Data anti-leakage method based on operating system virtualization principle
An operating system and virtualization technology, applied in digital data protection, electronic digital data processing, instruments, etc., can solve problems such as reducing system usability and work efficiency, directly reading data files, increasing system difficulty, etc., to achieve Improve ease of use and work efficiency, broad use prospects, and improve operating efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
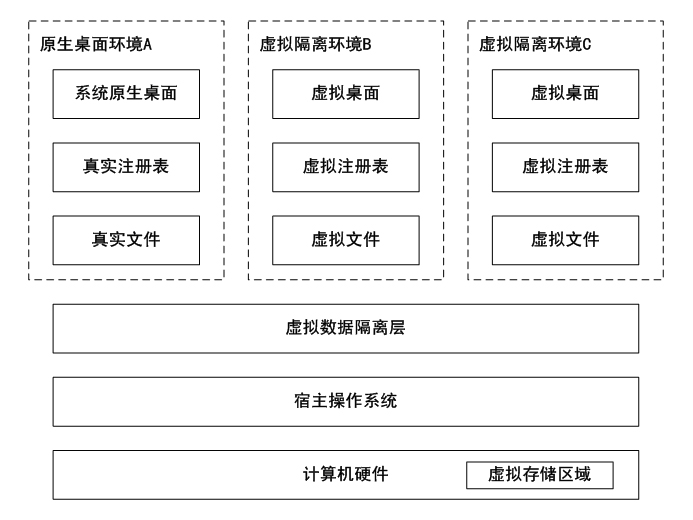
[0023] On a physical host, virtualized data leakage prevention software is installed, and one or more virtual isolation environments are established by the software, so that the computer has more than two user desktop environments. For ease of introduction, the following mainly introduces the system with two desktop environments.
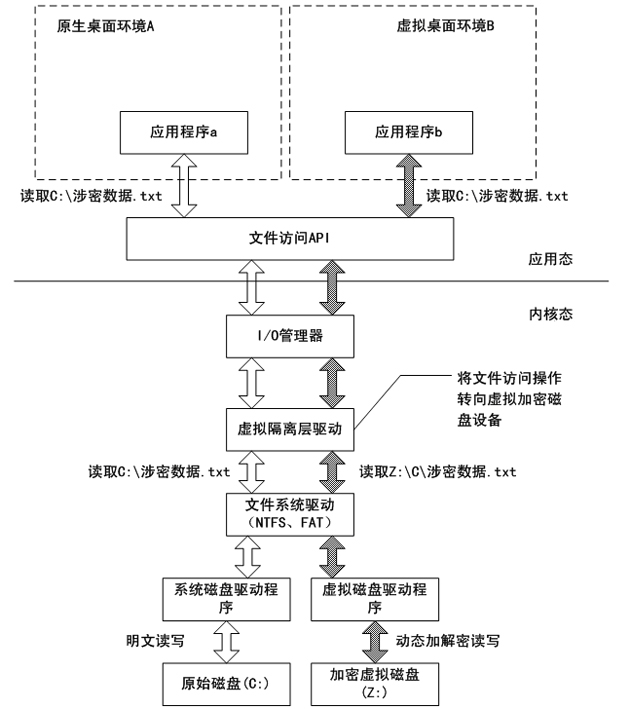
[0024] like figure 1As shown, among the two user desktops, one user desktop (desktop A) is a native desktop provided by the operating system of the physical host, and the other user desktop (desktop B) is a virtual desktop provided by data leakage prevention software. The files and registry information operated in the native desktop are all real data related to the host operating system, while the files and registry information operated in the virtual desktop are all virtual storage provided by the virtual isolation environment and stored on the physical hard disk Dummy data in the region. When the data leakage prevention software establishes a vi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com