Trust chain transfer method for trusted computing platform
A technology of trusted computing and chain of trust, applied in the field of information security, can solve the problems that the verification subject is easily bypassed, untrustworthy, and hijacked by the chain of trust. the effect of prevention
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0027] The method for establishing and transferring the chain of trust described in the description of the present invention includes the following steps:
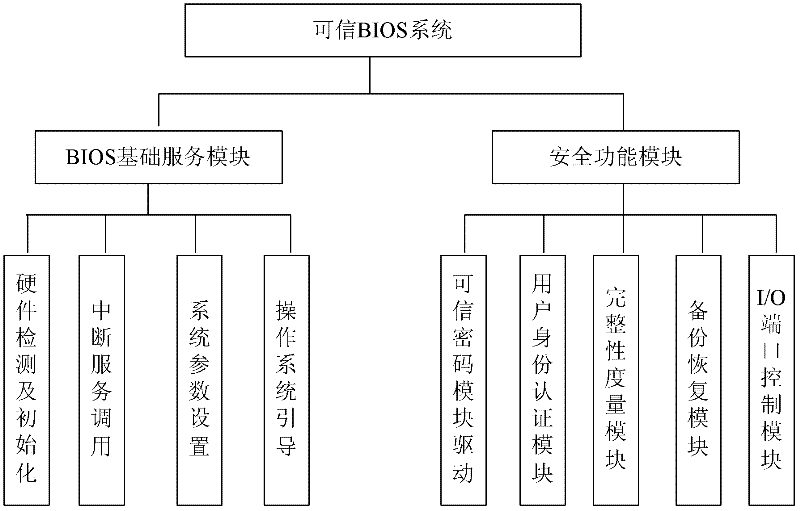
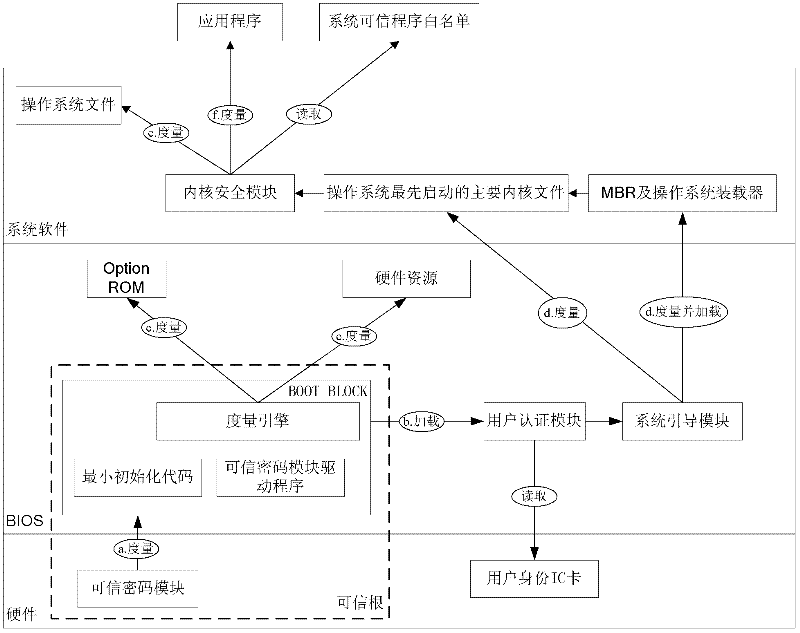
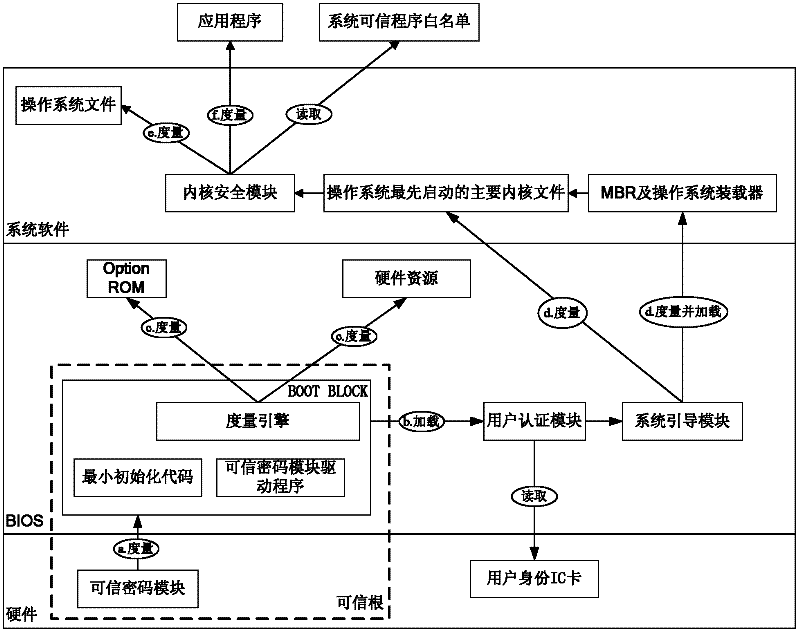
[0028] (1) After the mainboard of the trusted computing platform is powered on, the TCM first powers on to start initialization, and controls the power supply, clock and reset signal lines so that the trusted mainboard is in a reset state, and takes over the control of the system before the CPU is powered on. Actively read the binary code of the BOOT BLOCK of the BIOS through the LPC bus for integrity verification. After the verification is passed, the TCM releases the power supply, clock and reset signals, and connects the LPC bus of the trusted motherboard to the trusted BIOS chip through the internal hardware logic of the trusted platform control module, and the BIOS starts normally. Such as figure 2 The trusted cryptographic module in the medium measures the BOOT BLOCK and transfers the control right as shown in proc...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com