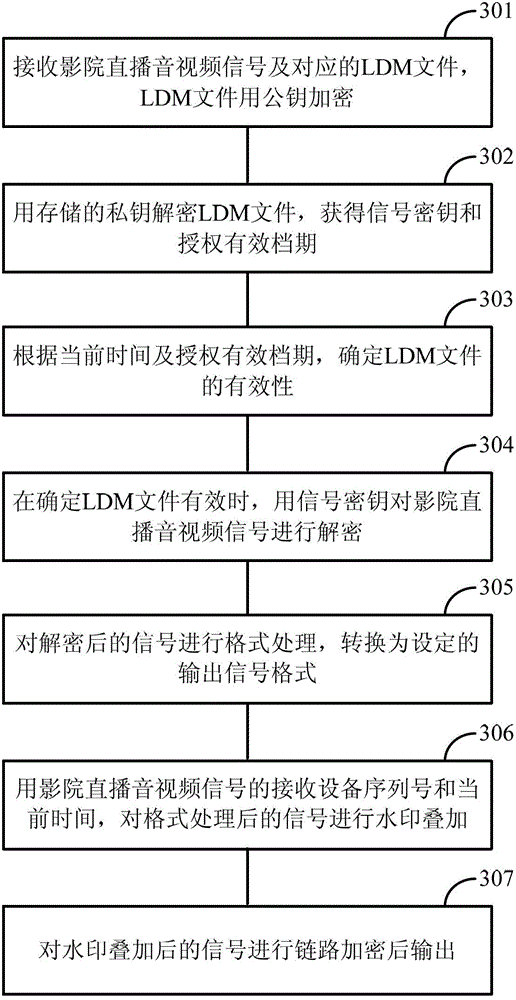
The invention discloses a cinema live-broadcasting authorized management system and method. The cinema live-broadcasting authorized management system comprises a signal input module, an authorization processing module, a signal decryption module, a signal conversion module, a watermark superimposing module and a line encryption and signal output module, wherein the signal input module is used for receiving a cinema live-broadcasting audio-video signal and a corresponding authorized distribution message LDM (Logical Data Model) file, wherein the LDM file is encrypted by a public key; the authorization processing module is used for decrypting the LDM file by using a stored private key to obtain a signal key and an authorization effective schedule and determining the effectiveness of the LDM file according to the current time and the authorization effective schedule; the signal decryption module is used for decrypting the cinema live-broadcasting audio-video signal by using the signal key when the LED file is effective; the signal conversion module is used for carrying out format processing on the decrypted signal and converting the decrypted signal into a set output signal format; the watermark superimposing module is used for carrying out watermark superimposing on the signal subjected to format processing by using the equipment sequence number of the cinema live-broadcasting authorized management system and the current time; and the link encryption and signal output module is used for carrying out link encryption on the signal subjected to watermark superimposition and then outputting the signal subjected to link encryption. The cinema live-broadcasting authorized management system and method disclosed by the invention can realize effective copyright protection on cinema live-broadcasting contents.
Owner:雷欧尼斯(北京)信息技术有限公司
Control method for Bluetooth security management
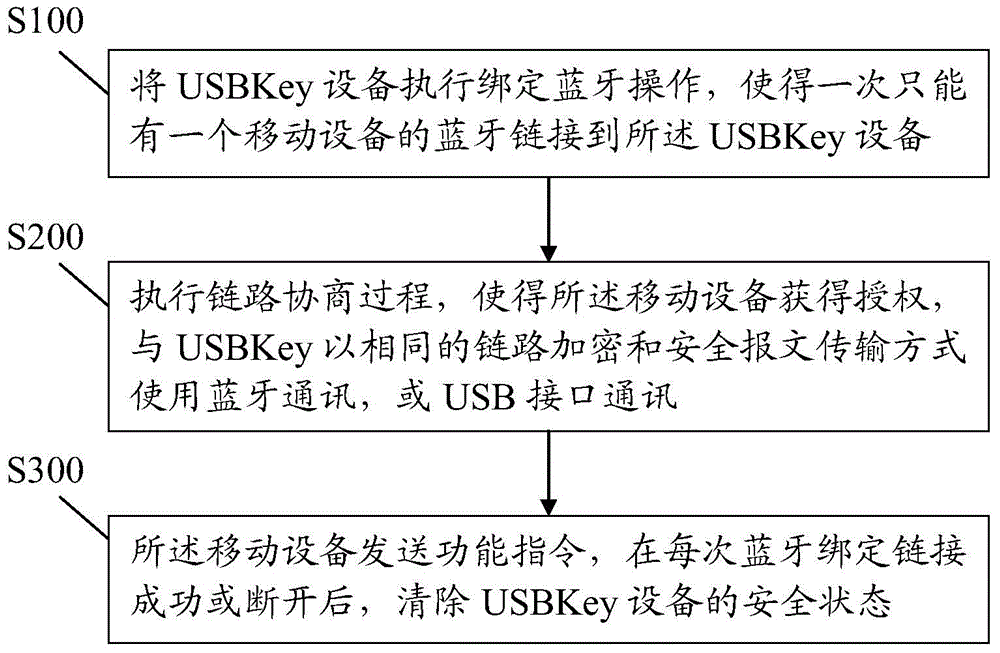
ActiveCN104902476AFix security issuesEasy to implementWireless commuication servicesSecurity arrangementPasswordSecure state
The application discloses a control method for Bluetooth security management. The method comprises the following steps: I, executing Bluetooth binding operation on USBKey equipment in order that the Bluetooth of only one piece of mobile equipment can be linked to the USBKey equipment; II, executing a link negotiation process in order that the mobile equipment acquires authorization, and communicates with USBKey via Bluetooth or a USB (Universal Serial Bus) interface in the same link encryption and security message transmission way; and III, transmitting a function command by the mobile equipment, and clearing the security state of the USBKey equipment after successful connection or disconnection of every Bluetooth binding. The control method has the advantages that an implementation method is simple, and the problems of security matching and credible communication between mobile intelligent equipment and intelligent password equipment is solved through the Bluetooth security management.
Owner:神州融安科技(北京)有限公司
Anti-theft flow device control system and method
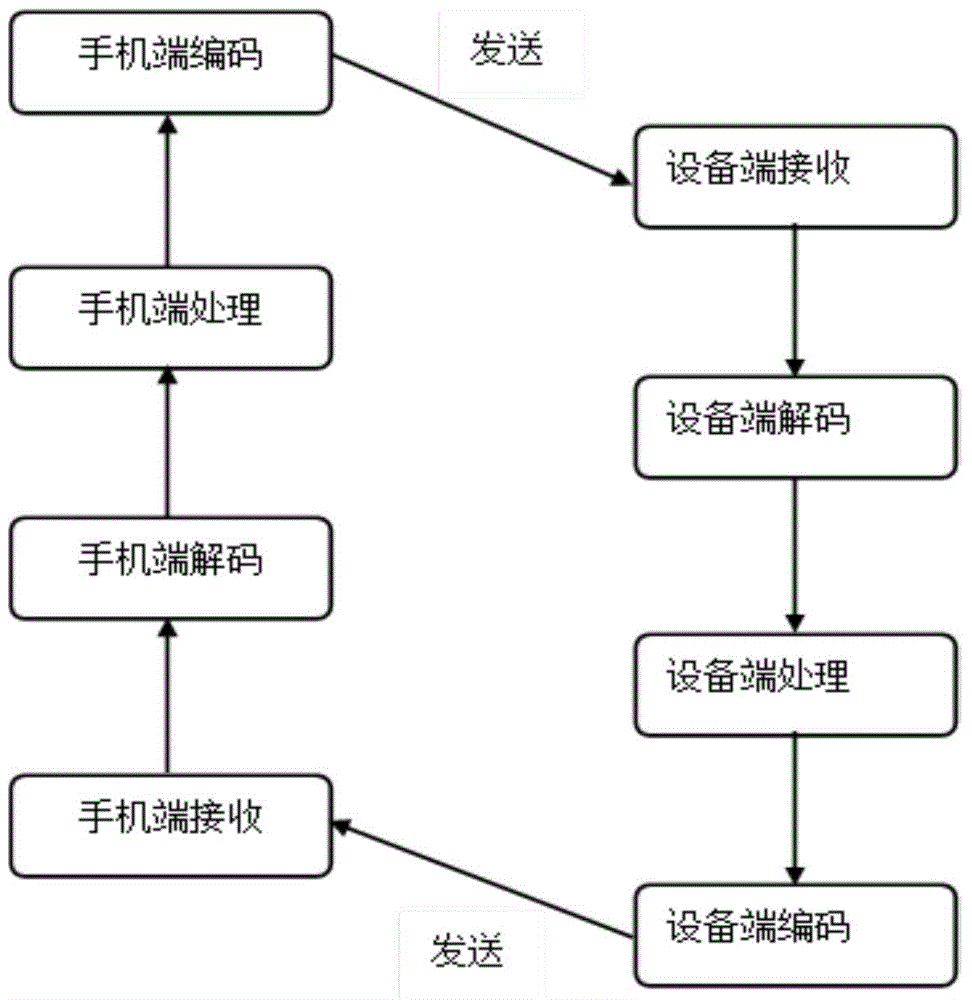
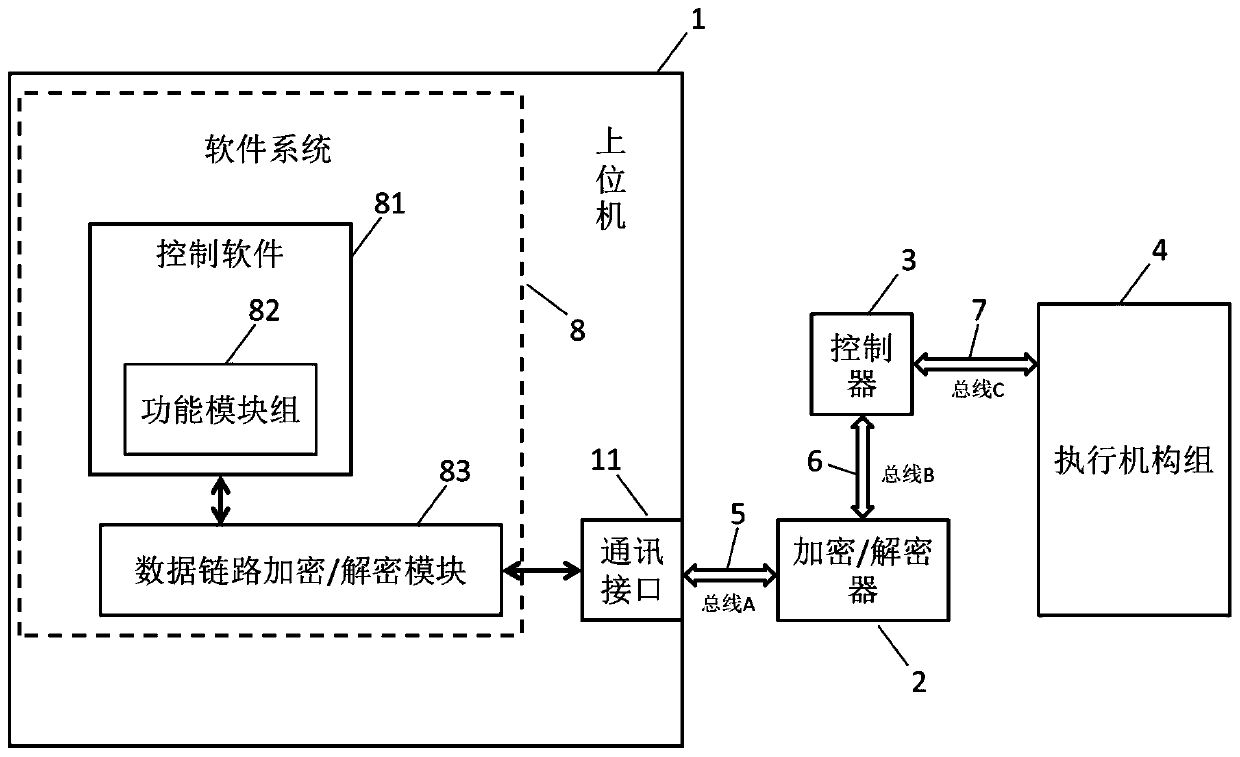
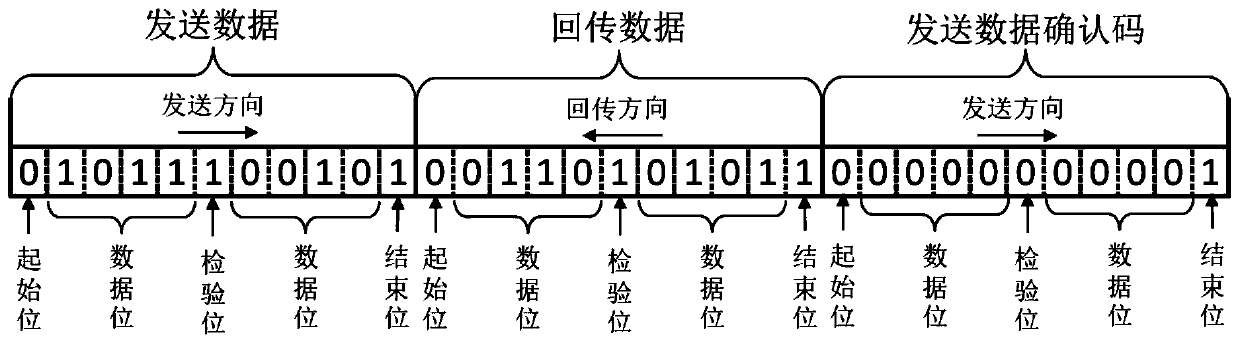
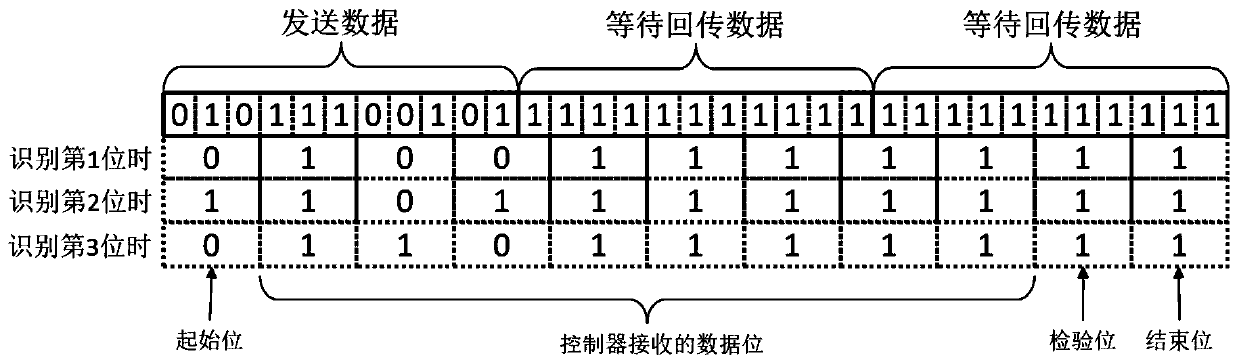
The invention belongs to the technical field of automatic control, and relates to an anti-theft flow device control system and method. The system comprises an upper computer, an encryption / decryptiondevice, a controller, an execution mechanism group, a bus A, a bus B, a bus C and a software system, the software system comprises control software, a function module and a data link encryption / decryption module, and a user can only edit the control software and call the function module and cannot edit the data link encryption / decryption module. Encryption modes of the data link encryption / decryption module and the encryption / decryption device comprise an encryption baud rate, an encryption data frame format and an encryption data transmission protocol. The system can prevent software developers of a flow standard device control system development company from embezzling the control system and protect intellectual properties of the flow standard device control system development company.
Owner:辽宁省计量科学研究院
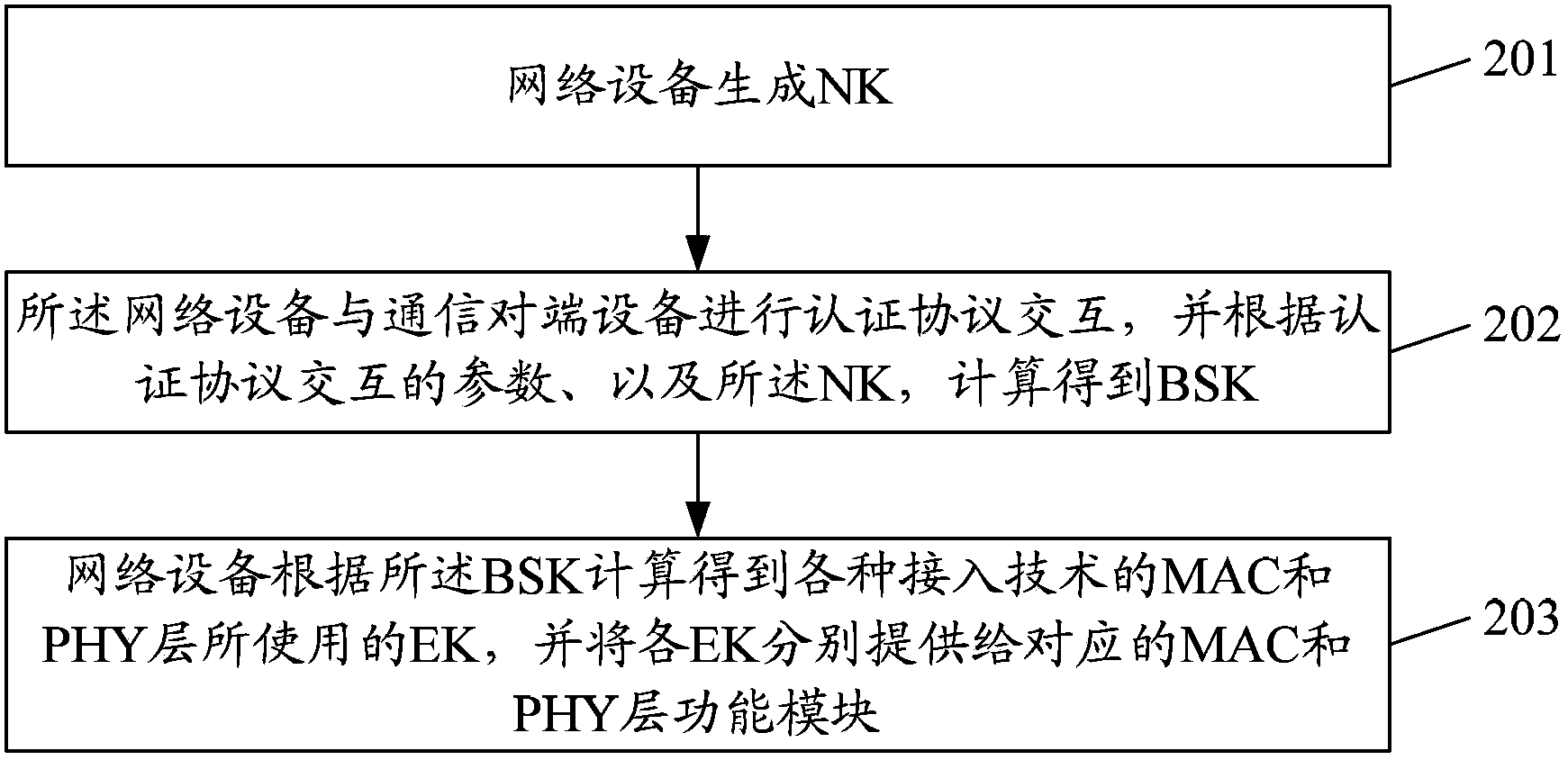
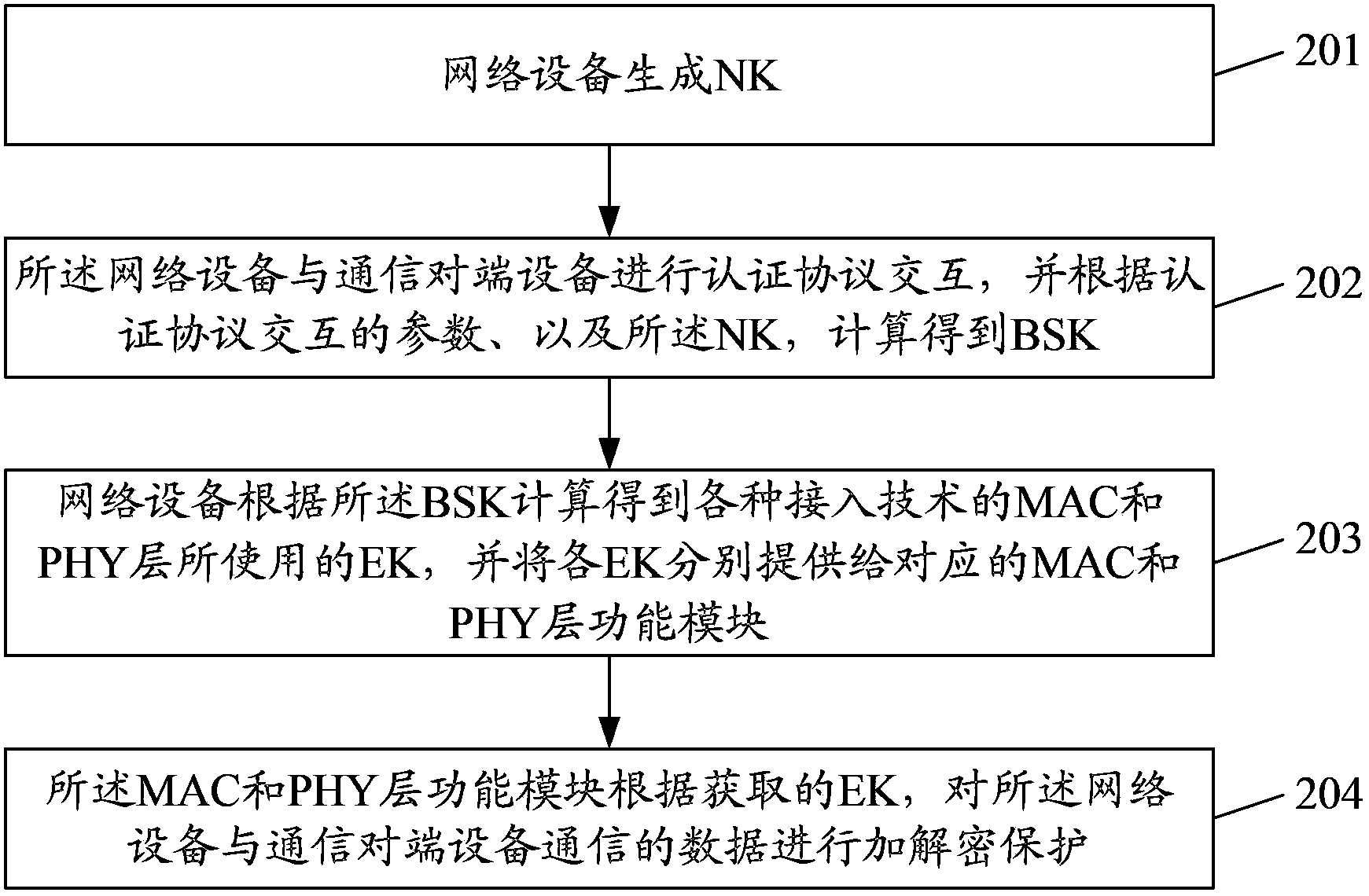
Network device and authentication and key management method thereof
ActiveCN103490887AData encryption and decryption methods remain unchangedAchieve legality certificationKey distribution for secure communicationUser identity/authority verificationNetwork keyHeterogeneous network
The invention discloses a network device and an authentication and key management method of the network device. The method includes the steps that the network device generates a network key (NK); authentication protocol interaction is performed on the network device and a communication opposite end device, and a basic session key (BSK) is obtained through calculation according to parameters of the authentication protocol interaction and the NK; according to the BSK calculation, the network device obtains link encryption keys (EK) used for media access control (MAC) layers and physical layers (PHY) of various access technologies, and all the EKs are provided for corresponding MAC layer functional modules and PHY functional modules respectively. Through the authentication and key management method of the network device, one-time authentication process is performed on the heterogeneous network device to verify the validity of the device, and the effect that uniform key management is performed on the various MAC layer technologies is achieved.
Owner:ZTE CORP
Multiband/Multilink Secure Key Generation and Delivery Protocol
InactiveCN102271128AKey distribution for secure communicationEncryption apparatus with shift registers/memoriesMulti bandMulti link
A method is described for negotiating the use of multi-link ciphering and for the generation of unique keys for each of the links using a single 4-way handshake protocol exchange.
Owner:INTEL CORP
Implementation method of online document cloud storage system
InactiveCN106776953AEasy to useAchieving AdaptivenessDigital data protectionFile/folder operationsPasswordComputer compatibility
The invention relates to the field of webpage front ends, PHP and databases, in particular to an implementation method of an online document cloud storage system. The method includes: configuring a PHP frame (taking codeigniter as an example), using an MVC mode to create five view pages which includes a registration / log-in page, a front page, a search page, a sharing page and an upload page, sequentially creating corresponding controller pages and model pages, and adding a method function uploaded to an appointed directory and a method function sharing a creating password and performing link encryption besides the creating, reading, updating and deleting of a database. By the implementation method applicable to the online document cloud storage system, the online document cloud storage system is convenient to use, high in efficiency, good in practicality and high in compatibility.
Owner:G CLOUD TECH
Safe data transmission method, system and device and storage medium
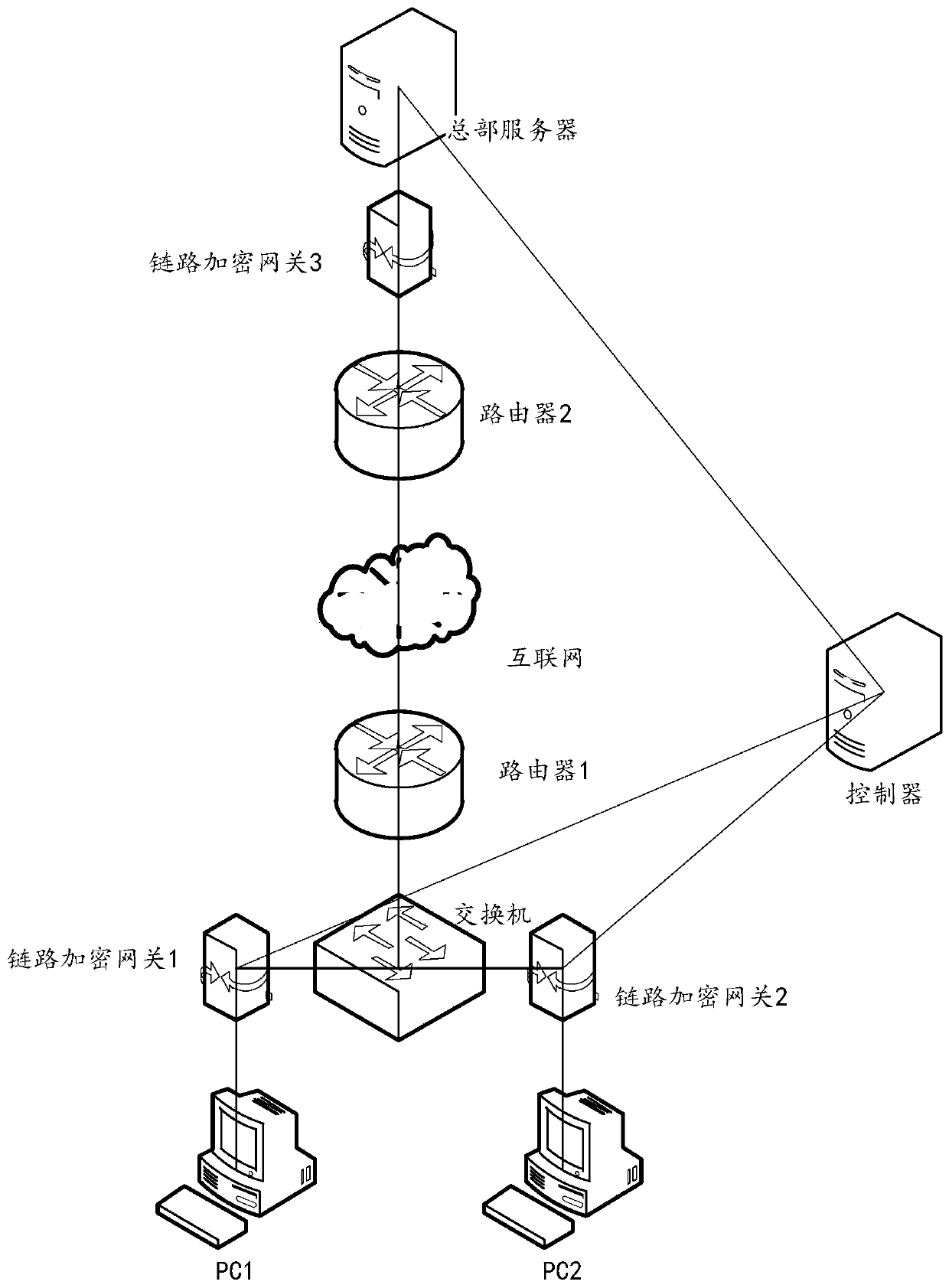
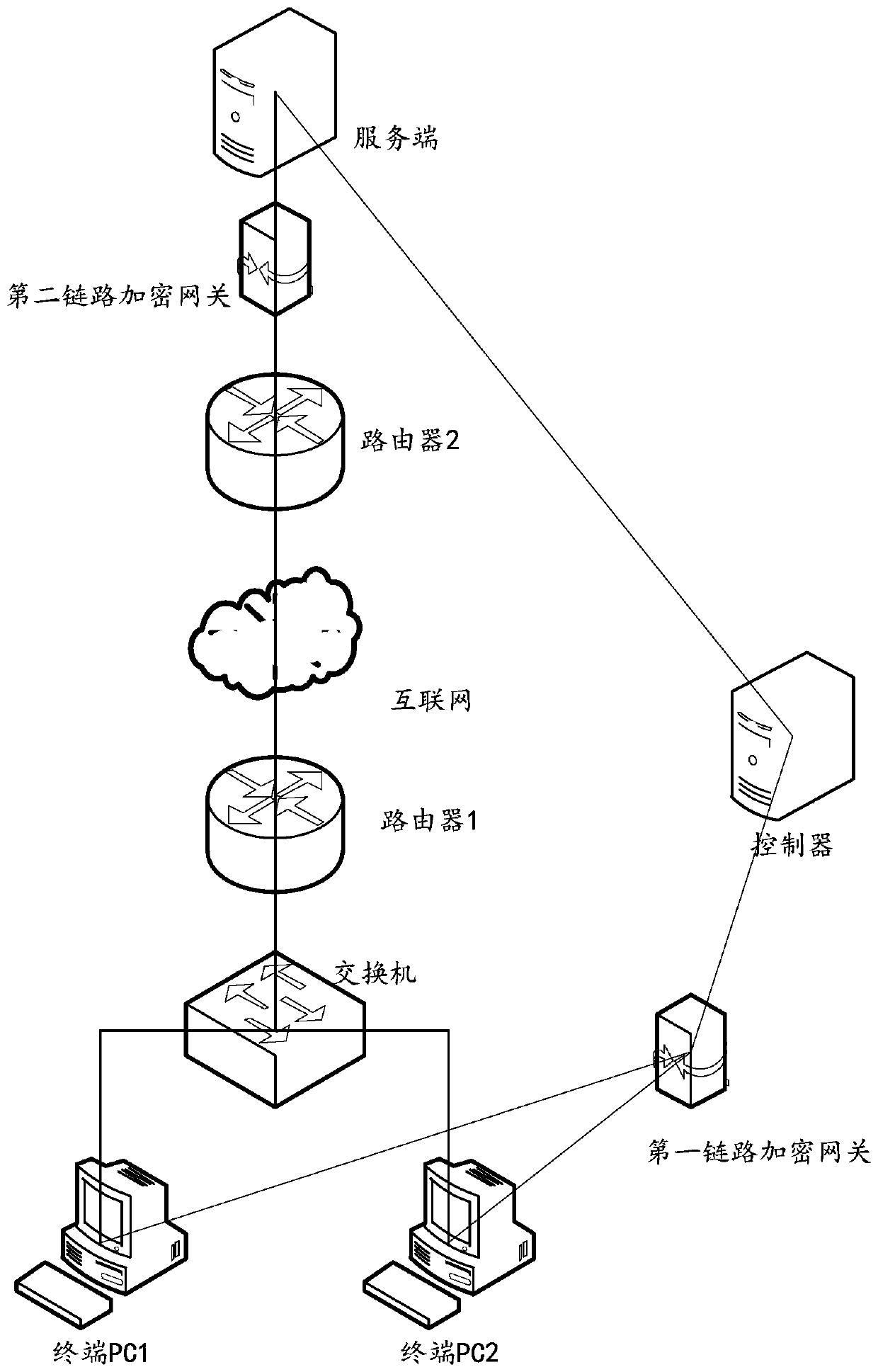
The invention provides a data security transmission method, system and device and a storage medium, and relates to the technical field of network security. The method is applied to a first link encryption gateway in communication connection with one or more terminals, the first link encryption gateway is also in communication connection with a second link encryption gateway, and the method comprises the following steps: receiving a first encrypted message sent by a terminal; determining that the first encrypted message passes the authentication; decrypting the first encrypted message to obtaina first decrypted message; encrypting the first decrypted message based on an encryption mode agreed with a second link encryption gateway to obtain a second encrypted message; and sending the secondencrypted message to a second link encryption gateway through a secure channel between the second encrypted message and the second link encryption gateway, so that the second link encryption gatewaydecrypts the second encrypted message and sends the decrypted second encrypted message to the server. According to the method, a plurality of terminals share one link encryption gateway, and an independent link encryption gateway does not need to be arranged at each terminal, so that the hardware cost is reduced.
Owner:MAIPU COMM TECH CO LTD
System, apparatus and method for providing a unified firewall manager
ActiveUS10785190B2Improve communication performanceImprove throughputData switching networksNetworked systemNetwork control
A network system is provided between at least a first client site and a second client site, the first and the second client site are at a distance from one another. A client site network component is implemented at least at the first client site, the client site network component bonding or aggregating one or more diverse network connections so as to configure a bonded / aggregated connection that has increased throughput. At least one network server component may be configured to connect to the client site network component using the bonded / aggregated connection. A cloud network controller may be configured to manage the data traffic and a virtual edge providing transparent lower-link encryption for the bonded / aggregated connection between the client site network component and the network server component.
Owner:ADAPTIV NETWORKS INC
System, apparatus and method for providing a virtual network edge and overlay with virtual control plane
ActiveUS10904142B2Improve communication performanceImprove throughputNetworks interconnectionPathPingNetwork connection
A network system is provided between at least a first client site and a second client site. A client site network component is implemented at least at the first client site, the client site network component aggregating one or more diverse network connections so as to configure an aggregated connection that has increased throughput. At least one network server component may be configured to connect to the client site network component using the aggregated connection. A cloud network controller may be configured to manage the data traffic and a virtual edge providing transparent lower-link encryption for the aggregated connection between the client site network component and the network server component. The network server component includes a virtual control plane interface configured to establish a unicast path between the network server component and each of a plurality of remote network server components.
Owner:ADAPTIV NETWORKS INC
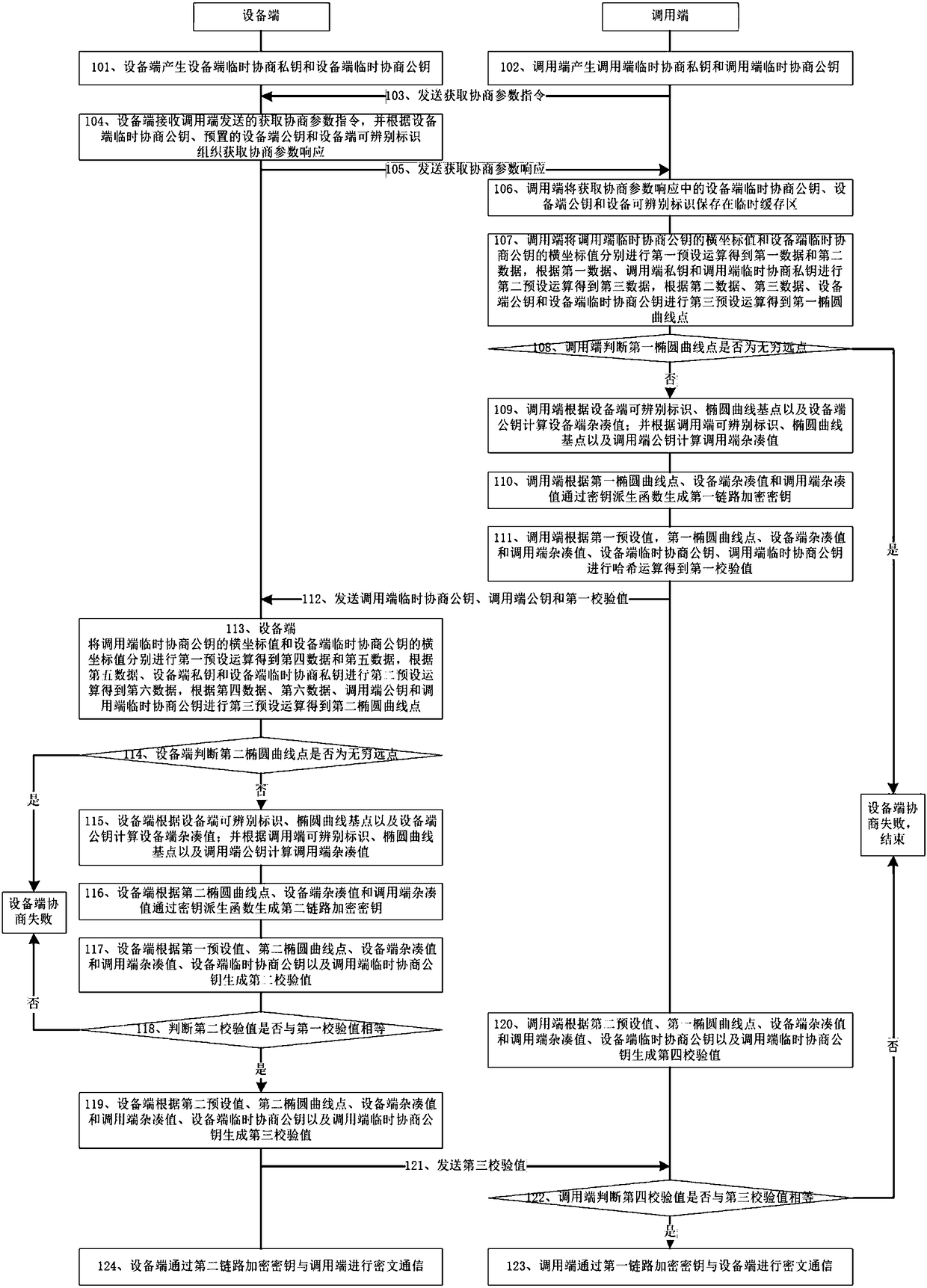
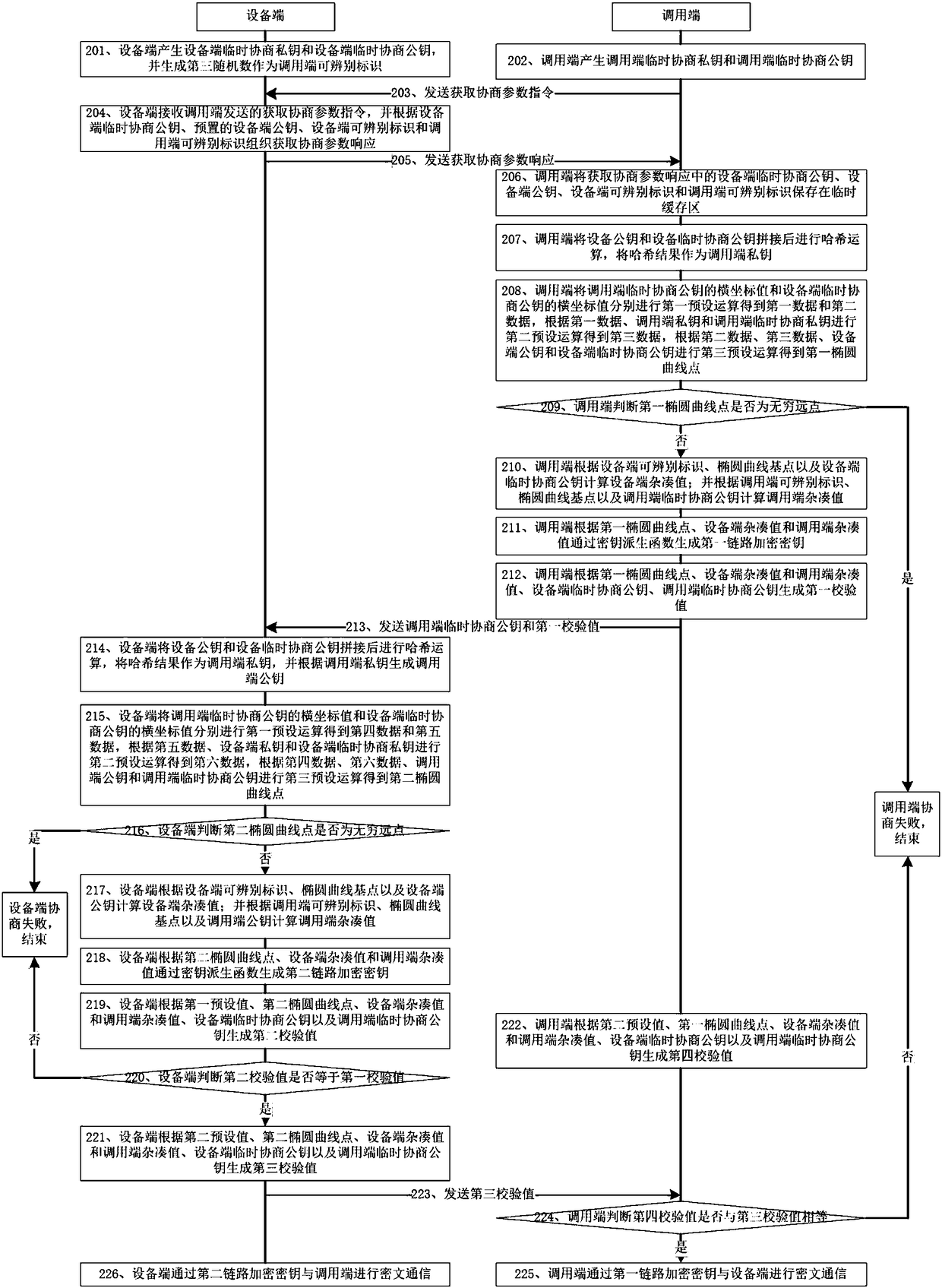
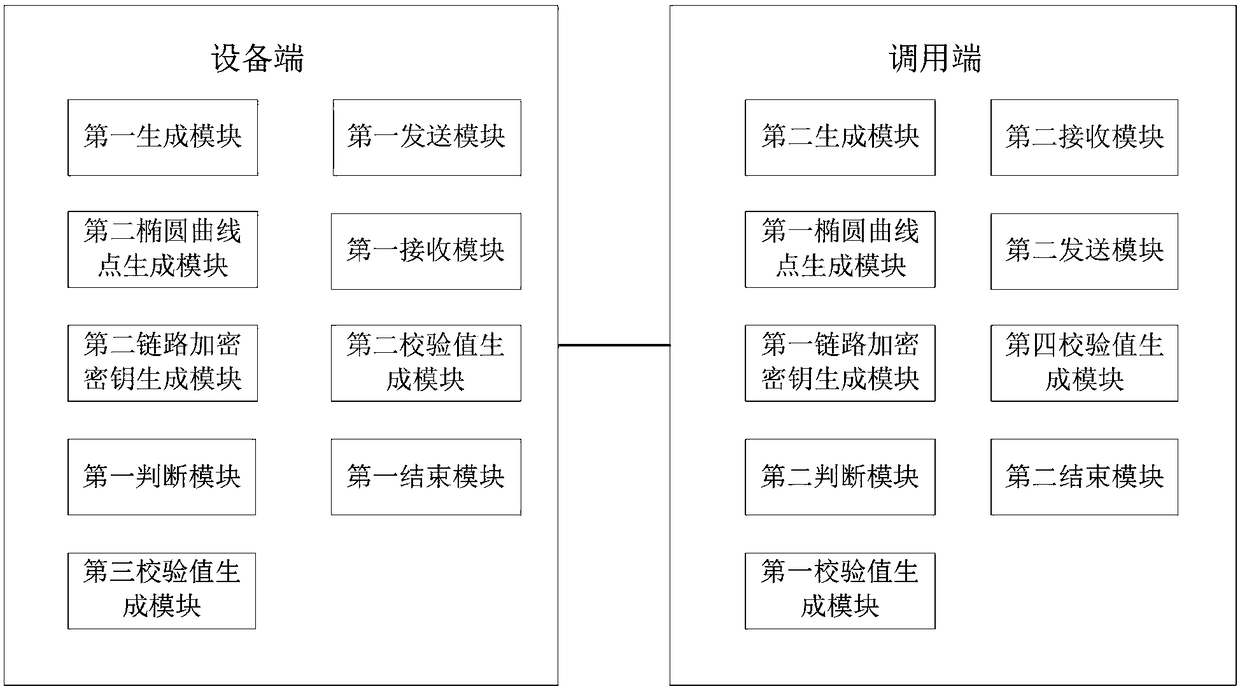
Communication link protection method and device
ActiveCN108306734AImprove securityKey distribution for secure communicationPublic key for secure communicationCommunications securityComputer hardware
The invention relates to the communication field, in particular to a communication link protection method and device. The device comprises an equipment end and a calling end; the equipment end comprises a first generation module, a first sending module, a first receiving module, a second elliptic curve point generation module, a second link encryption key generation module, a second verification value generation module, a first judgment module, a first terminating module and a third verification value generation module; and the calling end comprises a second receiving module, a second generation module, a first elliptic curve point generation module, a first link encryption key generation module, a first verification value generation module, a fourth verification value generation module, asecond judgment module, a second terminating module and a second sending module. According to the device, factors of the calling end takes participate in the link encryption key negotiation process,and therefore the communication security is improved.
Owner:FEITIAN TECHNOLOGIES
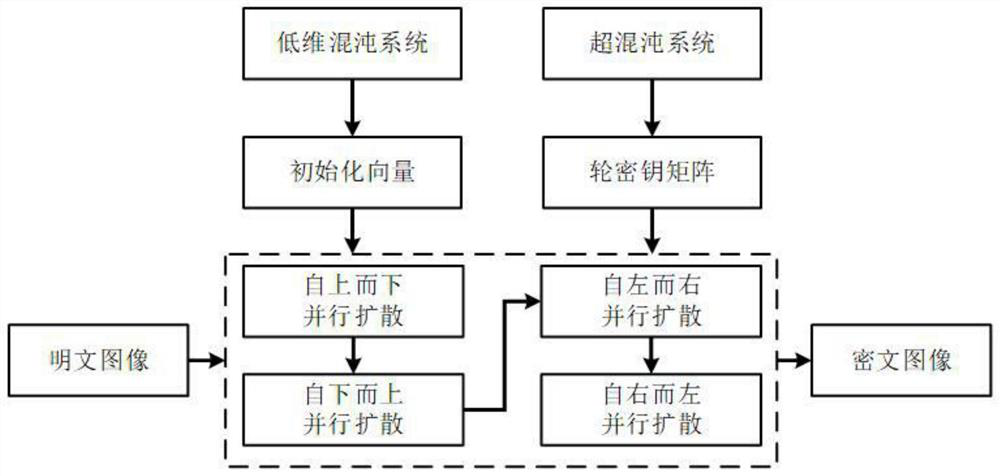
Lightweight hyper-chaotic rapid image encryption algorithm
PendingCN111783116AReduce the number of iterationsFast and fully obfuscatedDigital data protectionPlaintextCiphertext
The invention provides a lightweight hyper-chaotic rapid image encryption algorithm, which comprises the following steps of: firstly, quantitatively arranging a hyper-chaotic system, and rapidly generating four round key matrixes with the same size as an image; and then, on a plaintext image, completing efficient diffusion of pixel information through parallel block link encryption in four directions, and generating a ciphertext image with almost no correlation. According to the method, common cryptographic attack means such as statistical analysis attacks, plaintext (ciphertext) attacks and exhaustion attacks can be effectively resisted, the overall time complexity is only linear order O (M + N), and the method has higher practical value in occasions such as large-data-volume real-time image secret communication.
Owner:NANTONG VOCATIONAL COLLEGE
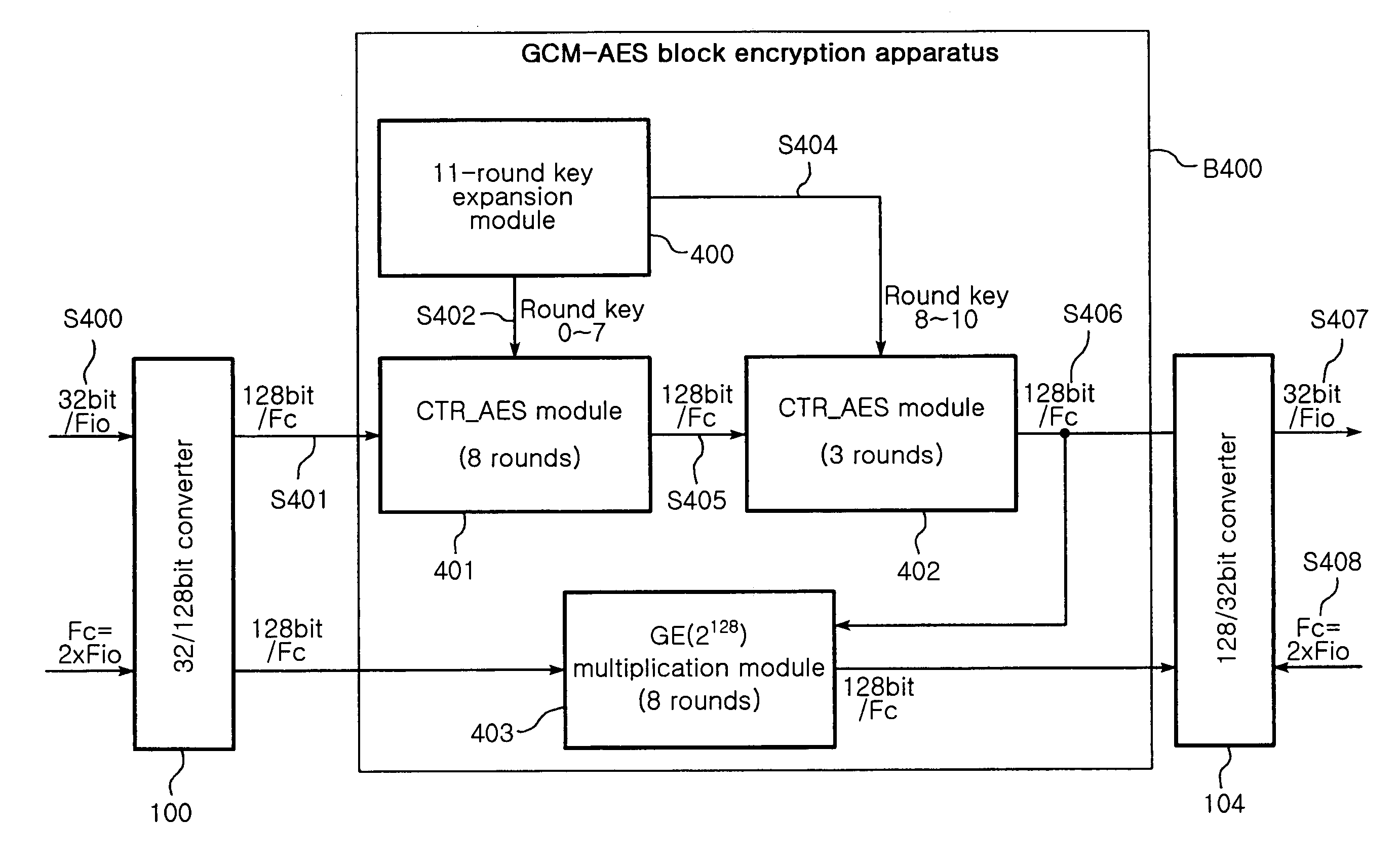
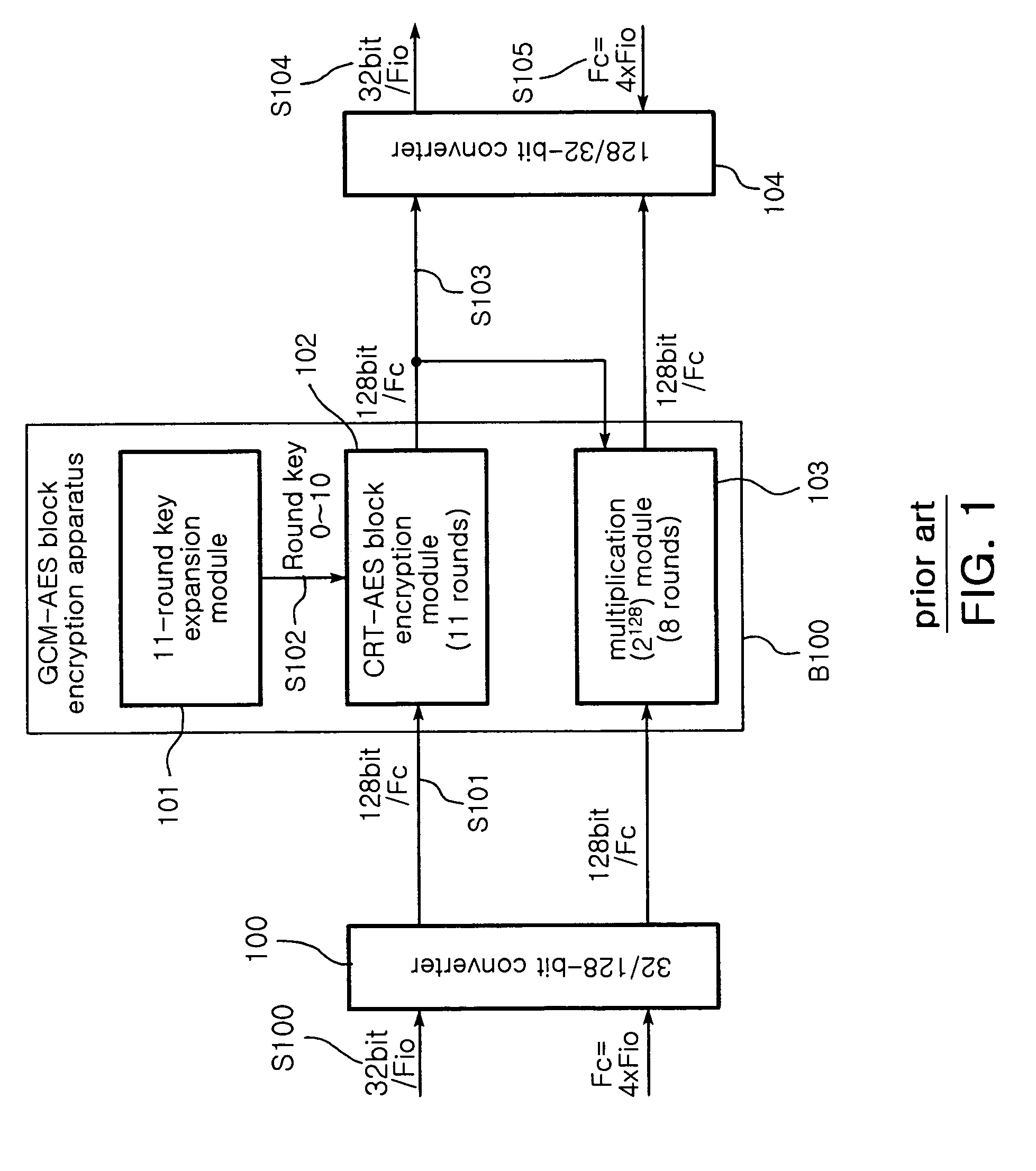
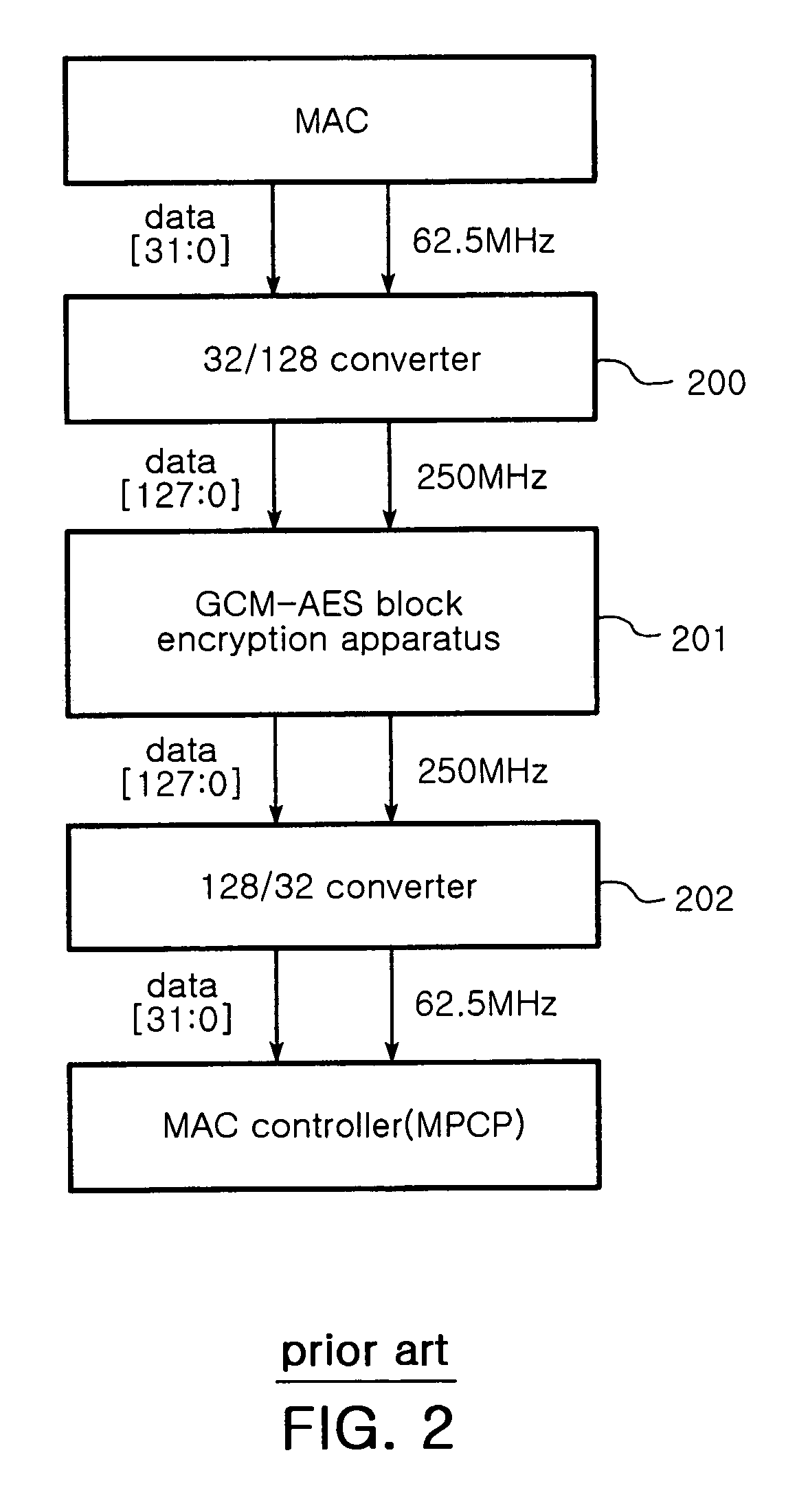
High-speed GCM-AES block cipher apparatus and method
InactiveUS7840003B2Encryption apparatus with shift registers/memoriesSecret communicationClock rateOptical line termination
A high-speed Galois Counter Mode-Advanced Encryption Standard (GCM-AES) block cipher apparatus and method is provided. The apparatus can operate at a low clock frequency of 125 MHz and provide a 2 Gbps link encryption function in an Optical Line Termination (OLT) and an Optical Network Unit (ONU) of an Ethernet Passive Optical Network (EPON). 11-round block cipher of 128- bit input data is implemented using an 8-round Counter-AES (CTR-AES) block cipher module and a 3-round CTR-AES block cipher module, so that it is possible to provide a 1 Gbps link security function for an input frequency of 62.5 MHz and a 2 Gbps link security function for an input frequency of 125 MHz.
Owner:ELECTRONICS & TELECOMM RES INST
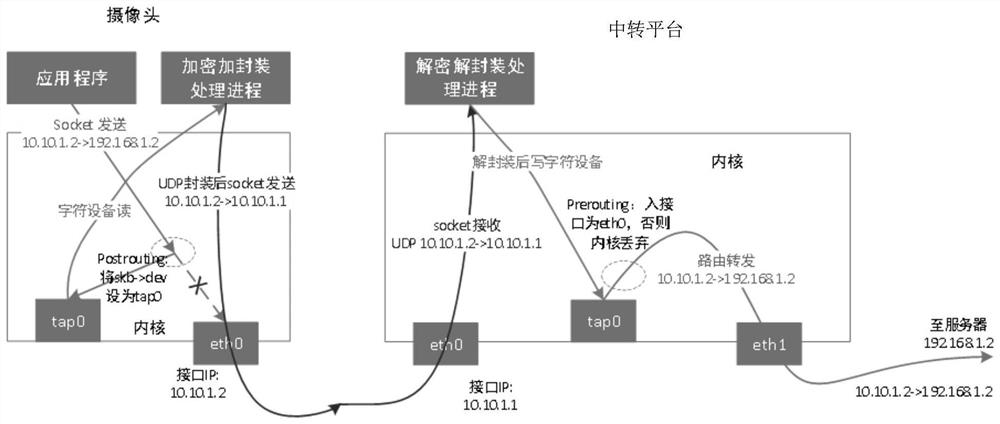
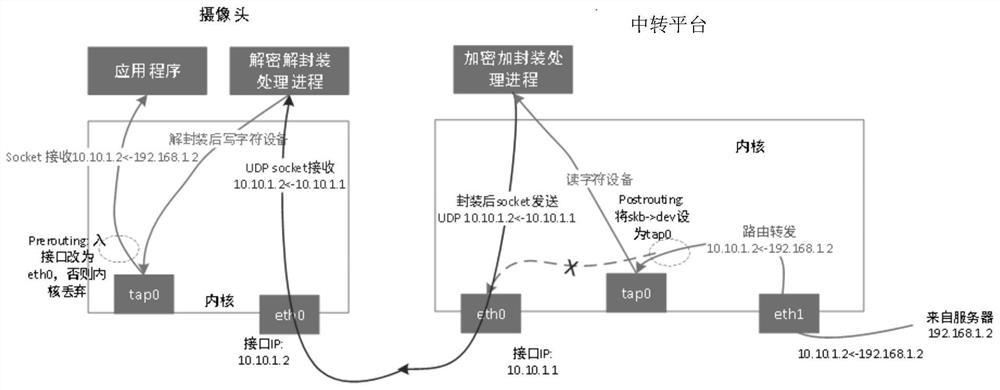
Data encryption and decryption transmission method and data transmission system for camera and server
PendingCN113037706AEasy data transferReliable data transmissionTransmissionComputer hardwareEngineering
The invention relates to a data encryption and decryption transmission method for a camera and a server, which utilizes a TUN / TAP virtual network device of Linux to realize encrypted tunnel transmission, enables a link between the camera and a platform to be encrypted, and is transparent for an application program running on the camera, that is, the application program on the camera does not need to be changed at all. The camera is still in normal communication with the platform and the server, but an encryption tunnel is provided at the bottom layer to carry out encryption transmission on data between the camera and the platform, so that the data transmission is more convenient and reliable.
Owner:深圳可信计算技术有限公司
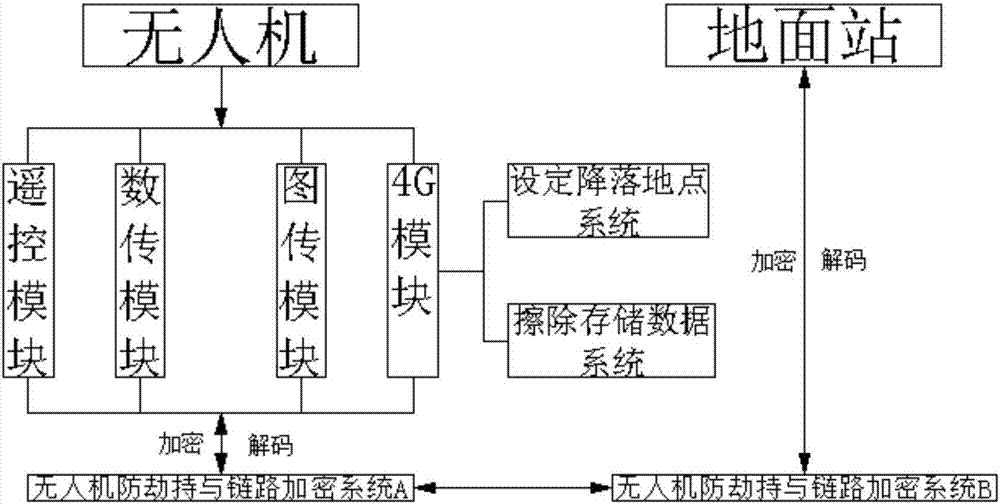
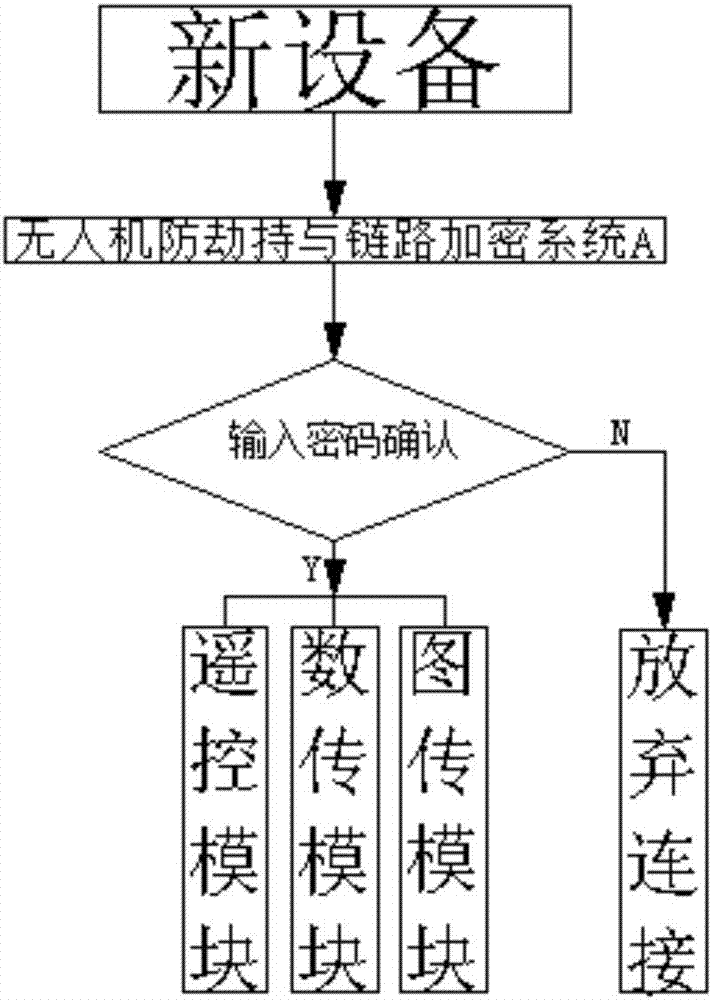
Anti-hijacking and link encryption system of unmanned aerial vehicle
InactiveCN107040919APrevent leakageEnsure flight safetyRadio transmissionSecurity arrangementData connectionRemote control
The invention discloses an anti-hijacking and link encryption system of an unmanned aerial vehicle. The system comprises a remote control module, a data transmission module and an image transmission module, and also comprises a 4G module, an anti-hijacking and link encryption system A of the unmanned aerial vehicle, an anti-hijacking and link encryption system B of the unmanned aerial vehicle and a ground station, wherein the remote control module, the data transmission module and the image transmission module are respectively in bidirectional data connection with the anti-hijacking and link encryption system A of the unmanned aerial vehicle; the anti-hijacking and link encryption system A of the unmanned aerial vehicle is in bidirectional data connection with anti-hijacking and link encryption system B; the anti-hijacking and link encryption system B of the unmanned aerial vehicle is in bidirectional data connection with the ground station; the 4G module comprises a landing location setting system and a storage data erasing system; and each of the anti-hijacking and link encryption system A of the unmanned aerial vehicle and the anti-hijacking and link encryption system B of the unmanned aerial vehicle is provided with an encryption algorithm module therein. According to system provided by the invention, the event that the unmanned aerial vehicle is hijacked by other people or the data of the unmanned aerial vehicle is stolen during a flight process is avoided, and flight security and data security of the unmanned aerial vehicle are ensured.
Owner:GUANGDONG RONGQE INTELLIGENT TECH CO LTD
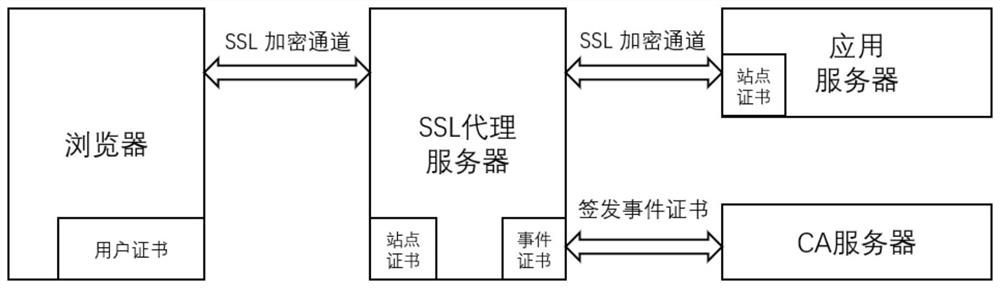
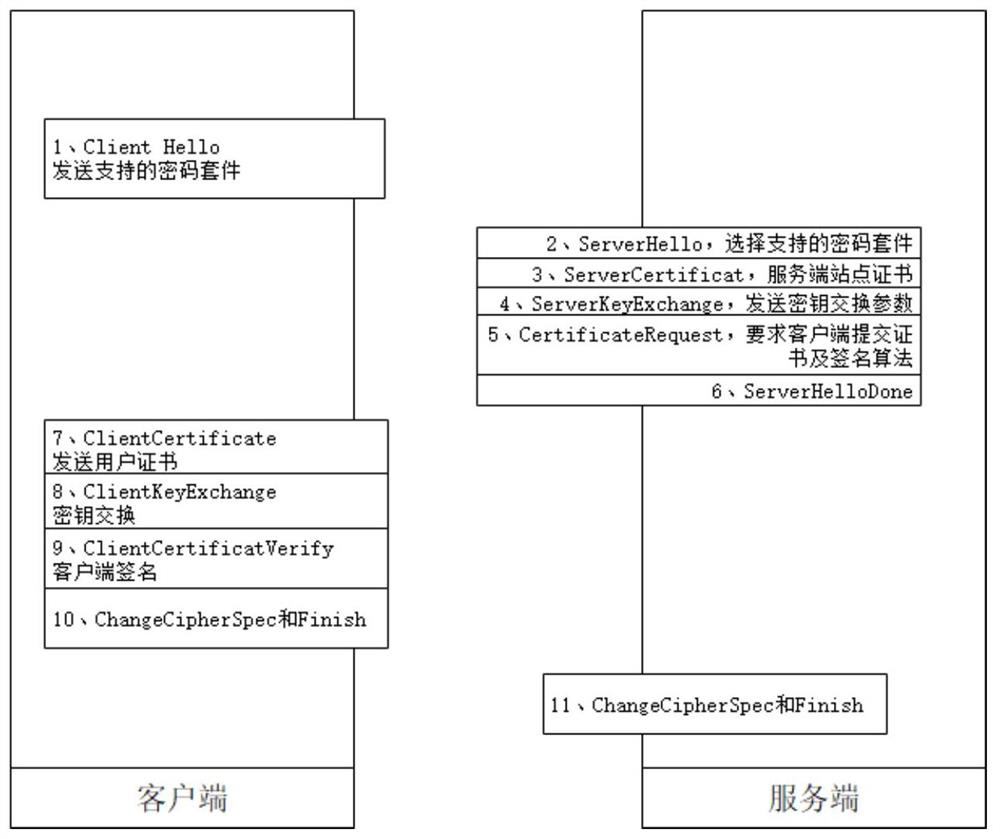
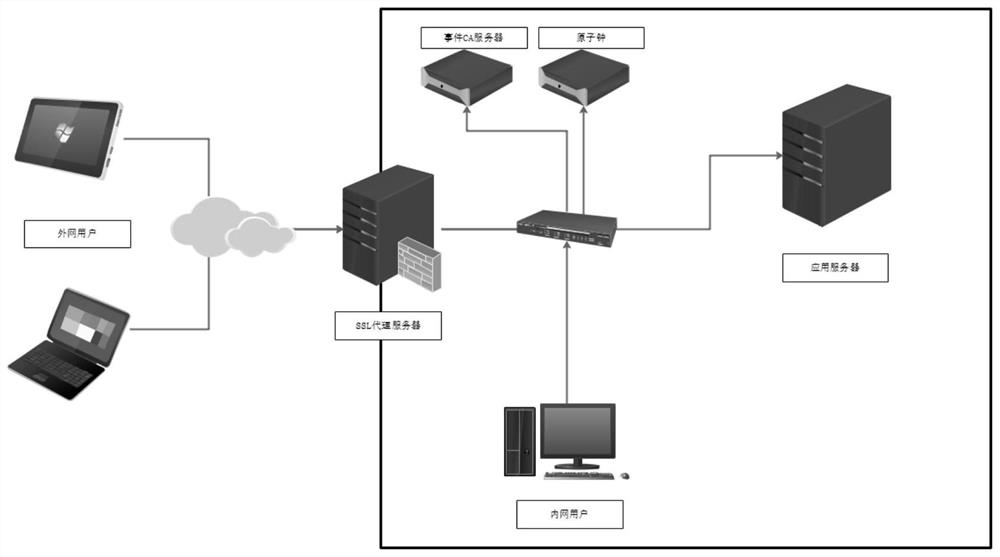
Method for realizing full-link encryption agent by using event certificate
ActiveCN111800402AAddress communication security issuesImprove securityUser identity/authority verificationApplication serverInternet privacy
The invention discloses a method for realizing a full-link encryption agent by using an event certificate. The method comprises the following steps: establishing an SSL encryption tunnel based on a digital certificate between a browser and an SSL proxy server, and then, dynamically generating an event certificate in the SSL proxy server in linkage with the CA server, and associating the event certificate to the SSL session to complete an SSL encryption tunnel with the back-end application server, so that the back-end application server can perform secondary identity authentication on the userand further perform fine-grained access control and single sign-on. By utilizing the event certificate, one-time pad of a session between the SSL proxy server and the application server can be realized, an authentication identifier of the session is consistent with a user identity identifier of an original visitor, and meanwhile, the characteristics of timely signing and issuing, no need of storage, short validity period and the like of the event certificate are fully utilized in the session. The SSL proxy server can realize micro-isolation from a user to an application by adopting an event certificate mode, and meanwhile, the access control capability of the whole system and the audit transparency are also improved.
Owner:北京格尔国信科技有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com