Communication link protection method and device
A communication link and link encryption technology, applied in the field of communication link protection methods and devices, to achieve the effect of improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
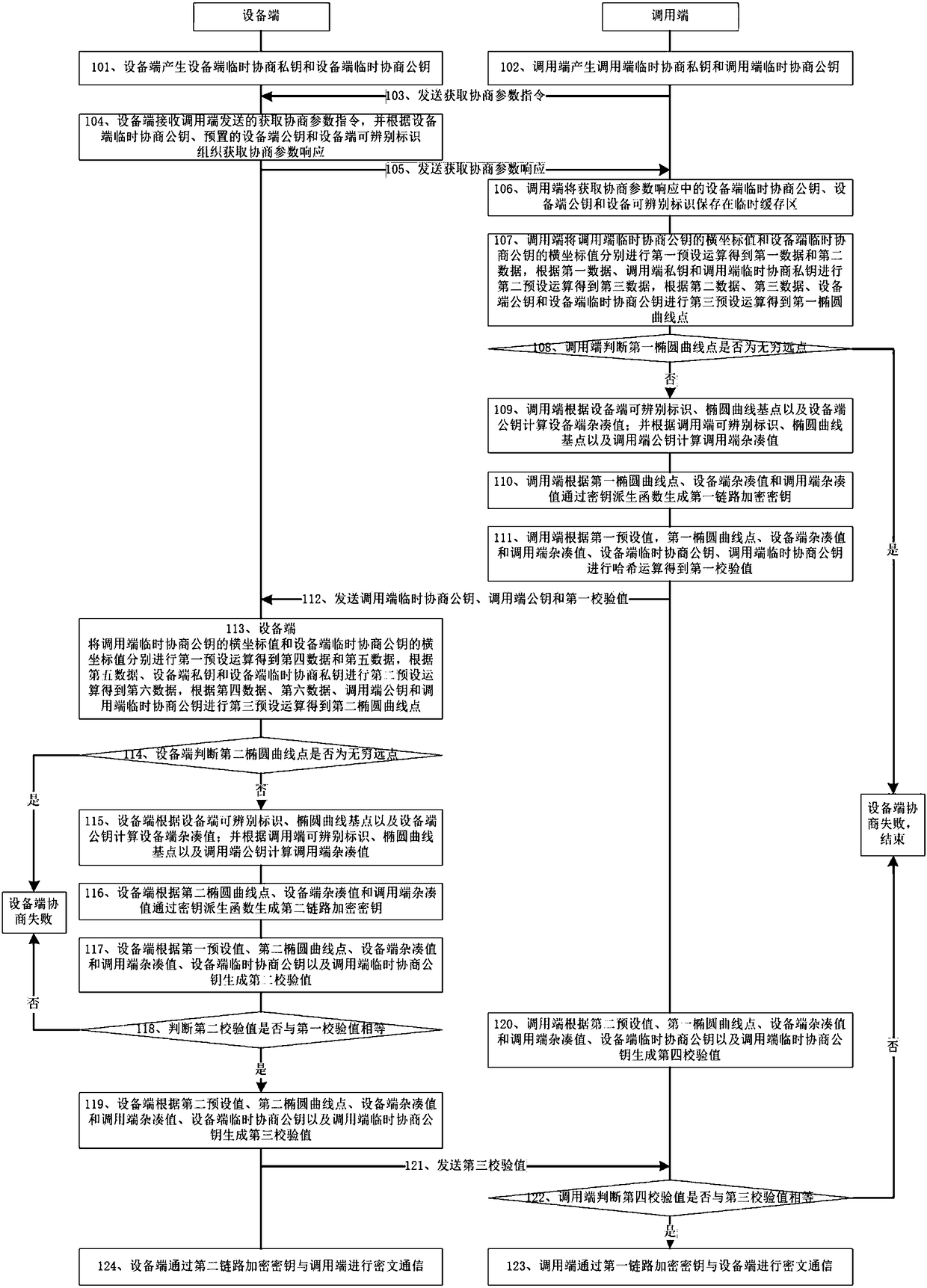
[0043] An embodiment of the present invention provides a communication link protection method, such as figure 1 shown, including:
[0044] Step 101, the device generates a device-side temporary negotiation private key and a device-side temporary negotiation public key;
[0045] The base point of the elliptic curve used in this embodiment is (00 CDB9CA7F 1E6B0441 F658343F 4B10297C0EF9B649 1082400A 62E7A748 5735FADD, 01 3DE74DA6 5951C4D76DC89220 D5F7777A611B2C381C83E260B)
[0046] The order of the elliptic curve is 7FFFFFFF FFFFFFFF FFFFFFFF FFFFFFFF BC972CF7 E6B6F900945B3C6A 0CF6161D;
[0047] Specifically, the device side generates the device side temporary negotiation private key and the device side temporary negotiation public key as follows: the device side generates the first random number as the device side temporary negotiation private key; the device side uses the first random number multiple of the elliptic curve base point as The device temporarily negotiates the publ...
Embodiment 2
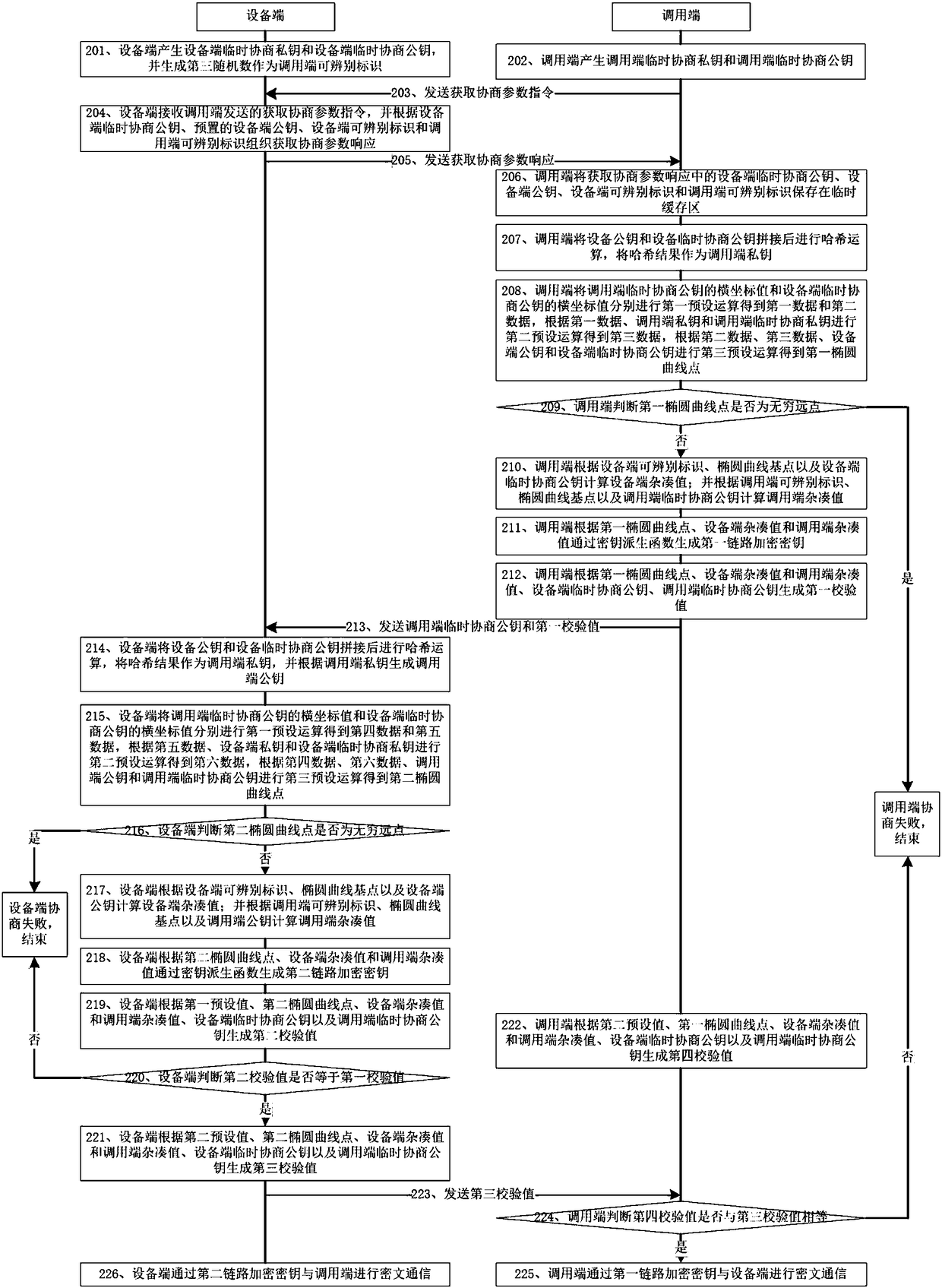
[0111] An embodiment of the present invention provides a communication link protection method, such as figure 2 shown, including:
[0112] Step 201, the device side generates a device-side temporary negotiation private key and a device-side temporary negotiation public key, and generates a third random number as the distinguishable identifier of the caller;
[0113] Specifically, the device side generates the device side temporary negotiation private key and the device side temporary negotiation public key as follows: the device side generates the first random number as the device side temporary negotiation private key; the device side uses the first random number multiple of the elliptic curve base point as The device temporarily negotiates the public key; and generates a third random number as the distinguishable identifier of the caller;
[0114] Step 202, the caller generates the caller's temporary negotiation private key and the caller's temporary negotiation public key...
Embodiment 3
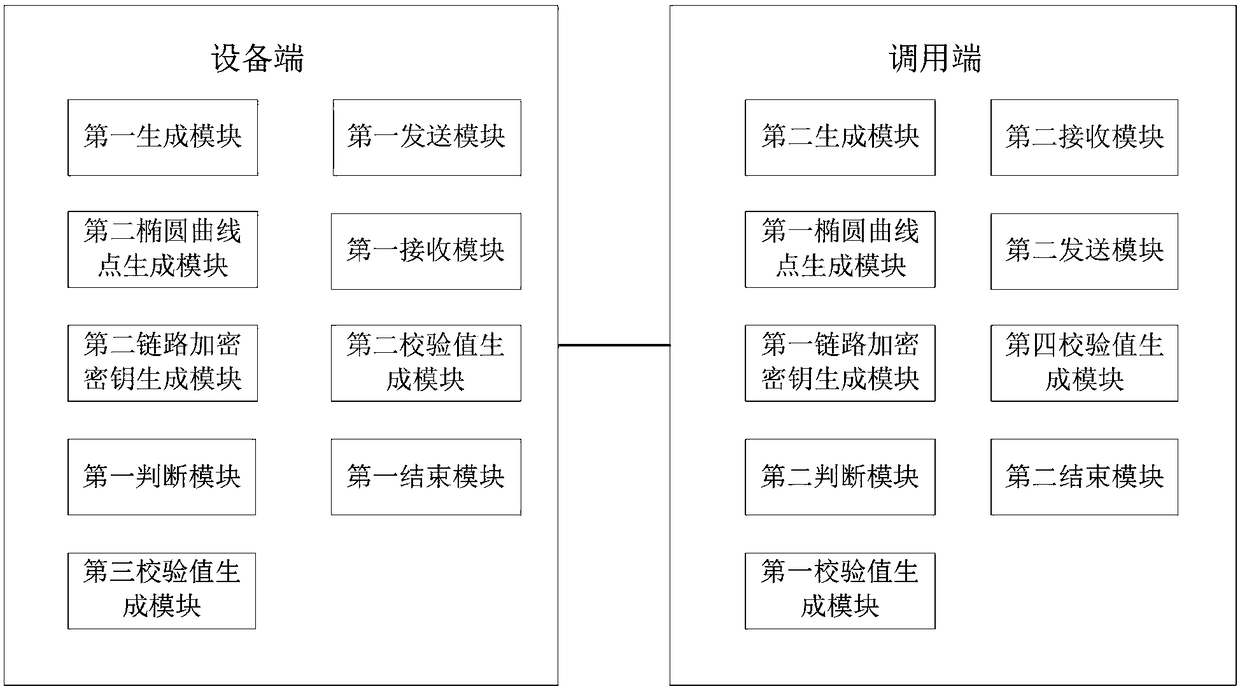
[0175] This embodiment provides a communication link protection device, see image 3 , including: the device side and the calling side;
[0176] The device side includes:
[0177] The first generation module is used to generate a device-side temporary negotiation private key and a device-side temporary negotiation public key;
[0178] Specifically, the first generating module is specifically configured to generate a first random number as a temporary private key for device-side negotiation; and the device-side uses a multiple of the first random number of the base point of the elliptic curve as a temporary public key for device-side negotiation.
[0179] The first sending module is used to send the device-side temporary negotiation public key and the device-side public key to the caller;
[0180] The first receiving module is used to receive the caller's temporary negotiation public key, the first check value and the caller's public key sent by the caller;
[0181] The seco...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com