Cross-domain security access and resource control method for virtualization equipment
An access control and resource control technology, applied in the field of virtualization, can solve problems such as hidden dangers in cross-domain access security and imperfect resource allocation and scheduling rules, and achieve the effect of improving security and utilization.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
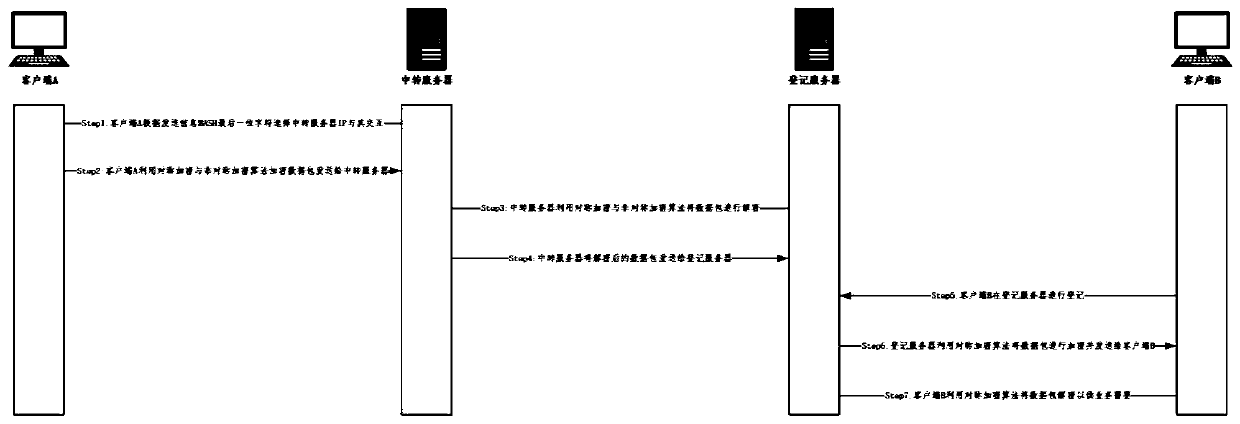
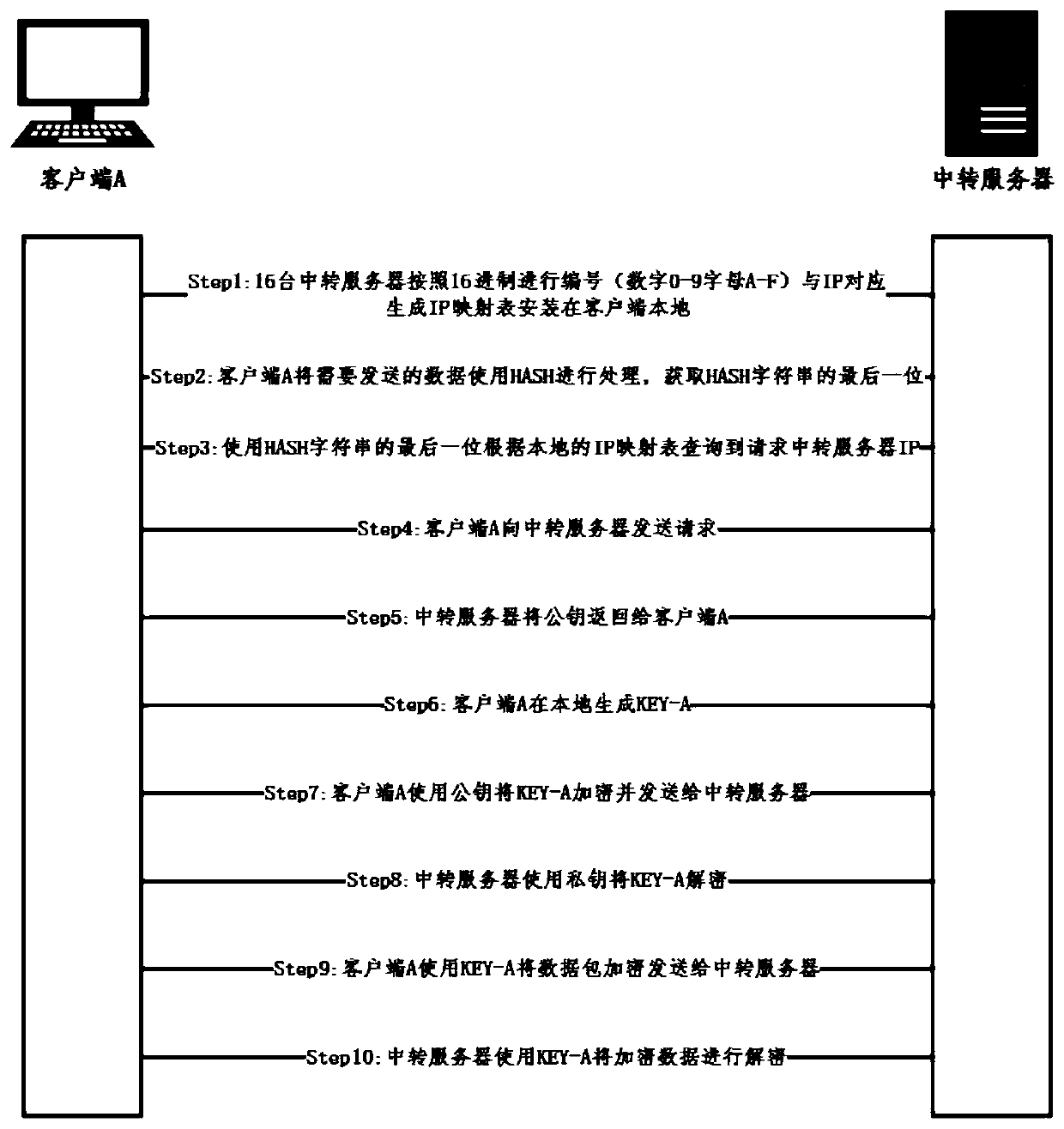
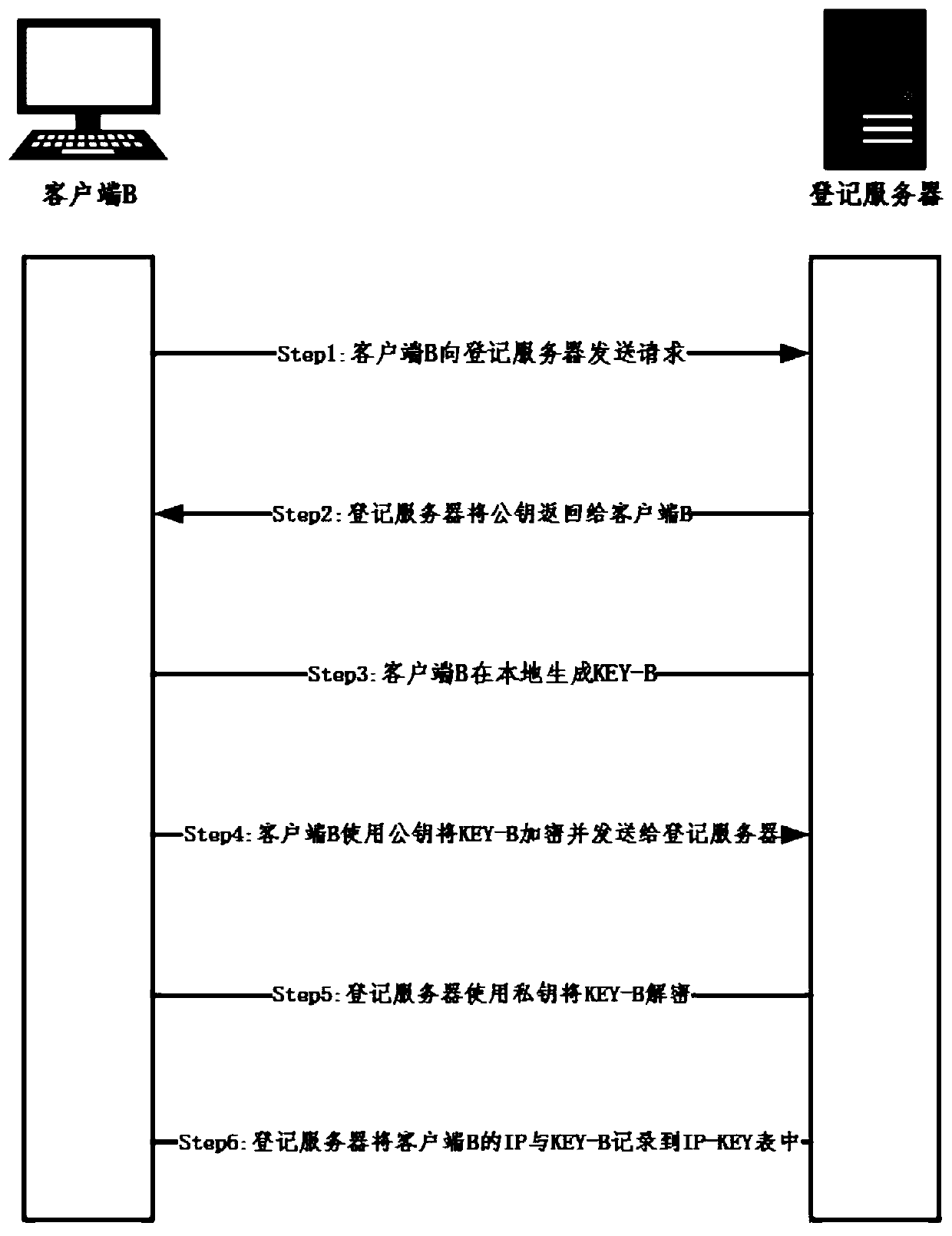
[0048] Such as figure 1 and figure 2 As shown, a cross-domain security access and resource control method for virtualized devices includes three parts: multiple virtualized device platforms, an access control center, and a resource pool. The specific implementation method is as follows: First, the newly added routing device establishes a neighbor relationship with each device participating in the routing through the neighbor table; secondly, the newly added routing device authenticates the device through the centralized authentication center; Confirm the authentication of the neighbor routing device; secondly, after the authentication and confirmation of the neighbor routing device, use the asymmetric encryption technology to encrypt the message and send it to the neighbor routing device. Finally, after receiving the encrypted message, the neighbor routing device uses the asymmetric Symmetric encryption technology decrypts messages to obtain original messages for business ne...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com