Patents
Literature
119 results about "Credential management" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
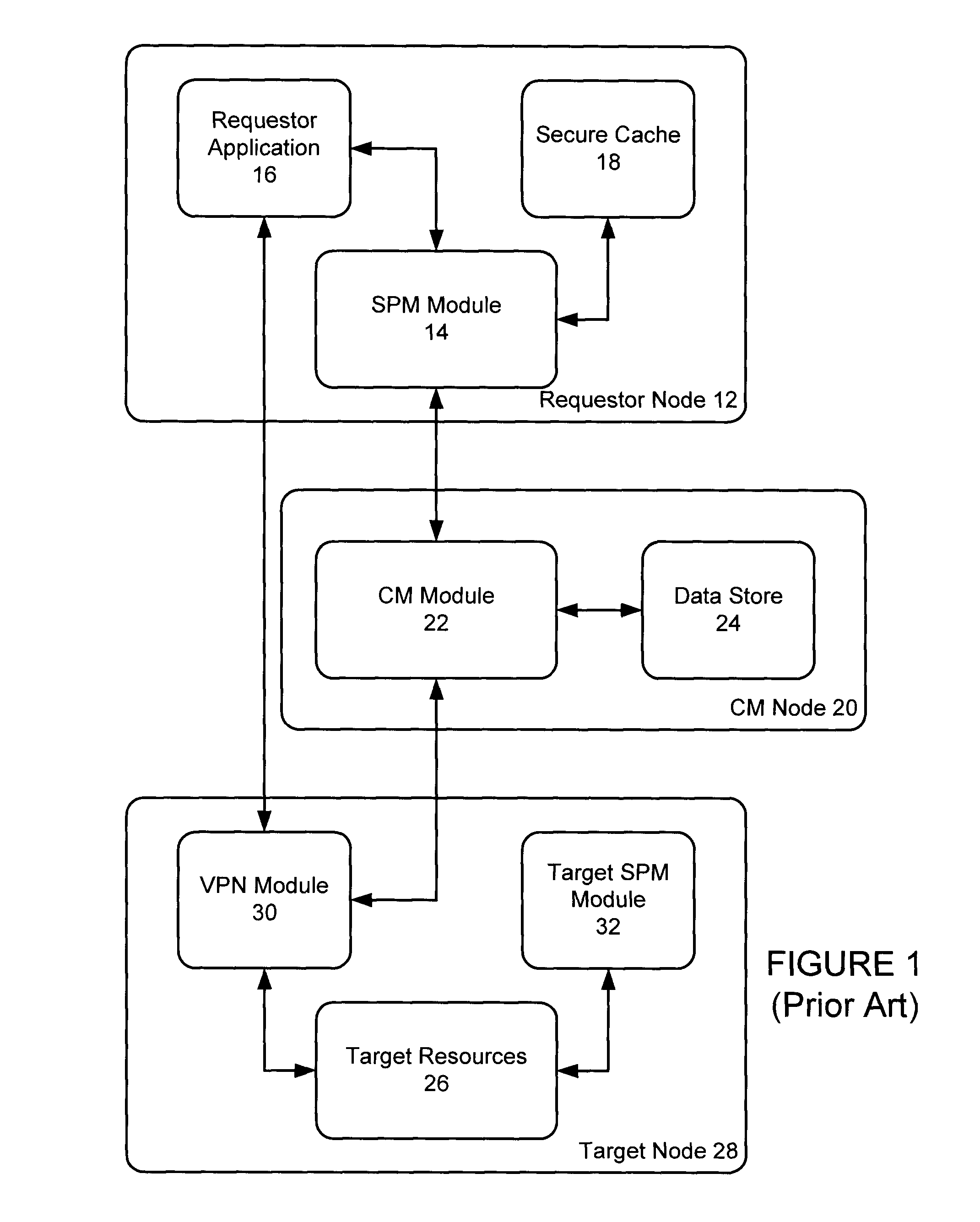
Credential Management. Credential Management is the set of practices that an organization uses to issue, track, update, and revoke credentials for identities within their context. A CREDENTIAL is authoritative evidence of an individual’s claimed identity.
Automated Access, Key, Certificate, and Credential Management
ActiveUS20150222604A1Effective rotationLow costMultiple keys/algorithms usagePublic key for secure communicationCredential managementTrust relationship
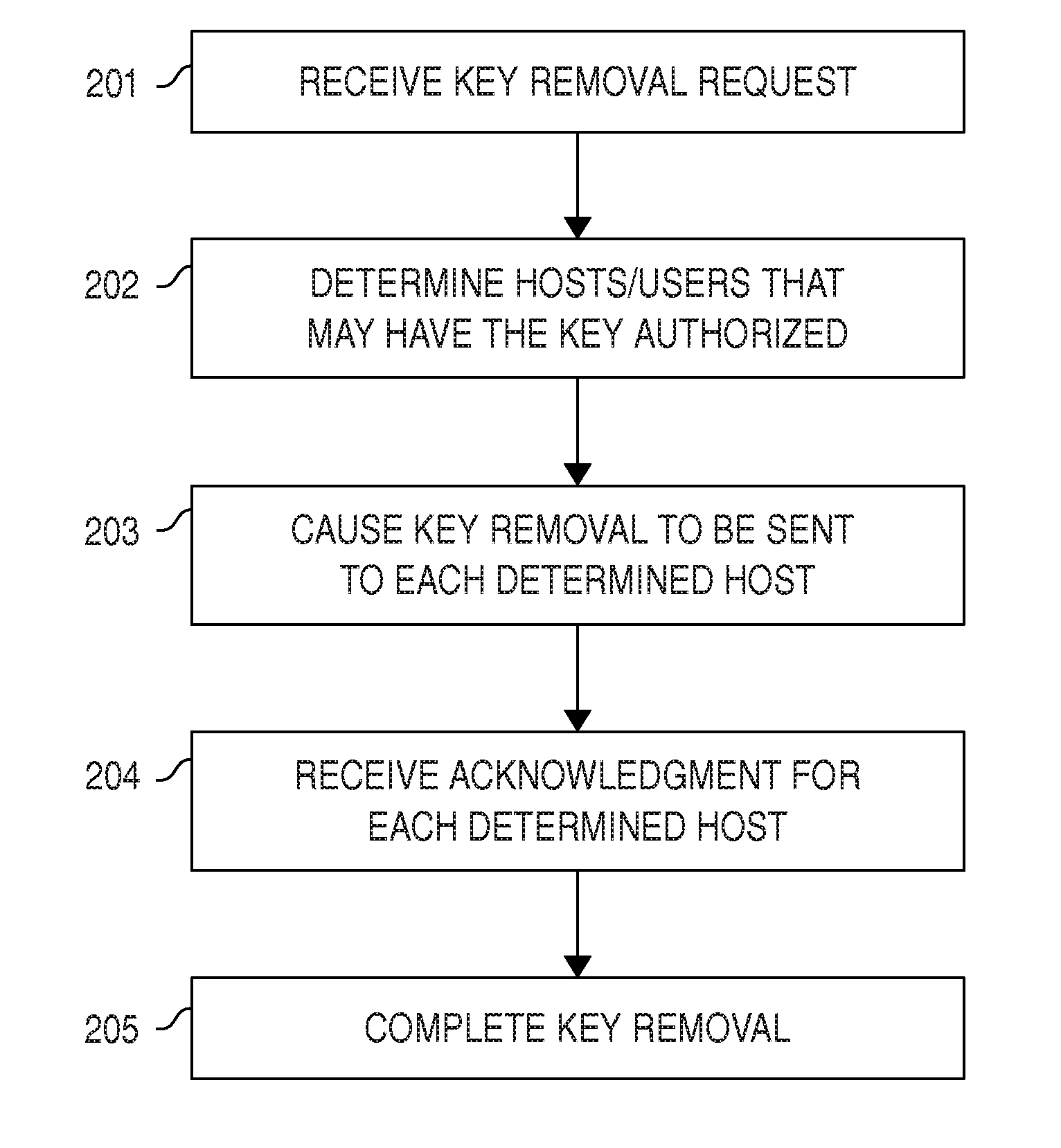
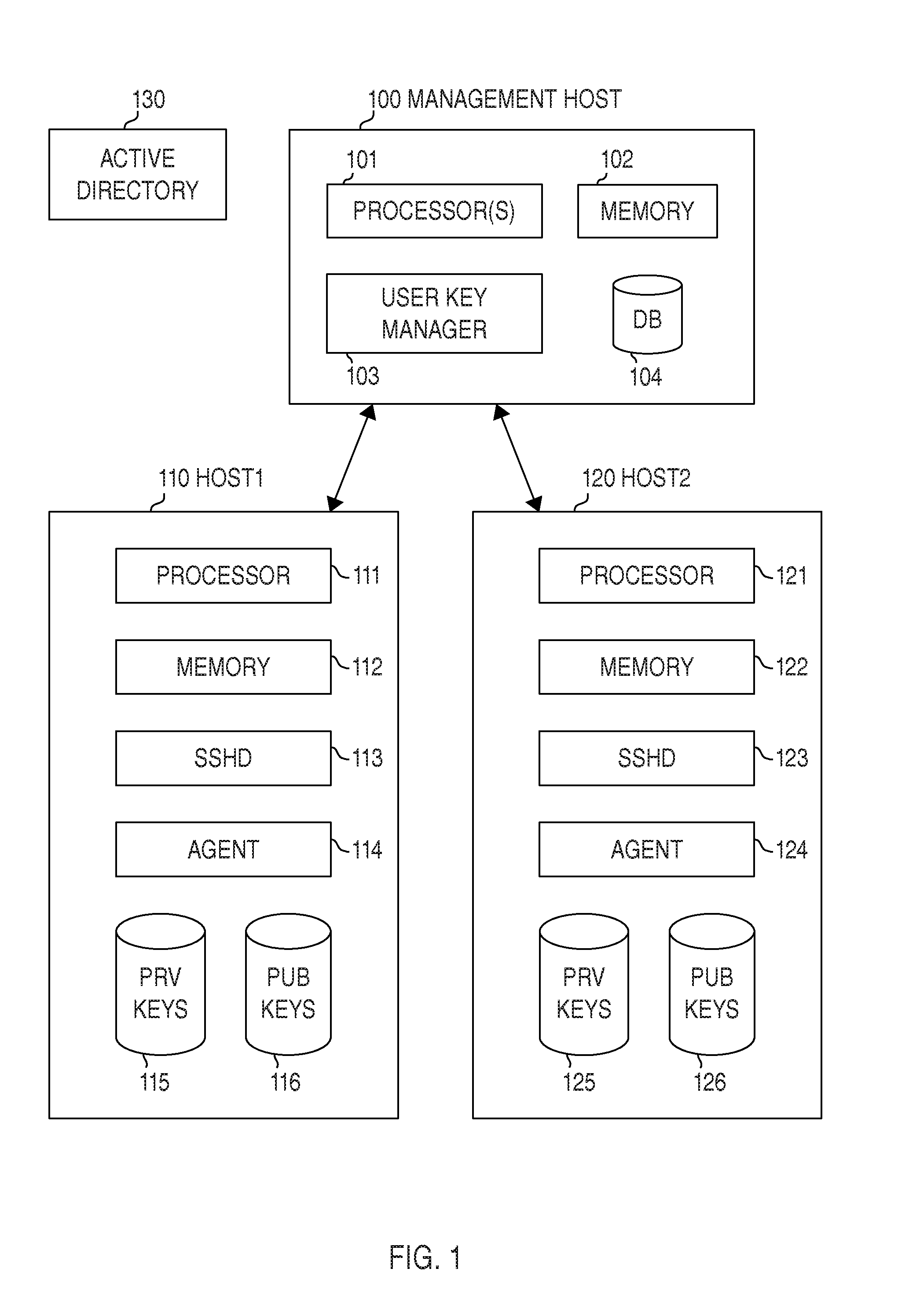
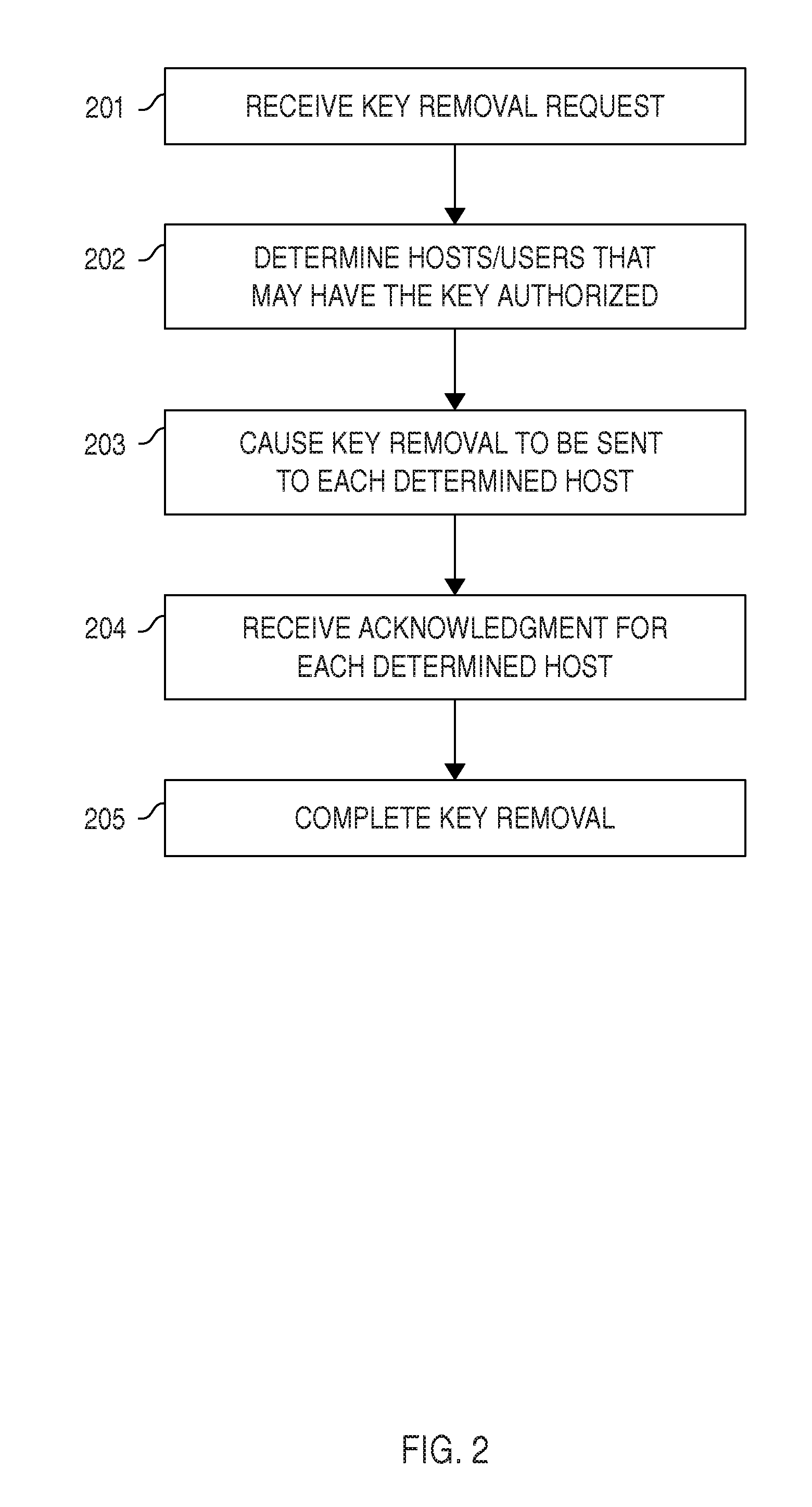
Certain embodiments provide means for managing automated access to computers, e.g., using SSH user keys and other kinds of trust relationships. Certain embodiments also provide for managing certificates, Kerberos credentials, and cryptographic keys. Certain embodiments provide for remediating legacy SSH key problems and for automating configuration of SSH keys, as well as for continuous monitoring.
Owner:SSH COMMUNICATIONS SECURITY
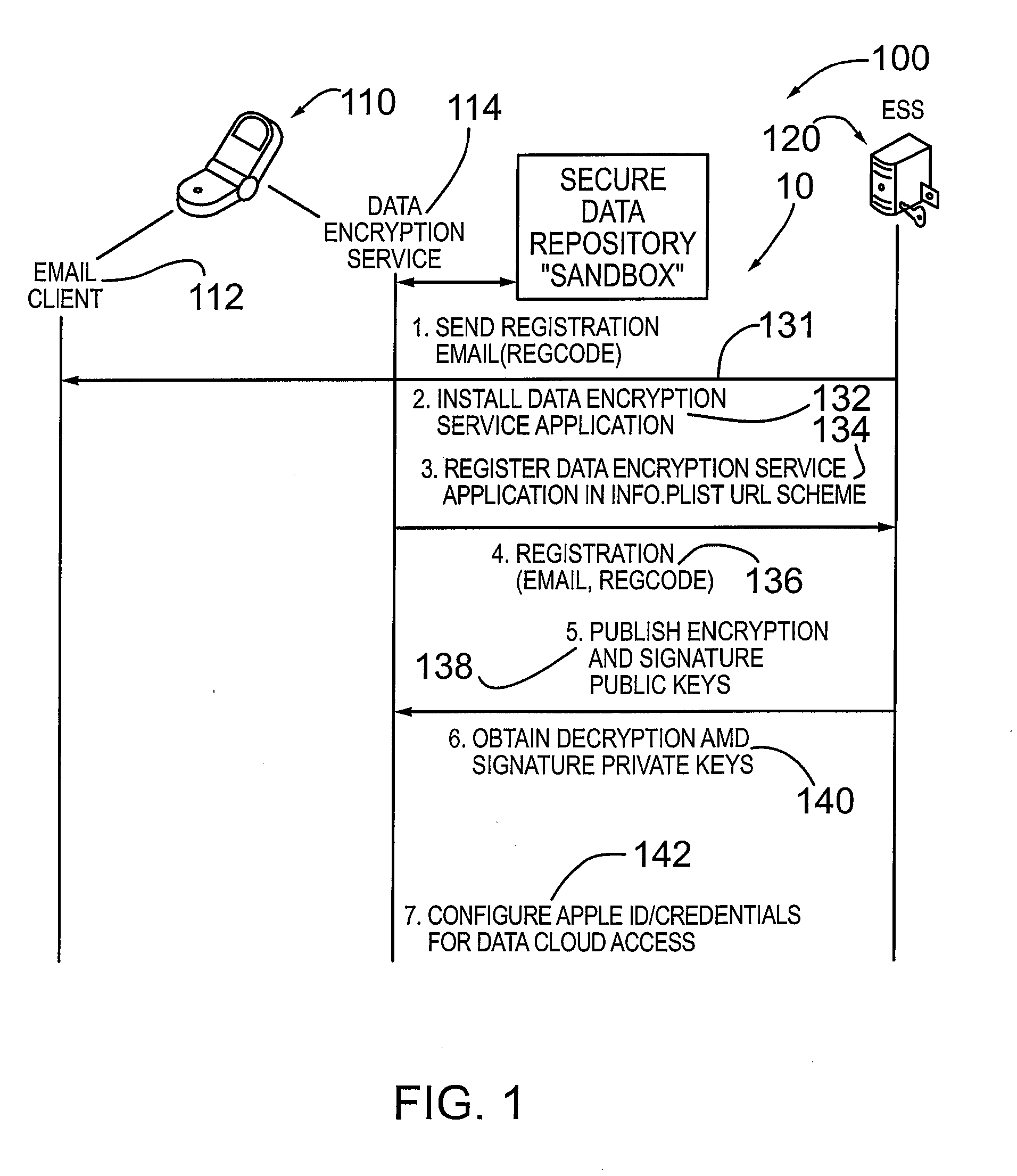
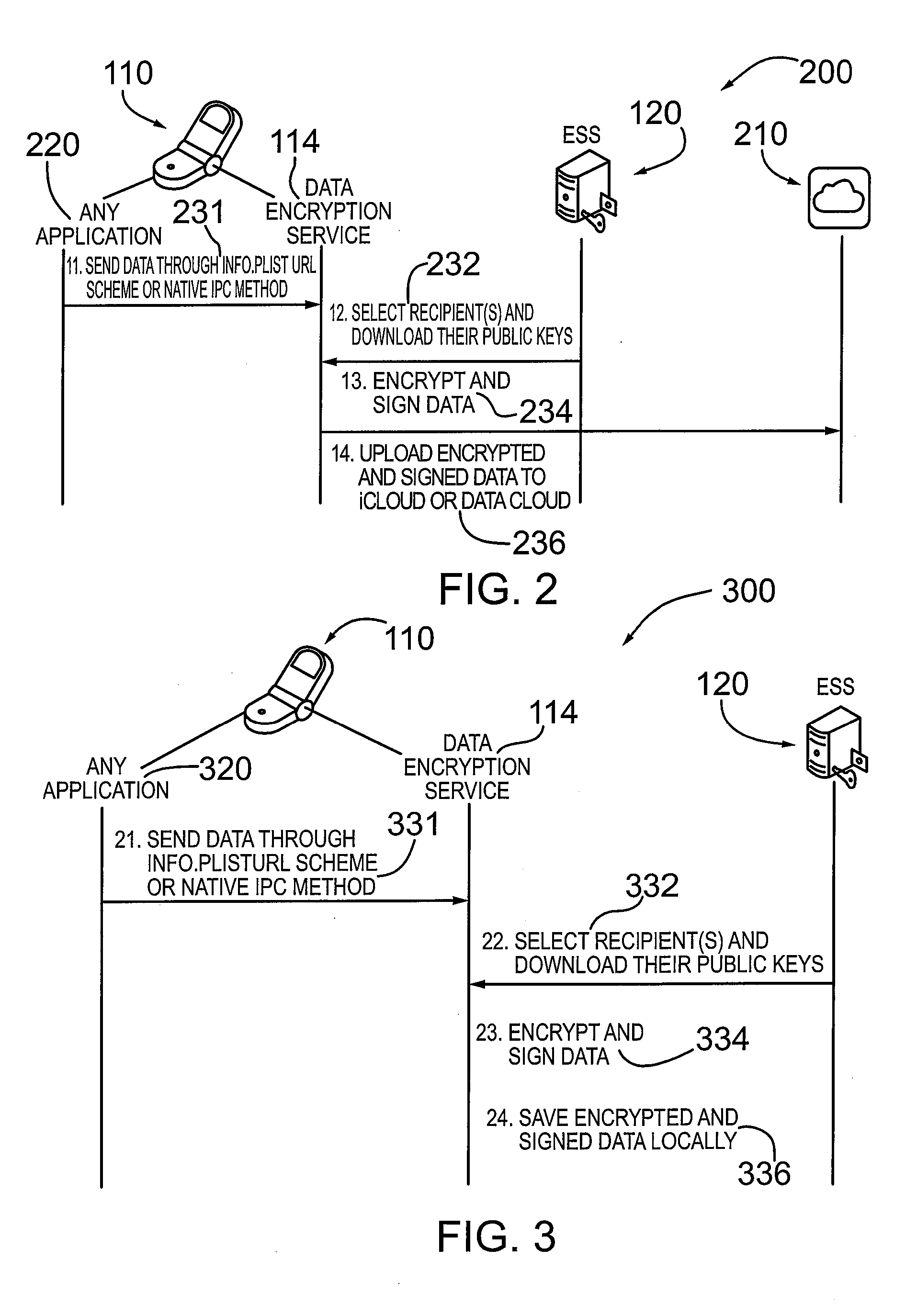
METHOD AND SYSTEM FOR CREDENTIAL MANAGEMENT AND DATA ENCRYPTION FOR iOS BASED DEVICES
InactiveUS20130067232A1User identity/authority verificationComputer security arrangementsOperational systemDigital signature
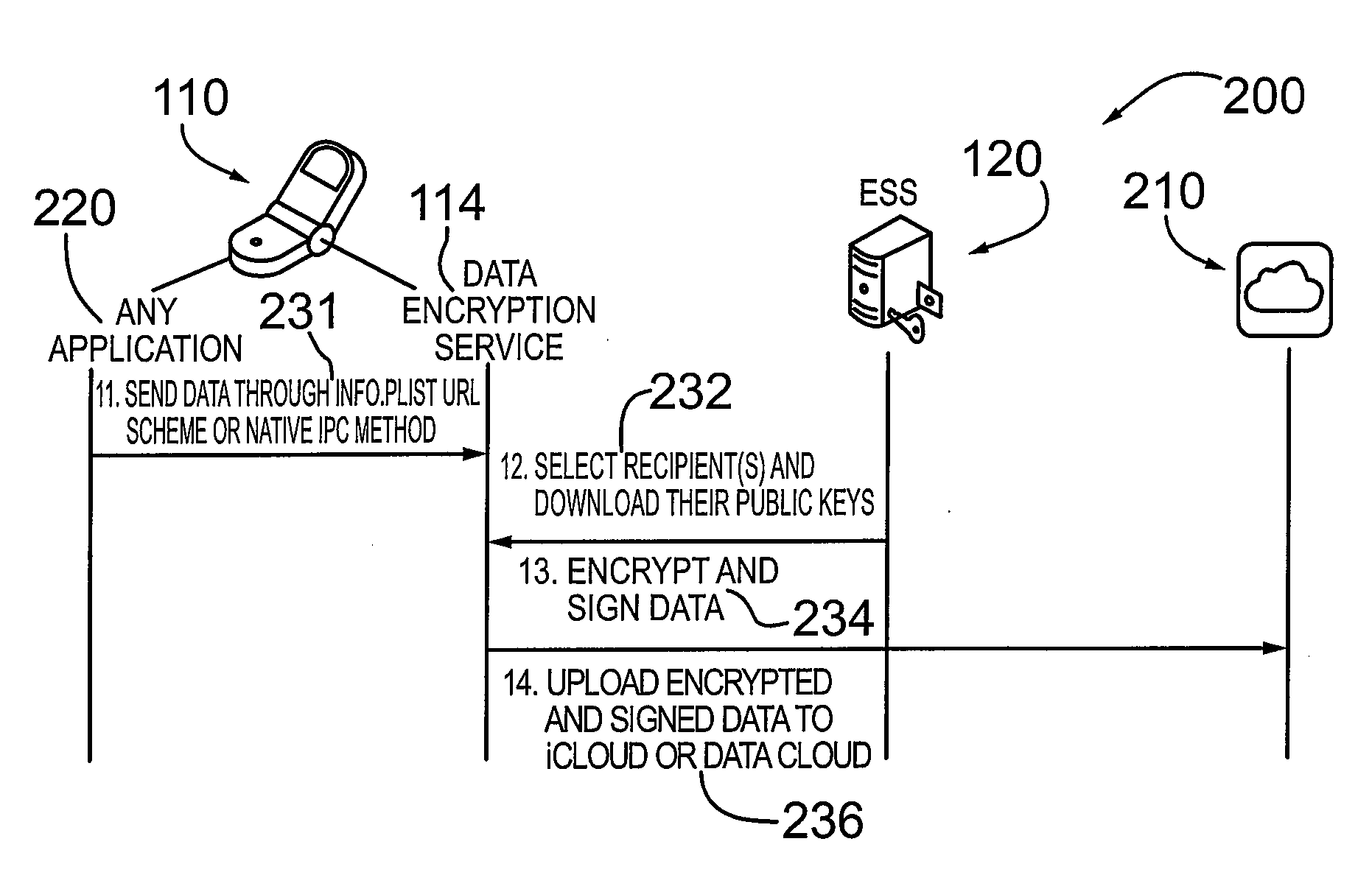
A mechanism and method for managing credentials on an electronic device and providing encryption and decryption services for the electronic device comprising a mobile communication device, smart phone or other computing device. According to an embodiment the device is configured with an iOS based operating system. The device is configured with a data encryption service application and an associated secure data repository. According to an embodiment, the electronic device is configured to download and / or cache credentials from a credential management system operatively coupled to the device, comprising public-private key pairs in a PKI system. According to an embodiment, the electronic device is configured with or stores a digital verification signature. The data encryption service application is configured to encrypt / decrypt data (e.g. files, documents) and optionally digitally sign the encrypted file. The encrypted (and digitally signed data) is contained in the sandbox associated with the data encryption service application.
Owner:ECHOWORX CORP
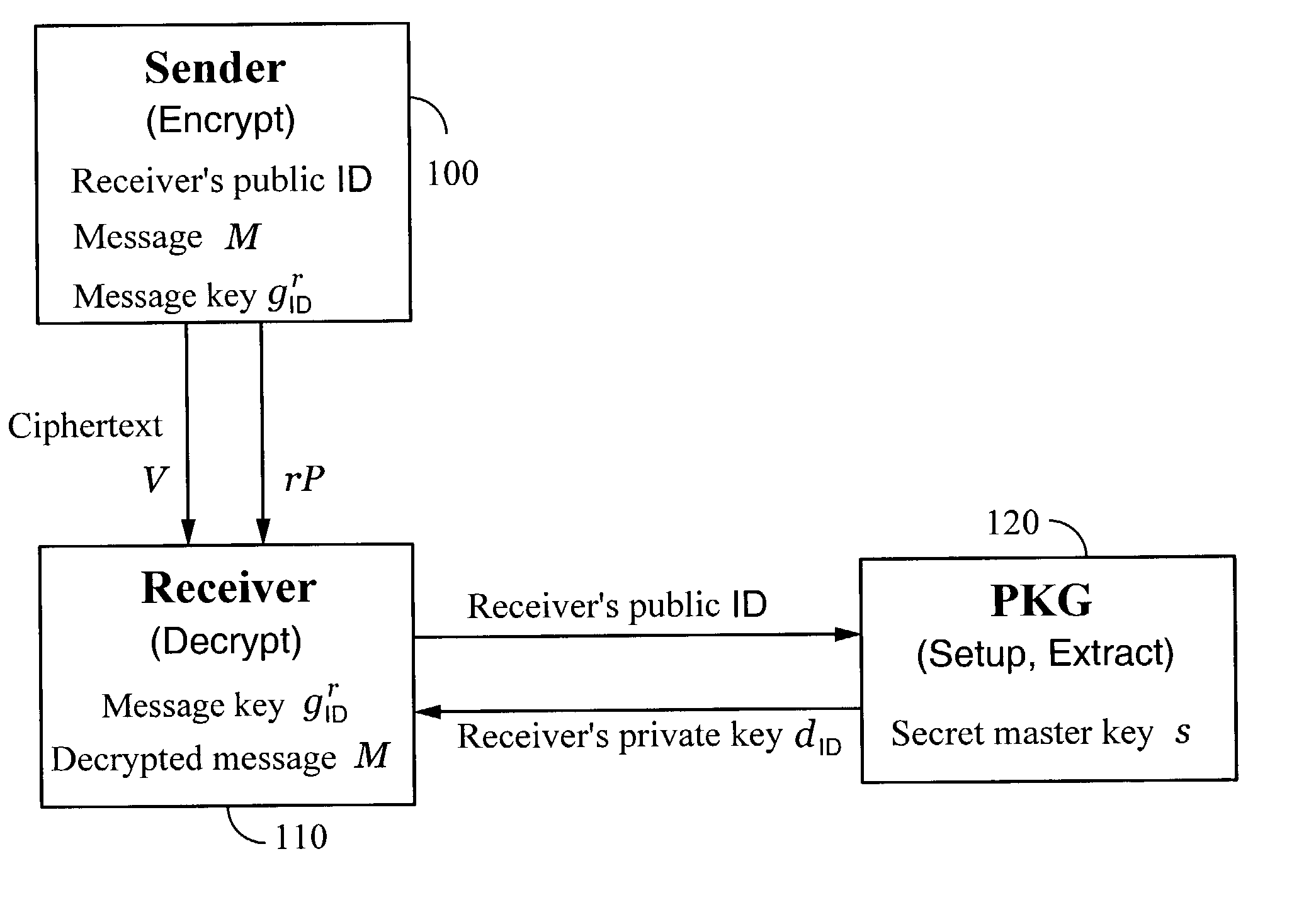
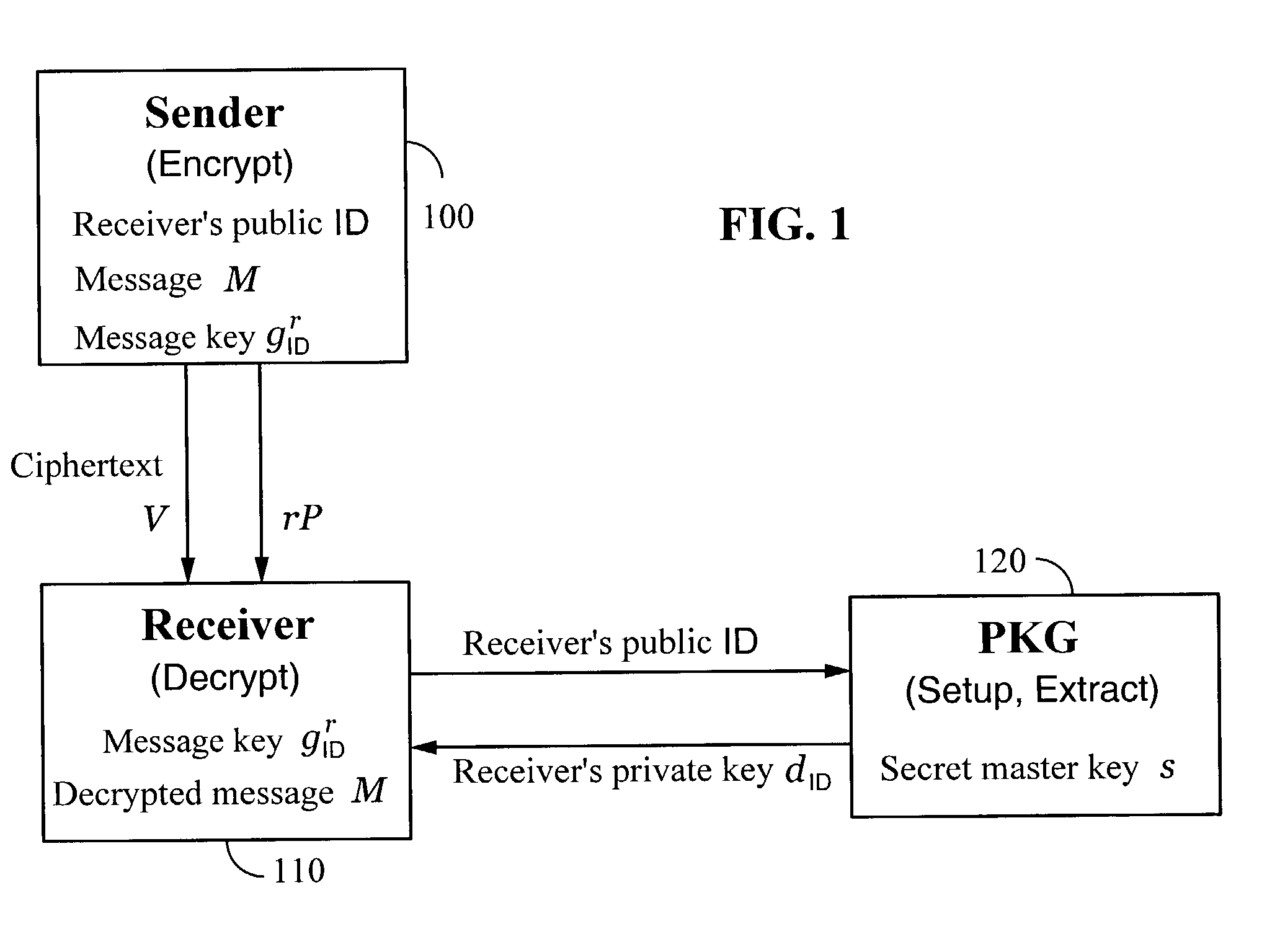
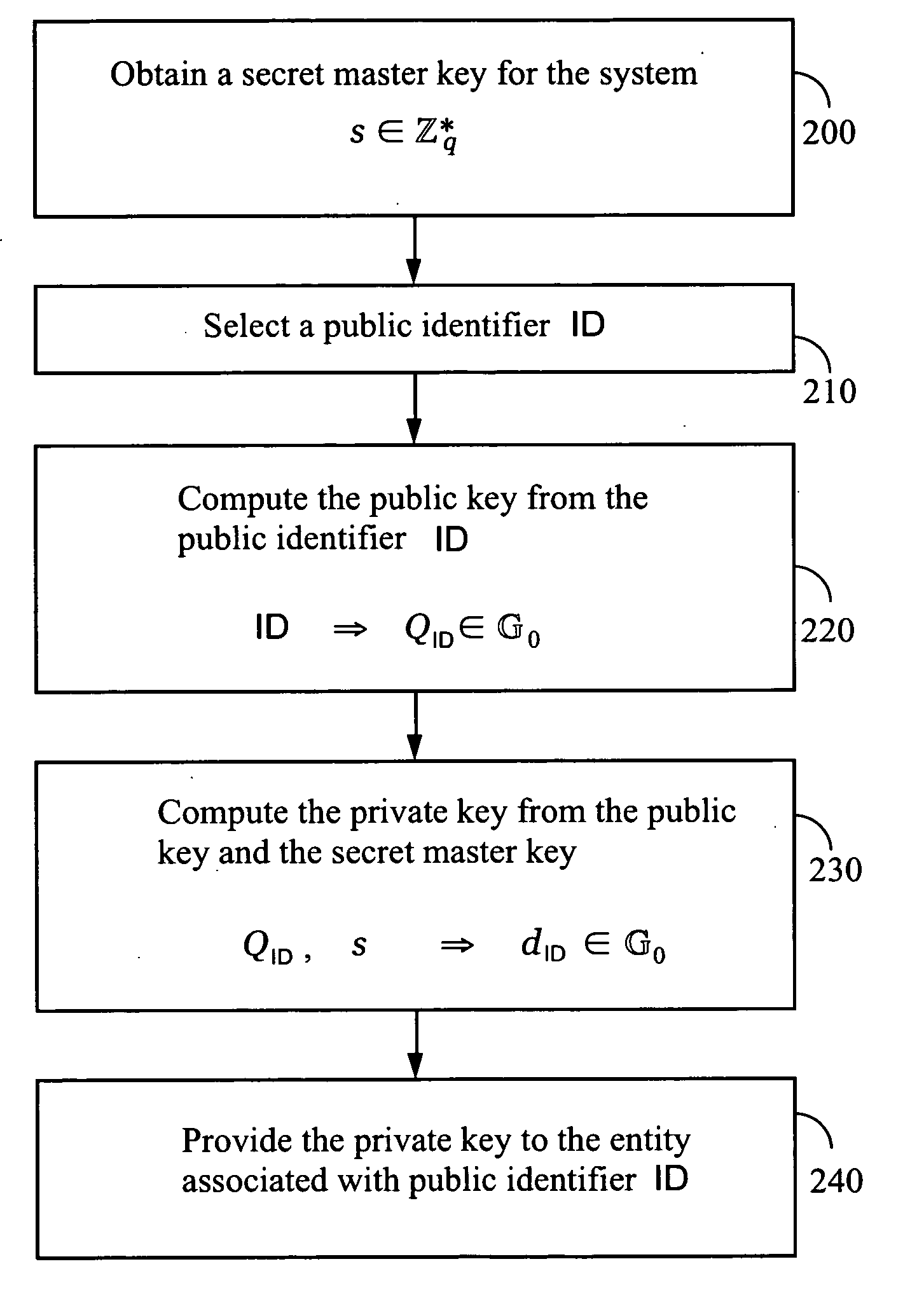
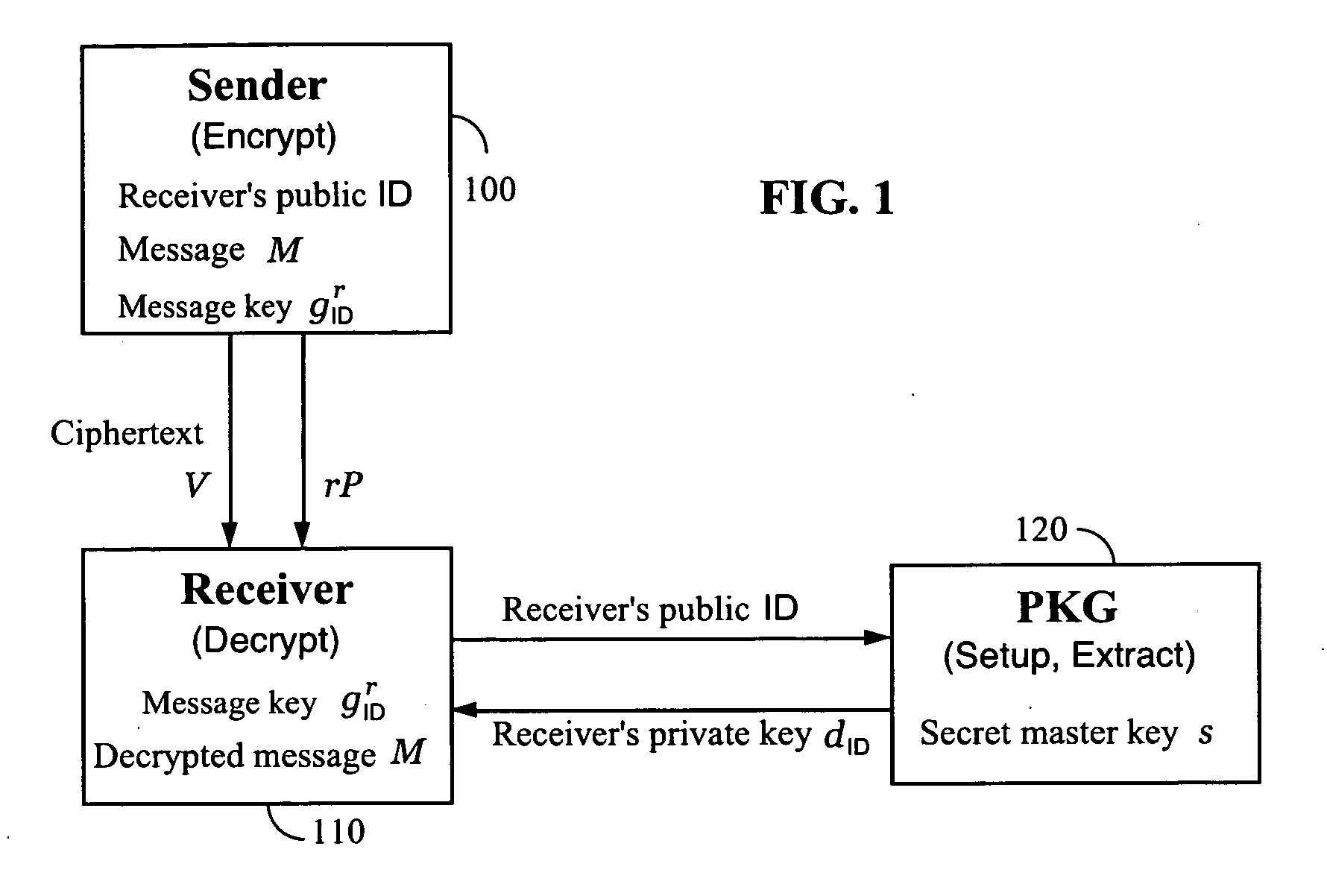
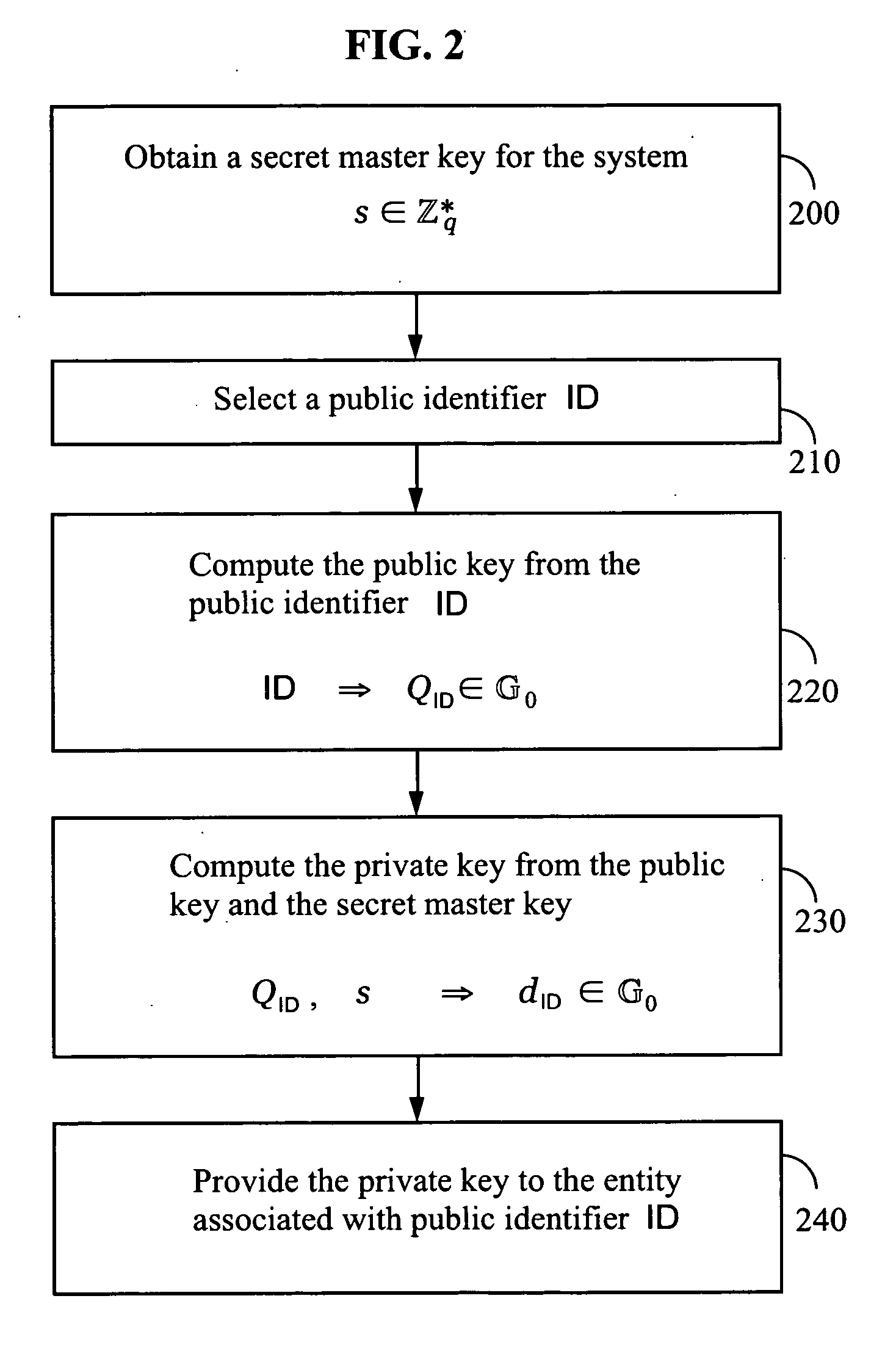
Systems and methods for identity-based encryption and related cryptographic techniques
ActiveUS7113594B2Key distribution for secure communicationPublic key for secure communicationEmail addressCiphertext
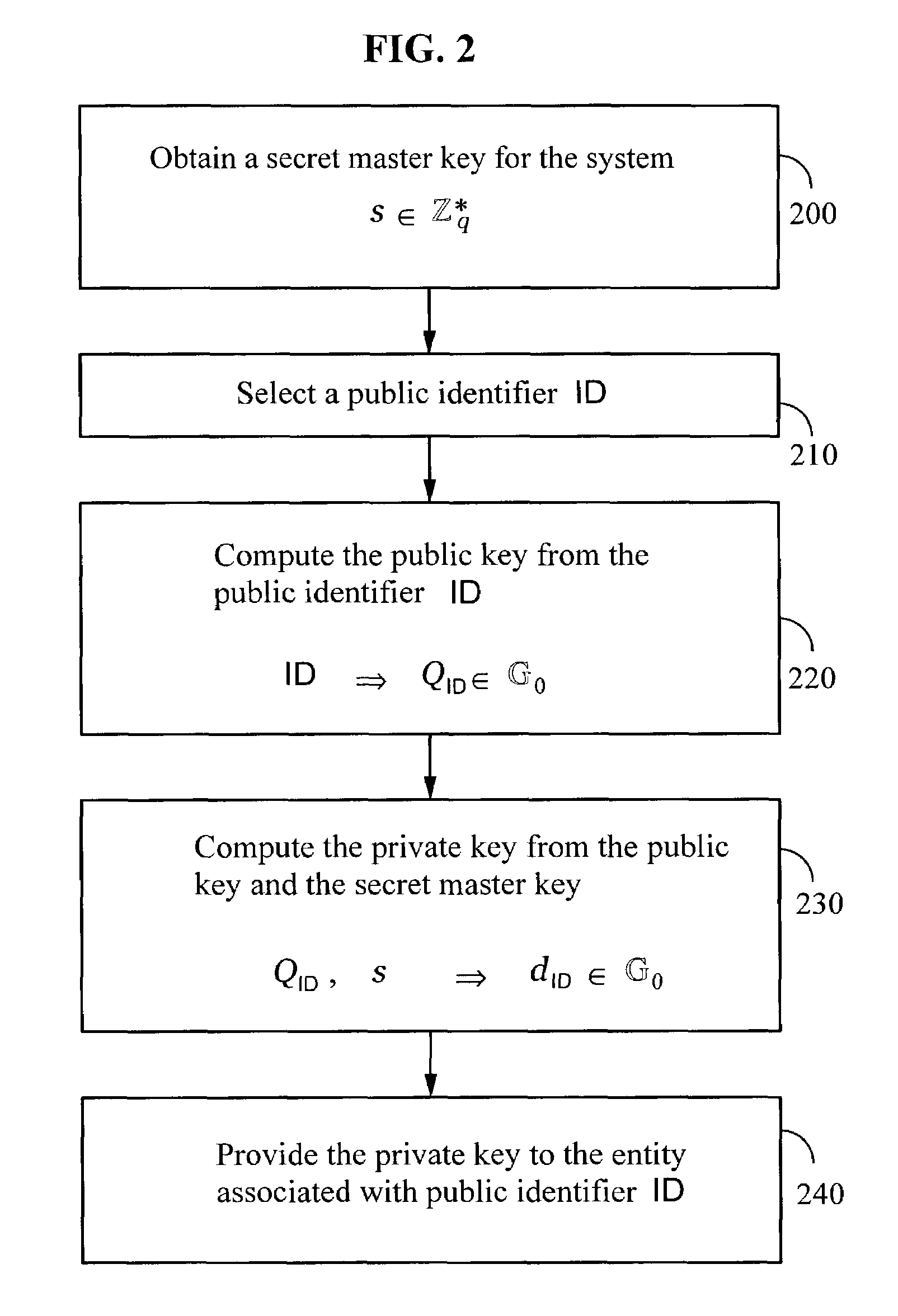
A method and system for encrypting a first piece of information M to be sent by a sender [100] to a receiver [110] allows both sender and receiver to compute a secret message key using identity-based information and a bilinear map. In a one embodiment, the sender [100] computes an identity-based encryption key from an identifier ID associated with the receiver [110]. The identifier ID may include various types of information such as the receiver's e-mail address, a receiver credential, a message identifier, or a date. The sender uses a bilinear map and the encryption key to compute a secret message key gIDr, which is then used to encrypt a message M, producing ciphertext V to be sent from the sender [100] to the receiver [110] together with an element rP. An identity-based decryption key dID is computed by a private key generator [120] based on the ID associated with the receiver and a secret master key s. After obtaining the private decryption key from the key generator [120], the receiver [110] uses it together with the element rP and the bilinear map to compute the secret message key gIDr, which is then used to decrypt V and recover the original message M. According to one embodiment, the bilinear map is based on a Weil pairing or a Tate pairing defined on a subgroup of an elliptic curve. Also described are several applications of the techniques, including key revocation, credential management, and return receipt notification.
Owner:THE BOARD OF TRUSTEES OF THE LELAND STANFORD JUNIOR UNIV +1
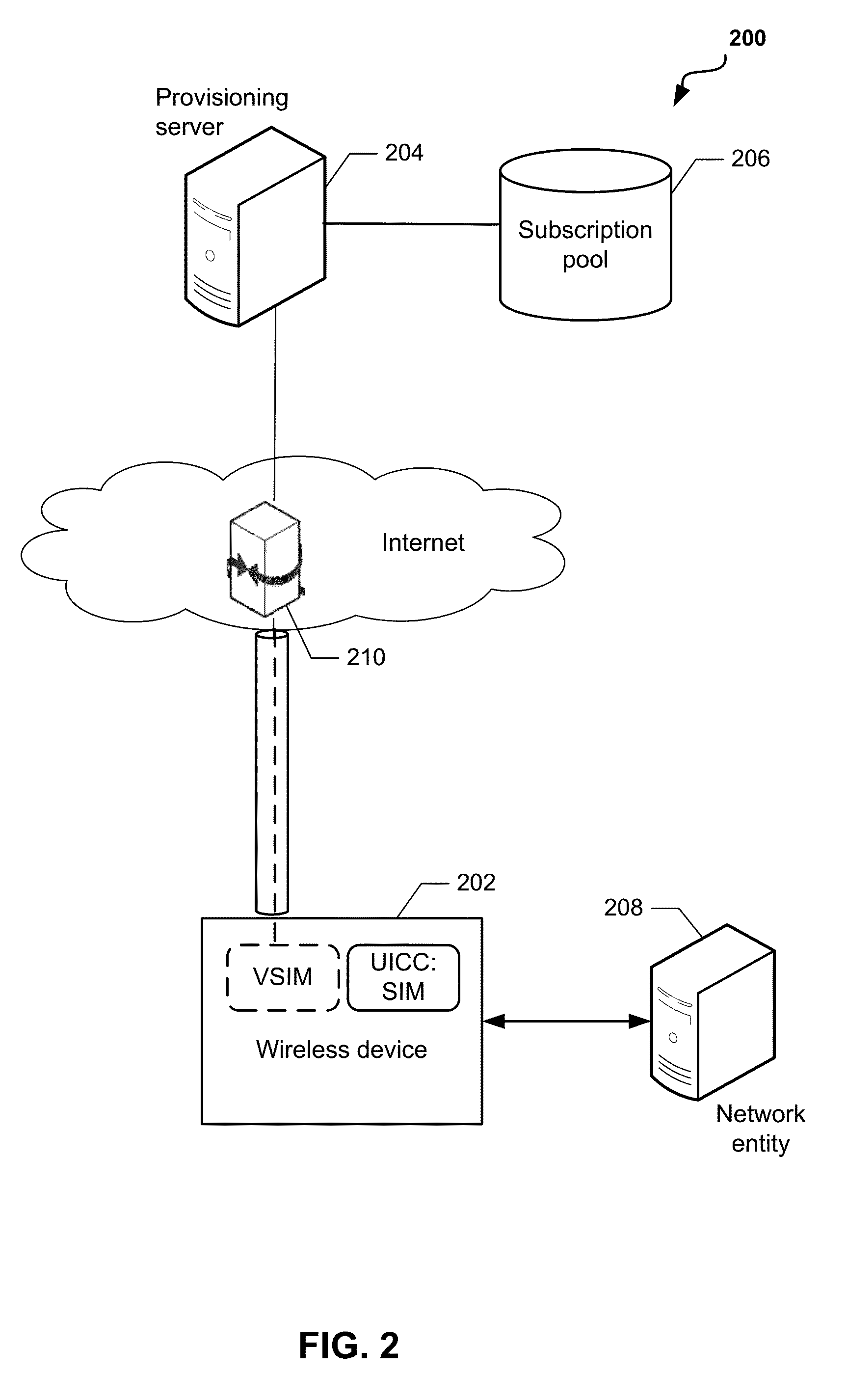
System and Methods for Dynamic SIM Provisioning on a Dual-SIM Wireless Communication Device
ActiveUS20150304506A1Accounting/billing servicesSecurity arrangementComputer hardwareCredential management
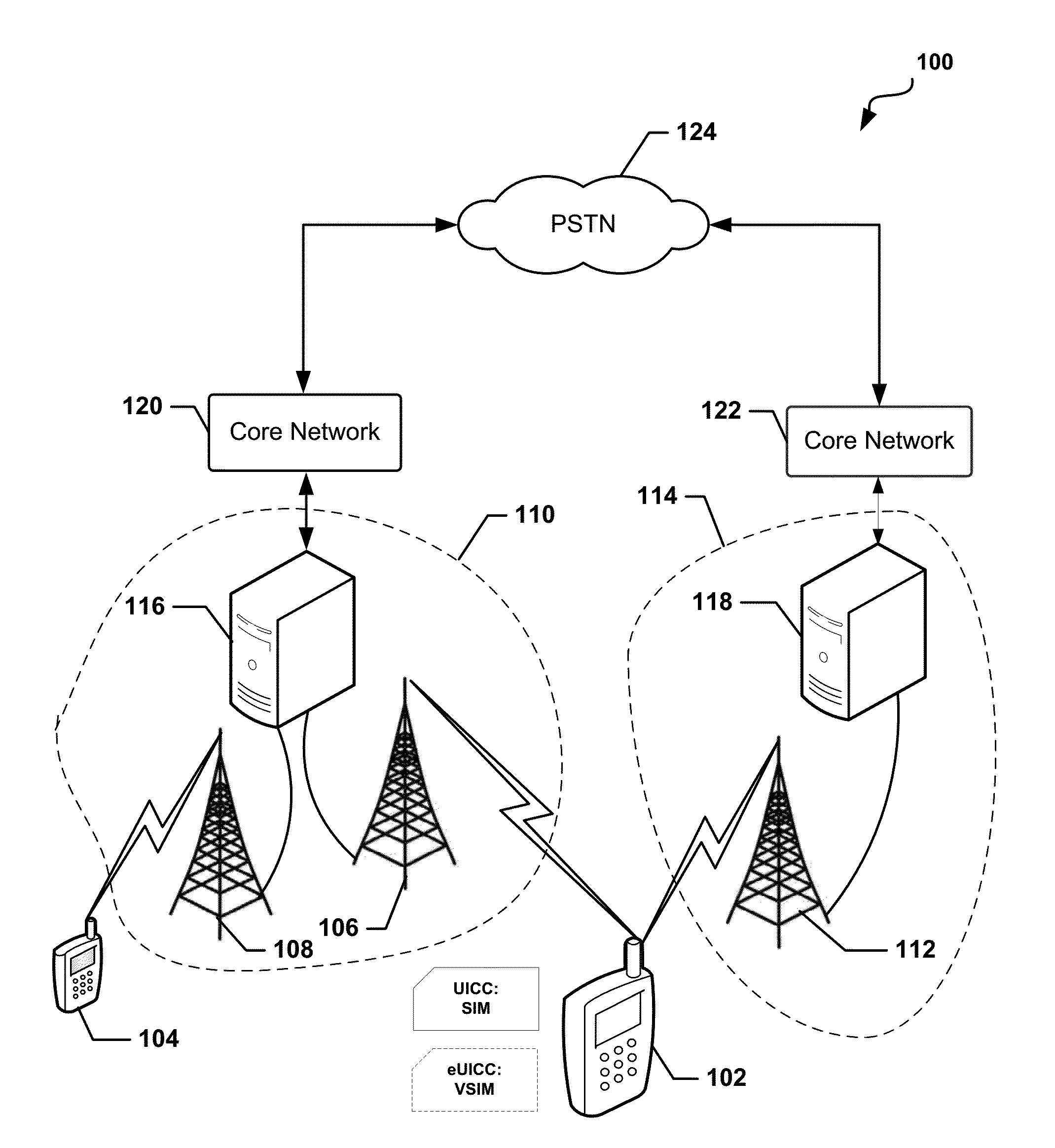
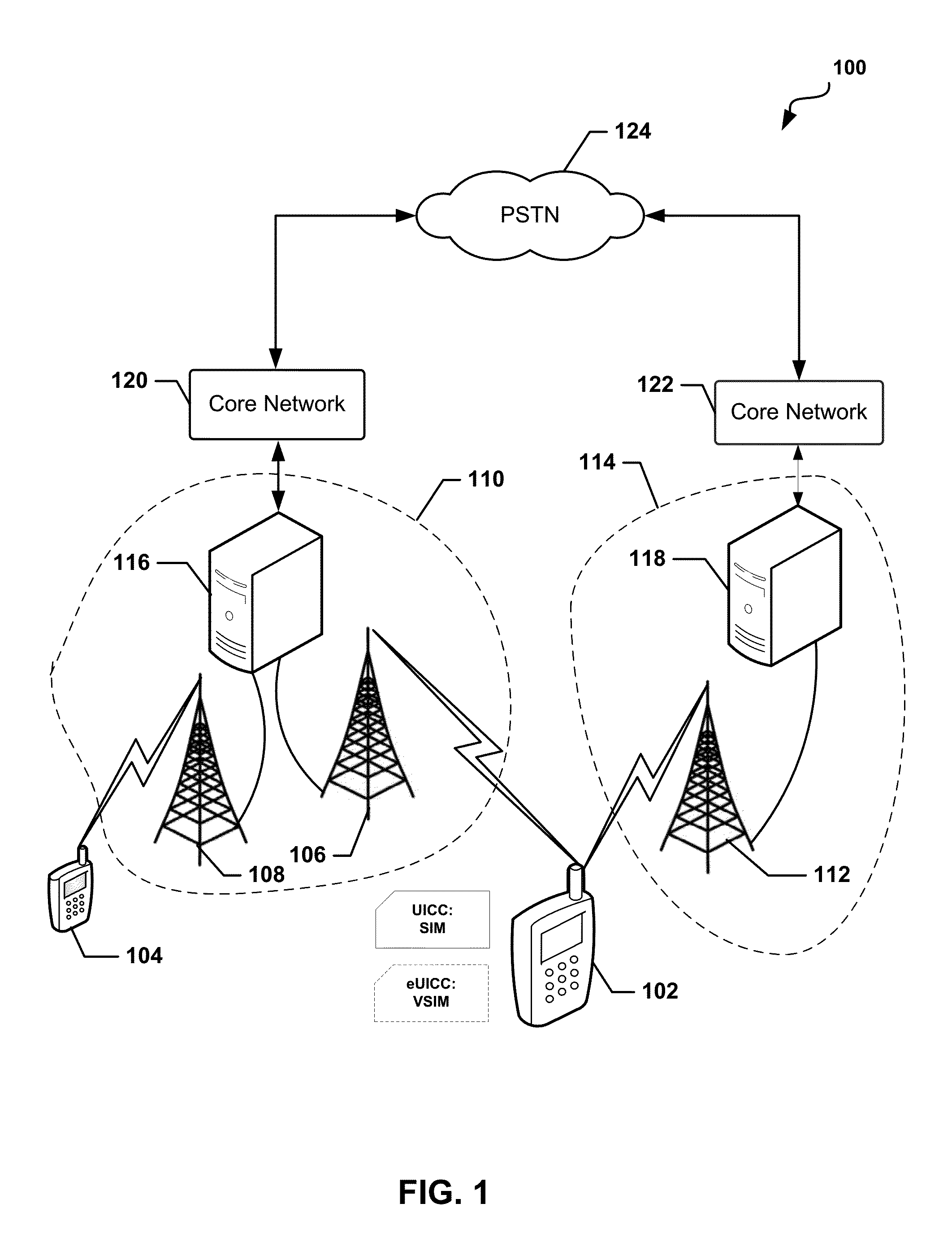
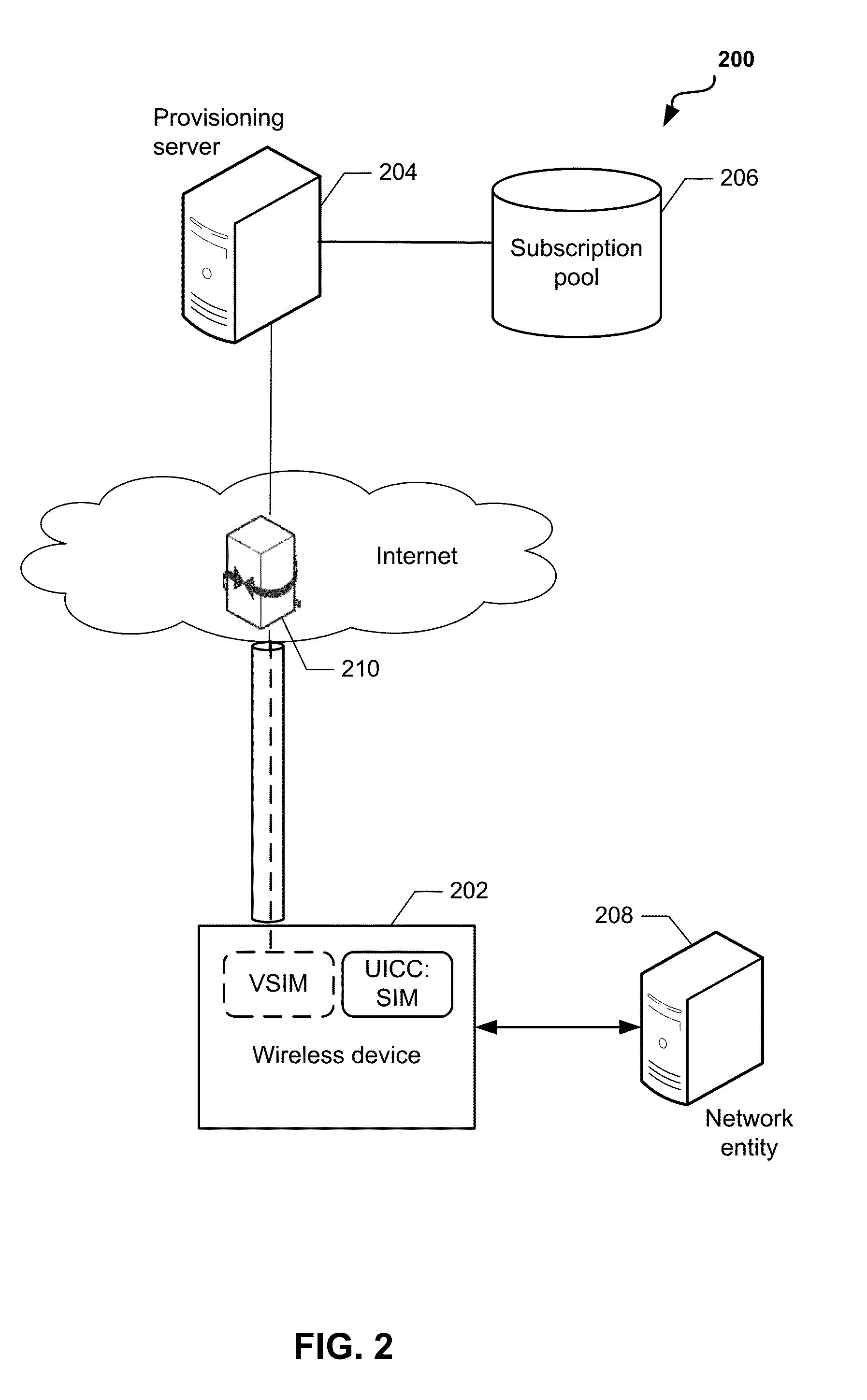
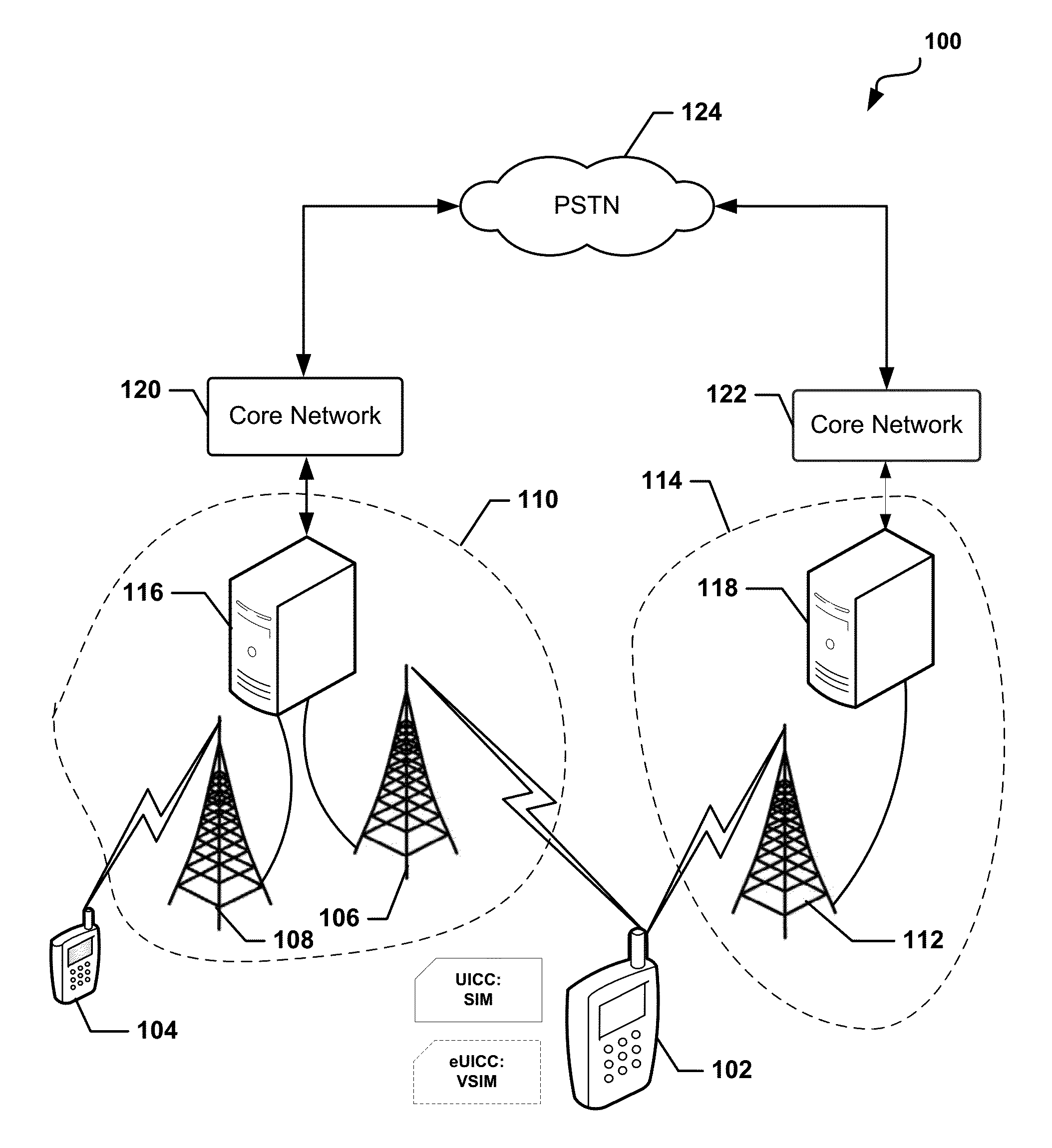
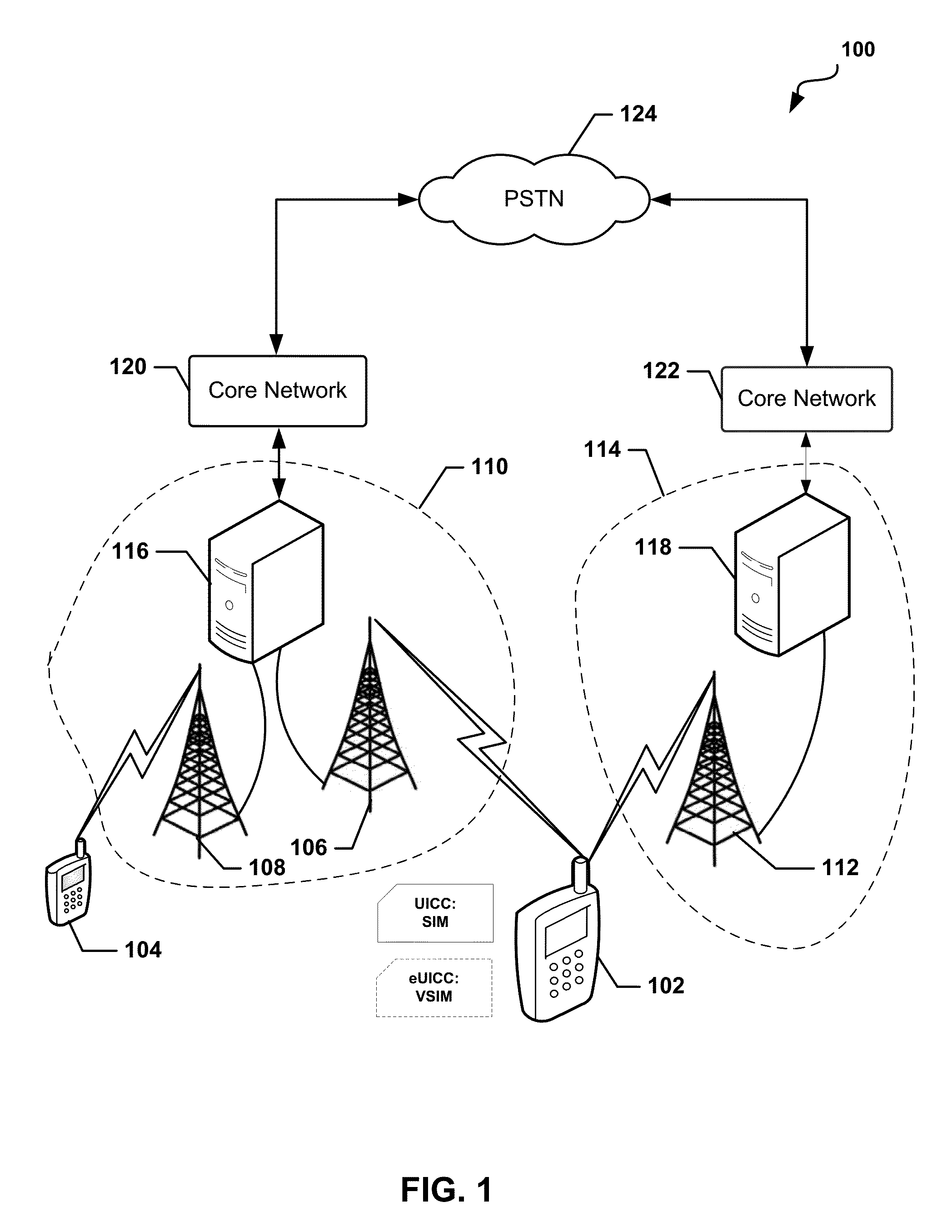
Methods and devices for dynamic VSIM provisioning on a multi-SIM wireless device having a first SIM as a Universal Integrated Circuit Card (UICC) and a virtual SIM (VSIM). A provisioning server may receive updated information from the wireless device, and based at least partially on the received information, determine whether the SIM profile on the VSIM of the wireless device should be changed. To change the SIM profile, the provisioning server may determine whether remote credential management procedures are enabled. If so, the provisioning server may select a new SIM profile from a plurality of SIM profiles, and provision the new SIM profile in the VSIM using remote credential management procedures. If remote credential management procedures are unavailable, the provisioning server may select a remote SIM from a plurality of remote SIMs associated with the provisioning server, and run the remote SIM to execute authentication processes for the wireless device.
Owner:QUALCOMM INC
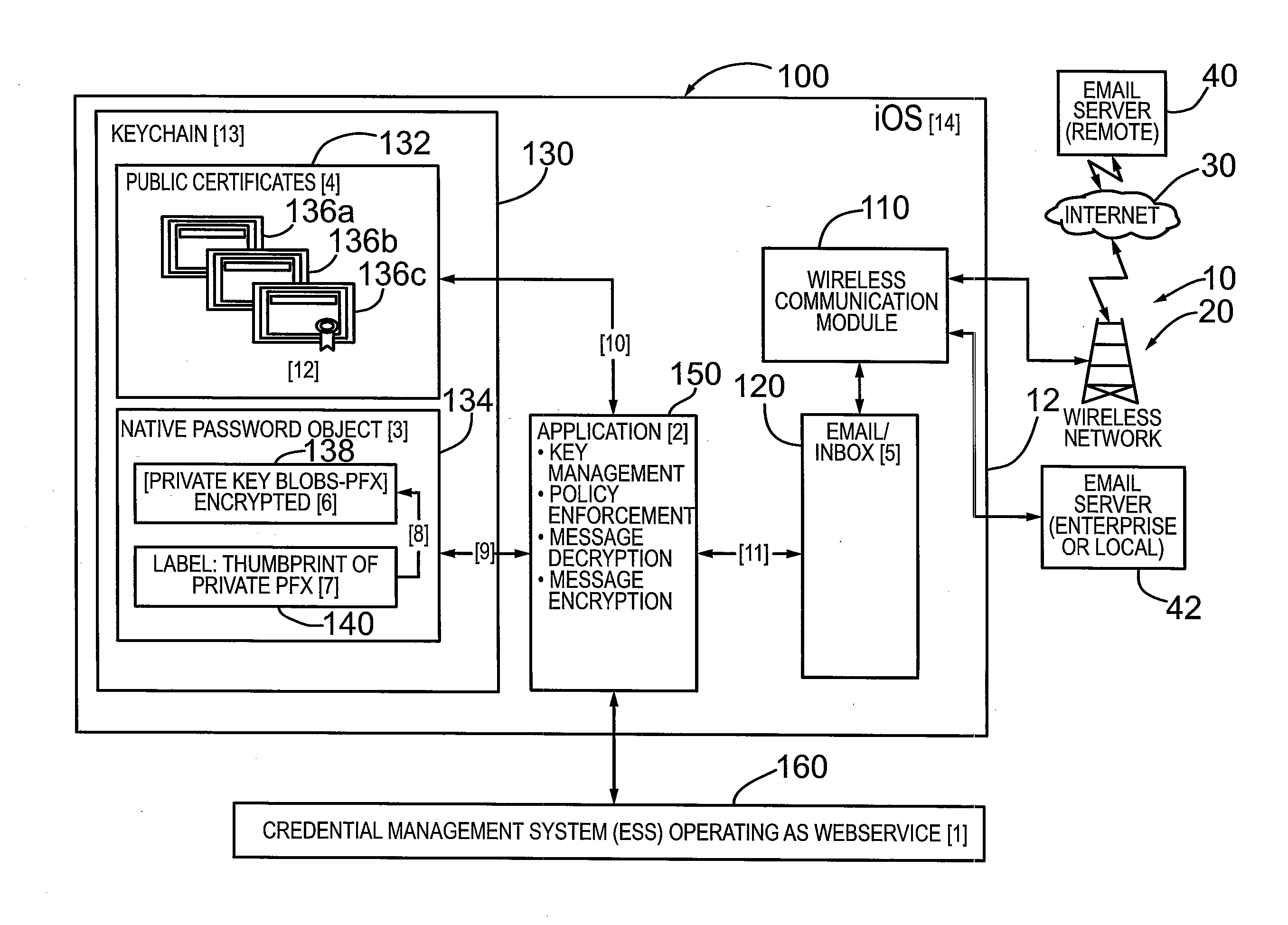
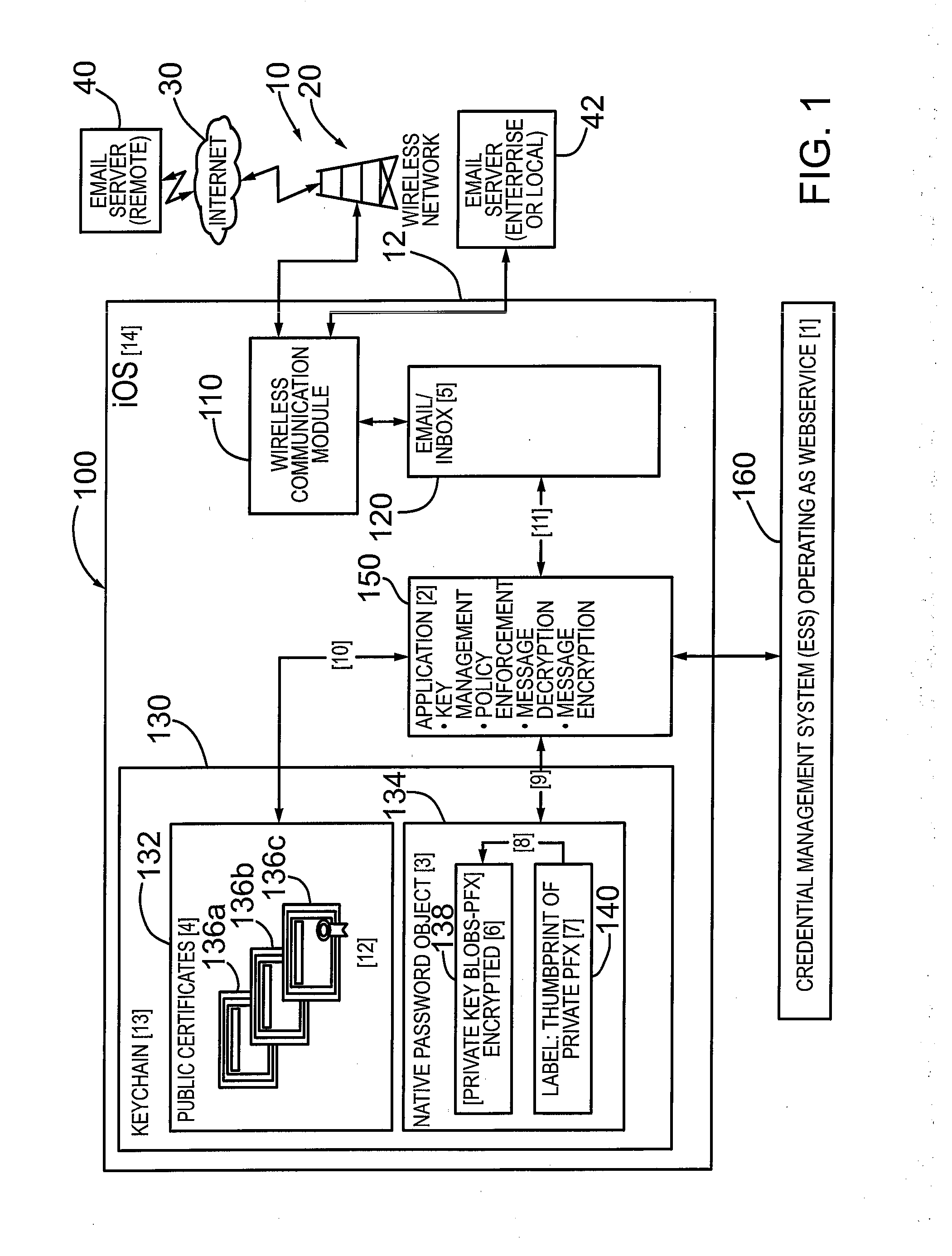
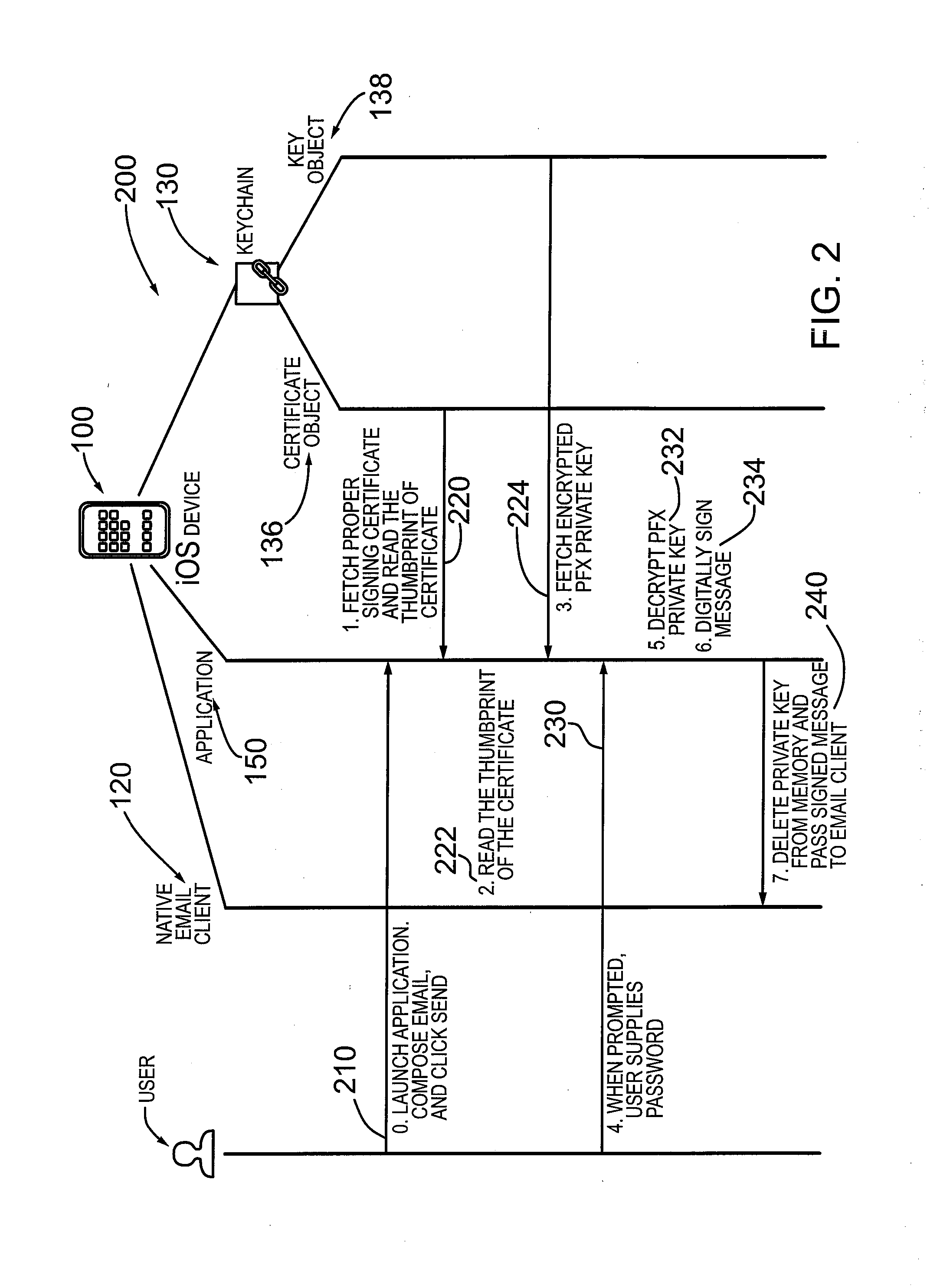
Mechanism and method for managing credentials on ios based operating system
ActiveUS20130024695A1User identity/authority verificationPublic key infrastructure trust modelsOperational systemPassword
A mechanism and method for managing credentials on an electronic device configured with an iOS based operating system. The iOS based device includes a “keychain” configured in device memory. According to an embodiment, the electronic device comprises an application configured to generate a public certificate object in the keychain and a password object in the keychain. The public certificate object is configured to store a public certificate, and the password object is configured to store a private key. The password object further includes a label or thumbprint for associating the private key with the corresponding public certificate. According to an embodiment, the application stores the private key in an encrypted container in the password object to provide an additional layer of security. The application is configured to unlock the encrypted container utilizing a password provided the user. According to a further aspect, the user password is not stored in memory on the device. According to an embodiment, the private key is generated and provided by a credential management system operatively coupled to the electronic device for digitally signing an email message.
Owner:ECHOWORX CORP
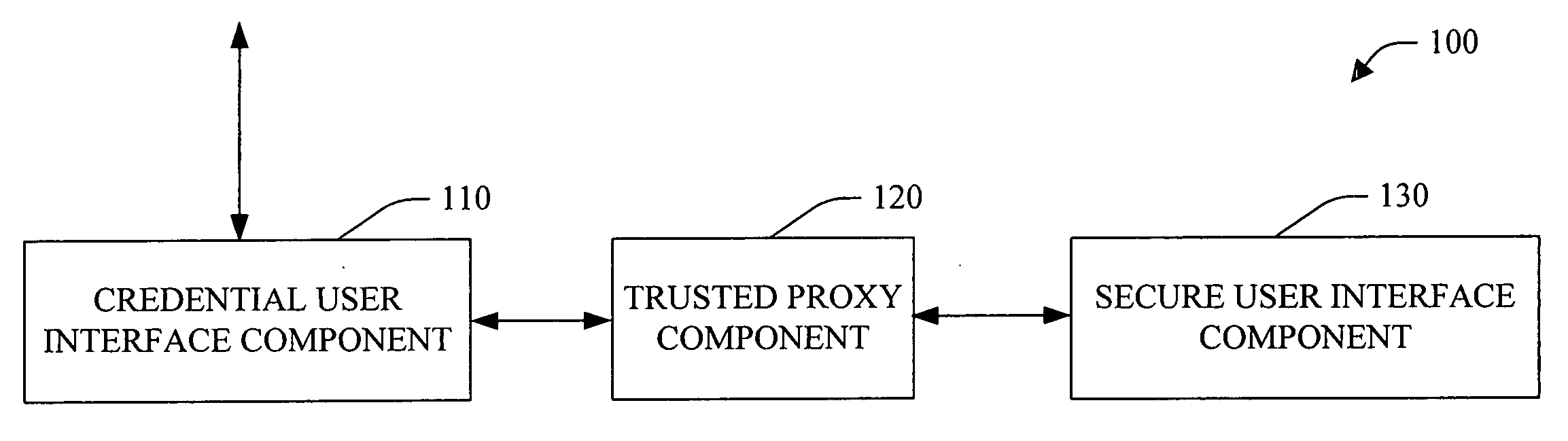
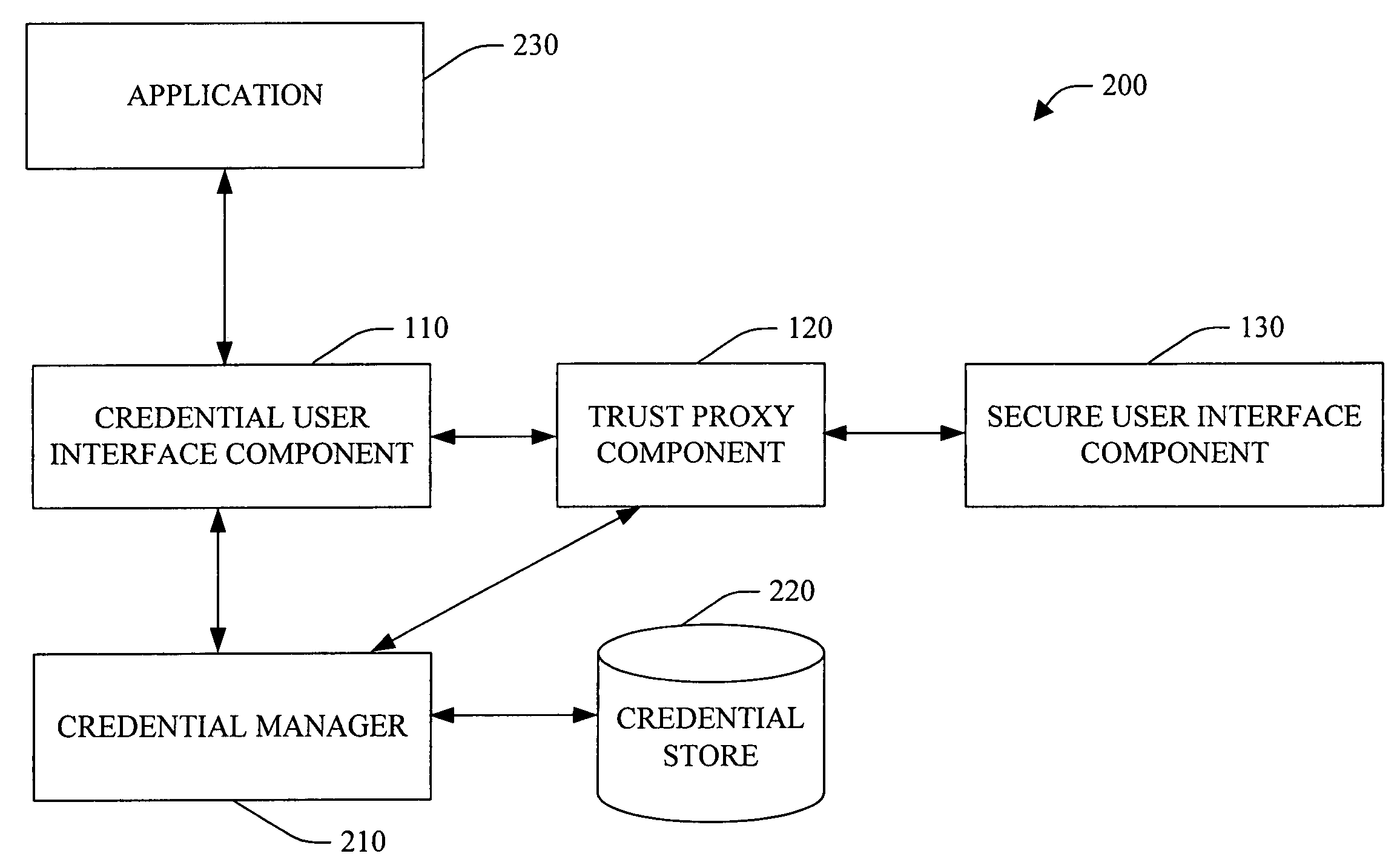
System and method facilitating secure credential management
ActiveUS20050188210A1Safety managementImprove protectionUser identity/authority verificationInternal/peripheral component protectionOperational systemCredential management
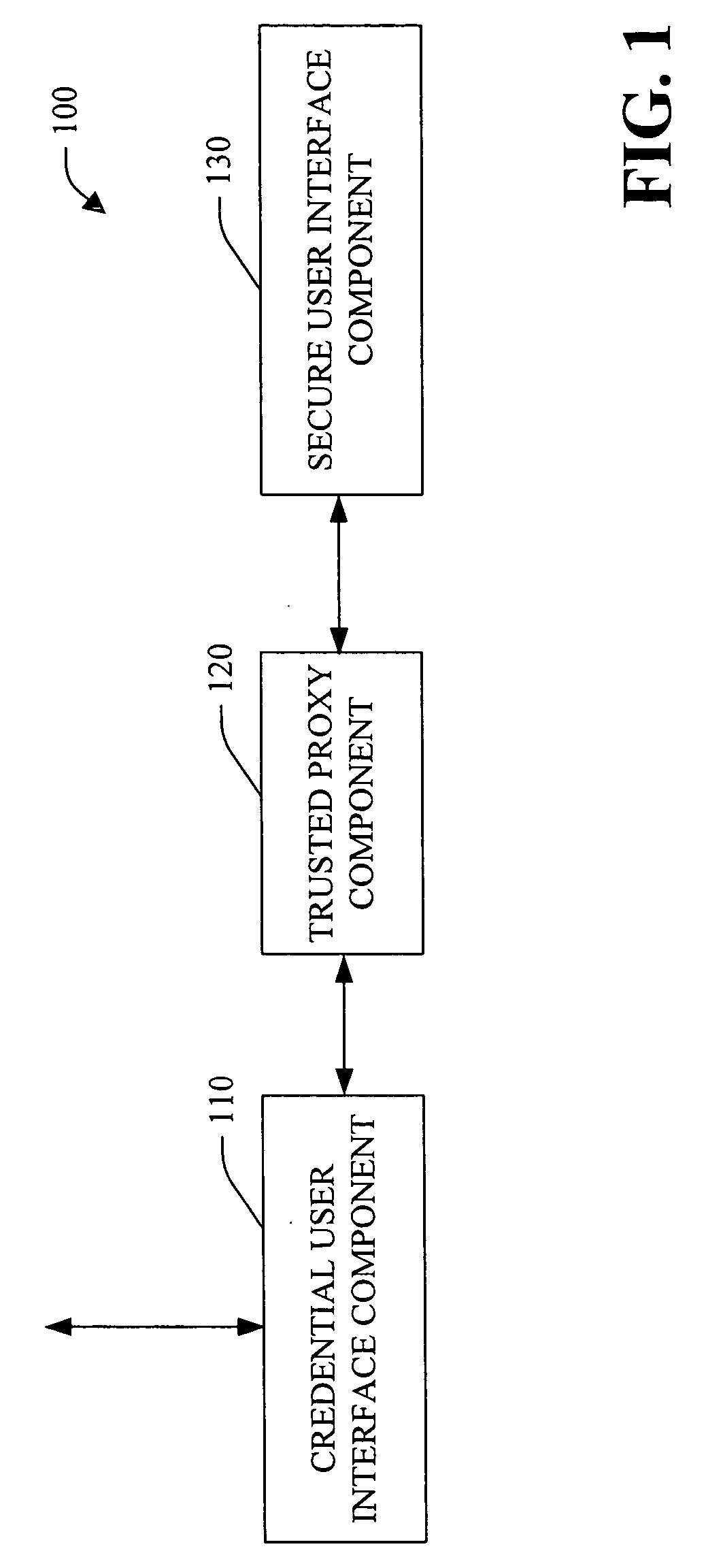
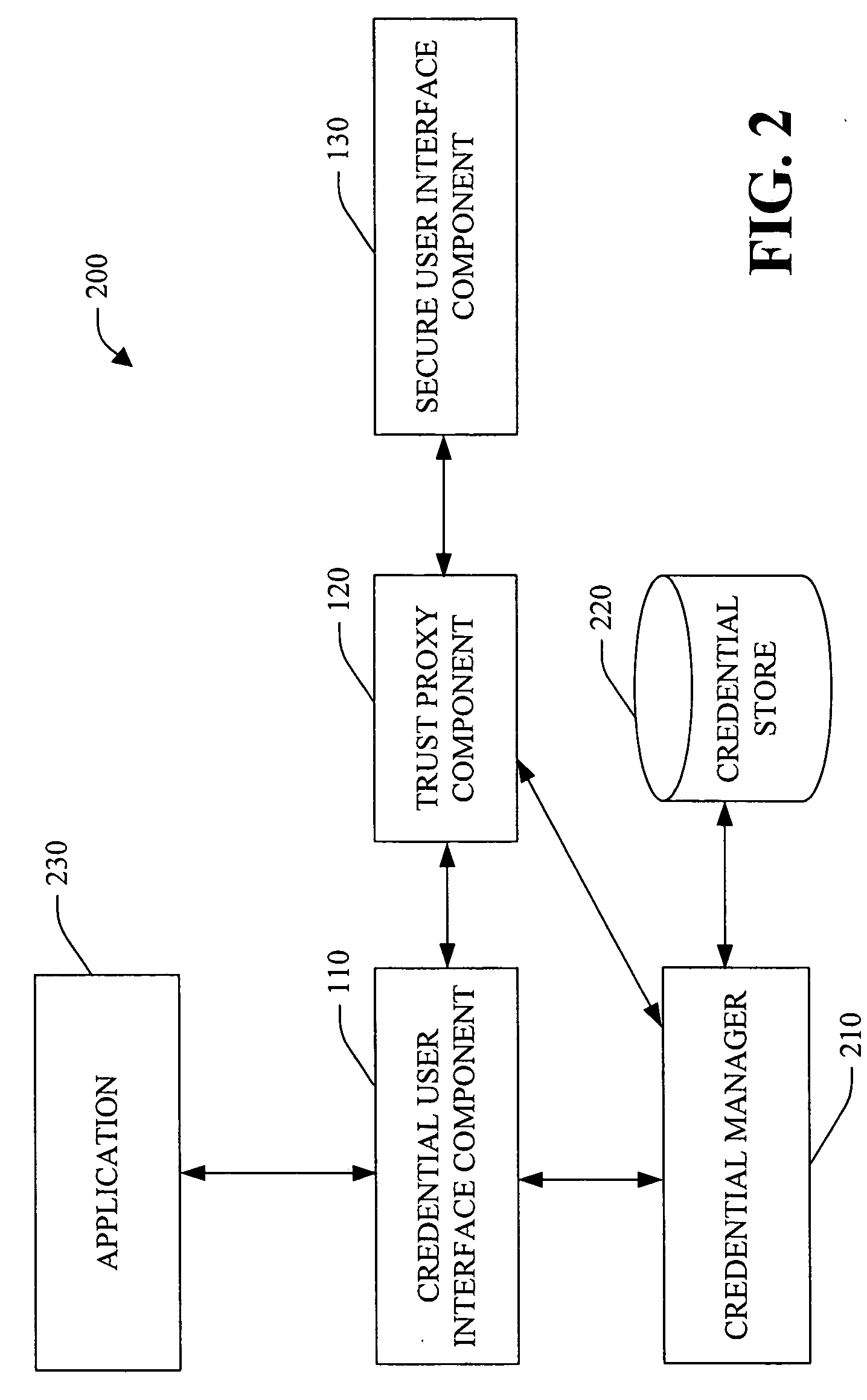
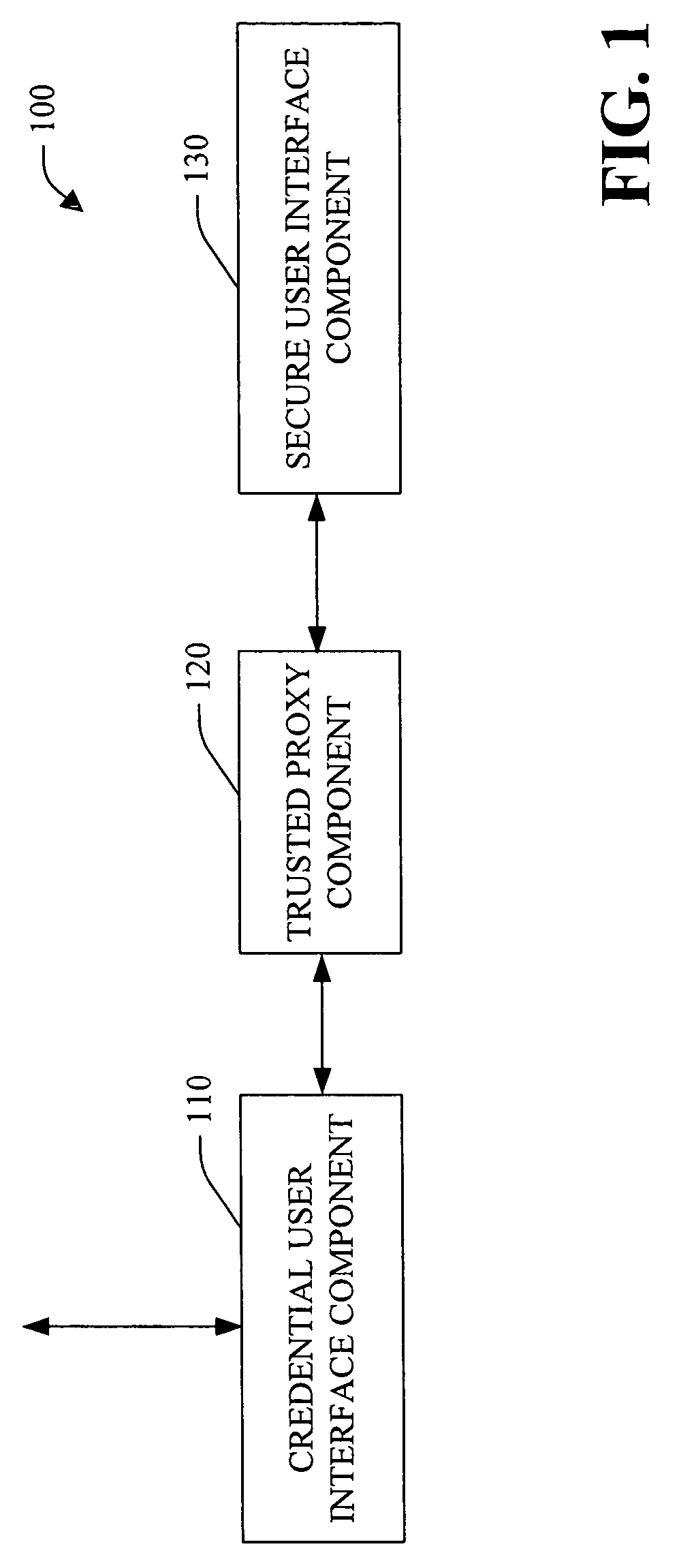
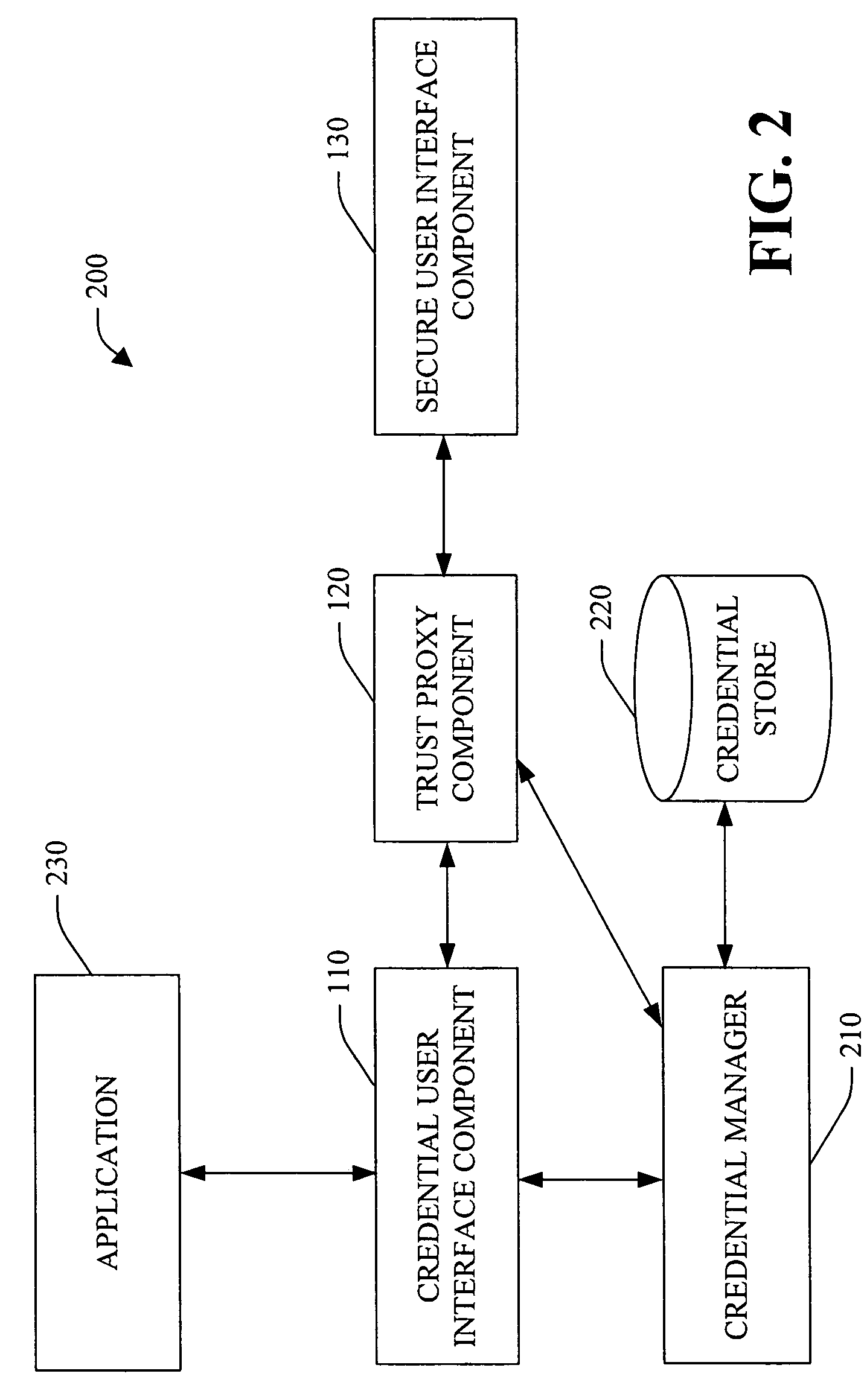
A system and method facilitating secure credential management is provided. An aspect of the present invention provides for a credential management system including a credential user interface component, a trusted proxy component and a secure user interface component. The system can facilitate the secure acquisition, storage and / or application of credential(s) for a user (e.g., when accessing a particular resource) through a secure, isolated environment. For example, the system can be a core building block for operating system component(s) and / or application(s) that handle credential(s) in a secure manner.
Owner:MICROSOFT TECH LICENSING LLC
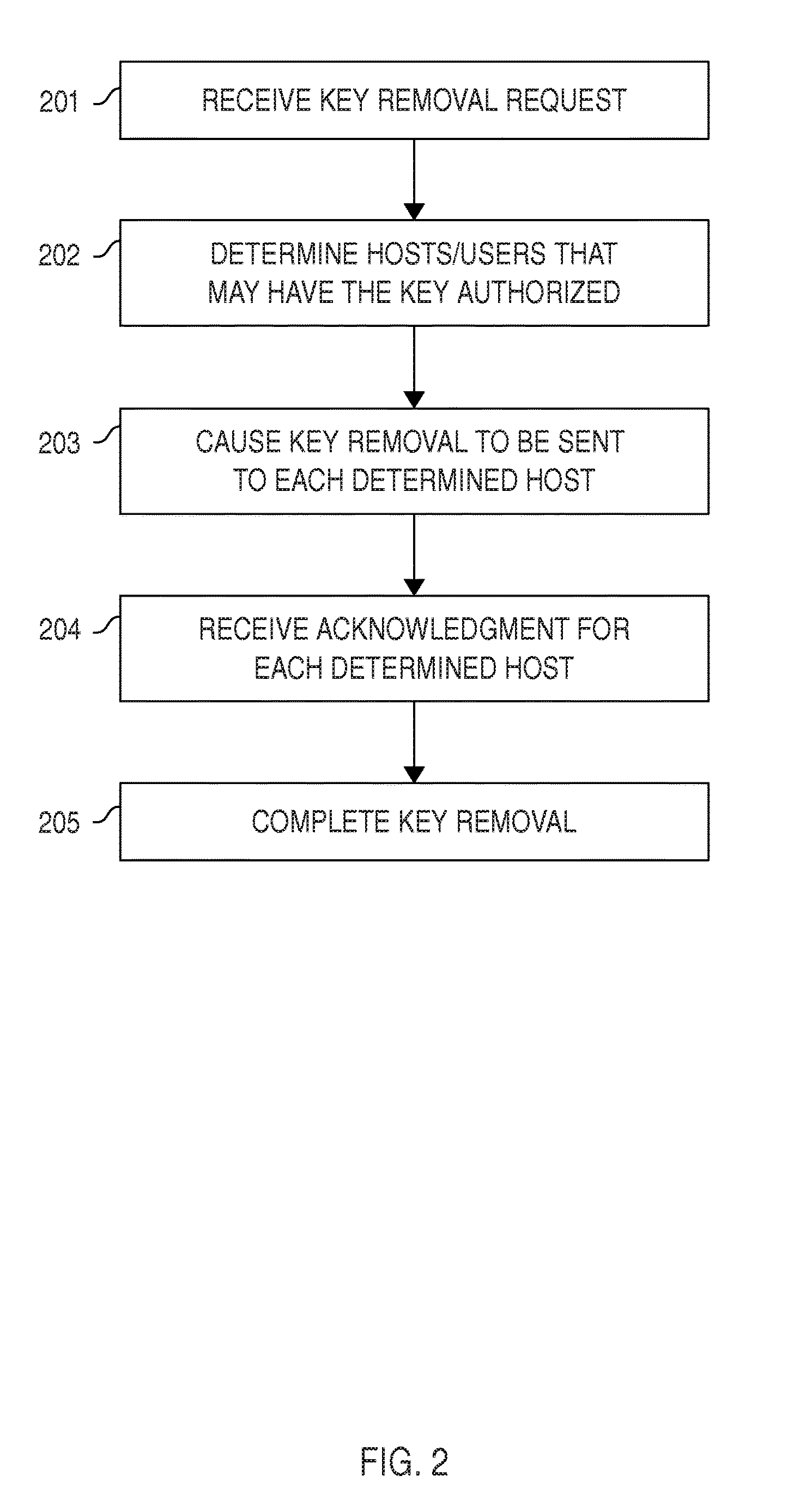
Automated access, key, certificate, and credential management
ActiveUS9515999B2Low costImprove securityKey distribution for secure communicationMultiple keys/algorithms usageCredential managementTrust relationship
Certain embodiments provide means for managing automated access to computers, e.g., using SSH user keys and other kinds of trust relationships. Certain embodiments also provide for managing certificates, Kerberos credentials, and cryptographic keys. Certain embodiments provide for remediating legacy SSH key problems and for automating configuration of SSH keys, as well as for continuous monitoring.
Owner:SSH COMMUNICATIONS SECURITY
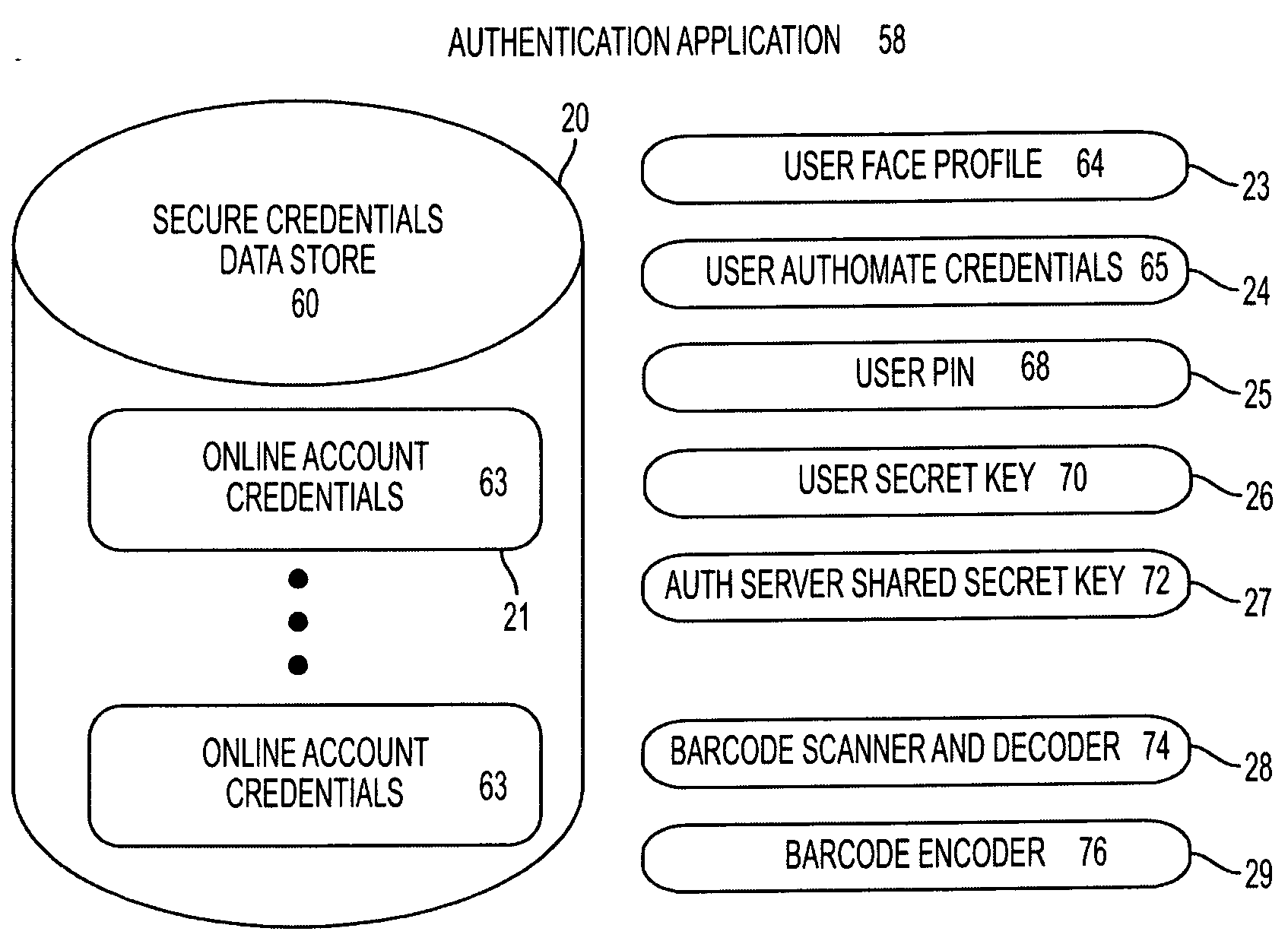
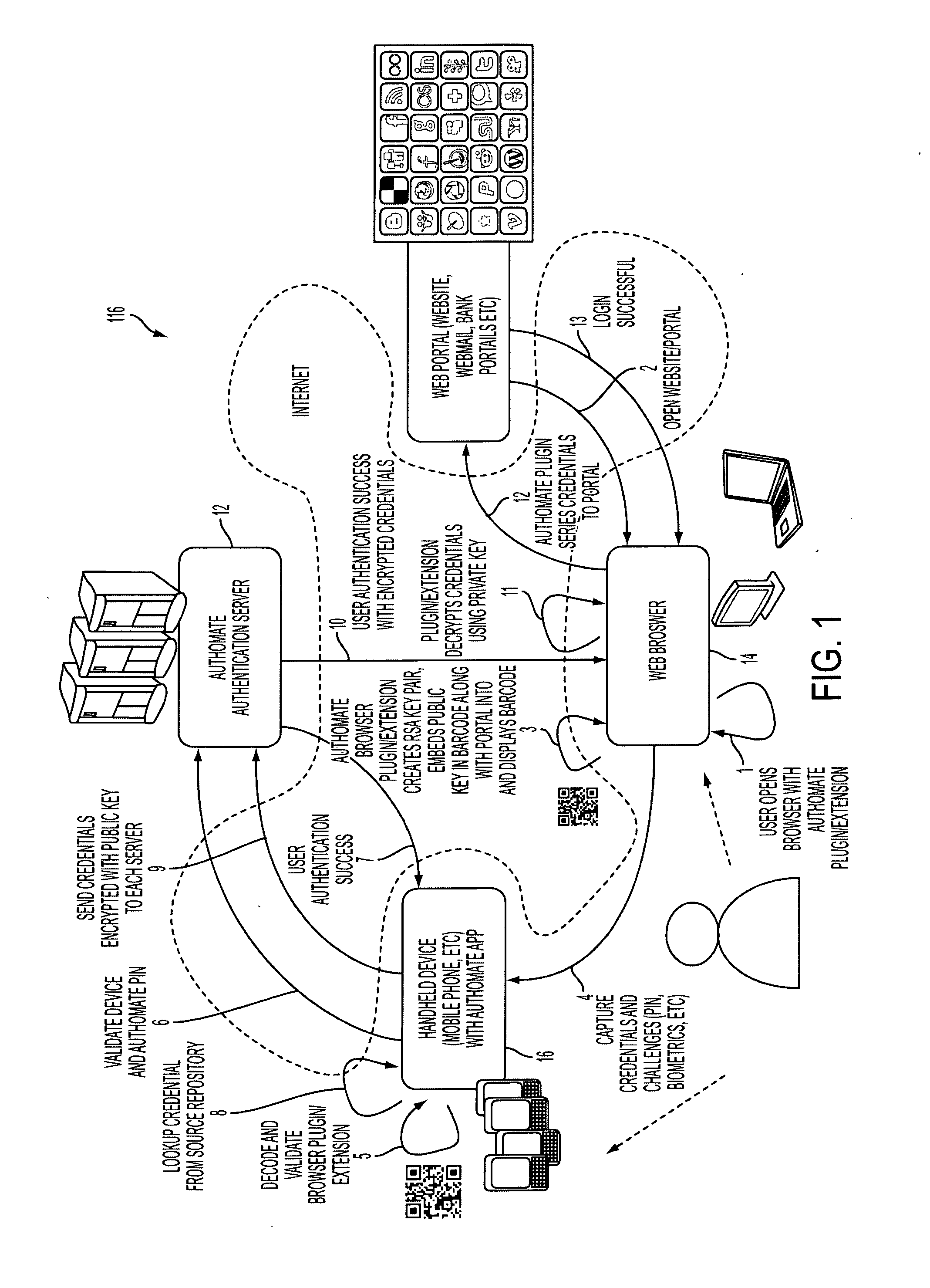
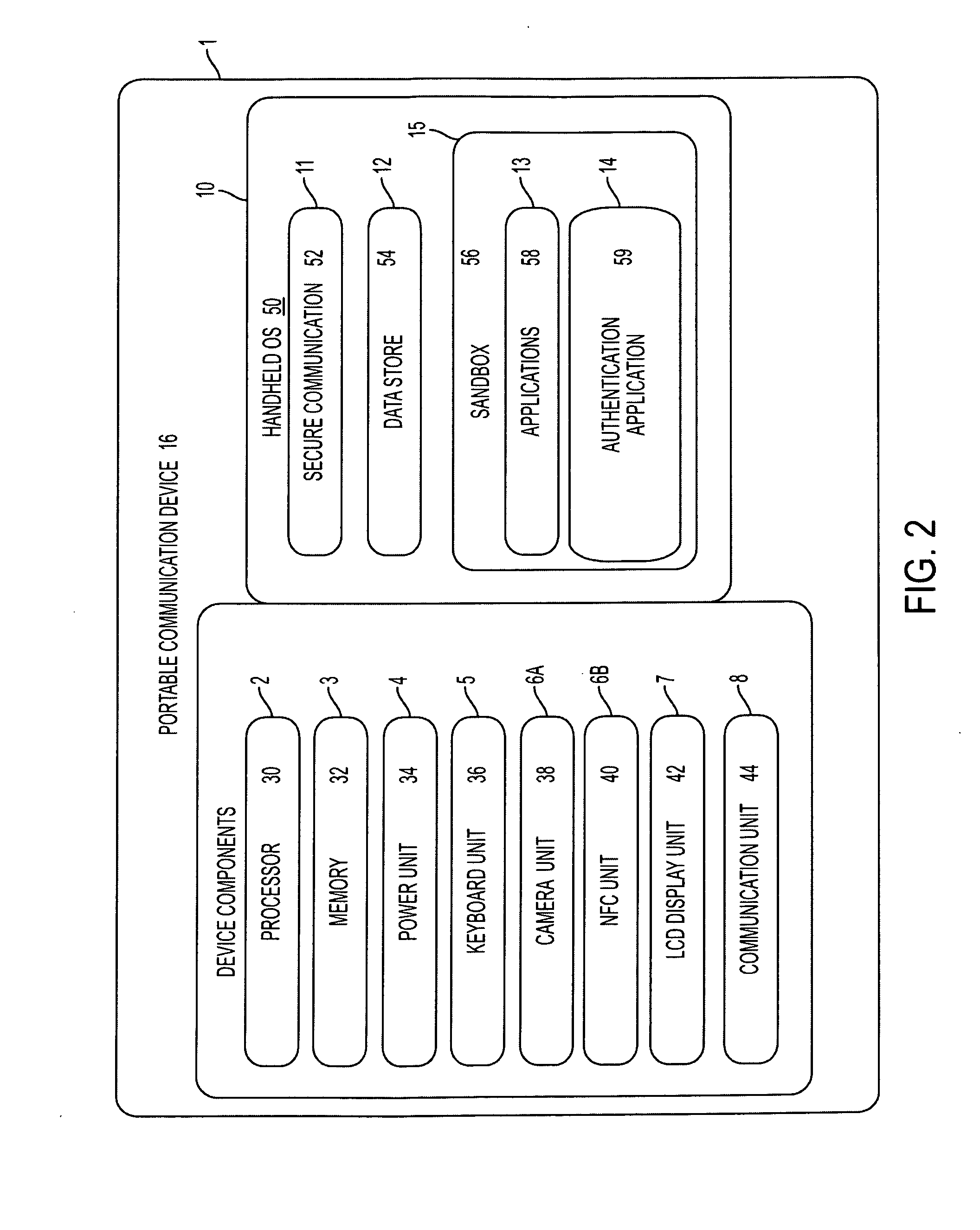
System, design and process for easy to use credentials management for online accounts using out-of-band authentication
ActiveUS20140223175A1Easy to useProtection attackUser identity/authority verificationCoding/ciphering apparatusApplication softwareMulti dimensional
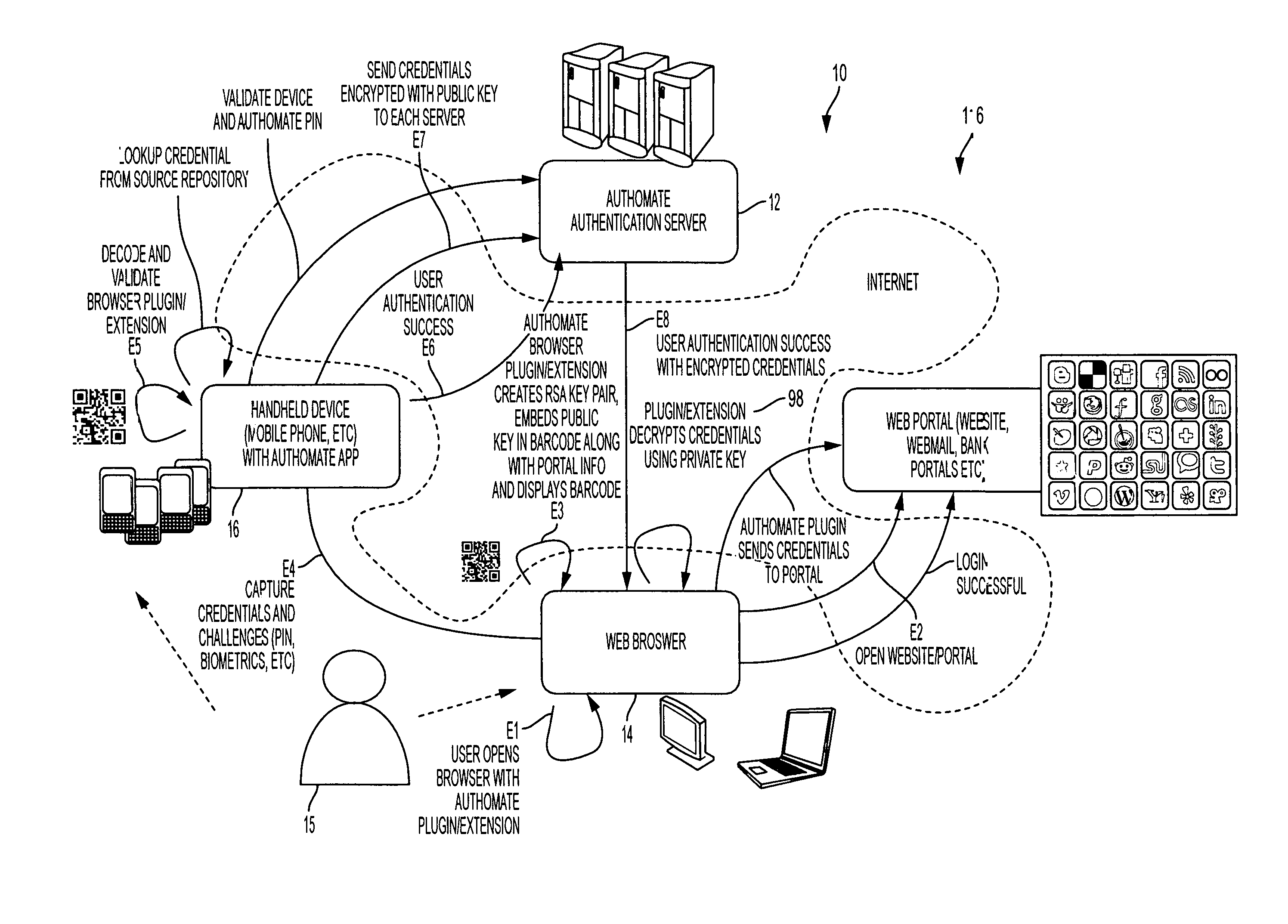
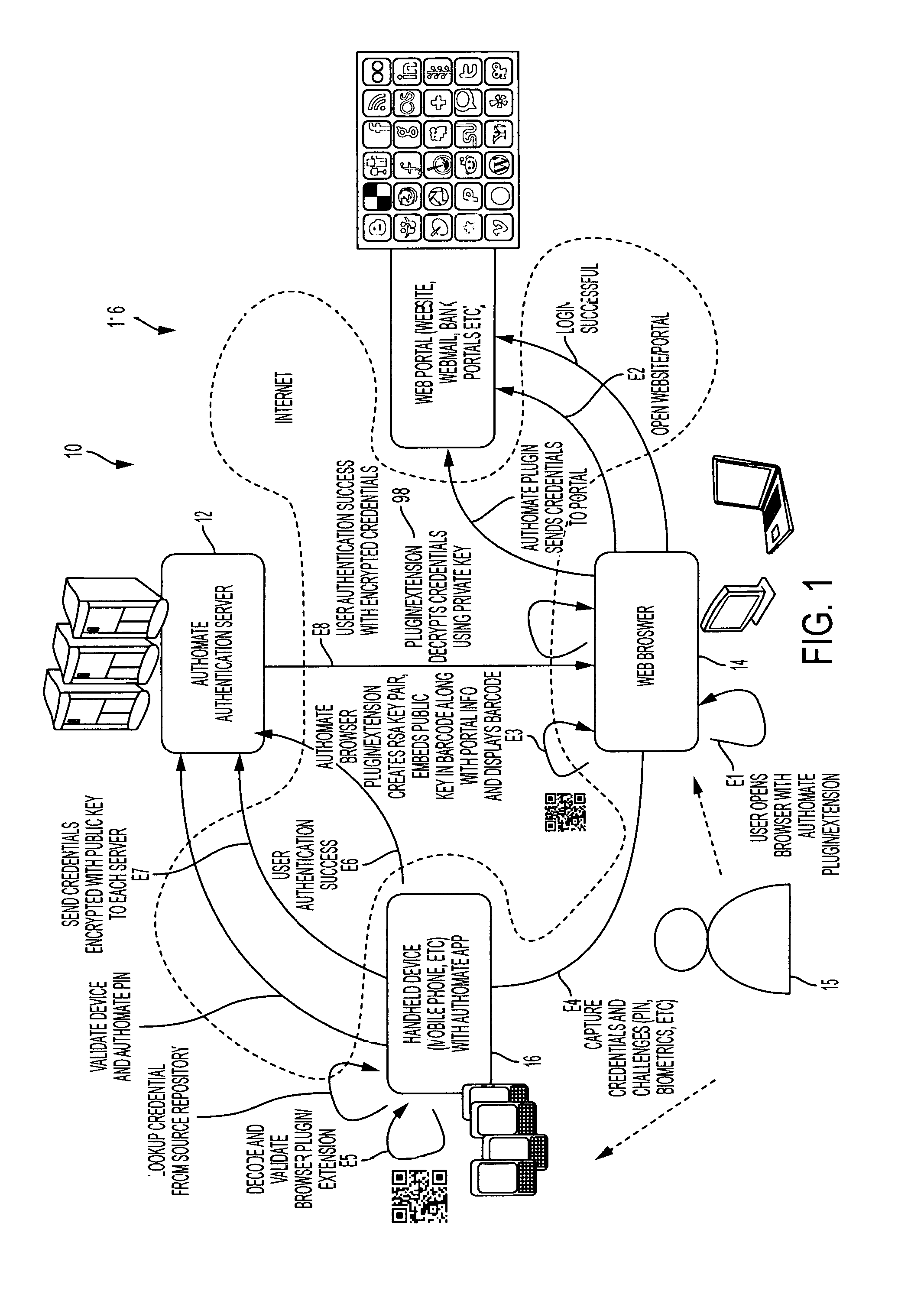
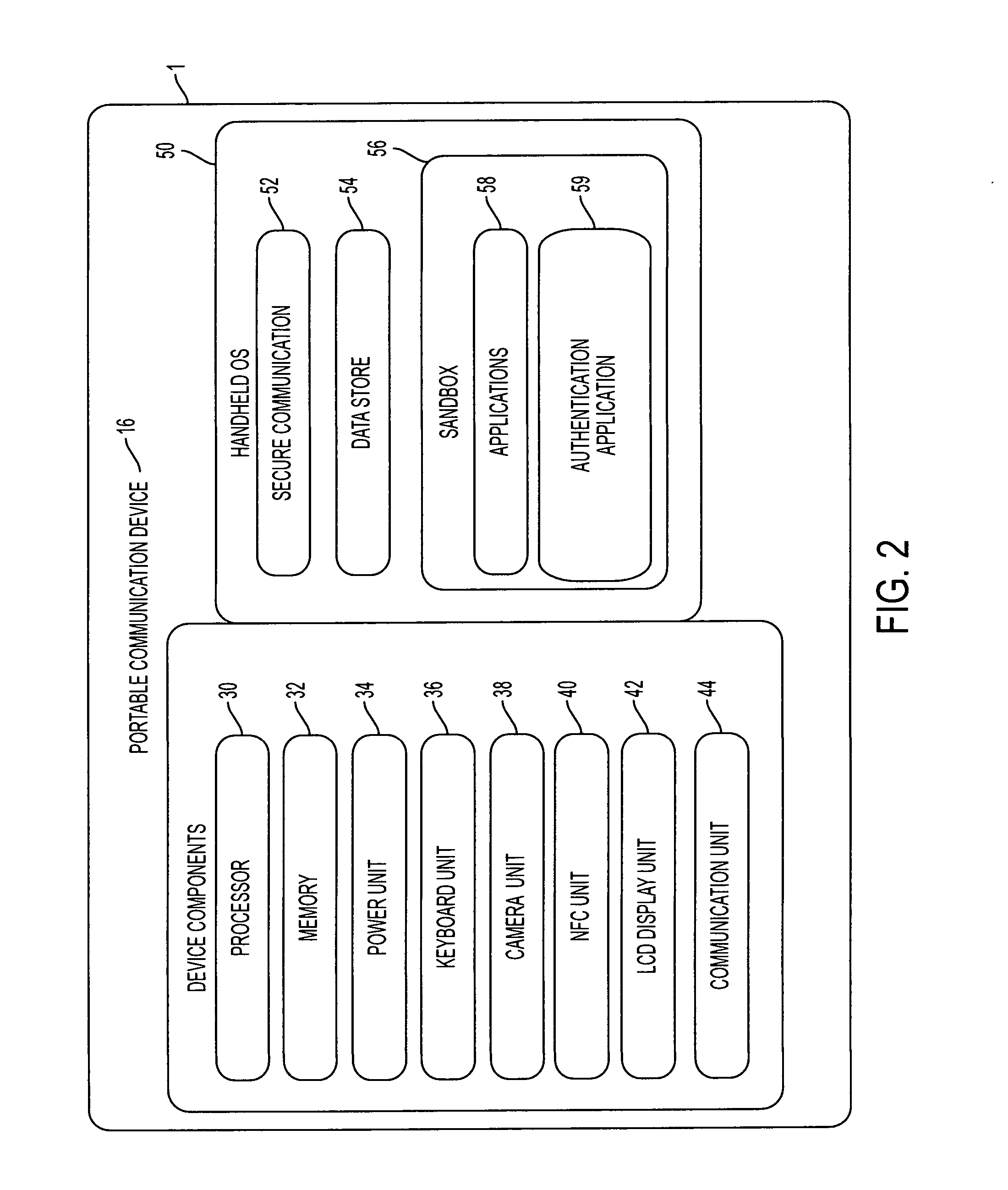
The invention provides an easy to use credential management mechanism for multi-factor out-of-band multi-channel authentication process to protect a large number of documents without the need to remember all the document passwords. When opened, the secure document application generates a multi-dimensional code. The user scans the multi-dimensional code and validates the secure document application and triggers an out-of-band outbound mechanism. The portable mobile device invokes the authentication server to get authenticated. The authentication server authenticates the user based on shared secret key and is automatically allowed access to the secure document. The process of the invention includes an authentication server, a secure document application to generate an authentication vehicle or an embodiment (i.e. multi-dimensional bar code) and handle incoming requests, secret keys and a portable communication device with a smartphone application.
Owner:GCOM IP LLC
Method and apparatus for credential management on a portable device
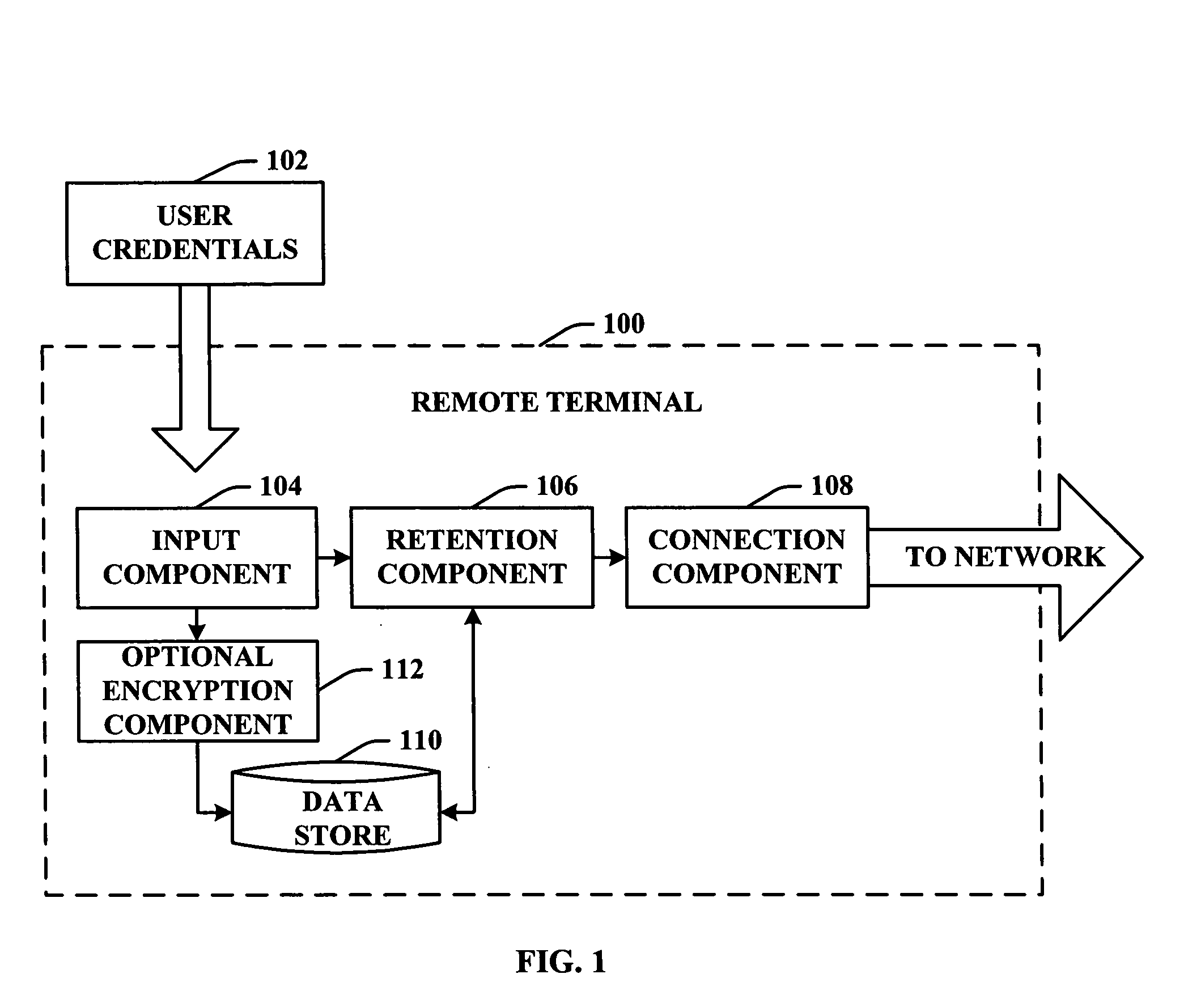
InactiveUS20050278778A1Increase contactOptimize networkDigital data processing detailsUser identity/authority verificationCredential managementData store
A system and / or method that enables a user to manage credential information for approving communications with various network and / or server components. A portable device is provided that facilitates management of a user credential that can be used to connect to a network (e.g., wireless, wired). The portable device includes an input component and a retention component. The input component defines a selected input method to input the user credential into the portable device. The retention component defines a parameter for storing the user credential in accordance with a user-defined selection. Additionally, the portable device can include a data store (e.g., cache memory) that retains the user credential and a purging component configured to subsequently erase the user credential in accordance with the user-defined selection.
Owner:SYMBOL TECH INC
System and method facilitating secure credential management
ActiveUS7783891B2Safety managementImprove protectionUser identity/authority verificationInternal/peripheral component protectionOperational systemCredential management
A system and method facilitating secure credential management is provided. An aspect of the present invention provides for a credential management system including a credential user interface component, a trusted proxy component and a secure user interface component. The system can facilitate the secure acquisition, storage and / or application of credential(s) for a user (e.g., when accessing a particular resource) through a secure, isolated environment. For example, the system can be a core building block for operating system component(s) and / or application(s) that handle credential(s) in a secure manner.
Owner:MICROSOFT TECH LICENSING LLC
System and methods for dynamic SIM provisioning on a dual-SIM wireless communication device
ActiveUS9451098B2Accounting/billing servicesSubstation equipmentComputer hardwareCredential management
Methods and devices for dynamic VSIM provisioning on a multi-SIM wireless device having a first SIM as a Universal Integrated Circuit Card (UICC) and a virtual SIM (VSIM). A provisioning server may receive updated information from the wireless device, and based at least partially on the received information, determine whether the SIM profile on the VSIM of the wireless device should be changed. To change the SIM profile, the provisioning server may determine whether remote credential management procedures are enabled. If so, the provisioning server may select a new SIM profile from a plurality of SIM profiles, and provision the new SIM profile in the VSIM using remote credential management procedures. If remote credential management procedures are unavailable, the provisioning server may select a remote SIM from a plurality of remote SIMs associated with the provisioning server, and run the remote SIM to execute authentication processes for the wireless device.
Owner:QUALCOMM INC
Management of credentials on an electronic device using an online resource
ActiveUS20150350177A1Digital data processing detailsMultiple digital computer combinationsComputer networkResource based
Systems, methods, and computer-readable media for using an online resource to manage credentials on an electronic device are provided. In one example embodiment, a method, at an electronic device, includes, inter alia, receiving account data via an online resource, accessing commerce credential status data from a secure element of the electronic device, providing initial credential management option data via the online resource based on the received account data and based on the accessed commerce credential status data, in response to the providing, receiving a selection of an initial credential management option via the online resource, and changing the status of a credential on the secure element based on the received selection. Additional embodiments are also provided.
Owner:APPLE INC
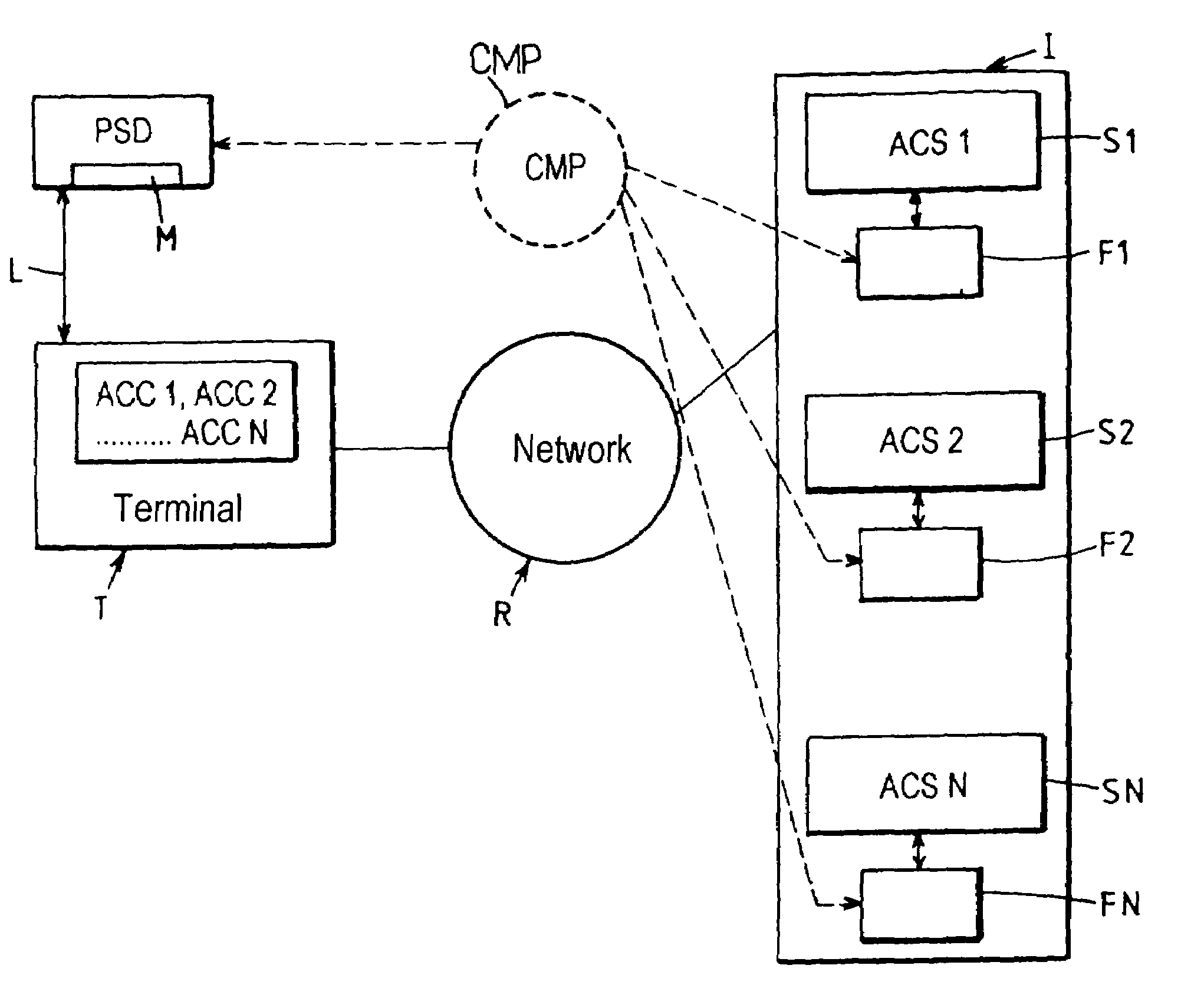
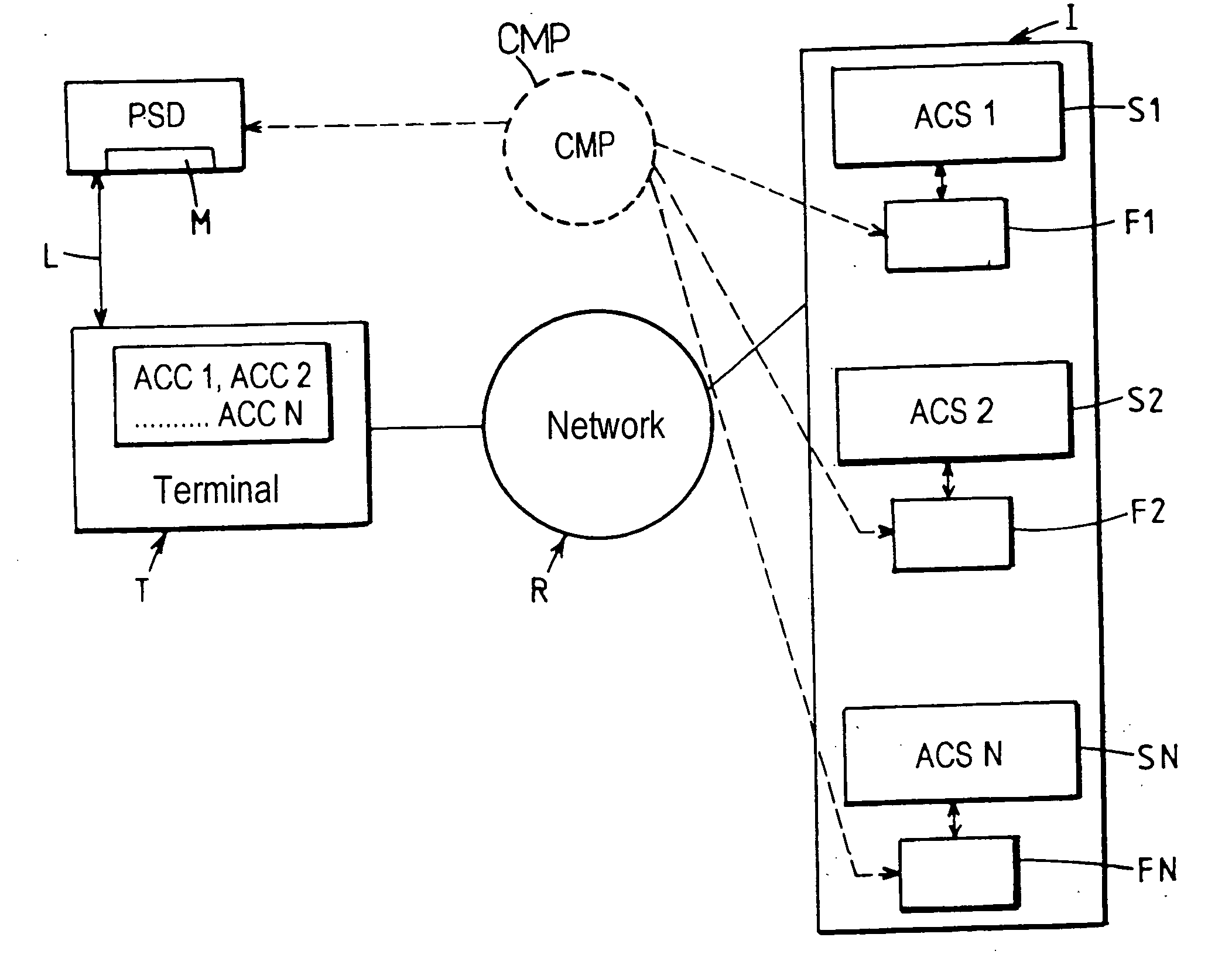
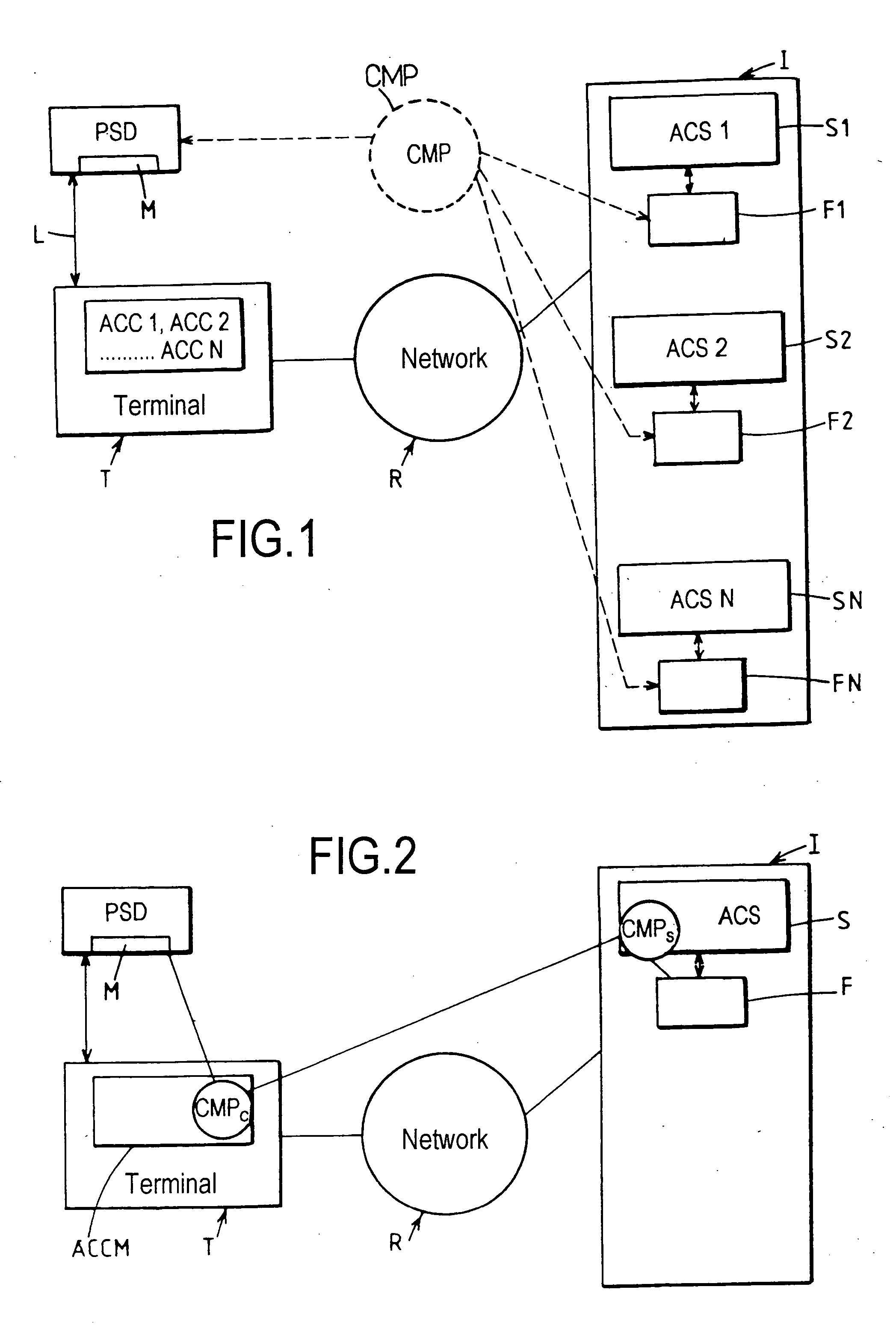
Data processing system for application to access by accreditation
InactiveUS6988210B1Improve securityError detection/correctionVolume/mass flow measurementData processing systemCredential management
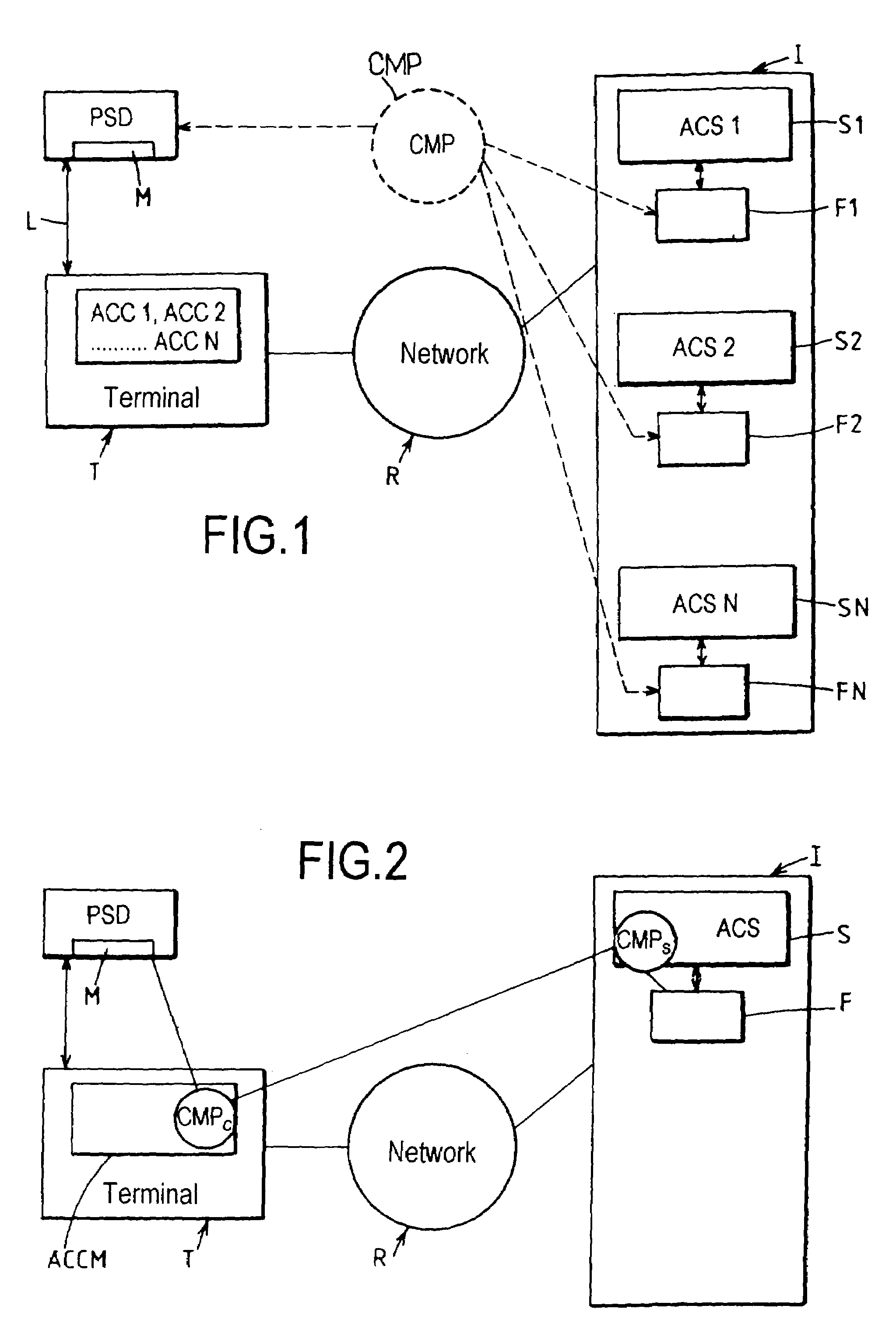
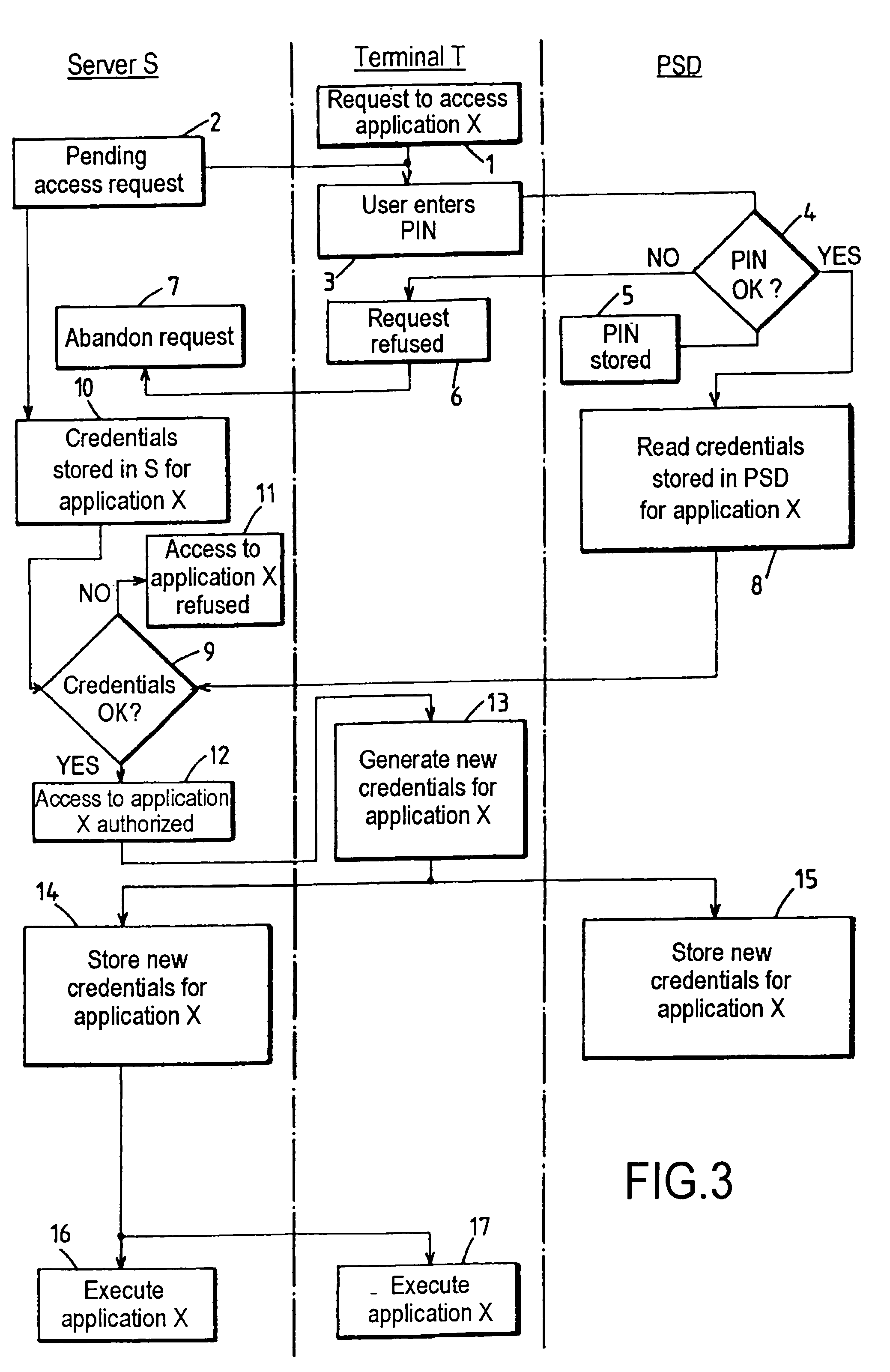
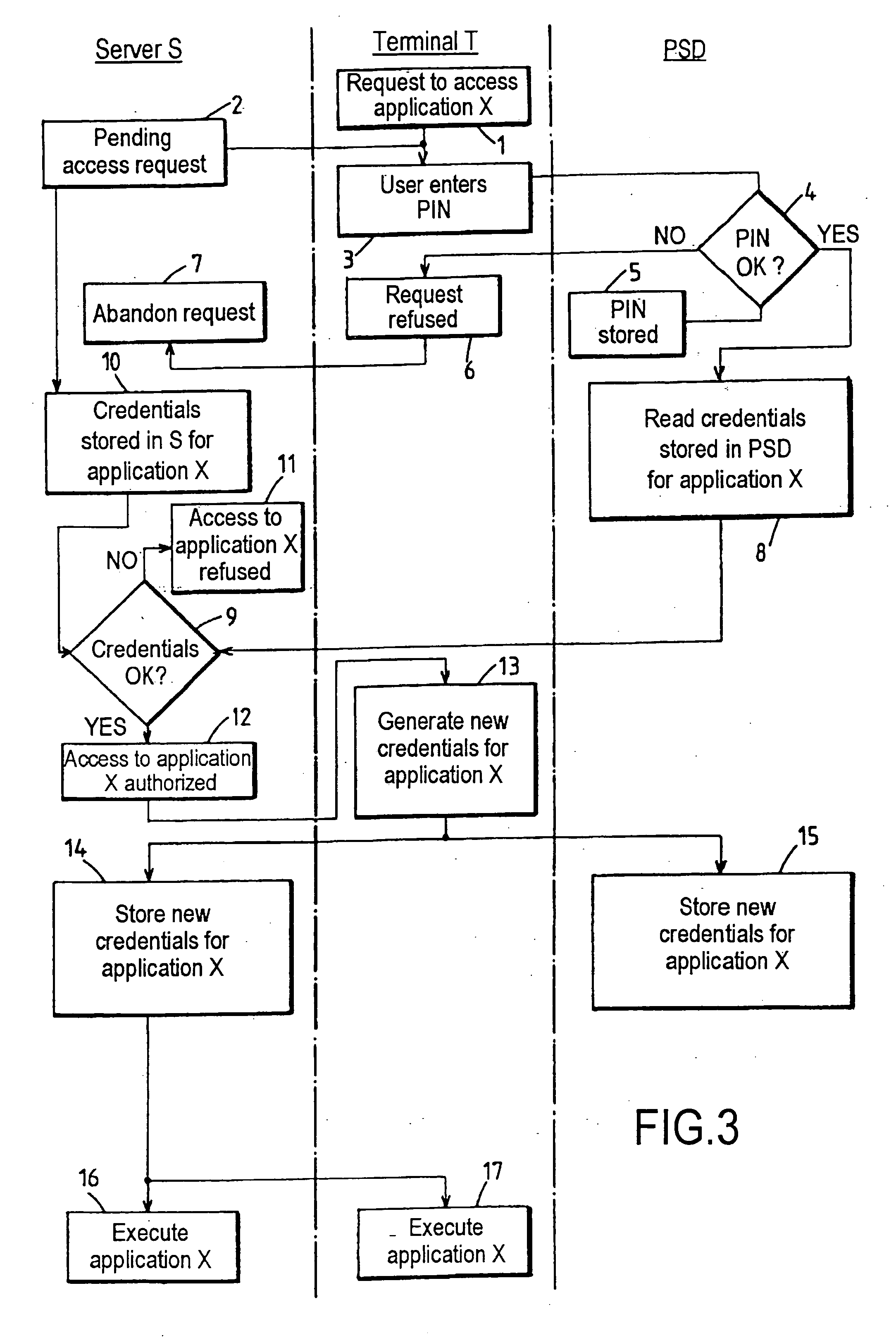
This system for executing a program to which access by a user is controlled by credentials includes a terminal (T), first memory means (F) associated with said program for storing at least first credentials specific to said user, access control means for authorizing access to said program in response to a match between said first credentials and second credentials applied via said terminal, and a security device (PSD) personal to said user, associated with said terminal and including second memory means (M) for secure storage of said second credentials. The terminal (T) includes at least some of credentials management means (CMP) including means for reading said second credentials and transmitting them to said access control means in response to presentation of a request to access said program, and credentials updating means for selectively commanding the generation and loading into said first and second memory means (F, M) of new credentials replacing the credentials previously stored.
Owner:ASSA ABLOY AB
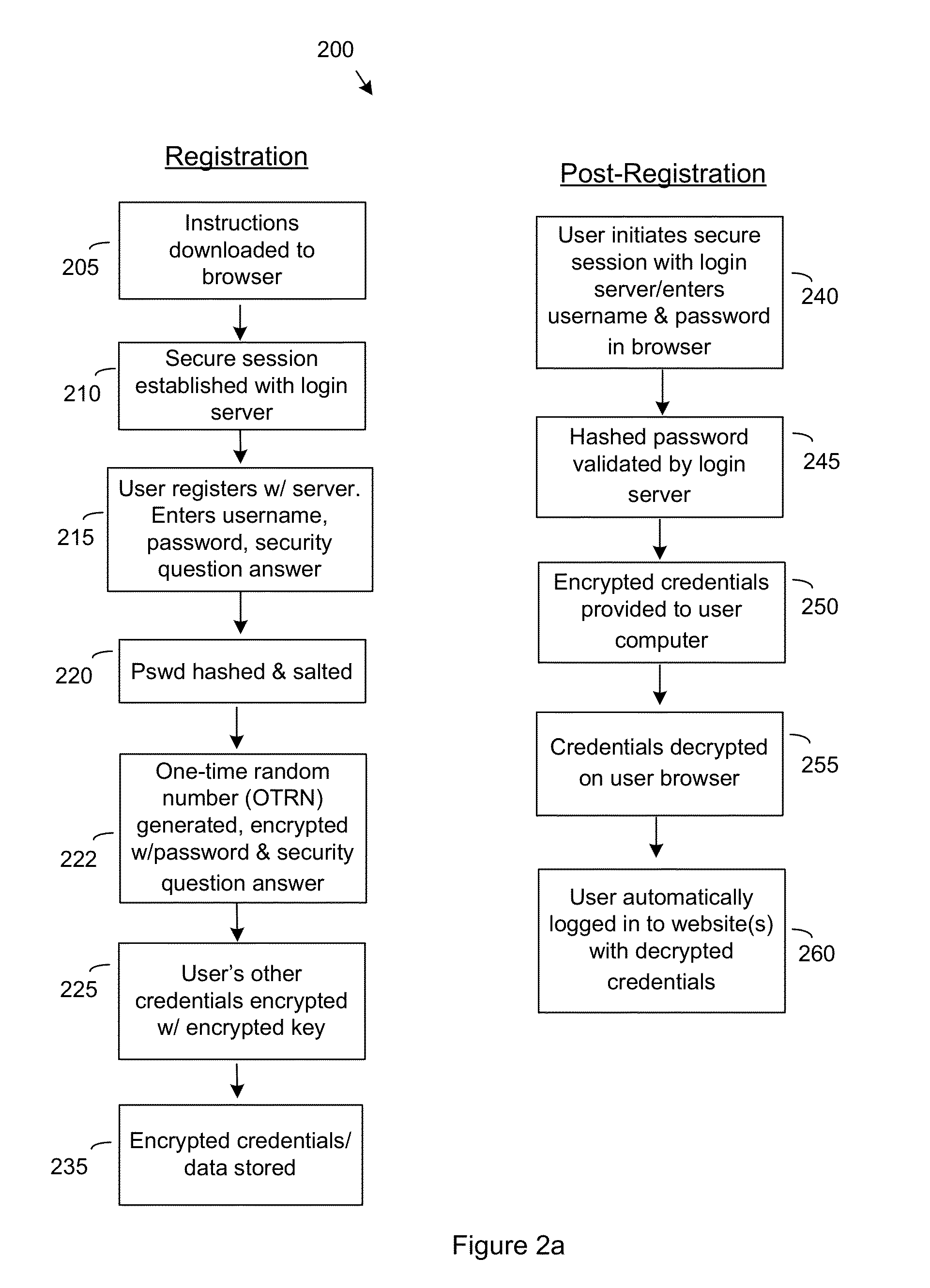
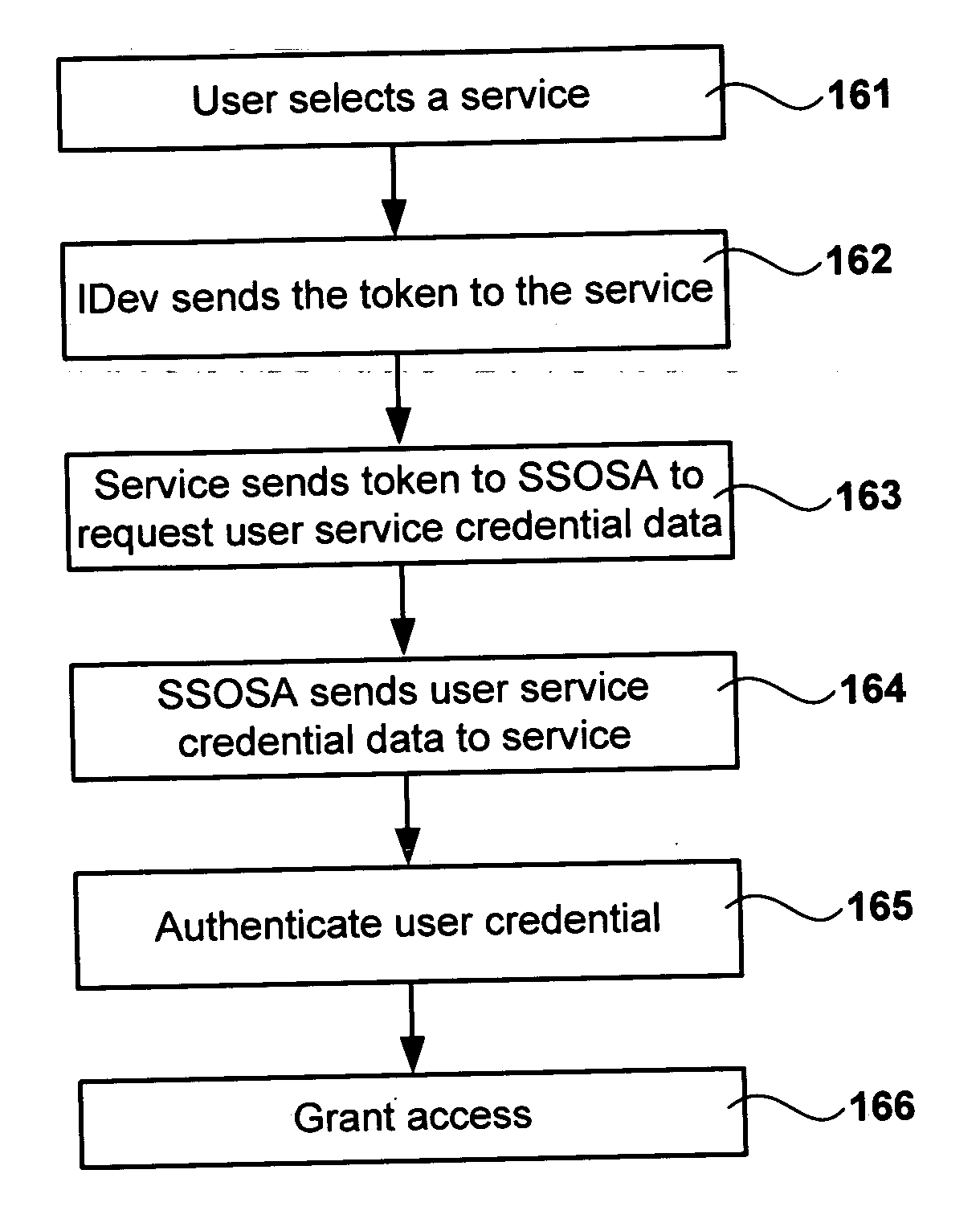
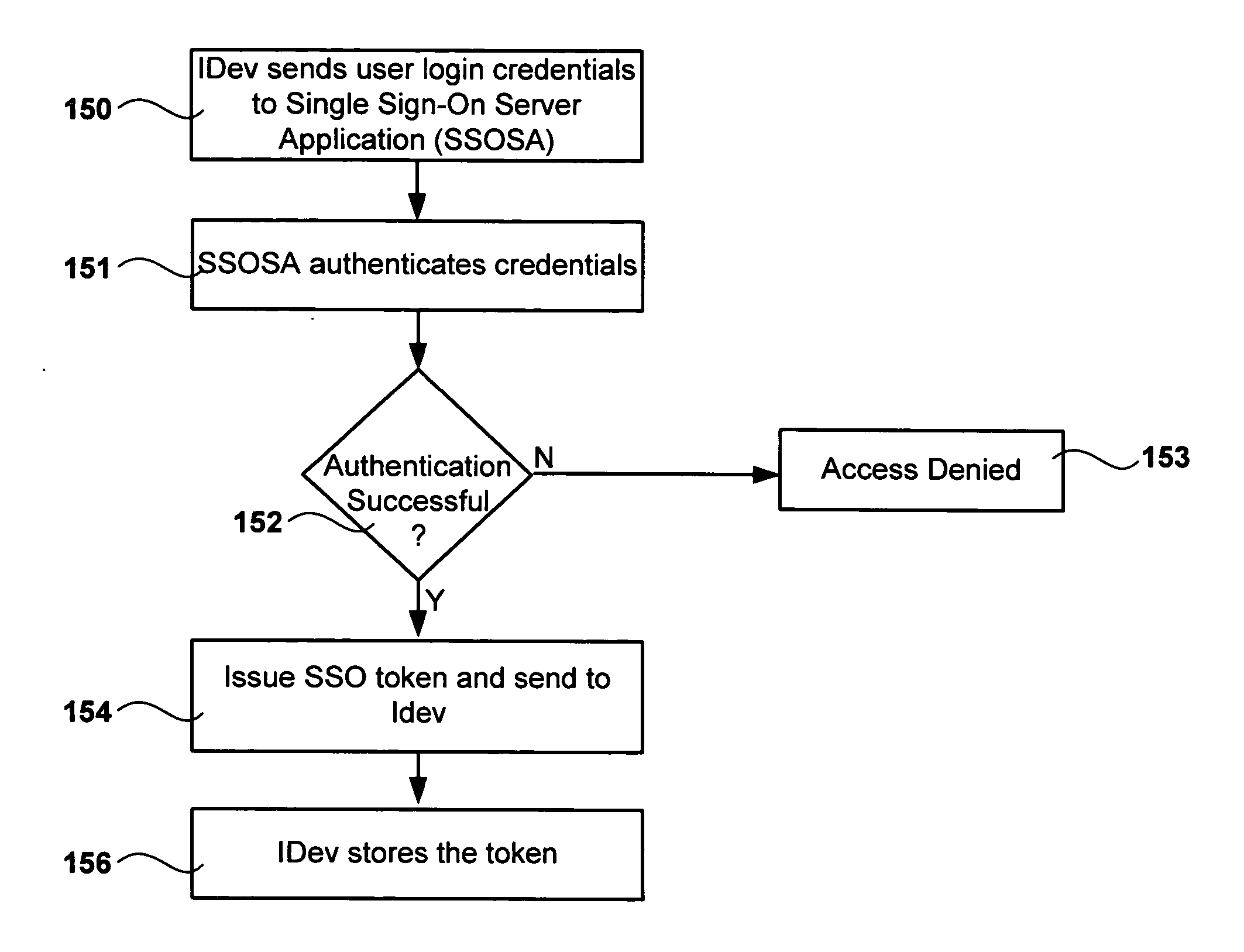
Methods for single signon (SSO) using decentralized password and credential management
ActiveUS8819444B2Decentralized credential managementShorten the timeComputer security arrangementsSecuring communicationEnd to end securityPassword
A method for single sign-on (SSO) that provides decentralized credential management using end-to-end security. Credential (and other personal user information) management is decentralized in that encryption is performed locally on the user's computer. The user's encrypted credentials may be stored by the login server and / or a plurality of distributed servers / databases (such as a cloud). The login server never has access to the user's credentials or other personal information. When the user wants to use single sign-on, he enters his password into his browser and the browser submits the encrypted / hashed password to the login server for validation. Upon validation, the browser receives the user's encrypted credentials. The credentials are decrypted by the browser and provided to relevant websites to automatically log the user in.
Owner:SHAHBAZI MAJID +1
Systems and methods for identity-based encryption and related cryptographic techniques
InactiveUS20070041583A1Key distribution for secure communicationPublic key for secure communicationID-based encryptionEmail address
A method and system for encrypting a first piece of information M to be sent by a sender [100] to a receiver [110] allows both sender and receiver to compute a secret message key using identity-based information and a bilinear map. In a one embodiment, the sender [100] computes an identity-based encryption key from an identifier ID associated with the receiver [110]. The identifier ID may include various types of information such as the receiver's e-mail address, a receiver credential, a message identifier, or a date. The sender uses a bilinear map and the encryption key to compute a secret message key gIDr, which is then used to encrypt a message M, producing ciphertext V to be sent from the sender [100] to the receiver [110] together with an element rP. An identity-based decryption key dID is computed by a private key generator [120] based on the ID associated with the receiver and a secret master key s. After obtaining the private decryption key from the key generator [120], the receiver [110] uses it together with the element rP and the bilinear map to compute the secret message key gIDr, which is then used to decrypt V and recover the original message M. According to one embodiment, the bilinear map is based on a Weil pairing or a Tate pairing defined on a subgroup of an elliptic curve. Also described are several applications of the techniques, including key revocation, credential management, and return receipt notification.
Owner:UNIV OF CALIFORNIA DAVIS +1
User credential management system and method thereof
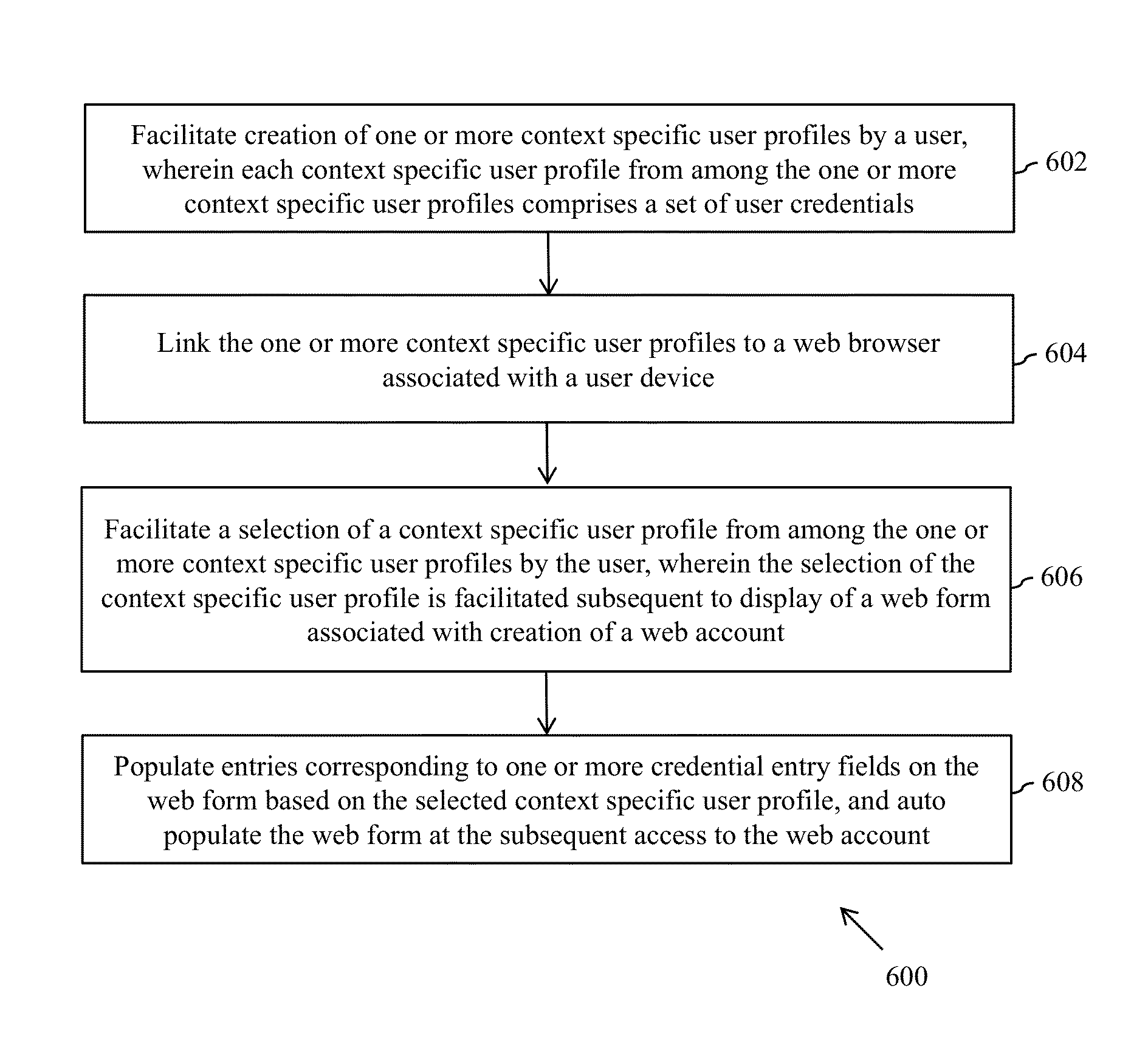
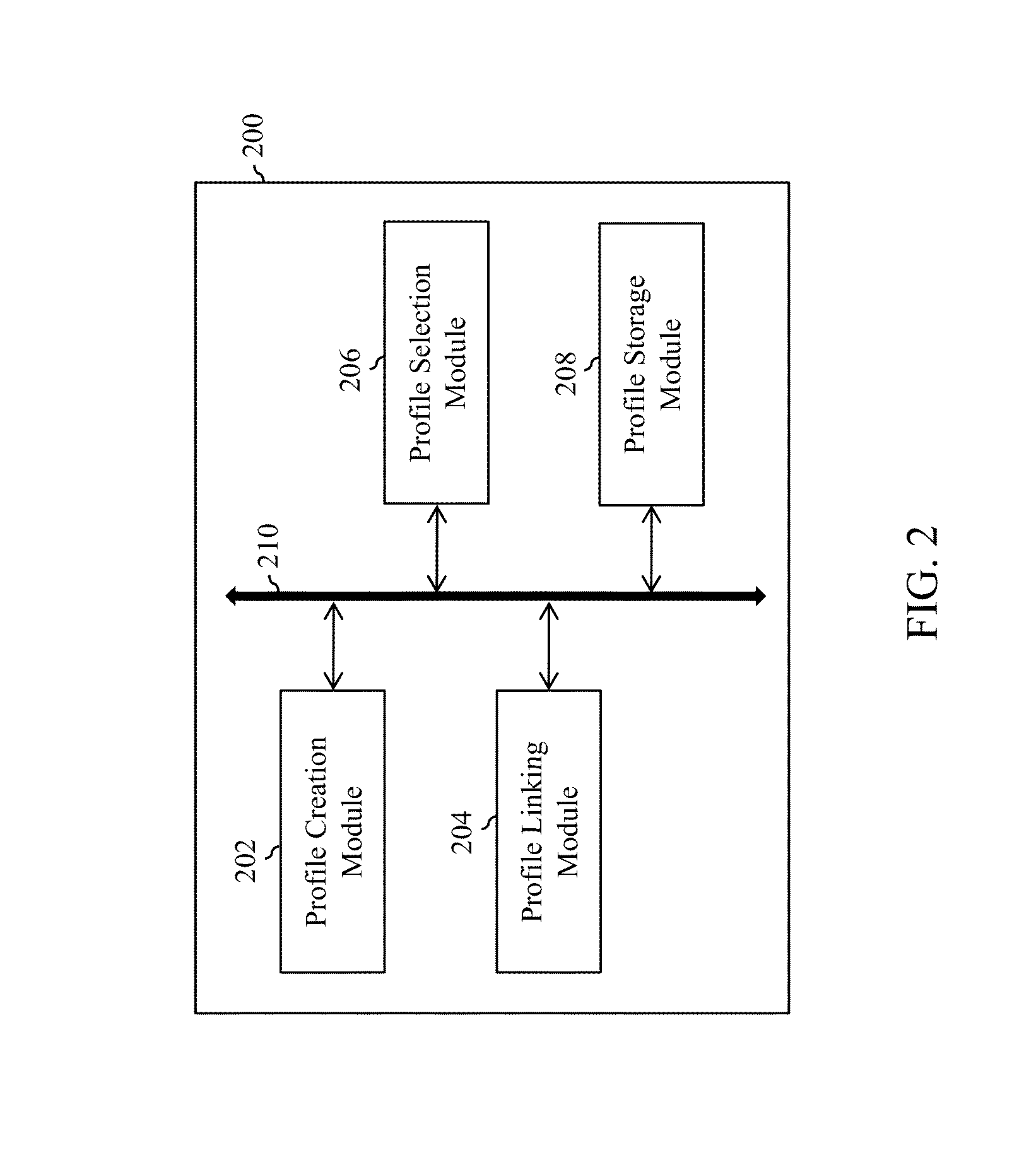
InactiveUS20140196129A1Easy to createGood choiceDigital data processing detailsMultiple digital computer combinationsMultiple contextWeb browser
The present invention provides a user credential management system and a method thereof. The system includes a profile creation module configured to facilitate creation of one or more context specific user profiles. Each context specific user profile comprises a set of user credentials. A profile linking module is configured to link the one or more context specific user profiles to a web browser. A profile selection module is configured to facilitate a selection of a context specific user profile from one of web account creation and a first time access to existing web account post creation of the context specific user profiles. The selection is subsequent to display of a web form associated with the web account. The profile selection module is further configured to populate entries corresponding to one or more credential entry fields on the web form based on the selected context specific user profile and auto populate the web form at the subsequent access to the web account.
Owner:PRIUM
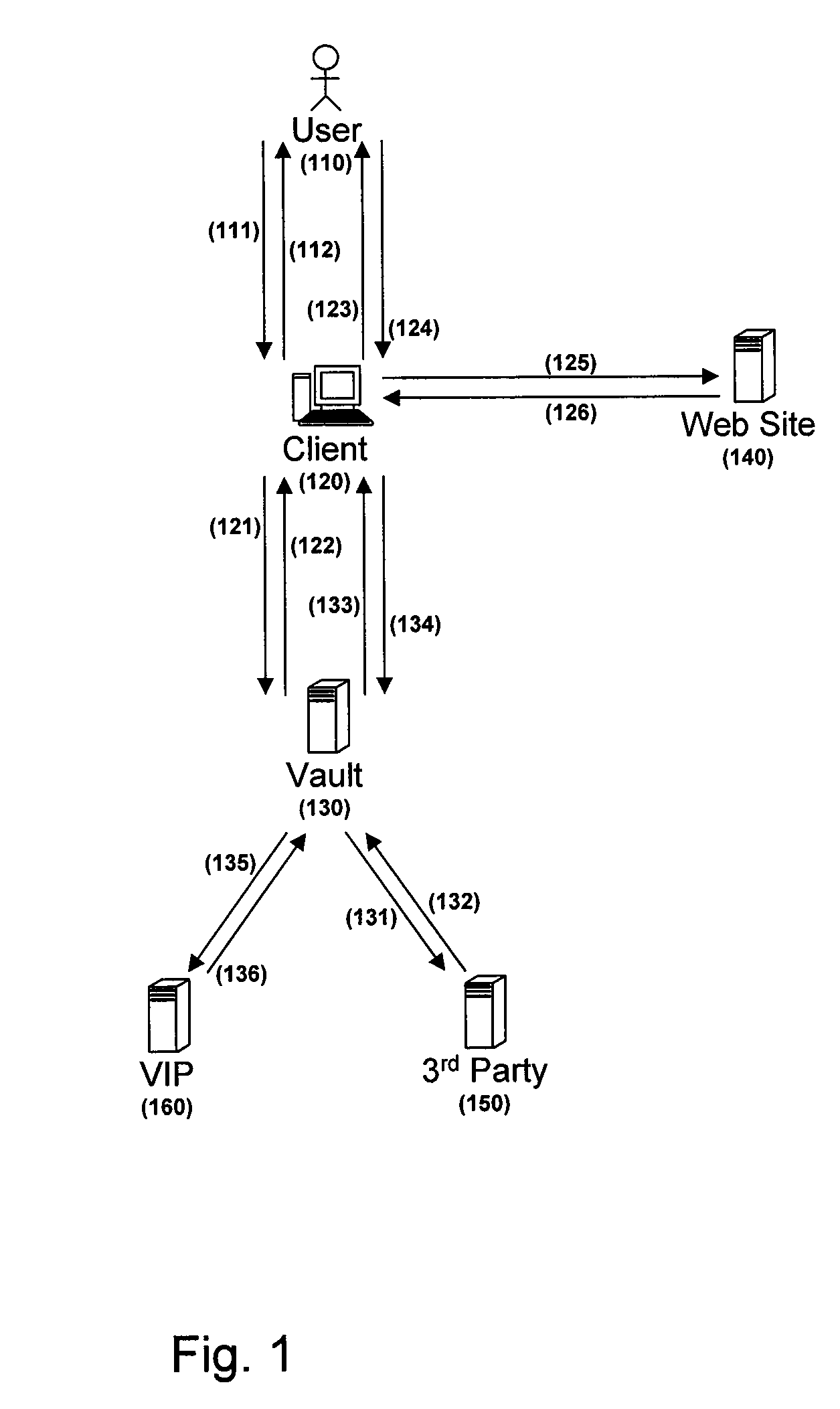
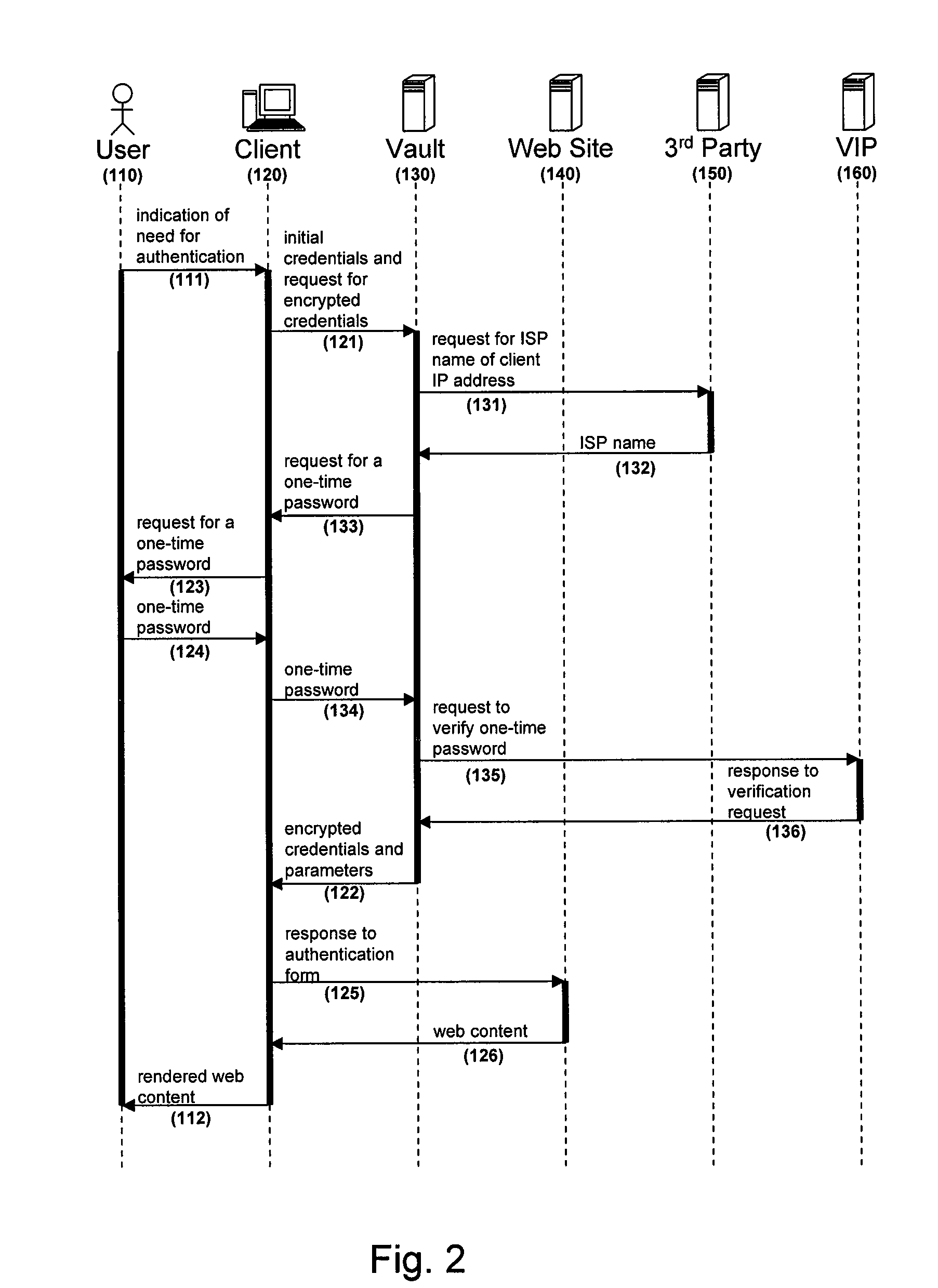
Credential management system and method
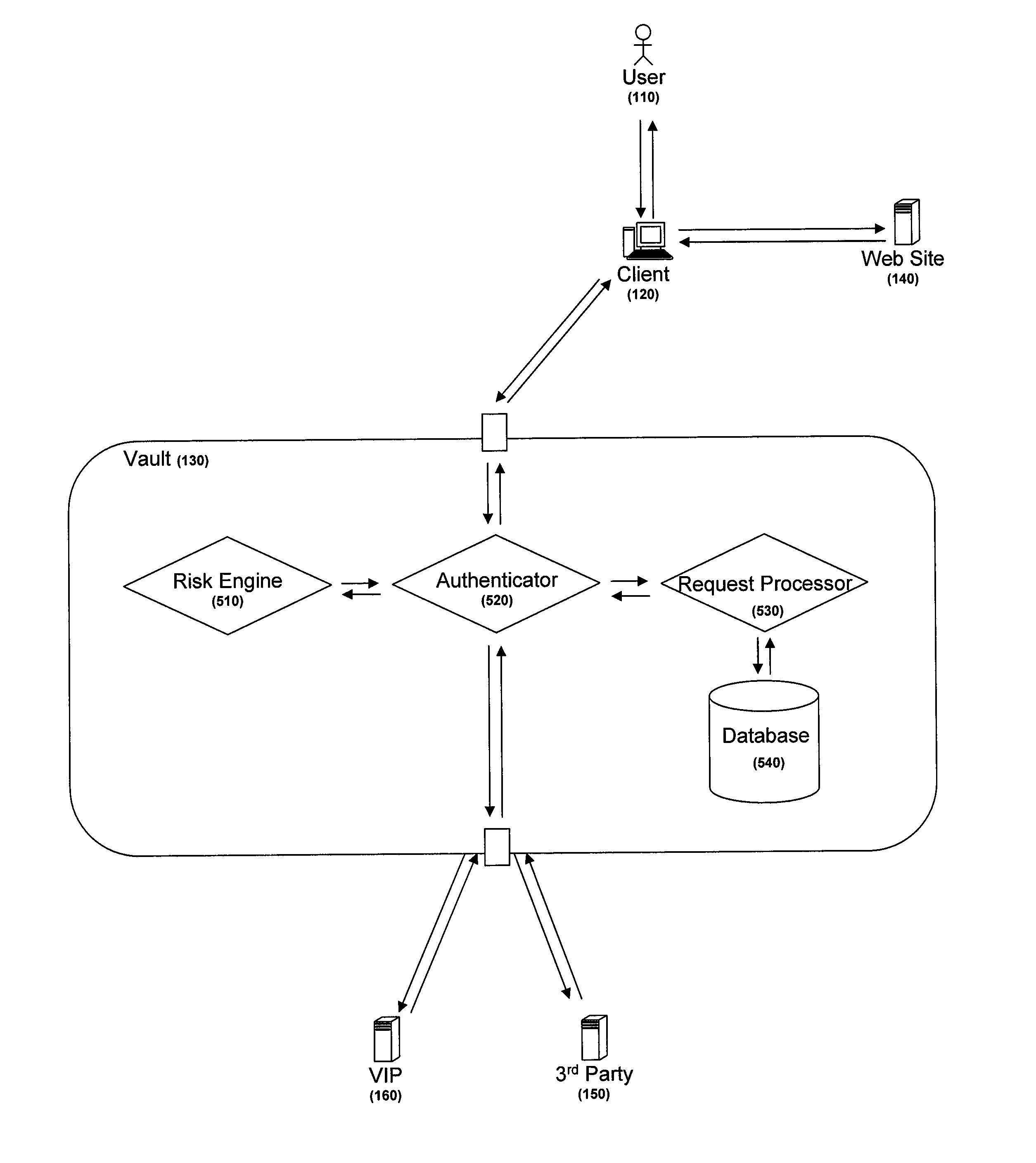
ActiveUS8438382B2Reduce riskVolume/mass flow measurementUser identity/authority verificationThird partyCode injection
A centralized credential management system includes website credentials that are stored at a vault. The website credentials are encrypted based upon a key not available to the vault and are for authenticating a user to a third party website. Through a client, a user authenticates to the vault and retrieves the encrypted website credentials and parameters and code for properly injecting the credentials into a website authentication form. The website credentials are decrypted at the client and injected into the authentication form using the parameters and code.
Owner:SYMANTEC CORP
Data processing system for application to access by accreditation
InactiveUS20060037066A1Improve securityDigital data processing detailsUser identity/authority verificationData processing systemCredential management
This system for executing a program to which access by a user is controlled by credentials includes a terminal (T), first memory means (F) associated with said program for storing at least first credentials specific to said user, access control means for authorizing access to said program in response to a match between said first credentials and second credentials applied via said terminal, and a security device (PSD) personal to said user, associated with said terminal and including second memory means (M) for secure storage of said second credentials. The terminal (T) includes at least some of credentials management means (CMP) including means for reading said second credentials and transmitting them to said access control means in response to presentation of a request to access said program, and credentials updating; means for selectively commanding the generation and loading into said first and second memory means (F, M) of new credentials replacing the credentials previously stored.
Owner:ASSA ABLOY AB
Cryptographic methods and systems for managing digital certificates with linkage values
ActiveUS20190089547A1Reduce in quantityImprove securityKey distribution for secure communicationParticular environment based servicesCredential managementManagement system
Improved pseudonym certificate management is provided for connected vehicle authentication and other applications. Temporary revocation of a certificate is enabled. With respect to Security Credential Management Systems (SCMS), linkage authorities can be eliminated without compromising the system security. Other embodiments are also provided.
Owner:UNIV DE SAO PAULO
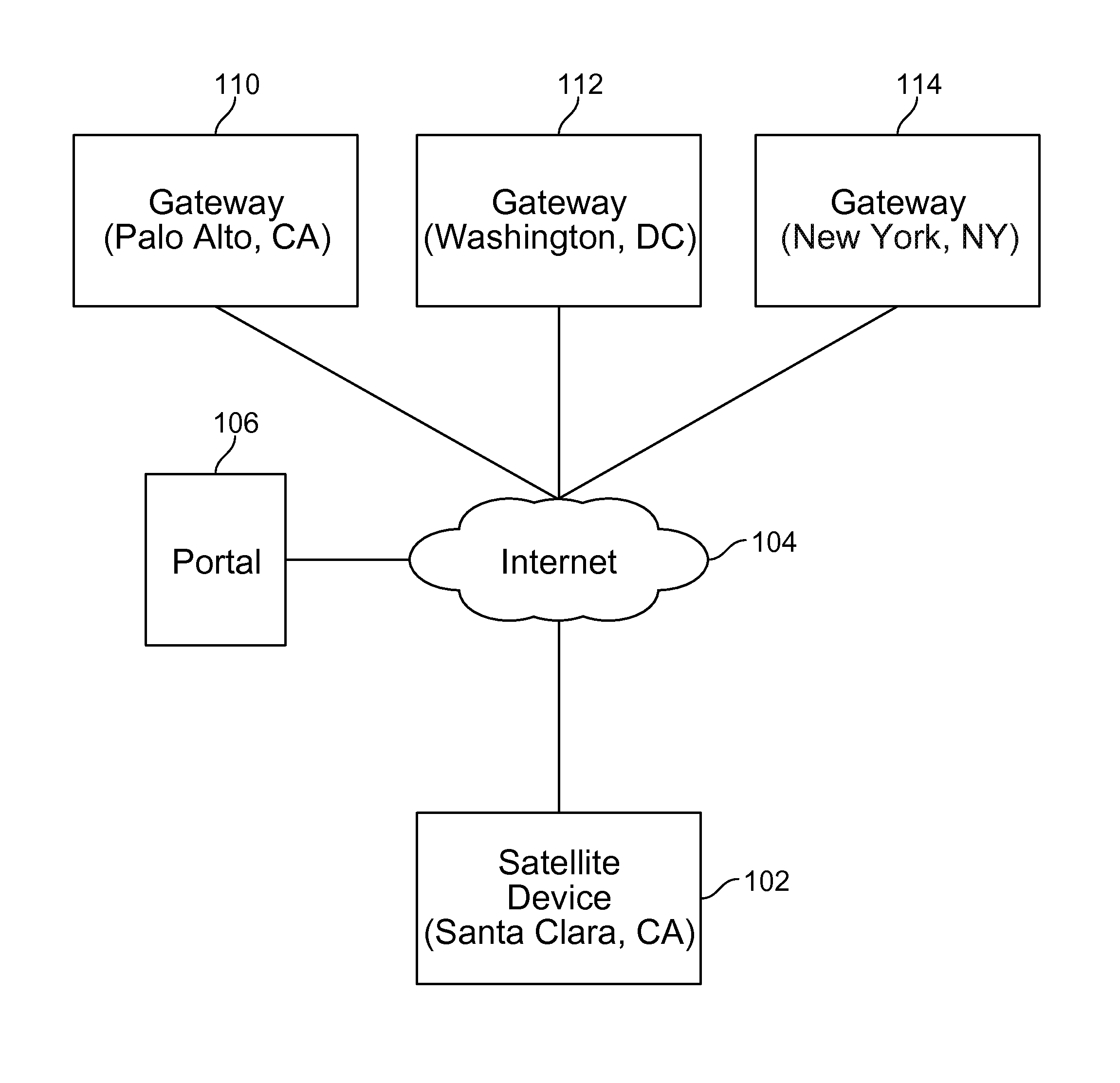
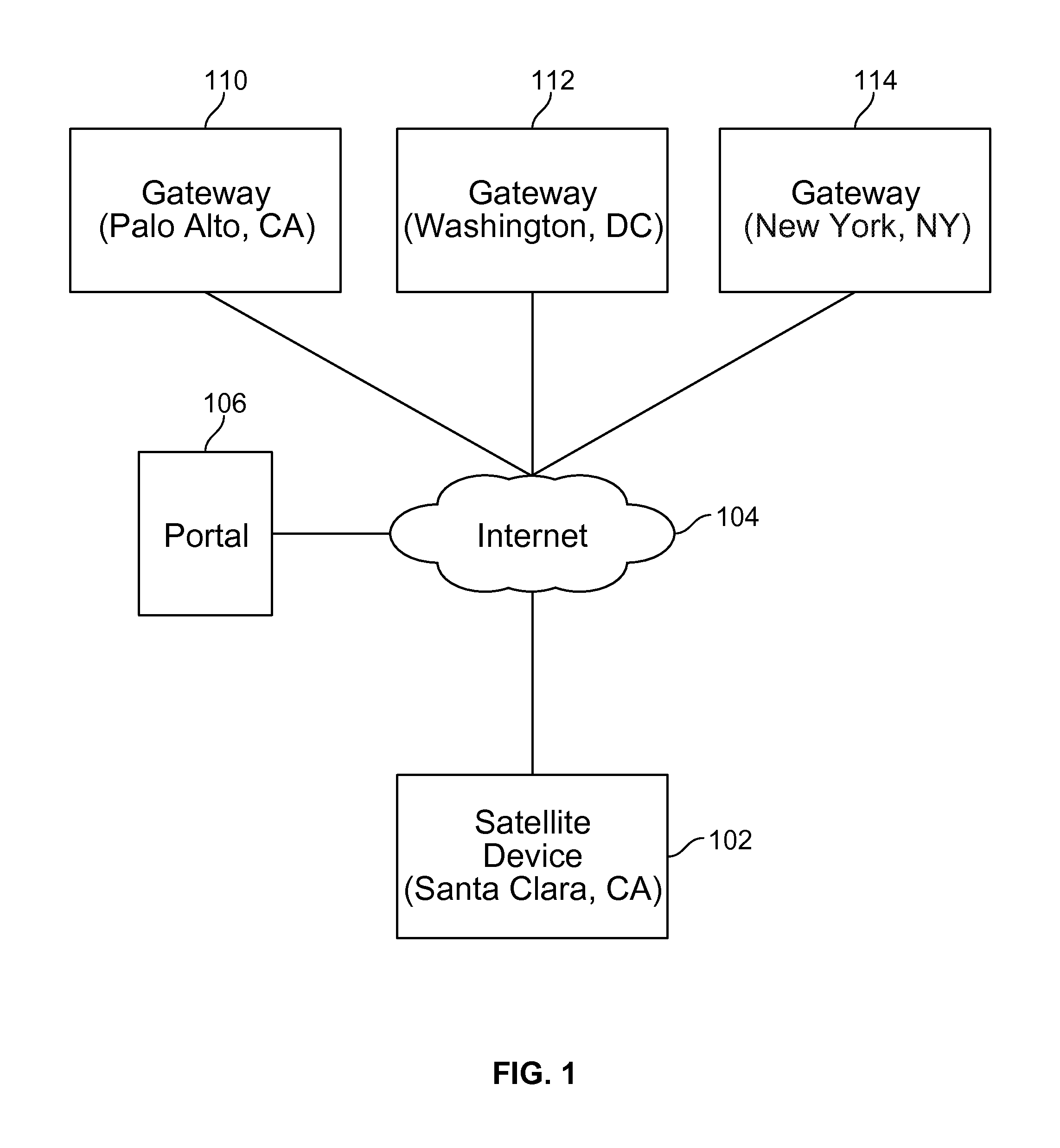
Credentials management in large scale virtual private network deployment
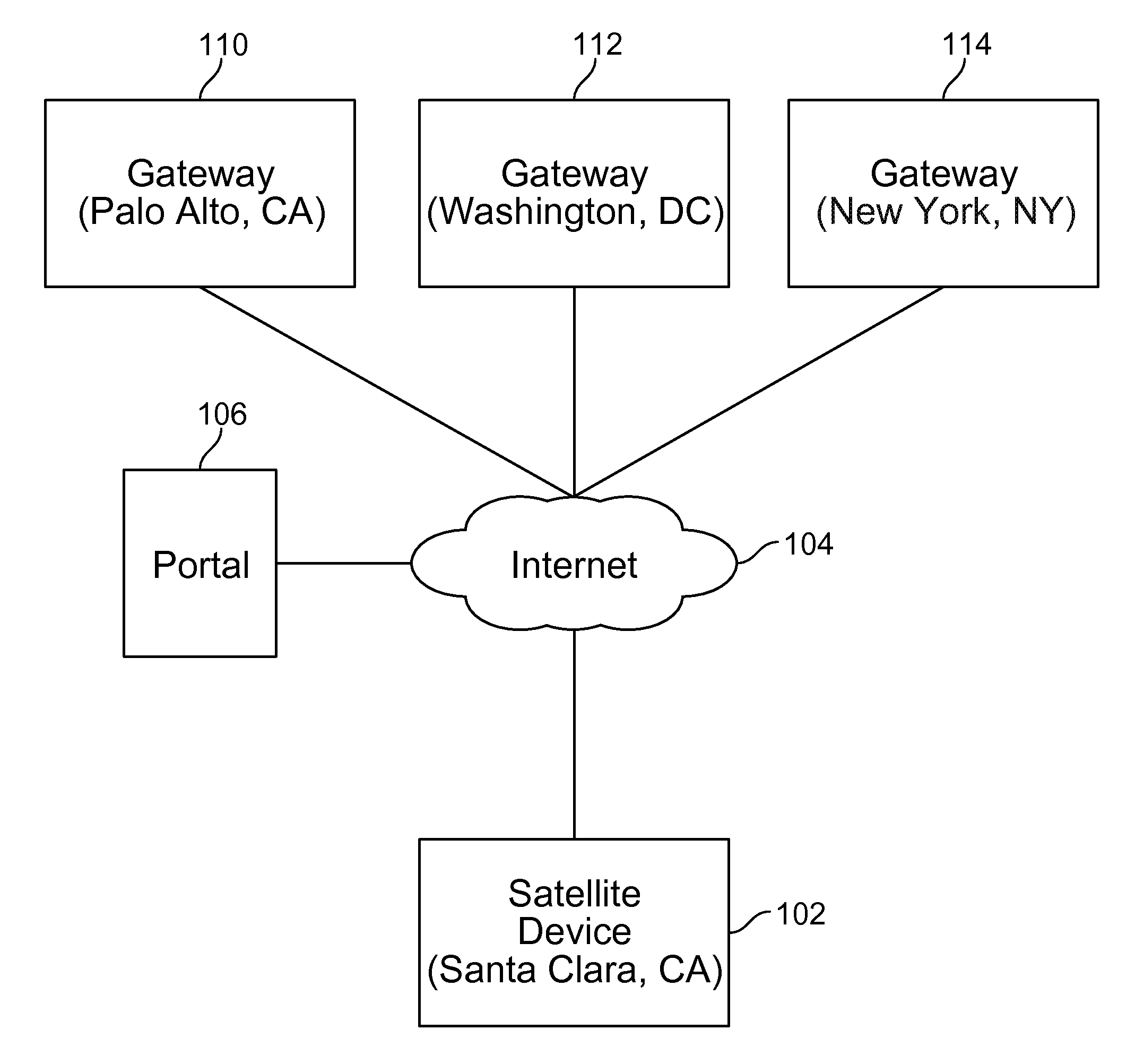
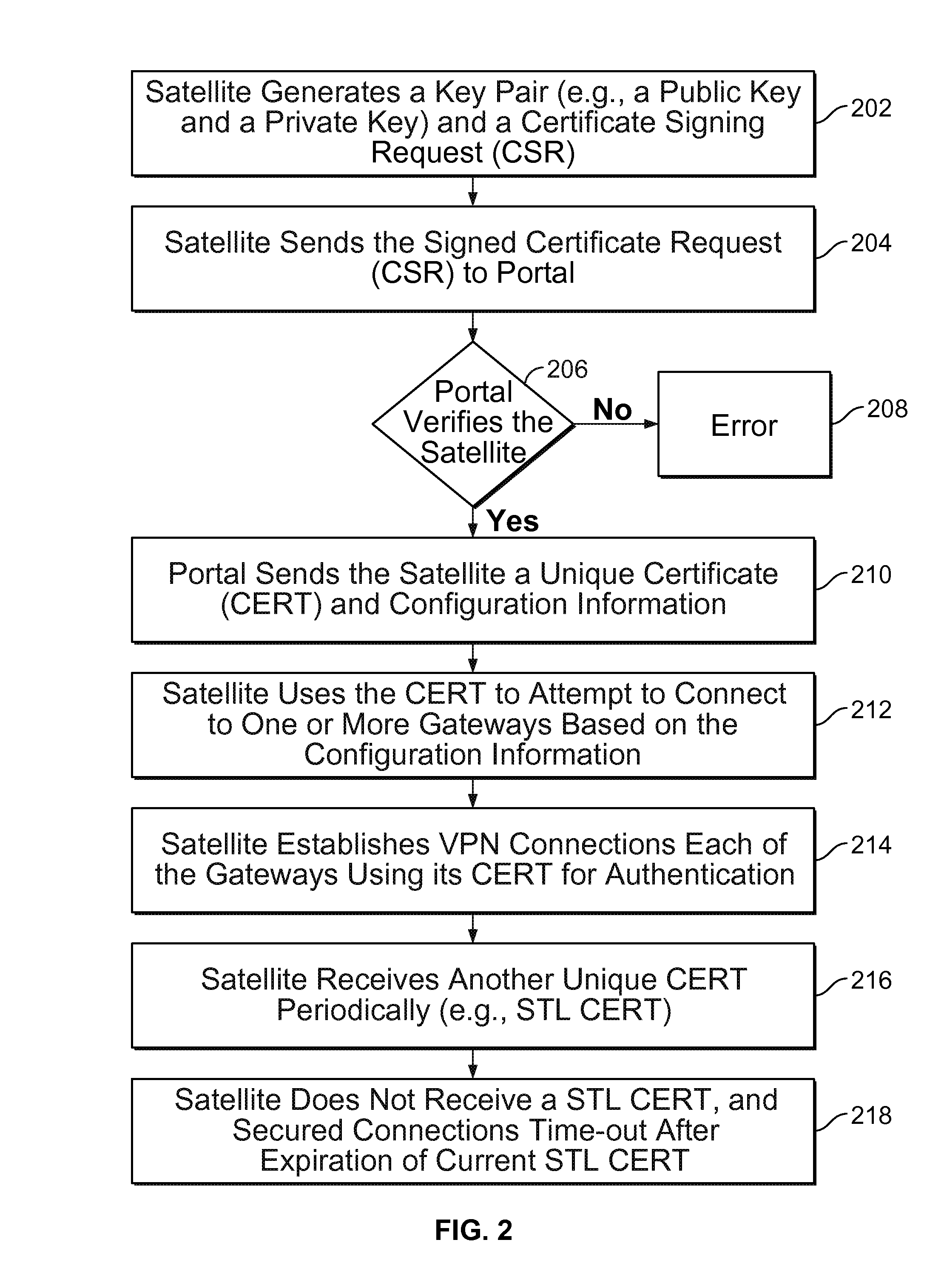
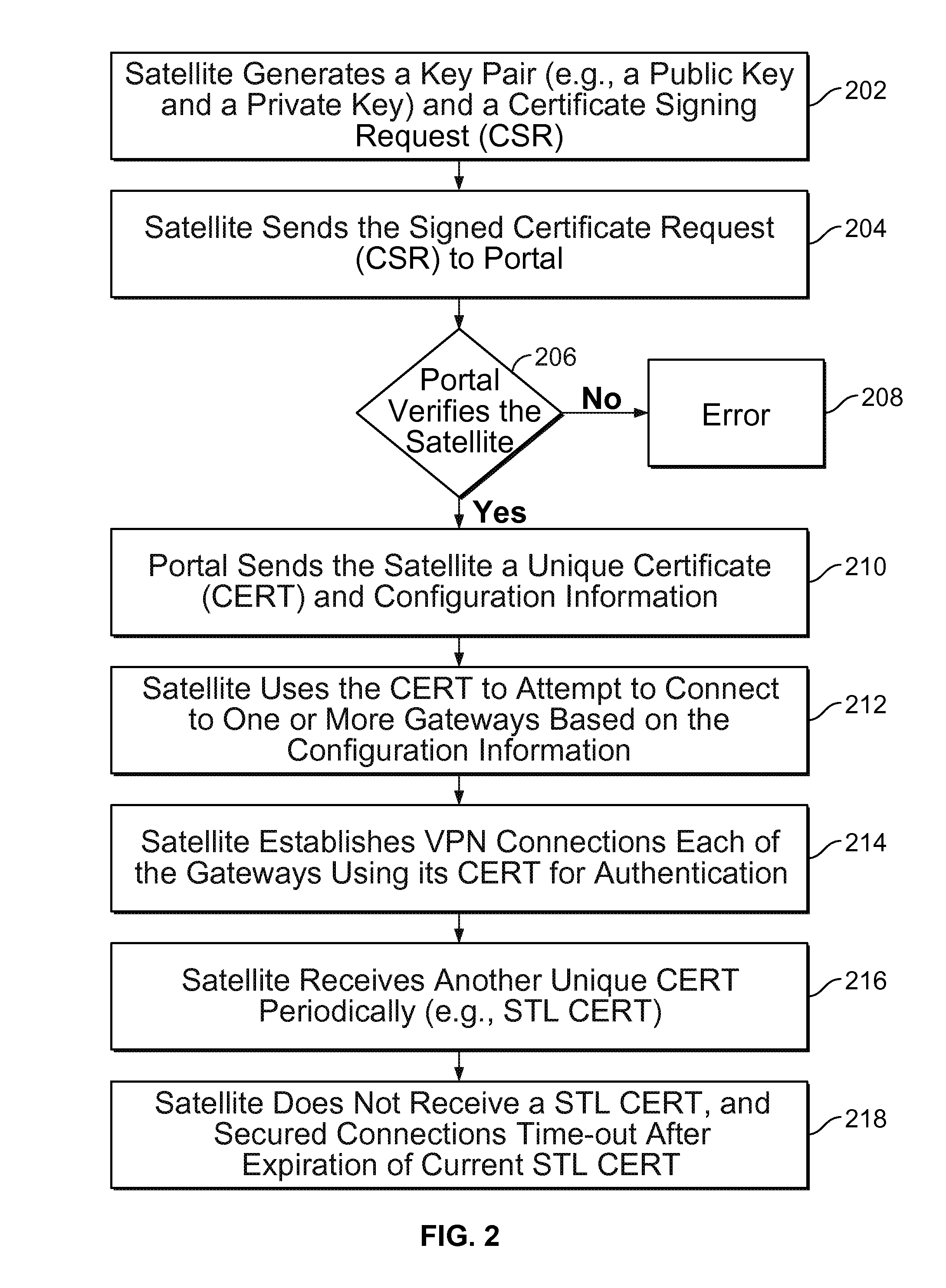
Techniques for credentials management in large scale virtual private network (VPN) deployment are disclosed. In some embodiments, credentials management in large scale VPN deployment includes generating a public / private key pair and a certificate signing request at a satellite device; automatically communicating the certificate signing request to a portal over a public, untrusted network to authenticate the satellite device using a serial number associated with the satellite device, in which the certificate signing request and the serial number are verified by the portal; and receiving a certificate from the portal for using to establish VPN connections and configuration information for the satellite device, in which the certificate includes a credential signed by a trusted certificate authority, and the configuration information includes gateway configuration information identifying a plurality of gateways to which the satellite device is configured to connect using VPN connections.
Owner:PALO ALTO NETWORKS INC
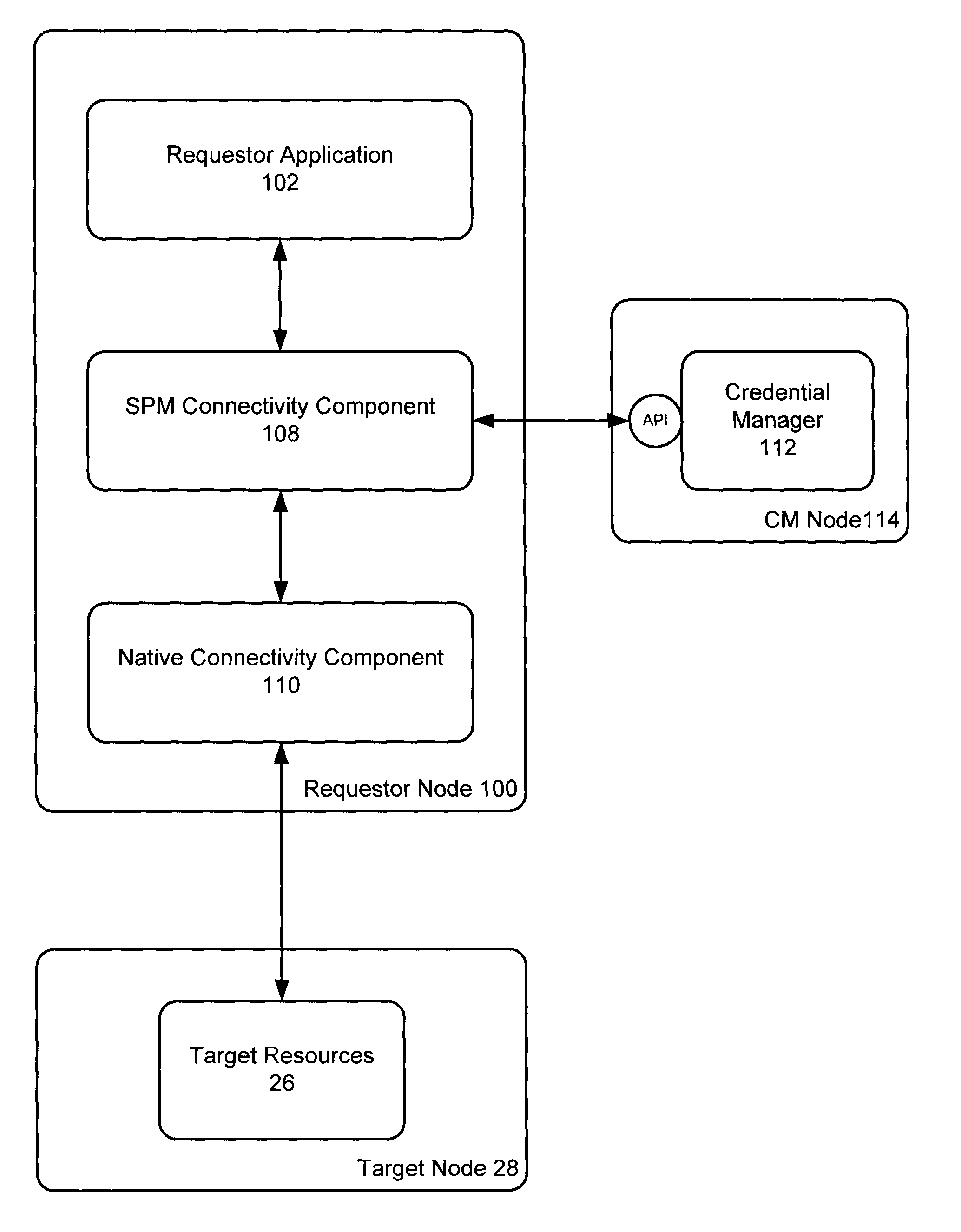
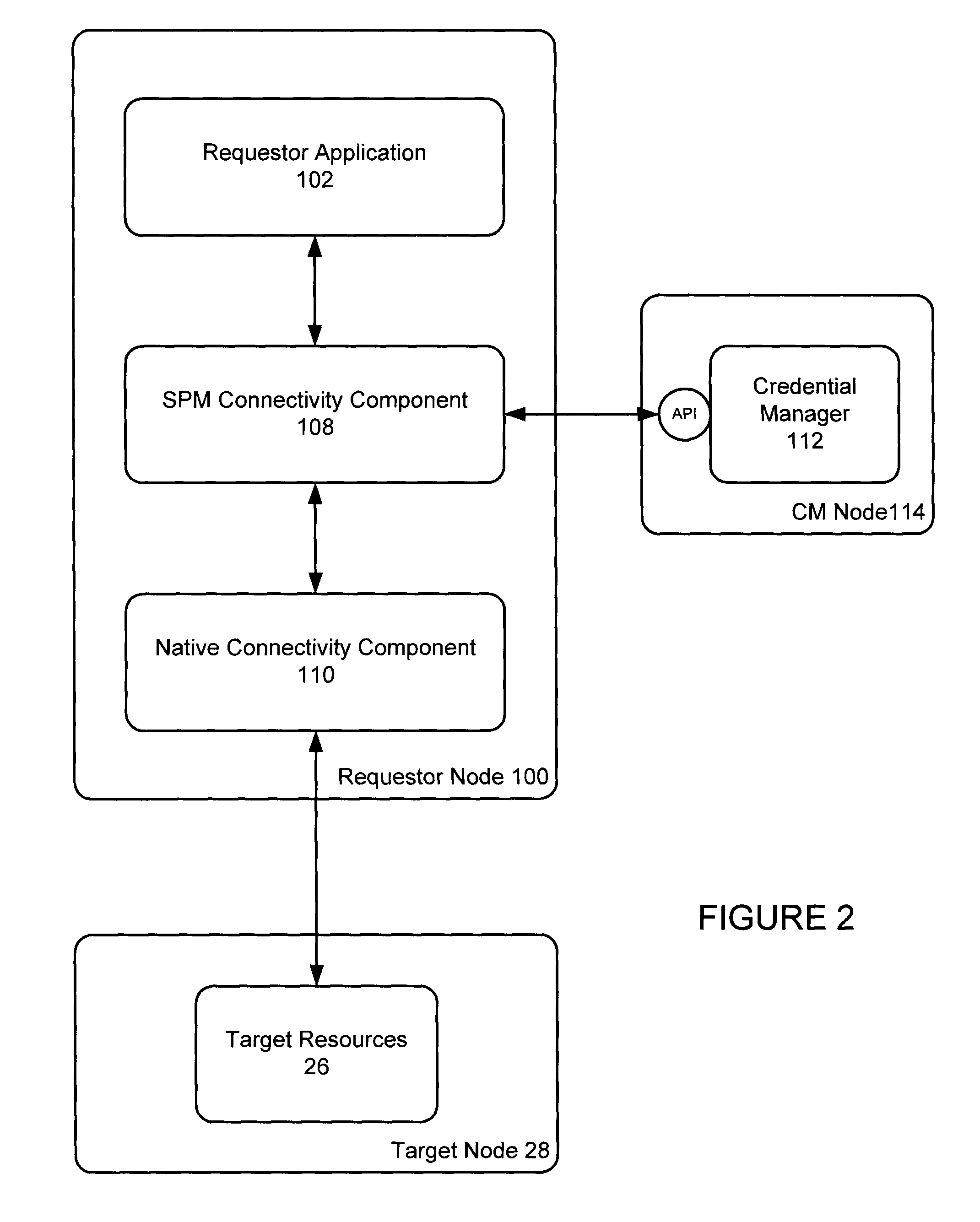
Authenticated database connectivity for unattended applications
ActiveUS20110093937A1Digital data processing detailsUser identity/authority verificationCredential service providerCredential management
A custom database connectivity component is deployed in conjunction with a native database connectivity component and a credential manager. The custom connectivity component has a requestor interface for communicating with a requestor application, a credential service interface for communicating with the credential manager, a native database connectivity interface for communicating with native connectivity components, and a decision engine for determining how to convert a request from a requestor to an appropriate API call to the credential manager. The custom connectivity component provides an authenticated and authorized database connection for a requestor application. The component transparently serves retrieves database, or other target resource, credentials on a real time basis, without requiring code changes to the requestor application.
Owner:IRDETO ACCESS
Credentials management in large scale virtual private network deployment
ActiveUS20150195252A1Digital data processing detailsMultiple digital computer combinationsPrivate networkCertificate signing request
Techniques for credentials management in large scale virtual private network (VPN) deployment are disclosed. In some embodiments, credentials management in large scale VPN deployment includes generating a public / private key pair and a certificate signing request at a satellite device; automatically communicating the certificate signing request to a portal over a public, untrusted network to authenticate the satellite device using a serial number associated with the satellite device, in which the certificate signing request and the serial number are verified by the portal; and receiving a certificate from the portal for using to establish VPN connections and configuration information for the satellite device, in which the certificate includes a credential signed by a trusted certificate authority, and the configuration information includes gateway configuration information identifying a plurality of gateways to which the satellite device is configured to connect using VPN connections.
Owner:PALO ALTO NETWORKS INC
System, Design and Process for Secure Documents Credentials Management Using Out-of-Band Authentication
ActiveUS20160351080A1Easy to useProtected growthUser identity/authority verificationCoding/ciphering apparatusApplication softwareMulti dimensional
The invention provides an easy to use credential management mechanism for multi-factor out-of-band multi-channel authentication process to protect a large number of documents without the need to remember all the document passwords. When opened, the secure document application generates a multi-dimensional code. The user scans the multi-dimensional code and validates the secure document application and triggers an out-of-band outbound mechanism. The portable mobile device invoices the authentication server to get authenticated. The authentication server authenticates the user based on shared secret key and is automatically allowed access to the secure document. The process of the invention includes an authentication server, a secure document application to generate an authentication vehicle or an embodiment (i.e. multi-dimensional bar code) and handle incoming requests, secret keys and a portable communication device with a smartphone application.
Owner:GCOM IP LLC
Operating system interface for credential management
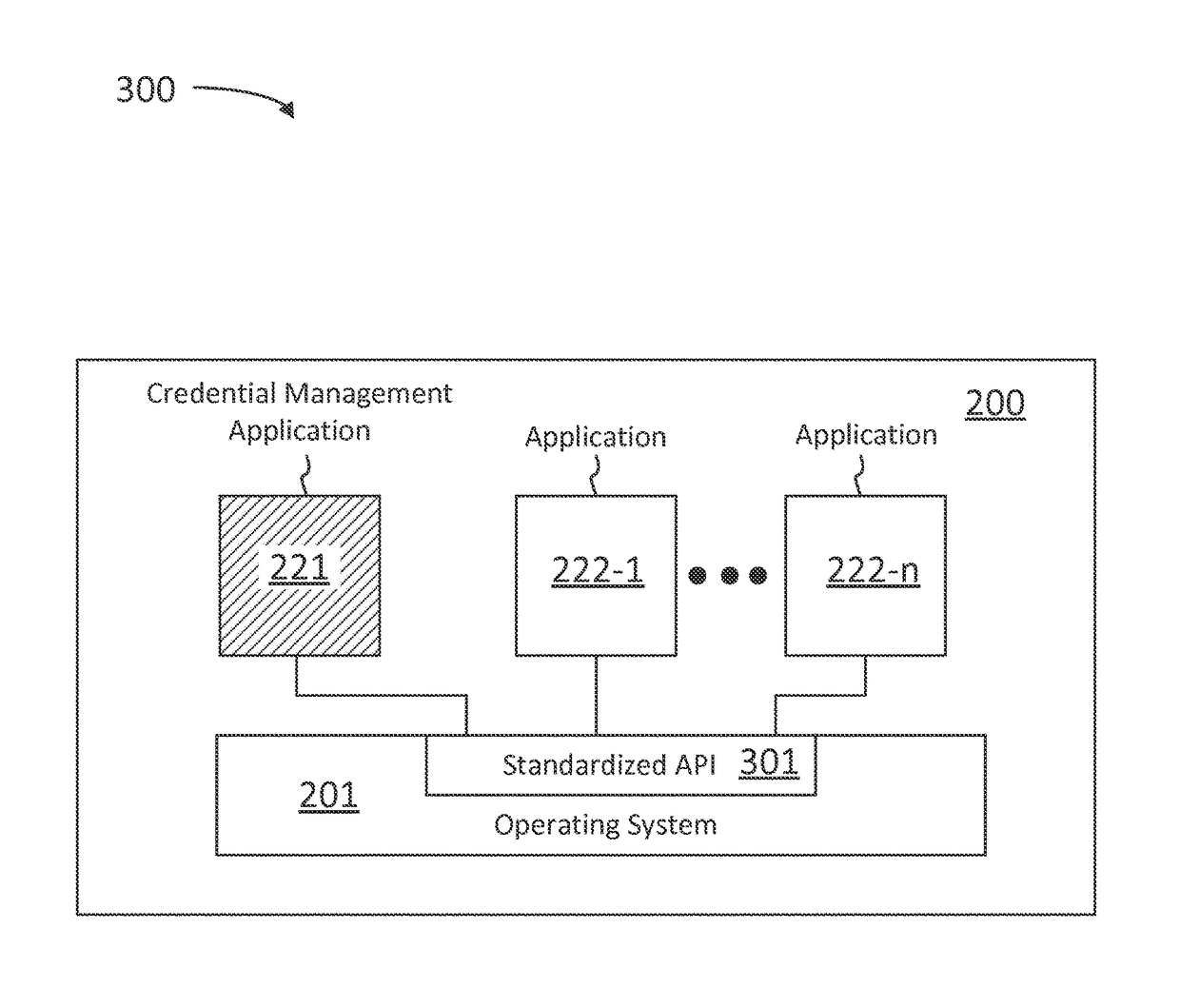
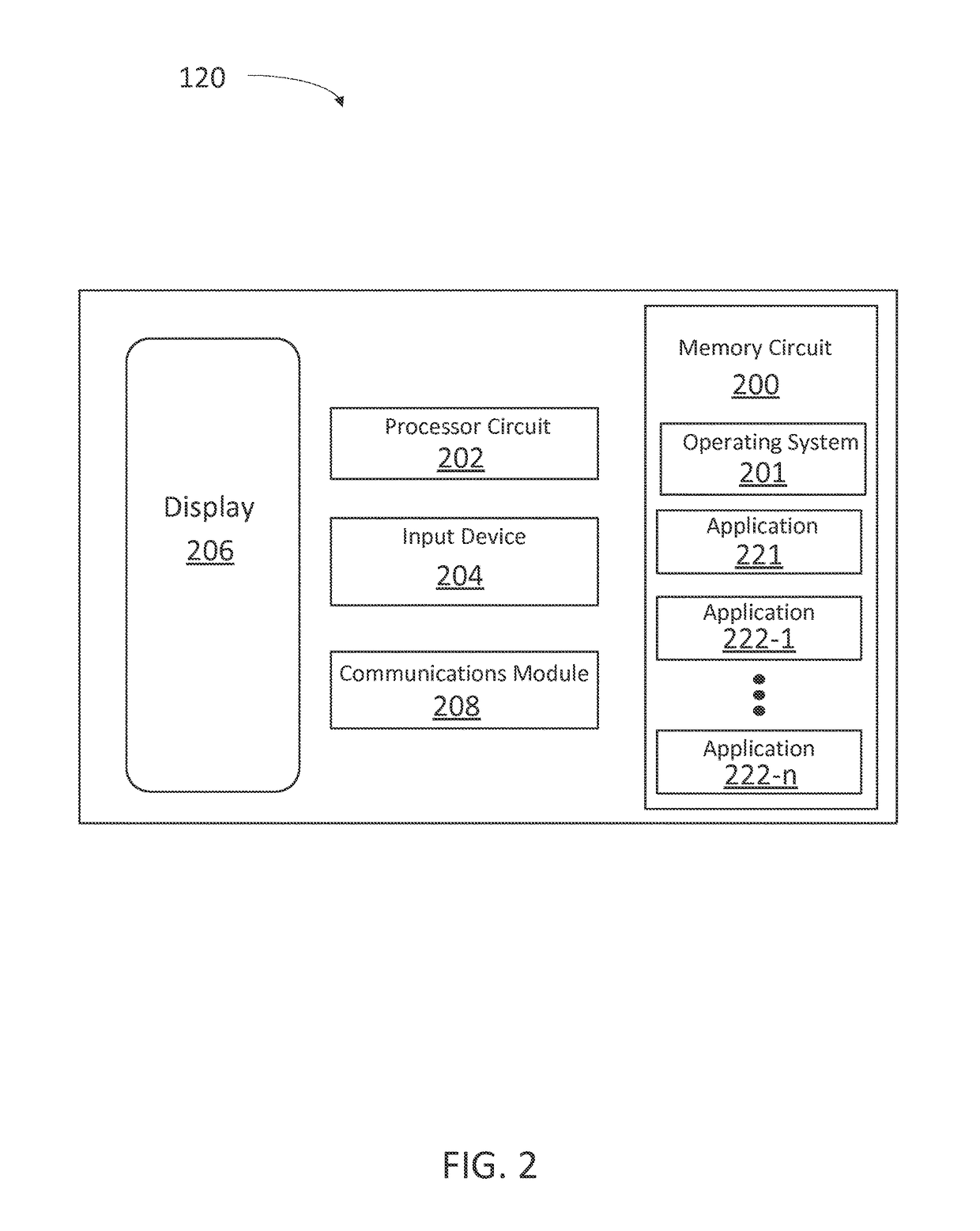
ActiveUS9825934B1User identity/authority verificationNatural language data processingOperational systemCredential management
A computer-implemented method for providing an operating system level interface for communicating credential data between applications includes detecting, by an operating system, a field configured to receive an authentication credential and identifying a credential management application configured to provide authentication credentials. The method includes requesting, by the operating system and using an operating system interface configured to communicate authentication credentials, the authentication credential from the credential management application. And when the credential management application provides the authentication credential using the operating system interface configured to communicate authentication credentials, the method includes providing the authentication credential for entry into the field.
Owner:GOOGLE LLC
Library information management system
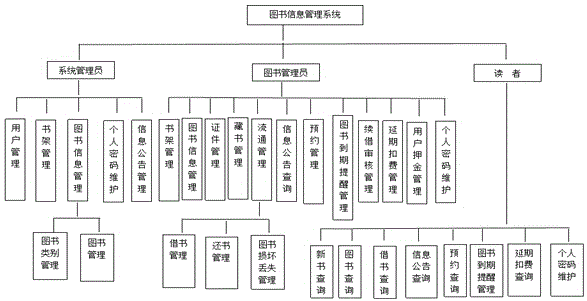
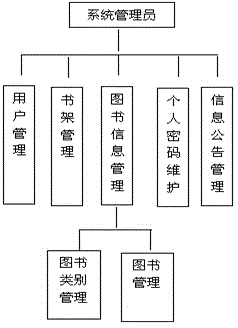
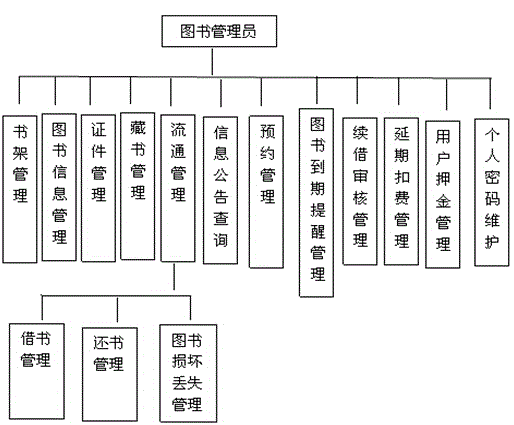
InactiveCN104318376AEasy to manageFacilitate information exchangeResourcesPasswordCredential management
The invention discloses a library information management system, and relates to a computer management system. The library information management system is provided with a system administrator unit, a librarian unit and a reader unit, wherein the system administrator unit comprises a user management module, a bookshelf management module, a library information management module, a personal password maintenance module and an information bulletin management module, the librarian unit comprises a bookshelf management module, another library information management module, a credential management module, a library management module, a circulation management module, an information bulletin inquiry module, an appointment management module, a book expiry reminding management module, a renewal audit management module, a postponement charging management module and a user deposit management module, and the reader unit comprises a new book recommendation inquiry module, a book inquiry module, a book borrowing management module, another information bulletin inquiry module, an appointment inquiry module, another book expiry reminding management module and a postponement charging inquiry module. The library information management system has the advantages of being rapid in information retrieval, convenient in search, high in reliability, large in storage capacity, strong in security, long in life, low in cost and the like.
Owner:SHENYANG INSTITUTE OF CHEMICAL TECHNOLOGY
Management of credentials on an electronic device using an online resource
Systems, methods, and computer-readable media for using an online resource to manage credentials on an electronic device are provided. In one example embodiment, a method, at an electronic device, includes, inter alia, receiving account data via an online resource, accessing commerce credential status data from a secure element of the electronic device, providing initial credential management option data via the online resource based on the received account data and based on the accessed commerce credential status data, in response to the providing, receiving a selection of an initial credential management option via the online resource, and changing the status of a credential on the secure element based on the received selection. Additional embodiments are also provided.
Owner:APPLE INC
Method and system for secure connected vehicle communication
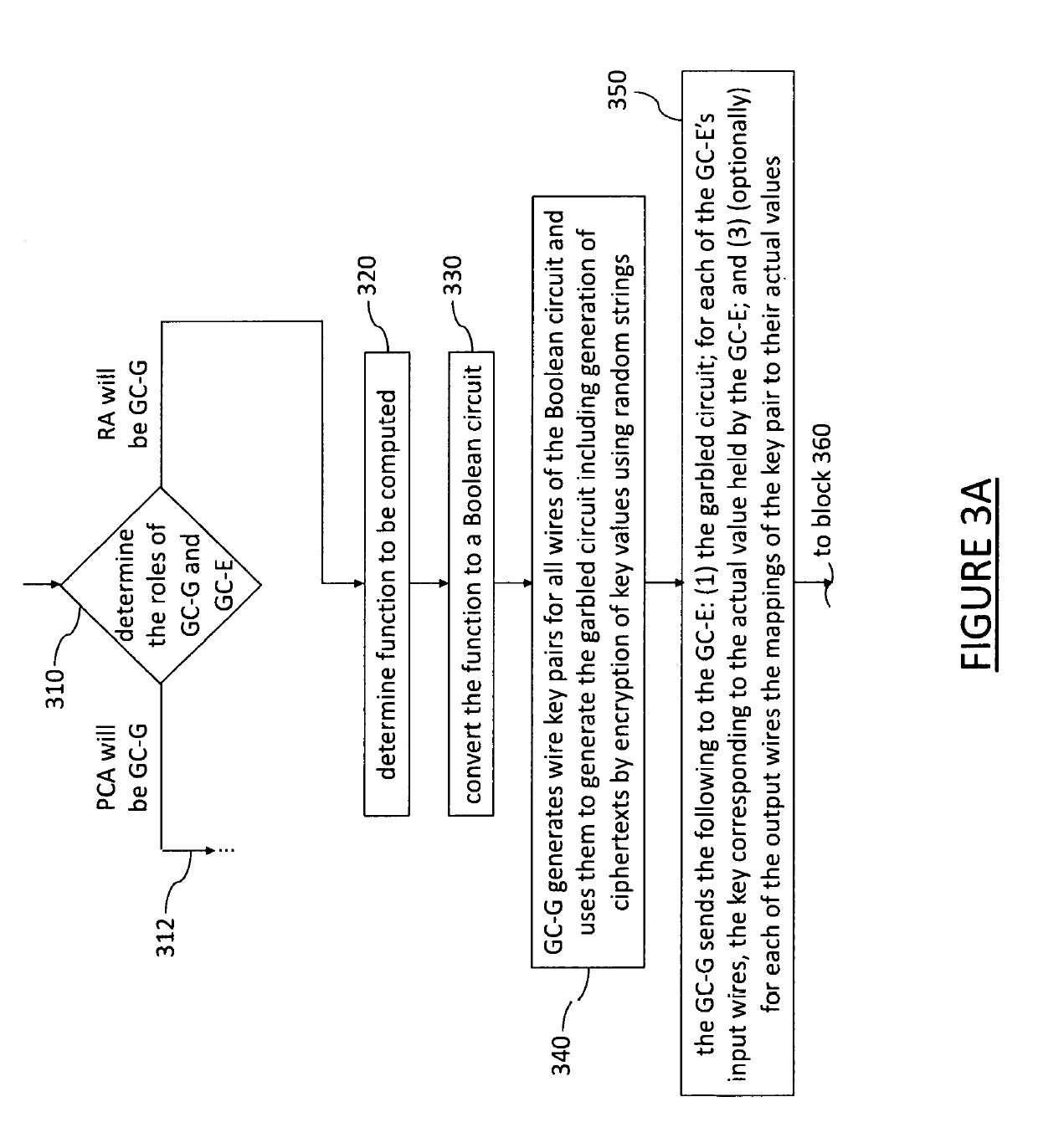
ActiveUS20190116048A1Improve efficiencyImprove securityKey distribution for secure communicationParticular environment based servicesRegistration authorityBoolean circuit
A method for producing linkage values to be contained within pseudonym digital certificates of a security credential management system for connected vehicles, including the following steps: providing a linkage value function that expresses linkage values as a function of a number of input parameters that include a linkage seed input from a pseudonym certificate authority processor entity and a plurality of inputs from a registration authority processor entity including a vehicle identifier and at least one index relating to a time period for the linkage value; producing a Boolean circuit representative of the function for a particular combination of the number of input parameters; and executing a garbled circuit protocol on the Boolean circuit between the registration authority processor entity and the pseudonym certificate authority processor entity, whereby the pseudonym certificate authority processor entity privately derives a linkage value for the particular combination of the number of input parameters.
Owner:ONBOARD SECURITY INC
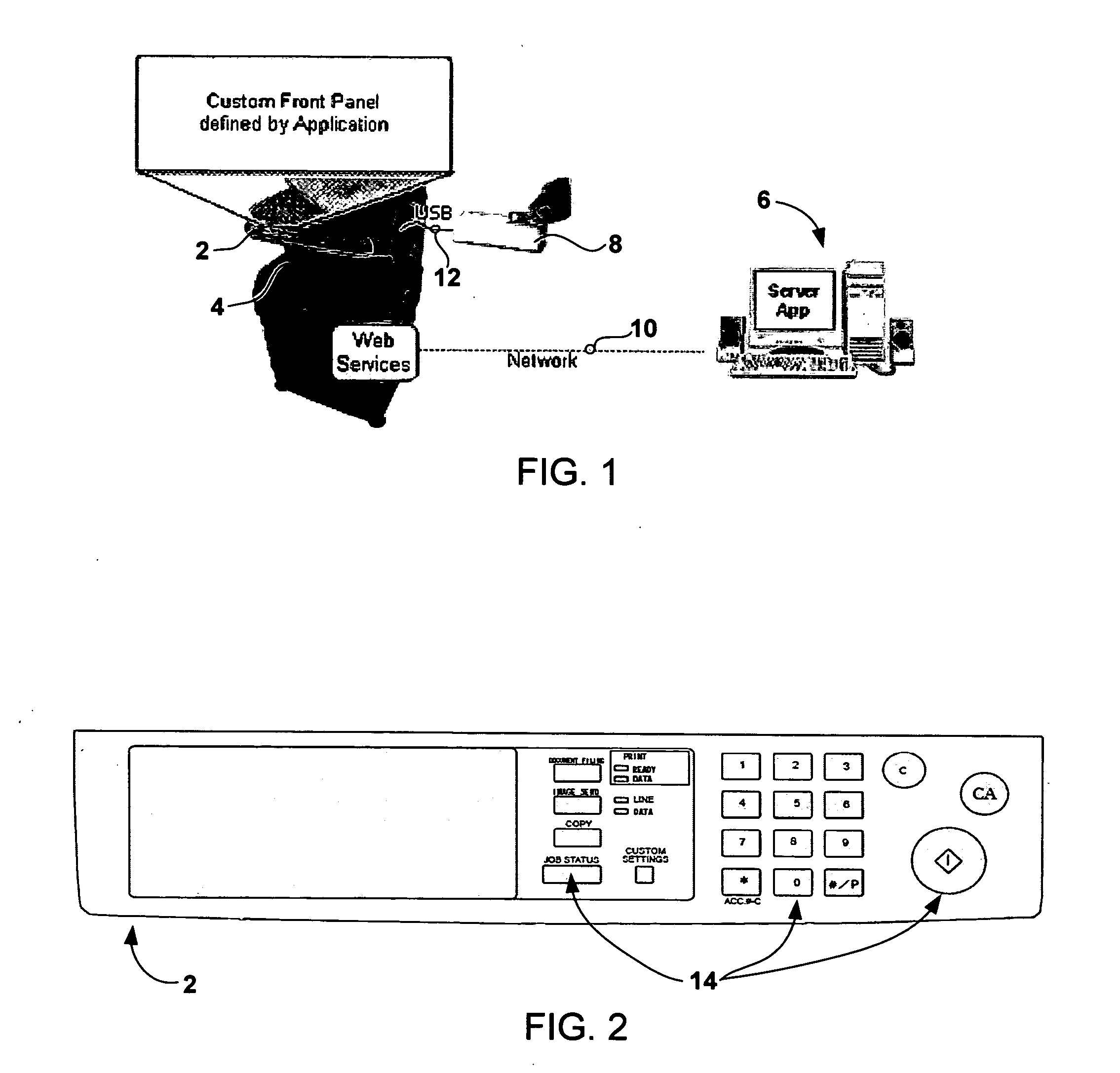
Methods and systems for imaging device credential management and authentication
ActiveUS20060077429A1Digital data processing detailsComputer security arrangementsCredential managementImaging equipment
Owner:SHARP KK
Methods and systems for imaging device credential management
ActiveUS20060077438A1Digital data processing detailsMultiple digital computer combinationsCredential managementImaging equipment
Owner:SHARP KK
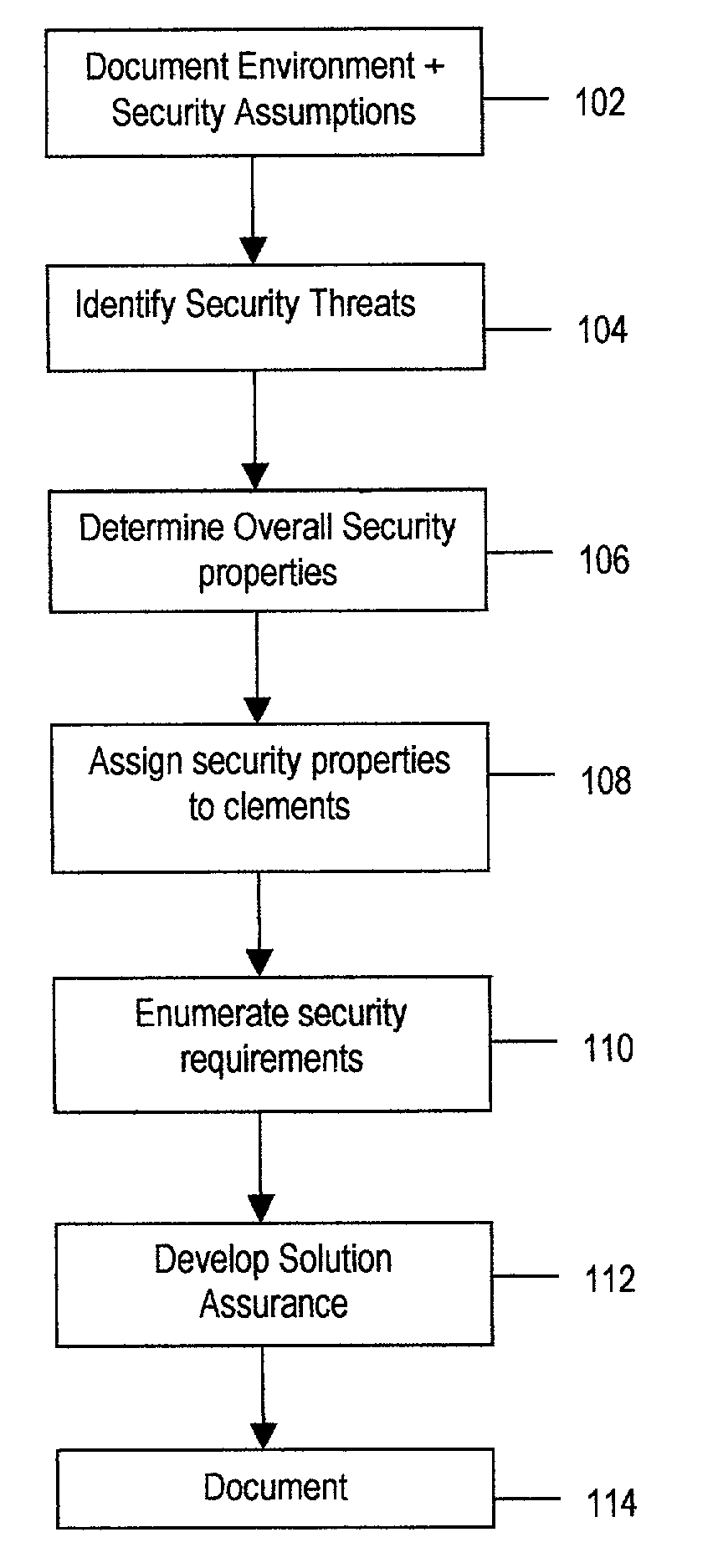
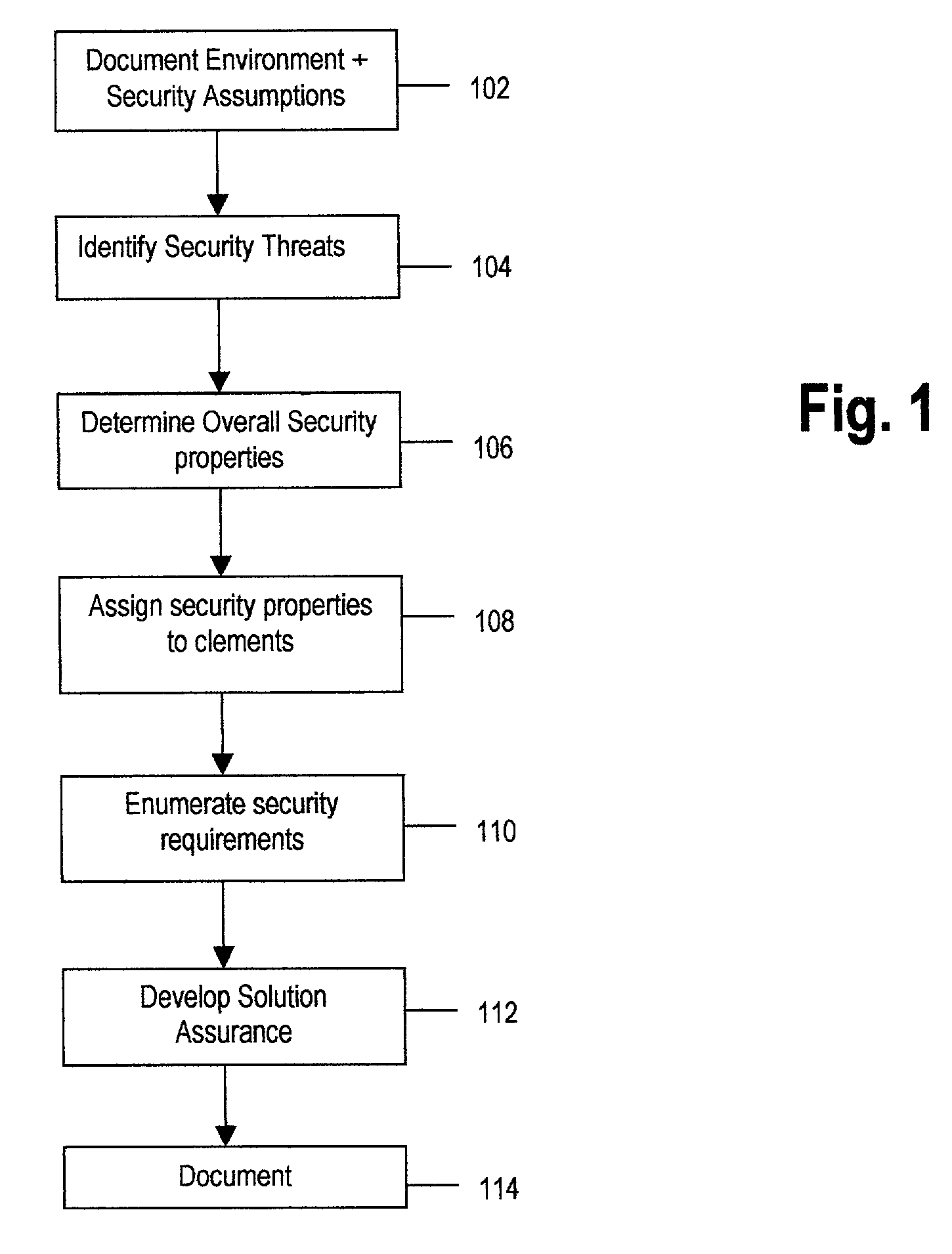
Method and system for architecting a secure solution
InactiveUS7251831B2The process is simple and effectiveMemory loss protectionError detection/correctionSafe systemCredential management
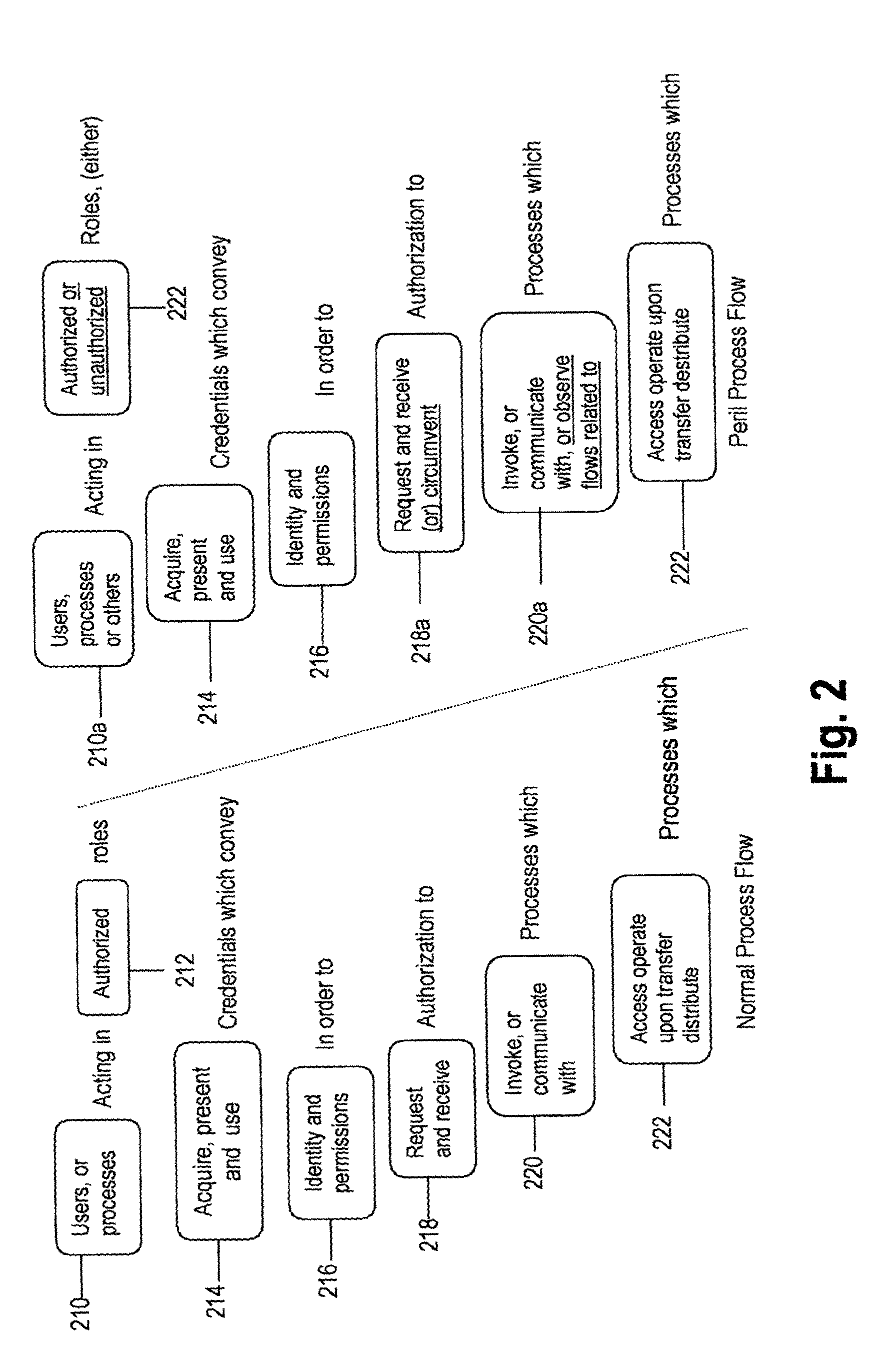
A system and method of designing a secure solution which meets the needs of a customer but which is appropriate and repeatable and may use components which are insecure or not trusted. In its preferred embodiment, the security system includes subsystems selected from access control, information flow, identity and credentials management, integrity and assurance In each subsystem, elements are employed to reduce the effect of perils and to provide a repeatable system design.
Owner:IBM CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com