Multi-end message encryption transmission method and system
A technology for encrypting transmission and messages, which is applied in transmission systems, digital transmission systems, and key distribution. It can solve problems such as potential safety hazards and key leakage, so as to avoid the risk of attacks, improve the security of data transmission, and reduce the risk of attack interception. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
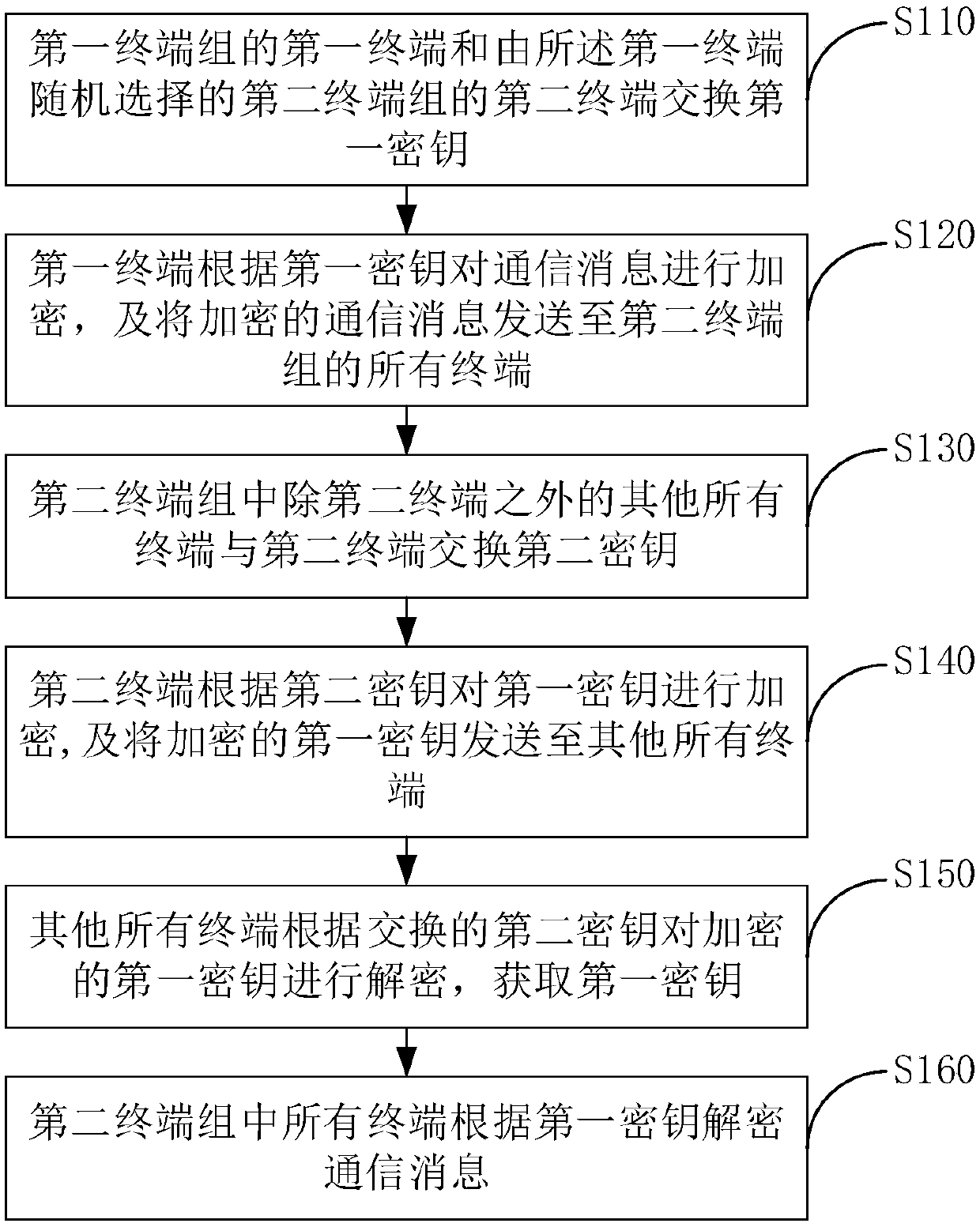
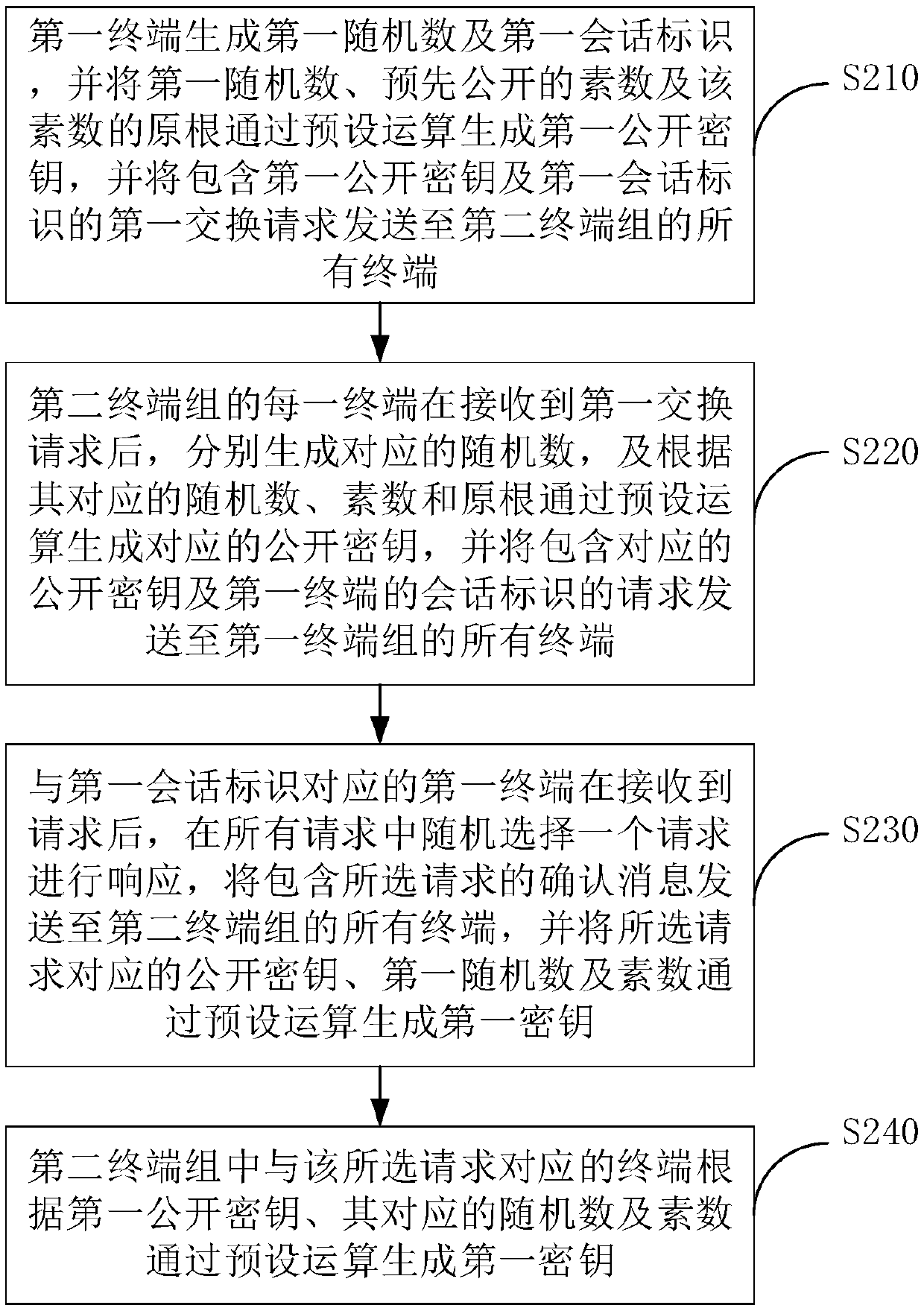
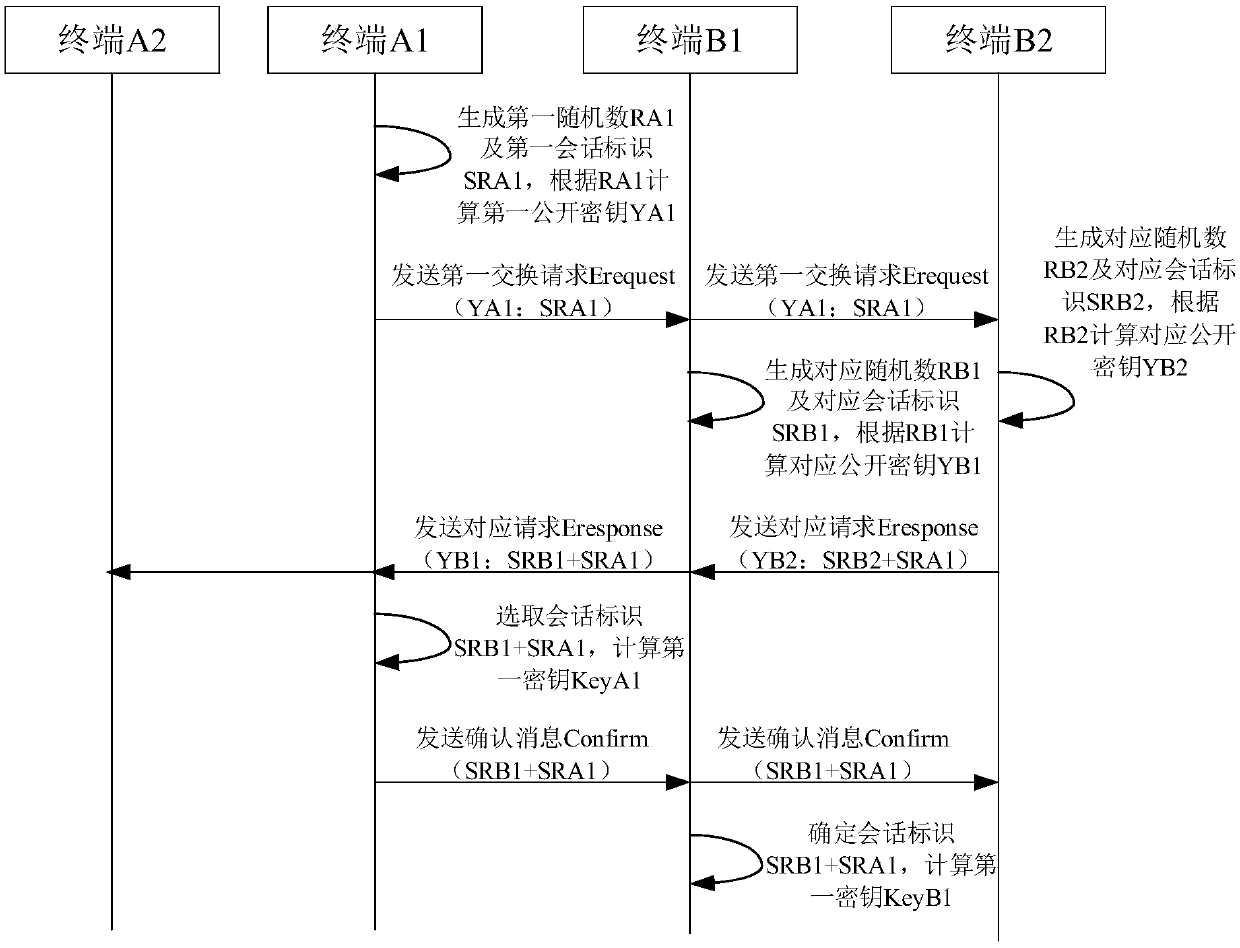
[0062] figure 1 A schematic flowchart of a multi-terminal message encryption transmission method provided by an embodiment of the present invention is shown. The method is applied to multiple terminal groups, each terminal group corresponds to one user, and at least one terminal group includes multiple terminals.
[0063] The terminal may include any terminal device such as a computer (personal computer), a mobile phone, a tablet computer, a PDA (Personal Digital Assistant, personal digital assistant), and a vehicle-mounted computer.
[0064] For example, in an IM (Instant Messaging, instant messaging) system, the first terminal group A corresponding to the first user may include terminal A1, terminal A2, etc., and the second terminal group B corresponding to the second user may include terminal B1, terminal B2, etc. Wait. When the first user A and the second user B communicate, when a terminal in the second terminal group B sends a communication message to the first user A,...
Embodiment 2
[0166] Image 6 A schematic structural diagram of a multi-terminal message encryption transmission system provided by an embodiment of the present invention is shown. The multi-terminal message encryption transmission system 400 includes multiple terminal groups, and at least one terminal group includes multiple terminals in the multiple terminal groups.
[0167] Specifically, as Image 6 As shown, the multi-terminal message encryption transmission system 400 may include a first terminal group 410 and a second terminal group 420 , the first terminal group 410 may include multiple terminals 411 , and the second terminal group 420 may include multiple terminals 411 .
[0168] In some other embodiments, the first terminal group 410 may further include one terminal 411 , and the second terminal group 420 may include multiple terminals 411 . In some other embodiments, the first terminal group 410 may include multiple terminals 411 , and the second terminal group 420 may include o...
Embodiment 3
[0178] Figure 7 A schematic structural diagram of a multi-terminal message encryption transmission device provided by an embodiment of the present invention is shown. The multi-terminal message encryption transmission apparatus 500 is applied to multiple terminal groups, and at least one terminal group includes multiple terminals.
[0179] The multi-terminal message encryption transmission device 500 includes a first exchange module 510 , a first encryption module 520 , a second exchange module 530 , a second encryption module 540 , a first decryption module 550 and a second decryption module 560 .
[0180] The first exchange module 510 is configured to exchange a first key between a first terminal of a first terminal group and a second terminal of a second terminal group randomly selected by the first terminal.
[0181] The first encryption module 520 is used for the first terminal to encrypt the communication message according to the first key, and to send the encrypted co...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com