Safe data transmission method, system and device and storage medium
A technology of data security and transmission method, applied in the field of network security, can solve the problem of high deployment cost
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0060] The technical solutions in the embodiments of the present application will be described below with reference to the drawings in the embodiments of the present application.
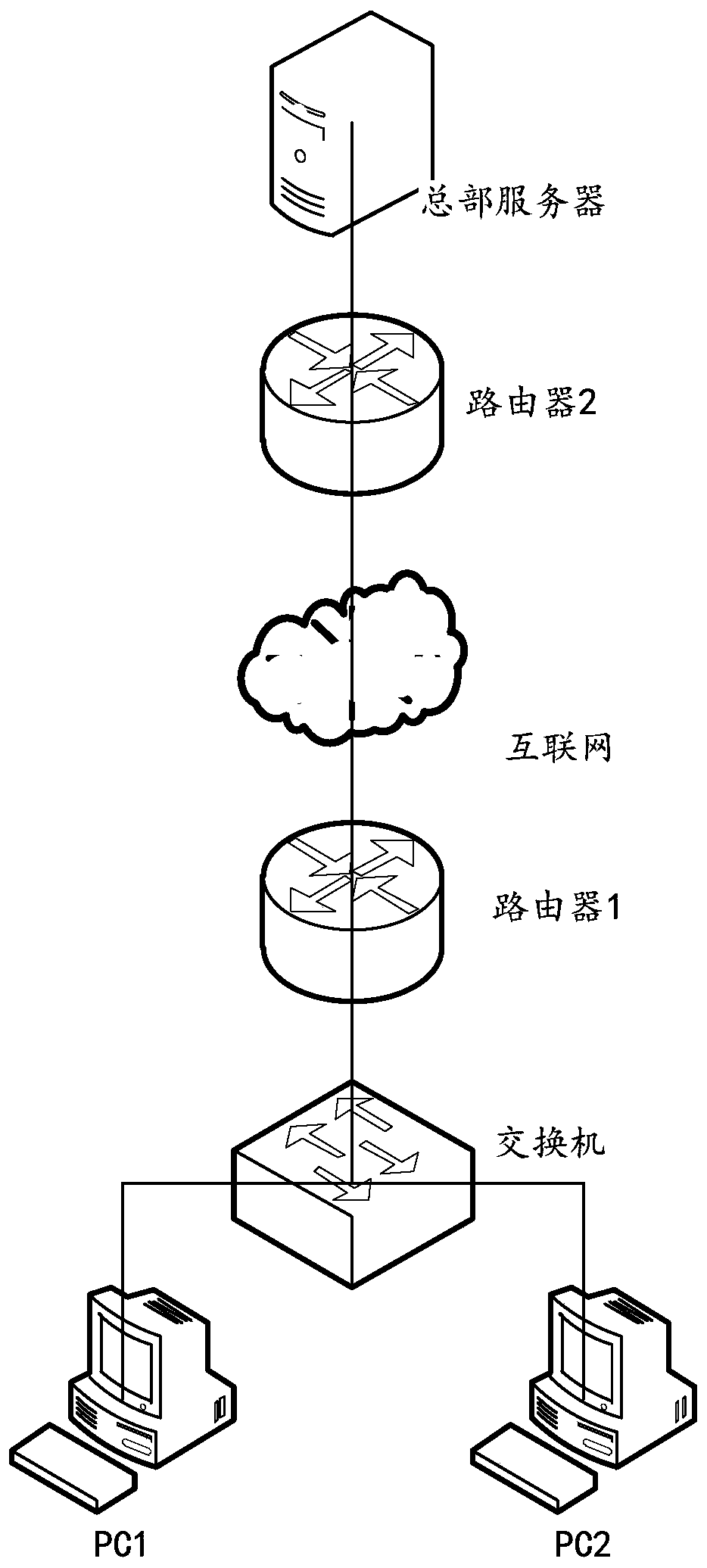
[0061] According to the research of the applicant, the data interaction under the existing branch-headquarters network architecture realizes the secure data transmission between the branch and the headquarters by setting up a separate link encryption gateway at each terminal, and there is a problem of high cost of hardware equipment. However, using software directly at the terminal to ensure secure transmission without using a link encryption gateway connected to the terminal will have security problems, and it is not suitable for data transmission scenarios with high security requirements.
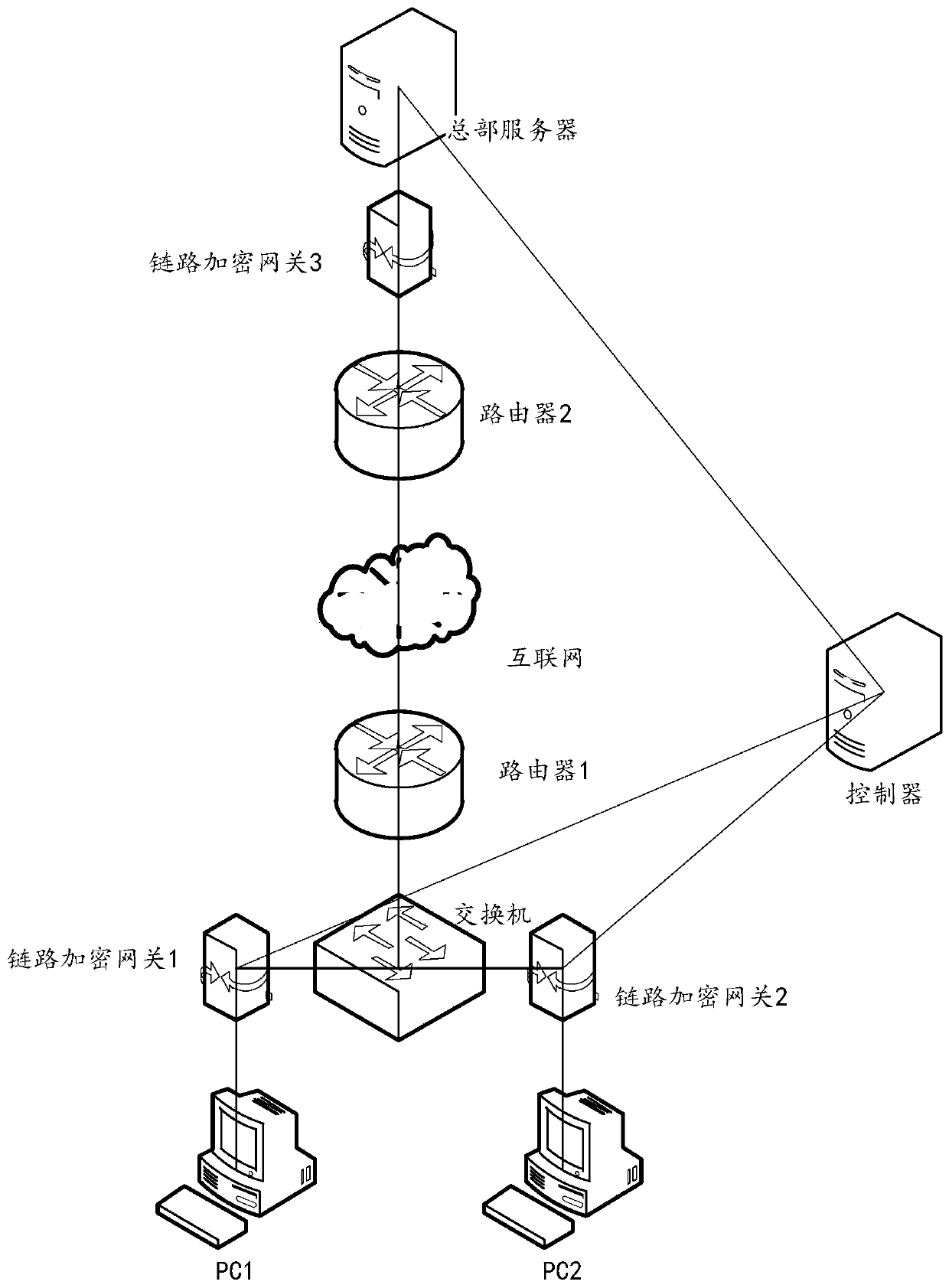
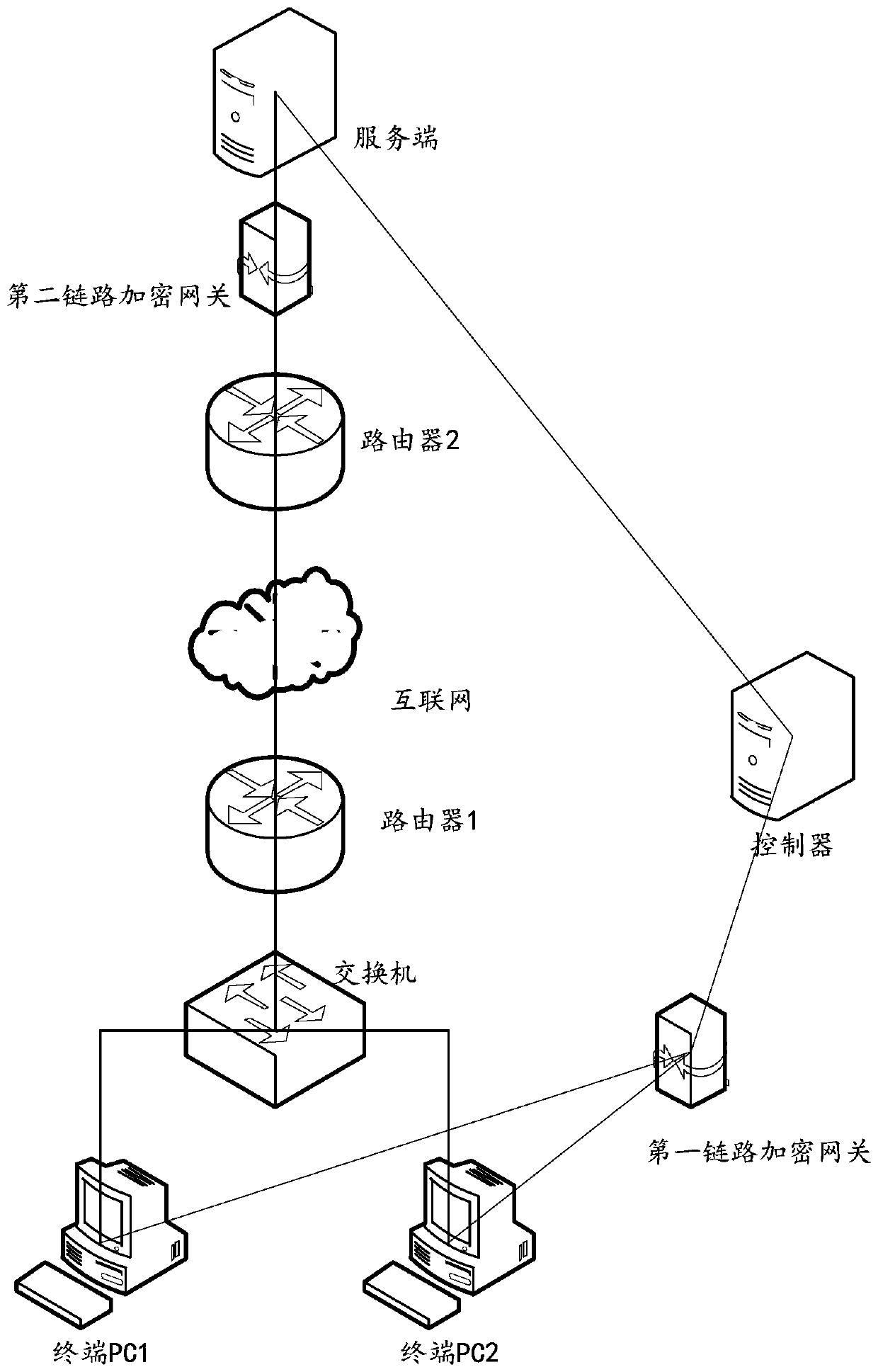
[0062] In order to solve the above problems, the embodiment of this application provides a data security transmission system 10, please refer to image 3 , image 3 It is a schematic structural diagram of a da...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com