Data encryption communication terminal method and device, terminal, server and storage medium
A technology of data encryption and communication methods, applied in the usage of multiple keys/algorithms, transmission systems, electrical components, etc., can solve the problems of server-side private key leakage, security loopholes, and the urgent need to improve encryption effects, so as to improve data encryption. Effect, encryption effect improved effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
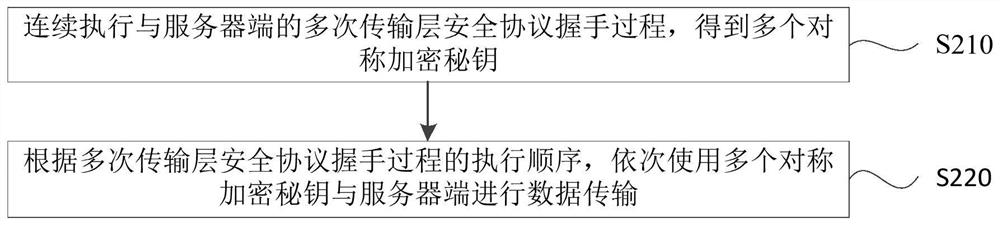
[0053] figure 2 It is a flow chart of the data encryption communication method provided by Embodiment 1 of the present invention. This embodiment is applicable to the situation where the client and the server establish a connection based on the transport layer security protocol handshake process, and perform data encryption communication through the connection. The method It can be executed by the client, and specifically includes the following steps:
[0054] Step 210: Continuously execute multiple transport layer security protocol handshake processes with the server to obtain multiple symmetric encryption keys.
[0055] Wherein, the first symmetric encryption key obtained in the first handshake process is used to encrypt the message in the second handshake process, and the second symmetric encryption key is obtained through the second handshake process; the first handshake process and the second handshake process are For any two adjacent handshake processes in the multiple...
Embodiment 2
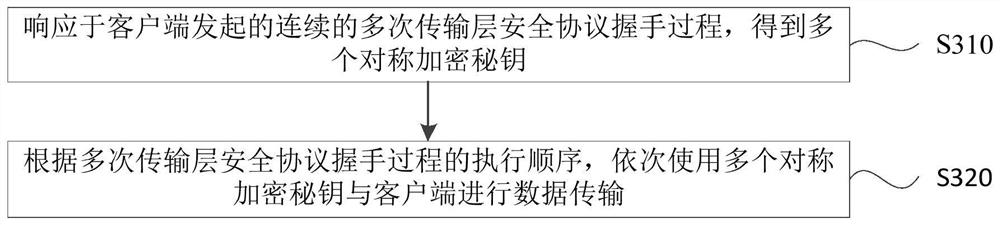
[0107] image 3 It is a flowchart of the data encryption communication method provided by Embodiment 2 of the present invention. This embodiment is applicable to the situation where the server and the client establish a connection based on the transport layer security protocol handshake process, and perform data encryption communication through the connection. The method It can be executed by the server side, specifically including the following steps:
[0108] Step 310: Obtain multiple symmetric encryption keys in response to multiple consecutive TLS protocol handshake processes initiated by the client.
[0109] Among them, the first symmetric encryption key obtained in the first handshake process is used to decrypt the message in the second handshake process, and the second symmetric encryption key is obtained through the second handshake process; the first handshake process and the second handshake process are For any two adjacent handshake processes in the multiple transp...
Embodiment 3
[0168] Figure 4 It is a schematic diagram of the structure of the data encryption communication device provided by the third embodiment of the present invention. This embodiment is applicable to the situation where the client and the server establish a connection based on the handshake process of the transport layer security protocol, and perform data encryption communication through the connection. The device It may be located at the client side, specifically including: a multiple handshake process initiation module 410 and a first data transmission module 420 .
[0169] The multiple handshake process initiation module 410 is used to continuously execute multiple transport layer security protocol handshake processes with the server to obtain multiple symmetric encryption keys; where the first symmetric encryption key obtained by the first handshake process is used for the second The message in the handshake process is encrypted, and the second symmetric encryption key is obt...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com