Patents
Literature
150 results about "Isolated environment" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
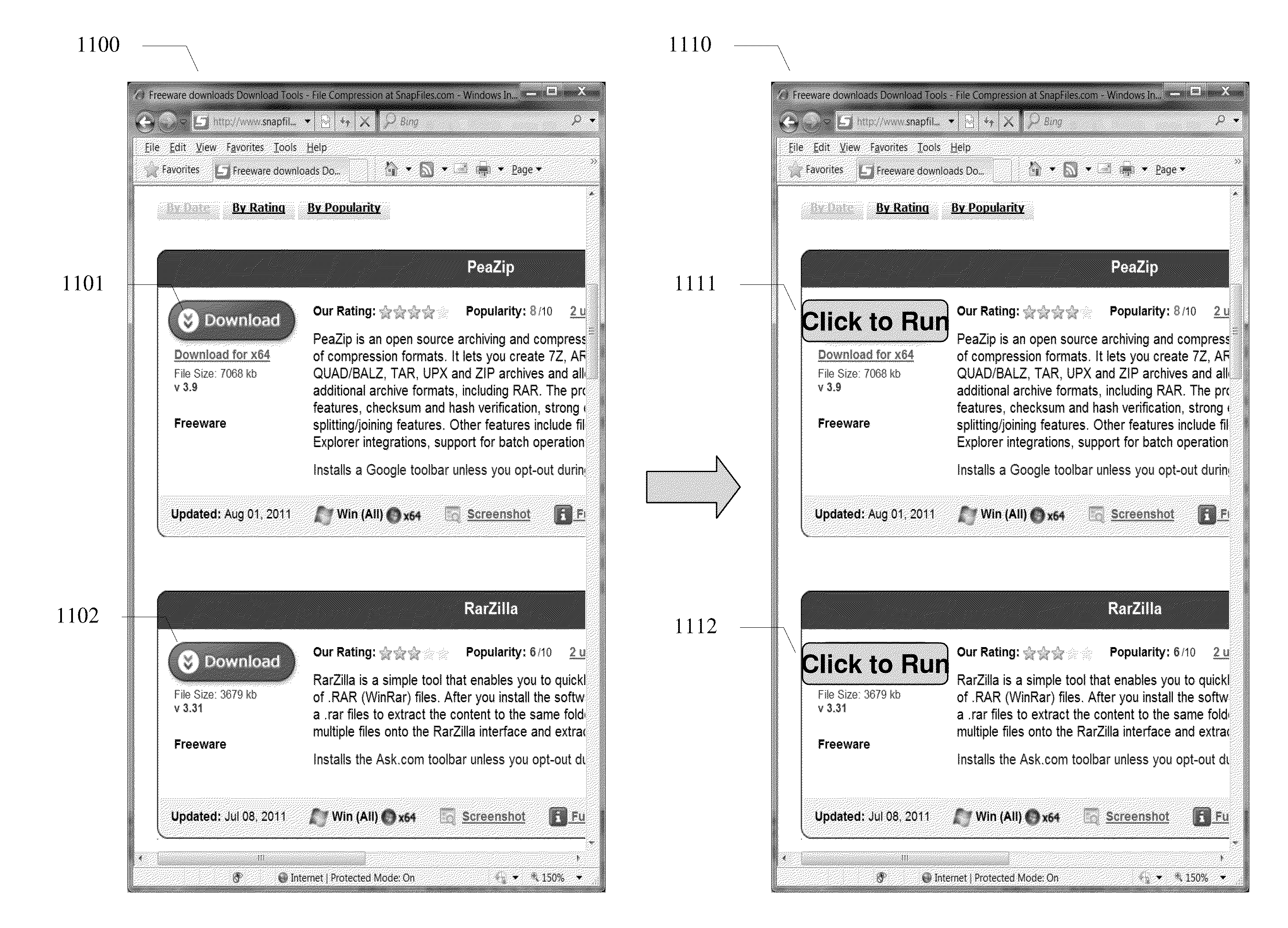
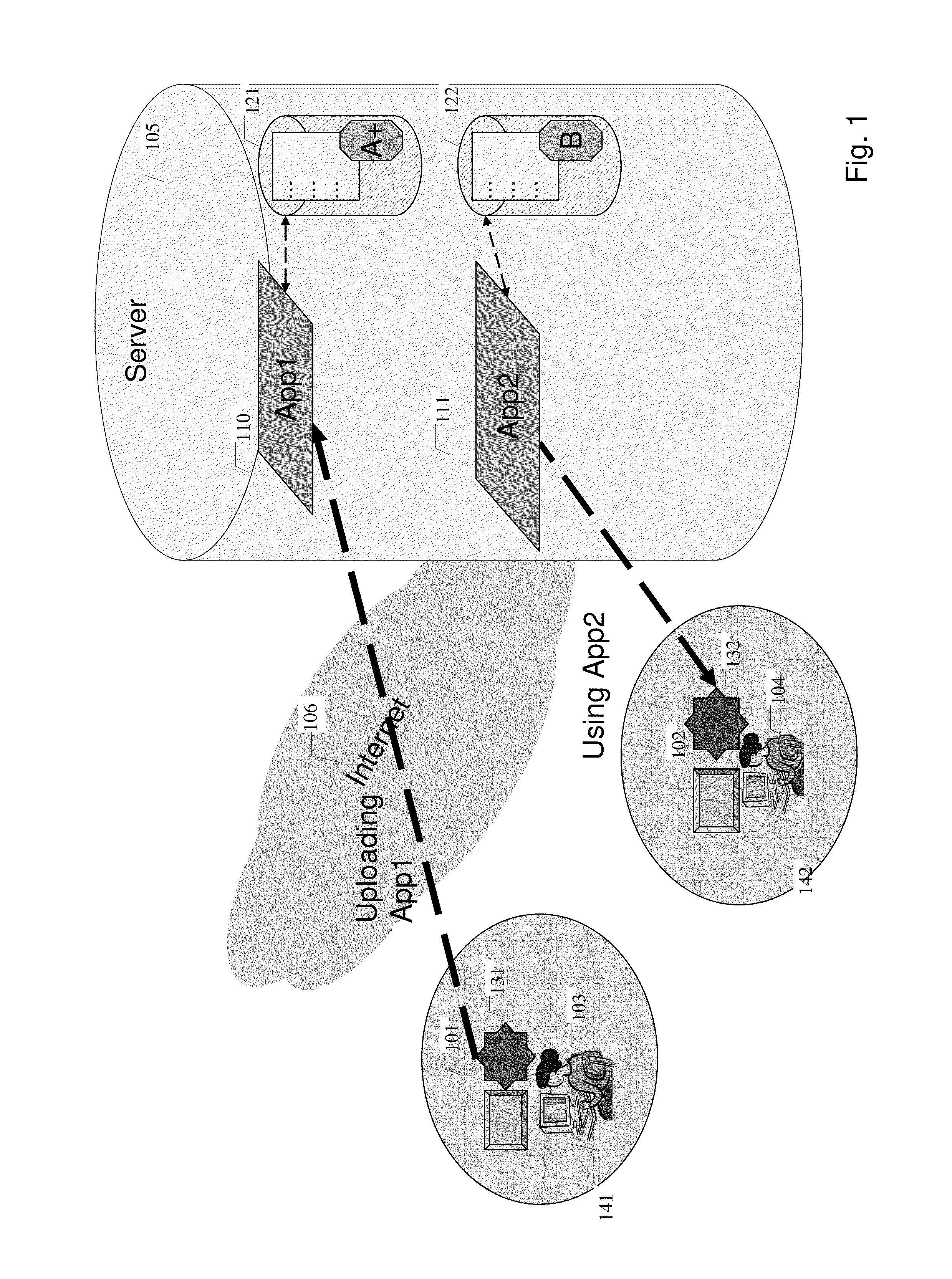
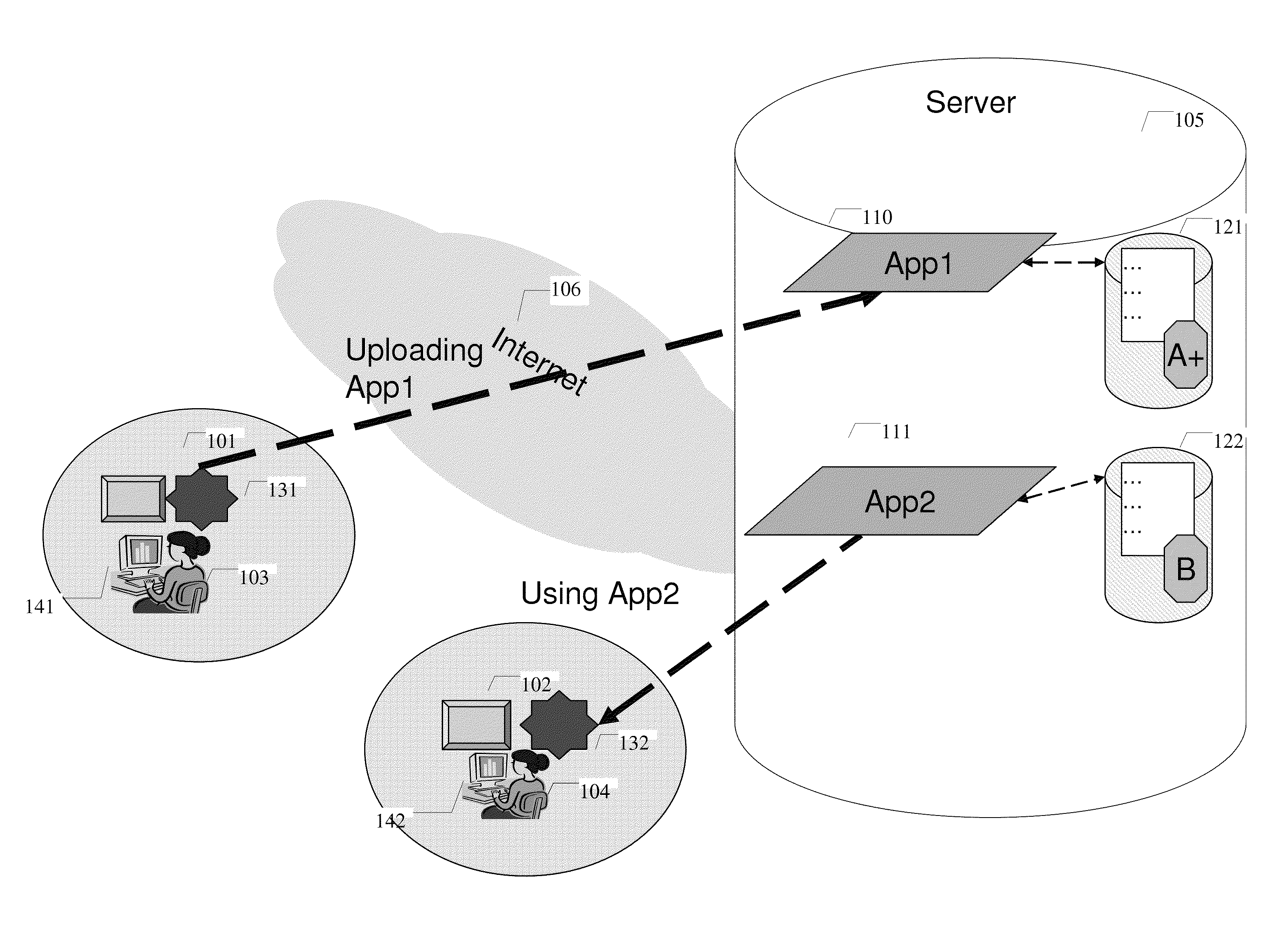
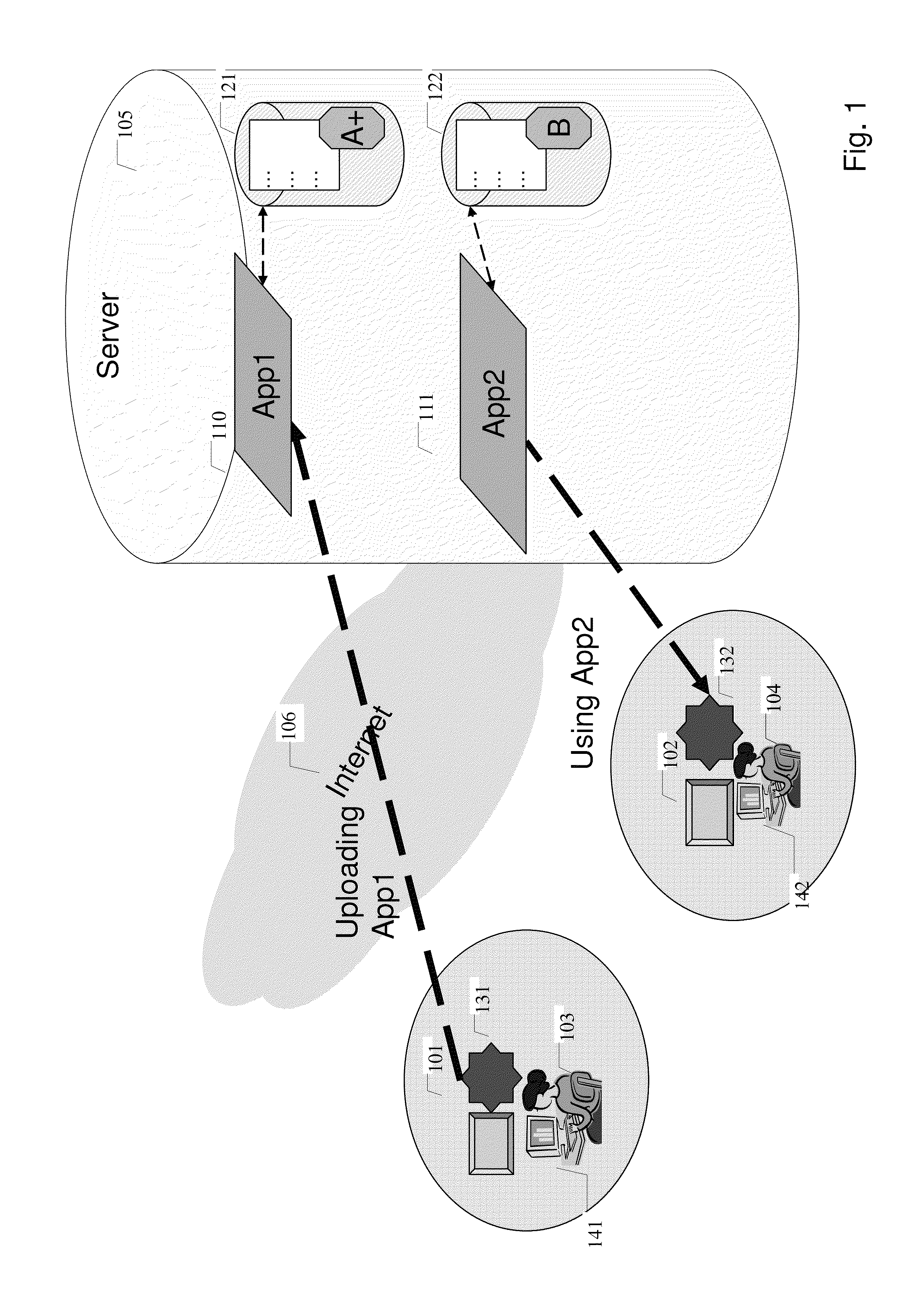
Online software execution platform
ActiveUS20130047149A1Reduce distractionsAccurate measurementText processingProgram code adaptionApplication softwareLocal environment
A system and method for a new type of software repository and remote execution solution where any native application can be run from within a web page is disclosed. Users now has a much easier way to launch, run or execute any software directly from within a server or server cloud without the need of manually download and installation. The system further allows software run inside an isolated environment to protect user's local environment.
Owner:YONGYONG XU
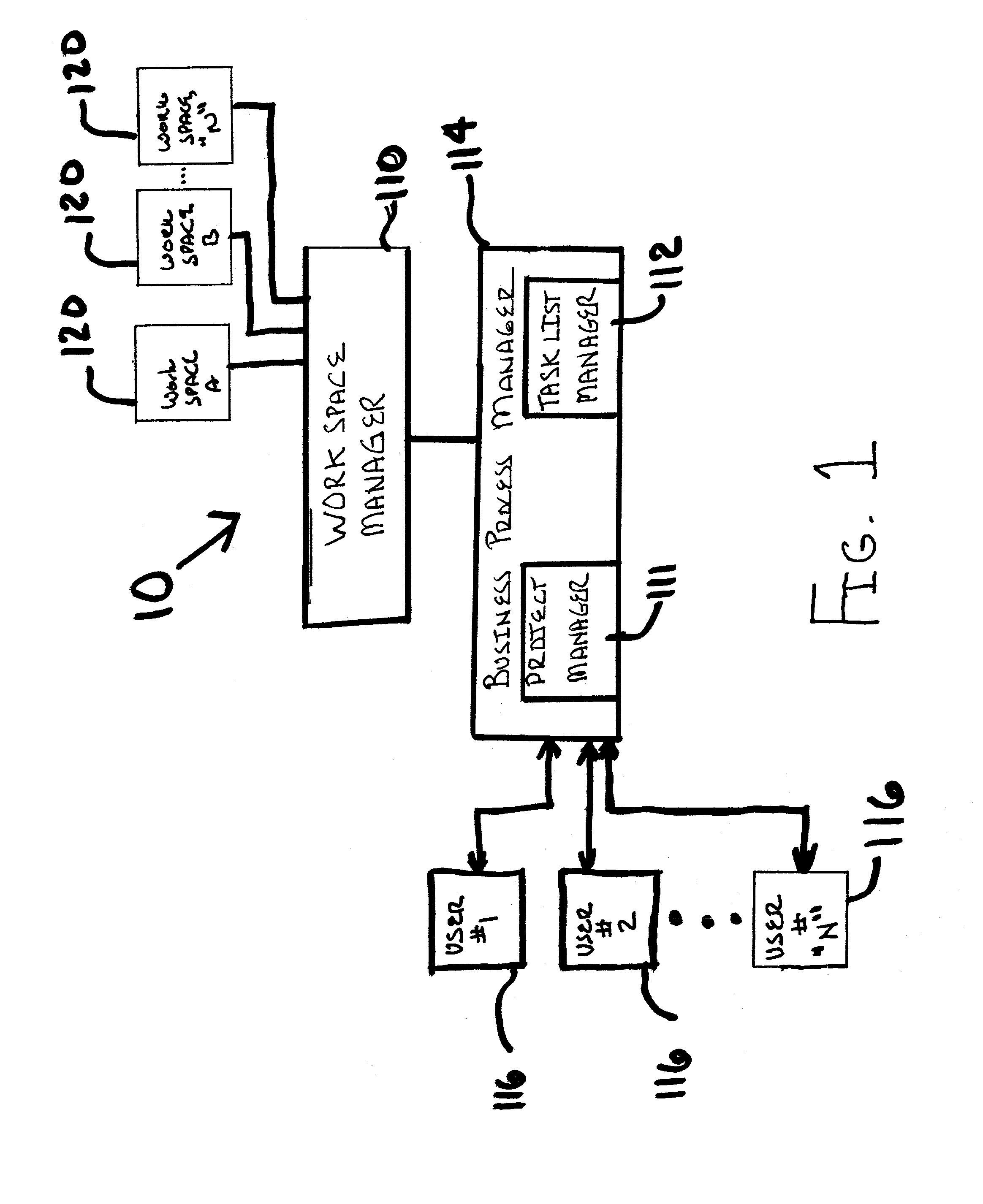
Framework to model and execute business processes within a collaborative environment
InactiveUS7386797B1Input/output for user-computer interactionOffice automationWorkspaceGood practice
A mechanism of specification of business process templates, to capture commonly performed business activities / workflows / projects within a business organization and encourage reuse of best practices. Long transaction workspaces based business process template execution mechanism are presented, which have several advantages over existing business process execution mechanisms in web collaboration frameworks. This execution approach provides support for an isolated environment for business process execution. This isolates the changes made on different resources while executing a business process from the external world until the business process completes. It enables the ability to concurrently manipulate same resources in different components of a business process, and later resolve conflicts if any and merge the different views of the same resource manipulated by different components of a business process. It also enables easy and effective mechanisms for error recovery and rollback during business process execution.
Owner:ORACLE INT CORP
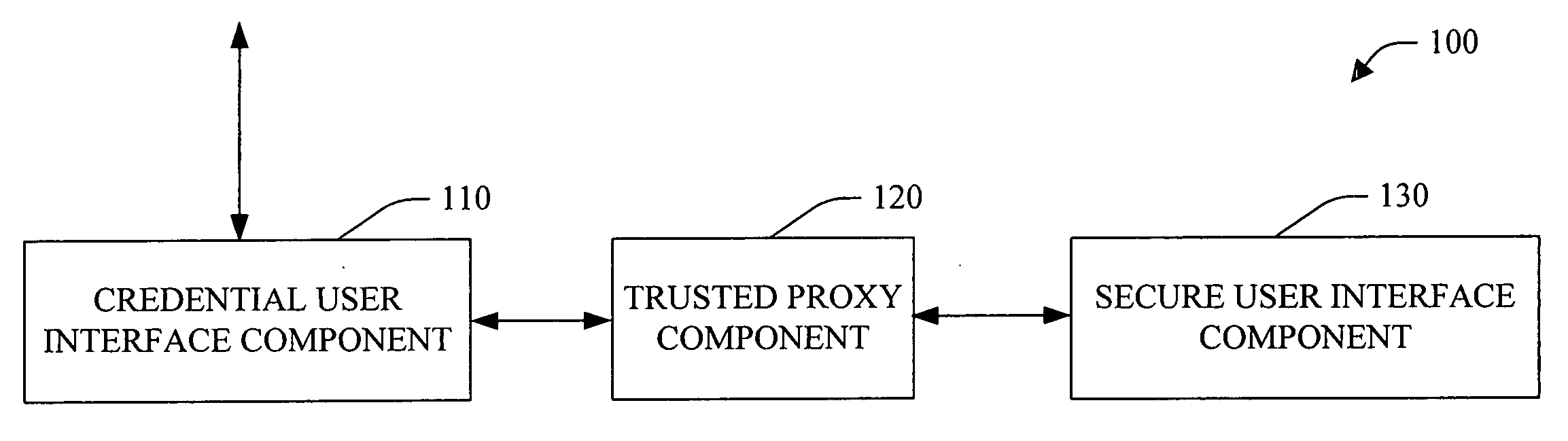
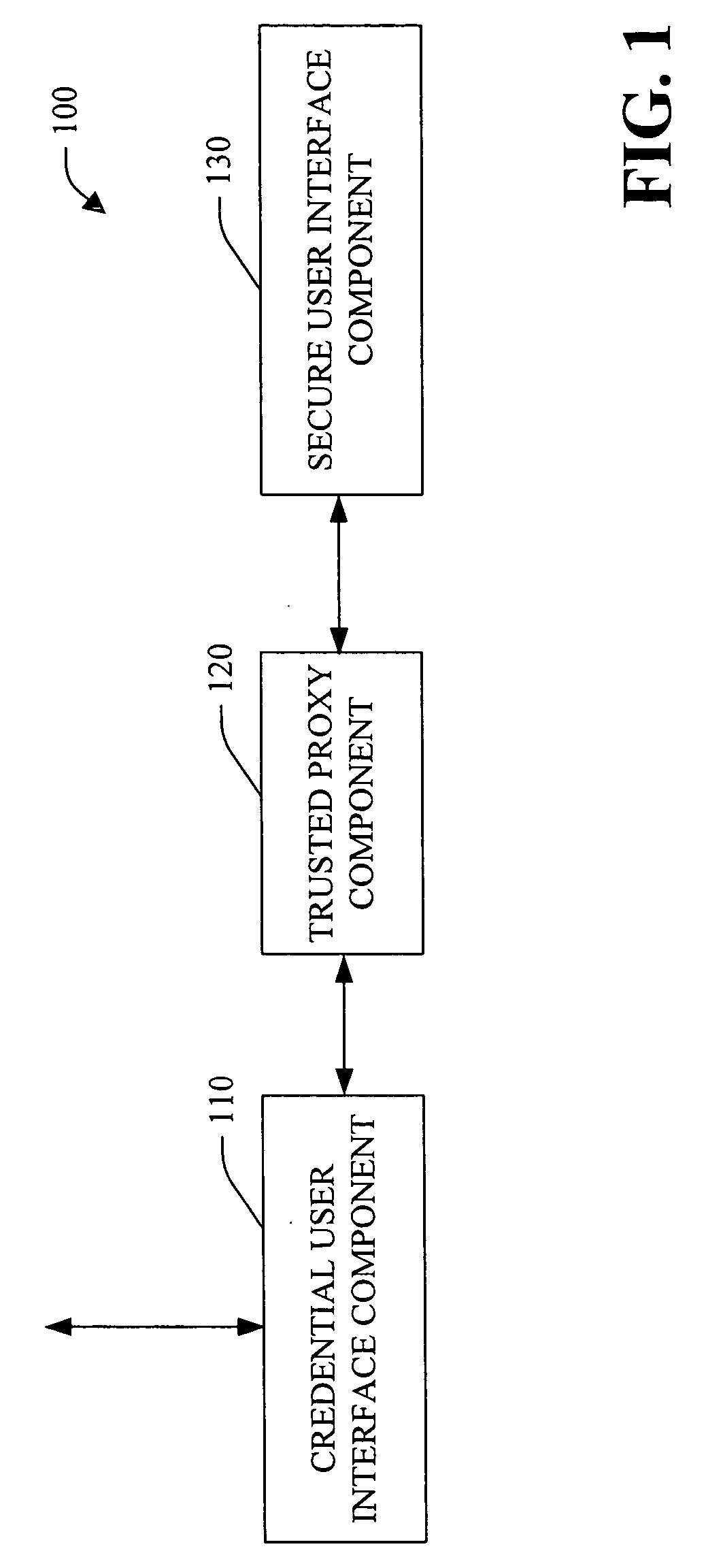
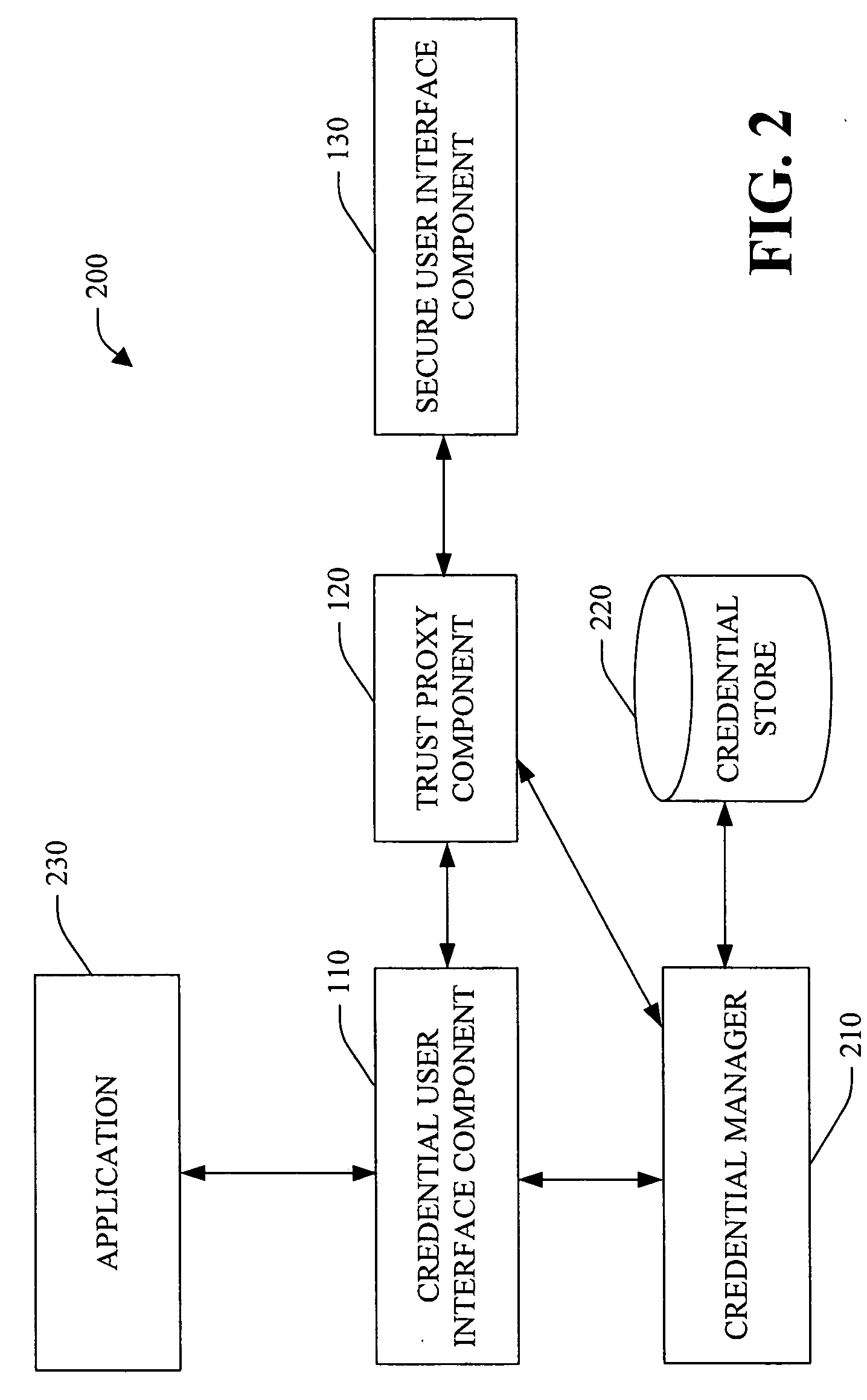
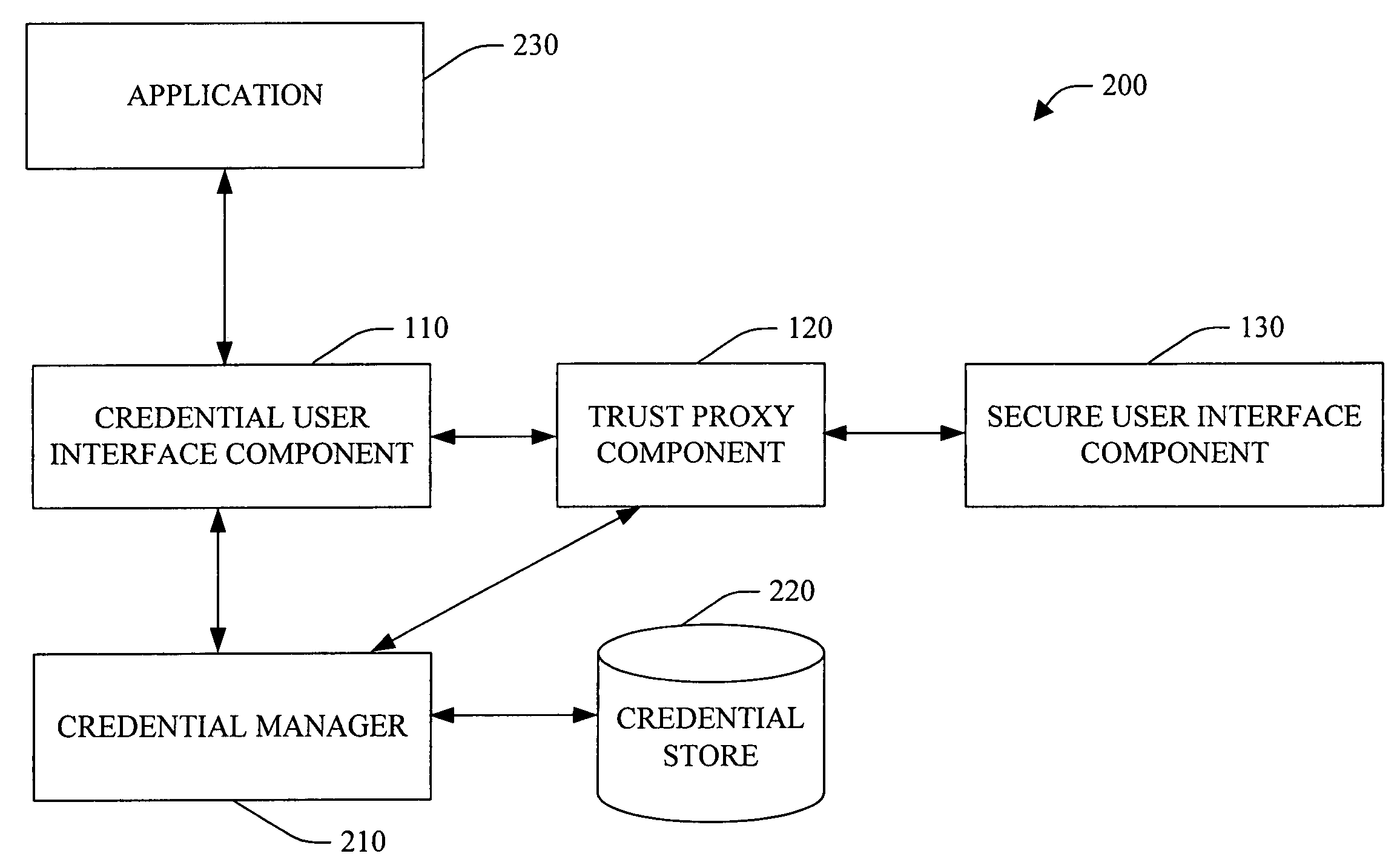
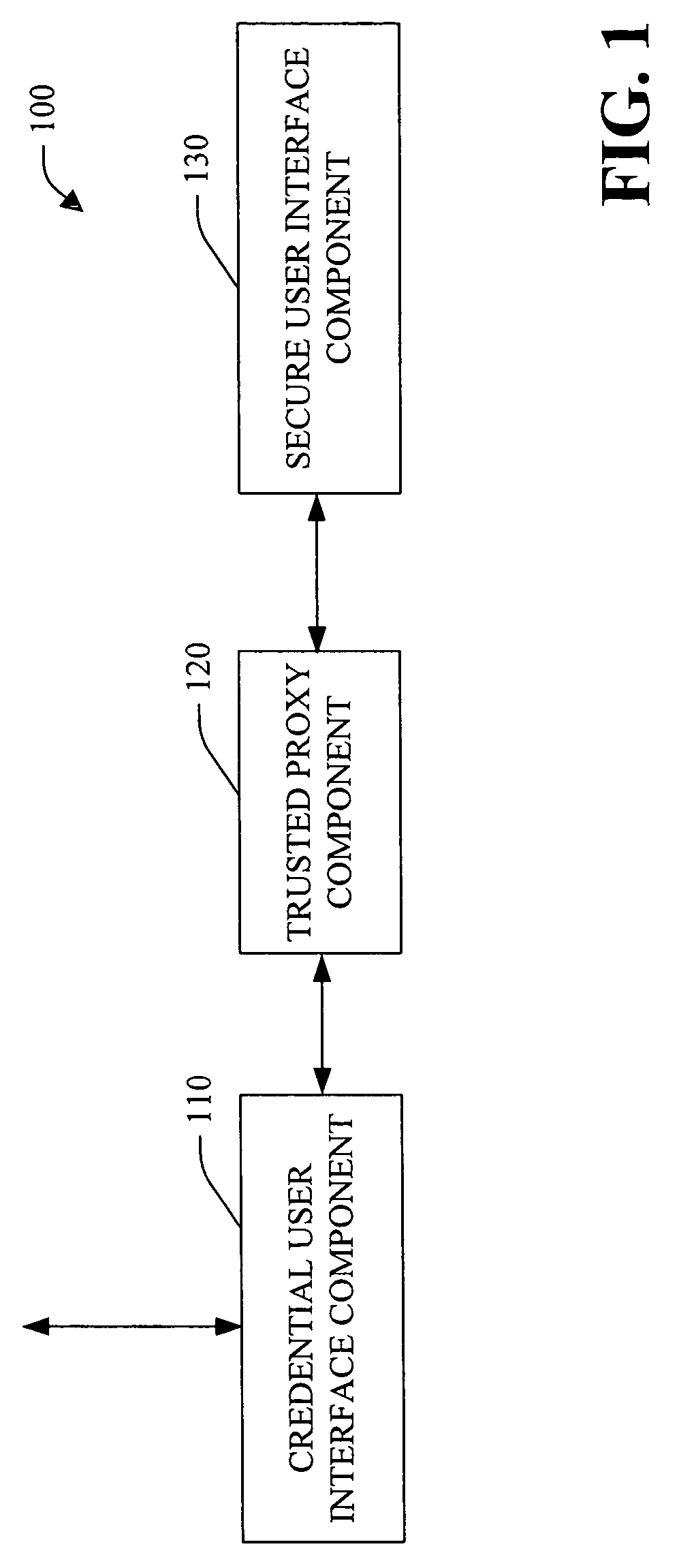
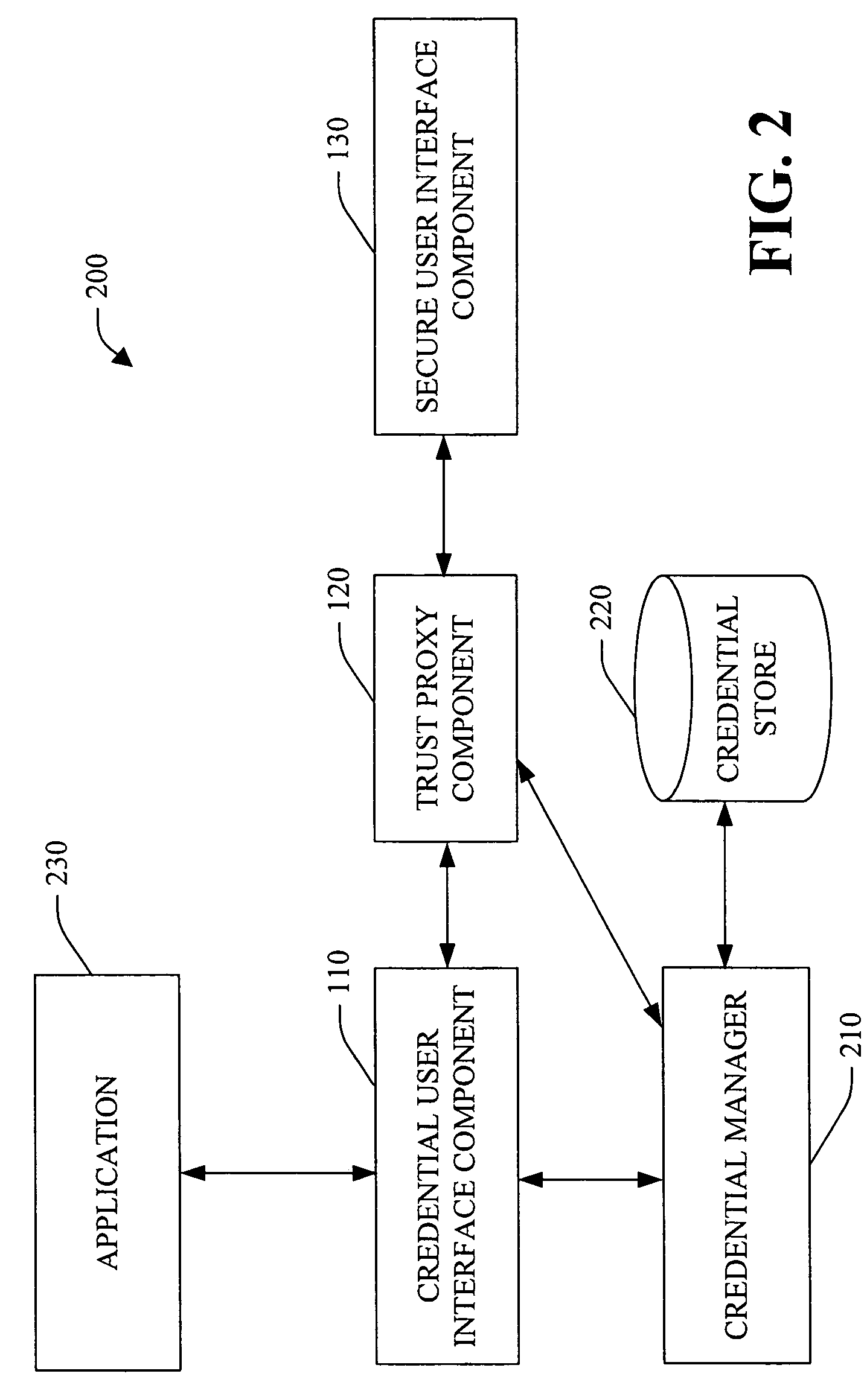
System and method facilitating secure credential management
ActiveUS20050188210A1Safety managementImprove protectionUser identity/authority verificationInternal/peripheral component protectionOperational systemCredential management
A system and method facilitating secure credential management is provided. An aspect of the present invention provides for a credential management system including a credential user interface component, a trusted proxy component and a secure user interface component. The system can facilitate the secure acquisition, storage and / or application of credential(s) for a user (e.g., when accessing a particular resource) through a secure, isolated environment. For example, the system can be a core building block for operating system component(s) and / or application(s) that handle credential(s) in a secure manner.
Owner:MICROSOFT TECH LICENSING LLC
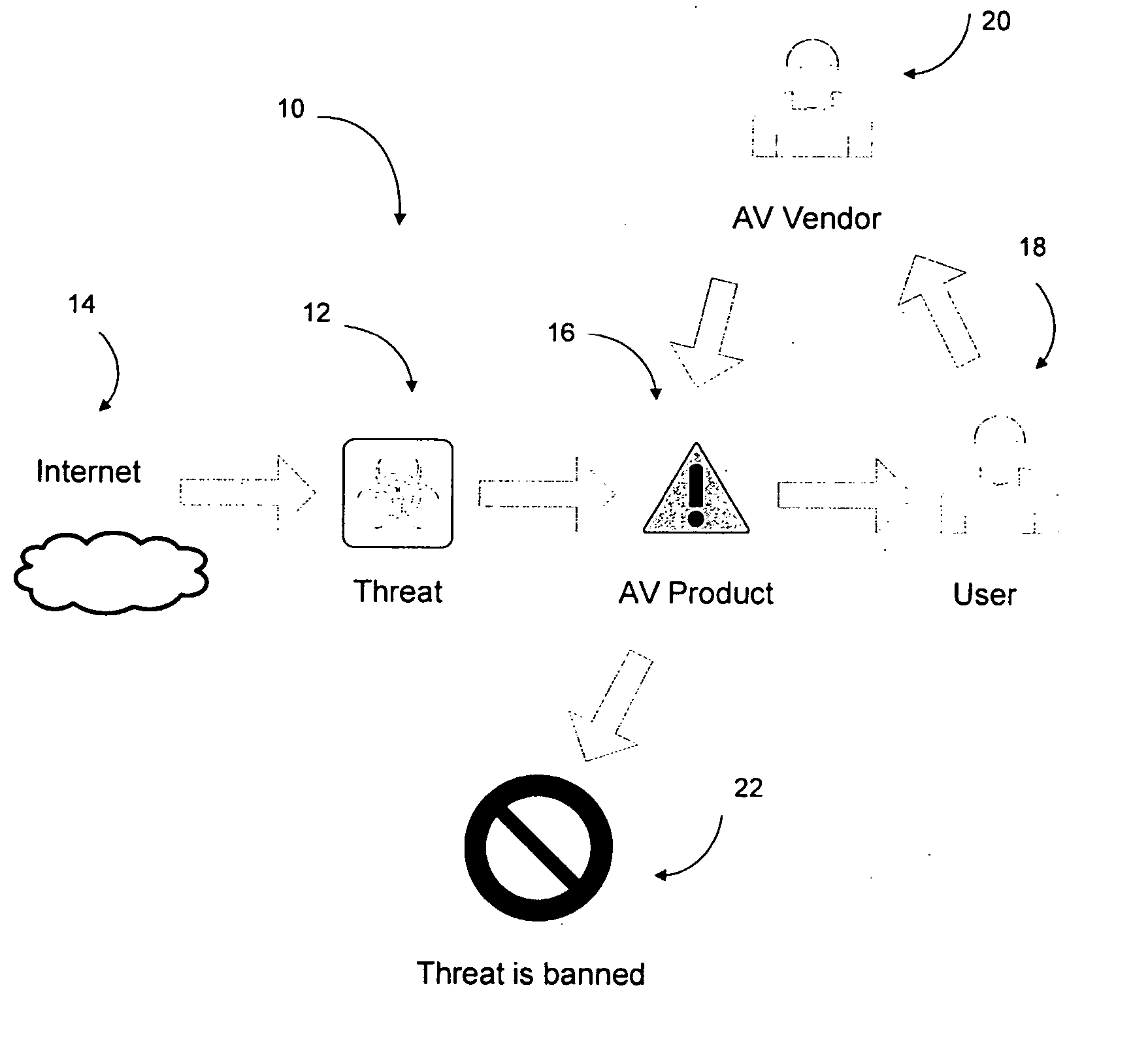
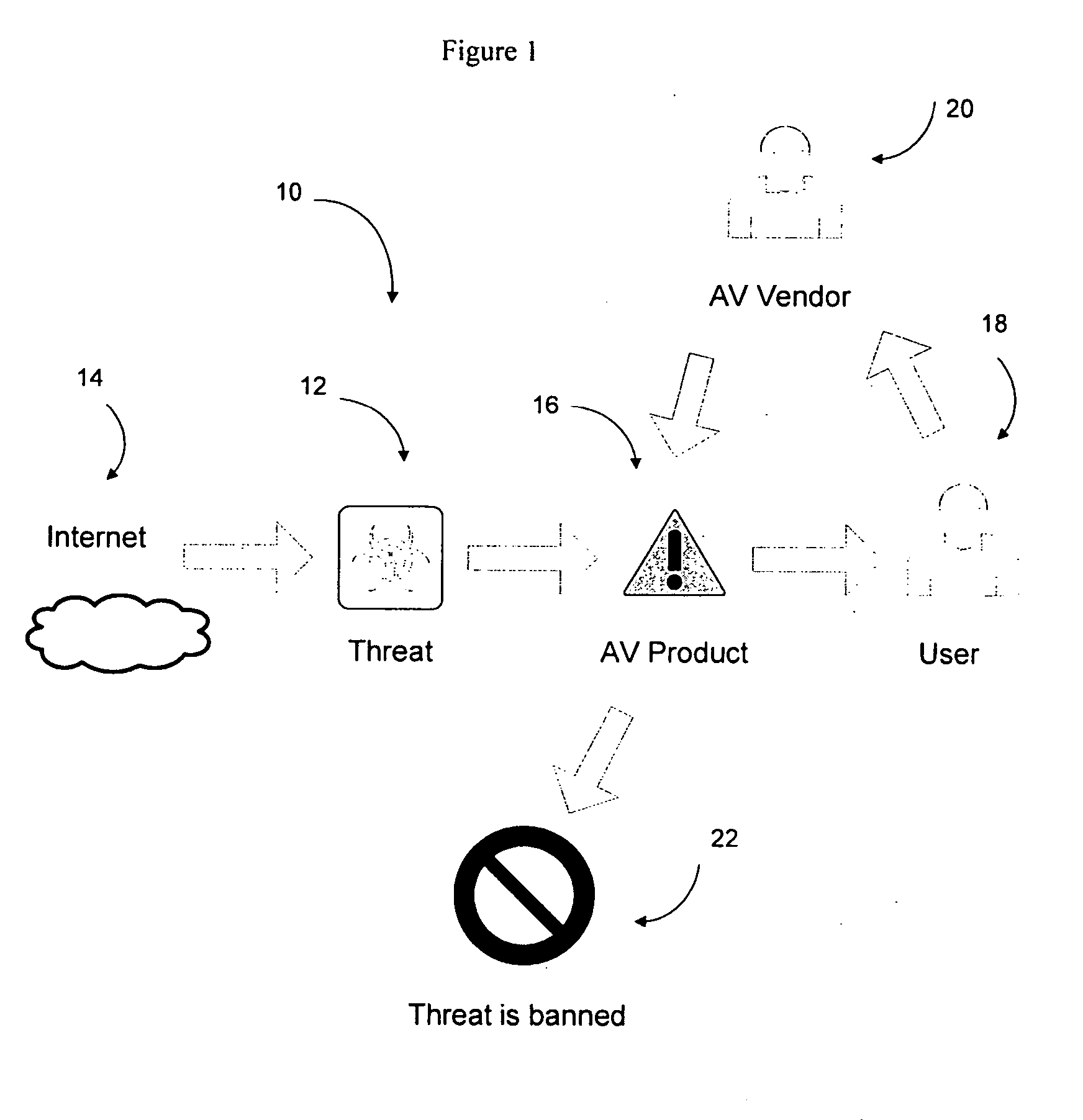
Automated threat analysis
InactiveUS20070283192A1Shorten the timeMore informationError detection/correctionComputer security arrangementsOperational systemCore component
An automated threat analysis system comprising a core in an isolated environment, the core associated with an input interface and an output interface. The core comprises one or more core components and an operating system having at least one library hooked to at least one of the one or more core components. In use, a threat (eg. malicious software) is passed into the core via the input interface and the threat is executed in the core using the operating system. Report data is generated by the one or more core components which monitors the functions / processes occurring in the system as a result of the threat, and the report data is passed out of the core via the output interface according to a predefined format so as to isolate any output from or escape of the threat.
Owner:SYMANTEC CORP
System and method facilitating secure credential management
ActiveUS7783891B2Safety managementImprove protectionUser identity/authority verificationInternal/peripheral component protectionOperational systemCredential management
A system and method facilitating secure credential management is provided. An aspect of the present invention provides for a credential management system including a credential user interface component, a trusted proxy component and a secure user interface component. The system can facilitate the secure acquisition, storage and / or application of credential(s) for a user (e.g., when accessing a particular resource) through a secure, isolated environment. For example, the system can be a core building block for operating system component(s) and / or application(s) that handle credential(s) in a secure manner.
Owner:MICROSOFT TECH LICENSING LLC
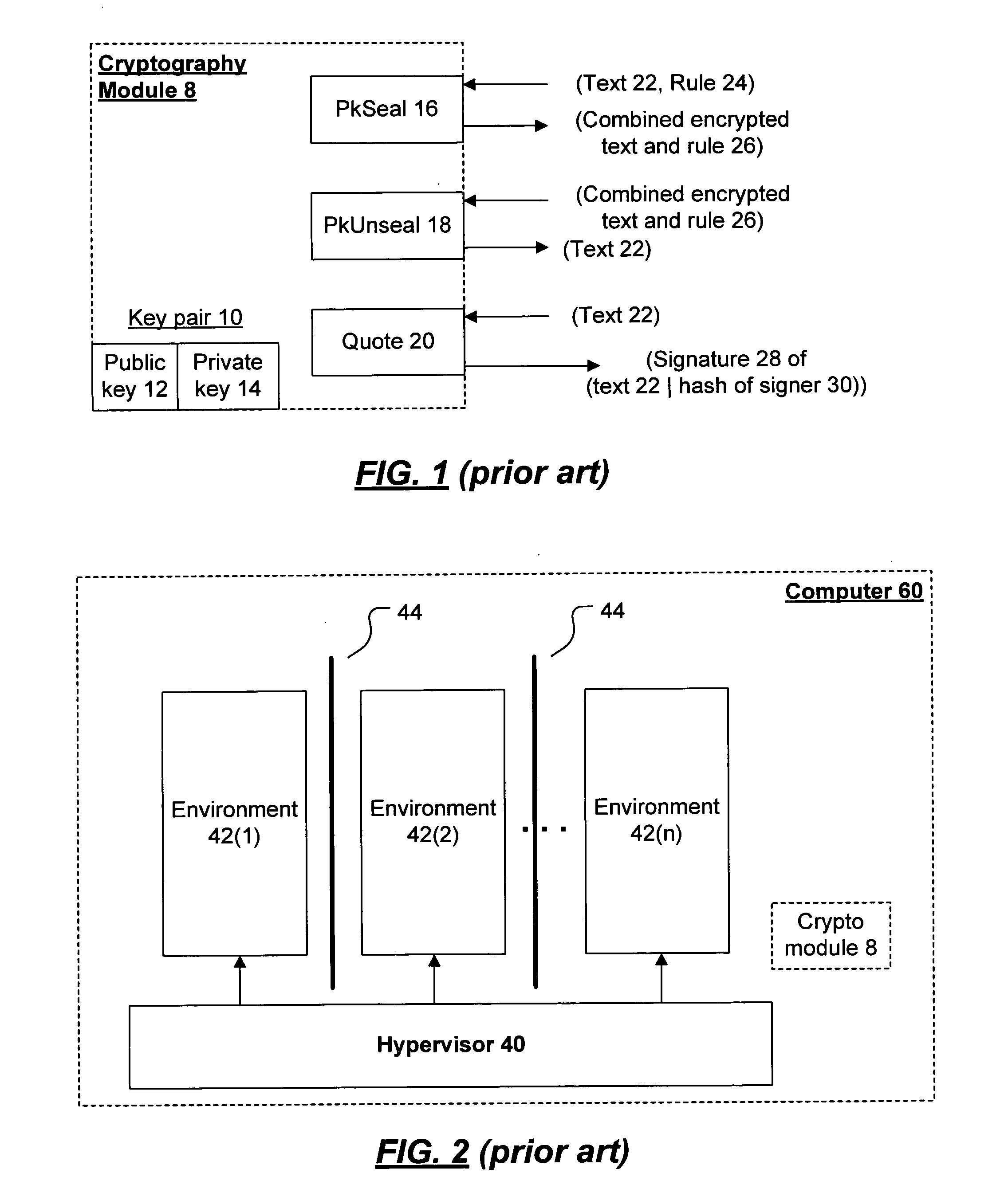
System and method for application isolation with live migration
InactiveUS8539488B1Error detection/correctionMultiprogramming arrangementsApplication softwareComputer science
A system, method, computer program, and / or computer readable medium for providing application isolation and live migration to one or more applications and their associated resources. The computer readable medium includes computer-executable instructions for execution by a processing system. The computer-executable instructions may be for creating a new isolated environment, for creating a copy of an isolated environment, live migrating applications within and between isolated environments, and for deploying an isolated environment Further, the instructions may be for launching one or more applications within one or more isolated environment, for terminating one or more applications within one or more isolated environments, for configuring resource mappings, exceptions and policies, for triggering a live migrate, and for delivery of one or more applications within isolated environments over the network.
Owner:IBM CORP
Managing the flow of data traffic
InactiveUS20050265317A1Error preventionFrequency-division multiplex detailsTraffic capacityClient-side
Owner:BROCADE COMMUNICATIONS SYSTEMS
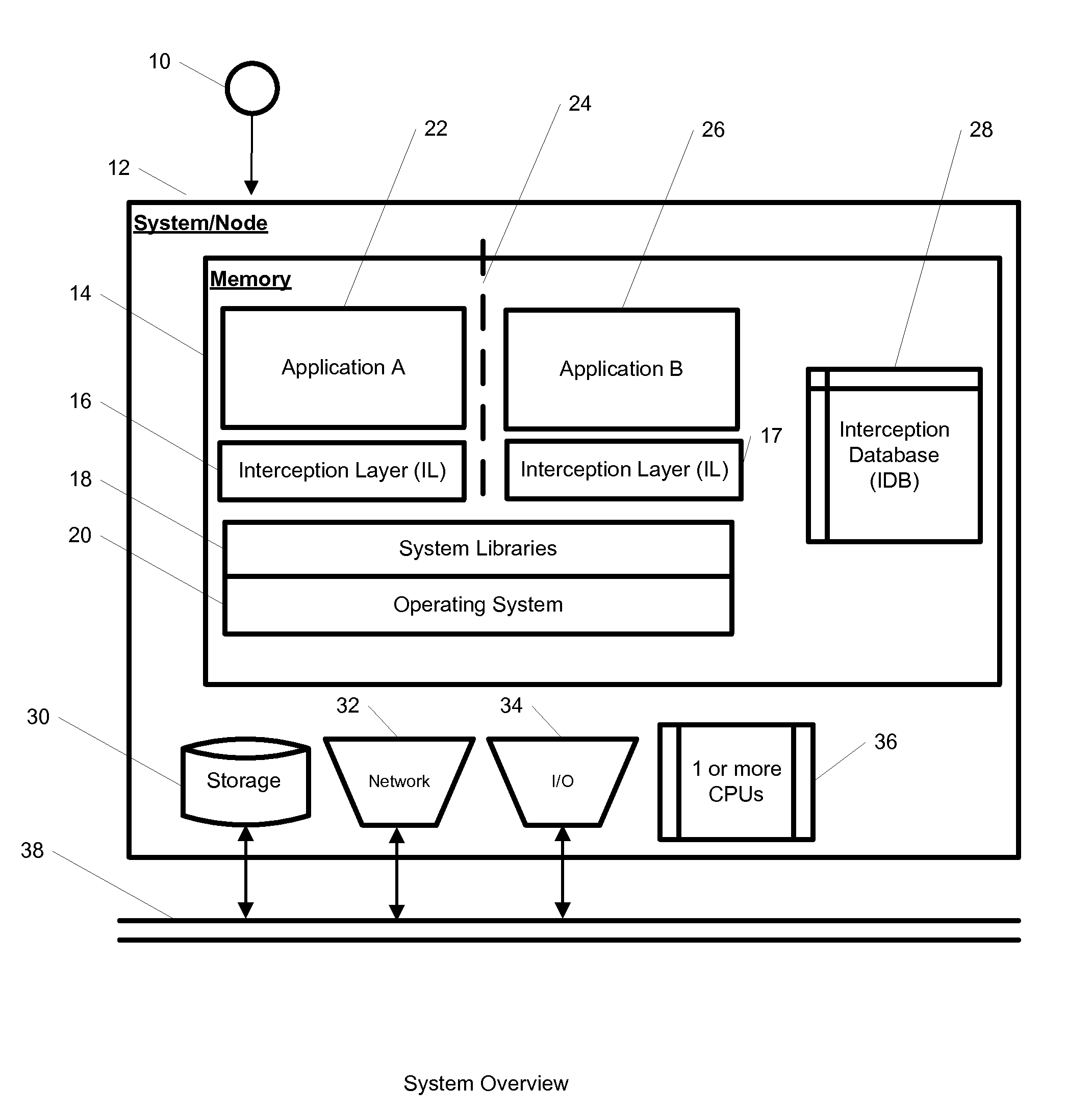
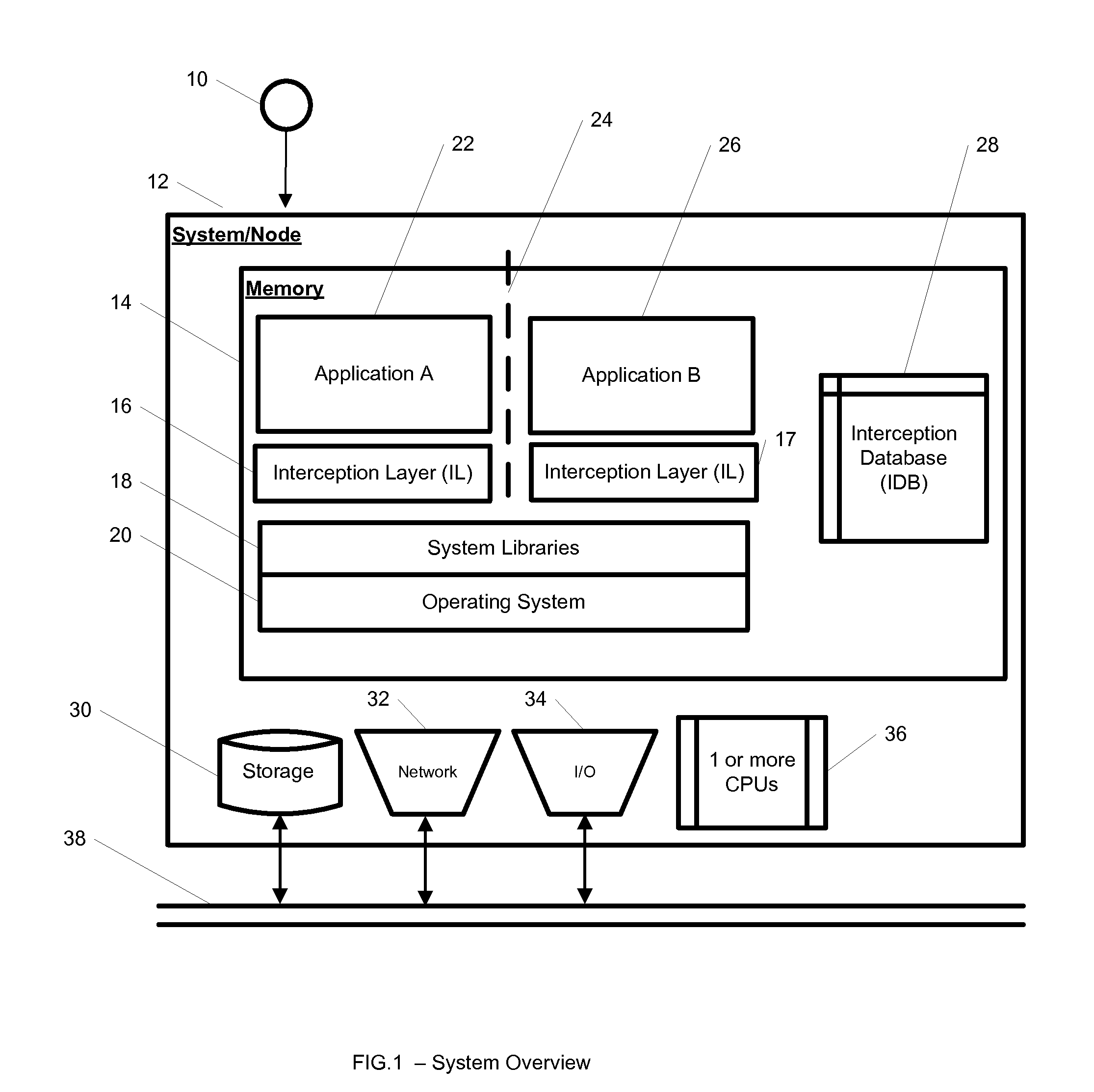
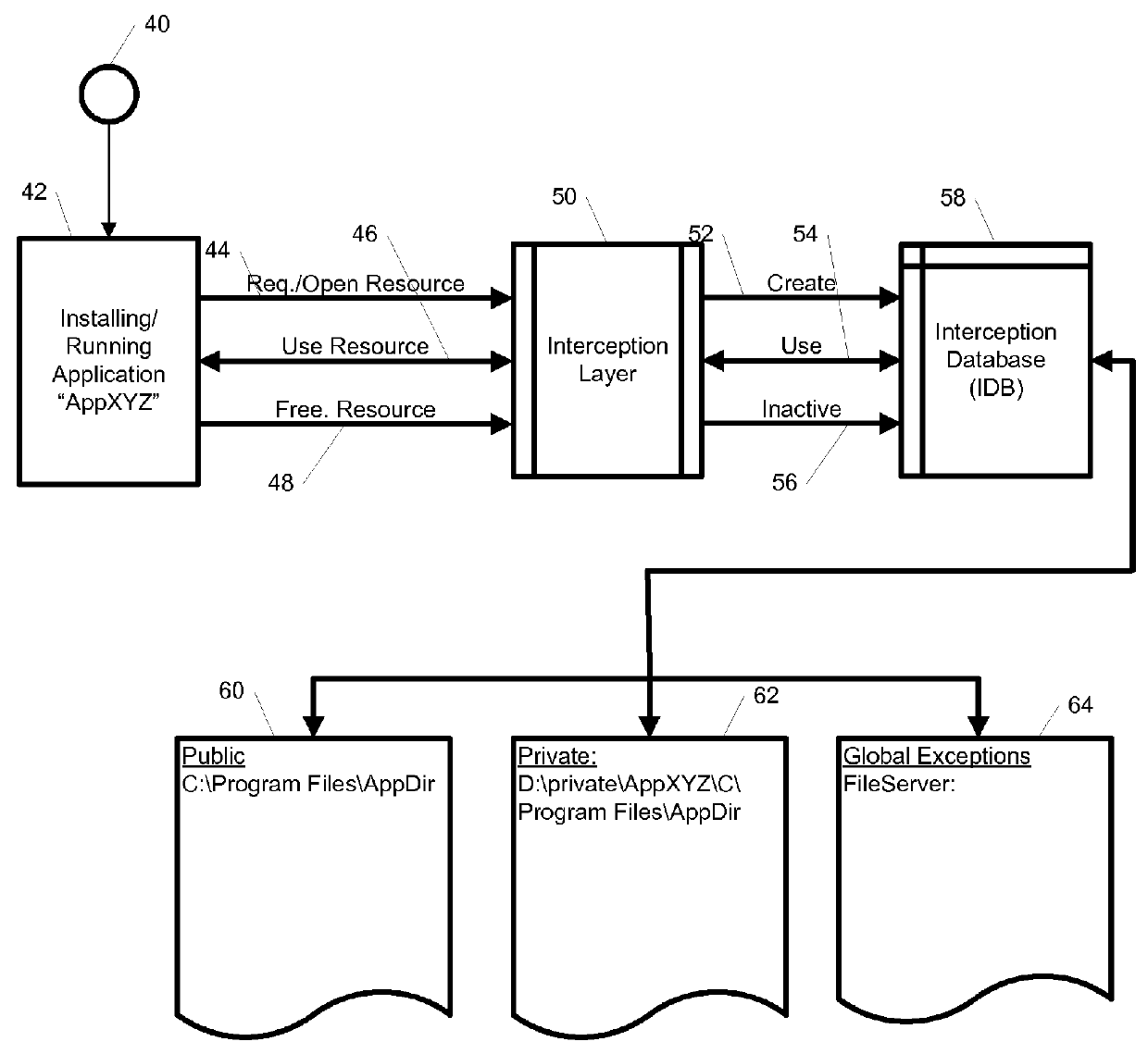
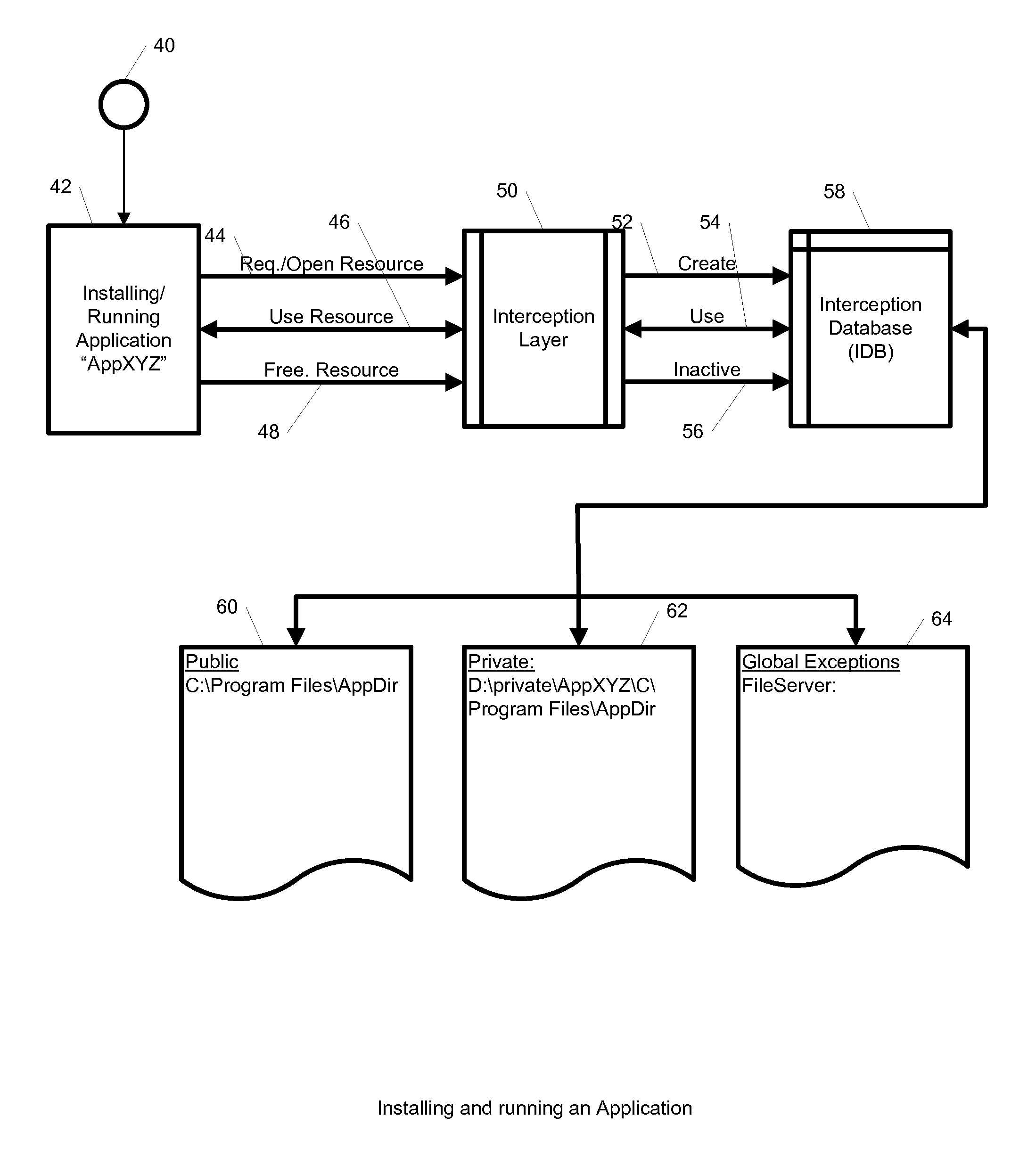
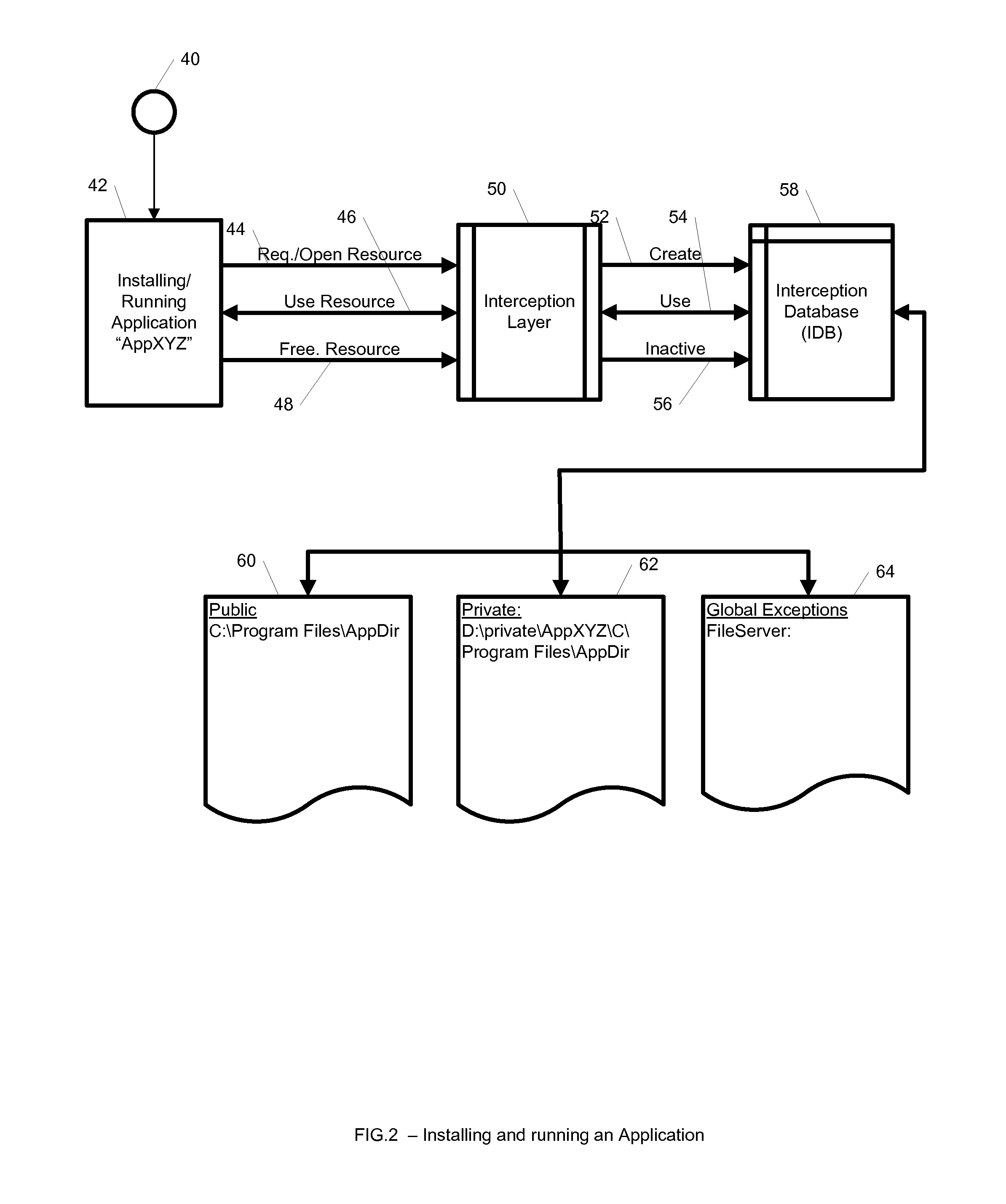
System and Method for Application Isolation
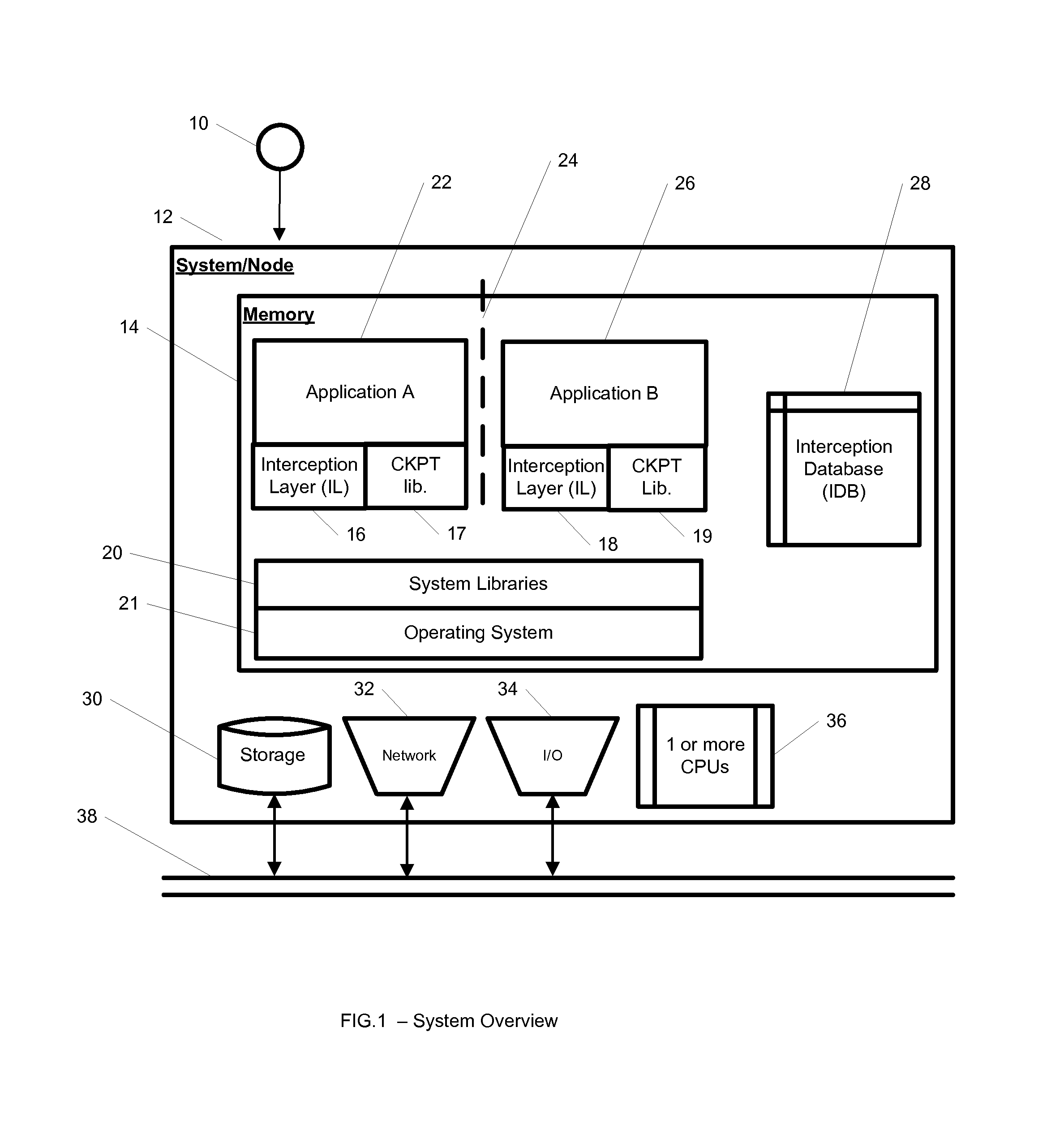
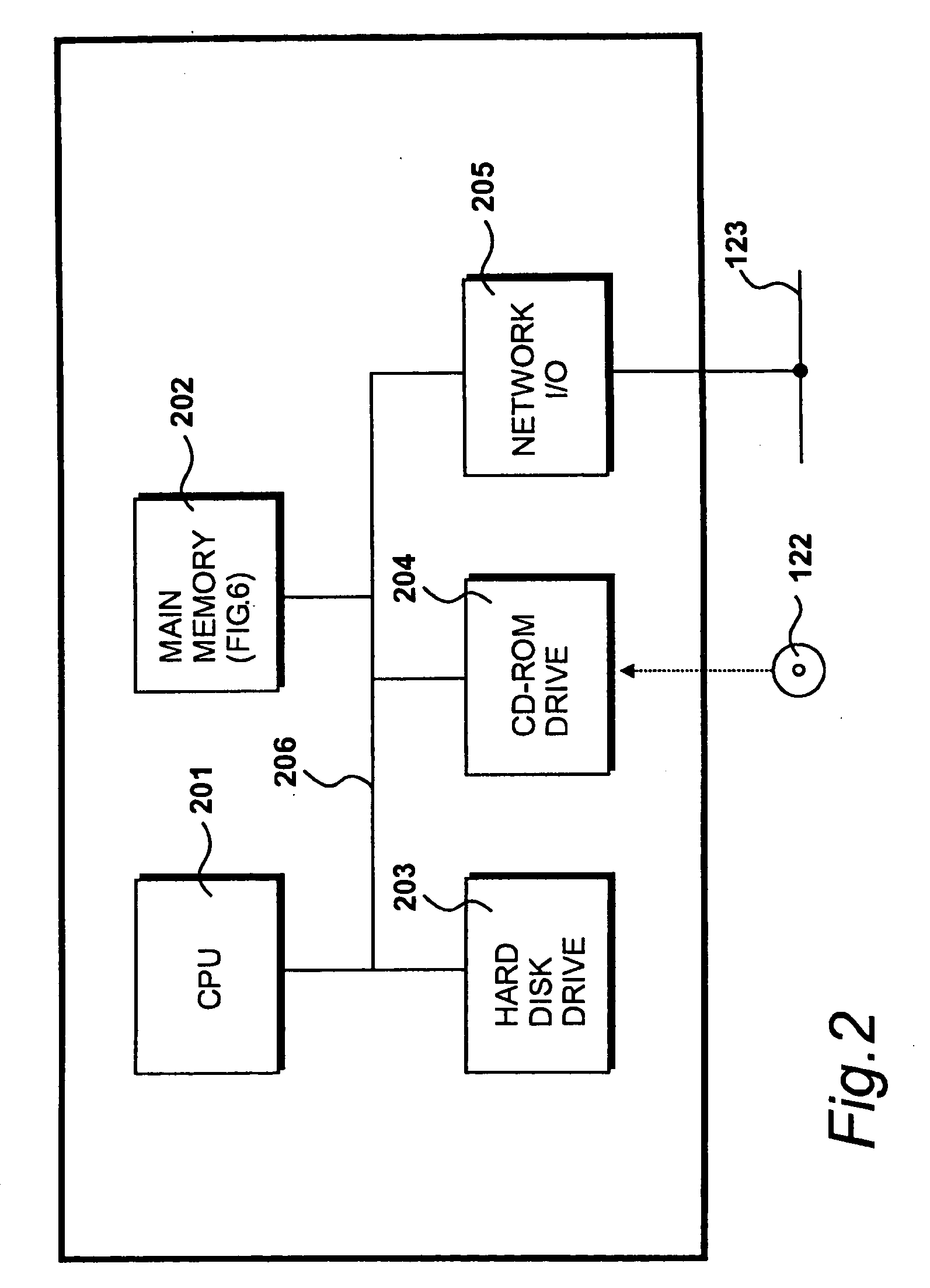
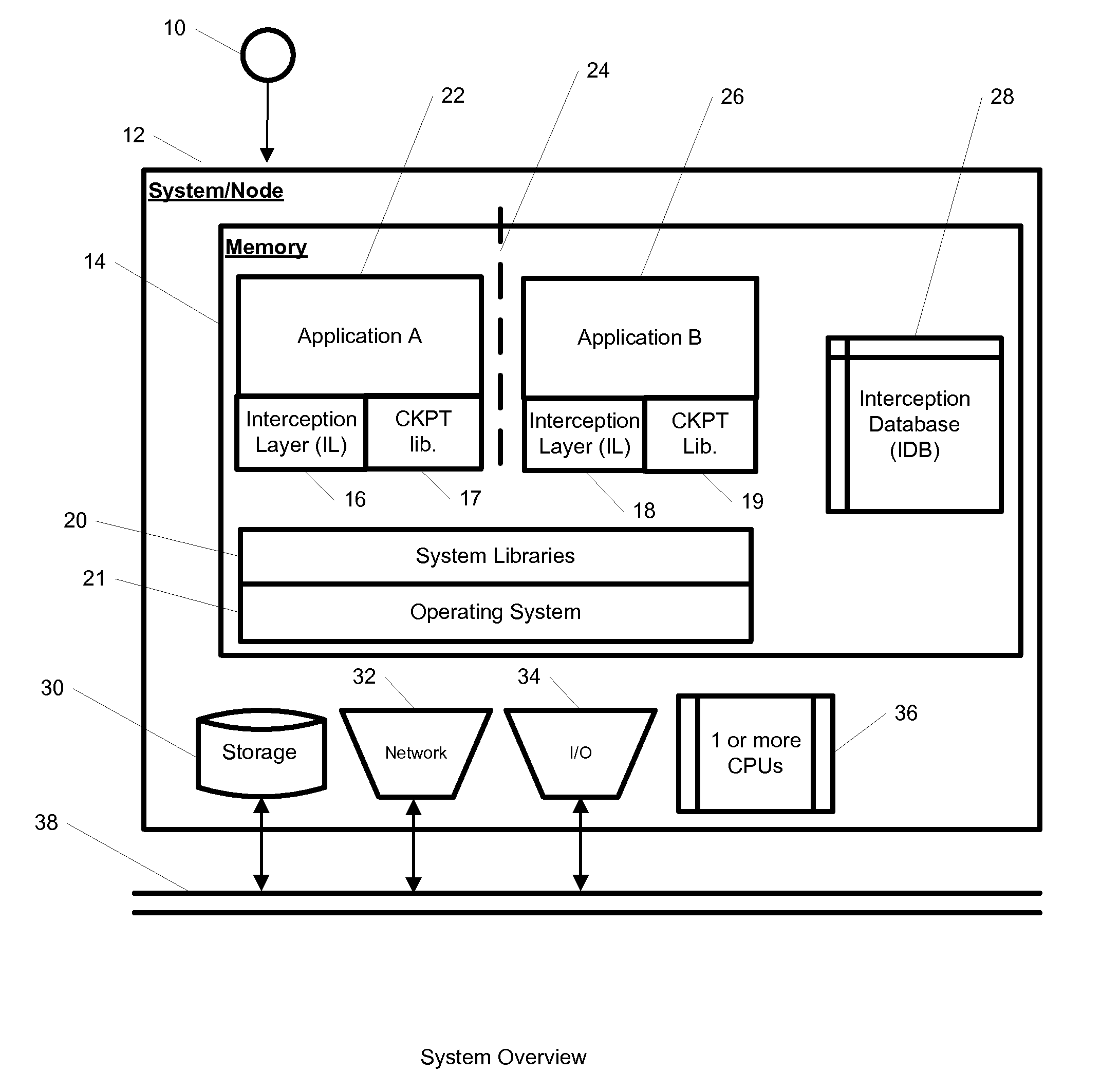
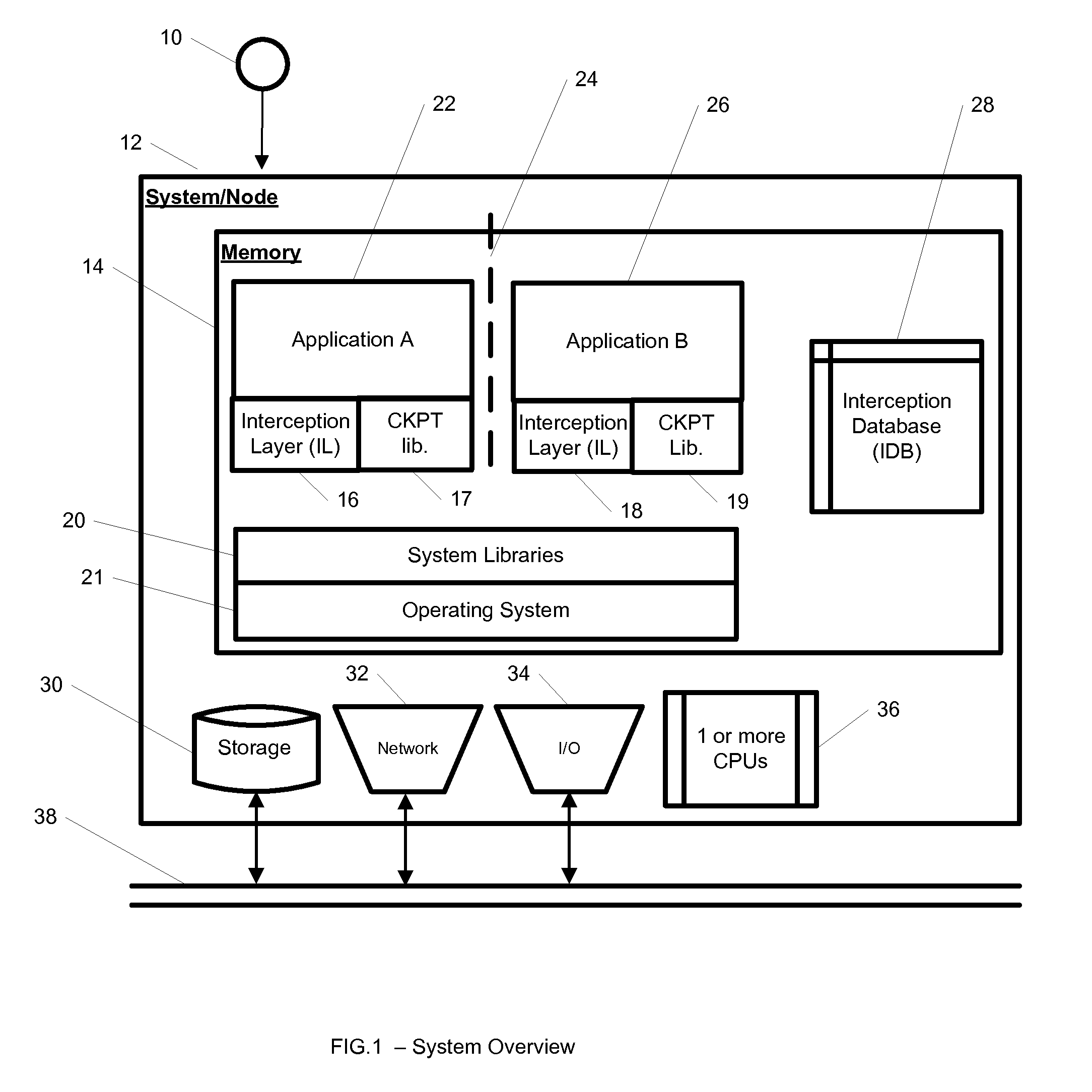
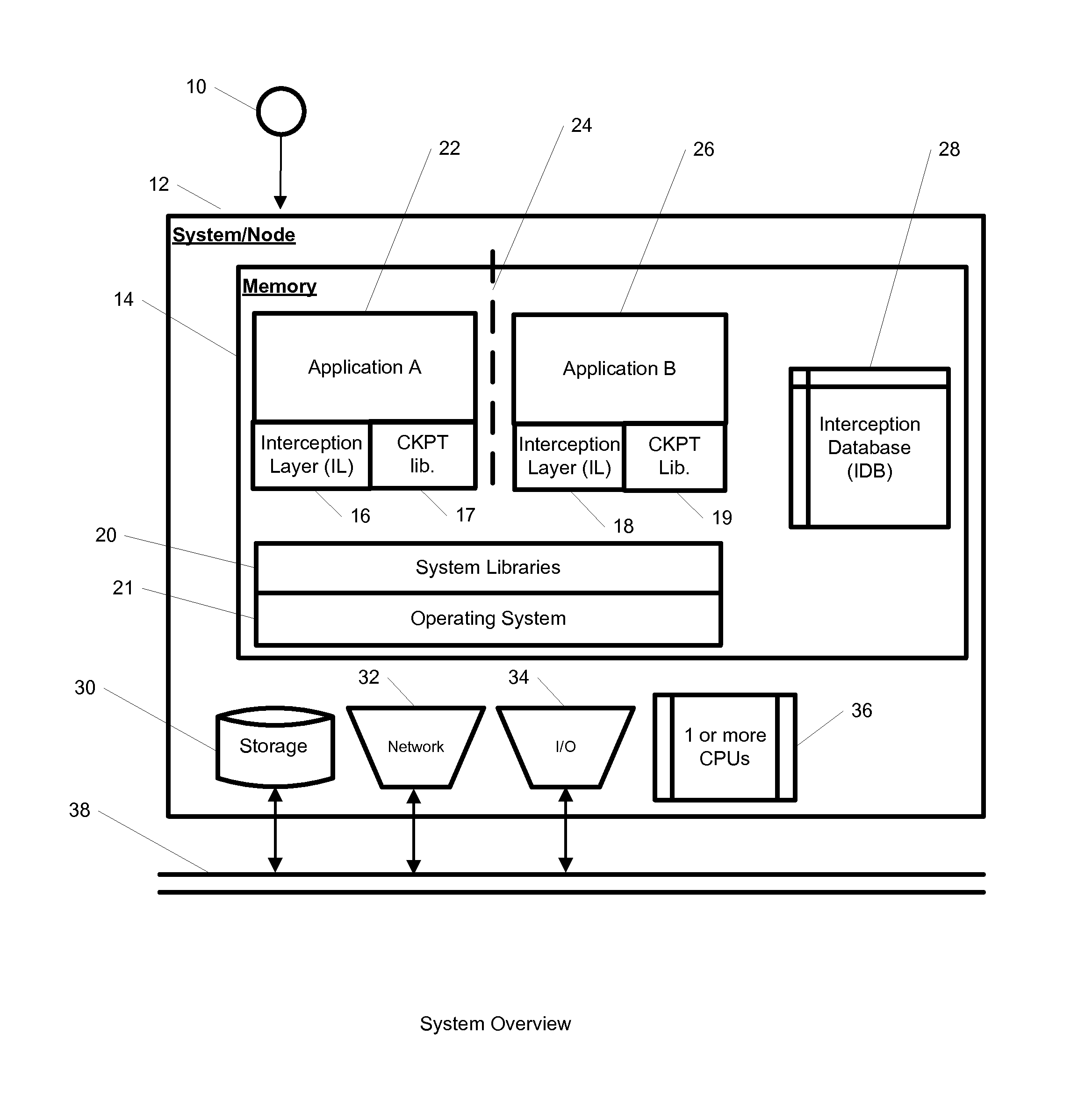
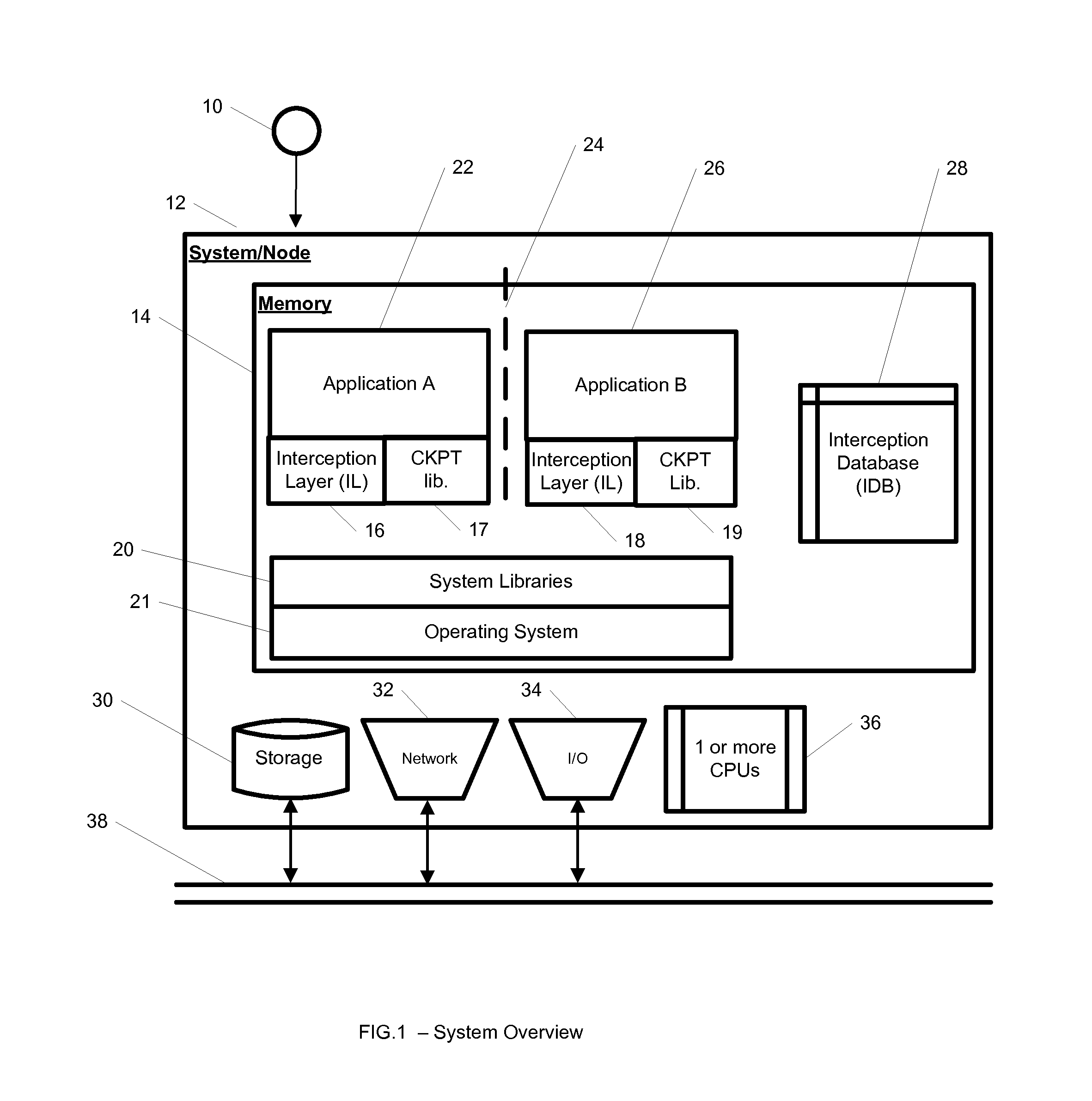
InactiveUS20100262977A1Program synchronisationError detection/correctionOperational systemApplication software
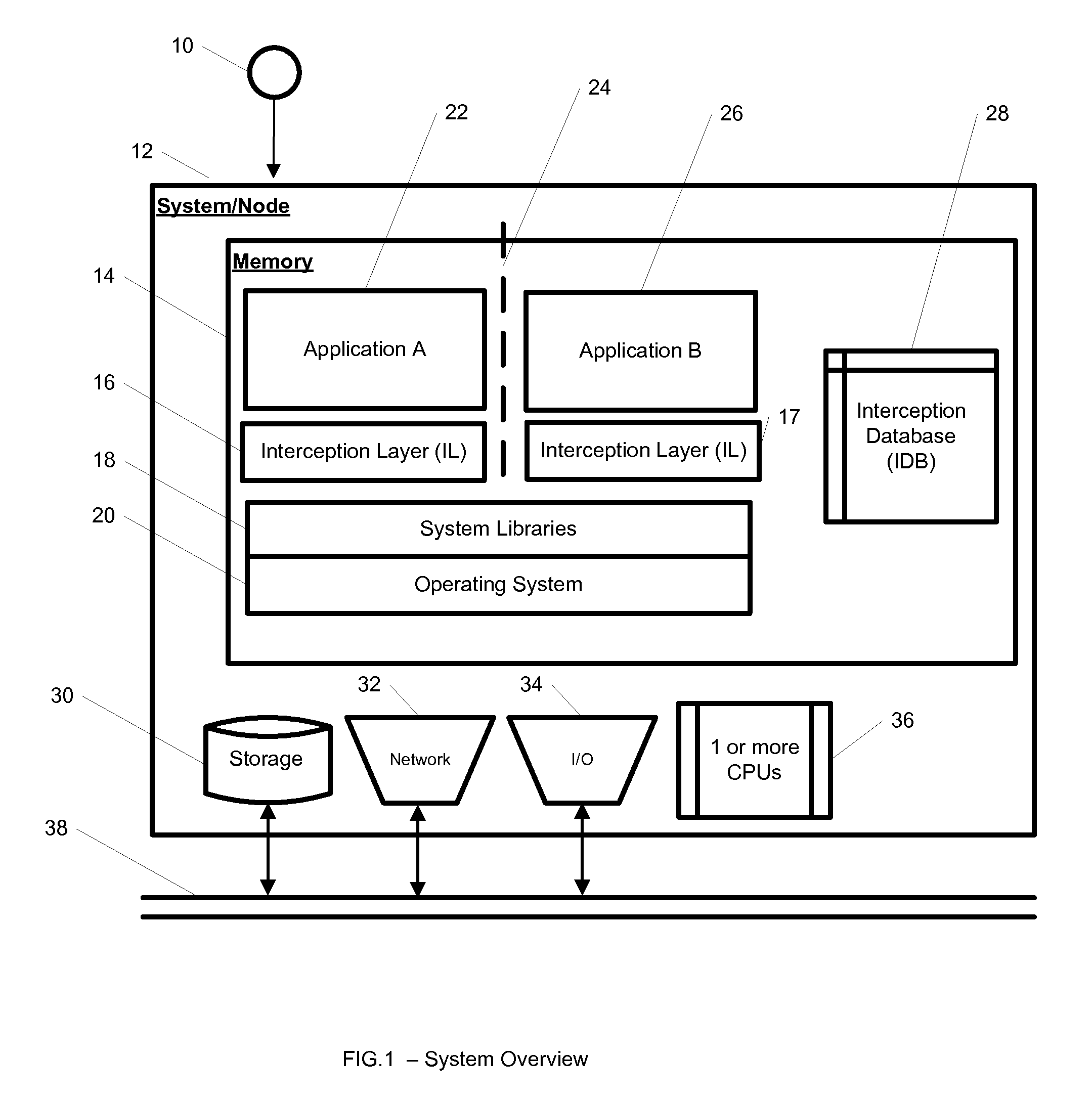
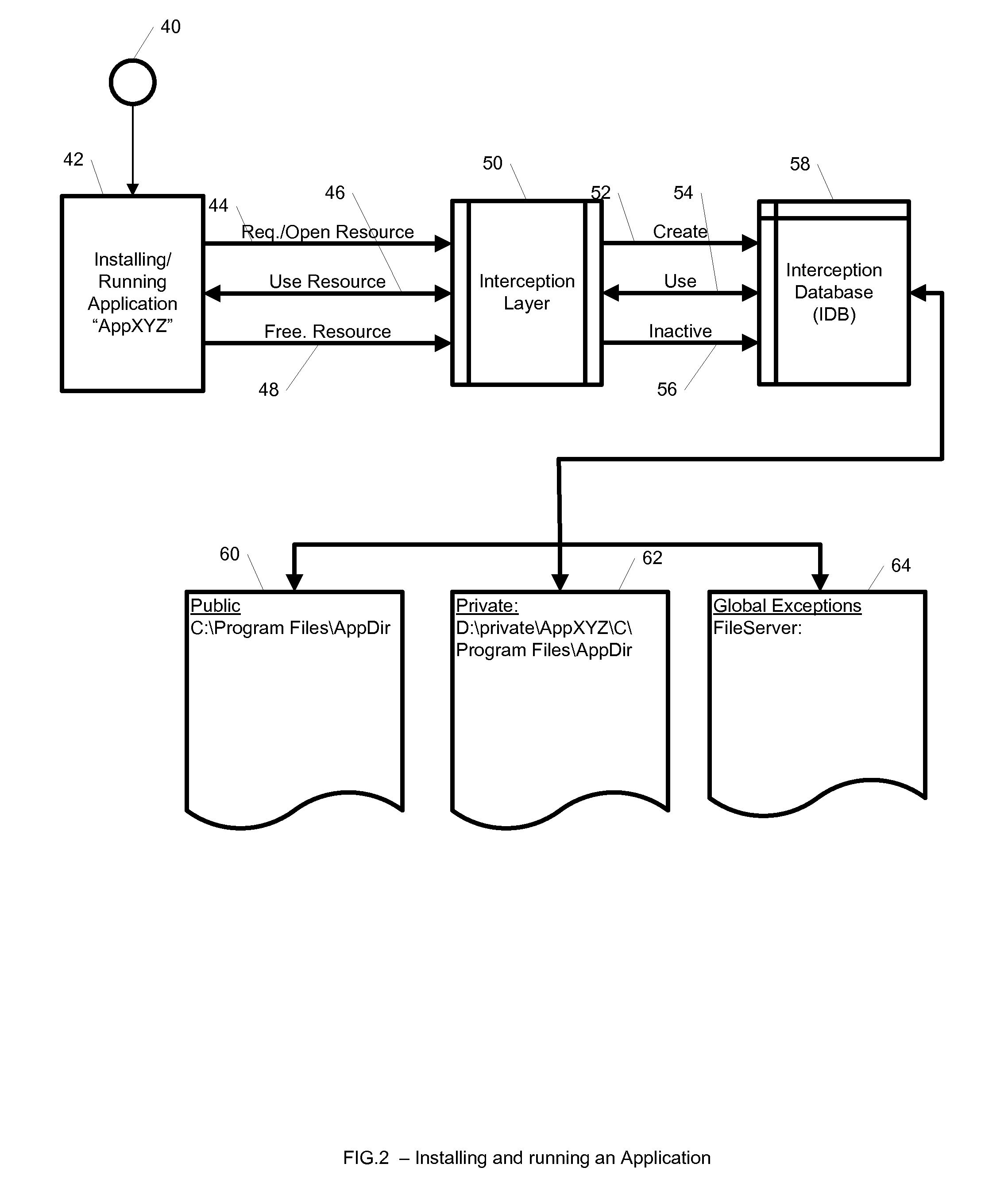
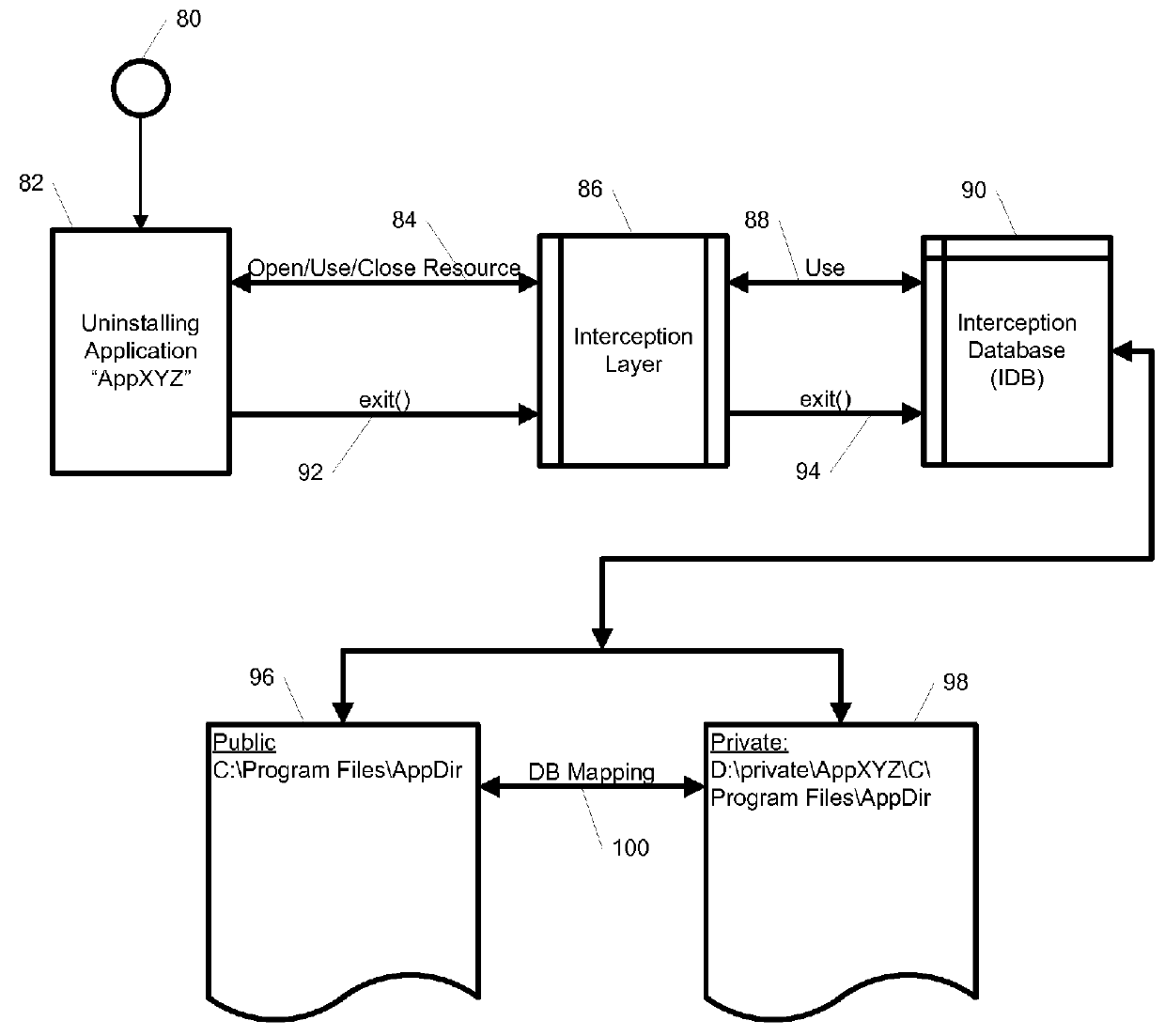
A system, method, and computer readable medium for providing application isolation to one or more applications. The system may include an isolated environment including application files and executables, and an interception layer intercepting access to system resources and interfaces. The system may further include an interception database maintaining mapping between the system resources inside the isolated environment and outside, and a host operating system, wherein the isolated environments are saved on at least one of a local and remote storage.
Owner:PHILIPS NORTH AMERICA LLC
System and method for interrupt handling
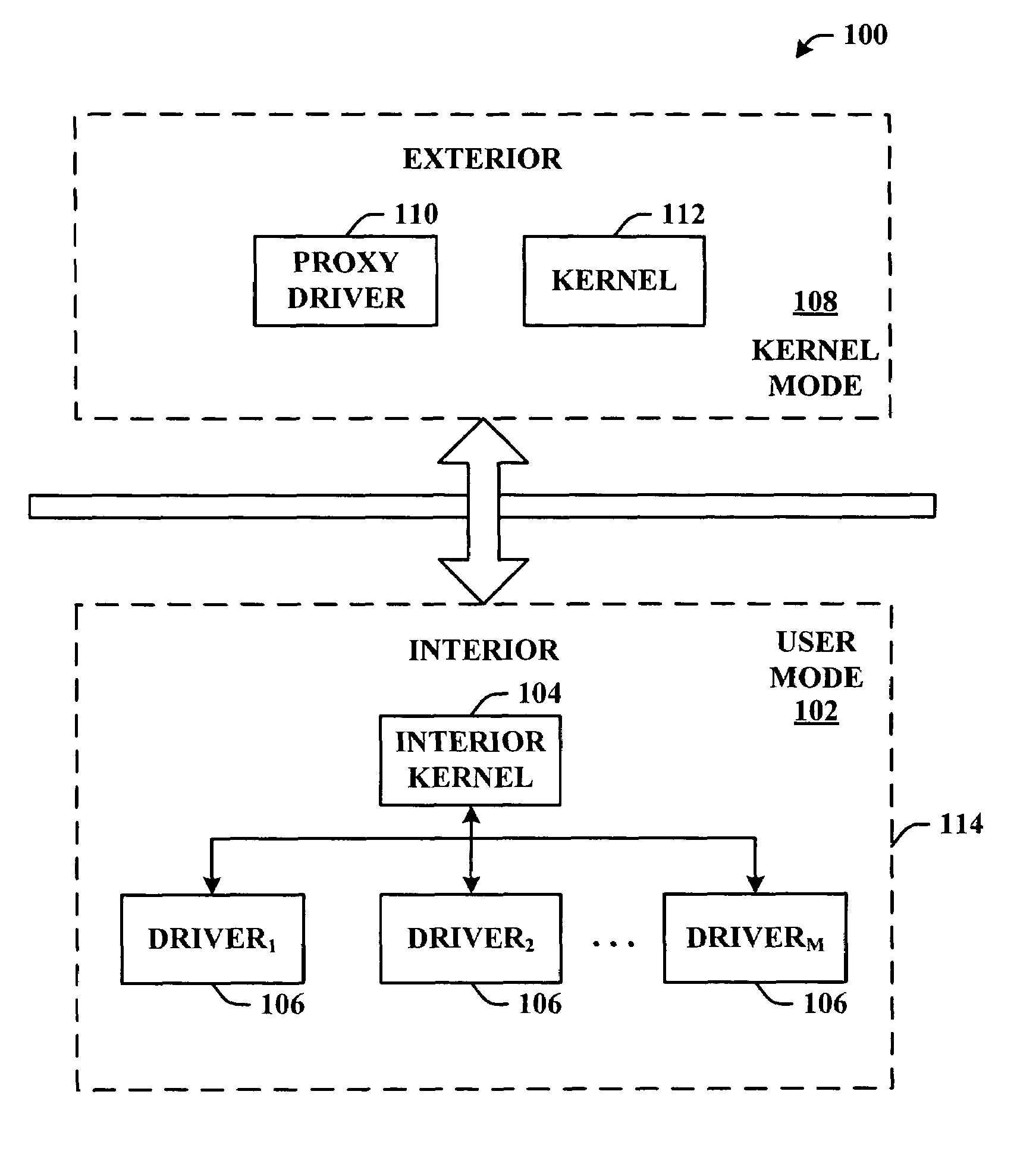
A system, methodology and / or computer architecture that facilitates processing device interrupts (including level-triggered interrupts) in a user-mode process is provided. The kernel interrupt handler can cause a dedicated thread in the process to wake and invoke the driver interrupt service routine. This thread can then return control to the kernel interrupt handler. In addition to processing interrupts in an isolated mode, the context switching technique could be used in any isolated environment to process interrupts via dedicated execution context methods.
Owner:MICROSOFT TECH LICENSING LLC
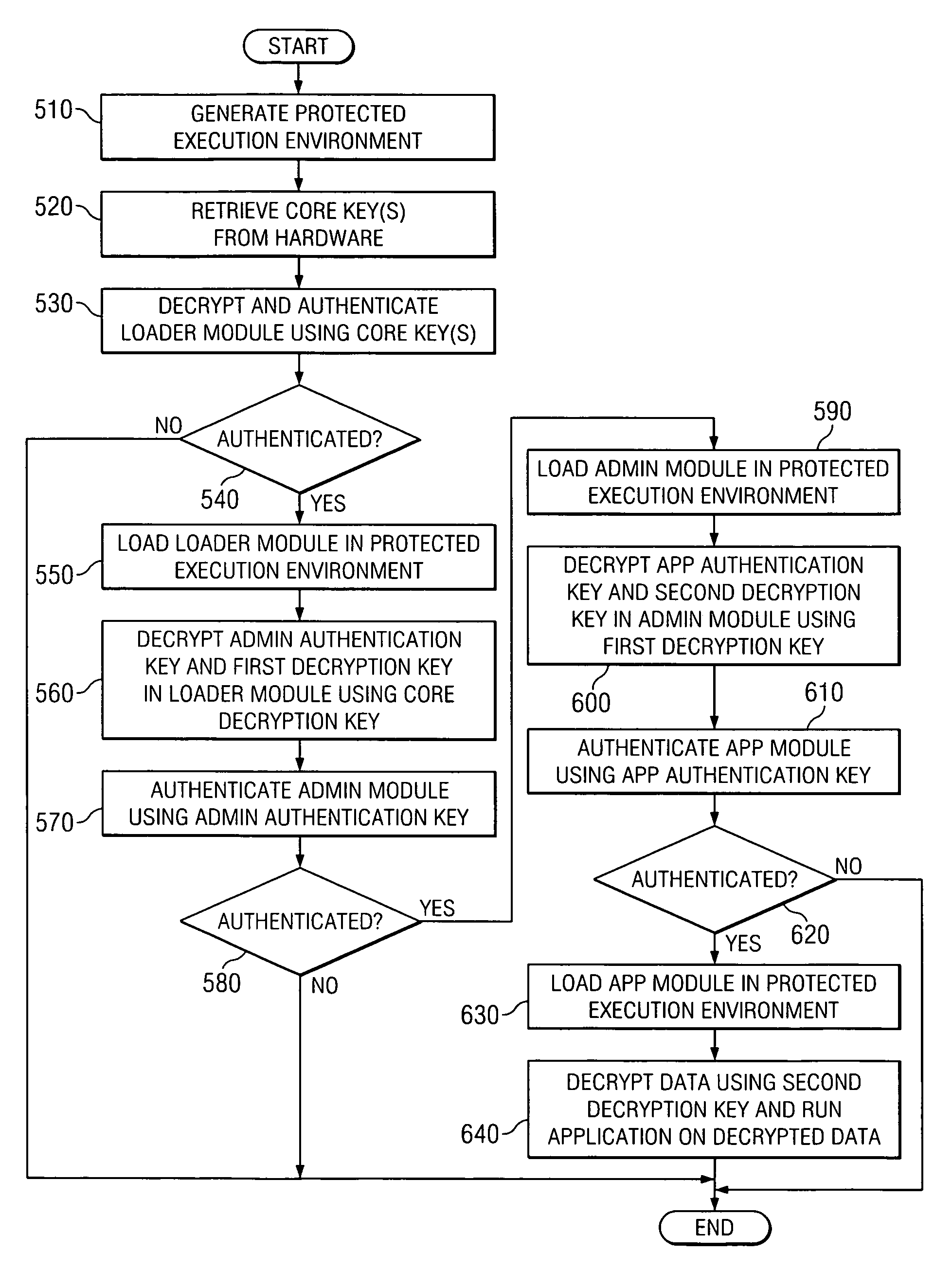
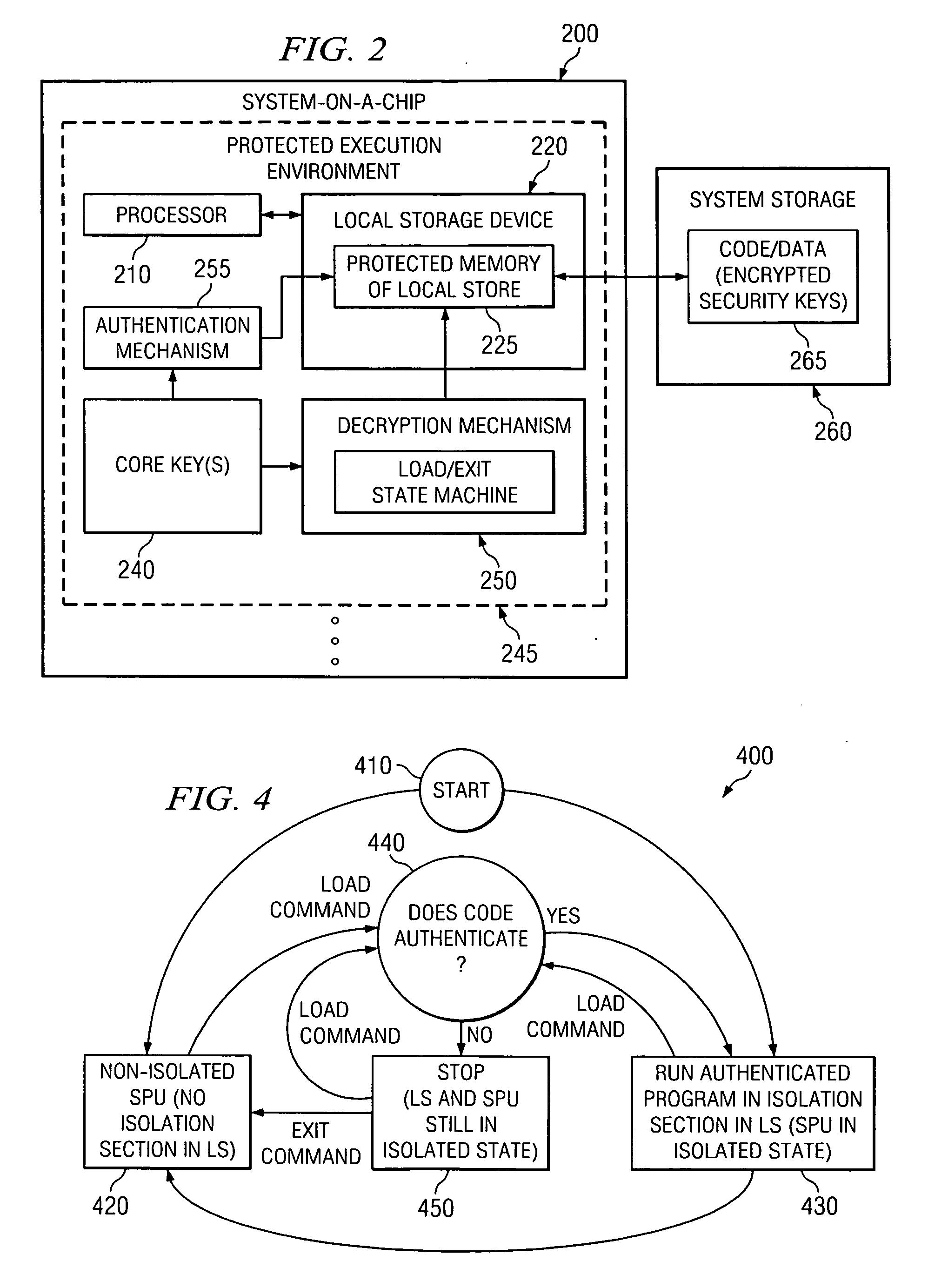
Apparatus and method for providing sealed storage in a data processing device
InactiveUS20070179904A1Protection attackGenerate accuratelyDigital data processing detailsUser identity/authority verificationComputer hardwareChain of trust
An apparatus and method for providing a sealed storage in a data processing device are provided. Processors of the data processing device may operate in a hardware isolation mode which allows a process to execute in an isolated environment on a processor and associated memory thereby being protected from access by other elements of the data processing device. In addition, a hardware controlled authentication and decryption mechanism is provided that is based on a hardware core key. These two features are tied together such that authentication occurs every time the isolation mode is entered. Based on the core key, which is only accessible from the hardware when in isolation mode, a chain of trust is generated by providing authentication keys for authenticating a next piece of software in the chain, in each piece of software that must be loaded, starting with the core key.
Owner:IBM CORP
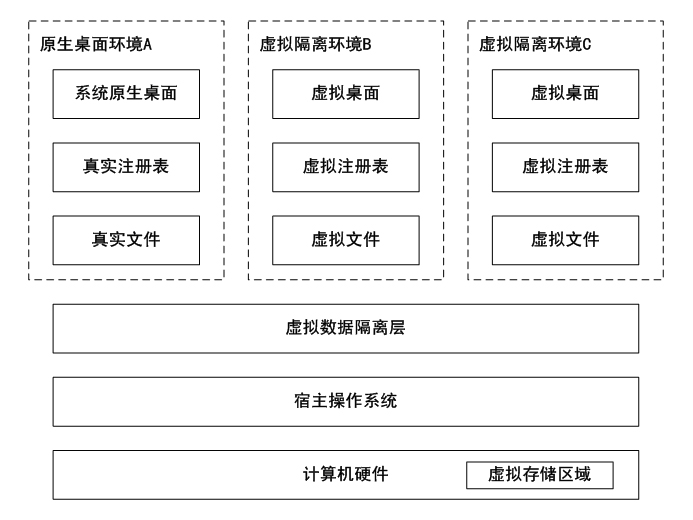
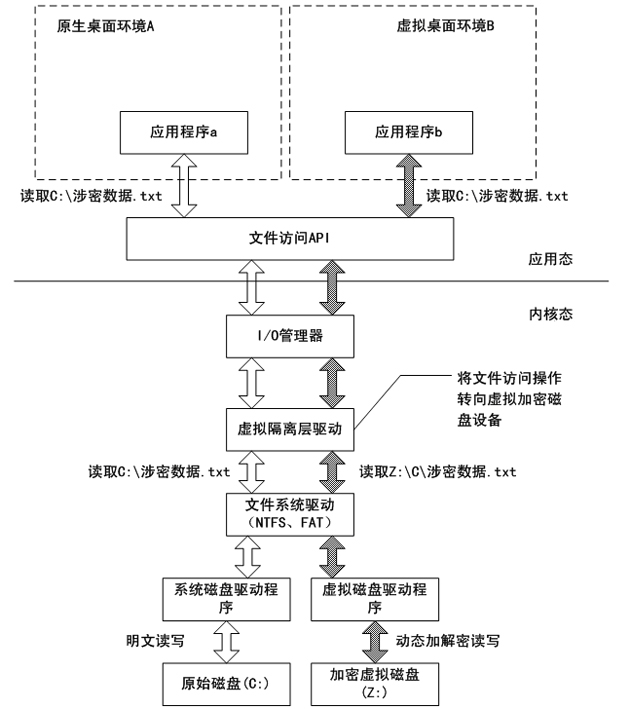
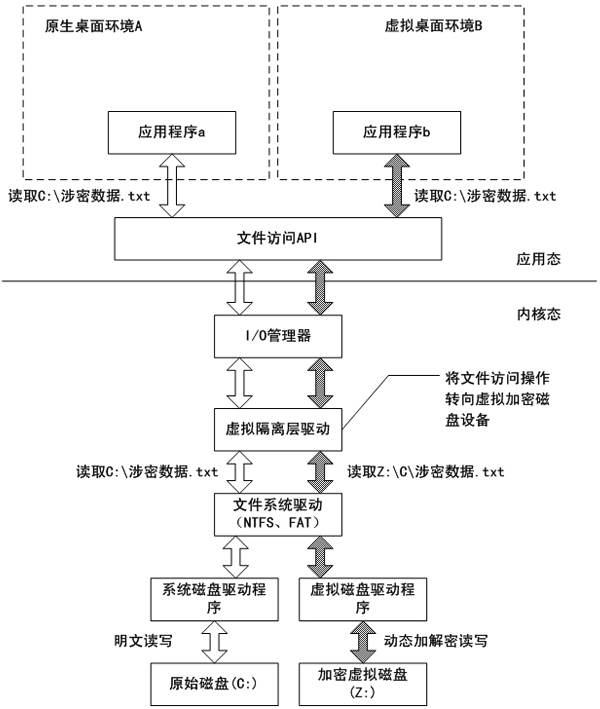
Data anti-leakage method based on operating system virtualization principle
InactiveCN102004886AReduce difficultySignificant progressDigital data protectionVirtualizationOperational system
The invention relates to a data anti-leakage method based on an operating system virtualization principle, belonging to the technical field of computer application. The data anti-leakage method is characterized by comprising the following steps of: increasing a virtual isolating layer and a virtual storage area in a host operating system of a computer on the basis of the operating system virtualization principle; structuring one or more virtual isolated environments on the basis of the virtual isolating layer and the virtual storage area by combining with a virtual desktop technology; and completely isolating and protecting data resources which are stored in each virtual isolated environment and include files and registration forms to ensure that data generated in the virtual isolated environments is not leaked out of the virtual isolated environments so as to prevent active or passive data leakage behaviors. The invention greatly enhances the operating efficiency of a data anti-leakage system by utilizing the innate advantages of the operating system virtualization principle, reduces the difficulty of applying a data anti-leakage scheme and enhances the easy use and the work efficiency of the data anti-leakage system.
Owner:上海安纵信息科技有限公司
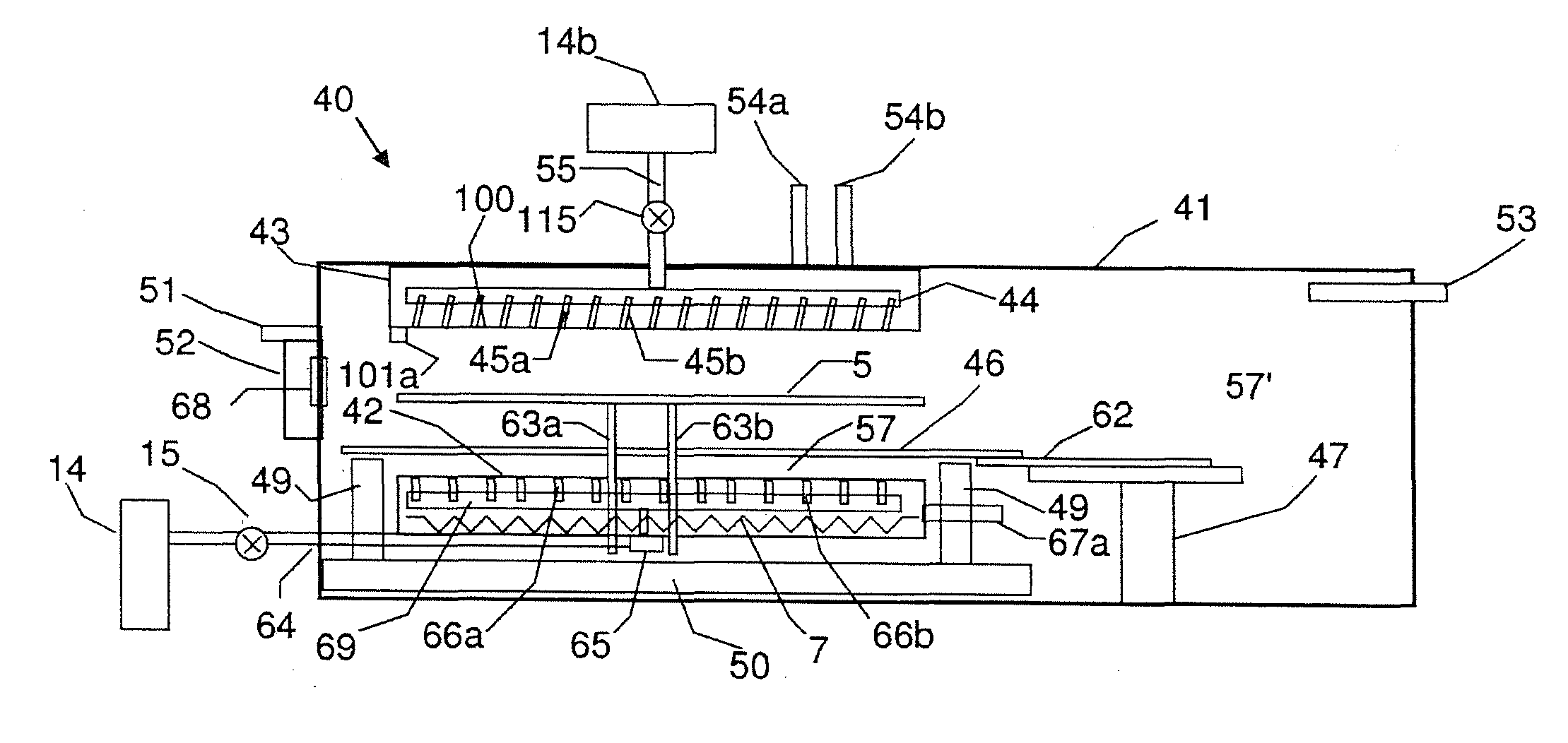
Apparatus for thermal processing with micro-environment
InactiveUS20110114623A1Reduce gas flowRestricting flow of gasSemiconductor/solid-state device manufacturingHandling discharged materialEngineeringIsolated environment
A substrate thermal processing system. The system has at least one substrate holding module having a housing configured for holding an isolated environment therein. A substrate heater is located in the housing and has a substrate heating surface. A substrate cooler is located in the housing and having a substrate cooling surface. A gas feed opening into the housing and feeding inert or reducing gas into the housing when the substrate is heated by the heating surface. A gas restrictor is within the housing restricting the fed gas between the substrate heating surface and a surrounding atmospheric region substantially surrounding the substrate heating surface in the housing and forming an aperture through which the fed gas communicates with the atmospheric region.
Owner:TEL NEXX INC
Process method for preparing cold brewing tea by ice crystallization cell wall breaking
InactiveCN101669553AInhibit peroxidationImprove solubilityPre-extraction tea treatmentData controlDrinking habits
The invention discloses a method for preparing cold brewing tea by ice crystallization treatment. The method comprises the following steps: putting fresh tea leaves in a low-temperature environment below 40 DEG C below zero for ice crystallization; putting the tea leaves subjected to the ice crystallization treatment into a vacuum container; slubbing the tea leaves in the vacuum container; heatingthe vacuum container at a heating temperature of between 70 and 100 DEG C; and stirring the tea leaves in the heated vacuum container until the tea leaves are dried. The ice crystallization process,which is adopted for replacing the conventional withering process, can change the conventional process depending on human experience control into data control and significantly improve the product consistency; the ice crystallization cooperated with the enzymatic oxidation of vacuum negative pressure isolated environment oxygen can avoid the problem of peroxided sensitive substances in the tea leaves; the adoption of an ice crystallization wall breaking process combined with vacuum evaporation dewatering drying can avoid the problem of reoxidation in the drying process; the tea prepared by theice crystallization wall breaking process has better solubility in cold water; the cold water brewing tea prepared by the ice crystallization wall breaking process can improve tea drinking habits ofhuman beings; and the adoption of the cold water brewing tea can save a large amount of energy for boiling water. The method can also be used for preparing cold water brewing beverages by using otherplants to conventionally be soaked in water for drinking, such as ginseng leaves, ginkgo leaves, chrysanthemums, green plums, olives and the like, thereby providing a new idea for enriching markets.
Owner:苏少宁
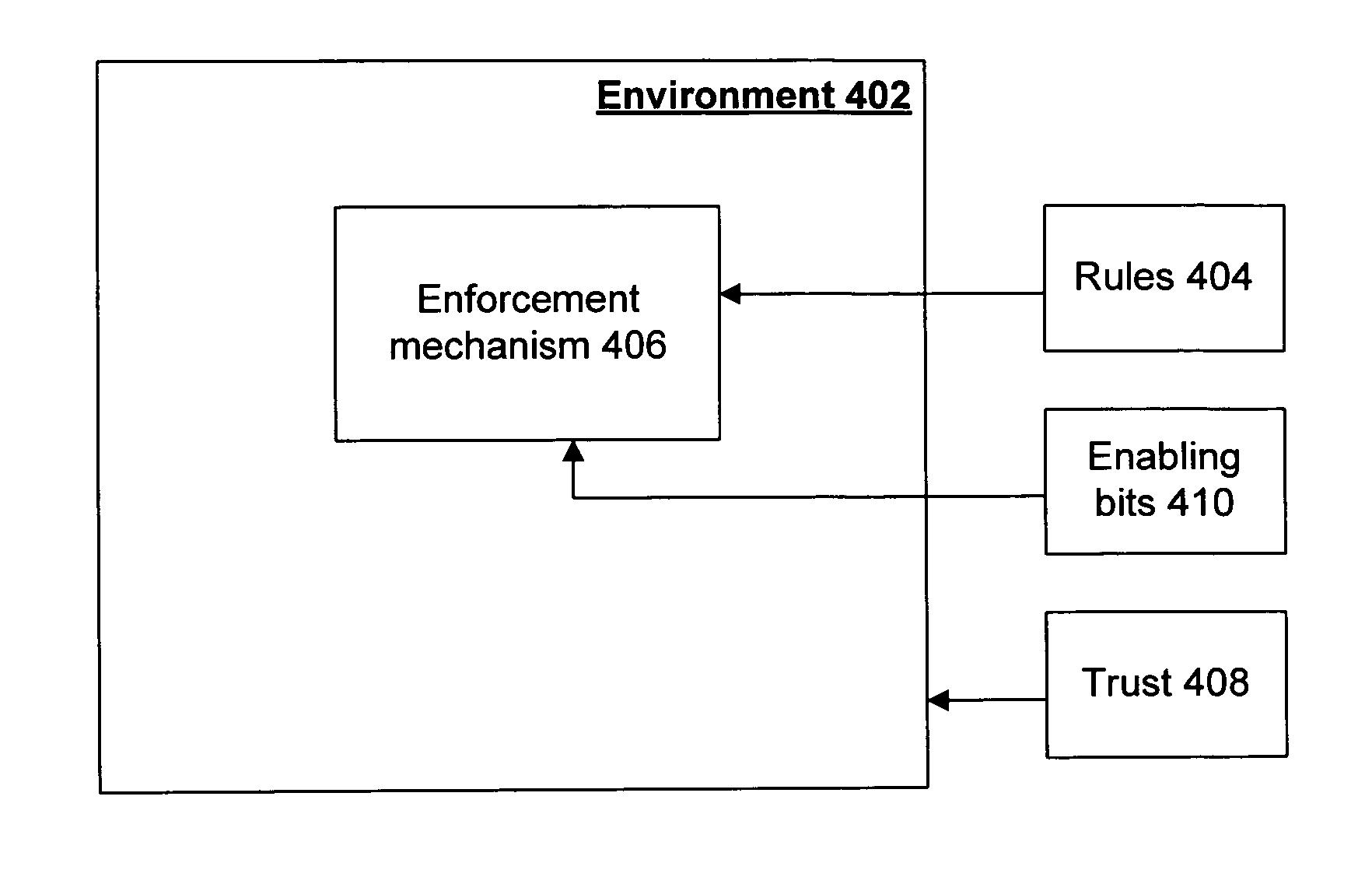
Enabling bits sealed to an enforceably-isolated environment
ActiveUS20060288238A1Reasonable protectionEffective trustUnauthorized memory use protectionHardware monitoringComputer hardwareComputer science
Prevention of unpermitted use of enabling bits is achieved by sealing the enabling bits to an environment in such a way that the bits can only be unsealed by or from the environment, and by using an isolation mechanism to isolate the environment from other environments on the machine on which the environment operates. The environment is trusted not to use the enabling bits except in accordance with a set of rules governing the bits. The enabling bits may be a decryption key for DRM-protected content, and the rules may be a license governing the use of that content. Trust that the enabling bits will not be misused is established by trusting the environment not to use the enabling bits contrary to the rules, trusting the isolation mechanism to isolate the environment, and trusting the unsealing mechanism only to unseal the bits for the environment.
Owner:MICROSOFT TECH LICENSING LLC
System and Method for Application Isolation
InactiveUS20100262970A1Resource allocationReliability/availability analysisOperational systemApplication software
A system, method, and computer readable medium for providing application isolation to one or more applications and their associated resources. The system may include one or more isolated environments including application files and executables, and one or more interception layers intercepting access to system resources and interfaces. Further, the system may include an interception database maintaining mapping between the system resources inside the one or more isolated environments and outside, and a host operating system. The one or more applications may be isolated from other applications and the host operating system while running within the one or more isolated environments.
Owner:IBM CORP
Customized protocol communication system and customized protocol communication method of mixed data in isolated environment between internal network and external network
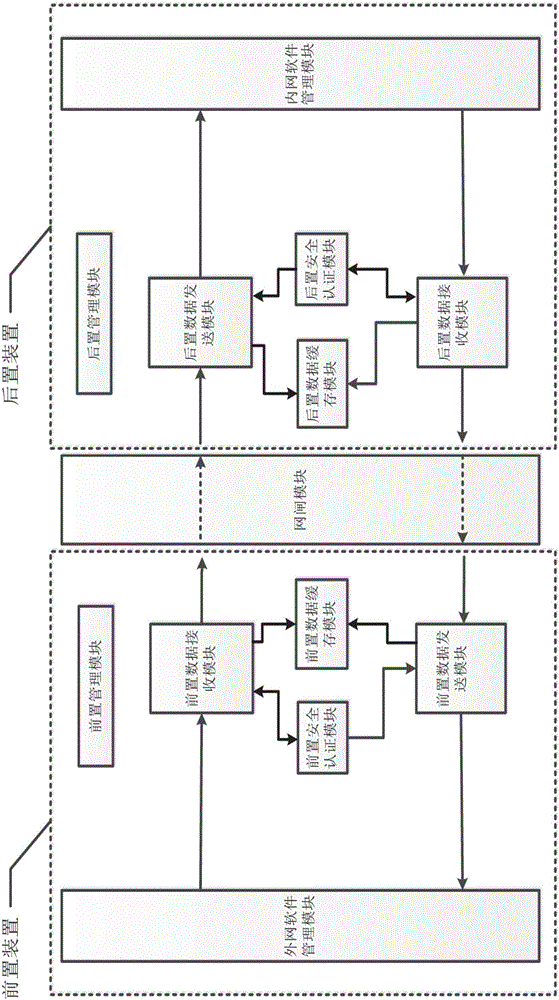
PendingCN106230806AImprove transfer efficiencyEnsure safetyTransmissionCommunications systemWeb service
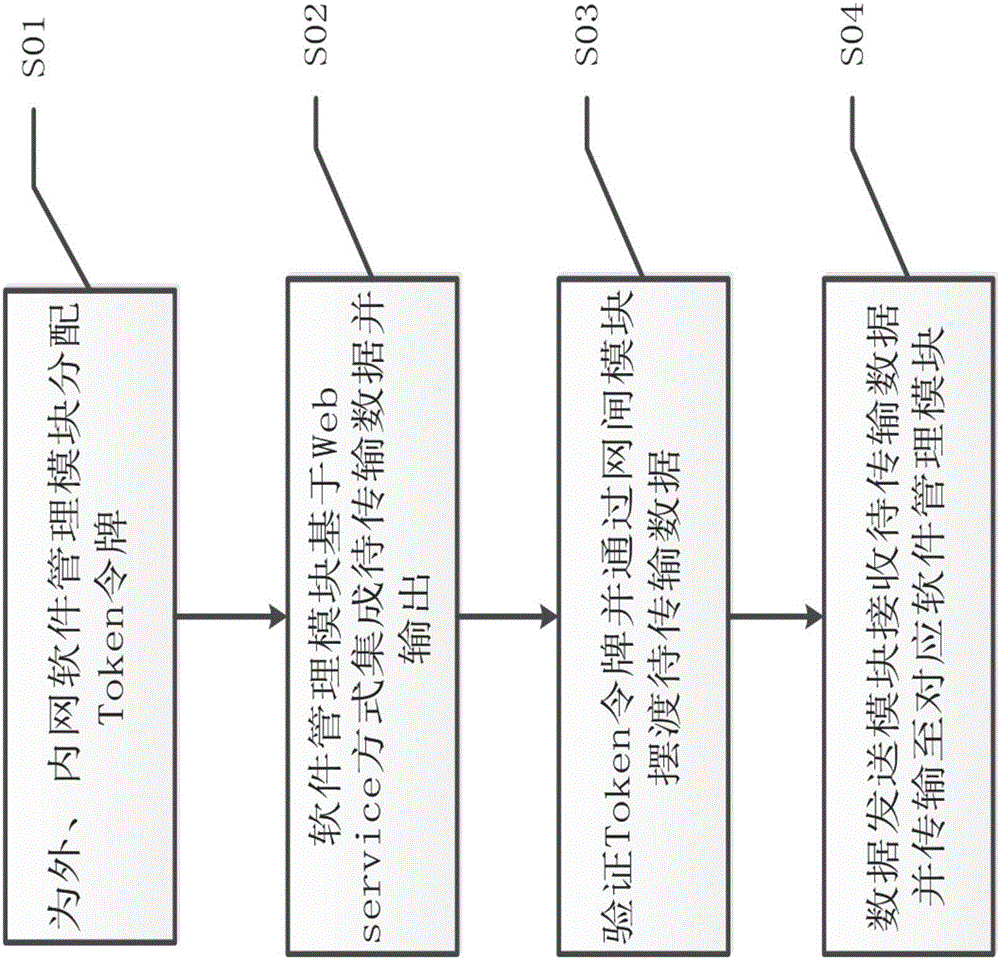
The invention discloses a customized protocol communication system and a customized protocol communication method of mixed data in an isolated environment between an internal network and an external network. The customized protocol communication system comprises the components of a frontend device which comprises an external network software management module, a frontend management module, a frontend data receiving module, a frontend safety authentication module, a frontend data buffer module and a frontend data transmission module; a backend device which is configured in a manner of corresponding with the frontend device; and a network gate module. The customized protocol communication method comprises the steps of assigning a token for the software management module; integrating to-be-transmitted data based on a web service manner and outputting the integrated data to a frontend data receiving module and a backend data receiving module; verifying the token by the data receiving modules and transferring the to-be-transmitted data to the data transmission module through the network gate module; and receiving the to-be-transmitted data by the data transmission module and transmitting the to-be-transmitted data to the software management module. Through an information mechanism issuing / customizing mode, the customized protocol communication system and the customized protocol communication method have advantages of controlling data exchange between software in real time, improving mastering capability of a user to data exchange, and reducing operation difficulty in controlling data exchange.
Owner:CHINA SOUTHERN POWER GRID DIGITAL GRID RES INST CO LTD
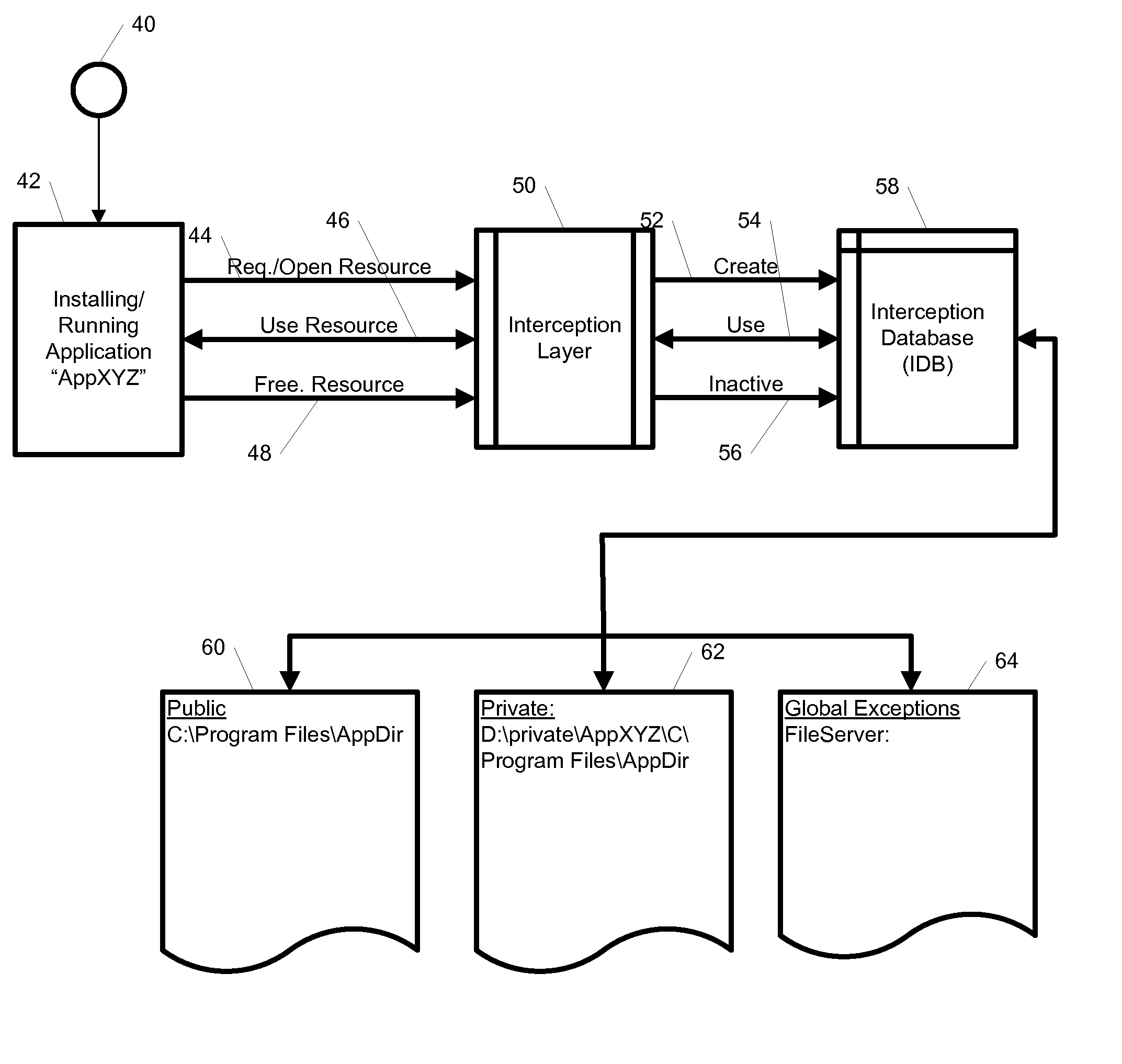
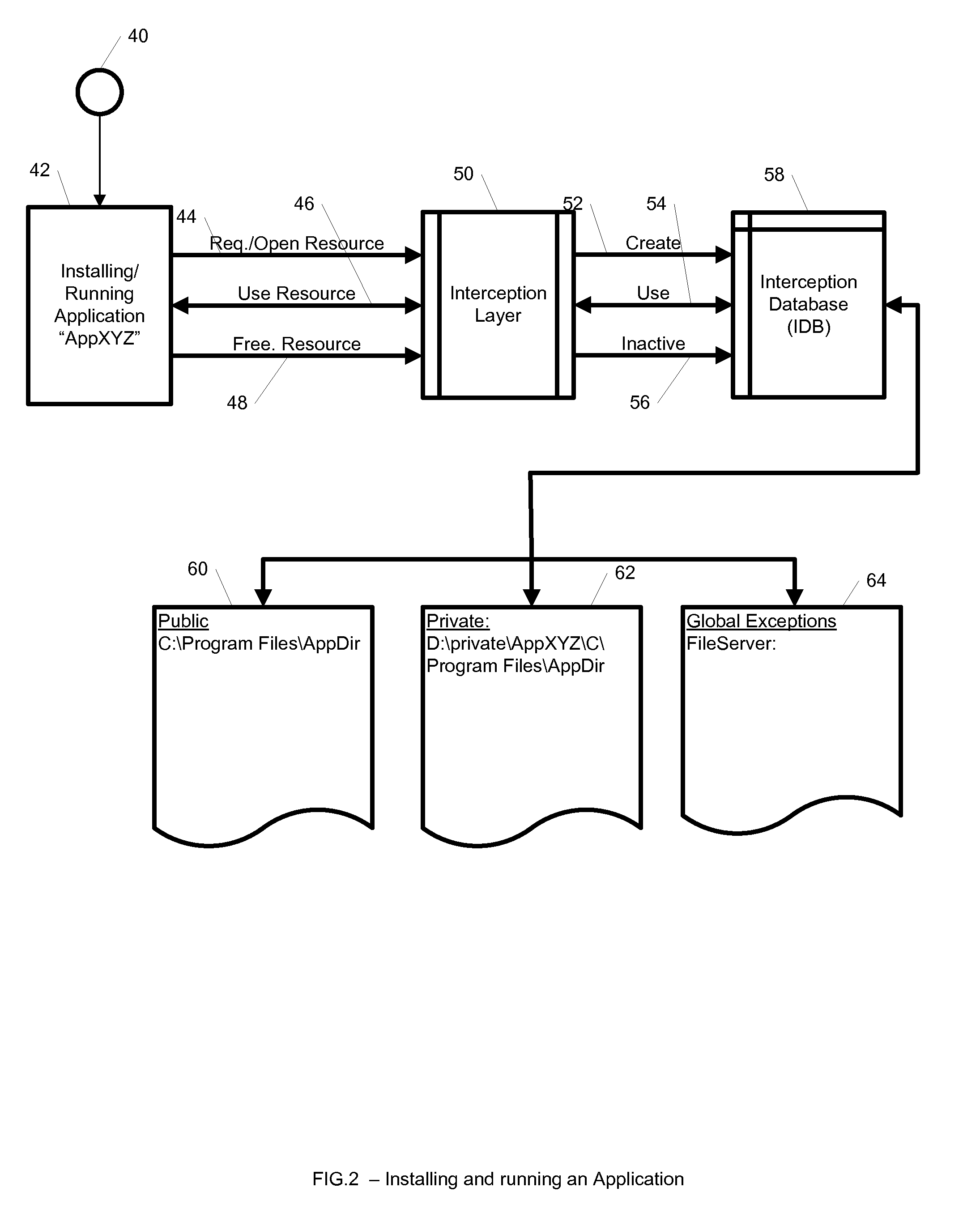
System and Method for Application Isolation
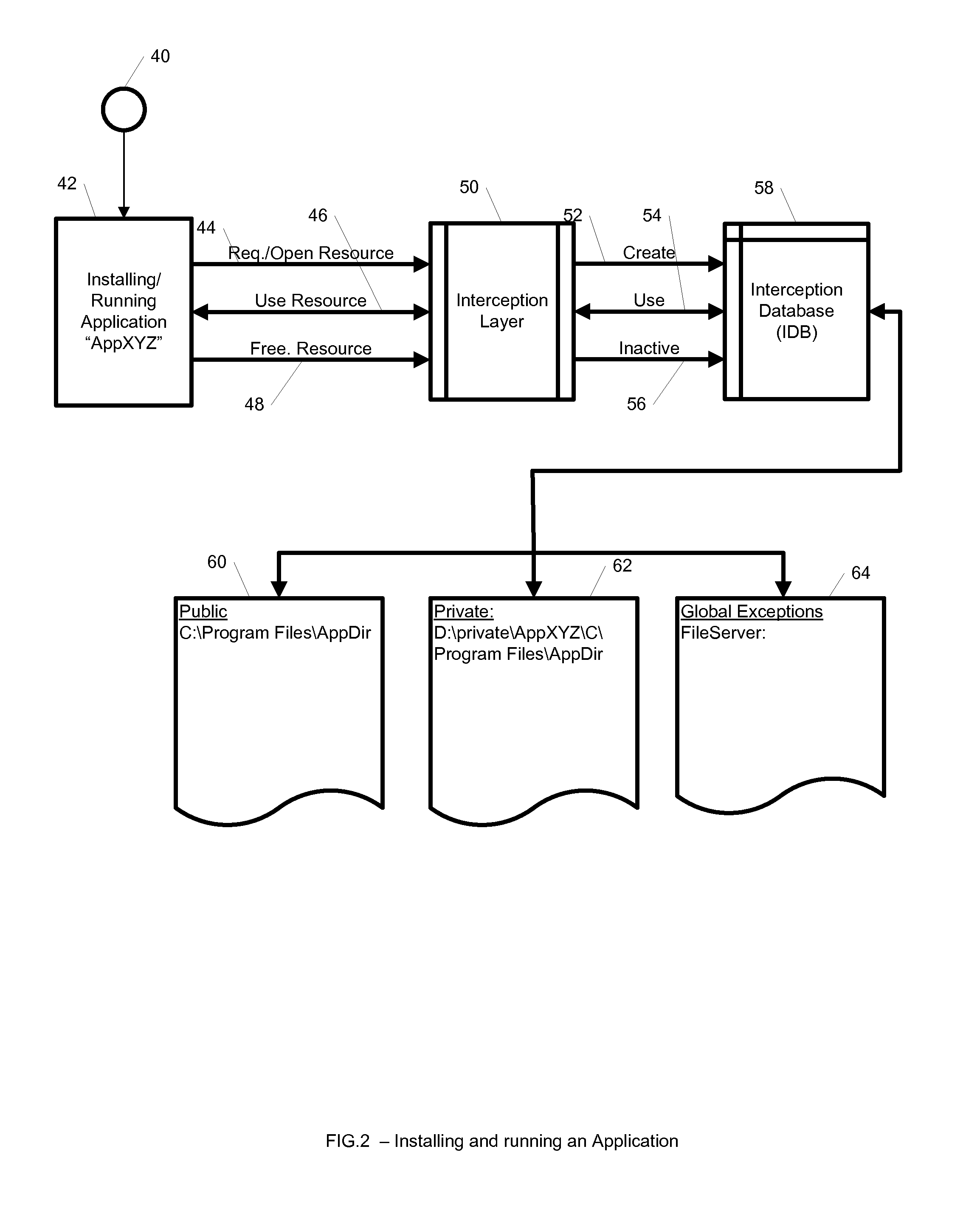
ActiveUS20100262694A1Error detection/correctionDigital computer detailsApplication softwareMultiple applications
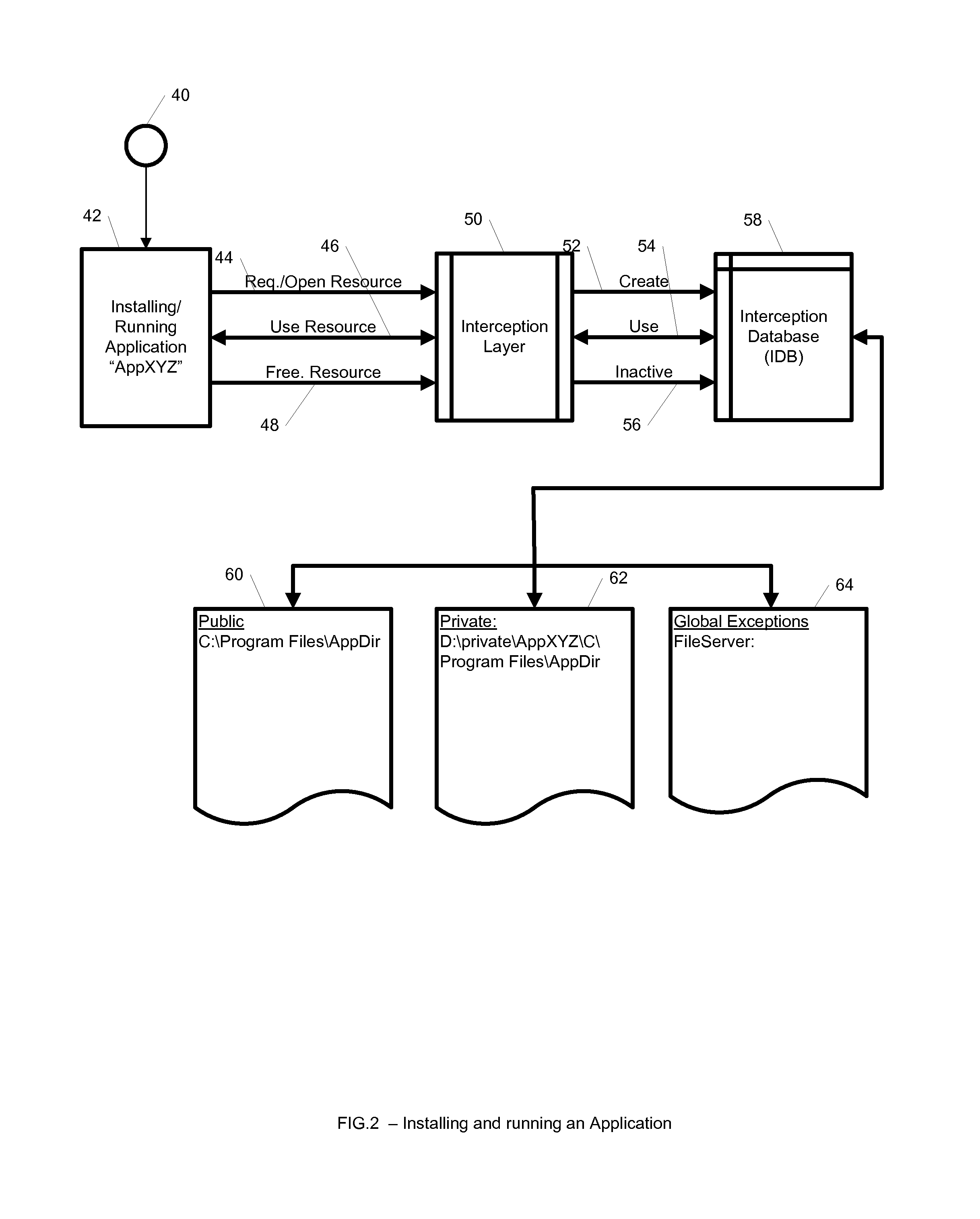
A system, method, and computer readable medium for maintaining mappings between resources inside an isolated environment and outside the isolated environment for one or more applications. The system may include a plurality of lists of resources requested by the one or more applications during installation and while executing, and a corresponding lists of resources inside the isolated environment. The system may also include a list of resource exceptions, wherein the mappings between resources as requested by the applications and their corresponding values in the isolated environment are maintained subject to the list of exceptions.
Owner:IBM CORP
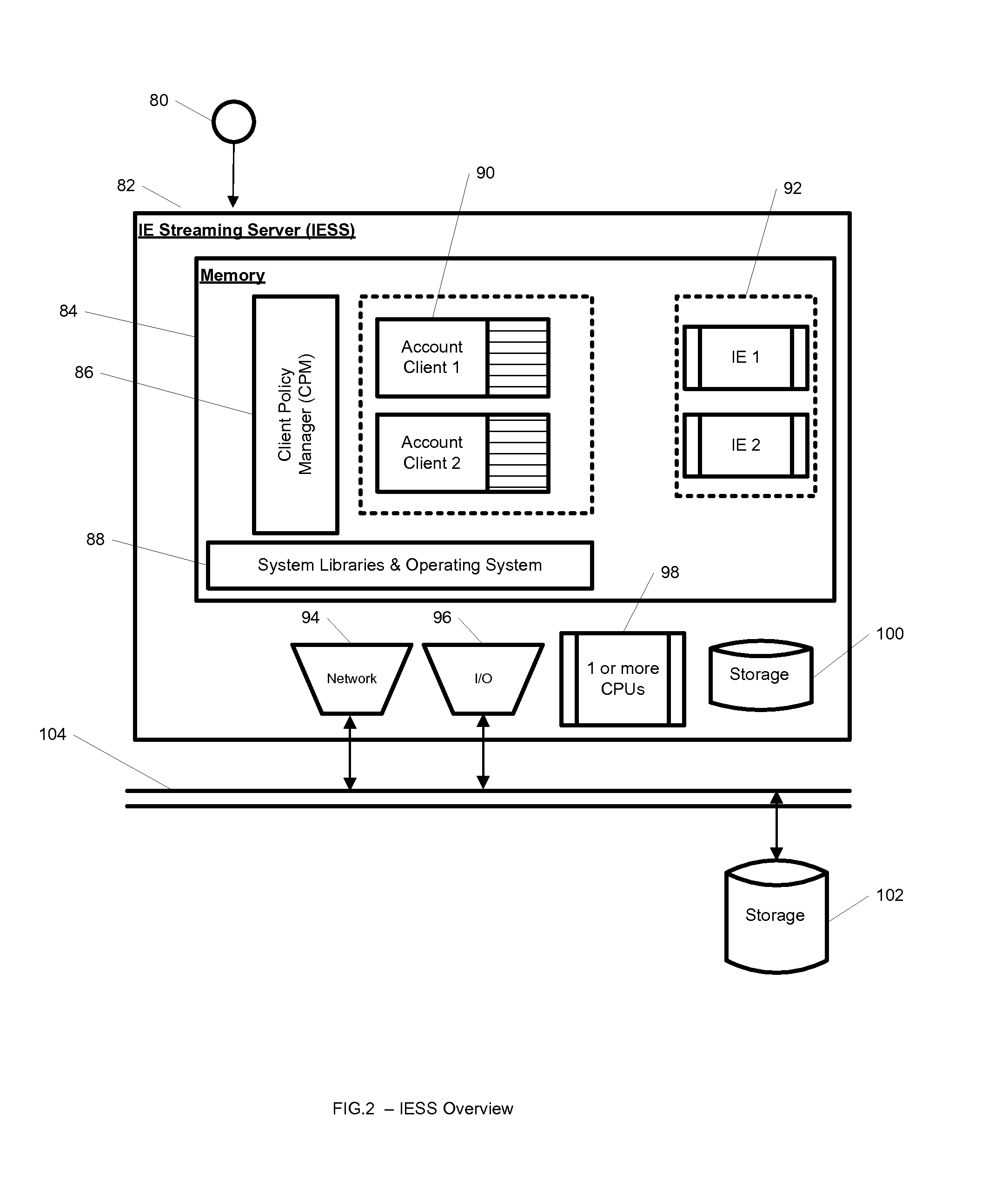
System and method for usage billing of hosted applications
A system, method, and computer readable medium for usage billing of one or more hosted applications serving one or more clients. The hosted applications are contained within one or more isolated environments or run without isolated environments. The system may include usage billing based on one or more of resources open, amount of data flowing through resources, number of open files, number of transactions, number of concurrent users, number of processes, CPU utilization and memory usage, The system may further include a management interface where administrators may add, remove and configure isolated environments, configure client policies and credentials, and force upgrades. If using isolated environments, the isolated environments may be isolated from other applications and the host operating system on the clients and applications within the isolated environments may run without performing an application-installation on the client.
Owner:OPEN INVENTION NEWTORK LLC
System and method for application isolation with live migration
ActiveUS9251004B1Program synchronisationRedundant operation error correctionHandling systemApplication software
Owner:INT BUSINESS MASCH CORP
Enabling bits sealed to an enforceably-isolated environment
ActiveUS7529946B2Reasonable protectionEffective trustUser identity/authority verificationUnauthorized memory use protectionComputer hardwareIsolated environment
Prevention of unpermitted use of enabling bits is achieved by sealing the enabling bits to an environment in such a way that the bits can only be unsealed by or from the environment, and by using an isolation mechanism to isolate the environment from other environments on the machine on which the environment operates. The environment is trusted not to use the enabling bits except in accordance with a set of rules governing the bits. The enabling bits may be a decryption key for DRM-protected content, and the rules may be a license governing the use of that content. Trust that the enabling bits will not be misused is established by trusting the environment not to use the enabling bits contrary to the rules, trusting the isolation mechanism to isolate the environment, and trusting the unsealing mechanism only to unseal the bits for the environment.
Owner:MICROSOFT TECH LICENSING LLC
Online software execution platform
ActiveUS8930940B2Accurate measurementSimple processText processingProgram code adaptionApplication softwareWeb page
A system and method for a new type of software repository and remote execution solution where any native application can be run from within a web page is disclosed. Users now have a much easier way to launch, run or execute any software directly from within a server or server cloud without the need to manually download and install. The system further allows software to run inside an isolated environment to protect user's local environment.
Owner:YONGYONG XU
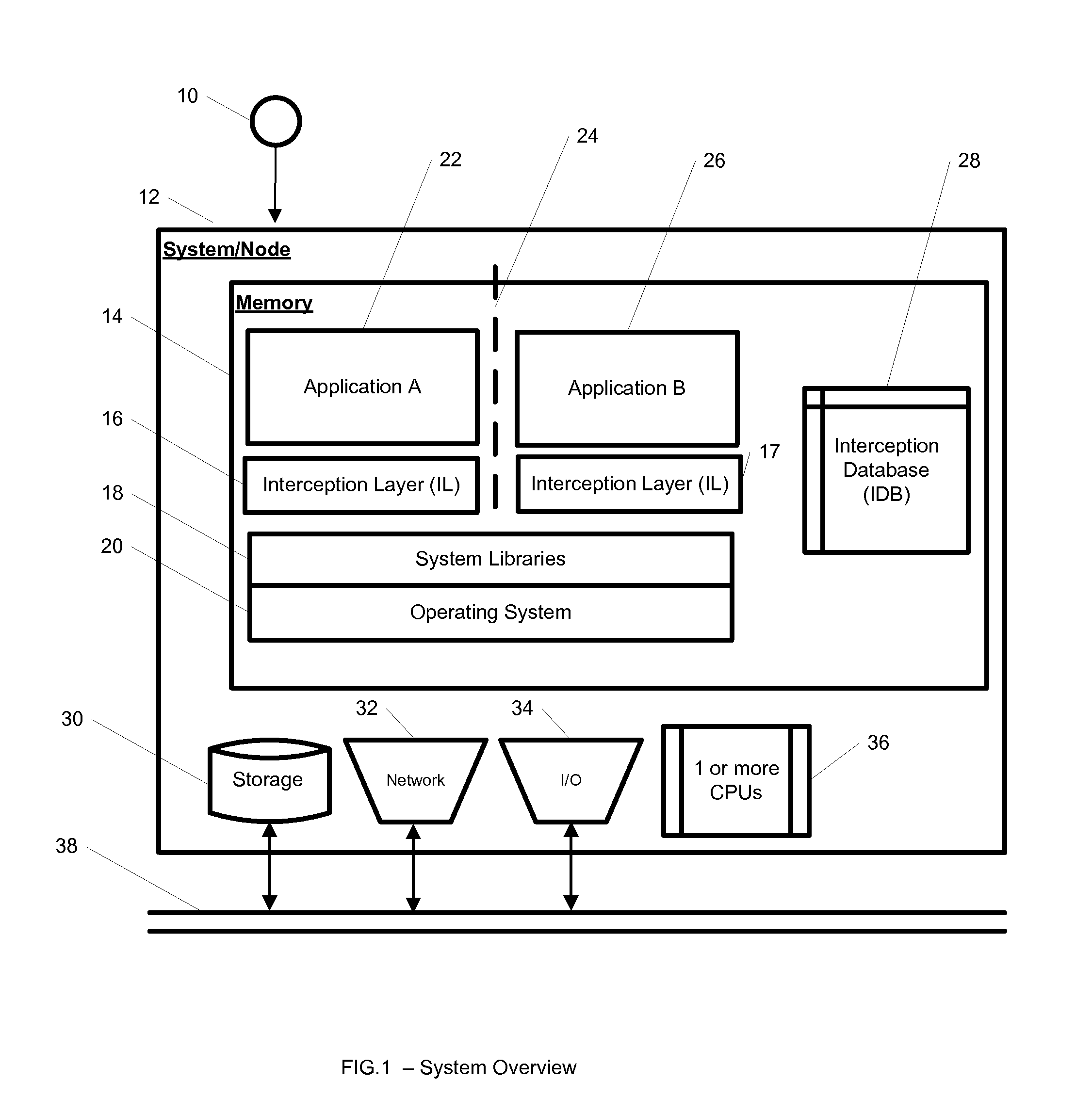
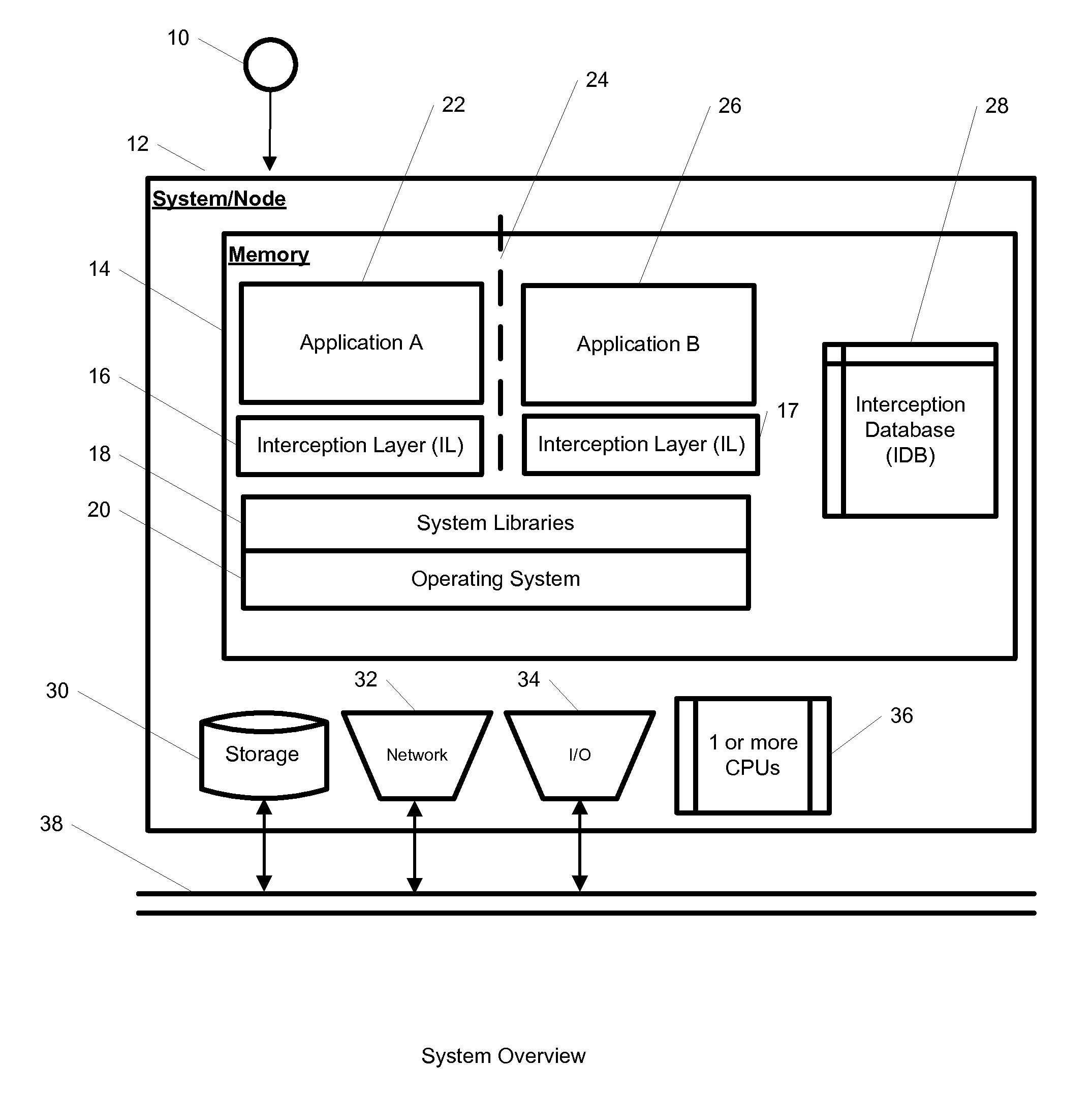
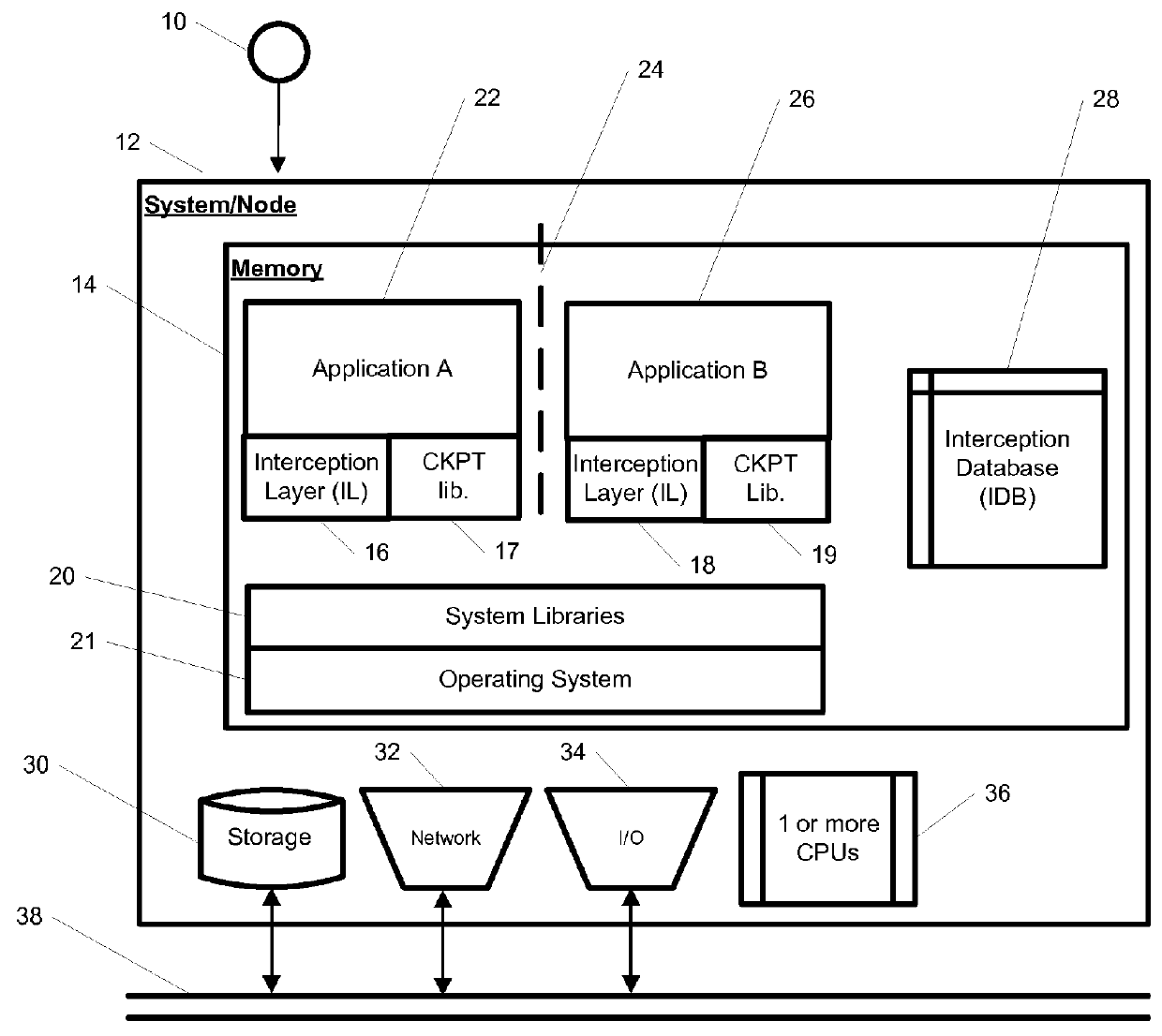
System and method for hierarchical interception with isolated environments
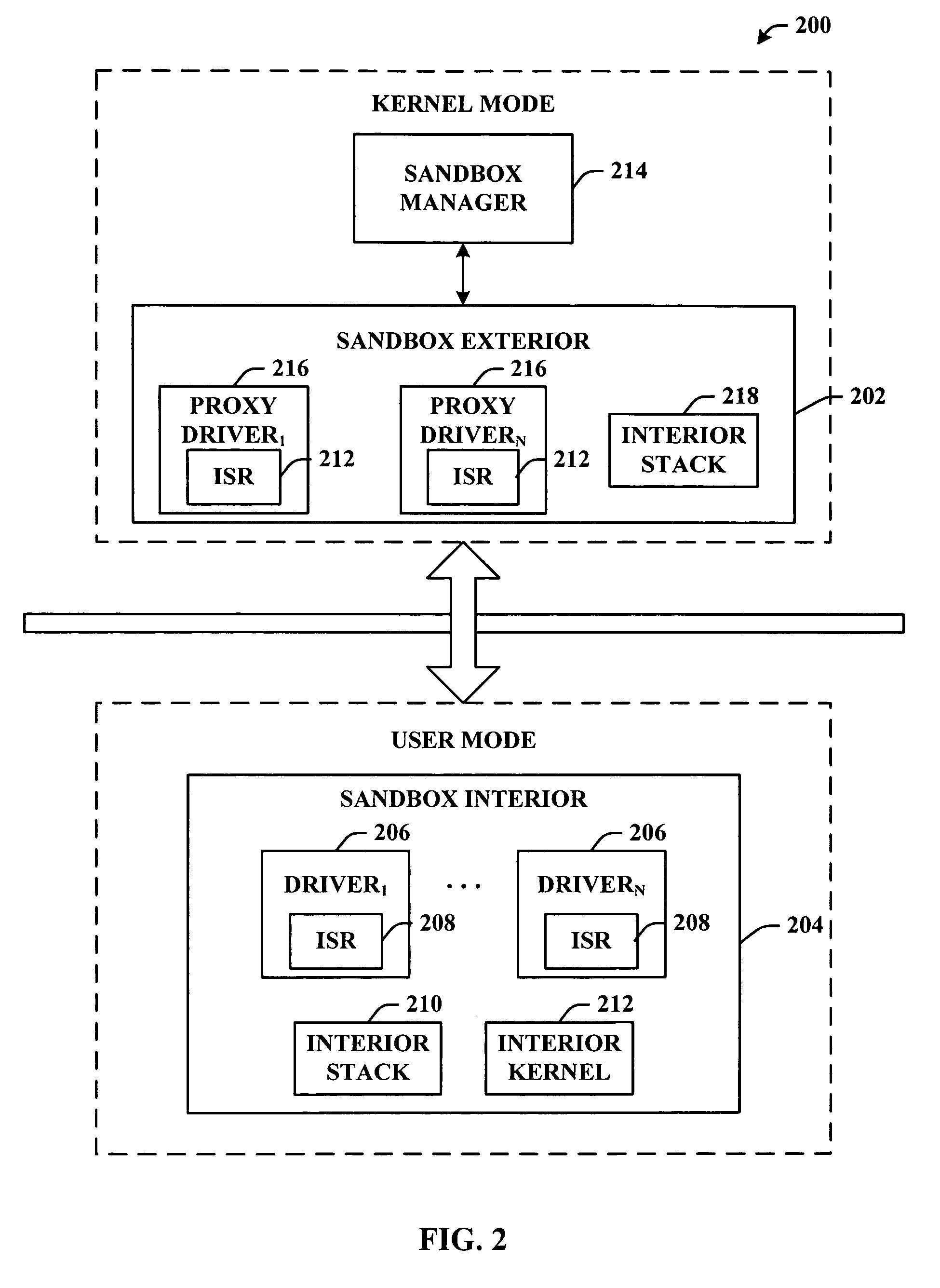
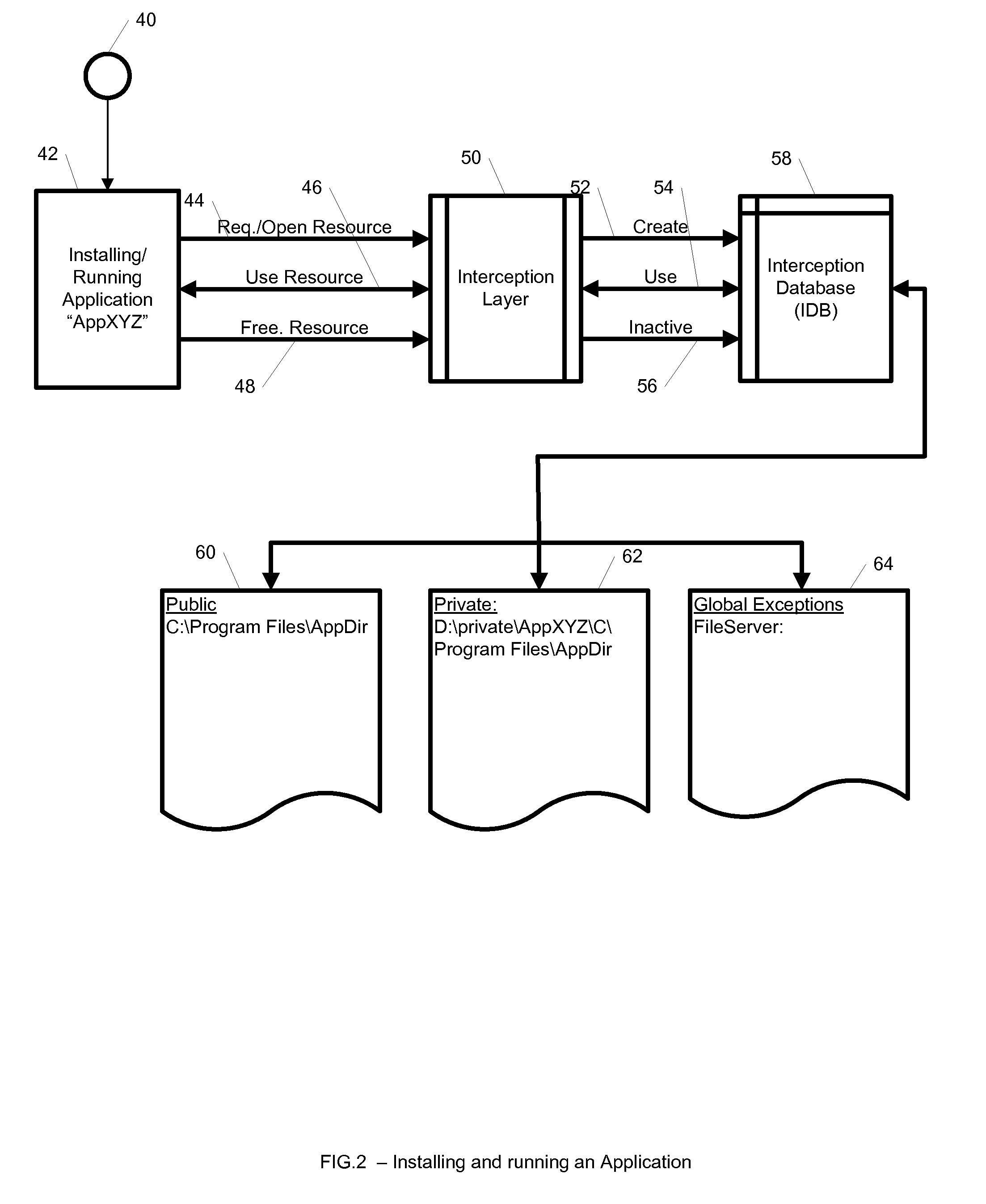
InactiveUS8464256B1Transmission systemsProgram synchronisationApplication softwareIsolated environment
A system, method, computer program, and / or computer readable medium for providing hierarchical interception for applications within isolated environments The computer readable medium includes computer-executable instructions for execution by a processing system. The computer-executable instructions may be for installing interceptors, configuring interceptors, preloading shared libraries, using trampoline functions, removal of interceptors, mapping between resources inside and outside the isolated environment, providing an interception database, loading the interception database, redirection of resources, and providing the hierarchy of interceptors.
Owner:OPEN INVENTION NEWTORK LLC
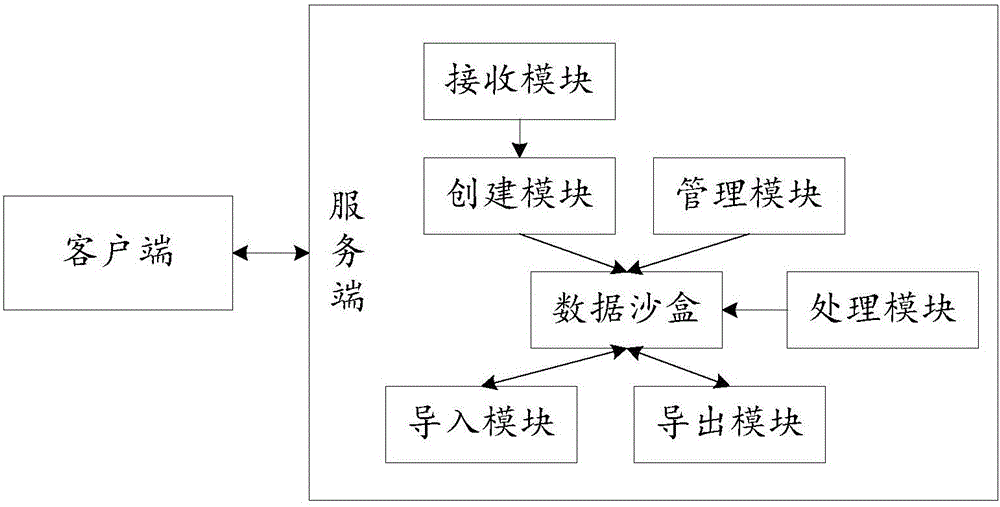
Method and system for implementing data sandbox based on mongoDB
InactiveCN105868389AImprove usabilityAchieve isolationResource allocationOther databases retrievalData warehouseExternal data
The invention relates to a method and system for implementing a data sandbox based on mongoDB. The method comprises the steps that a server receives a data sandbox creation application sent by a user side; the server creates an independent data sandbox on the mongoDB according to the application; the server stores the data sandbox and manages operation resource quotas; the server leads data warehouse data or external data into the data sandbox and performs data processing in a data sandbox environment; and after the data processing, the server leads processed data out of the data sandbox, destroys the data sandbox and recycles system resources. An elastic data operating environment is provided for users, and the request on local installation and transaction database management is omitted; through an isolated environment, data risks caused by misoperation by users are effectively avoided, the conditions that a data warehouse is retarded due to a centralized mode are reduced, environmental availability is improved, and efficient data access is achieved while the overhead of the data warehouse is reduced.
Owner:北京思特奇信息技术股份有限公司
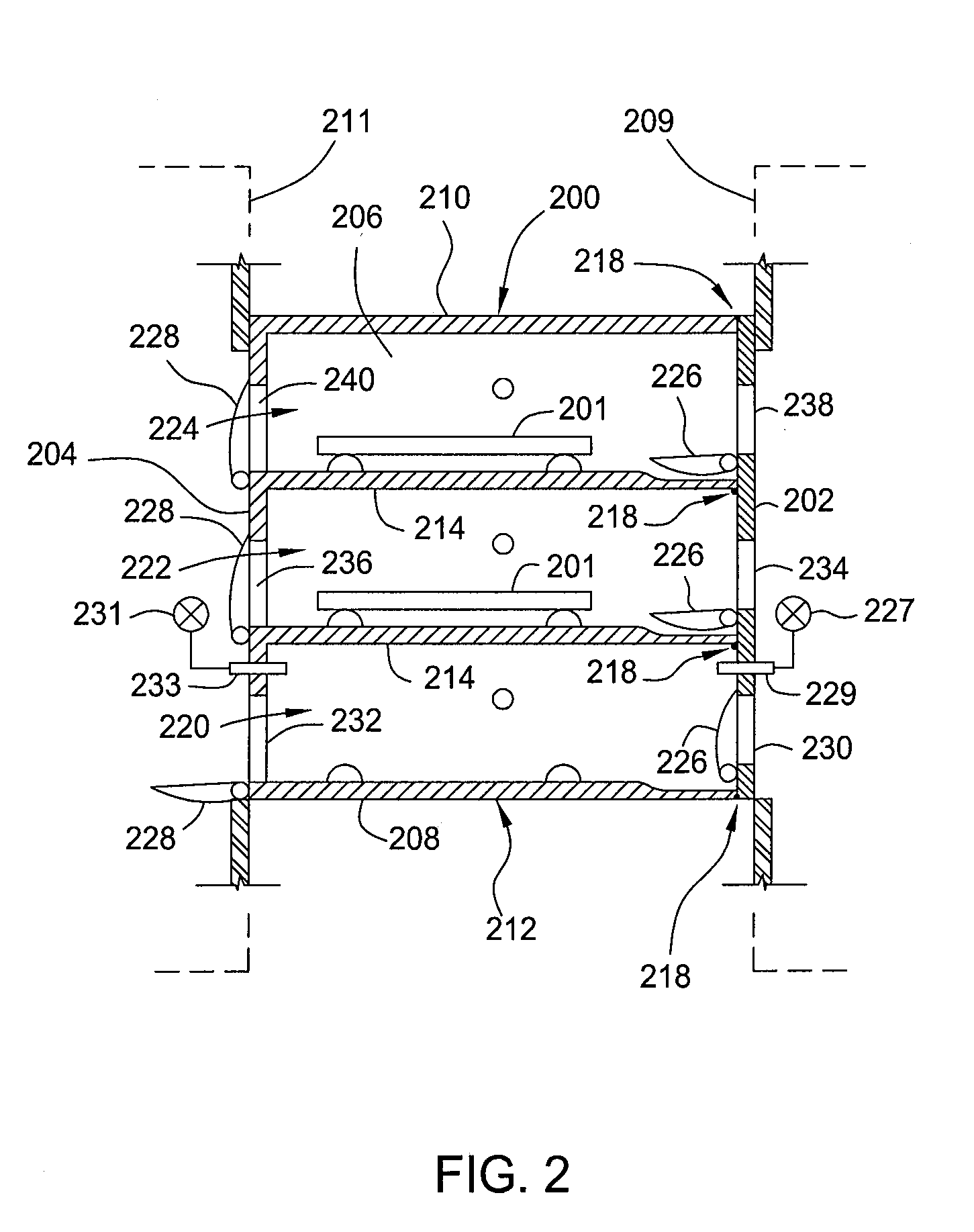
Load lock chamber for large area substrate processing system
ActiveUS20100054905A1Reduce pollutionSemiconductor/solid-state device manufacturingConveyor partsIsolated environmentContamination
The present invention generally includes a load lock chamber for transferring large area substrates into a vacuum processing chamber. The load lock chamber may have one or more separate, environmentally isolated environments. Each processing environment may have a plurality exhaust ports for drawing a vacuum. The exhaust ports may be located at the corners of the processing environment. When a substrate is inserted into the load lock chamber from the factory interface, the environment may need to be evacuated. Due to the exhaust ports located at the corners of the environment, any particles or contaminants that may be present may be pulled to the closest corner and out of the load lock chamber without being pulled across the substrate. Thus, substrate contamination may be reduced.
Owner:APPLIED MATERIALS INC
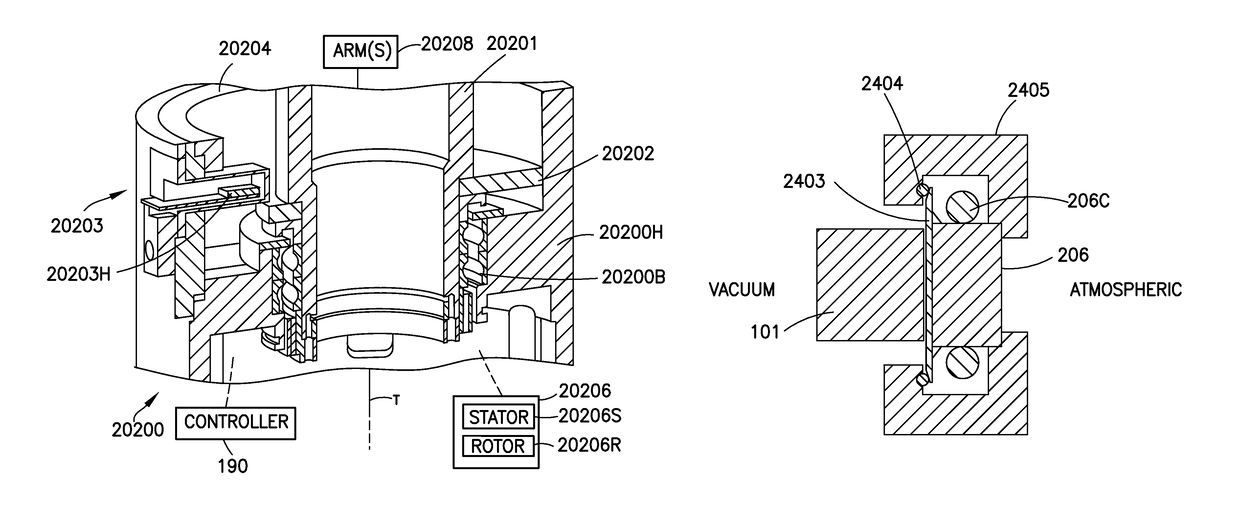
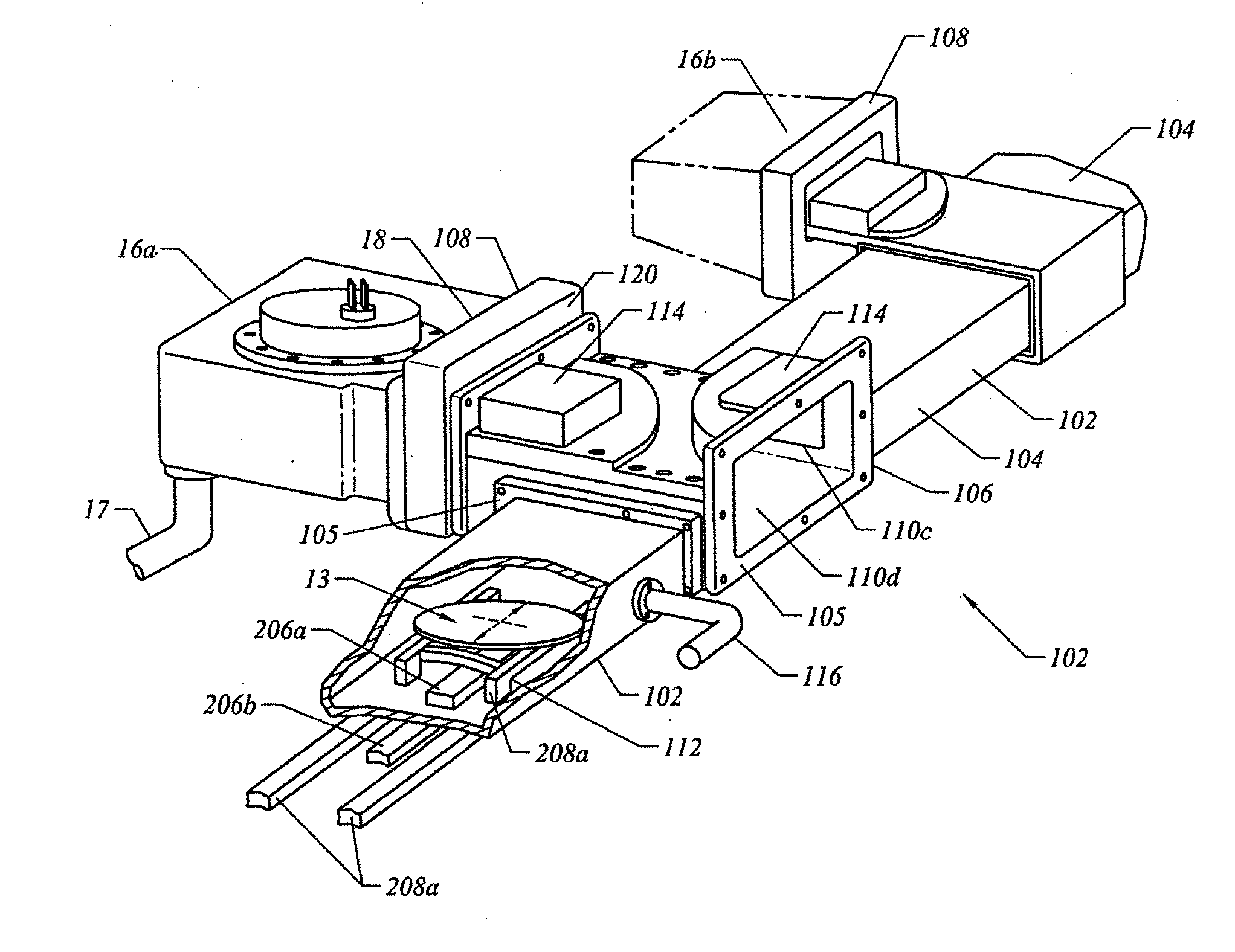
Sealed robot drive
ActiveUS9948155B2Improve motor efficiencyAvoid excessive deflectionMagnetic circuit rotating partsSynchronous motorsFlux loopEngineering
A transport apparatus including a housing, a drive mounted to the housing, and at least one transport arm connected to the drive where the drive includes at least one rotor having at least one salient pole of magnetic permeable material and disposed in an isolated environment, at least one stator having at least one salient pole with corresponding coil units and disposed outside the isolated environment, where the at least one salient pole of the at least one stator and the at least one salient pole of the rotor form a closed magnetic flux circuit between the at least one rotor and the at least one stator, and at least one seal configured to isolate the isolated environment where the at least one seal is integral to the at least one stator.
Owner:BOOKS AUTOMATION US LLC
System and method for hierarchical interception with isolated environments
ActiveUS8943501B1Program synchronisationDigital data processing detailsIsolated environmentData library
A system, method, computer program, and / or computer readable medium for providing hierarchical interception for applications within isolated environments The computer readable medium includes computer-executable instructions for execution by a processing system. The computer-executable instructions may be for installing interceptors, configuring interceptors, preloading shared libraries, using trampoline functions, removal of interceptors, mapping between resources inside and outside the isolated environment, providing an interception database, loading the interception database, redirection of resources, and providing the hierarchy of interceptors.
Owner:INT BUSINESS MASCH CORP
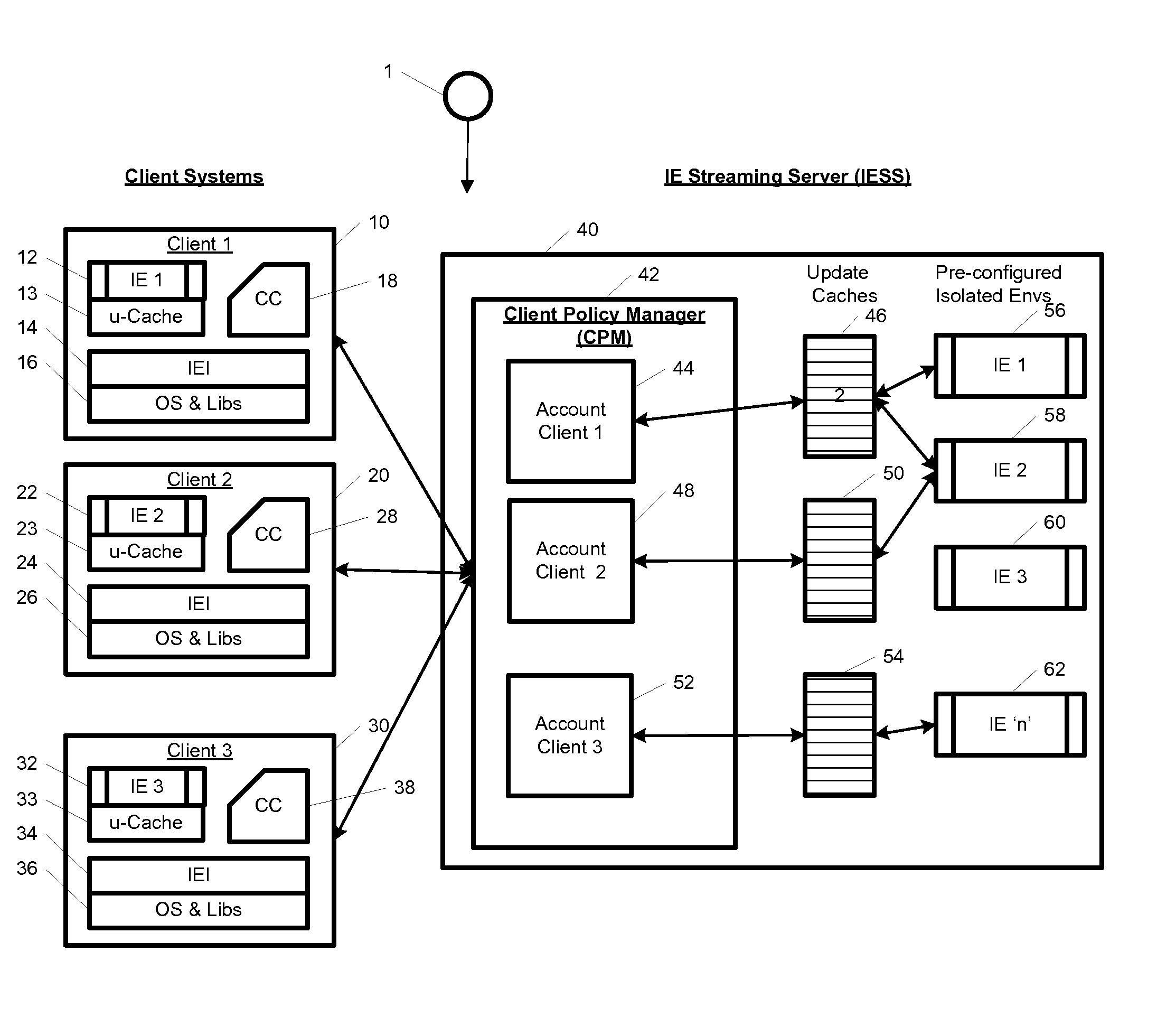
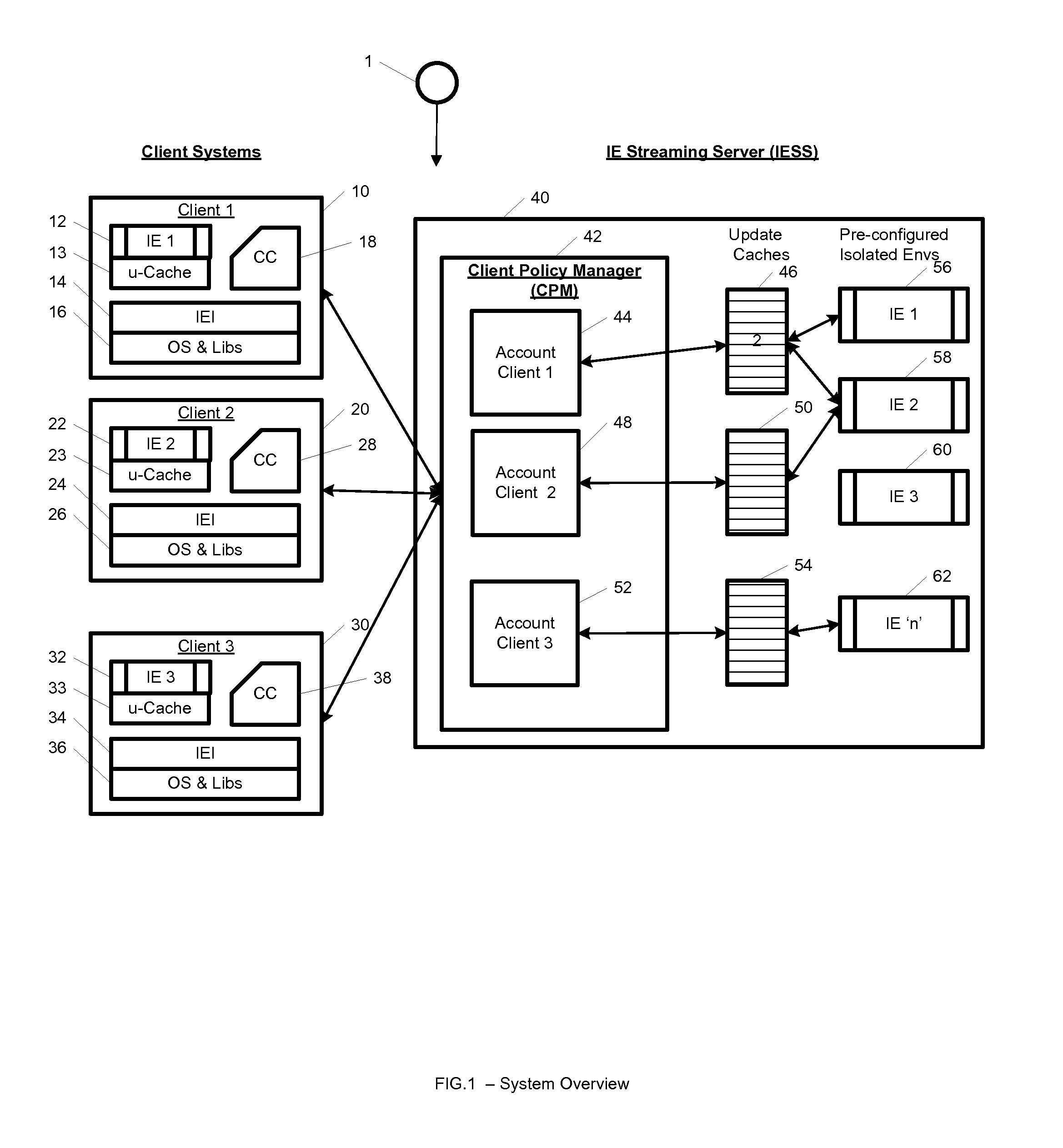
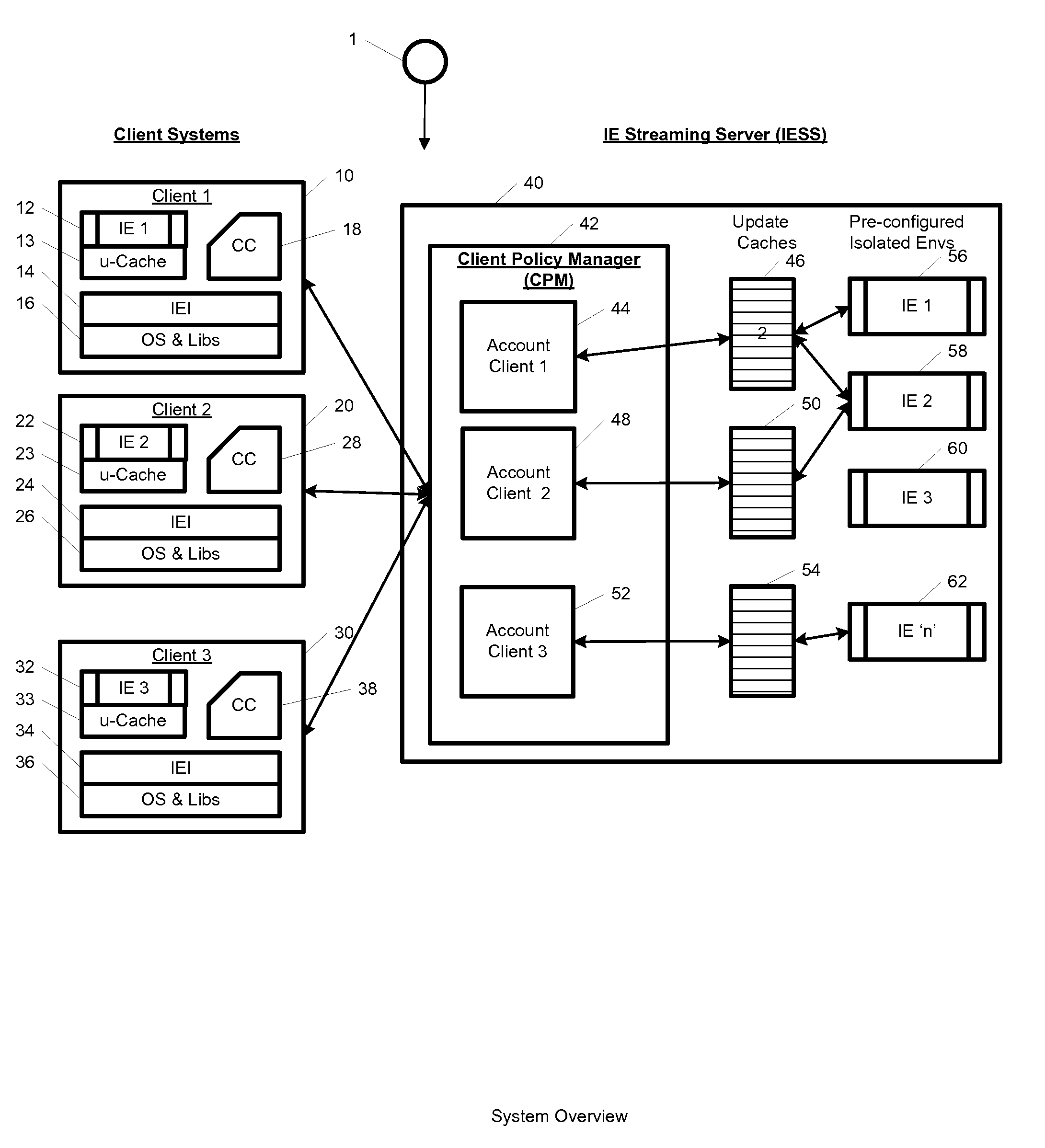
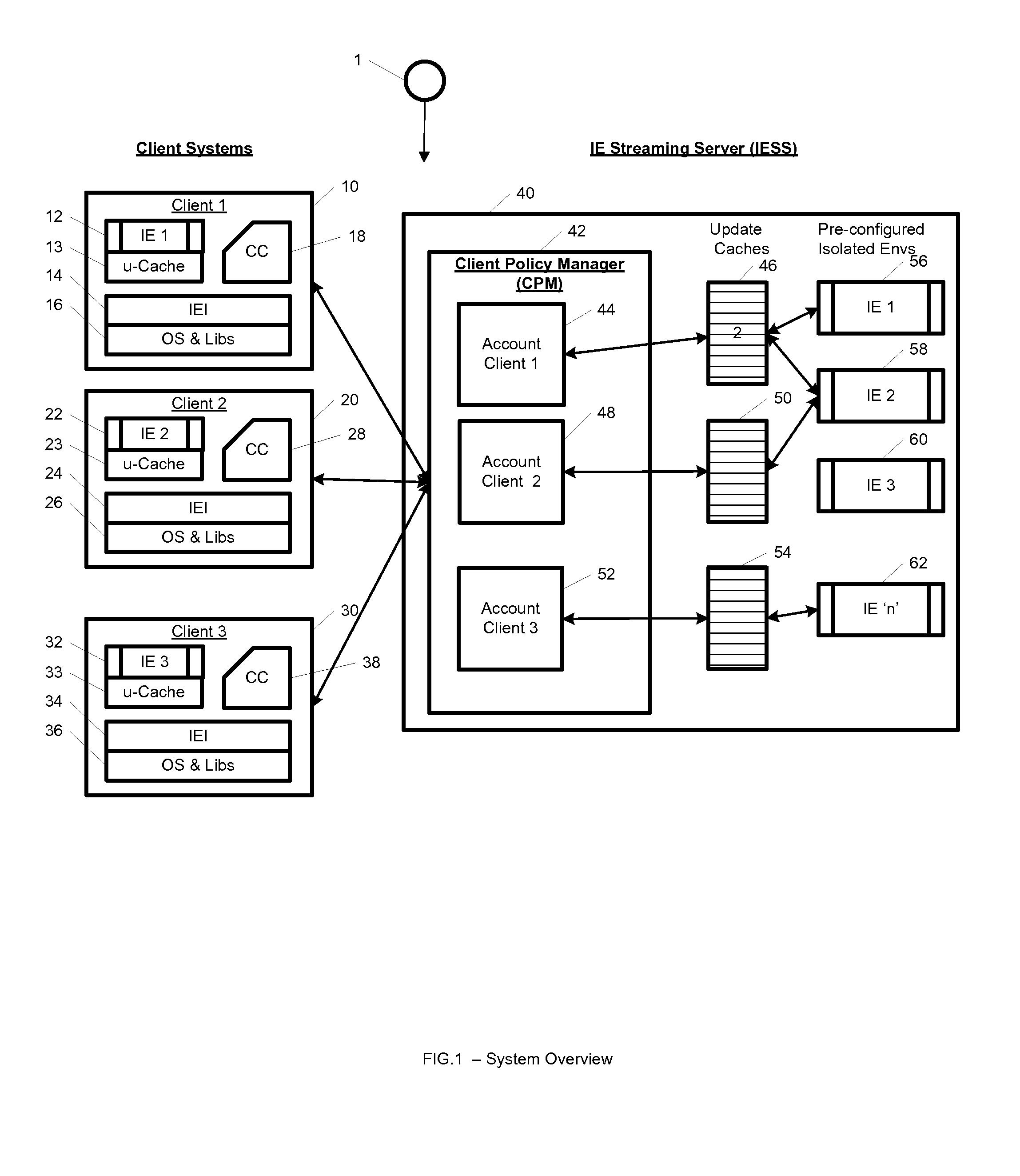
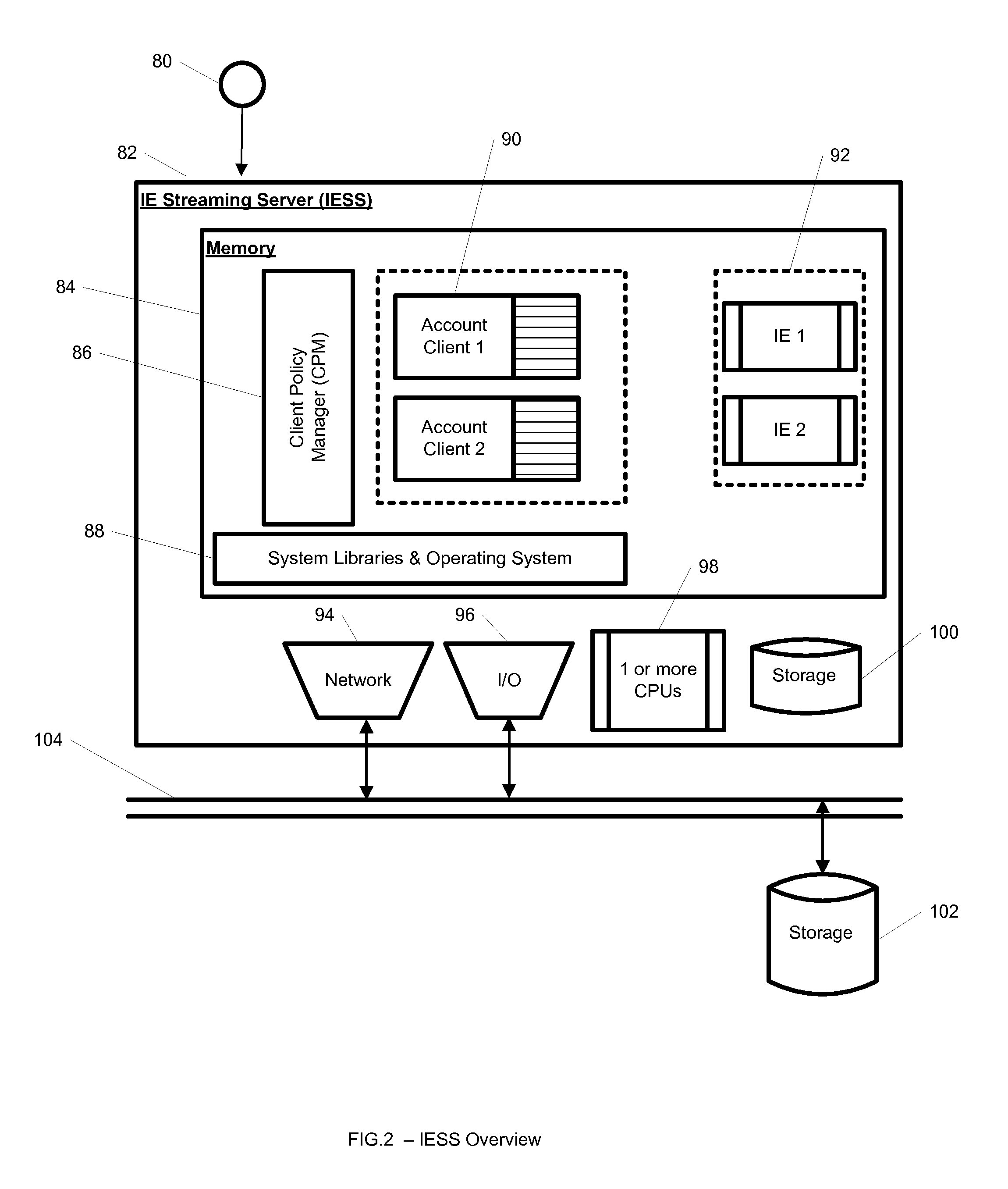
System and method for streaming application isolation
InactiveUS8418236B1Optimizing streamingDigital data processing detailsUser identity/authority verificationCredentialingOperational system
A system, method, computer program and / or computer readable medium for providing streaming of one or more applications from streaming servers onto one or more clients. The computer readable medium includes computer-executable instructions for execution by a processing system. The one or more applications are contained within one or move isolated environments, and the isolated environments are streamed from the servers onto clients. The system may include authentication of the streaming servers and authentication of clients and credentialing of the isolated environments and applications the clients are configured to run. The system may further include encrypted communication between the streaming servers and the clients. The system may further include a management interface where administrators may add, remove and configure isolated environments, configure client policies and credentials, and force upgrades. The streamed isolated environments may be isolated from other applications and the host operating system on the clients and applications within the isolated environments may run without performing an application-installation on the client.
Owner:OPEN INVENTION NEWTORK LLC
Universal modular wafer transport system
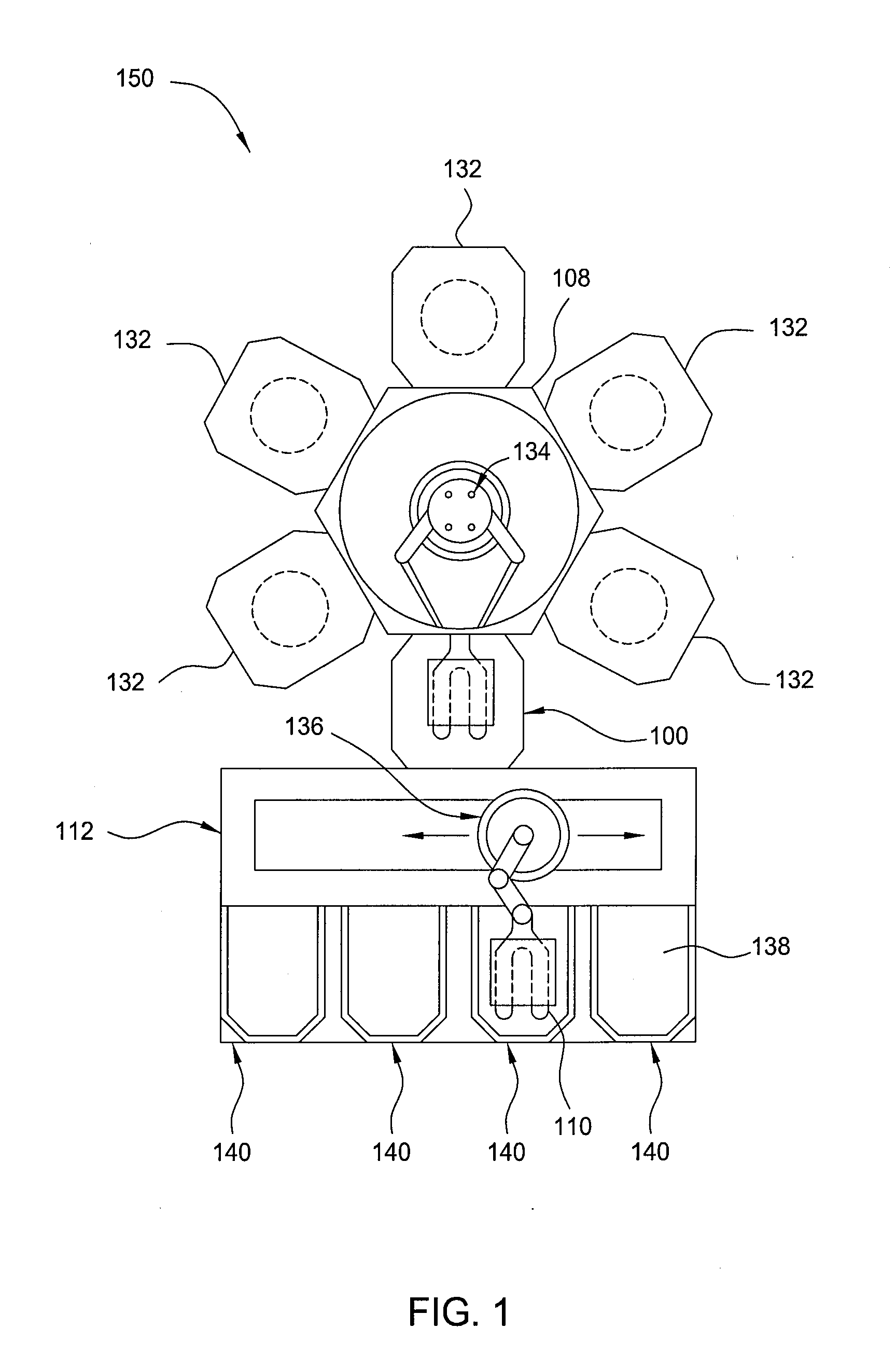
InactiveUS20080101892A1Reduce the amount requiredAccurate locationSemiconductor/solid-state device manufacturingSliding/levitation railway systemsAir bearingTransfer system
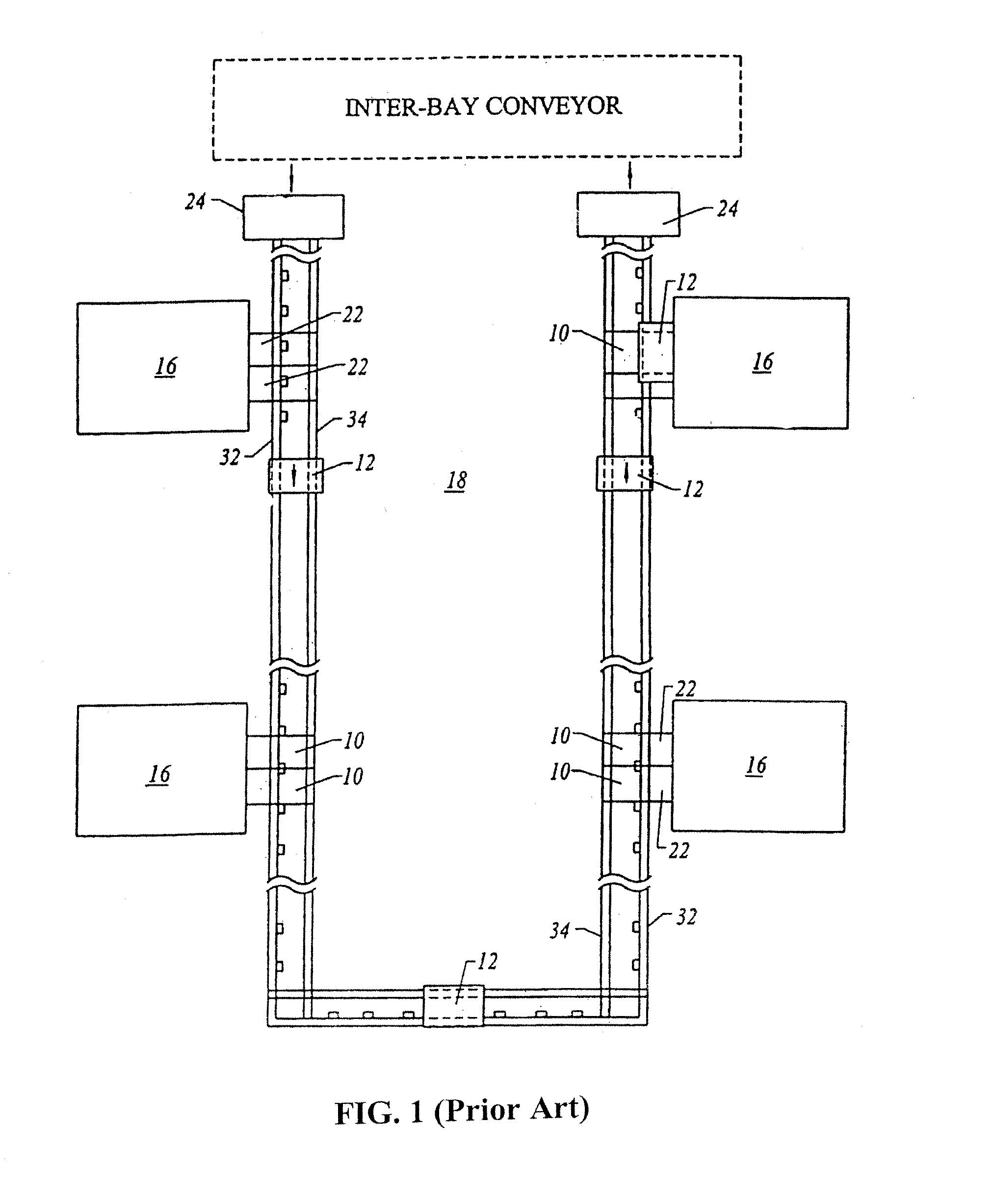
The present invention is a wafer transfer system that transports individual wafers between chambers within an isolated environment. In one embodiment, a wafer is transported by a wafer shuttle that travel within a transport enclosure. The interior of the transport enclosure is isolated from the atmospheric conditions of the surrounding wafer fabrication facility. Thus, an individual wafer may be transported throughout the wafer fabrication facility without having to maintain a clean room environment for the entire facility. The wafer shuttle may be propelled by various technologies, such as, but not limited to, magnetic levitation or air bearings. The wafer shuttle may also transport more than one wafer simultaneously. The interior of the transport enclosure may also be under vacuum, gas-filled, or subject to filtered air.
Owner:BOOKS AUTOMATION US LLC
High Throughput Processing Using Metal Organic Chemical Vapor Deposition
InactiveUS20130171350A1Little effectSignificant changeLiquid surface applicatorsChemical vapor deposition coatingSupporting systemGas phase
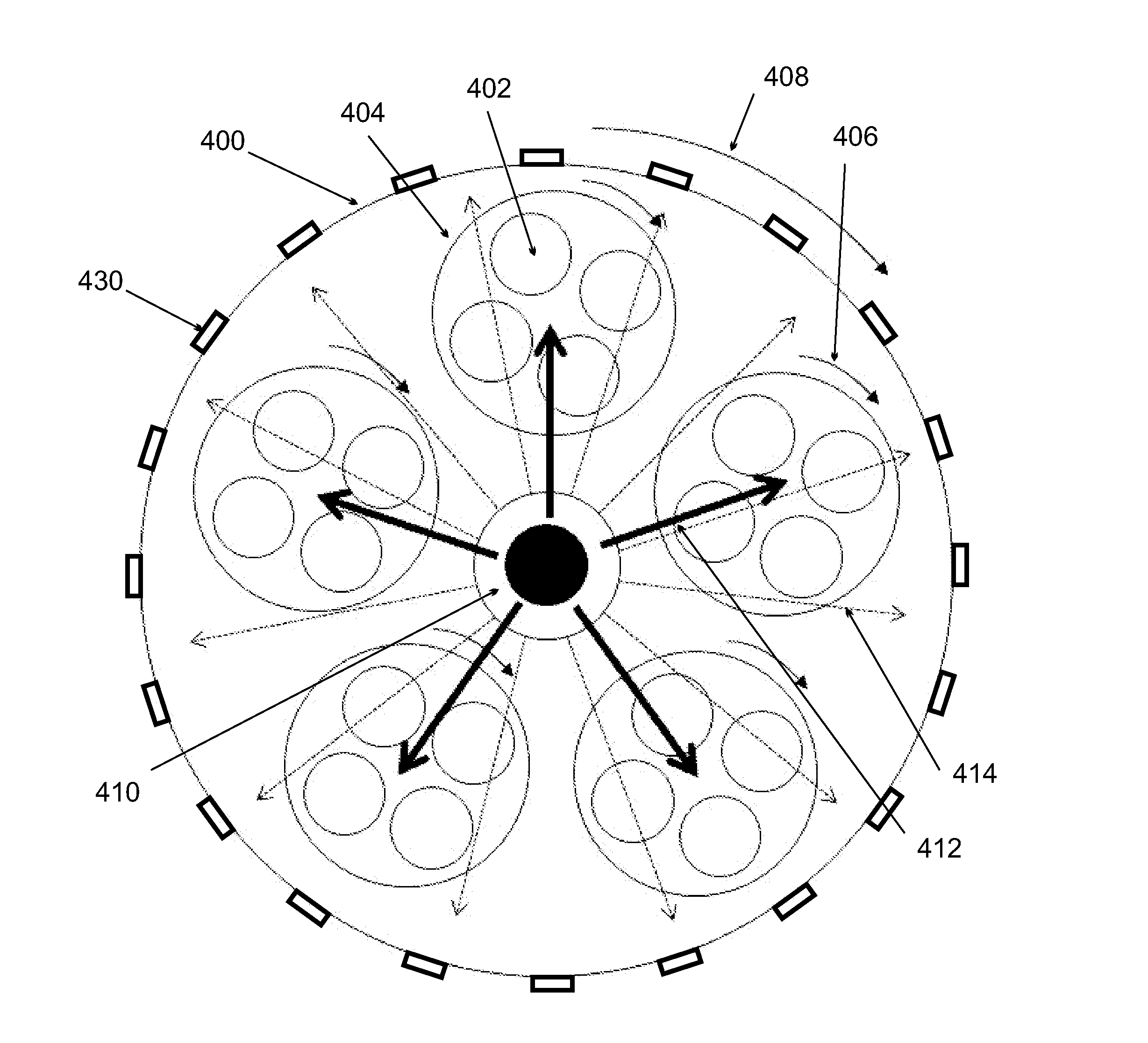
A metal-organic chemical vapor deposition (MOCVD) system is provided for high throughput processing. The system comprises a chamber containing a substrate support system comprising a plurality of substrate support planets operable to support one or more substrates, and a gas emission system operable to provide a plurality of isolated environments suitable for depositing uniform layers on the substrates. The MOCVD system is operable to independently vary one or more process parameters in each isolated environment, and to provide common process parameters to all substrates for depositing one or more layers on all substrates. Methods of forming uniform layers on a substrate are provided wherein at least one of the layers is deposited in an isolated environment.
Owner:INTERMOLECULAR
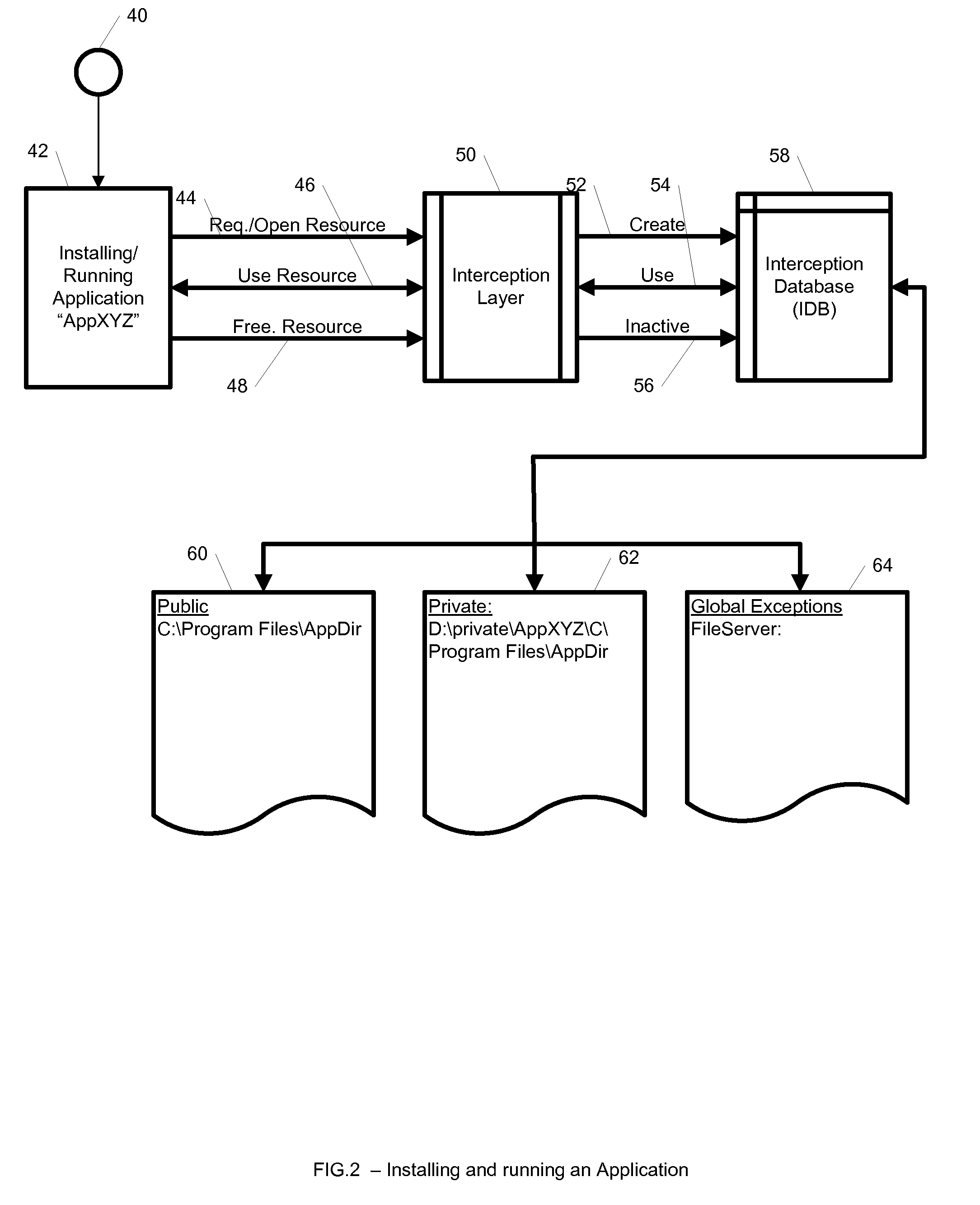
System and method for maintaining mappings between application resources inside and outside isolated environments
ActiveUS8904004B2Error detection/correctionDigital computer detailsApplication softwareIsolated environment
A system, method, and computer readable medium for maintaining mappings between resources inside an isolated environment and outside the isolated environment for one or more applications. The system may include a plurality of lists of resources requested by the one or more applications during installation and while executing, and a corresponding lists of resources inside the isolated environment. The system may also include a list of resource exceptions, wherein the mappings between resources as requested by the applications and their corresponding values in the isolated environment are maintained subject to the list of exceptions.
Owner:INT BUSINESS MASCH CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com