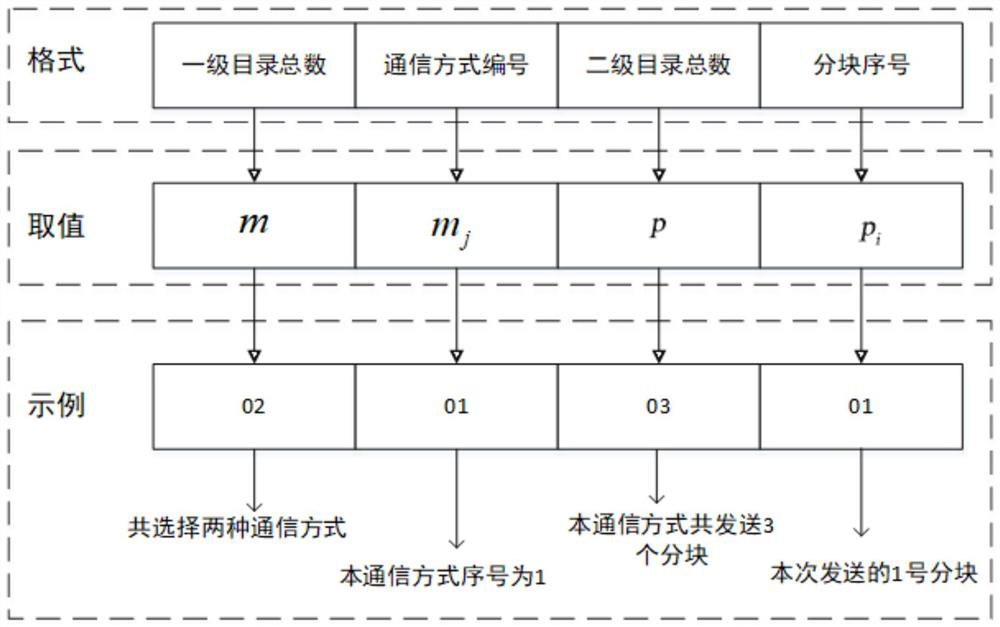
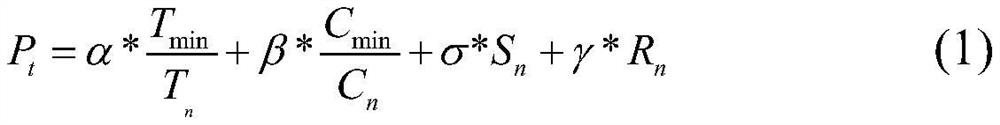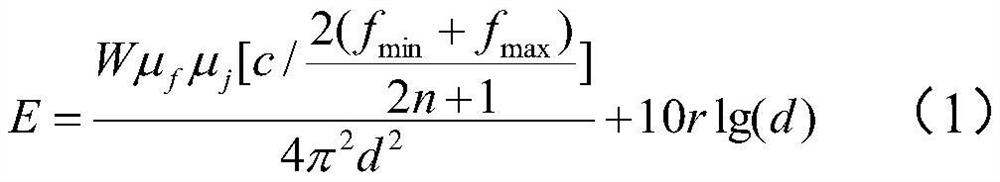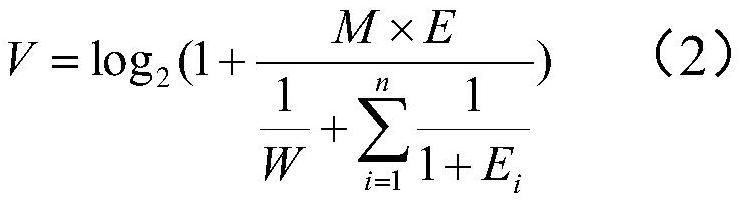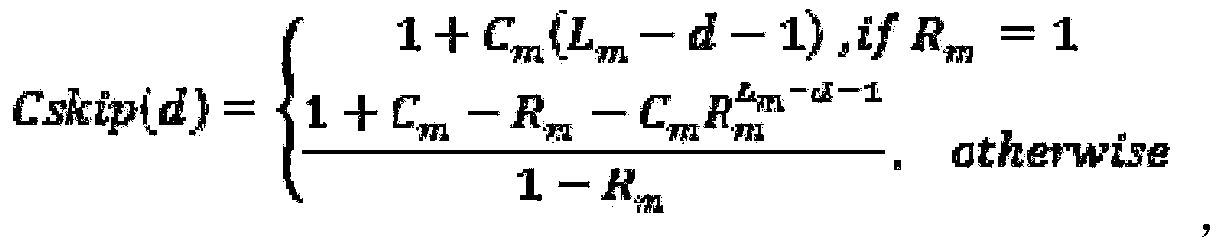Patents
Literature
56results about How to "Improve data transmission security" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
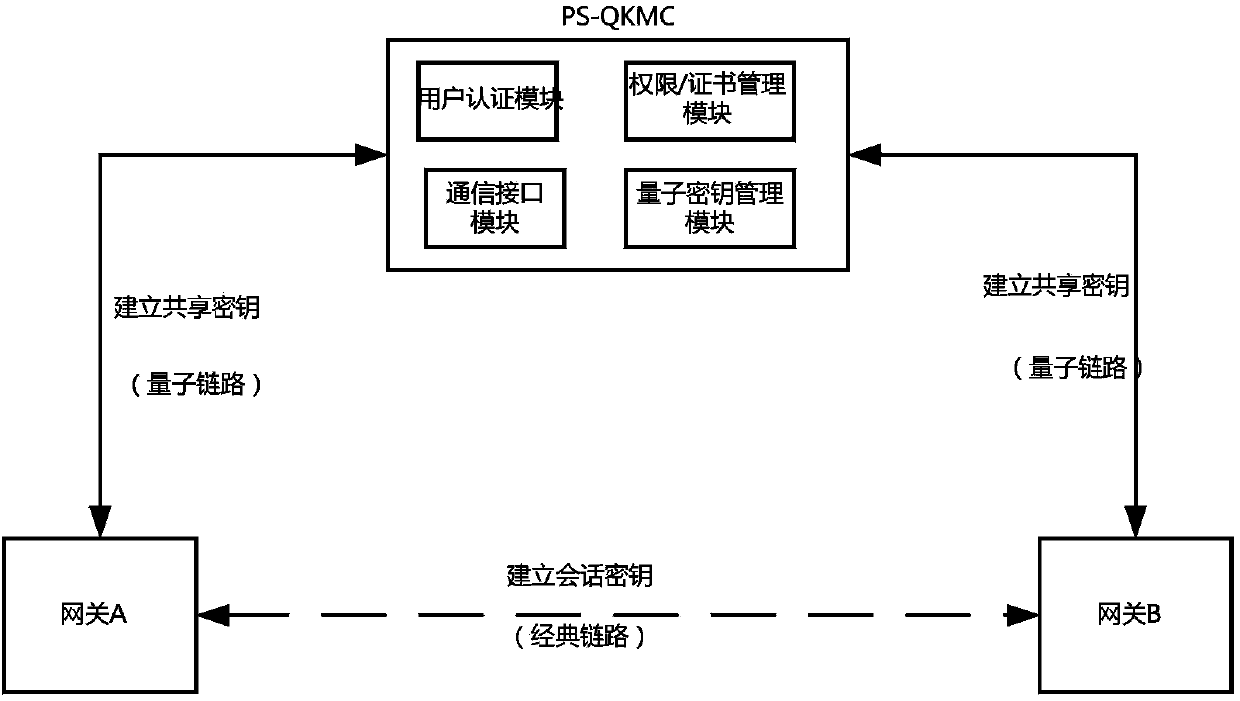
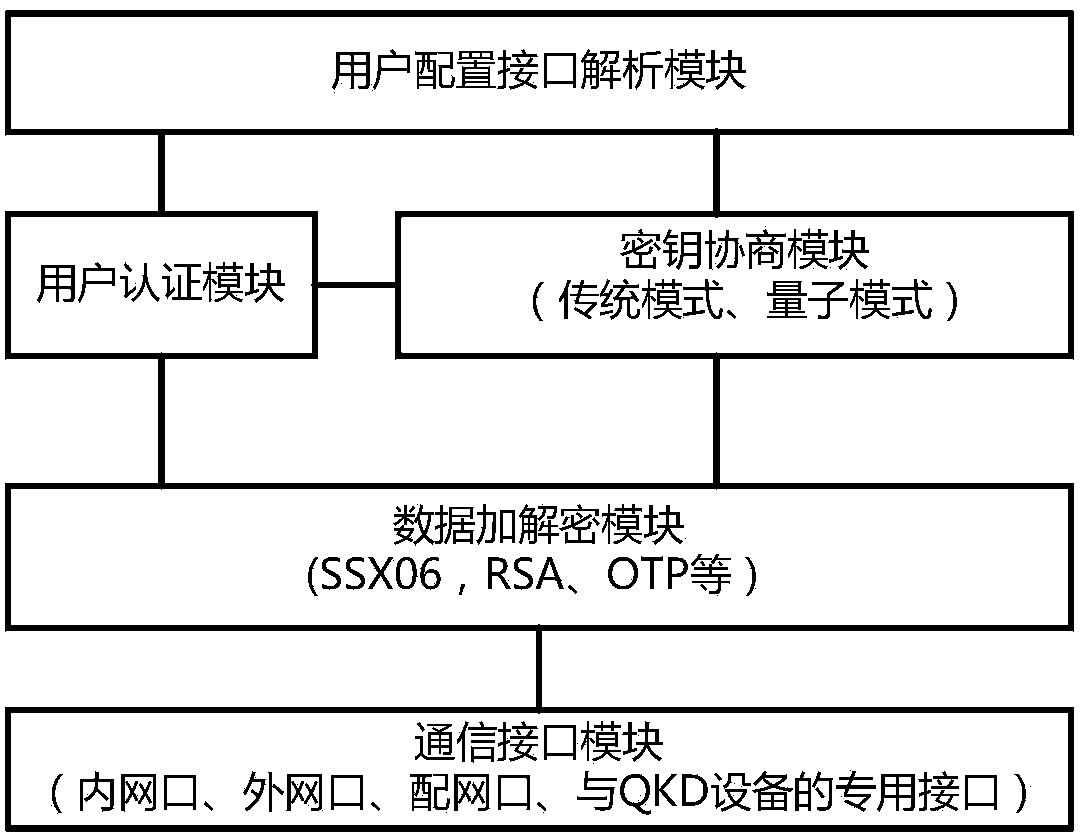
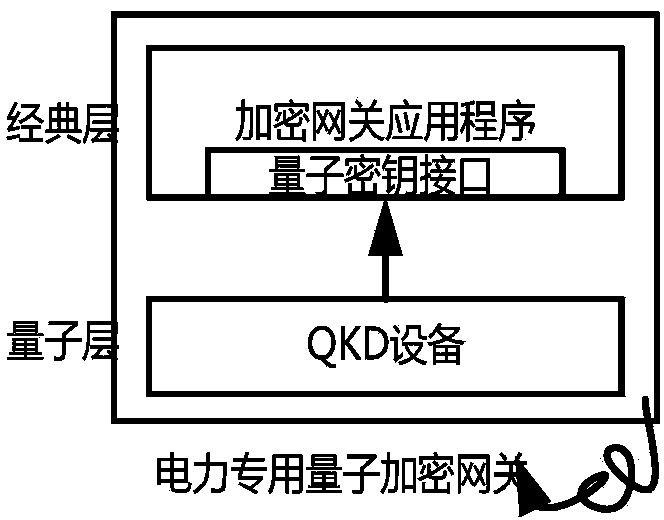
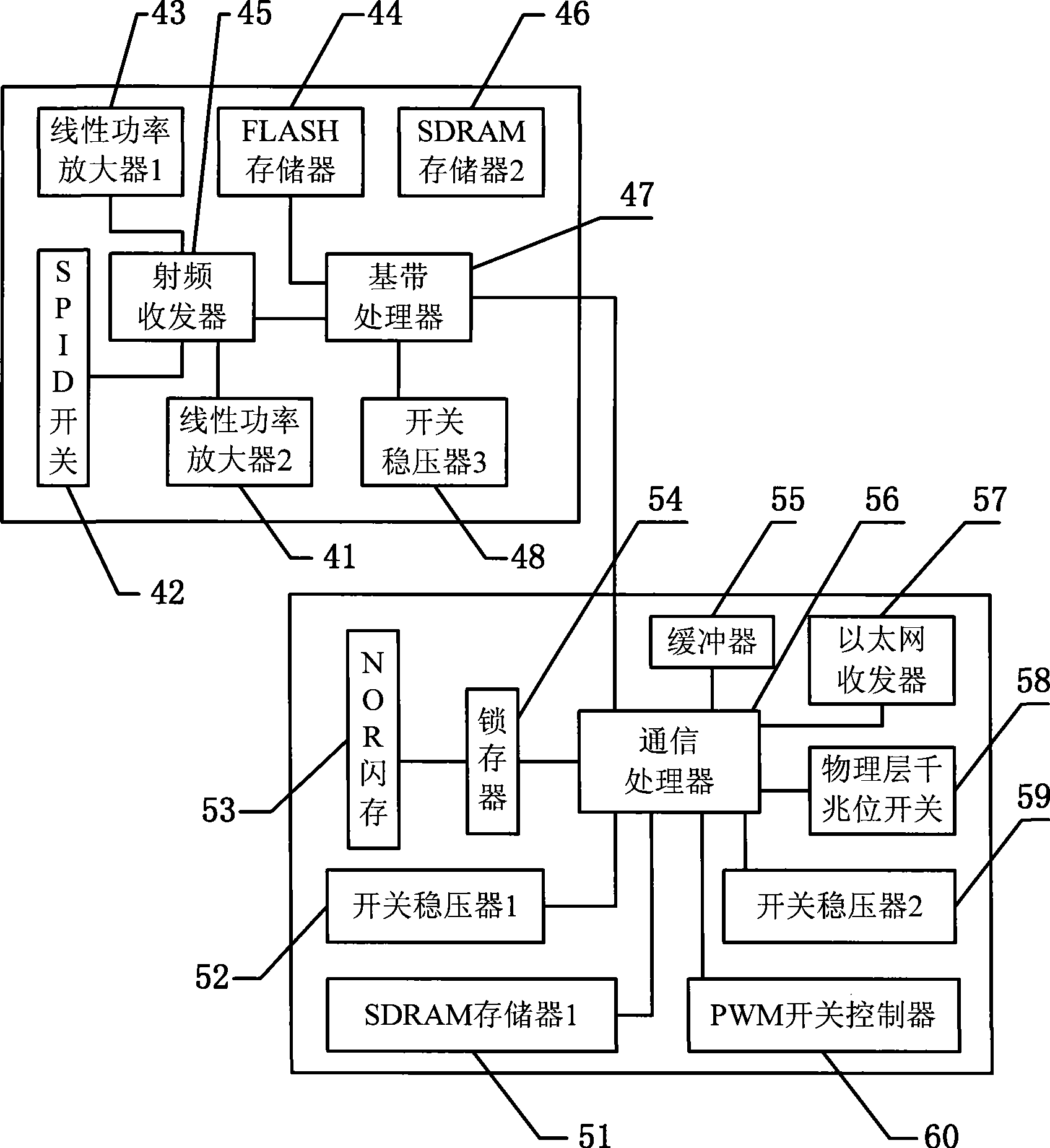
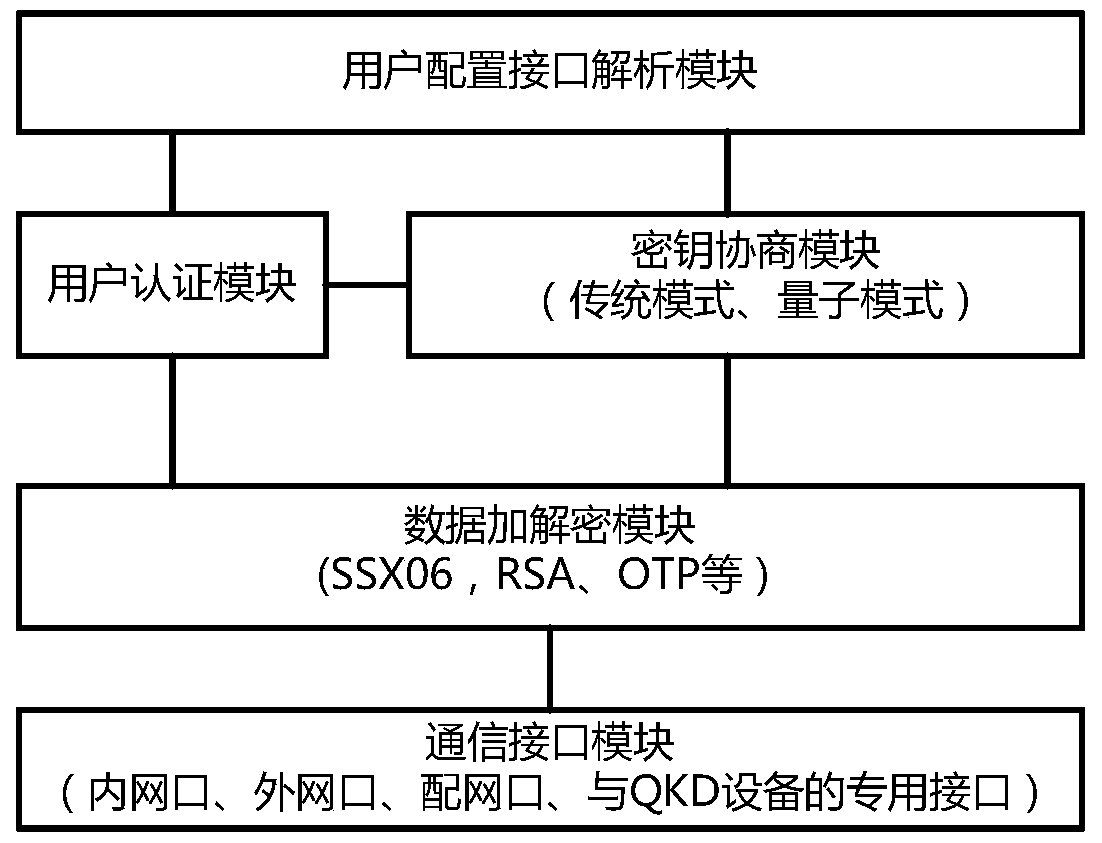
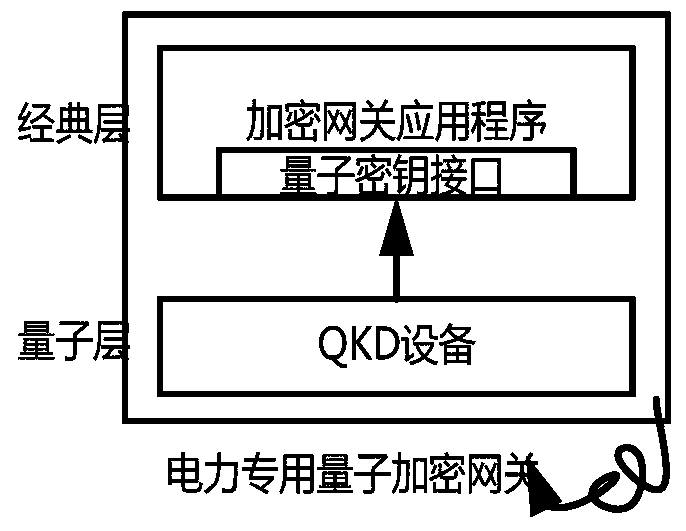
Power special quantum encryption gateway system
ActiveCN103475464AAdd extensionsMinor changesKey distribution for secure communicationNetwork connectionsCommunication interfaceElectric power system
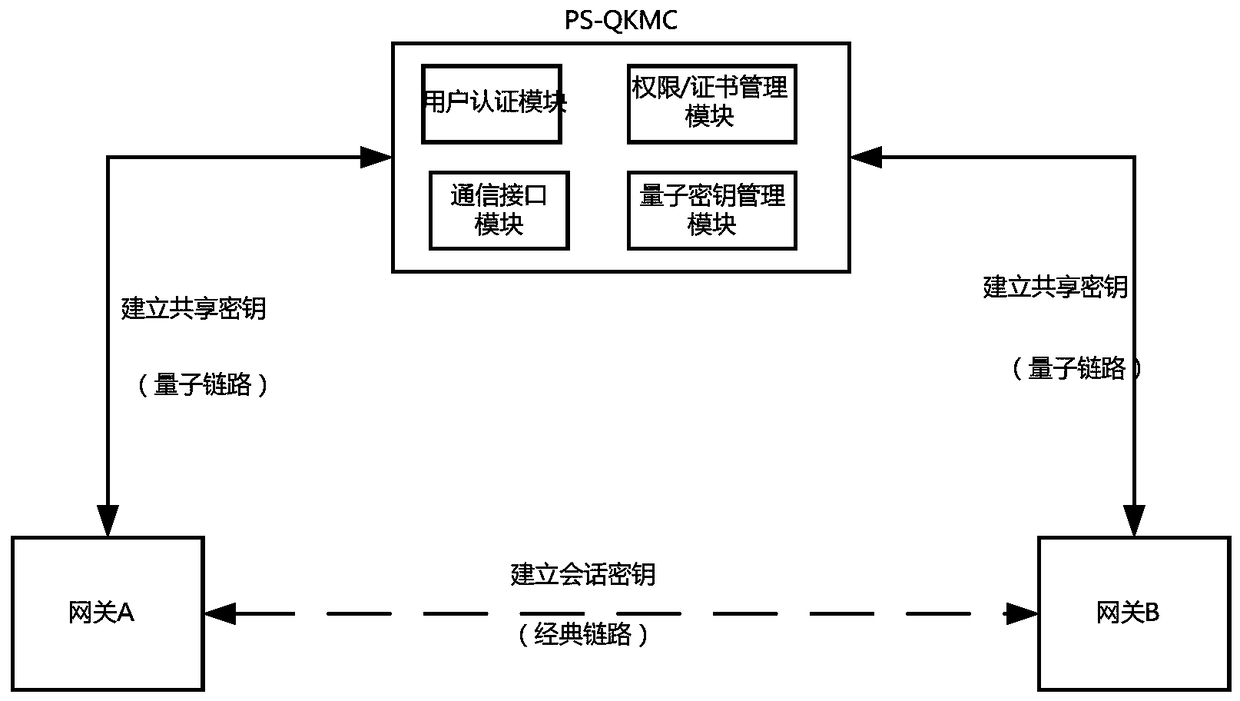
The invention provides a power special quantum encryption gateway system. The system comprises a power special quantum encryption gateway communicated with a gateway management device through a quantum link; the power special quantum encryption gateway is used for performing encryption communication through the quantum link or a classic link; a quantum secret key distributing device is integrally arranged on the power special quantum encryption gateway and comprises a vertical integration model and a transverse integration mode; the quantum link comprises a quantum secret key sending device and a quantum secret key receiving device which are connected with each other through an optical fiber or a free space; the gateway management device comprises a user authentication module, a user right / certificate management module, a quantum secret key management module and a communication interface module. Compared with the prior art, the power special quantum encryption gateway system provided by the invention is capable of synchronously supporting the traditional mode encryption function and the quantum mode encryption function, and capable of providing unconditional information security assurance for the power system data transmission under the quantum mode, and convenient for the large-scale deployment and industrial practicality of the power special quantum encryption network.
Owner:STATE GRID CORP OF CHINA +3
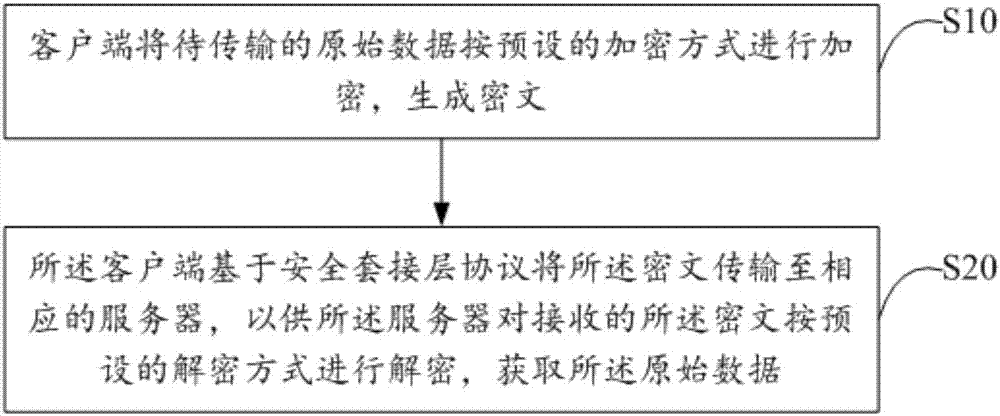
Data transmission method based on network communication, client and server
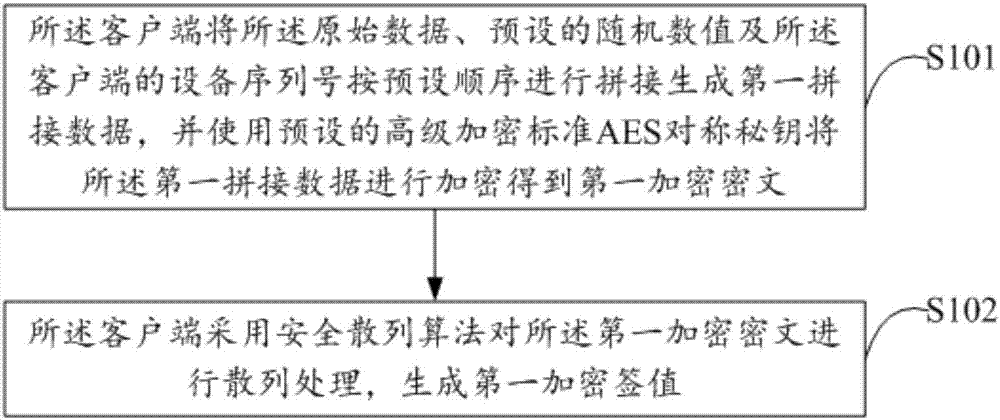
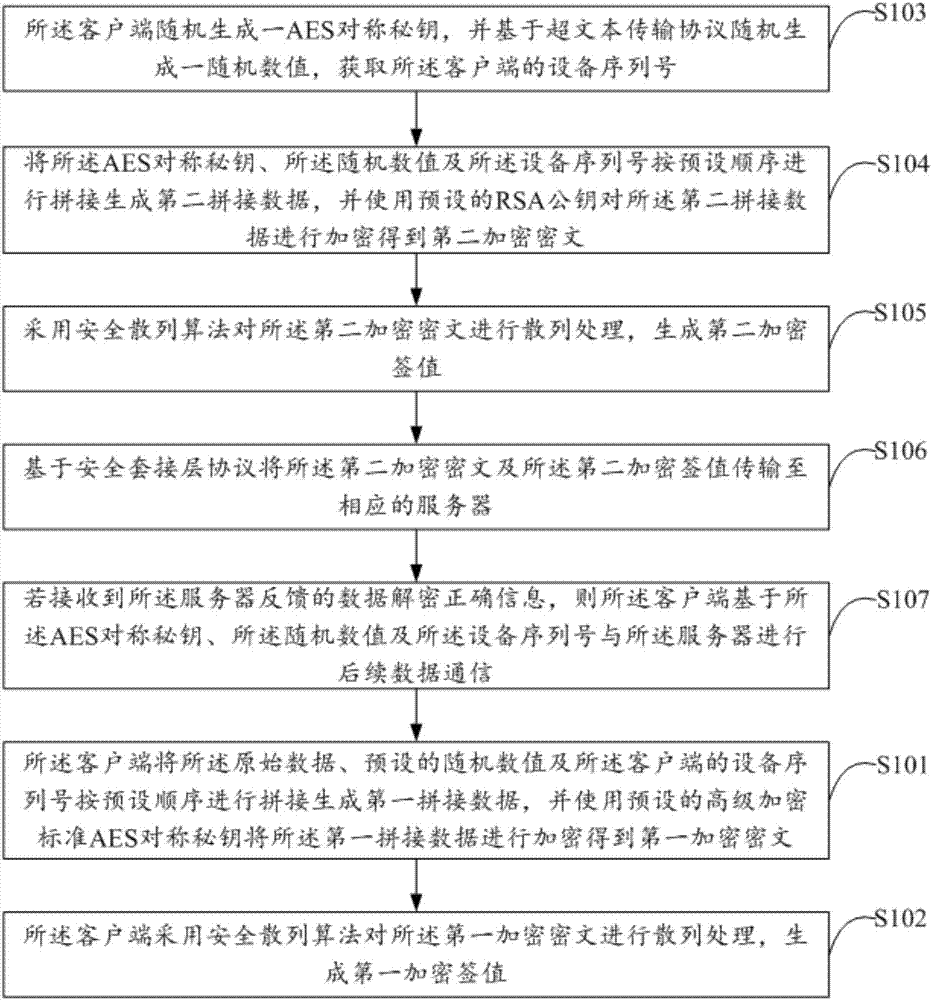
ActiveCN107294937APrevent leakageImprove data transmission securityEncryption apparatus with shift registers/memoriesPublic key for secure communicationPlaintextCiphertext
The invention discloses a data transmission method based on network communication. The method comprises the following steps: the client encrypts to-be-transmitted original data according to a preset encryption mode, and a ciphertext is generated; the client transmits the ciphertext to the corresponding server based on a secure socket layer protocol to enable the server to decrypt the received ciphertext according to a preset decryption mode, and the original data are acquired. The invention also discloses a client and a server. The to-be-transmitted original data themselves are subjected to encryption processing, the ciphertext after the original data are encrypted is transmitted based on an SSL security defense strategy, and double encryption defense is carried out from an external network communication layer and the original data themselves. Even if the SSL security defense strategy fails completely, as the original data themselves are subjected to encryption processing, plaintext exposure is not caused, leakage of the original data is prevented, and the data transmission security based on network communication is effectively improved.
Owner:PING AN TECH (SHENZHEN) CO LTD
Digital public transport information publishing and cluster controlling method and device
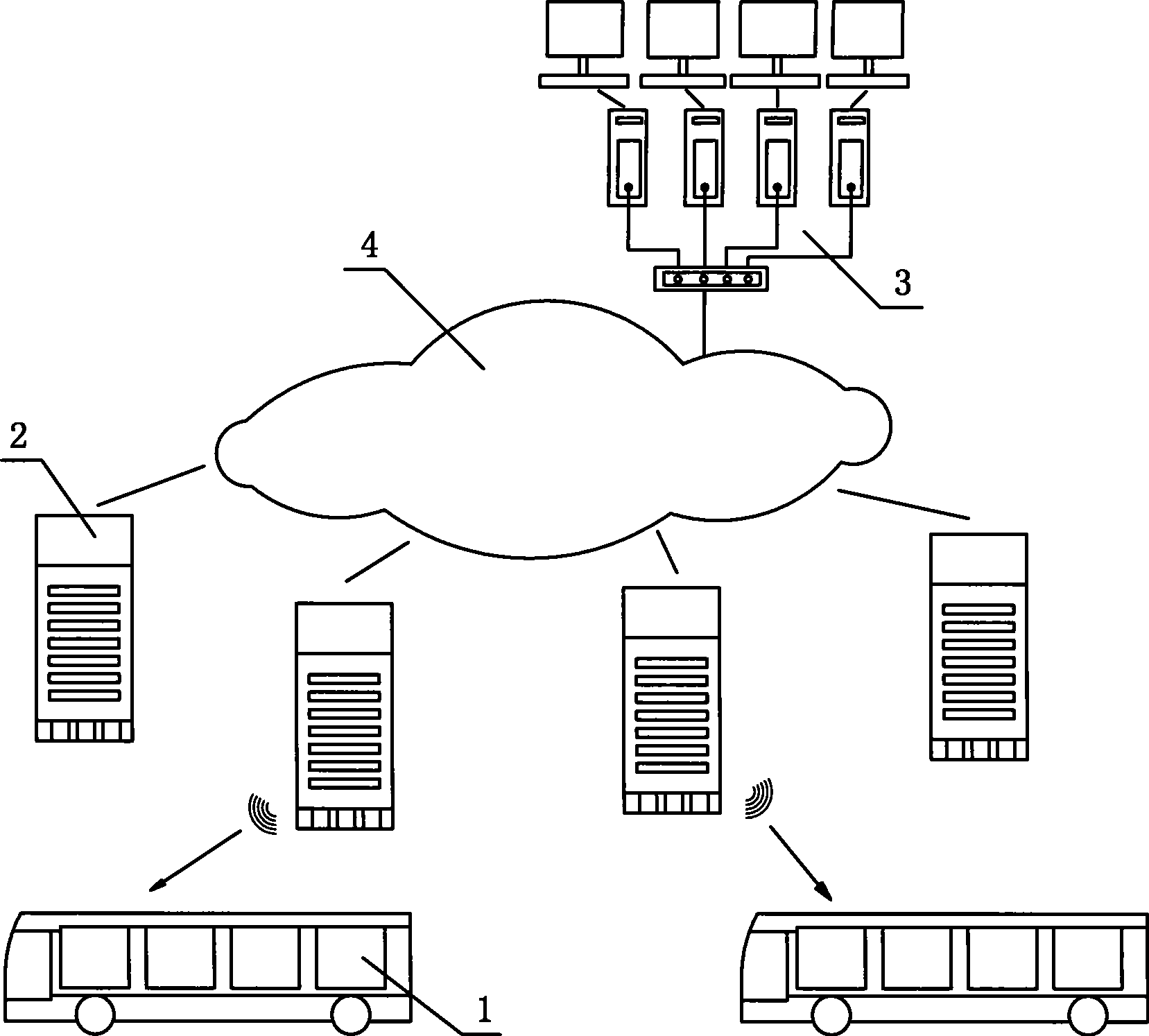
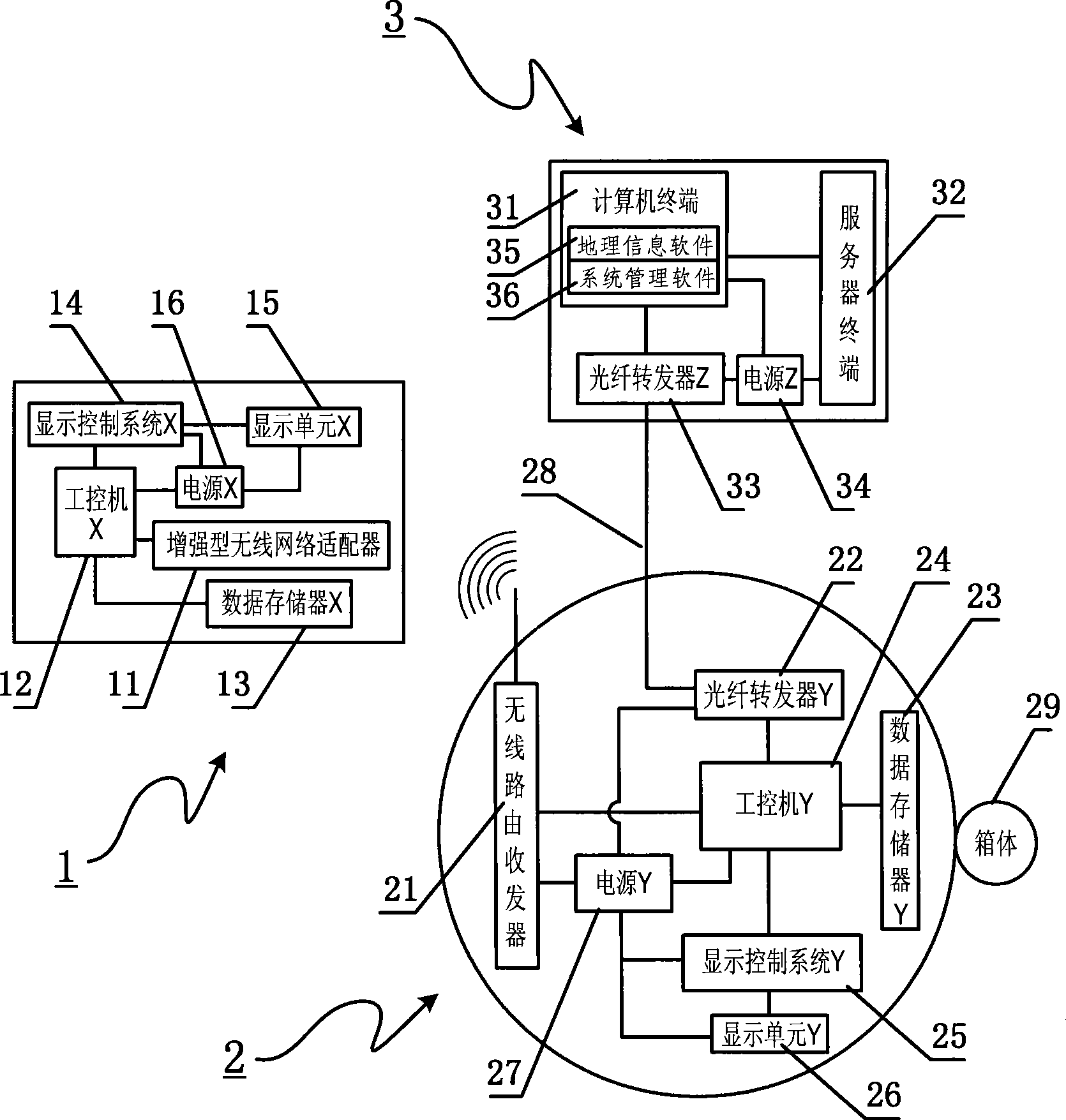
InactiveCN101398975AWide coverageIntegrity guaranteedDetection of traffic movementTelecommunications linkEngineering
The invention relates to a method used for digital bus information releasing and group control and a device thereof. The technical measure comprises the following steps: a vehicle terminal system, an electronic station board system and a vehicle technical information management centre are arranged, the electronic station board system is the vehicle technical information management centre are connected into a bi-directional communication network by line link, the vehicle terminal system transmits the vehicle information to the electronic station board system in a wireless communication, the electronic station board system reports the information to the vehicle technical information management centre, the bus coming to station at each station can be found out by inquiring a database, the station arriving time of the bus is calculated according to experimental data including average running speed, average running time between the stations and the like, finally, the arriving time is fed back to the electronic station board system, and the arriving time is displayed to the waiting passengers in a digital way. The method can effectively solve the problems of bus reduction in city and dispatching, information releasing, passenger facilitation, intelligent management control and the like. Therefore, the method realizes intelligent bus dispatching.
Owner:JIANGSU HANDSON INTELLIGENT TECH CO LTD
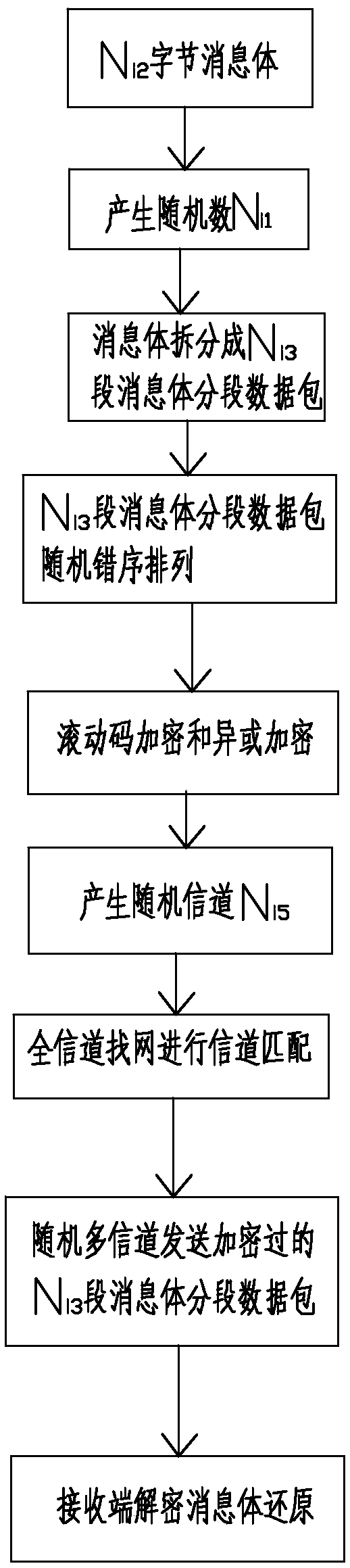
Encrypted data transmission method
ActiveCN108989324AImprove data transmission securityEliminate potential safety hazardsTransmissionNetwork packetByte
FIELD OF THE INVENTION that present invention relate to the field of communications technology, A method for encrypt data transmission comprises the following steps: S1, a message body with the numberof bytes set as Ni2 is transmitted freely in Ni4 channels, a random number Ni1 is generated by using a timing counter, and the message body with the number of bytes set as Ni2 to be transmitted is randomly divided into Ni3 segment message body segmented data packets according to the random number Ni1; S2, the Ni3 segment message body segmented data packets separated in the previous step are randomly misordered by an encoder, and then are dynamically encrypted and transmitted in a random multi-channel manner; 3, message body is restored, wherein the receiving end receives the segmented data packets of each segment of the message body, stores and decrypts the true value of the restored data through a decoder, namely, reorganizing the segmented data of each segment of the message body into complete message body data according to a packet sequence number and a misordering rule, and sequentially splicing the segmented data of each segment of the message body. The invention solves the problem that the encryption mode of the existing intelligent security system is simple and easy to cracke and the intercepted information has the hidden danger of safety.
Owner:QUANZHOU HEYI ELECTRONICS CO LTD
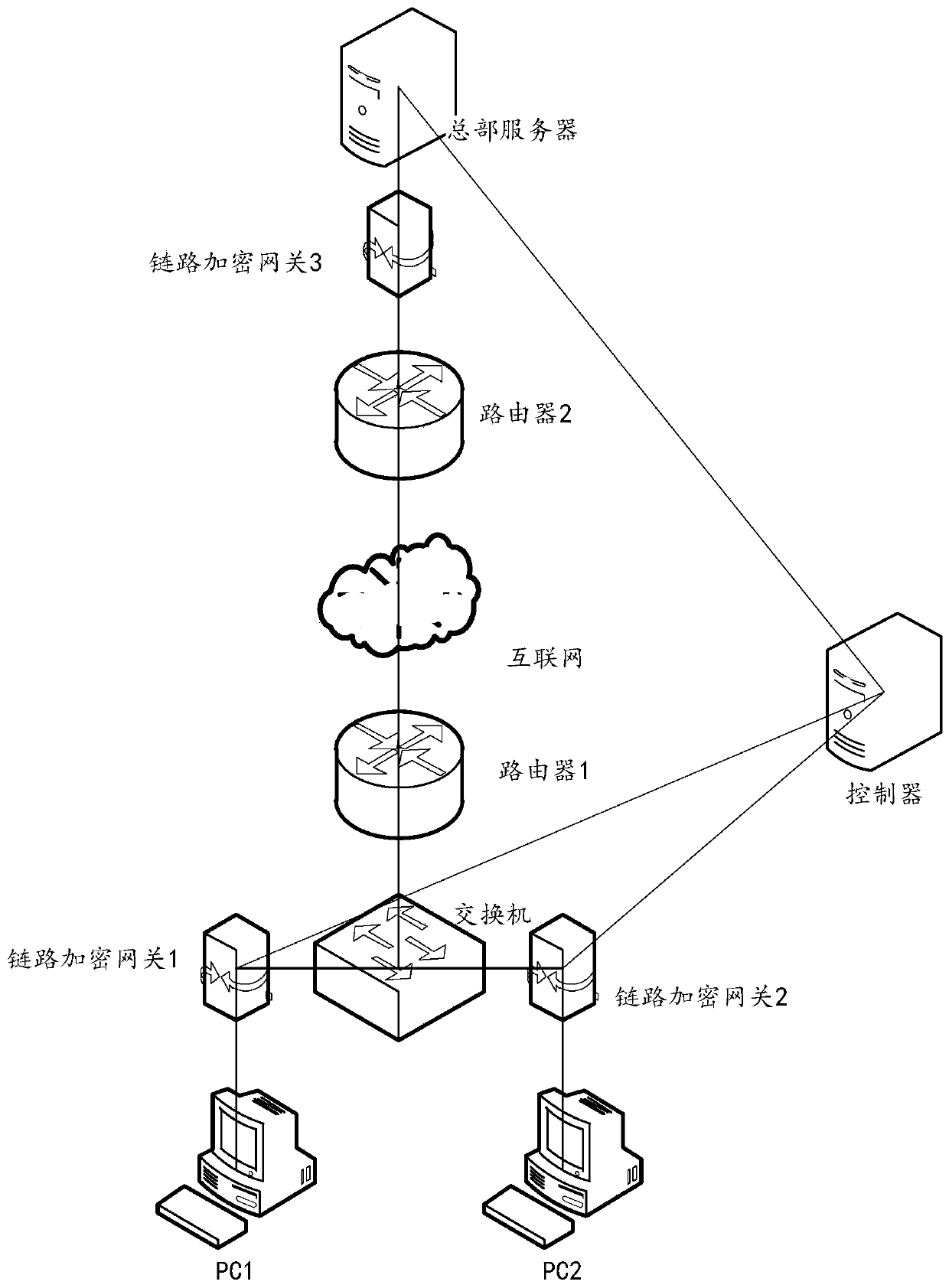
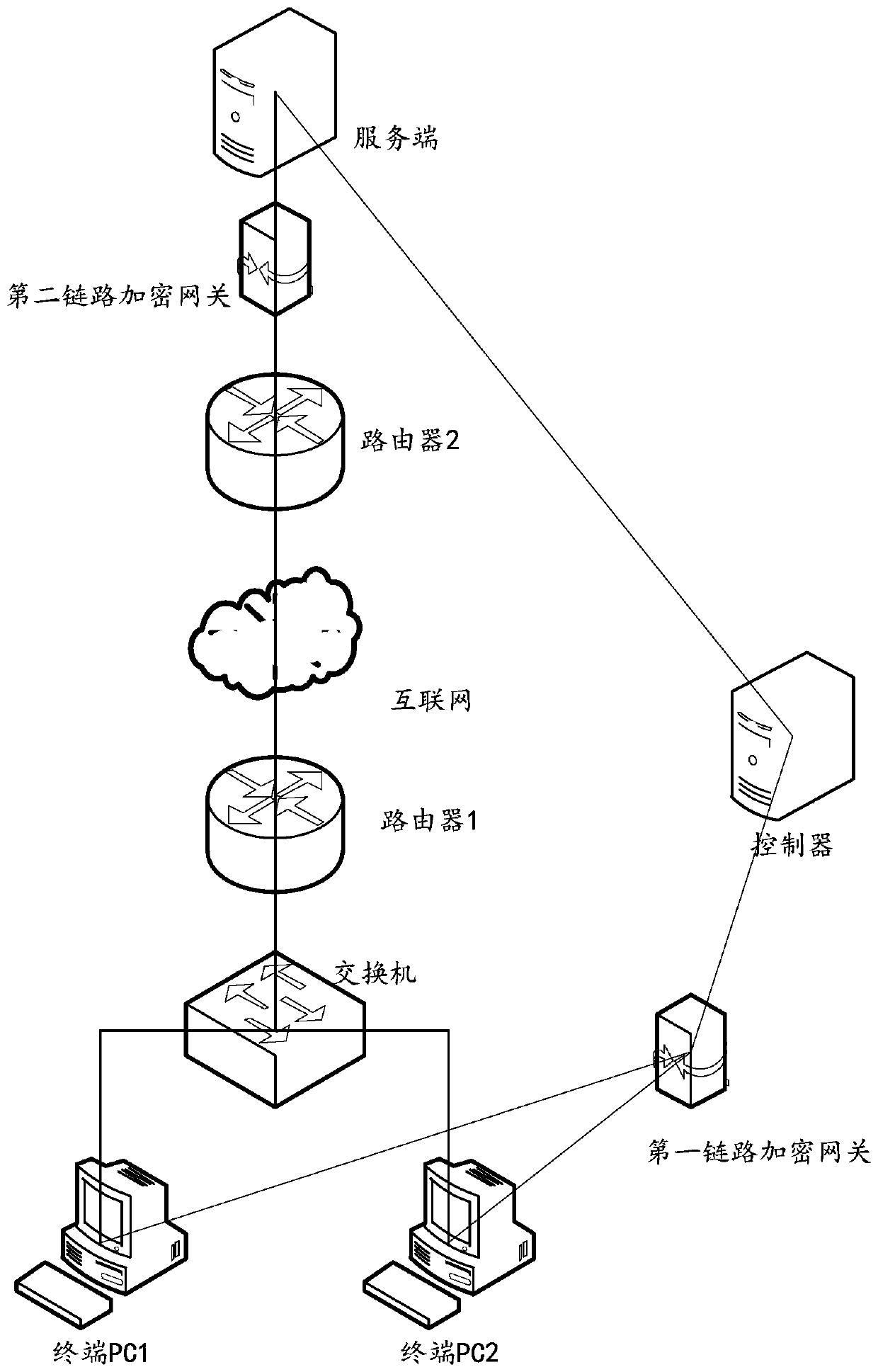
Safe data transmission method, system and device and storage medium
The invention provides a data security transmission method, system and device and a storage medium, and relates to the technical field of network security. The method is applied to a first link encryption gateway in communication connection with one or more terminals, the first link encryption gateway is also in communication connection with a second link encryption gateway, and the method comprises the following steps: receiving a first encrypted message sent by a terminal; determining that the first encrypted message passes the authentication; decrypting the first encrypted message to obtaina first decrypted message; encrypting the first decrypted message based on an encryption mode agreed with a second link encryption gateway to obtain a second encrypted message; and sending the secondencrypted message to a second link encryption gateway through a secure channel between the second encrypted message and the second link encryption gateway, so that the second link encryption gatewaydecrypts the second encrypted message and sends the decrypted second encrypted message to the server. According to the method, a plurality of terminals share one link encryption gateway, and an independent link encryption gateway does not need to be arranged at each terminal, so that the hardware cost is reduced.
Owner:MAIPU COMM TECH CO LTD
Data separation method and system
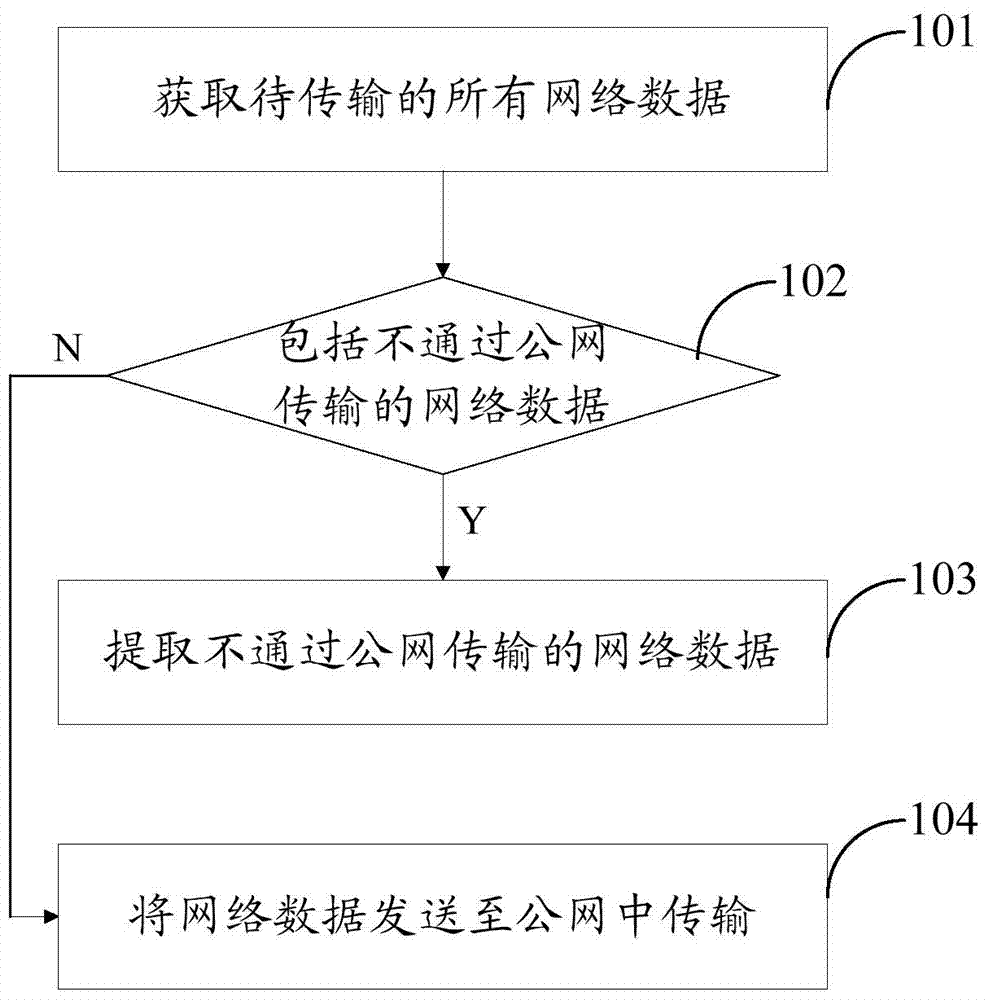
InactiveCN103618661AAchieve separationReduce distractionsNetworks interconnectionPrivate networkPublic network
The invention provides a data separation method and a data separation system. The data separation method comprises the following steps: acquiring all network data to be transmitted; judging that whether all the network data comprises network data which is not transmitted through a public network or not, if so, extracting the network data which is not transmitted through the public network. According to the data separation method provided in the invention, whether all the network data comprises the network data which is not transmitted through the public network or not is judged, so that the network data which is not transmitted through the public network is determined and is extracted from all the network data of users, and the network data which is not transmitted through the public network is separated from network data transmitted through the public network. Furthermore, a virtual private network can be established between a terminal and a target server and is specially used for transmitting the extracted network data, and the extracted network data is transmitted between the terminal and the target server through the virtual private network.
Owner:SICHUAN XUNYOU NETWORK TECH
Powerline remote meter reading repeating method
InactiveCN101673456AOccupies less bandwidthImprove data transmission securityElectric signal transmission systemsData transmissionRemote meter reading
The invention provides a powerline remote meter reading repeating method which is as follows: the mode set of a collector and a concentrator in the prior art is not changed, only one or a plurality ofrepeaters are additionally arranged on the powerline according to the actual condition, and wired or wireless network transmission data are adopted in the repeaters. The method can realize the function of data transmission under the condition that the distance between the collector and the concentrator is long, and only carry out data retransmission between the collector and the concentrator witha repeating requirement to increase the network efficiency.
Owner:SHANGHAI DIANJI UNIV
Security control method used for cloud platform network
ActiveCN105591928APrevent eavesdroppingPrevent tamperingUser identity/authority verificationData switching networksHash functionControl data
The invention provides a security control method used for a cloud platform network. The security control method comprises the steps that: a controller of the cloud network platform performs hash operation on application layer data in a control data message based on a preset security level value, a first currently valid secret key and a predetermined hash function when sending the control data message, so as to obtain an operation result; a first part of the operation result serves as authentication data and is attached to the control data message, and the second part of the operation result serves as a new first currently valid secret key to be used in the next hash operation; and the control data message with the authentication data is sent to a target node in the cloud network platform, and the target node adopts an algorithm corresponding to the hash operation adopted by the controller to authenticate the authentication data. The security control method used for the cloud platform network disclosed by the invention has high security level.
Owner:CHINA UNIONPAY
Data security transmission method based on air-sea cross-domain communication gateway and storage medium
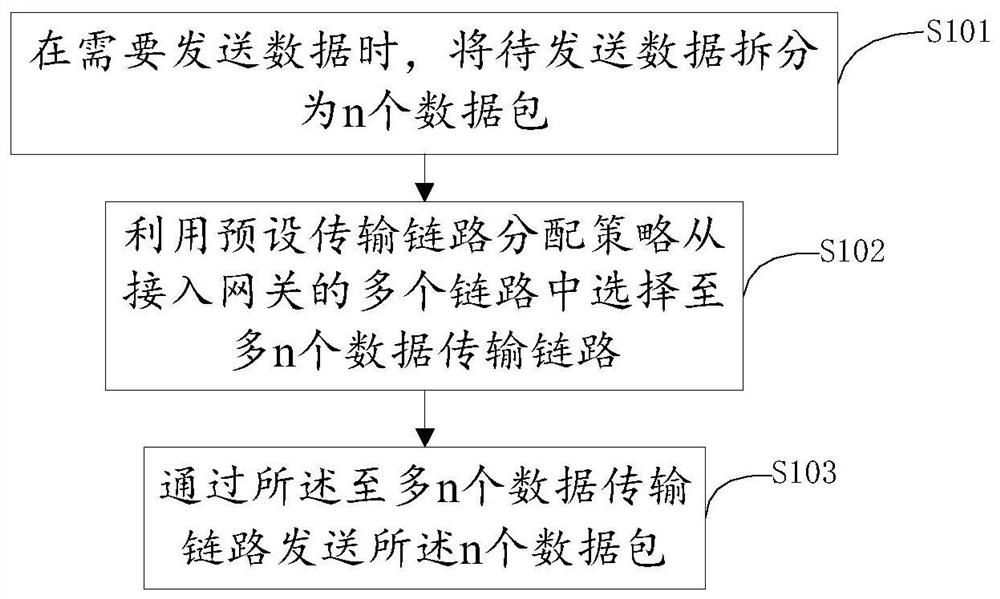
The invention discloses a data security transmission method based on an air-sea cross-domain communication gateway and a storage medium, and the method comprises the steps: splitting to-be-sent data into n data packets when the data needs to be sent; selecting at most n data transmission links from a plurality of links of the access gateway by using a preset transmission link allocation strategy; and sending the n data packets through the at most n data transmission links. According to the method provided by the invention, data splitting is realized, and the data are transmitted through a plurality of data transmission links, so that the data transmission security of the air-sea cross-domain communication gateway is effectively improved.
Owner:CHINA ACADEMY OF ELECTRONICS & INFORMATION TECH OF CETC
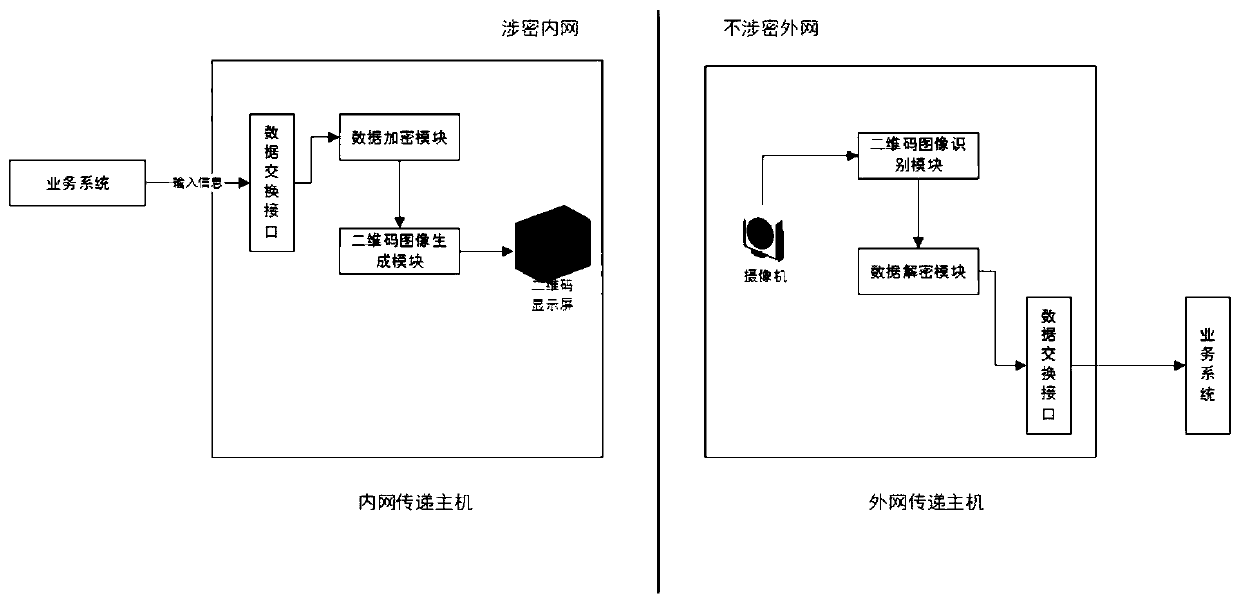
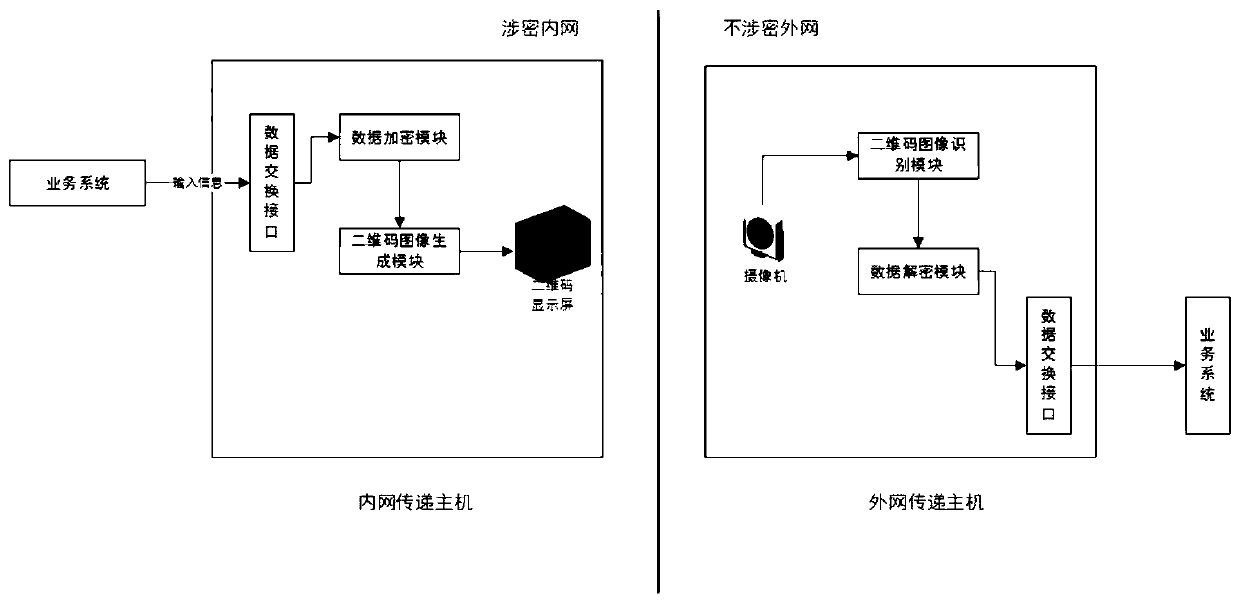
Two-dimensional code big data secure transmission device based on dynamic multistage encryption and decryption
ActiveCN110011993AAddress unsafe technical issuesIncrease capacityTransmissionRecord carriers used with machinesComputer hardwareSecure transmission
The invention discloses a two-dimensional code big data secure transmission device based on dynamic multistage encryption and decryption, and the device comprises a first data exchange interface whichis used for obtaining and sending to-be-exchanged data information; a data encryption module which is used for receiving the to-be-exchanged data information and carrying out dynamic multistage encryption; a two-dimensional code image generation module which is used for encoding the encrypted to-be-exchanged data to generate a two-dimensional code image; a two-dimensional code display module which is used for displaying the two-dimensional code image; the acquisition module is used for acquiring the two-dimensional code image; a two-dimensional code image recognition module which is used forrecognizing the collected two-dimensional code image and extracting feature data information; a data decryption module which is used for carrying out dynamic multistage decryption on the two-dimensional code feature data information; and a second data exchange interface which is used for outputting the decrypted exchange data; according to the invention, the data transmission capacity and the datatransmission security are greatly improved.
Owner:HAOYUN TECH CO LTD
Network information security intelligent analysis early warning management system based on multi-dimensional analysis
PendingCN114826691AImprove operational efficiencyImprove data transmission securityPlatform integrity maintainanceSecuring communicationDetailed dataNetwork management
The invention discloses a network information security intelligent analysis early warning management system based on multi-dimensional analysis, and relates to the technical field of network information security. The problems that when a traditional network information security management system uses network transmission and data sharing as information storage and communication means, the system is lack of security protection, dangerous signals carried in transmission cannot be tracked in real time, and information updating is slow are solved. According to the network information security intelligent analysis and early warning management system based on multi-dimensional analysis, cross correlation and multi-angle combined analysis are performed on data in different dimensions through the supervision platform, high-level summarized data are refined and deepened into low-level detailed data, the accuracy of network information security analysis is greatly improved, and the network information security analysis efficiency is improved. Through a bottom layer driving filtering technology, various behavior operation requests are intercepted in real time, bad behaviors in data information operation are dynamically tracked, processed and detected, and a decision basis is provided for network management and optimization.
Owner:深圳市博博信息咨询有限公司
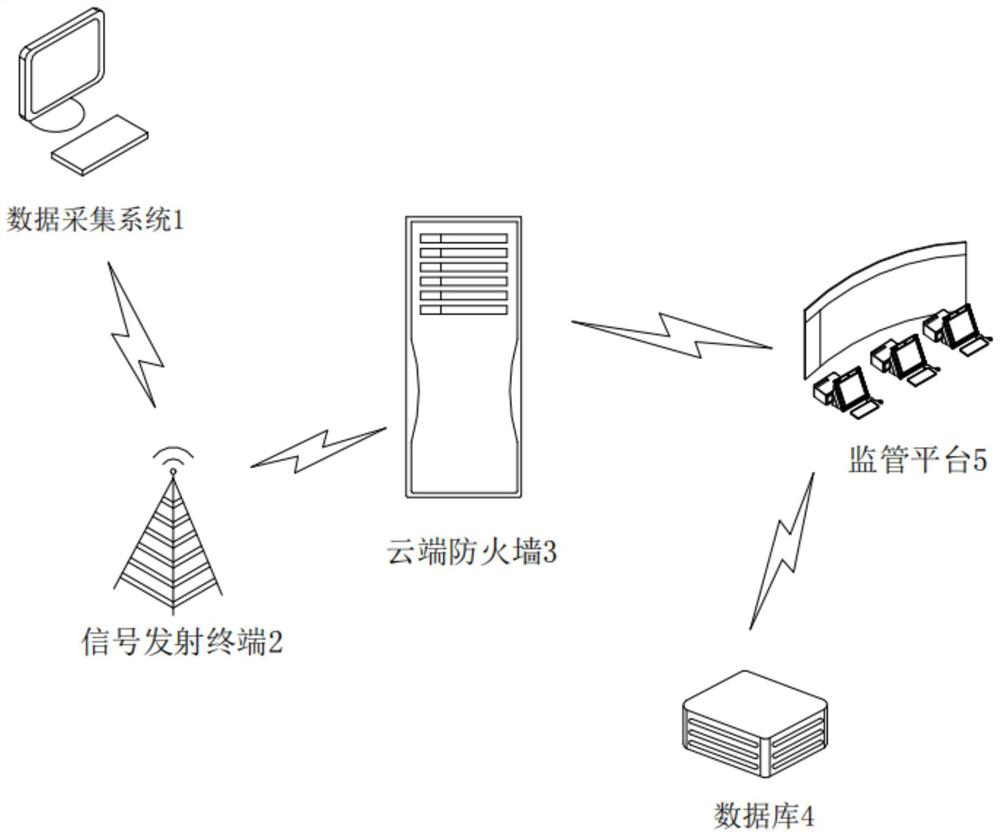
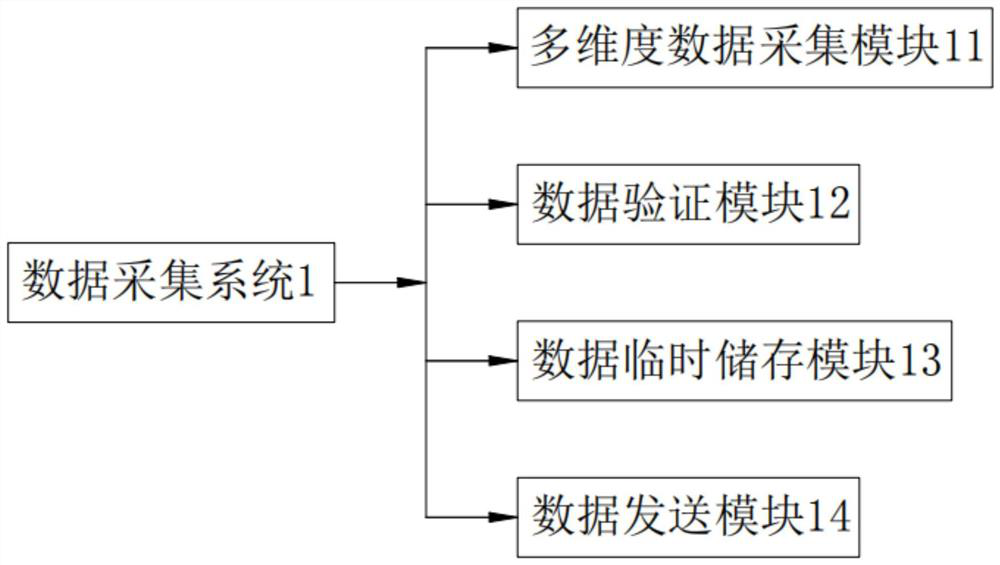
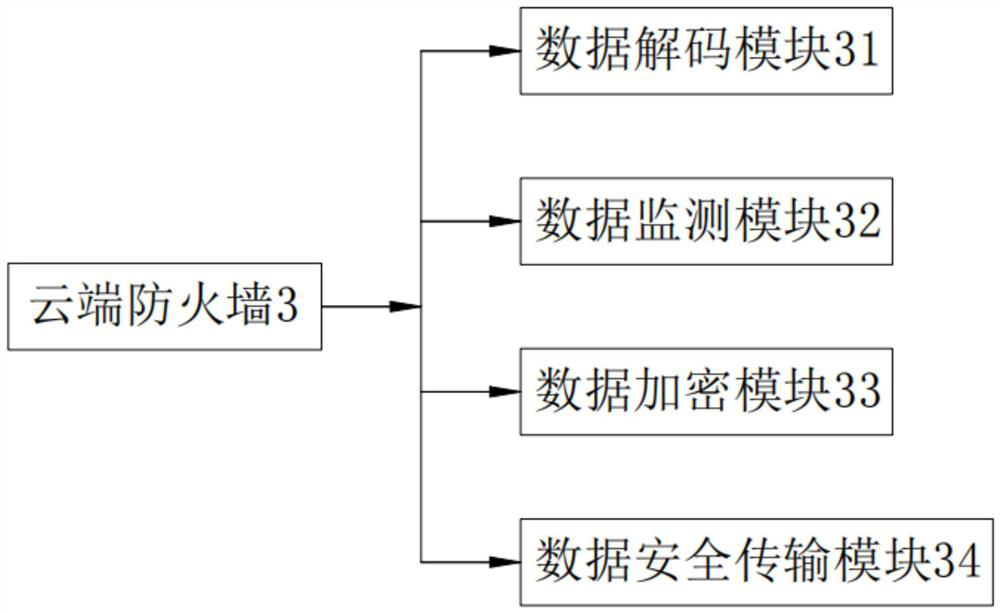
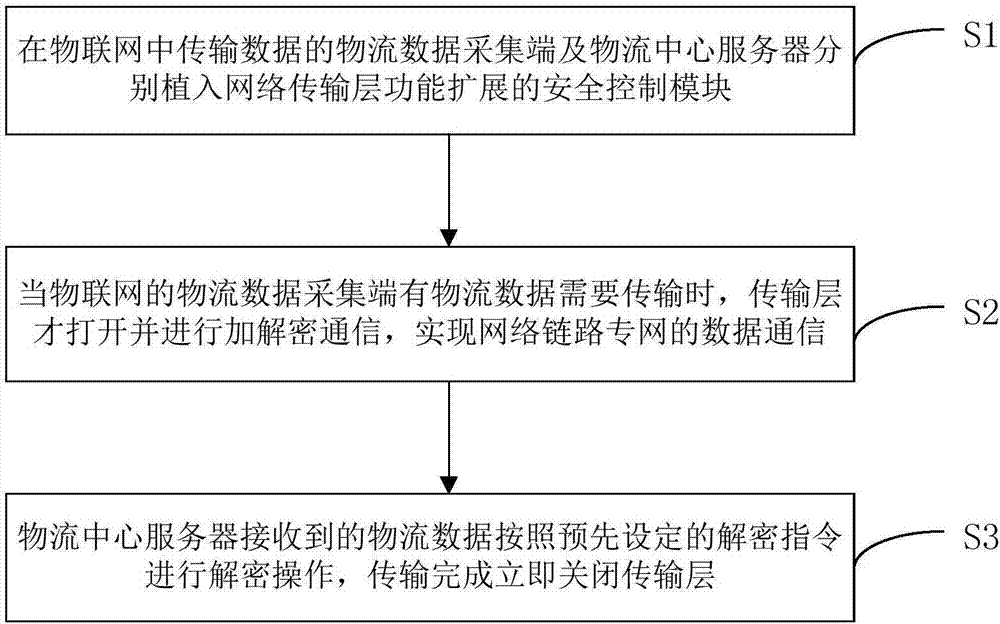
Efficient applicative safety private network transmission method and system based on internet of things
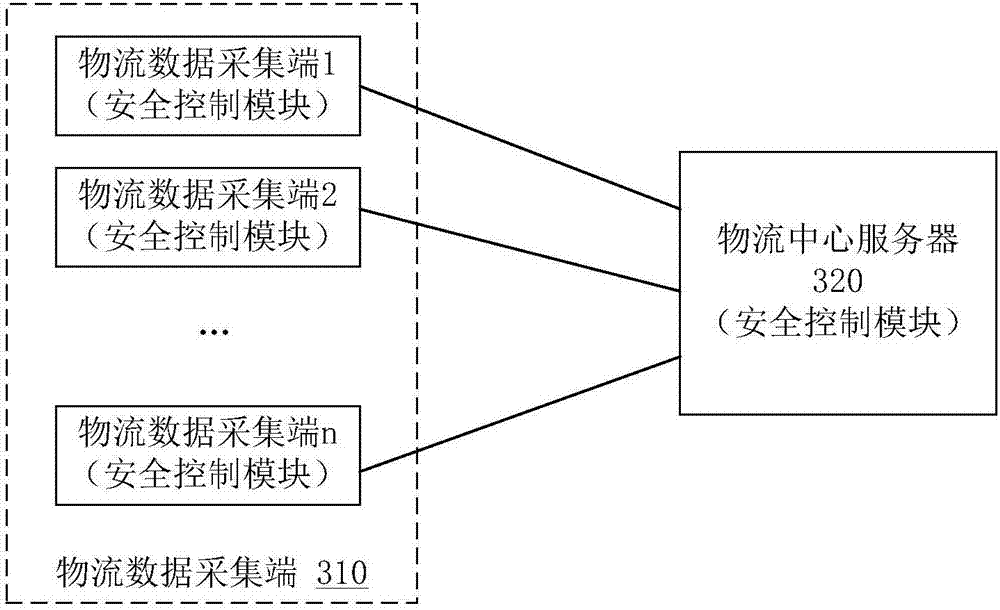
InactiveCN107147668AImprove securityImprove data transmission securityLogisticsTransmissionLogistics managementNetworked Transport of RTCM via Internet Protocol
The invention provides an efficient applicative safety private network transmission method and system based on the internet of things. The method comprises the following steps: respectively implanting a safety control module for network transmission function extension in a logistics data acquiring end for transmitting the data in the internet of things and a logistics center server, wherein the safety control module at least comprises the following settings: an initialization operation for reading in a configuration file to call kernel information and setting the logistics center server port information and the information in a communication port of the logistics data acquiring end; an opening / closing instruction operation for defining a data transmission function between the transmission layers; a sending / receiving instruction operation for defining the transmission layer to perform the data transmission; and a data encryption / decryption instruction operation for defining the transmission layer to perform the data transmission; when the internet of things has the data to transmit, the transmission layer is only opened and the encryption / decryption communication is performed to realize the data communication of the network link private network; the logistics data received by the logistics center server is decrypted according to a preset decryption instruction, and the transmission layer is immediately closed after the transmission is accomplished.
Owner:上海枫昱能源科技有限公司
Automobile ECU information monitoring system
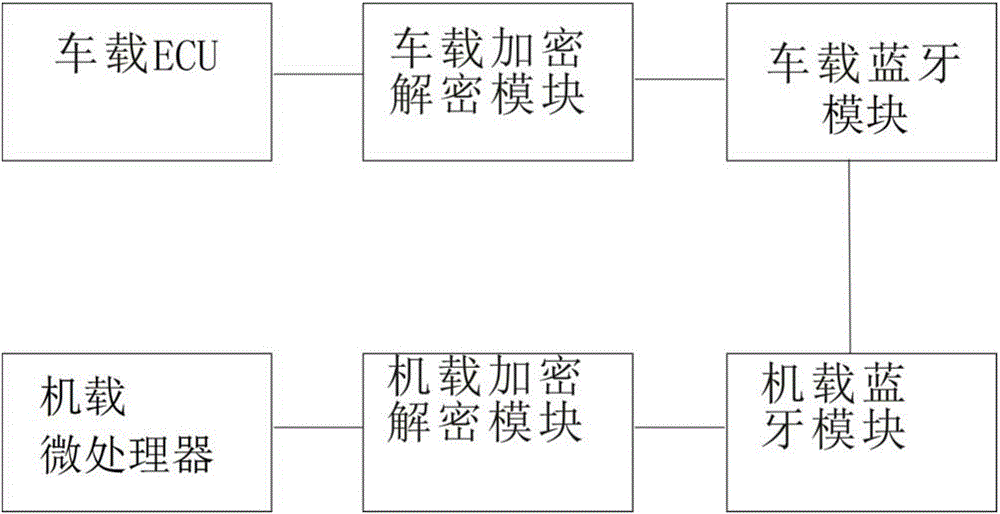
InactiveCN106230583ADoes not affect driving safetyImprove transmission securityKey distribution for secure communicationSecuring communication by chaotic signalsEngineeringComputer terminal
The invention provides an automobile ECU information monitoring system, relates to the technical field of automobile monitoring, and solves the technical problem of monitoring of automobile conditions. The system comprises a vehicle ECU, a vehicle bluetooth module, a vehicle encryption and decryption module, and a mobile terminal, the vehicle ECU is mutually connected with the vehicle encryption and decryption module through an SPI bus, the vehicle encryption and decryption module is mutually connected with the vehicle bluetooth module through a data bus, an airborne microprocessor, an airborne bluetooth module, and an airborne encryption and decryption module are arranged in the mobile terminal, the airborne microprocessor is mutually connected with the airborne encryption and decryption module through a data bus, the airborne encryption and decryption module is mutually connected with the airborne bluetooth module through a data bus, and the airborne bluetooth module is mutually connected with the vehicle bluetooth module in a bluetooth communication manner. The system is applicable to the monitoring of the operation condition of vehicles.
Owner:成都安程通科技有限公司
Distributed covering network
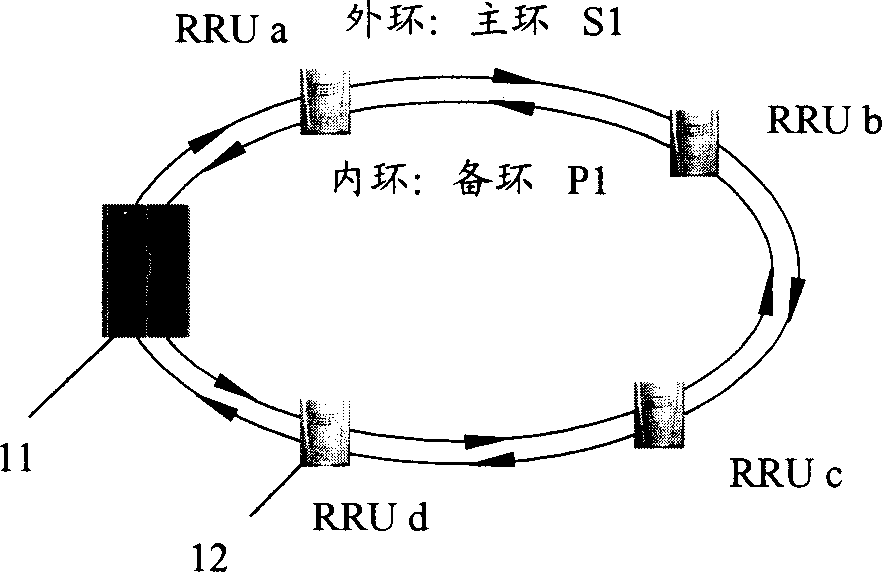
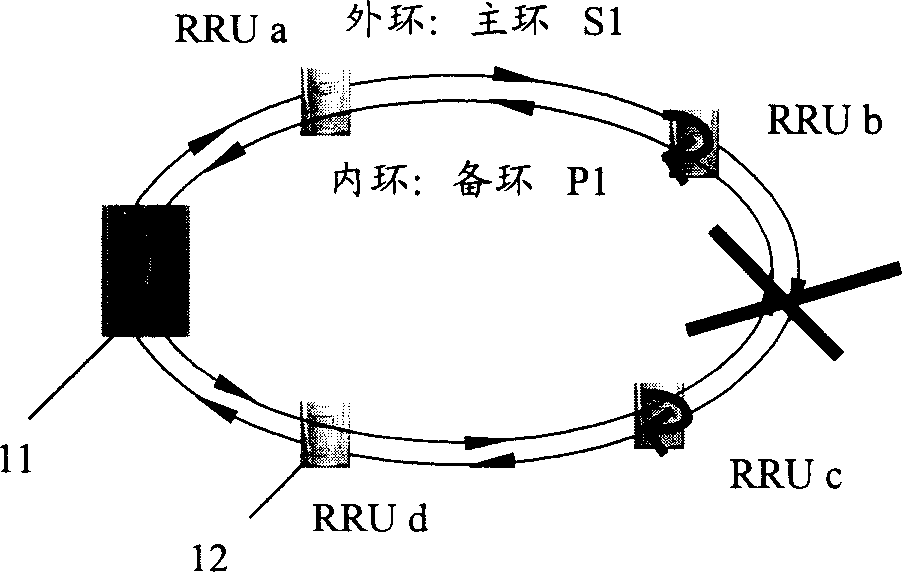
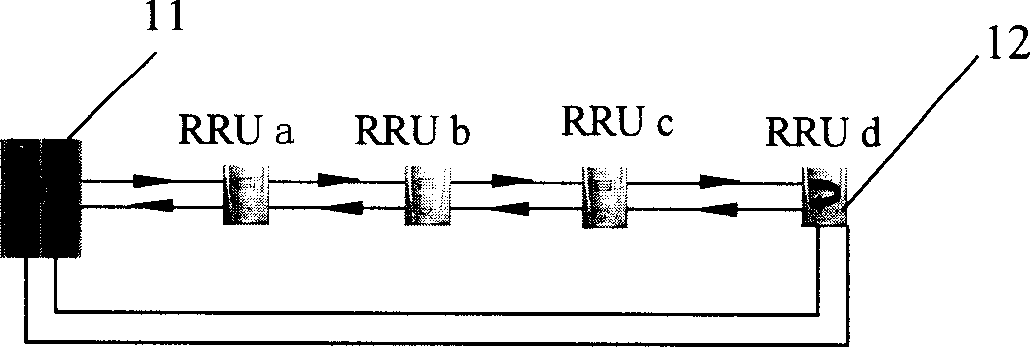
InactiveCN1780456AImprove data transmission securityReduce adverse effectsData switching by path configurationRadio-over-fibreTime delaysStream data
The invention consists of a host base station and several radio frequency-far end modules. Each radio frequency far end module connects to antenna. Several radiofrequency far end modules are concatenated one-by-one through optical fiber in turn, and the one of radio frequency far end module in last stage connects to the host base station. The invention makes the up stream and down stream data transmitted between RRU and host base station have same time delay. The data transmitted in the distributing overlay network has high security level, and when the break point appears in transmission link, the RRU behind the break point is connected with host base station through redundant optical fiber by new chain type network.
Owner:HUAWEI TECH CO LTD
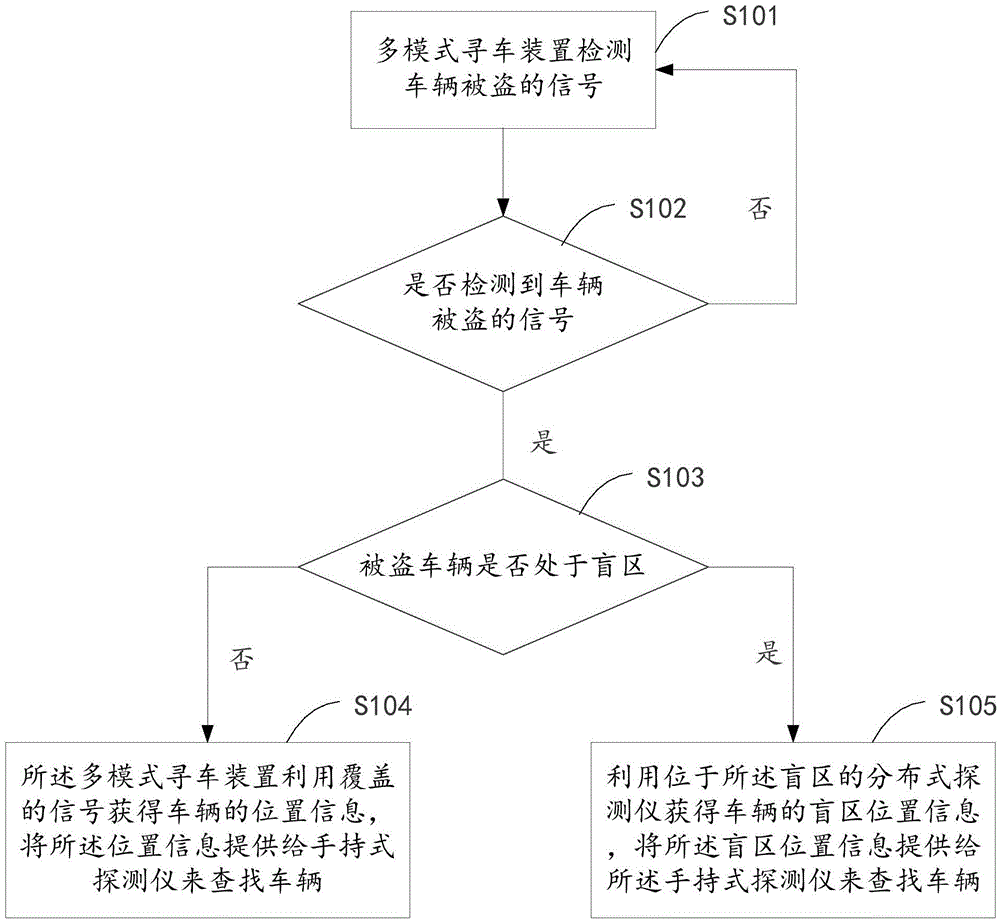
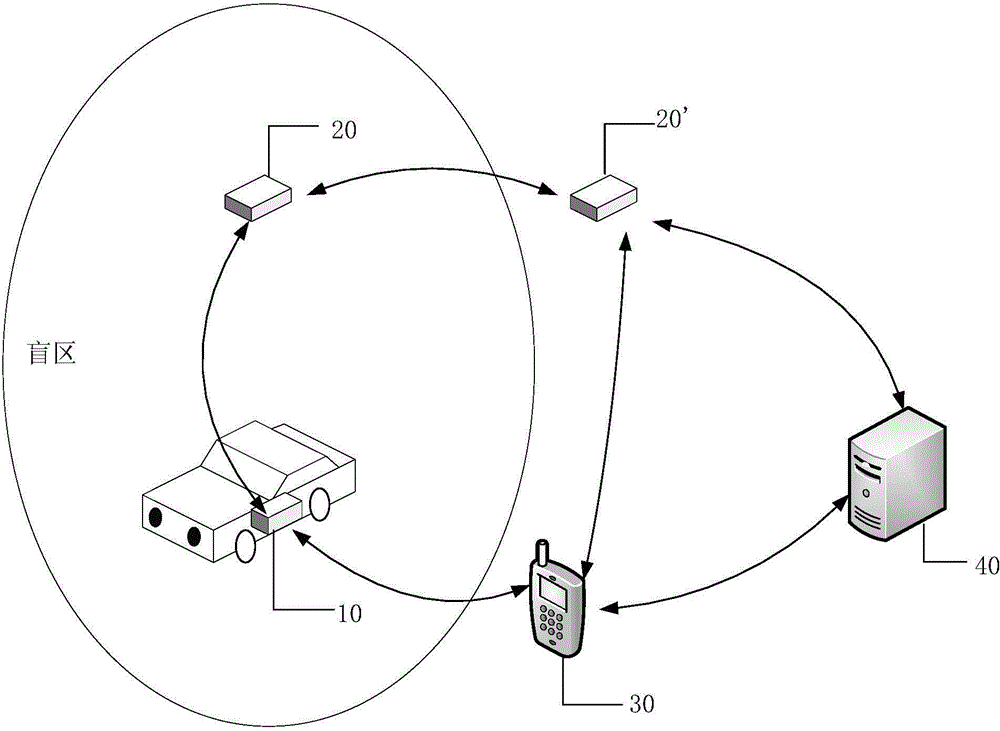
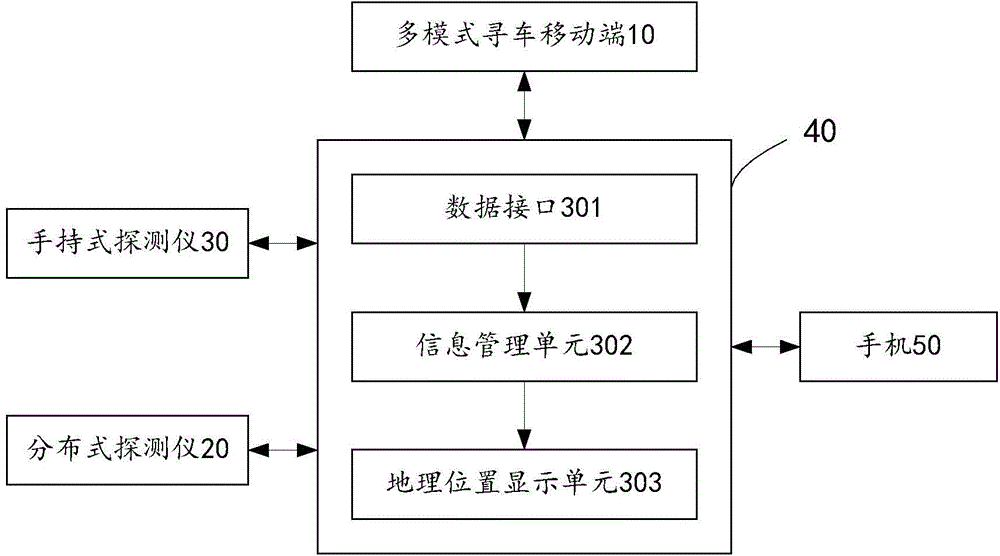
Multi-mode car searching method, multi-mode car searching device and multi-mode car searching system
The invention relates to a multi-mode car searching method, a multi-mode car searching device and a multi-mode car searching system. The method comprises the following steps: when a multi-mode car searching device which is installed on a car detects a signal that the car is stolen, starting positioning of the stolen car; if the car is located in a signal covering region, obtaining the position information of the car by the multi-mode car searching device by virtue of a covered signal and providing the position information for a portable detector to search for the car; if the car is located in a blind region which is not covered by the signal, obtaining blind region position information of the car by using a distributive detector which is located in the blind region and providing the blind region position information to the portable detector to search for the car. According to the scheme provided by the invention, even if the stolen car is located in the blind region, the stolen car can be further accurately positioned.
Owner:江苏舟航物联网技术有限公司
Cross-domain security access and resource control method for virtualization equipment
ActiveCN111190700AImprove securityAdd authentication mechanismSoftware simulation/interpretation/emulationResource poolEngineering
The invention discloses a cross-domain security access and resource control method for virtualization equipment, and the method comprises the steps: firstly carrying out the authentication of each virtualization equipment platform at an access control center; secondly, after platform authentication is passed, each set of virtualization equipment needs to be authenticated in an access control center; thirdly, the platform needs to carry out authentication confirmation on the access control center every time the virtualization equipment is started; after secondary authentication and confirmationof the virtualization equipment, encrypting a virtualization equipment starting command line by using an asymmetric encryption technology, and sending the encrypted virtualization equipment startingcommand line to an access control center; and finally, the access control center decrypts the virtualization equipment operation command line by using an asymmetric encryption technology, and sends the decrypted virtualized equipment operation command line to the resource pool starting equipment after meeting the resource allocation rule. The security of each virtualization platform and the virtual equipment is effectively improved, the utilization rate of virtual the virtualization resources is improved, the risk that the command line is captured and cracked in the transmission process is reduced and the network data transmission security is greatly improved.
Owner:北京安盛联合科技有限公司
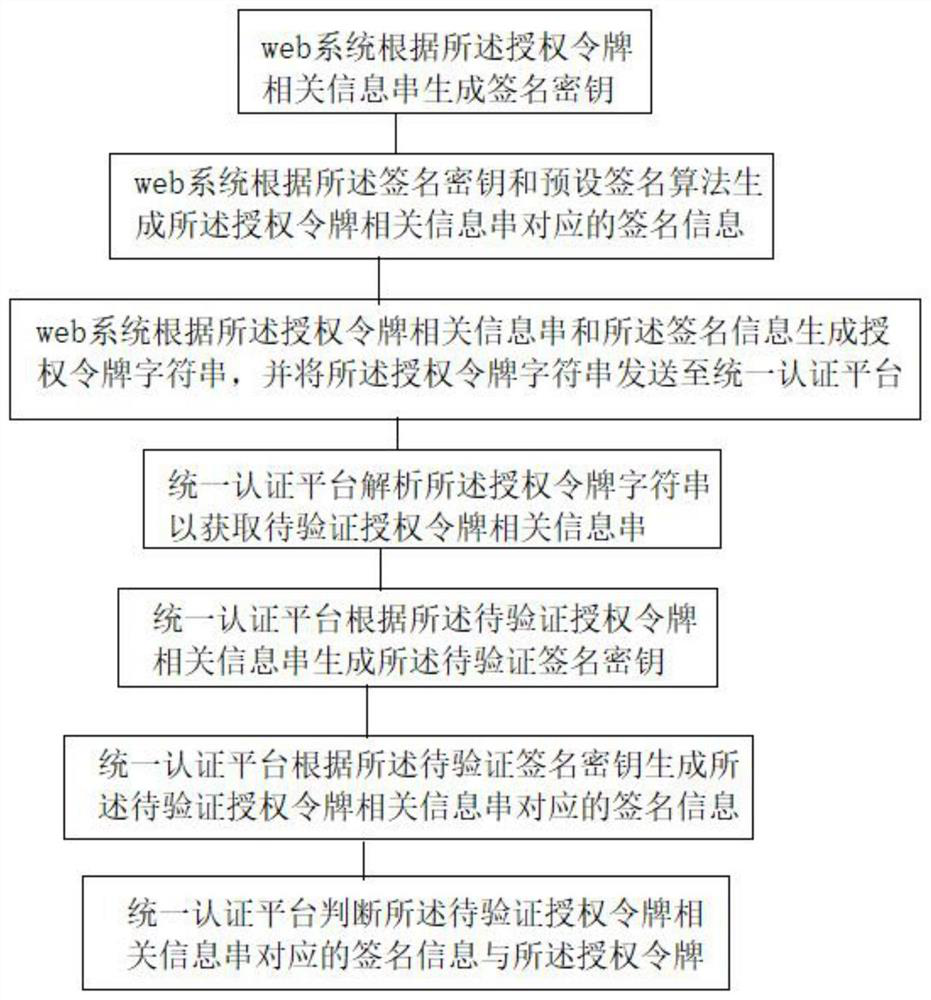
Method for session re-detection of token validity after web system accesses unified authentication platform
PendingCN111835743AGuaranteed validityImprove data transmission securityUser identity/authority verificationEngineeringData transmission
The invention provides a method for session re-detection of token validity after a web system accesses a unified authentication platform. The method comprises the following steps that: (1), a web system generates a signature key according to an authorization token related information string; (2) the web system generates signature information corresponding to the authorization token related information string according to the signature key and a preset signature algorithm; (3) the web system generates an authorization token character string according to the authorization token related information string and the signature information, and sends the authorization token character string to the unified authentication platform; (4) the unified authentication platform analyzes the authorization token character string to obtain an authorization token related information string to be verified; (5) the unified authentication platform generates the signature key to be verified according to the related information string of the authorization token to be verified. According to the method, the effectiveness of the authentication token in the use process can be ensured, and the data transmissionsecurity is improved.
Owner:BEIJING EYOU INFORMATION TECH CO LTD
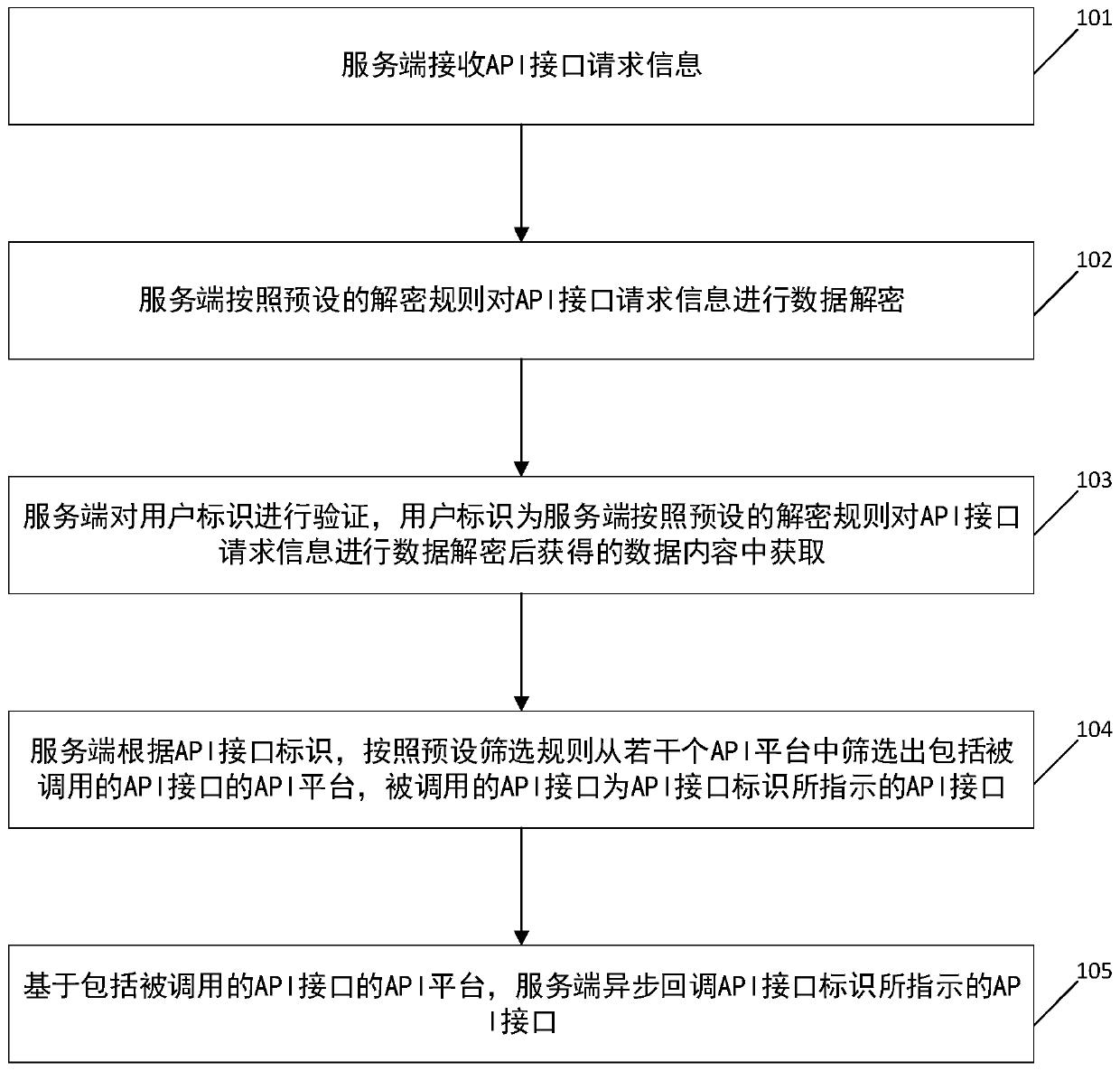
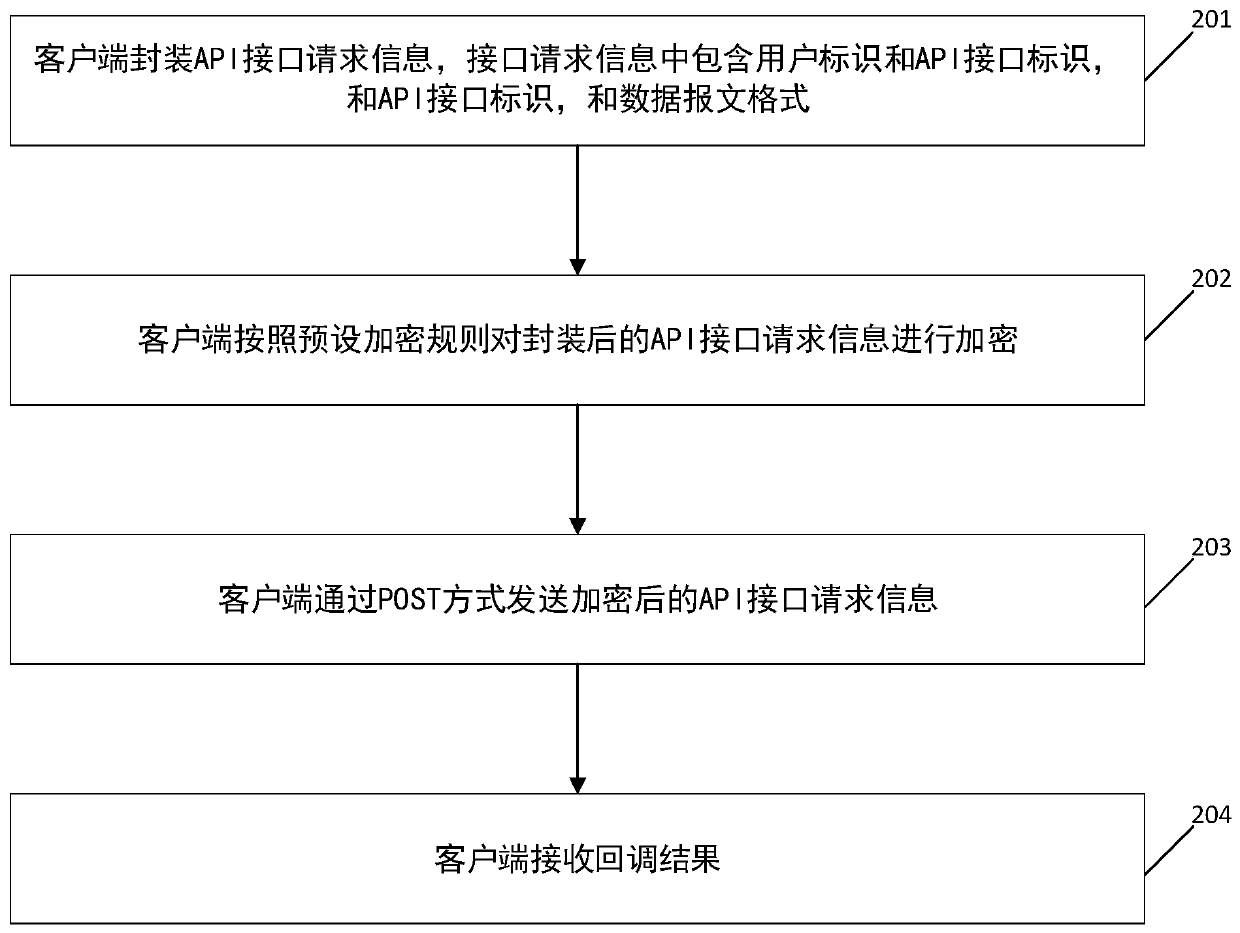
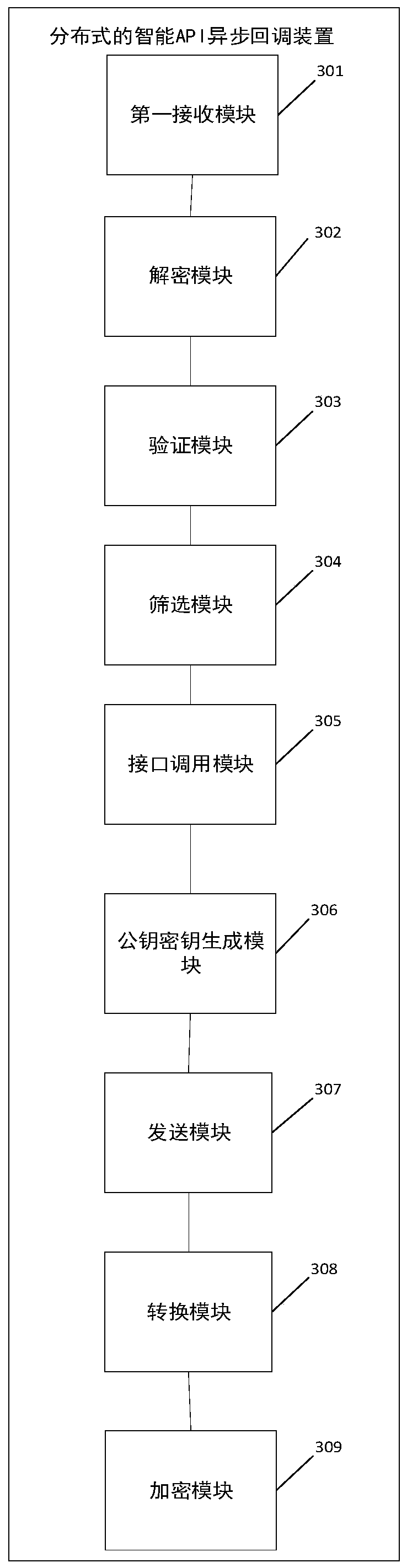
Distributed intelligent API asynchronous callback method and device
PendingCN110287037AQuick buildImprove data transmission securityInterprogram communicationUser identifierComputer science
The invention relates to the field of monitoring, in particular to a technology for monitoring service nodes through software, and particularly discloses a distributed intelligent API asynchronous callback method. The method includes: enabling a service end to receive API interface request information; performing data decryption on the API request information according to a preset decryption rule, wherein the decrypted API request information comprises an API identifier, a user identifier and a data message format; verifying the user identifier; according to the API identifier, screening out an API platform comprising a called API interface from a plurality of API platforms according to a preset screening rule, the called API interface being an API indicated by the API identifier; and asynchronously calling back the API indicated by the API identifier based on the API platform comprising the called API. The invention discloses a distributed intelligent API asynchronous callback device. The method has the advantages of high data security and function establishment flexibility.
Owner:PING AN TECH (SHENZHEN) CO LTD
Communication method, terminal and server
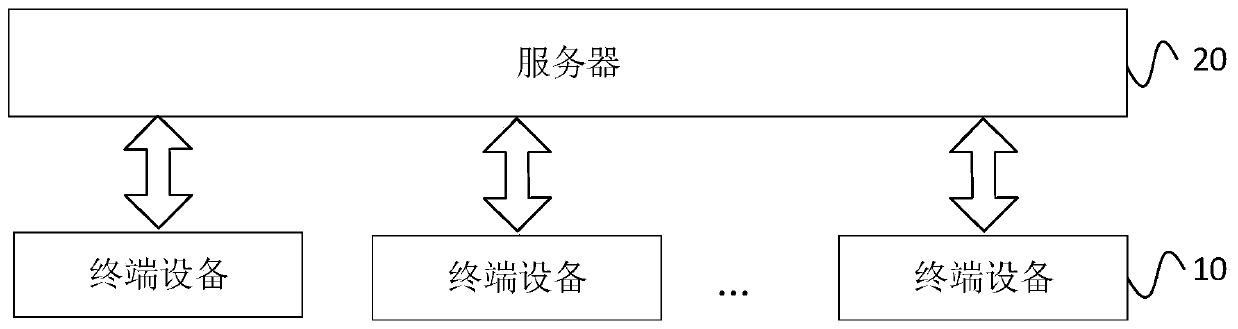
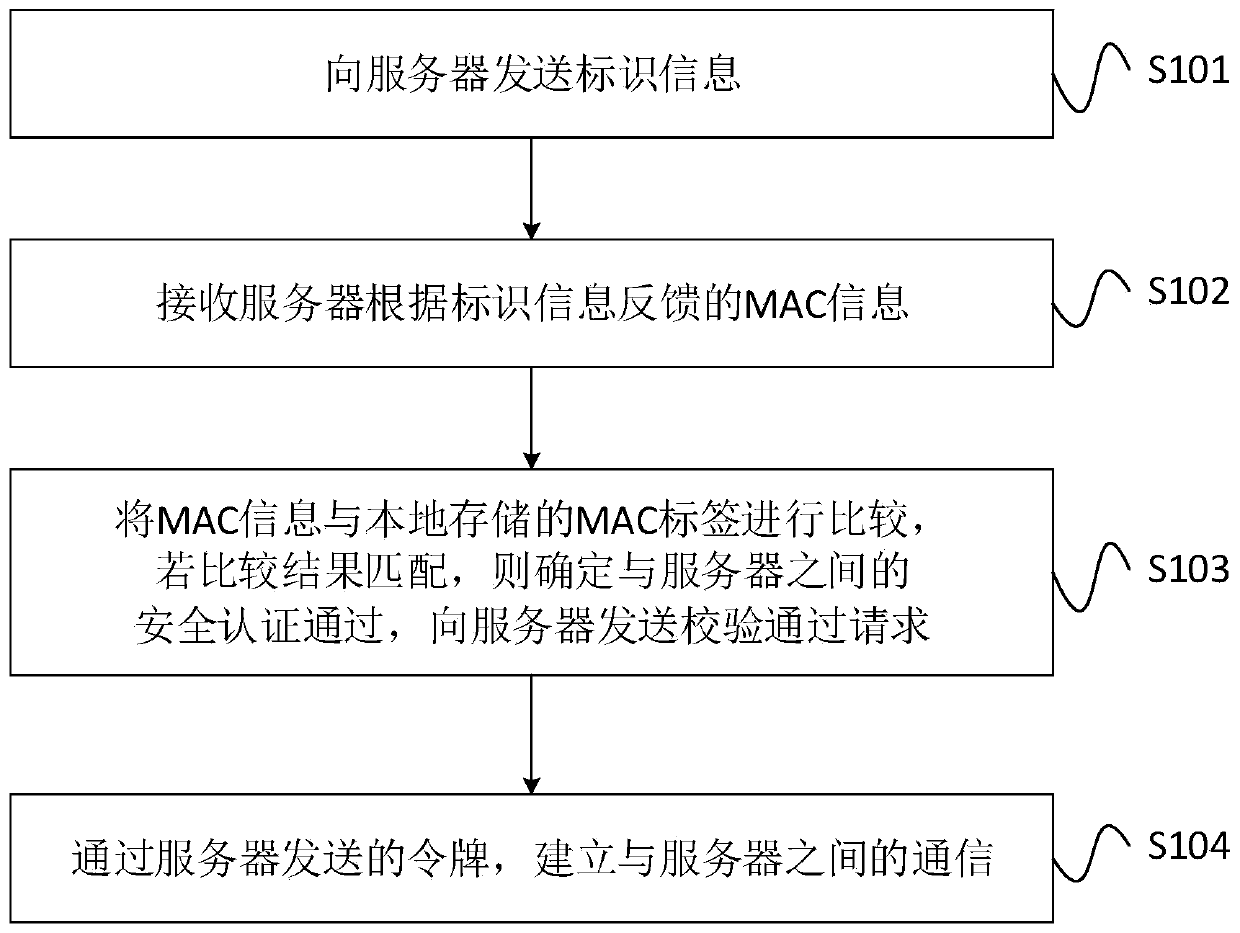
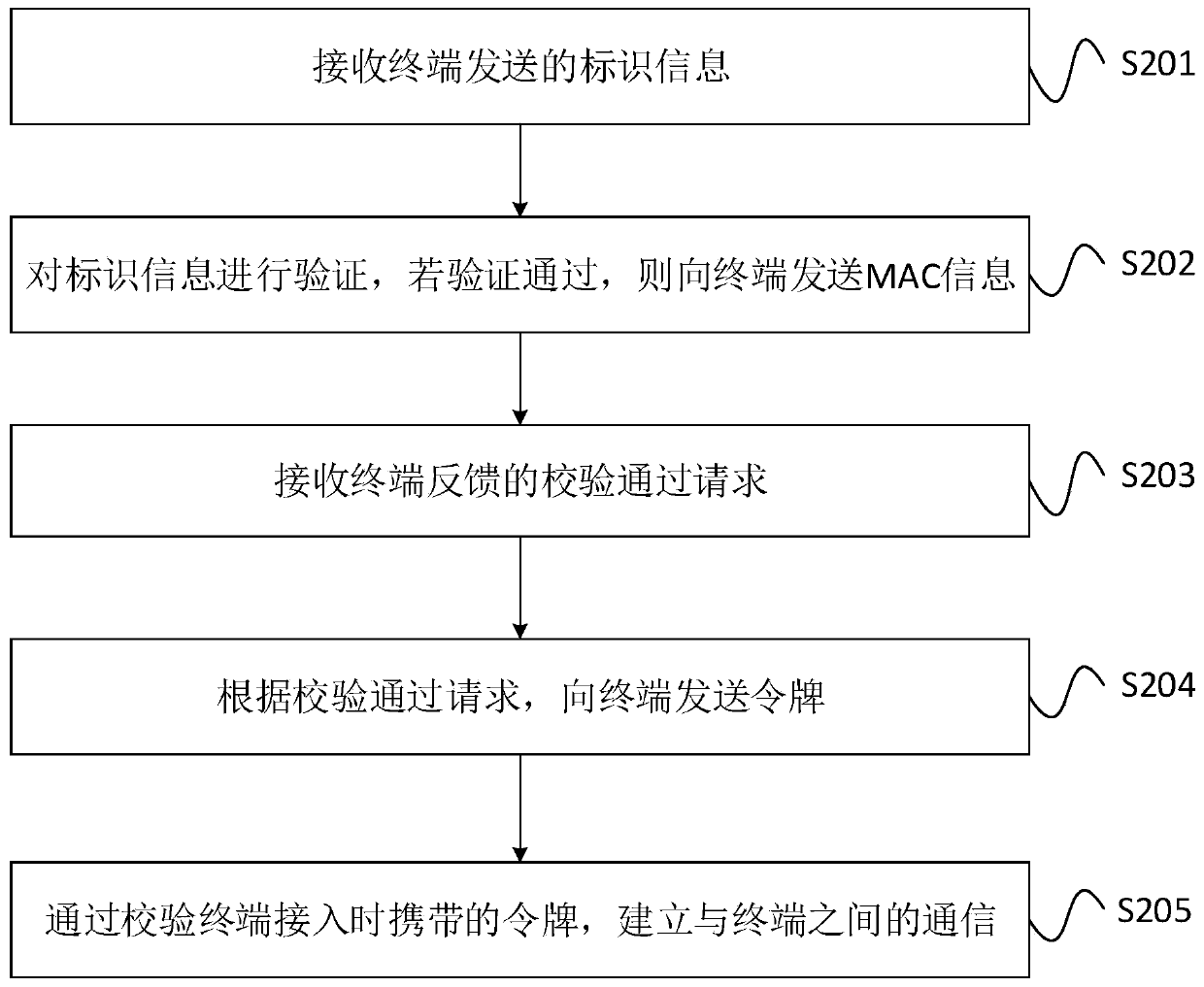
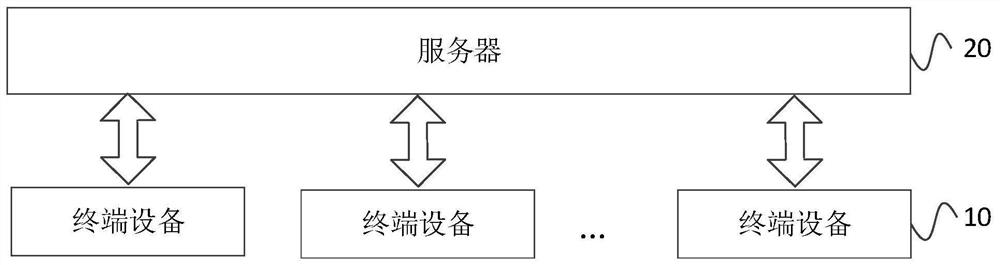
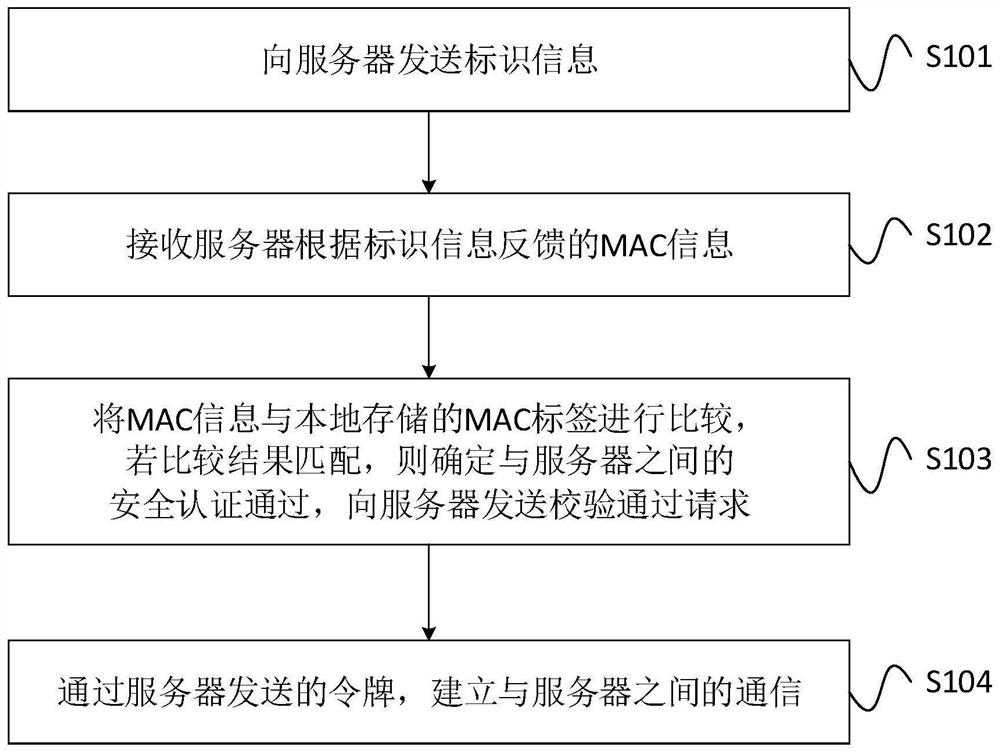
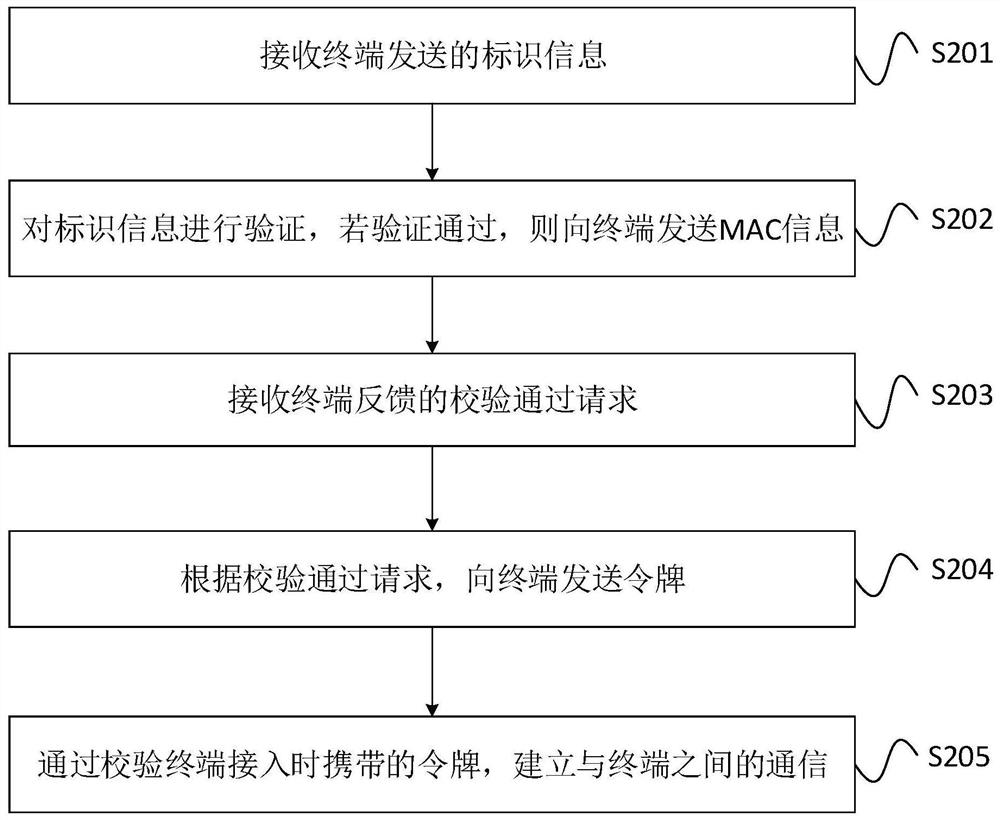
ActiveCN111131300AImprove data transmission securityTransmissionSecurity authenticationData transmission
The invention provides a communication method, a terminal and a server, which are applied to a network formed by the server and the terminal. The method comprises the steps of sending identification information to the server; receiving MAC information fed back by the server according to the identification information; comparing the MAC information with a locally stored MAC label, if a comparison result is matched, determining that security authentication with the server is passed, and sending a verification passing request to the server; and establishing communication with the server through atoken sent by the server. According to the mode, the data transmission security between the server and the terminal can be effectively improved.
Owner:QUECLINK WIRELESS SOLUTIONS
Monitoring management system
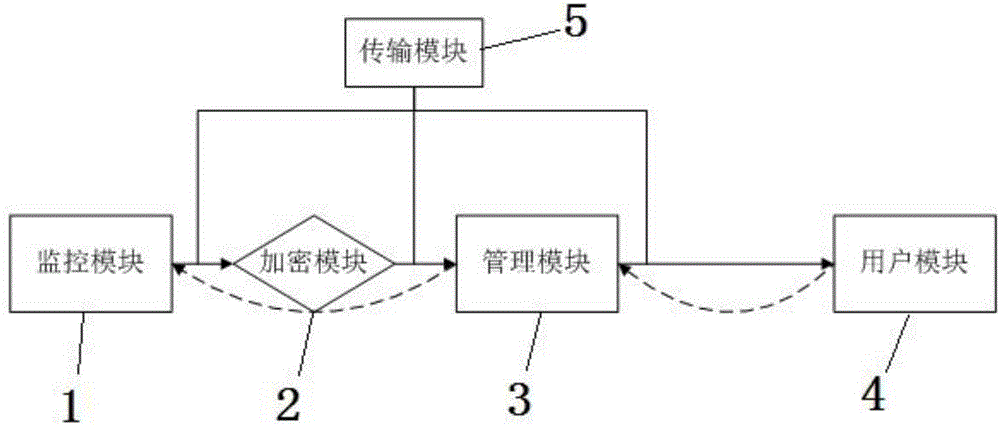
ActiveCN106210661AReal-time positioningAvoid crackingClosed circuit television systemsVideo monitoringInformation transmission
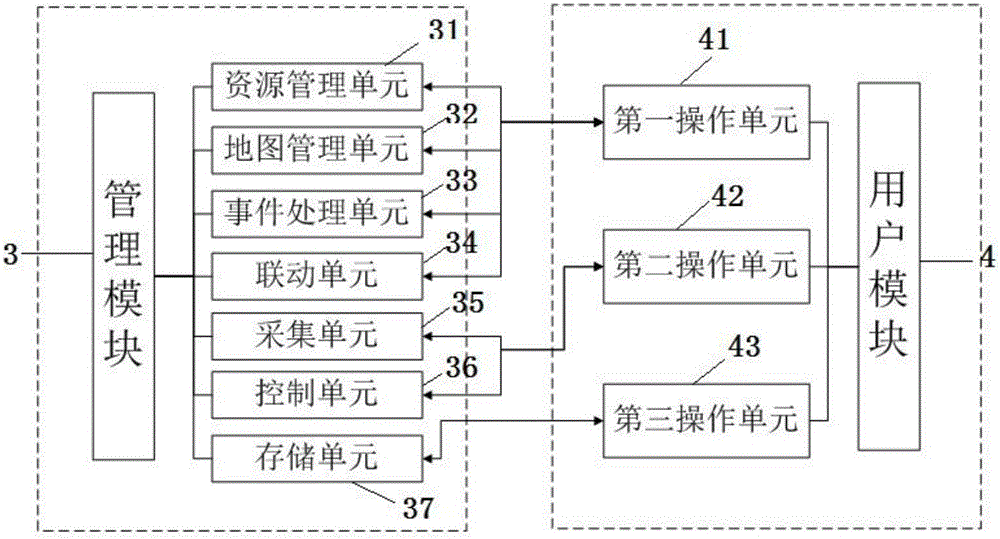
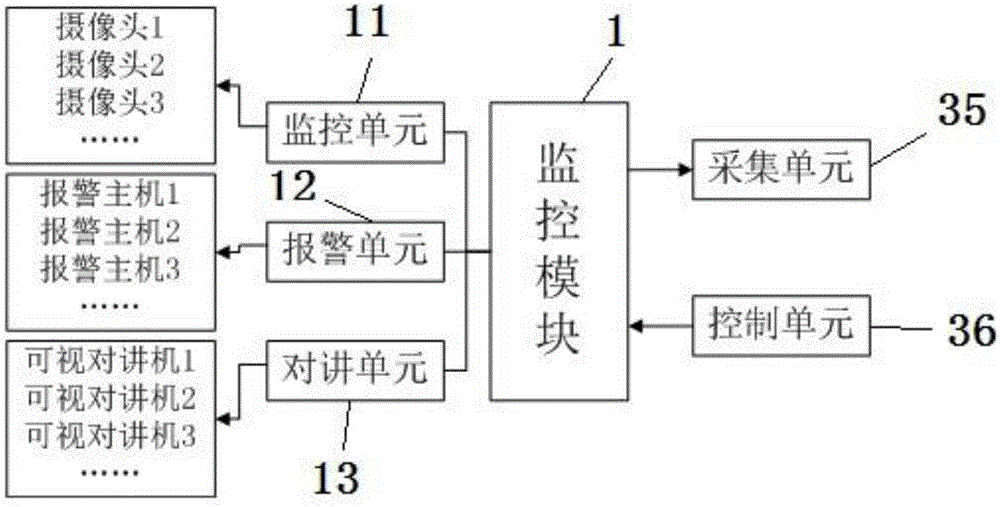
The invention discloses a monitoring management system which comprises a monitoring module, a transmission module, an encryption module, a management module and a user module. The monitoring module comprises a monitoring unit, the monitoring unit comprises at least one video monitoring device, and each video monitoring device has unique identity information; the encryption module is connected with the transmission module and used for conducting encryption processing on data transmitted by the system; the transmission module is used for information transmission among the modules; the user module is connected with the management module and used for allowing a user to operate a control unit and a storage unit. The system can identify multiple devices and achieve multi-terminal management; an electronic map is imported, and a monitoring area is positioned in real time; data is encrypted, and the transmission safety is high; the system has diverse functions and can process a variety of events; the user module is interfaced, and operation is intuitive, easy and convenient.
Owner:NINGBO BAOXING INTELLIGENT ENG
Data acquisition device and acquisition method thereof
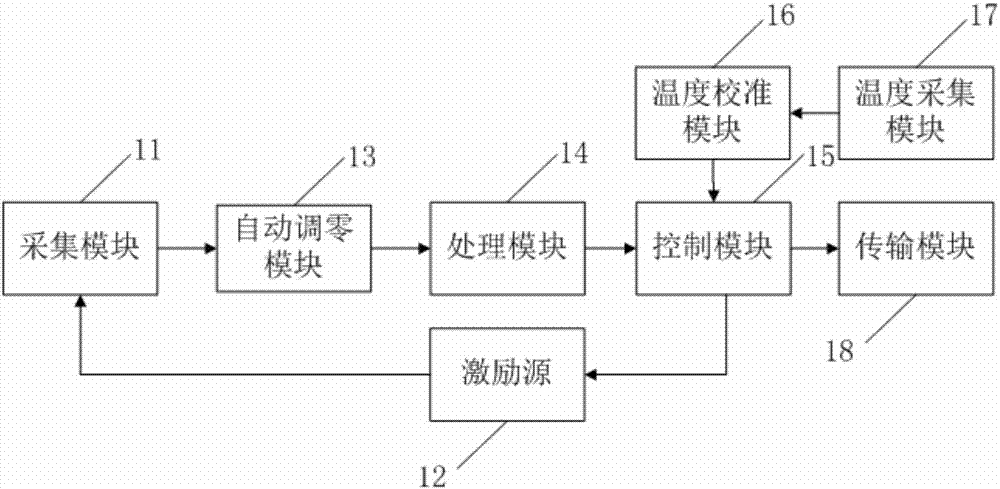
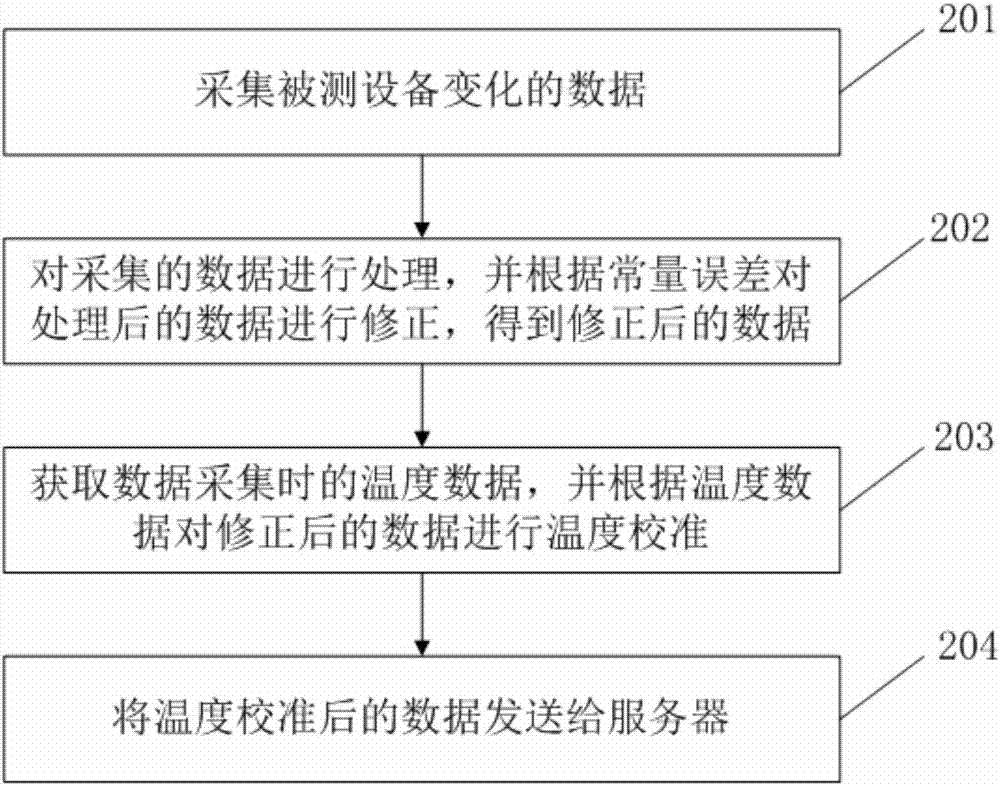
PendingCN106989844AHigh precisionReduce volumeThermometer testing/calibrationThermometer applicationsComputer hardwareAcquisition apparatus
The invention discloses a data acquisition device. The device is characterized in that an acquisition module is connected to an excitation source and an automatic zero setting module and is used for collecting changed data of detected equipment; the other end of the excitation source is connected to a control module and is used for connecting or disconnecting the acquisition module under control of the control module; the other end of the automatic zero setting module is connected to a processing module; the other end of the processing module is connected to the control module; a temperature acquisition module is connected to a temperature calibration module; the temperature calibration module is connected to the control module; and the control module is also connected to a transmission module. In the invention, data acquisition precision is increased, simultaneously, because of the temperature calibration module, the data acquisition device is miniature so that usage and loading are convenient.
Owner:UNIV OF SCI & TECH BEIJING
LoRa router for optimizing LoRa Internet-of-Things system
ActiveCN112118571AImprove data transfer efficiencyChange the transmission pathSecurity arrangementHigh level techniquesEmbedded systemRouter
The invention provides a LoRa router for optimizing a LoRa Internet-of-Things system. The router preprocesses the LoRa data generated by a sensor in the Internet of Things, converts the LoRa data intoTCP / IP data matched with a conventional network, encrypts the TCP / IP data, and coordinates the working states of different function modules in the router so that different gateways in the LoRa routercan transmit the data in parallel at the same time to improve the data transmission efficiency of the LoRa router. Compared with the traditional Internet of Things, the LoRa router greatly shortens the data transmission time, can reduce the data transmission power consumption of the Internet of Things, improve the data transmission security of the Internet of Things, dynamically adjusts the the access number of node devices, and is suitable for construction and deployment of the large LoRa Internet of Things.
Owner:慧之安信息技术股份有限公司
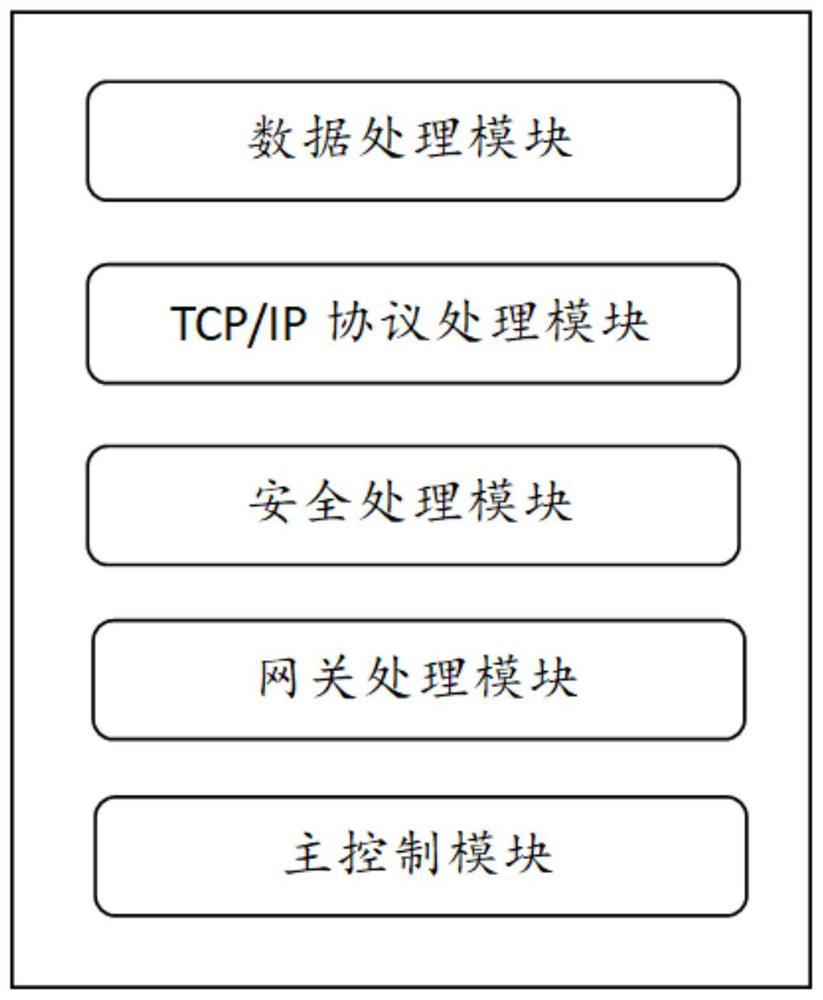
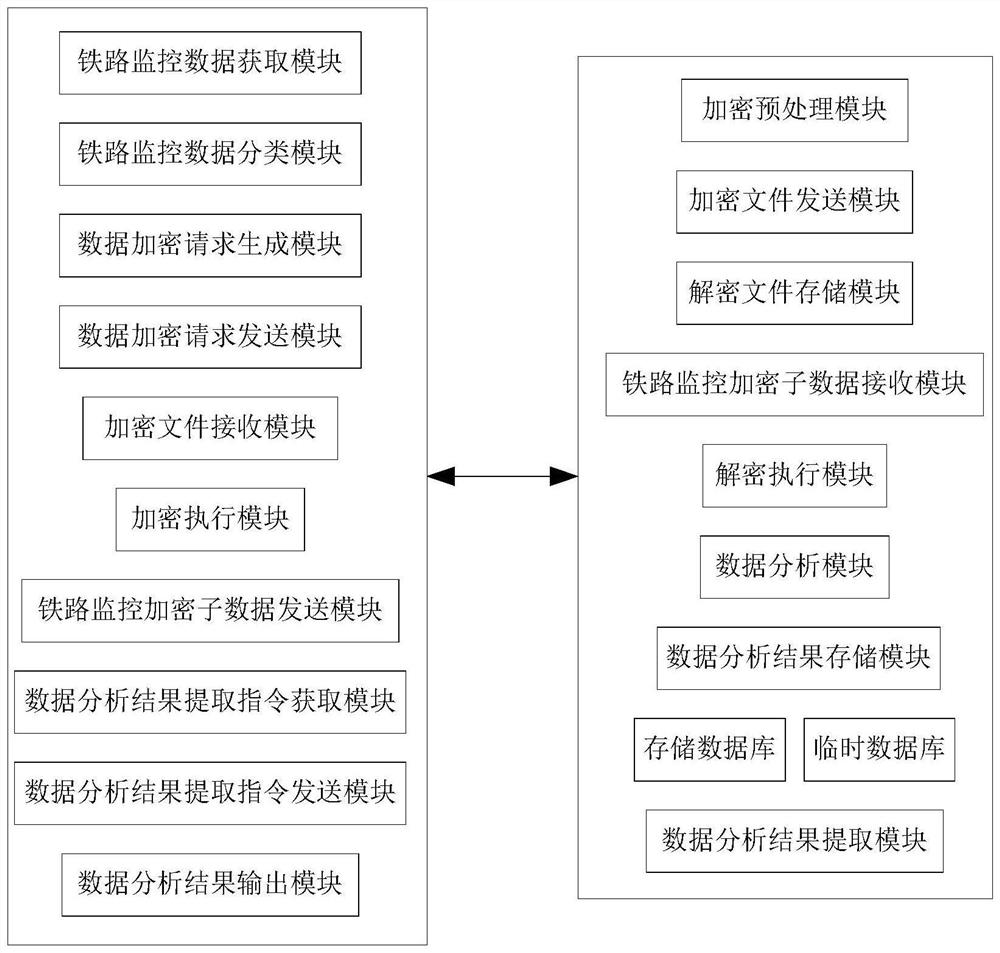
Railway monitoring data transmission system
InactiveCN112181998AImprove transmission securityReduce the likelihood of illegal acquisitionDatabase updatingDatabase management systemsComputer hardwareData acquisition
The invention relates to a railway monitoring data transmission system. The system comprises a railway monitoring data processing device and a background server, wherein the railway monitoring data processing device comprises a railway monitoring data acquisition module, a railway monitoring data classification module, a data encryption request generation module, a data encryption request sendingmodule, an encryption file receiving module, an encryption execution module and a railway monitoring encryption sub-data sending module; the background server comprises an encryption preprocessing module, an encryption file sending module, a decryption file storage module and a railway monitoring encryption sub-data receiving module. The railway monitoring data is classified, the railway monitoring sub-data obtained by classification is encrypted according to different encryption files, and the encryption files are output to the railway monitoring data processing device only after the background server receives the data encryption request, so the data transmission security is improved.
Owner:郑州迈拓信息技术有限公司
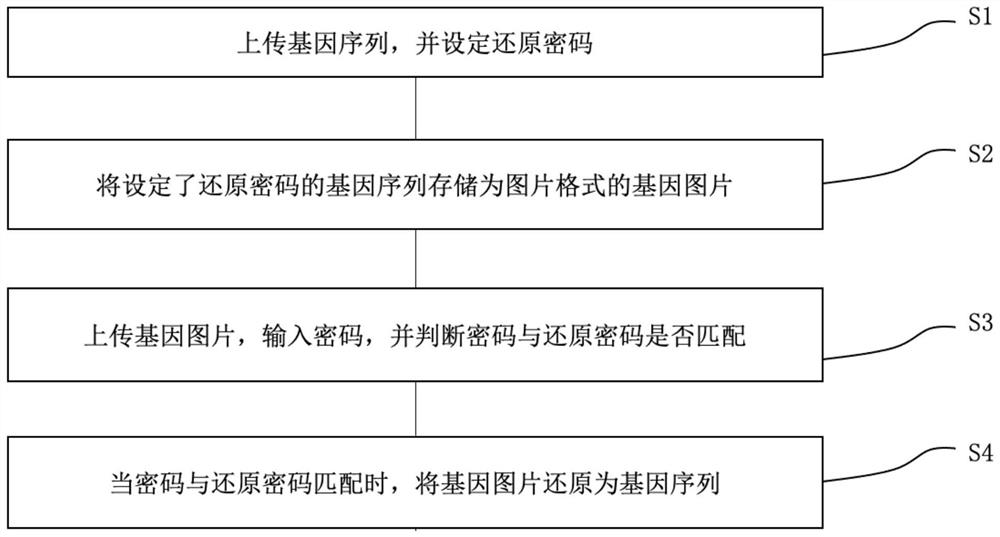
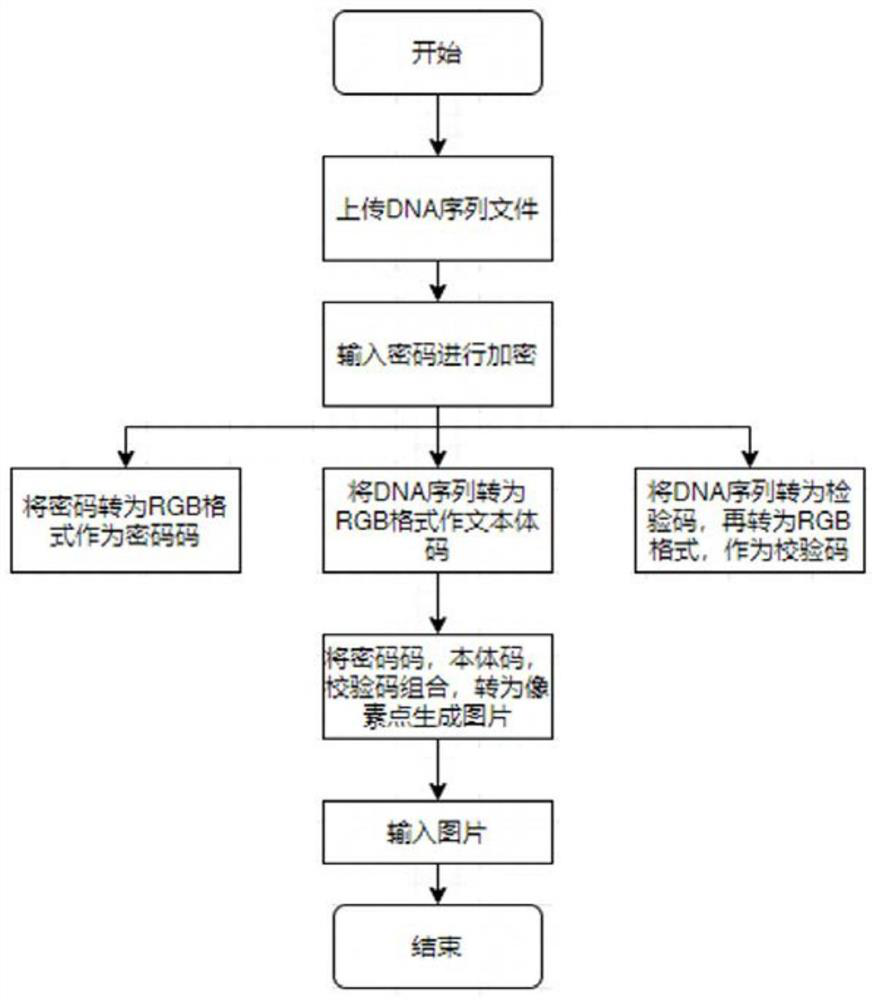
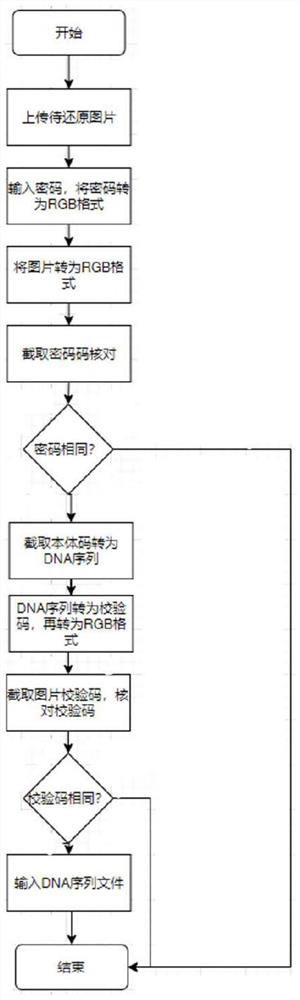
Gene sequence processing method, computer storage medium and electronic equipment
ActiveCN112700819AImprove data transmission securitySequence analysisInstrumentsComputer hardwarePassword
The invention provides a gene sequence processing method, a computer storage medium and electronic equipment, and the gene sequence processing method comprises the following steps: S1, uploading a gene sequence, and setting a restoration password; s2, storing the gene sequence set with the reduction password as a gene picture in a picture format; s3, uploading the gene picture, inputting a password, and judging whether the password is matched with the restored password or not; and S4, when the password is matched with the reduction password, reducing the gene picture into the gene sequence. According to the gene sequence processing method provided by the embodiment of the invention, when the gene sequence is stored, the gene sequence is converted into a picture format to be stored, so that the space occupied by data storage can be greatly reduced, the transmission speed of the gene sequence is increased, and the gene sequence is encrypted in the process of converting the gene sequence into a picture; information security can be effectively improved.
Owner:YUNZHOU BIOSCIENCES (GUANGZHOU) INC
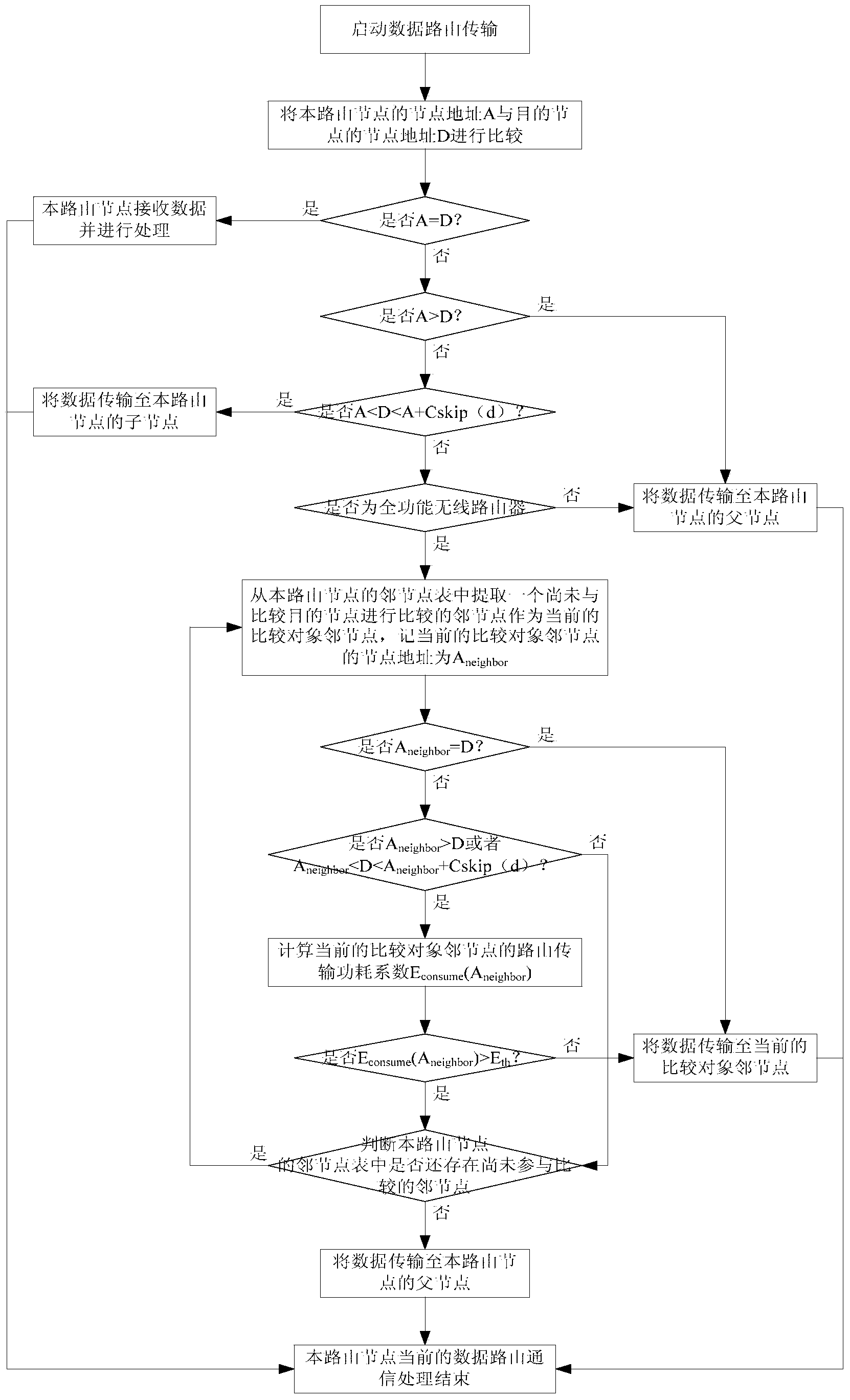
Data routing transmission control method of wireless autonomous monitoring network of wind farm
InactiveCN103442403AImprove the real-time performance of data transmissionReduce transmission delayNetwork topologiesHigh level techniquesTree clusteringData transmission
The invention provides a data routing transmission control method of a wireless autonomous monitoring network of a wind farm. By adopting the data routing transmission control method of a wireless autonomous monitoring network of a wind farm provided by the invention, when a node performing data transmission and a destination node are positioned in different sub-tree clusters, as long as a neighbor node meeting the routing conditions and the energy storage requirements exists, cross-tree cluster routing transmission is directly performed without the necessity of forwarding through a root node (a network coordinator) again, thus the routing path is effectively shortened, the routing transmission delay is reduced, and the real-time property of data transmission of the wireless autonomous monitoring network of the wind farm is improved; and moreover, the method also performs judgment on the energy storage conditions of the neighbor node, the phenomenon that ongoing data routing transmission cannot be supported due to insufficient energy storage of the neighbor node during the cross-tree cluster routing transmission is avoided, and the data transmission safety of the wireless autonomous monitoring network of the wind farm is improved.
Owner:CHONGQING UNIV
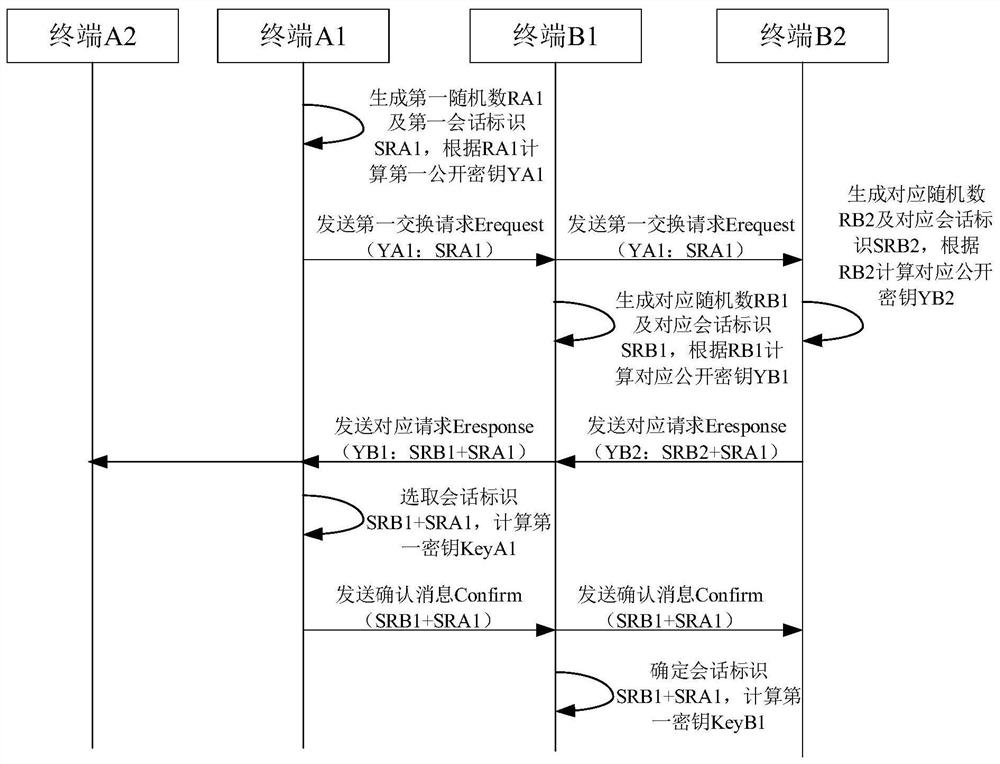
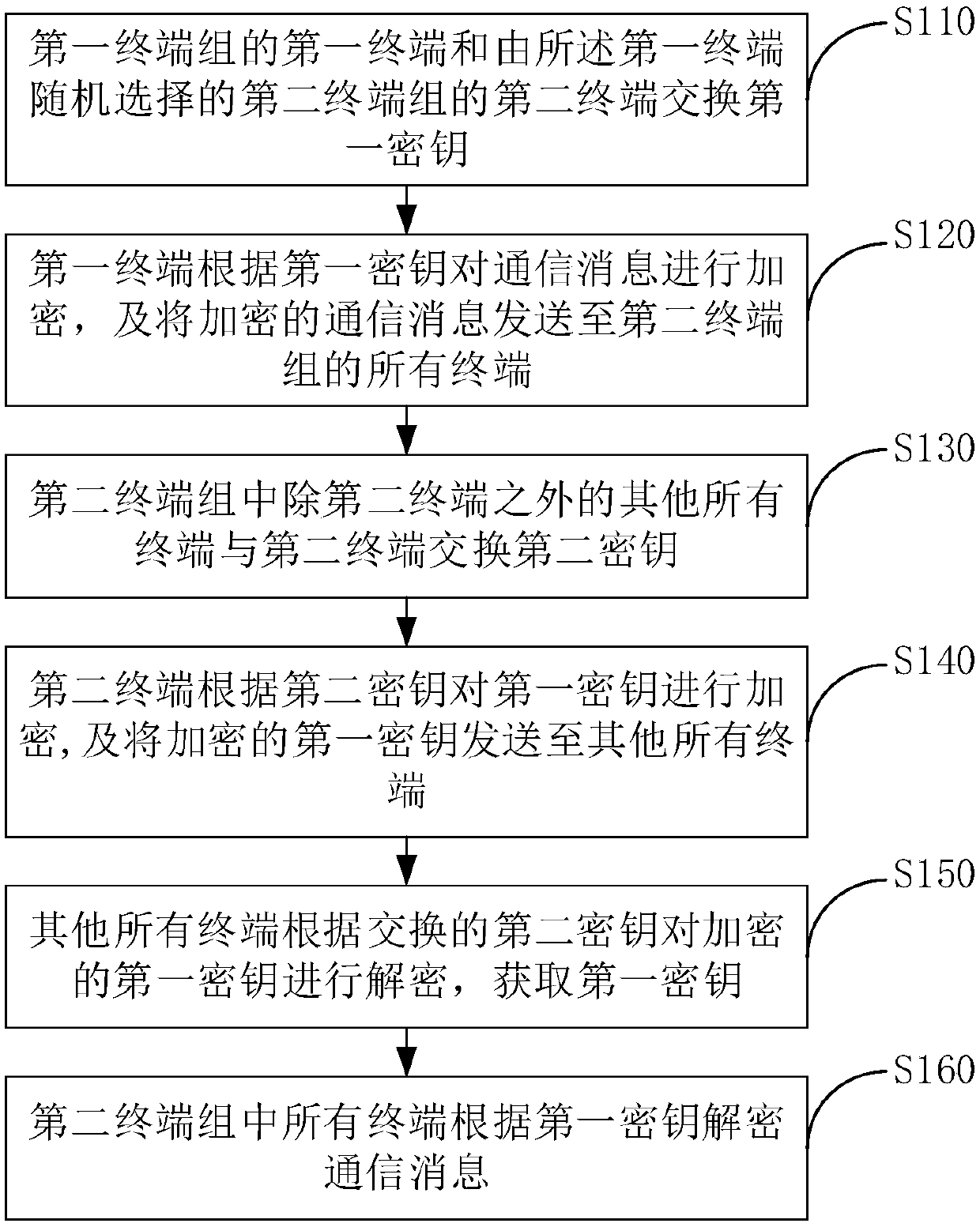
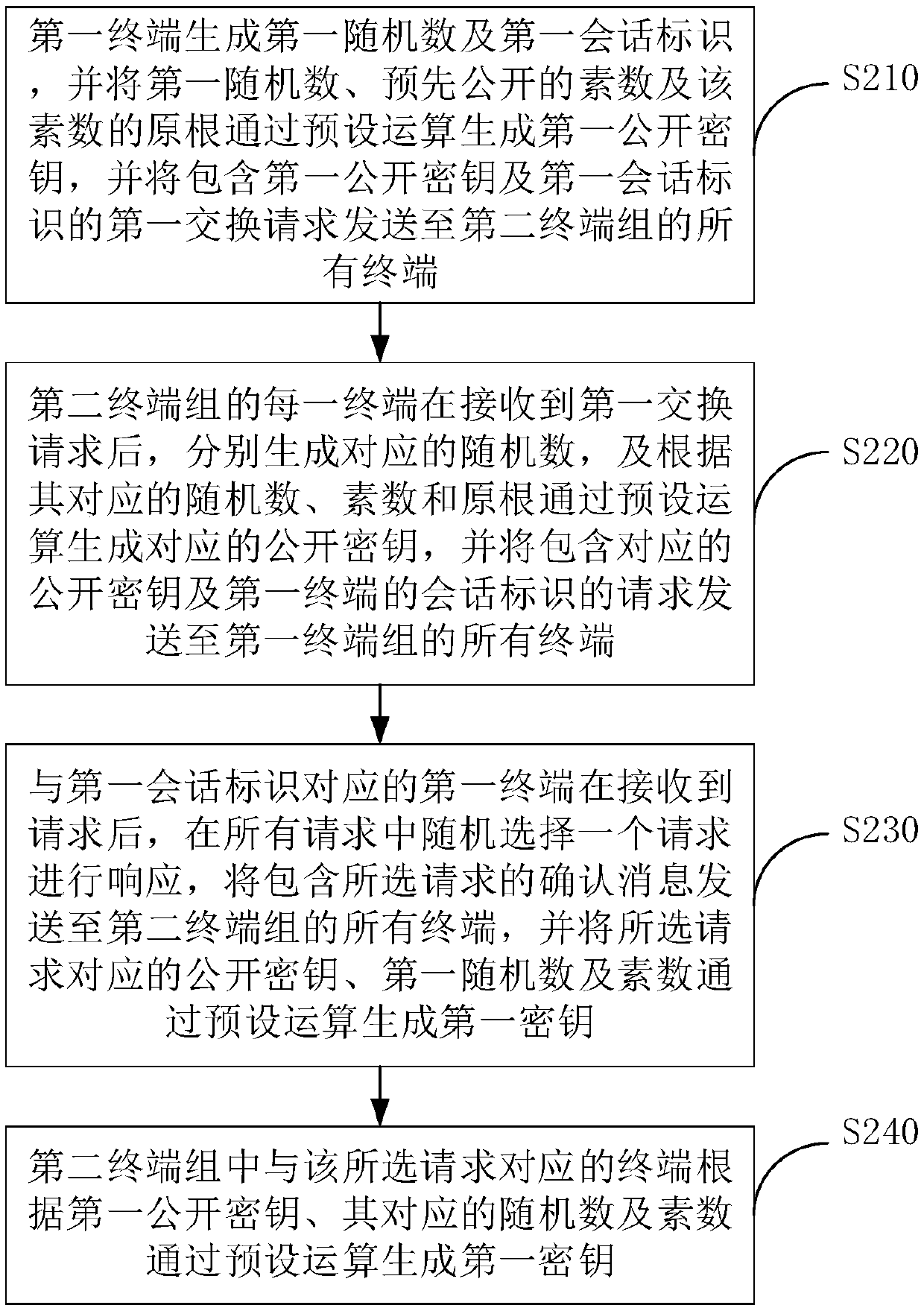
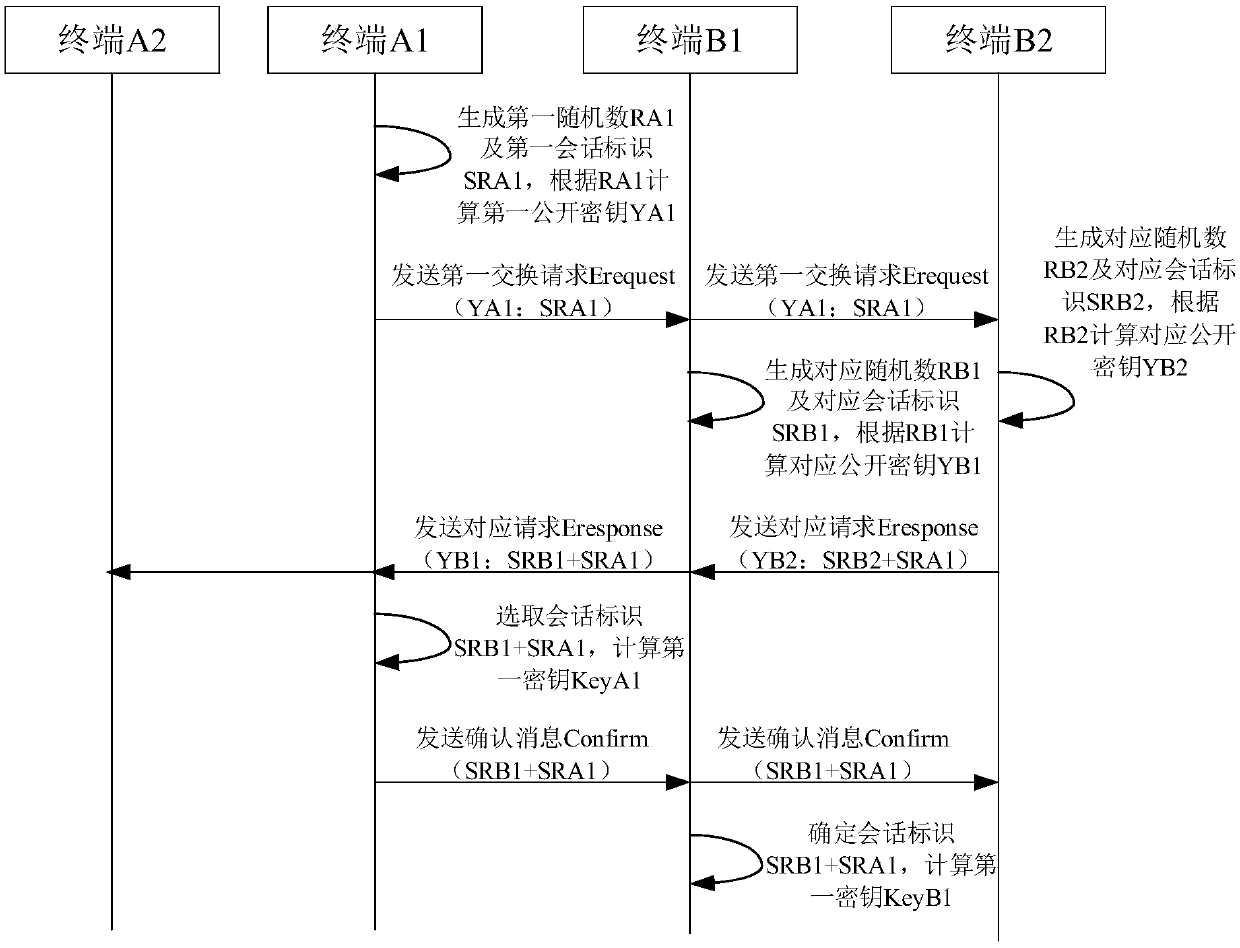
Multi-terminal message encryption transmission method and system
ActiveCN109525612BImprove data transmission securityReduce the risk of being intercepted by an attackKey distribution for secure communicationEngineeringData transmission
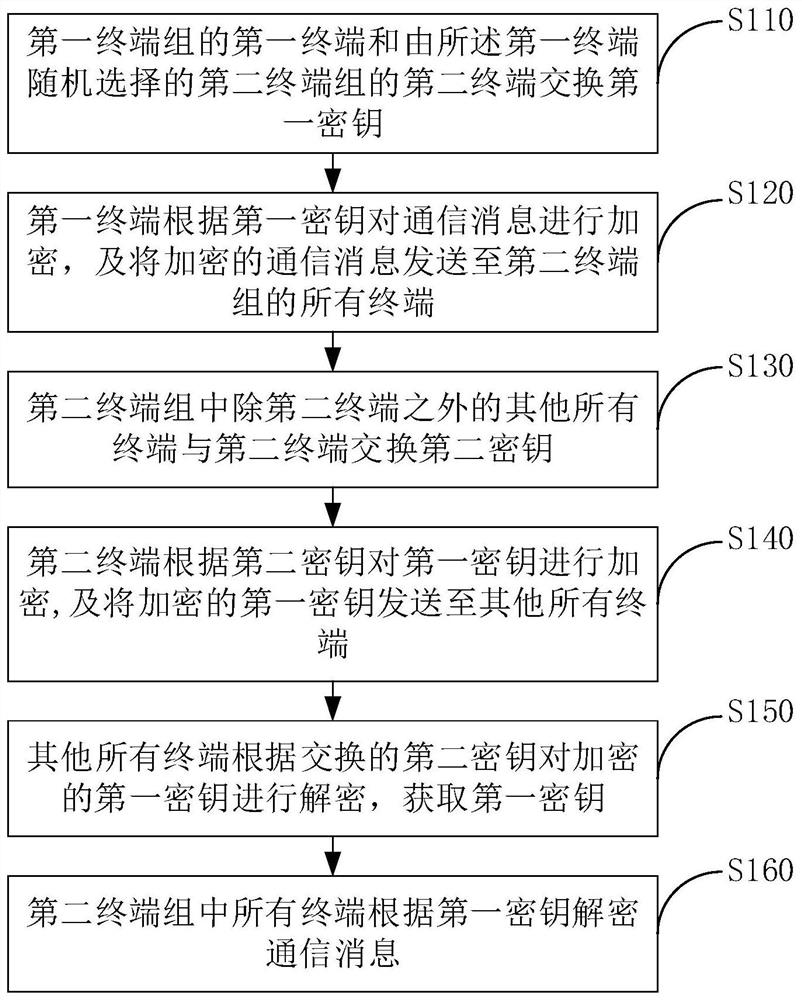
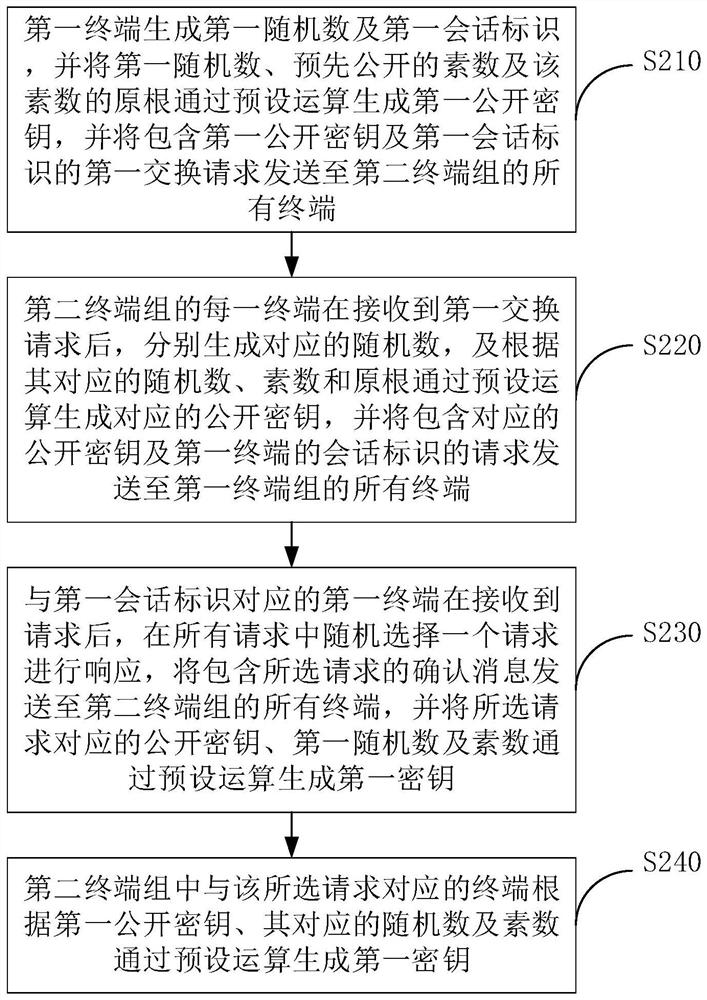
The present invention discloses a multi-terminal message encrypted transmission method and system, the method comprising: exchanging a first key between a first terminal of a first terminal group and a second terminal of a second terminal group randomly selected by the first terminal; The terminal encrypts the communication message according to the first key, and sends the encrypted communication message to all terminals in the second terminal group; all other terminals in the second terminal group except the second terminal exchange the second terminal with the second terminal. key; the second terminal encrypts the first key according to the second key, and sends the encrypted first key to all other terminals; all other terminals encrypt the encrypted first key according to the exchanged second key Decrypt to obtain the first key; all terminals in the second terminal group decrypt the communication message according to the first key. The invention can realize the encryption and decryption between different terminal groups, and improve the security of data transmission.
Owner:北京云中融信网络科技有限公司
Multi-end message encryption transmission method and system
ActiveCN109525612AImprove data transmission securityReduce the risk of being intercepted by an attackKey distribution for secure communicationComputer terminalData transmission
The invention discloses a multi-end message encryption transmission method and system. The method includes: exchanging a first key by a first terminal of a first terminal group and a second terminal of a second terminal group randomly selected by the first terminal; encrypting a communication message by the first terminal according to the first key, and sending encrypted communication message to all terminals of the second terminal group; exchanging a second key by all terminals other than the second terminal in the second terminal group and the second terminal; encrypting the first key by thesecond terminal according to the second key, and sending an encrypted first key to all the other terminals; decrypting the encrypted first key by all the other terminals according to the exchanged second key to obtain the first key; and decrypting the communication message by all the terminals in the second terminal group according to the first key. The method can realize encryption and decryption between the different terminal groups, and improve data transmission security.
Owner:北京云中融信网络科技有限公司
Communication method, terminal and server
ActiveCN111131300BImprove data transmission securitySecuring communicationSecurity authenticationData transmission
The present invention provides a communication method, a terminal and a server, which are applied to a network composed of a server and a terminal. The method includes: sending identification information to the server; receiving MAC information fed back by the server according to the identification information; combining the MAC information with the local Stored MAC tags are compared, and if the comparison result matches, then it is determined that the security authentication with the server is passed, and a verification pass request is sent to the server; through the token sent by the server, an authentication with the server is established. communication. In this way, the security of data transmission between the server and the terminal can be effectively improved.
Owner:QUECLINK WIRELESS SOLUTIONS
A special quantum encryption gateway system for electric power
ActiveCN103475464BAdd extensionsMinor changesKey distribution for secure communicationNetwork connectionsCommunication interfaceElectric power system
The invention provides a power special quantum encryption gateway system. The system comprises a power special quantum encryption gateway communicated with a gateway management device through a quantum link; the power special quantum encryption gateway is used for performing encryption communication through the quantum link or a classic link; a quantum secret key distributing device is integrally arranged on the power special quantum encryption gateway and comprises a vertical integration model and a transverse integration mode; the quantum link comprises a quantum secret key sending device and a quantum secret key receiving device which are connected with each other through an optical fiber or a free space; the gateway management device comprises a user authentication module, a user right / certificate management module, a quantum secret key management module and a communication interface module. Compared with the prior art, the power special quantum encryption gateway system provided by the invention is capable of synchronously supporting the traditional mode encryption function and the quantum mode encryption function, and capable of providing unconditional information security assurance for the power system data transmission under the quantum mode, and convenient for the large-scale deployment and industrial practicality of the power special quantum encryption network.
Owner:STATE GRID CORP OF CHINA +3
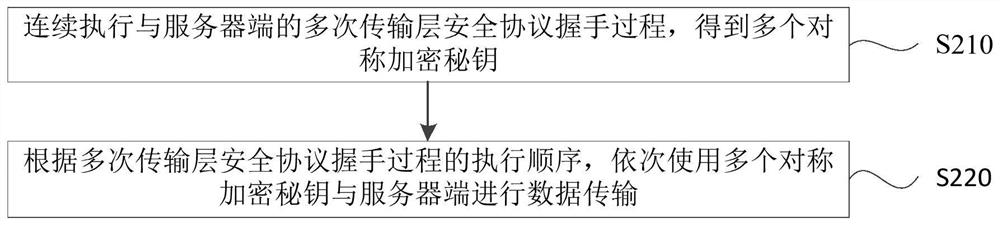
Data encryption communication terminal method and device, terminal, server and storage medium
PendingCN112751858AImprove encryptionImprove data encryption effectMultiple keys/algorithms usageData transmissionProtocol for Carrying Authentication for Network Access
The invention discloses a data encryption communication terminal method and device, a terminal, a server and a storage medium, and the method comprises the steps: continuously executing a multi-time transport layer security protocol handshake process with a server side, and obtaining a plurality of symmetric encryption keys, wherein the message in the second handshake process is encrypted by using a first symmetric encryption key obtained in the first handshake process, a second symmetric encryption key is obtained through the second handshake process, the first handshake process and the second handshake process are any two adjacently executed handshake processes in multiple transport layer security protocol handshake processes, and the first handshake process is executed before the second handshake process; and according to the execution sequence of the multiple transport layer security protocol handshake processes, sequentially using the plurality of symmetric encryption keys to carry out data transmission with the server side. According to the method and the device, the counterfeited server side can be identified, so the data encryption effect is improved, the counterfeited server side cannot correctly decrypt the received encrypted data, and the data transmission security is improved.
Owner:EVERSEC BEIJING TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com