Safe screen projection method of cloud mobile phone, mobile terminal and server
A mobile phone security and server technology, which is applied in the network field, can solve the problems of no cloud mobile phone, content leakage, and low efficiency in the process of screen projection, so as to achieve the effect of realizing efficiency and ensuring security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
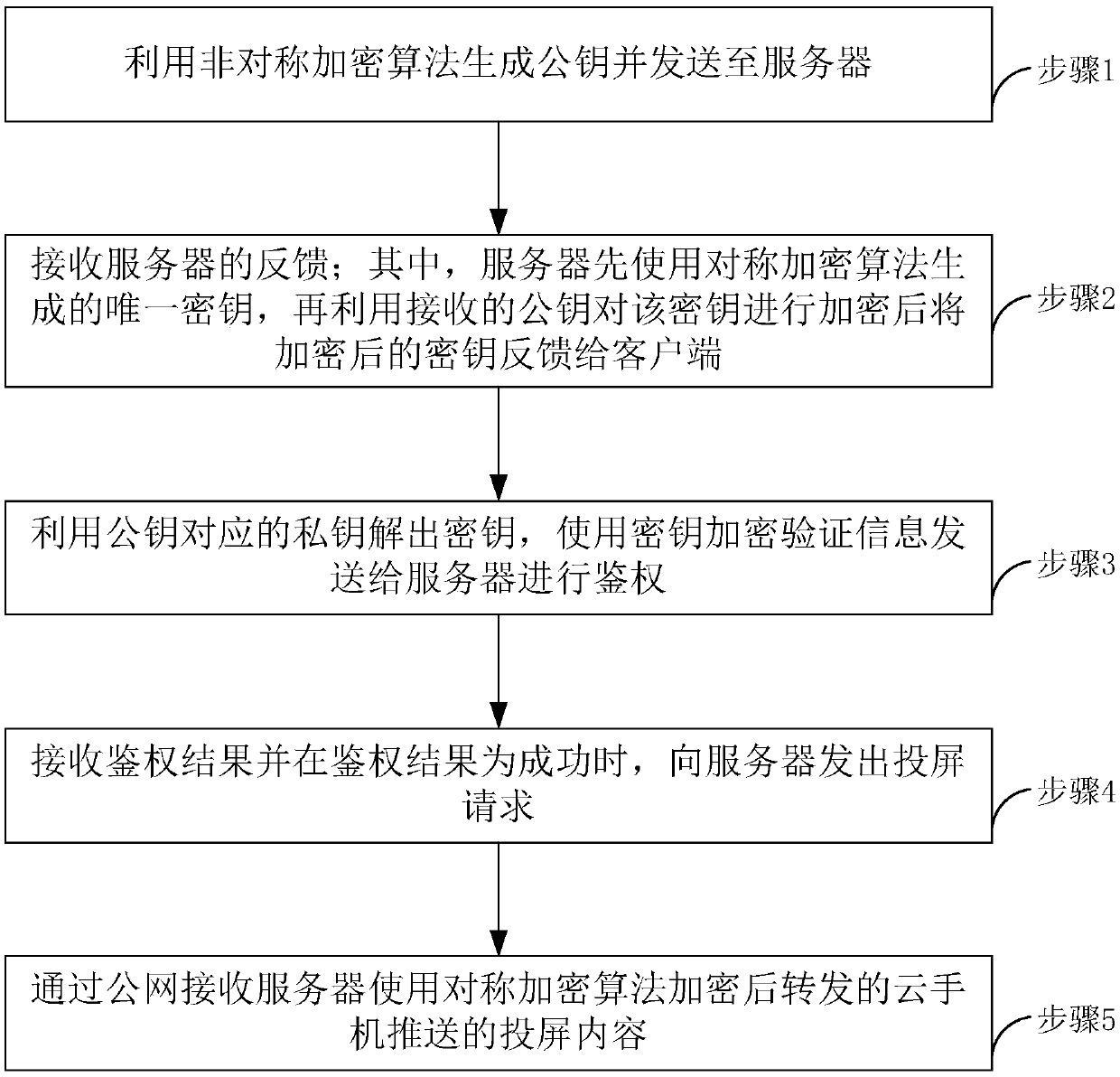
[0033] see figure 1 , the method for safe screen projection of cloud mobile phone according to the embodiment of the present invention, the method includes:
[0034] Step 1, the client uses an asymmetric encryption algorithm to generate a public key and sends it to the server;
[0035] Step 2, the client receives the feedback from the receiving server; wherein, the server first uses the unique key generated by the symmetric encryption algorithm, then encrypts the key with the received public key, and then feeds back the encrypted key to the client;
[0036] Step 3, the client uses the private key corresponding to the public key to decrypt the key, and uses the key to encrypt the verification information and send it to the server for authentication;
[0037] Step 4, the client receives the authentication result and sends a screen projection request to the server when the authentication result is successful;
[0038] Step 5: The client receives the screen projection content pu...
Embodiment 2
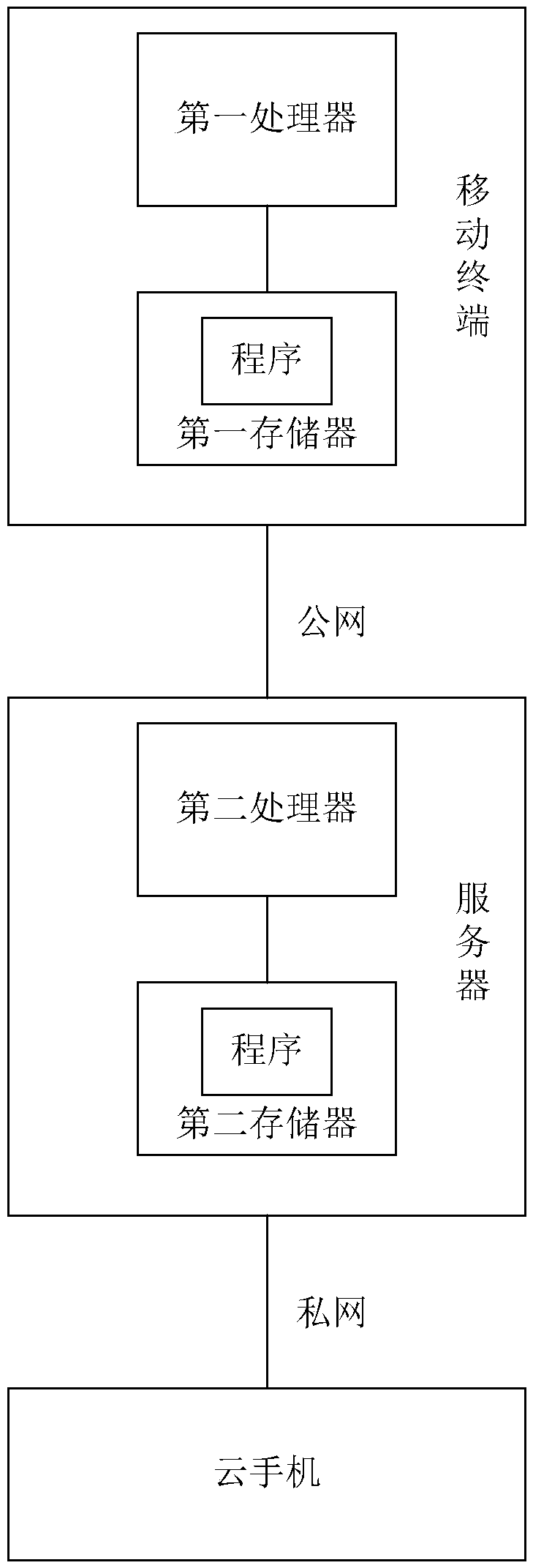
[0056] A mobile terminal according to an embodiment of the present invention, the mobile terminal includes one or more first processors, a first memory, and one or more programs, the mobile terminal and the server are connected through a public network communication, and the server and the cloud mobile phone are Network communication connection, wherein, one or more programs are stored in the first memory, and are configured to be executed by one or more first processors, the programs are used to execute the instructions of the method for securely projecting screens on cloud mobile phones in Embodiment 1 , that is, a client is installed on the mobile terminal, and the client executes the following methods in the form of one or more programs:
[0057] Step 1, use an asymmetric encryption algorithm to generate a public key and send it to the server;
[0058] Step 2, receiving the feedback from the server; wherein, the server first uses the unique key generated by the symmetric e...
Embodiment 3
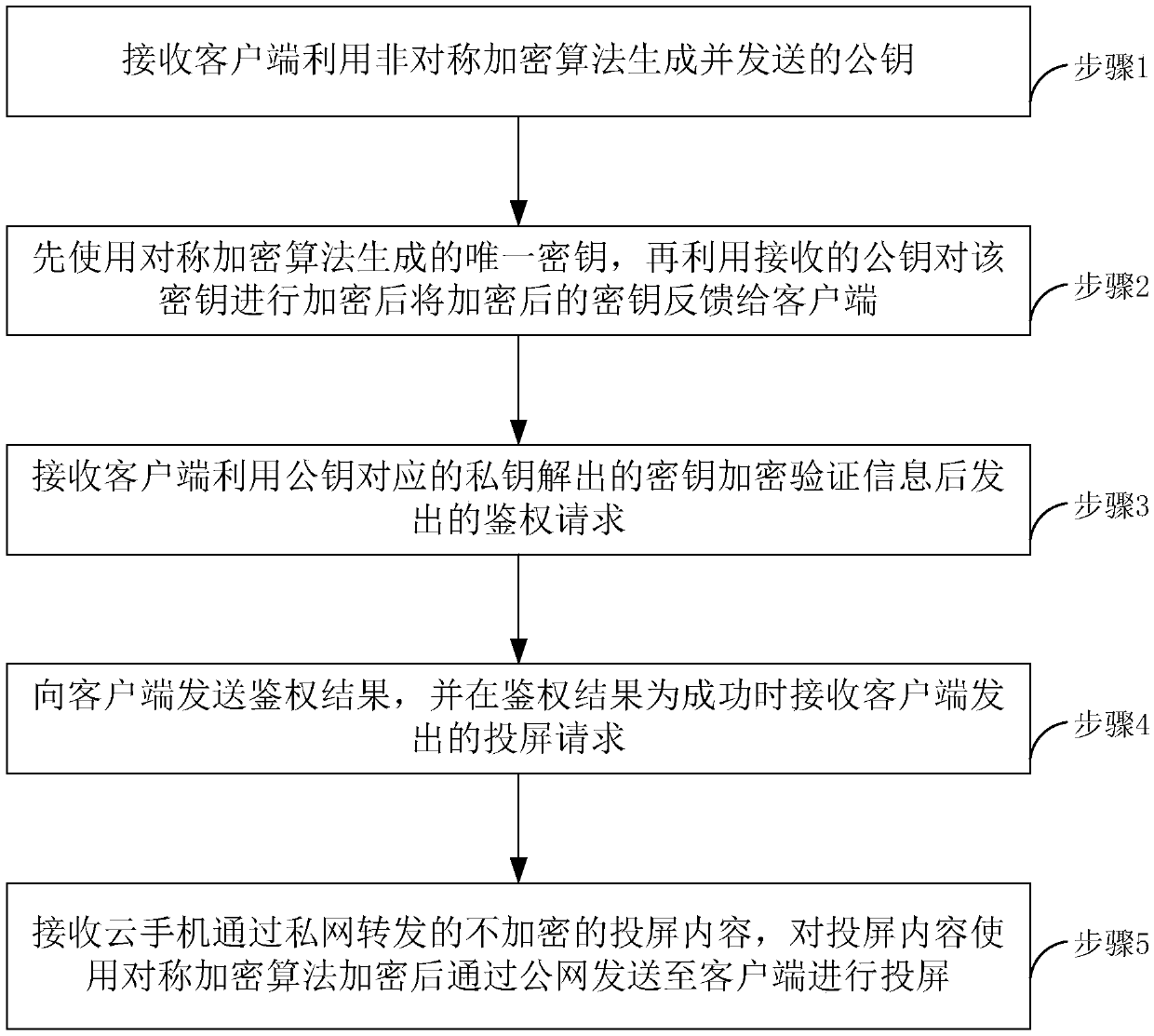
[0063] see image 3 , a method for safely projecting a screen from a cloud mobile phone according to an embodiment of the present invention, the method comprising:
[0064] Step 1, the server receives the public key generated and sent by the client using an asymmetric encryption algorithm;
[0065] Step 2, the server first uses the unique key generated by the symmetric encryption algorithm, then encrypts the key with the received public key, and then feeds back the encrypted key to the client;
[0066] Step 3, the server receives the authentication request sent by the client after encrypting the verification information with the key decrypted by the private key corresponding to the public key;
[0067] Step 4, the server sends the authentication result to the client, and receives the screen projection request sent by the client when the authentication result is successful;
[0068] Step 5: The server receives the unencrypted screen projection content forwarded by the cloud p...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com