Dynamic trusted measurement method and safe embedded system
An embedded system and reliability technology, applied in computer security devices, instruments, electrical digital data processing, etc., can solve problems such as lack of perfect solutions, achieve physical isolation and get rid of dependence
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
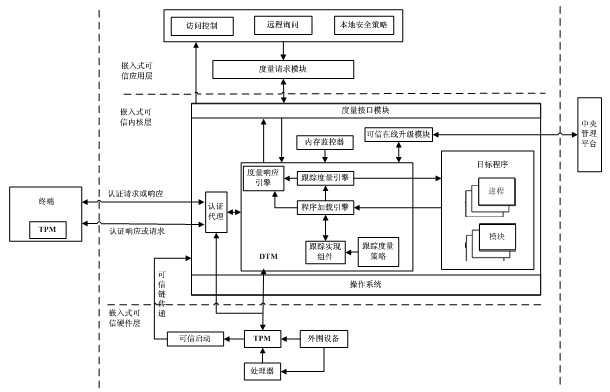
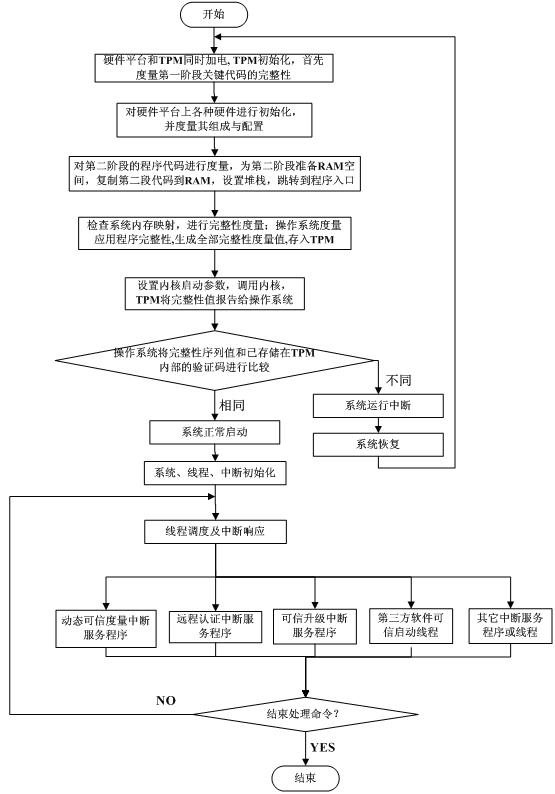
[0047] Embodiments of the present invention: a credibility measurement method utilizing the aforementioned system, comprising the following steps:
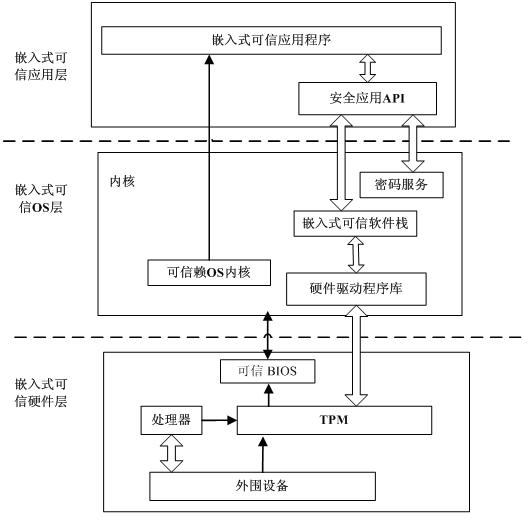
[0048] S1, the hardware layer redesigns the trusted BIOS through the TPM chip and traditional hardware, and the trust chain is passed from the TPM security chip, trusted BIOS, trusted OS kernel, and embedded software stack to the application program to realize the reliability of the dynamic trusted measurement module DTM It is also possible to integrate CRTM (CRTM is the execution code for the platform to execute RTM, and there are three roots of trust in a trusted platform: measurement root of trust RTM, storage root of trust RTS, and report root of trust RTR) into TPM In this way, the CRTM does not directly interact with the main processor of the embedded device, avoiding the impact of platform heterogeneity on the CRTM;
[0049] S2, the application layer measurement request module generates measurement request information...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com