Anonymous connection method of broadband radio IP network
An IP network and broadband wireless technology, applied in the field of communication security, can solve problems such as poor scalability, poor robustness, and low protocol efficiency, and achieve the effect of improving utilization
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
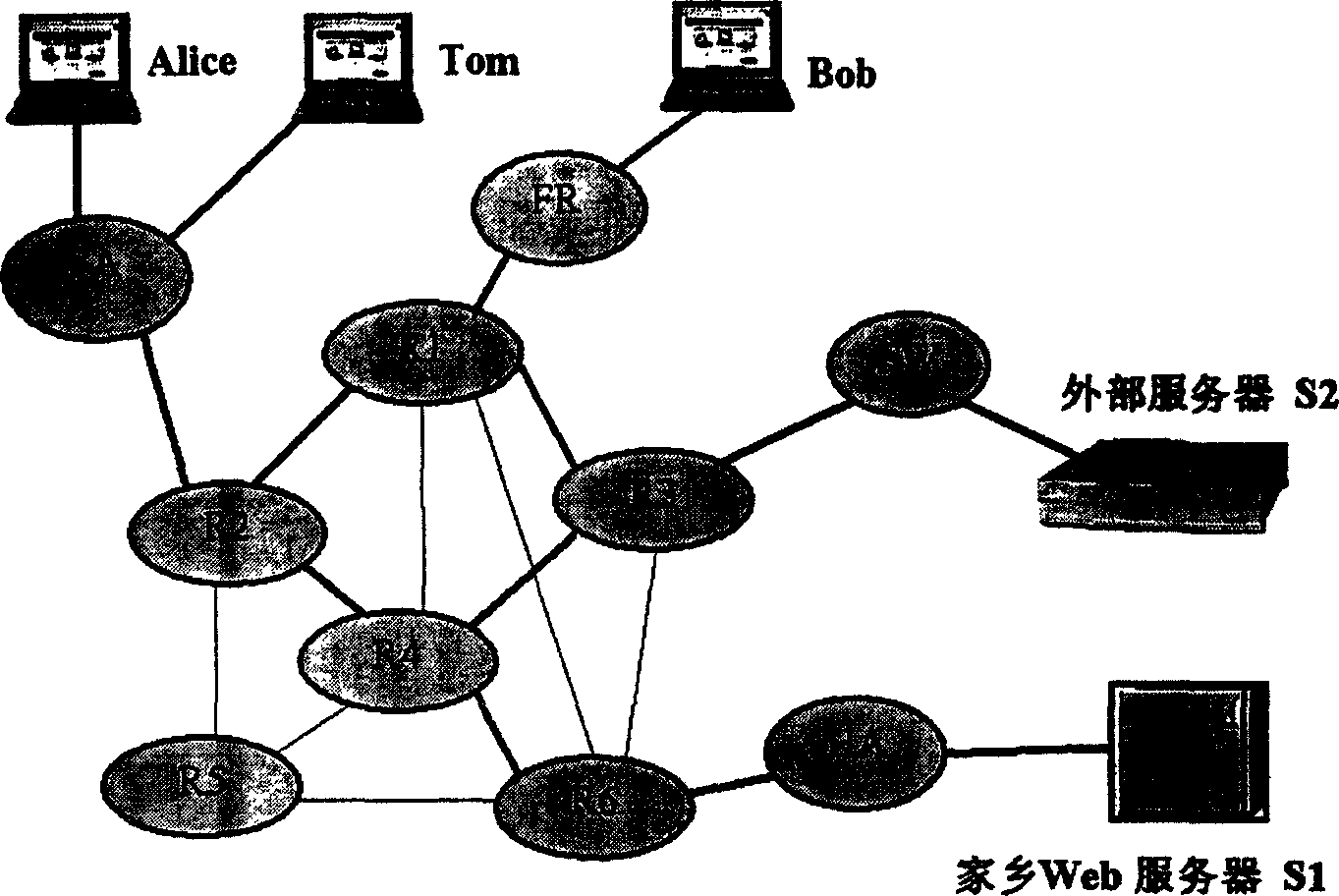
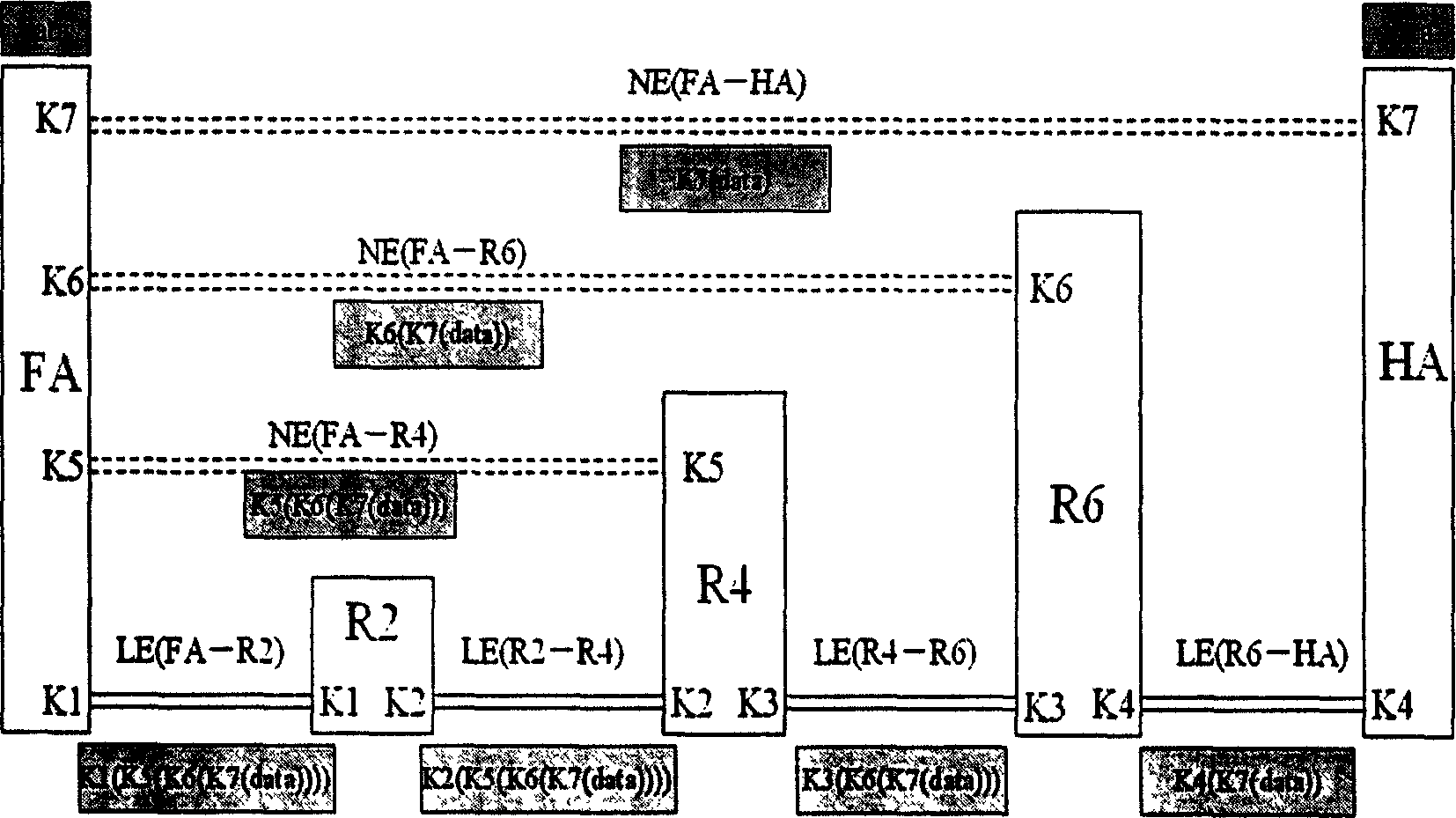
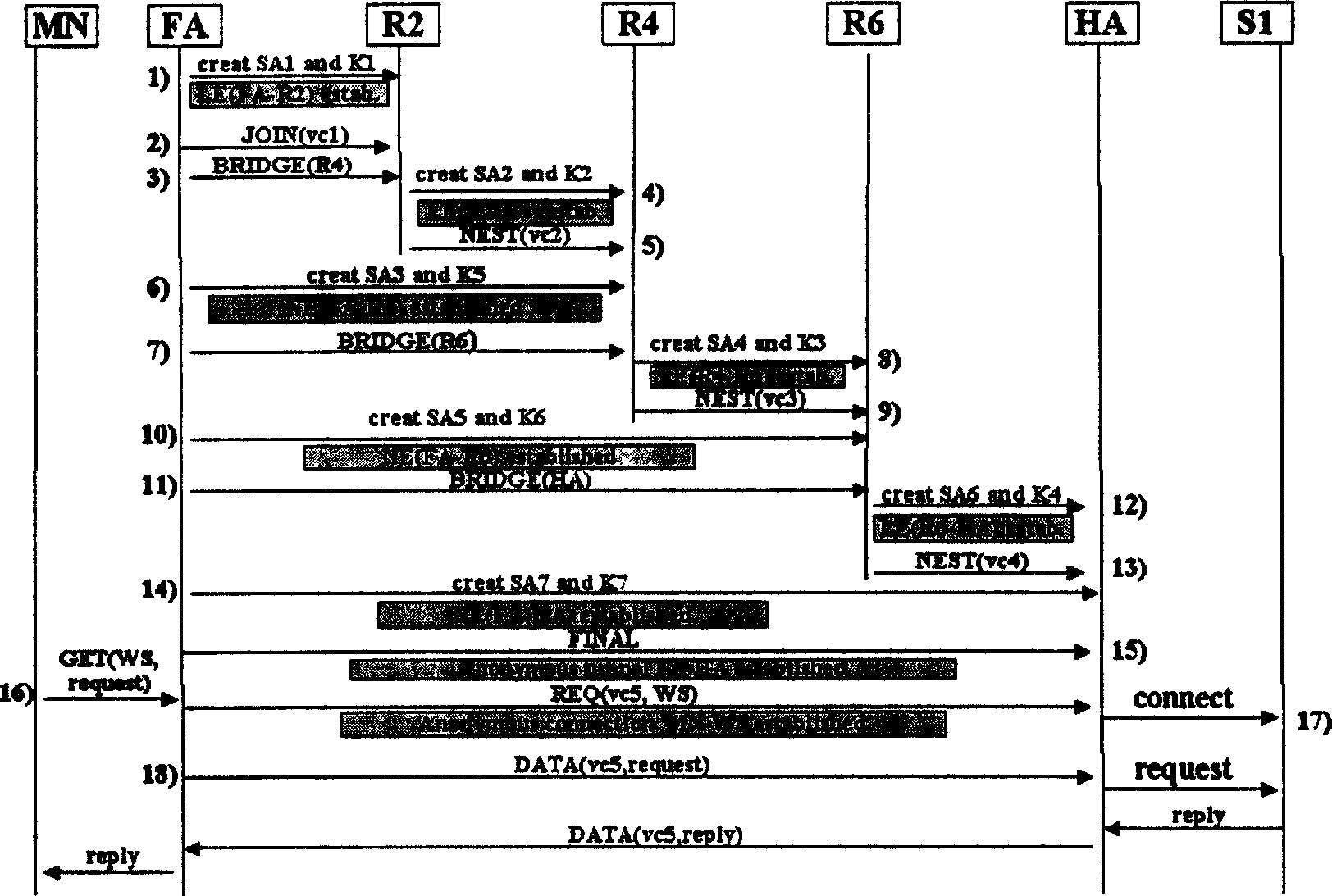
[0058] The BWIP network anonymous system uses the distributed system idea, combined with the actual situation of the BWIP network, to change the global connection mode of the anonymous communication system into a segmented local connection, so that the BWIP network anonymous system not only improves the anti-traffic analysis, but also has the versatility powerful. In order to illustrate the BWIP network anonymity technical solution proposed in this patent, the present invention proposes an anonymous network system model existing in a safe key application and key management environment, combined below figure 1 Analyze and illustrate the implementation of anonymous technology for mobile users to browse Web servers anonymously.
[0059] figure 1 It is a BWIP network anonymous model, in which Alice, Tom and Bob (three names) represent mobile users MN, S1 and S2 represent anonymous servers that provide various services on the Internet, such as S1 is a Web server, S2 is an FTP serv...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com