Method for realizing full-link encryption agent by using event certificate
A full-link, user-certificate technology, which is applied in the field of full-link encrypted proxy using event certificates, can solve problems such as cross-trust domains
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0025] In order to make the technical means, creative features, goals and effects achieved by the present invention easy to understand, the following will further explain how to implement the present invention in combination with specific diagrams.
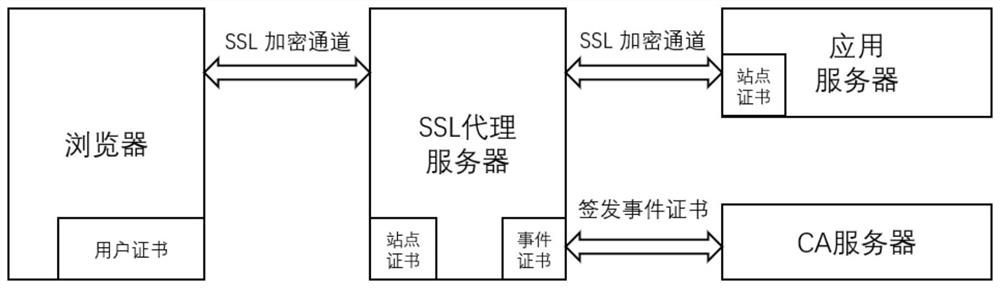
[0026] (1) Digital certificate issuance and trust domain
[0027] Use the root CA to issue the secondary user certificate CA and event certificate CA, the user certificate CA is used to issue user certificates, and the event CA server is used to issue event certificates. Intranet application servers trust the user certificate CA and event CA certificate chains. Trust the user certificate CA on the SSL proxy server.
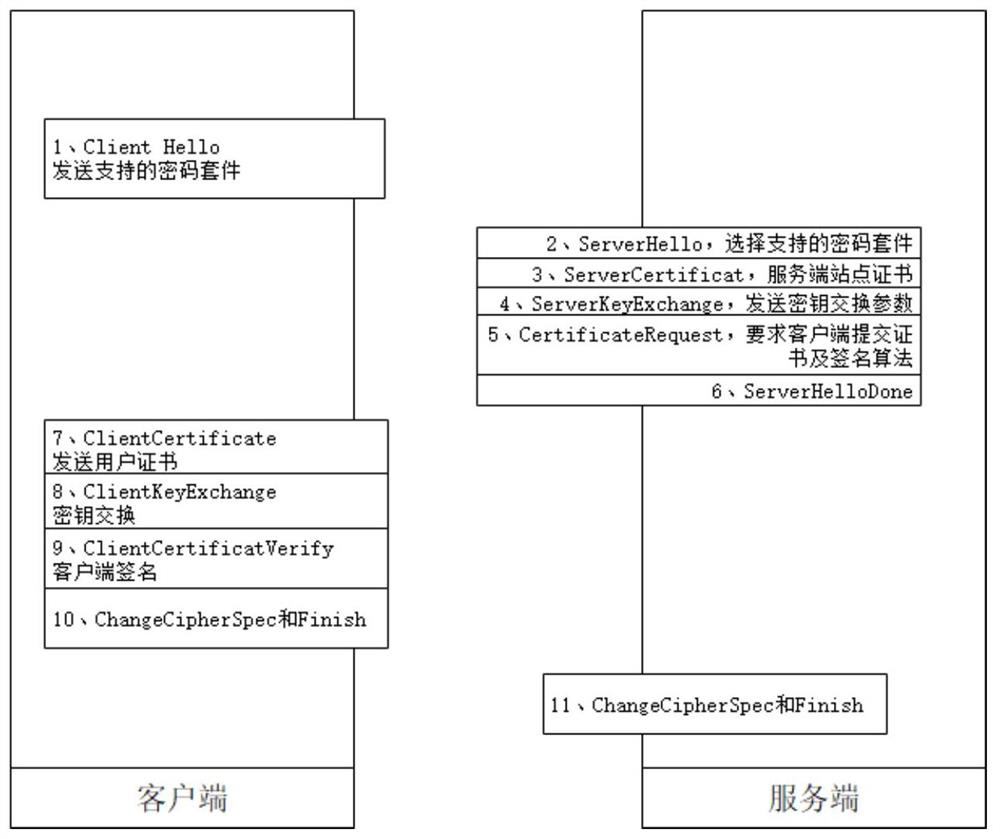
[0028] (2) User access process
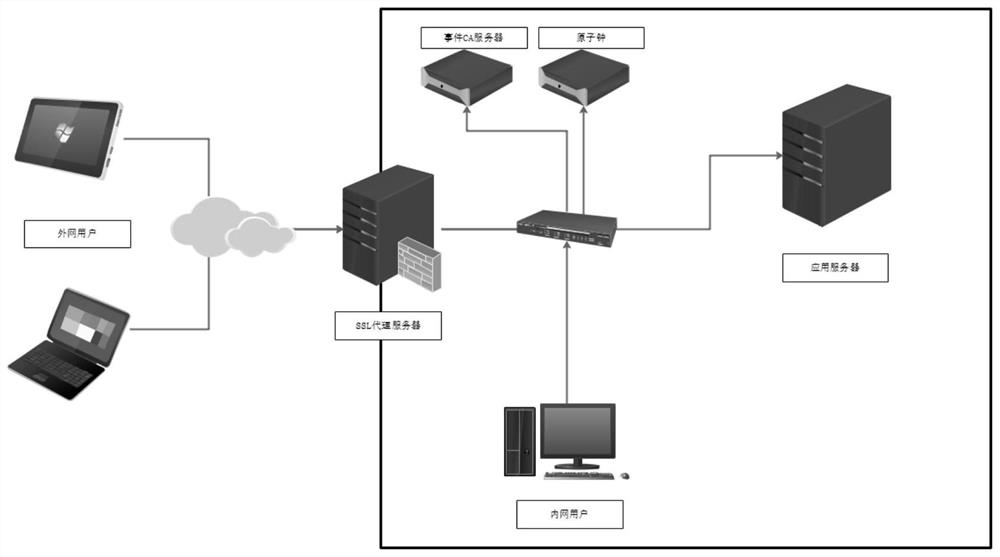
[0029] see image 3 , Deploy a forward or reverse SSL proxy server at the network border, the CA server is used to issue event certificates, the atomic clock provides the time source, and the SSL proxy server, CA server, and application server synchronize time with the atomic clock....
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com