Integrated identity based encryption (IBE) data encryption system
A technology of data encryption and authentication system, which is used in transmission systems, electrical components, user identity/authority verification, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0063] The specific implementation of the present invention will be further described below.
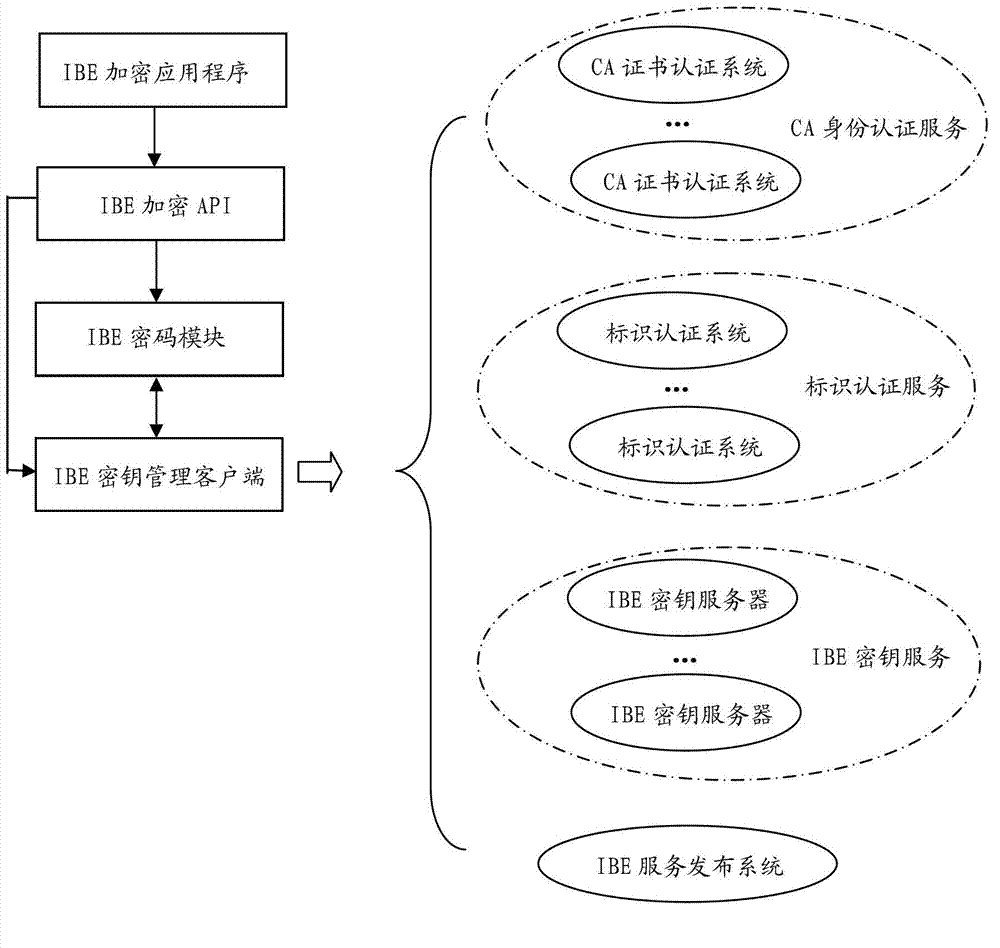
[0064] Such as figure 1 As shown, the integrated IBE data encryption system based on the present invention consists of an IBE key server, a CA certificate authentication system, an identification authentication system, an IBE service publishing system, an IBE encryption application program, an IBE encryption API, an IBE cipher module, and an IBE key management client It consists of several parts.
[0065] The IBE key server is a service system based on the C / S (Client / Server) mode, and its client is the IBE key management client. The IBE key server can adopt common information system development technology, such as C / C++ or C#.Net or J2EE development language and environment; the generation of its IBE key can be realized by referring to relevant specifications, such as RFC5091. IBE key generation can be implemented either in software or in hardware. The security of information int...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com