Integrity verification method for data in cloud storage
An integrity verification and cloud storage technology, applied in the field of cloud storage security, can solve the problems of heavy TPA storage burden, user data information leakage, data encryption and other problems, and achieve the effect of reducing storage burden, ensuring security, and improving utilization.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
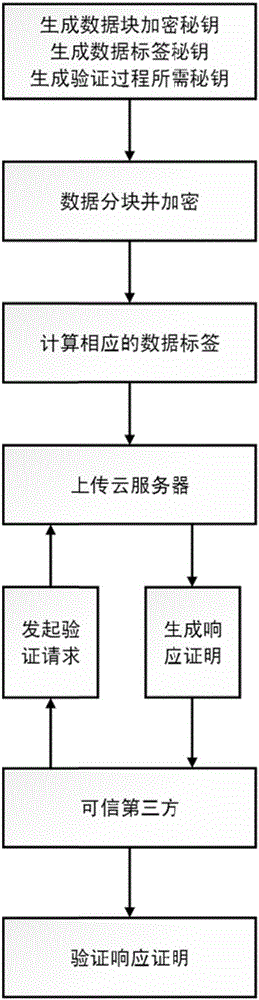
[0024] refer to figure 1 , the implementation steps of the present invention are as follows:
[0025] Step 1: The user generates the key dk for encrypting the data block, the key sk required for the data label, and the key pk required for the verification process.
[0026] (1.1) The user is in the prime number field F q Randomly select a number as the key dk for data block encryption;
[0027] (1.2) The user selects one defined in the prime number field F q The elliptic curve E(F q ), take point G as the base point on the curve, and then randomly select a number x on [1,q-1] as the key sk required for the data label, where q represents a large prime number;
[0028] (1.3) Calculate the public point G A =xG, will (G A , G) as the key pk required in the verification process.
[0029] Step 2: Perform block processing on the data m to be uploaded to the cloud server.
[0030] Set the length of each data block to l, and divide the data m to be uploaded to the cloud server a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com